Configuring SAML SSO with GitHub Enterprise Server and PingOne for Enterprise
Learn how to enable GitHub sign on from the PingOne for Enterprise console (IdP-initiated sign-on) and direct GitHub sign on using PingOne for Enterprise (SP-initiated sign-on).
Before you begin
-
Link PingOne for Enterprise to an identity repository containing the users requiring application access.
-
Populate GitHub with at least one user to test access.
-
You must have administrative access to PingOne for Enterprise and GitHub.
Download the GitHub metadata
-
Go to where your GitHub server publishes its metadata (
https://GitHub-hostname/saml/metadata). -
Save the metadata as an XML file.
Set up the GitHub application in PingOne for Enterprise
-
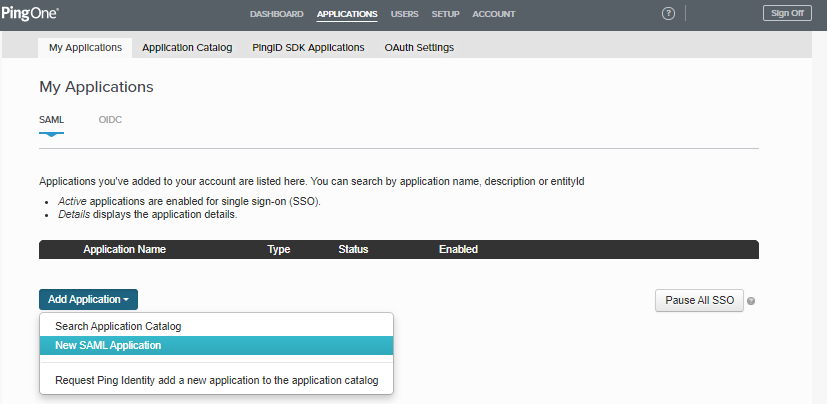
Sign on to PingOne for Enterprise for Enterprise and go to Applications → Application Catalog.
-
On the SAML tab, click Add Application.
-
Enter GitHub as the application name.
-
Enter a suitable description.
-
Select Collaboration as the category.
-
Click Continue to Next Step.
-
In the Upload Metadata row, click Select File and upload the metadata file that you saved from GitHub.
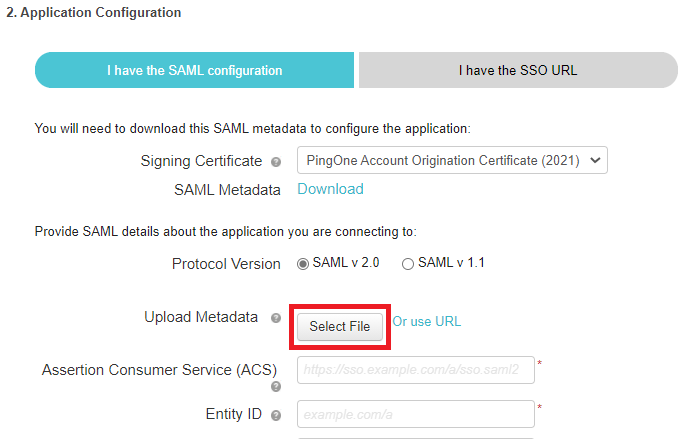
The following values should now be populated:
-
ACS URL:
https://github.com/orgs/your-tenant/saml/consume -
Entity ID:
https://github.com/orgs/your-tenant
-
-
Click Continue to Next Step.
-
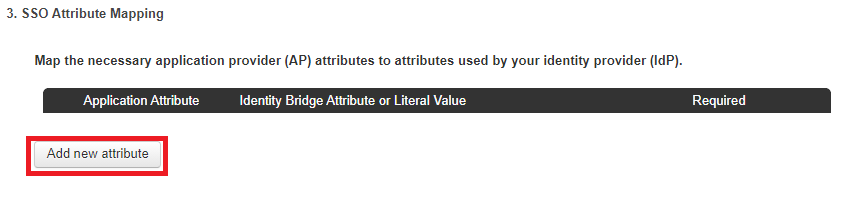
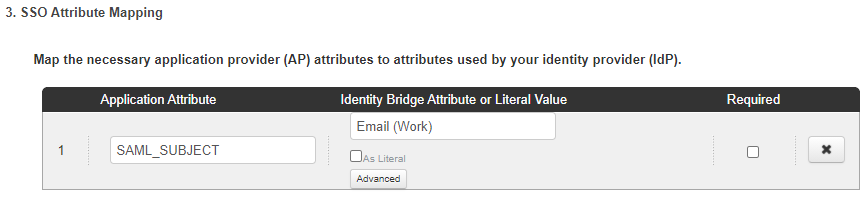
Click Add new attribute and map SAML_SUBJECT to the attribute containing the user’s email address.
