Configuring SAML SSO with GitHub Enterprise Server and PingFederate
Learn how to enable GitHub sign-on from a PingFederate URL (IdP-initiated sign-on) and direct GitHub sign-on using PingFederate (SP-initiated sign-on).
Before you begin
-
Configure PingFederate to authenticate against an IdP or datastore containing the users requiring application access.
-
Populate GitHub with at least one user to test access.
-
You must have administrative access to PingFederate and GitHub.
Download the GitHub metadata
-
Go to where your GitHub server publishes its metadata (
https://GitHub-hostname/saml/metadata). -
Save the metadata as an XML file.
Create a PingFederate SP connection for GitHub
-
Sign on to the PingFederate administrative console.
-
Create an SP connection for GitHub in PingFederate using the GitHub metadata file:
-
Configure using Browser SSO profile SAML 2.0.
-
Enable the following SAML Profiles:
-
IdP-Initiated SSO
-
SP-Initiated SSO
-
-
In Assertion Creation: Attribute Contract, if you want to have these values populated in GitHub, extend the contract to add attributes called username and full_name.
-
In Assertion Creation: Authentication Source Mapping: Attribute Contract Fulfillment, map SAML_SUBJECT to an attribute containing the user’s email address.
If added, map username and full_name to appropriate attributes.
-
In Protocol Settings: Allowable SAML Bindings, enable POST.
-
In Credentials: Digital Signature Settings, select the PingFederate Signing Certificate.
-
-
Save the configuration.
-
Export the signing certificate.
-
Export and then open the metadata file.
Copy the value of the entityID and the Location entry (
https://your-value/idp/SSO.saml2).
Add the PingFederate IdP Connection to GitHub
-
Sign on to GitHub Enterprise Server as an administrator.
-
Click the Rocket icon.
-
Click Management Console.
-
Click Authentication.
-
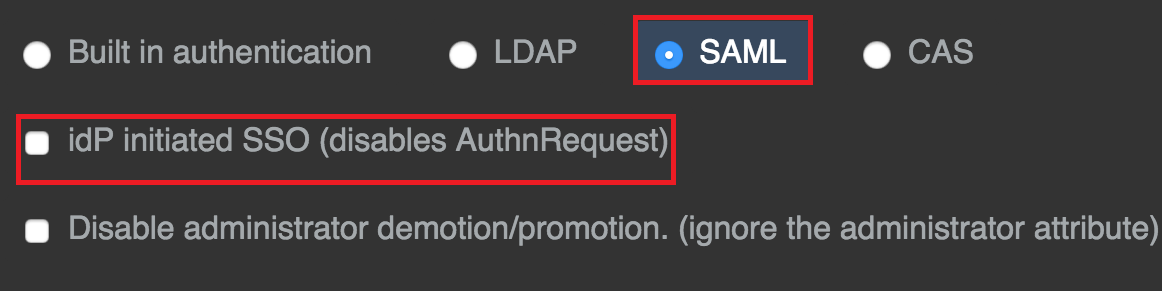
Click SAML and select the idP initiated SSO (disables AuthnRequest) check box.
-
In the Single sign-on URL field, enter the PingFederate Location value (
https://your-value/idp/SSO.saml2).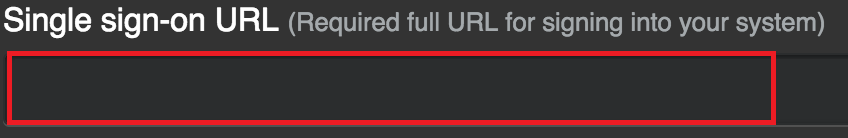
-
In the Issuer field, enter the PingFederate entityID value.
-
Click Choose File for the Verification Certificate and upload the PingFederate signing certificate that you downloaded
-
Click Save Settings.