Configuring SAML SSO with Jira/Confluence and PingOne for Enterprise
Learn how to configure SAML single sign-on (SSO) with Jira/Confluence on premise and PingOne for Enterprise.
About this task
The following table details the required and optional attributes to be configured in the assertion attribute contract.
| Attribute Name | Description | Required / Optional |
|---|---|---|
SAML_SUBJECT |
Username |
Required |
|
A predefined application exists in the application catalog for use with Atlassian Cloud. It is recommended that this is used for Atlassian Cloud integrations. |
Create a PingOne for Enterprise application for Jira/Confluence on premise
|
The following configuration is untested and is provided as an example. Additional steps might be required. |
-
Sign on to the Atlassian application as an administrator and go to Administration → System → SAML Authentication.
-
Select SAML Single Sign On and note the Audience URL (Entity ID) and Assertion Consumer Service URL values.
-
Download the signing certificate.
-
Sign on to PingOne for Enterprise and click Applications.
-
On the SAML tab, click Add Application.
-
Click New SAML Application.
-
In the Application Details section, enter the following:
-
A suitable application name, such as Confluence.
-
A suitable description.
-
A suitable category, such as Information Technology.
-
(Optional) Upload an icon to be used in the PingOne for Enterprise dock.
-
-
Click Continue to Next Step.
-
Select I have the SAML configuration.
-
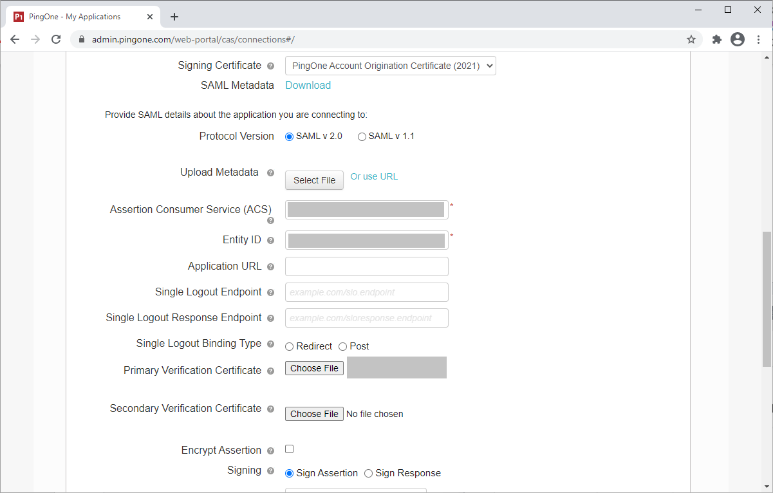
In the Signing Certificate list, select a suitable signing certificate.
-
For Protocol Version, click SAML v.2.0.
-
In the Assertion Consumer Service (ACS) field, enter the ACS value from the Atlassian single sign-on settings.
-
In the Entity ID field, enter the Entity ID value from the Atlassian single sign-on settings.
-
For Primary Verification Certificate, select the signing certificate that you downloaded.
-
Click Continue to Next Step.
-
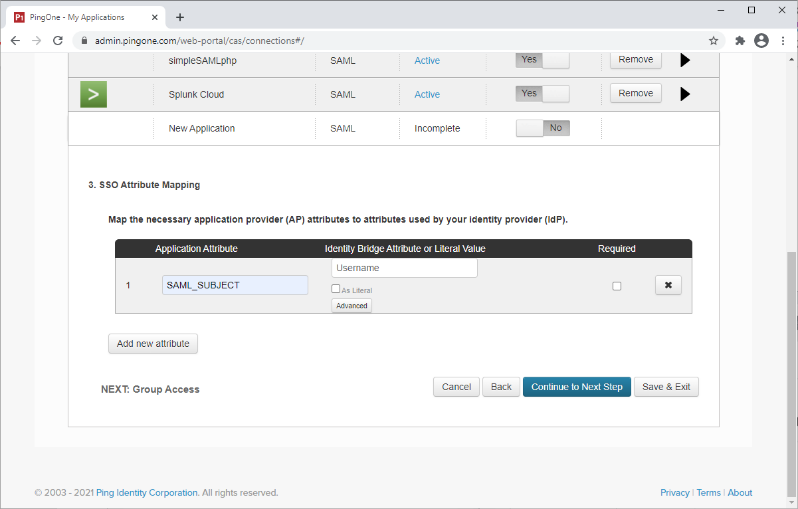
In the SSO Attribute Mapping section, add the following mapping for the SAML_SUBJECT:
-
For Identity Bridge Attribute or Literal Value, select the appropriate attribute. This should match the username for the user in the application.
-
Select the Required check box.
-
-
Click Continue to Next Step.
-
Add the user groups for the application.