-
Optional: Add the username and full_name attributes, then map these to appropriate attributes.
This populates these values in GitHub when a new user signs on.
-
Click Continue to Next Step.
-
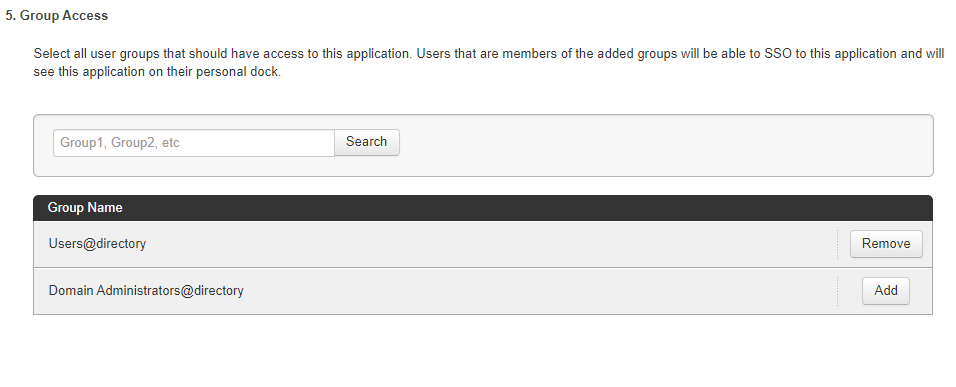
Click Add for all user groups that should have access to GitHub.
-
Click Continue to Next Step.
-
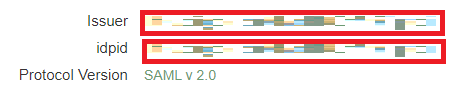
Copy the Issuer and idpid values.
-
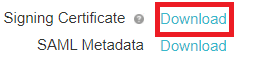
Download the signing certificate.
-
Click Finish.
Add the PingOne for Enterprise IdP Connection to GitHub
-
Sign on to GitHub Enterprise Server as an administrator.
-
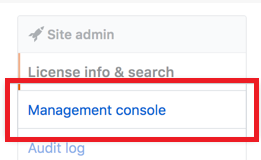
Click the Rocket icon.
-
Click Management Console.
-
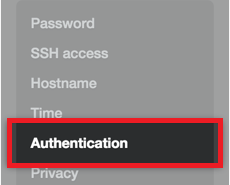
Click Authentication.
-
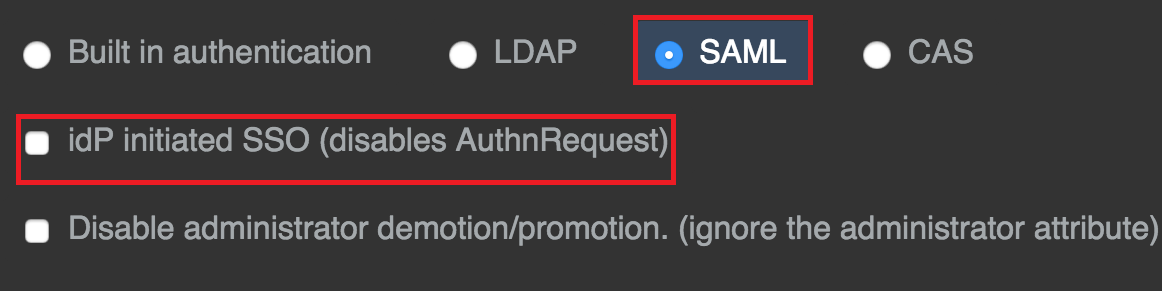
Click SAML and select the idP initiated SSO (disables AuthnRequest) check box.
-
In the Single sign-on URL field, enter
https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid=idpid-value-from-PingOne.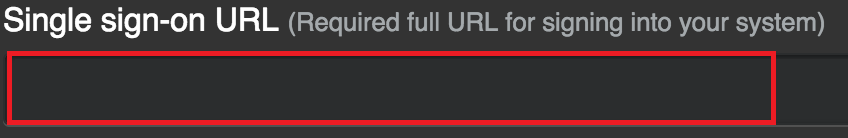
-
In the Issuer field, enter the PingOne for Enterprise Issuer value.
-
Click Choose File for the Verification Certificate and upload the PingOne signing certificate that you downloaded.
-
Click Save Settings.