Configuring SAML SSO with Terraform and PingOne
Learn how to enable Terraform sign-on from the PingOne SSO console (IdP-initiated sign-on) and direct Terraform login using PingOne SSO (SP-initiated sign-on).
Before you begin
-
Link PingOne to an identity repository containing the users requiring application access.
-
Populate Terraform with at least one user to test access.
-
You must have administrative access to PingOne and an administrative account with site-admin permission on Terraform.
|
Whenever TFE-HOSTNAME is specified throughout this document, replace it with the actual value of your Terraform instance hostname. |
Add the Terraform application to PingOne
-
In PingOne, go to Connections → Applications and click + to add a new application.
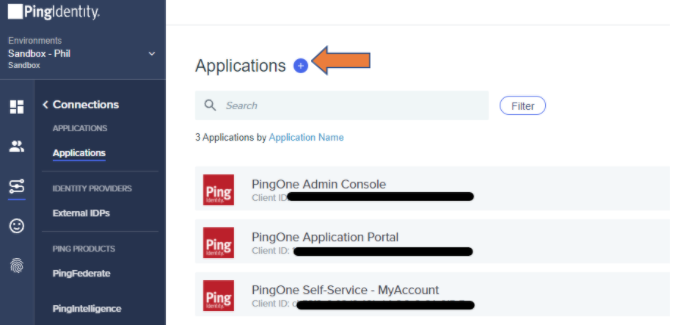
-
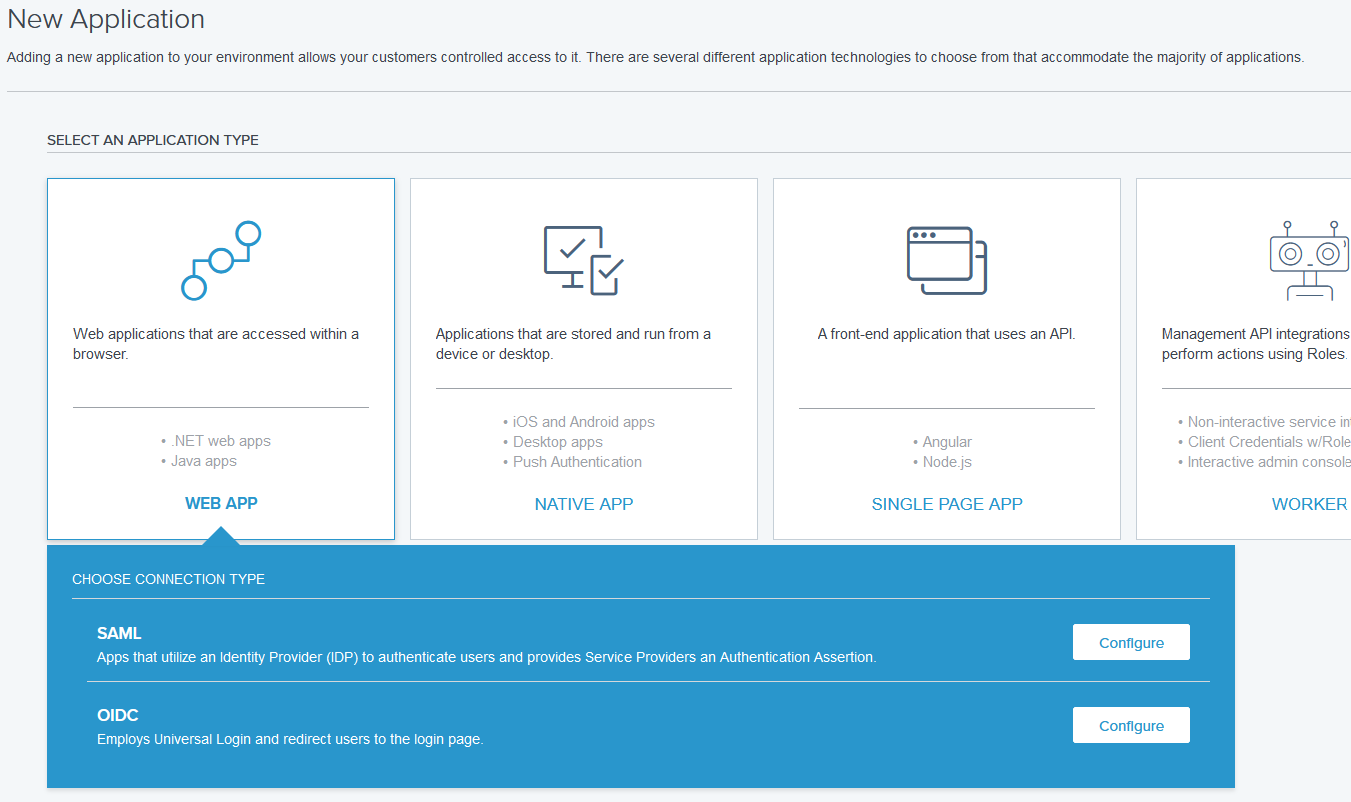
In Select an Application Type, click Web App.