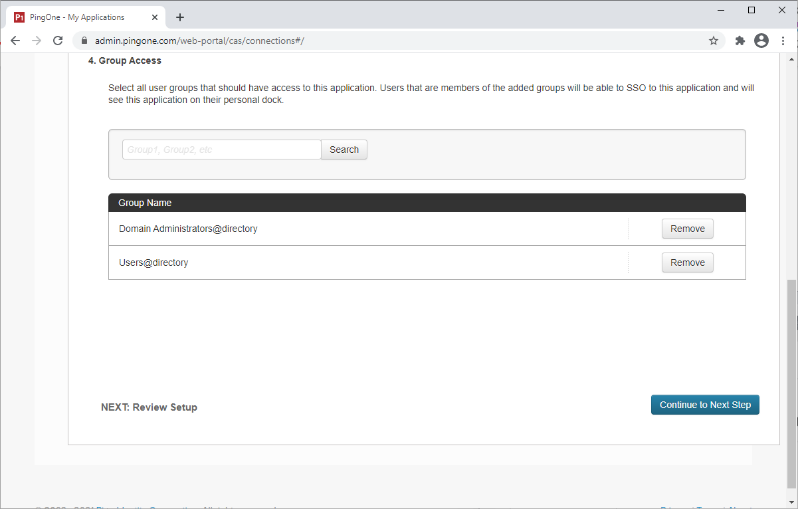
-
Click Continue to Next Step.
-
Review the settings.
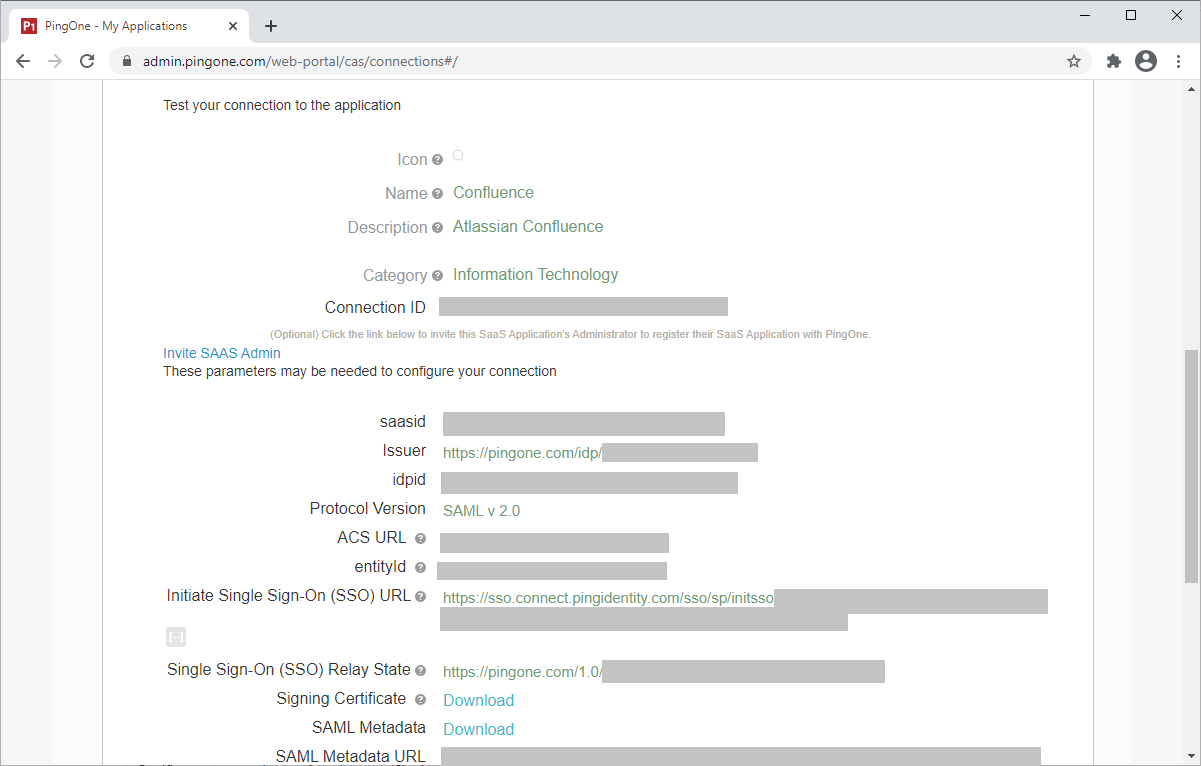
-
Copy the Single Sign-On (SSO) URL value to a temporary location.
This is the IdP-initiated SSO URL that you can use for testing.
-
Note the idpid and Issues values.
-
On the Signing Certificate line, click Download.
You’ll use this for the application configuration.
-
On the SAML Metadata line, click Download.
You’ll use this for the application configuration.
-
Click Finish.
Configure the PingOne for Enterprise IdP Connection for Jira/Confluence on-premise
-
Sign on to the Atlassian application as an administrator.
-
Go to Administration → System → SAML Authentication.
-
Select SAML Single Sign On.
-
Configure the following.
Setting Value Single sign-on issuer
The issuer from PingOne for Enterprise application details noted earlier.
Identity provider single sign-on URL
Enter the Single Sign-On Service URL in the following form, using the idpid previously noted.
https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid=idpidAlternatively, you can retrieve the URL from the metadata that you downloaded.
X509 Certificate
Upload the PingOne for Enterprise signing public certificate that you downloaded.
Login Mode
Choose whether SAML is your primary or secondary authentication.
Configuration is complete.