Configuring SAML SSO with SuccessFactors and PingFederate
Learn how to enable SuccessFactors sign-on from a PingFederate URL (IdP-initiated sign-on) and direct SuccessFactors sign-on using PingFederate (SP-initiated sign-on).
Before you begin
-
Configure PingFederate to authenticate against an IdP or datastore containing the users requiring application access.
-
Populate SuccessFactors with at least one user to test access.
-
You must have administrative access to PingFederate.
-
You must have access to either SuccessFactors Customer Support or the SuccessFactors Provisioning tool.
Create a PingFederate SP connection for SuccessFactors
-
Sign on to the PingFederate administrative console.
-
Create an SP connection for SuccessFactors in PingFederate:
-
Configure usingBrowser SSO profile SAML 2.0.
-
Set Partner’s Entity ID to
https://www.successfactors.com. -
Enable the following SAML Profiles:
-
IdP-Initiated SSO
-
SP-Initiated SSO
-
-
In Assertion Creation: Attribute Contract, extend the contract to add an attribute named SAML_NAME_FORMAT.
-
In Assertion Creation: Authentication Source Mapping: Attribute Contract Fulfillment, map SAML_SUBJECT and map SAML_NAME_FORMAT to
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent. -
In Protocol Settings: Assertion Consumer Service URL, set binding to POST, and set Endpoint URL to
http://placeholder.You will update this value later.
-
In Protocol Settings: Allowable SAML Bindings, enable POST.
-
In Credentials: Digital Signature Settings, select the PingFederate signing certificate.
-
-
Save the configuration.
-
Export the signing certificate.
-
Export and then open the metadata file, and copy the following values:
-
The entityID
-
The Location entry (
https://your-value/idp/SSO.saml2)
-
Add the PingFederate IdP Connection to SuccessFactors
-
Sign on to the SuccessFactors Provisioning application.
If you do not have access to this application, you will need to contact SuccessFactors’ Customer Support. -
Search for your company and click its name link.
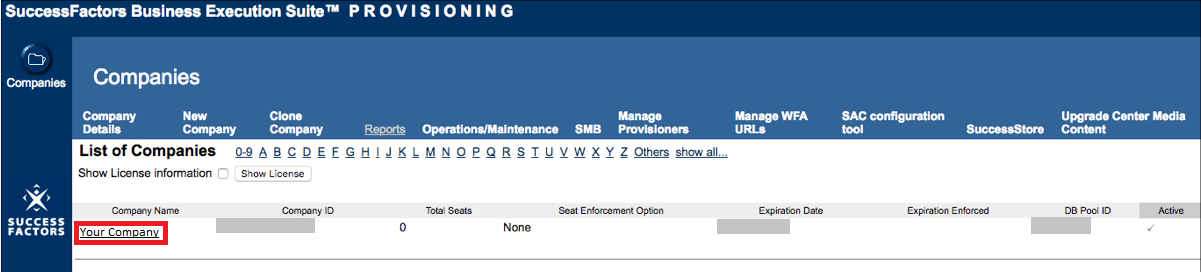
-
Click Single Sign-On (SSO) Settings.
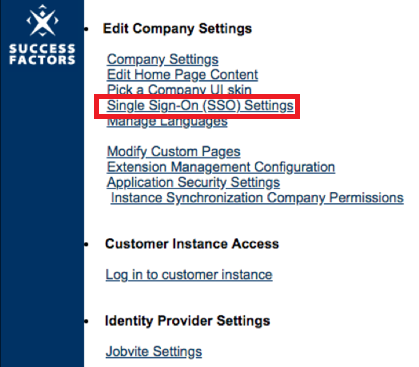
-
In the For SAML based SSO section, click SAML v2 SSO.
-
In the SAML Asserting Parties (IdP) list, select Add a SAML Asserting Party, and enter the following values:
Field Value SAML Asserting Party Name
PingFederate
SAML Issuer
The PingFederate Issuer value
Require Mandatory Signature
Assertion
Enable SAML Flag
Enabled
Login Requested Signature (SF Generated/SP/RP)
Select No.