-
In Choose Connection Type, click Configure next to SAML.
-
Enter Terraform as the application name.
-
Optional: Enter a suitable description.
-
Optional: Upload an icon.
-
Click Next.
-
For Provide App Metadata, select Manually Enter.
-
For ACS URLs, enter
https://TFE-HOSTNAME/users/saml/auth -
Choose the Signing Key to use and then click Download Signing Certificate to download it as X509 PEM (
.crt). -
For Entity ID, enter
https://TFE-HOSTNAME/users/saml/metadata -
Leave SLO Endpoint and SLO Response Endpoint blank. Terraform does not support single logout (SLO).
-
In the Subject NameID Format list, select urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress.
-
Set a suitable value for Assertion Validity Duration (in seconds). A value of 300 seconds is typical.
-
Click Save and Continue.
By default, Terraform generates a Username when an account is first created upon initial SSO. This is based on the user email address.
-
Optional: If you want to dictate the Username created for a user, you can include the Username attribute in the security assertion.
You can include the MemberOF attribute to automatically add users to specific Teams in the Terraform platform. Configure which PingOne User Attribute to map to each of these Terraform attributes.
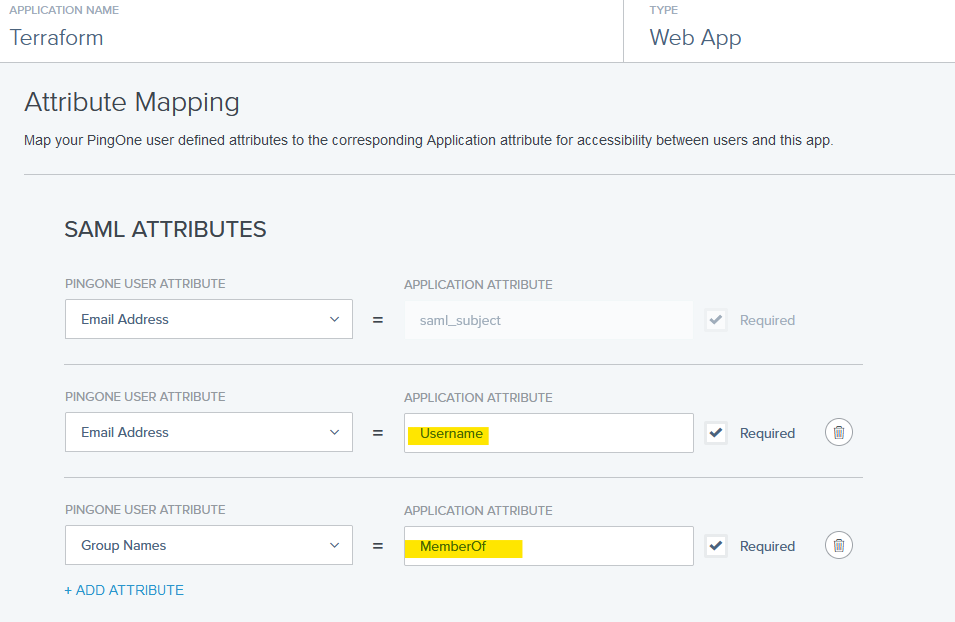
-
Click Save and Close.
-
Enable user access to this new application by moving the toggle to the right.
-
On the Configuration tab of the newly created Terraform application, copy and save the Issuer ID and Initiate Single Sign-On URL values. You will use these for configuring SAML on Terraform.

Add PingOne as an identity provider (IdP) to Terraform
-
Go to
https://TFE-HOSTNAME/app/admin/samland sign on with an administrator account that has site-admin permissions. -
Paste the Initiate Single Sign-On URL value that you saved previously into the Single Sign-On URL field.
-
Open the
.crtfile that downloaded previously in a text editor and copy and paste the entire contents into the IDP Certificate field. -
Click Save SAML settings.
Test the PingOne IdP integration
-
Go to the PingOne application portal and sign on with a user account.
You can find the PingOne Application Portal URL in Dashboard → Environment Properties.
-
Click the Terraform icon.
You’re redirected and presented with a PingOne sign on prompt.
-
Enter your PingOne username and password.
After successful authentication, you’re redirected back to Terraform as a signed-on user.