SAML Profile
Browser/Post Profile
SAML Verifying Certificate
Paste the PingFederate signing certificate contents.
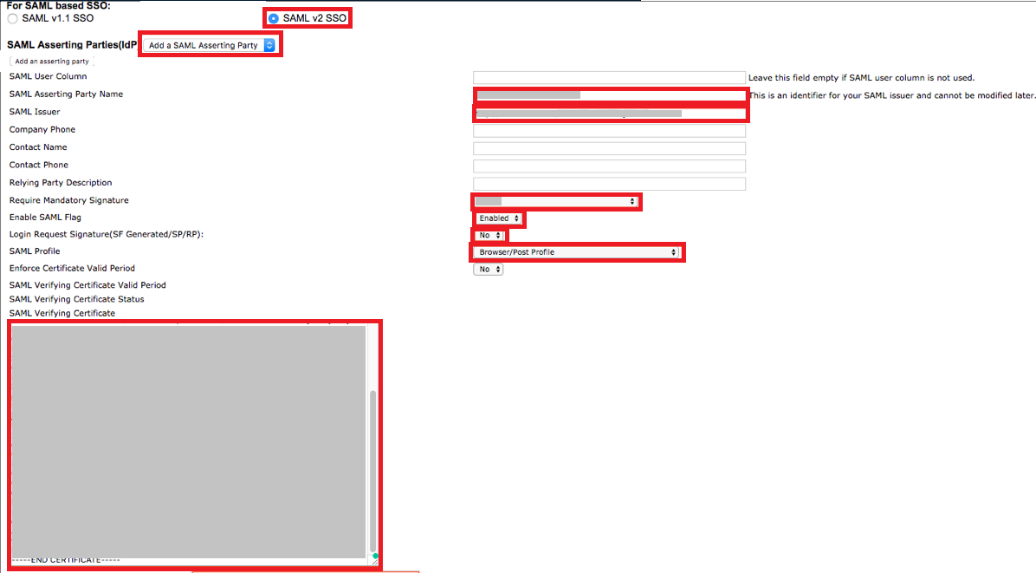
-
In the SAML v2: SP-initiated login section, enter the following values:
Field Value Enable sp initiated login (AuthnRequest)
Select Yes.
Default issuer
Selected.
single sign on redirect service location (to be provided by idp)
https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid=IdP-ID-valueSend request as Company-Wide issuer
Select Yes.
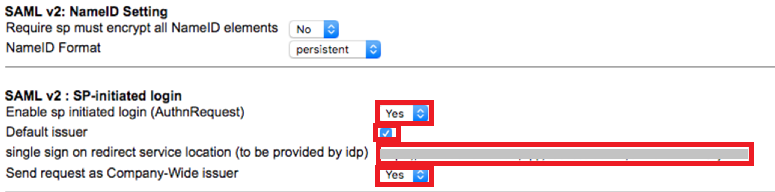
-
Click Add an asserting party to save the configuration.
-
In the SAML Asserting Parties (IdP) list, select the asserting party that you created.
-
Go to Single Sign On Features.
-
In the Single Sign On Features section, enter any text value in the Reset Token field.
A value is required only to switch on SSO.
-
Click Save Token.

-
Record the SuccessFactors Assertion Consumer Service URL value containing your SuccessFactors Hostname and Company ID.
(
https://your-hostname.successfactors.com/saml2/SAMLAssertionConsumer?company=your-company-ID)
Update the ACS URL values in PingFederate
-
Sign on to the PingFederate administrative console.
-
Edit the SP connection for SuccessFactors.
-
Set Assertion Consumer Service URL → Endpoint URL to the SuccessFactors Assertion Consumer Service URL value.
(
https://your-hostname.successfactors.com/saml2/SAMLAssertionConsumer?company=your-company-ID) -
Save the changes.