Configuring SAML SSO with Freshworks and PingOne
Learn how to configure SAML single sign-on (SSO) with Freshworks and PingOne.
Before you begin
You must have a Business level or higher plan in Freshworks. Learn more at https://support.freshworks.com/support/solutions/articles/237923.
Configure SSO in Freshworks
-
Sign on to your Freshworks Admin account homepage and go to the Security tab.
-
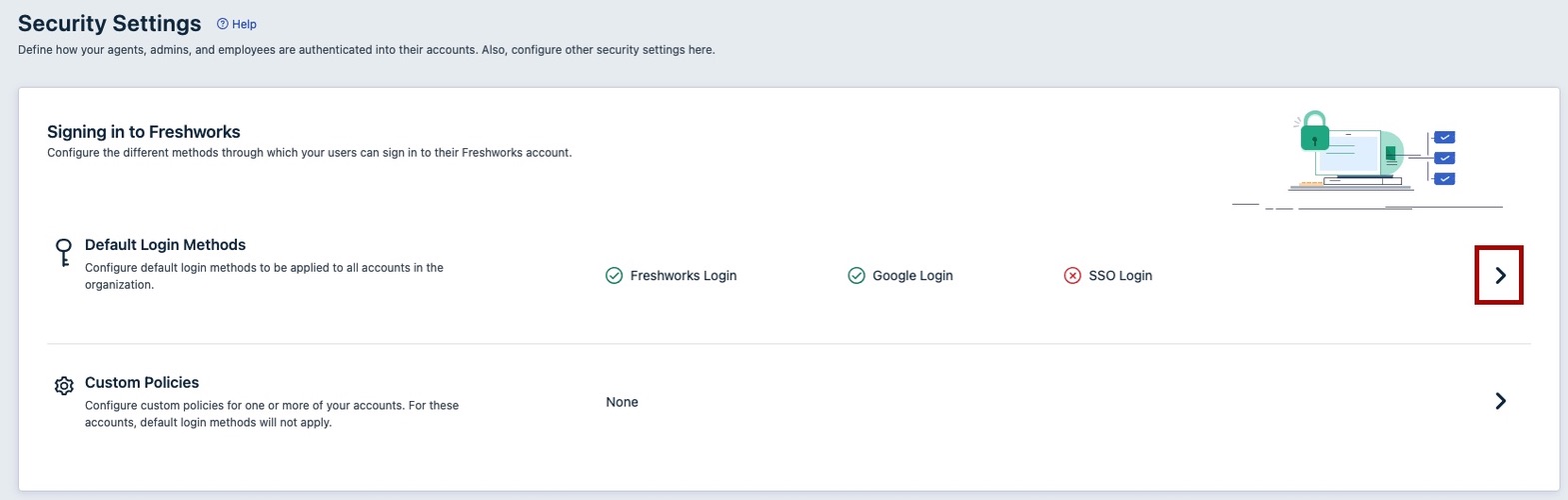
On the Security Settings page, in the Default Login Methods section, click the right arrow.
-
On the corresponding Login Methods page, click the SSO Login toggle.
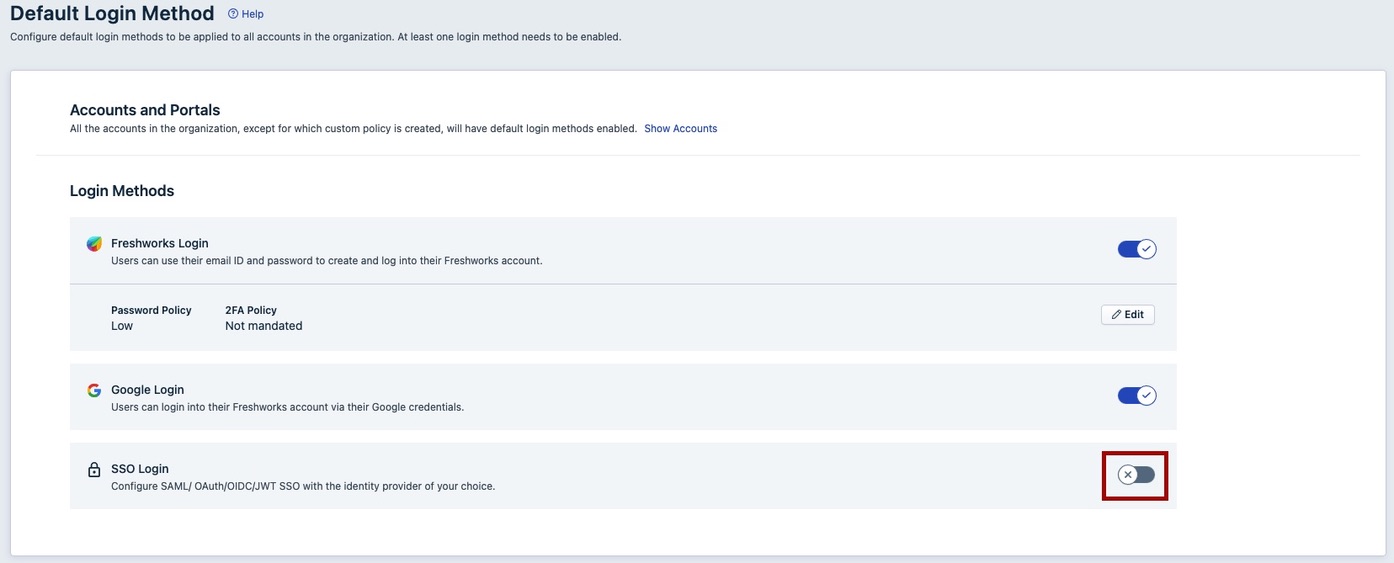
The Configure SSO panel opens.
-
On the Configure SSO panel, in the IdP of your choice section, click SAML.
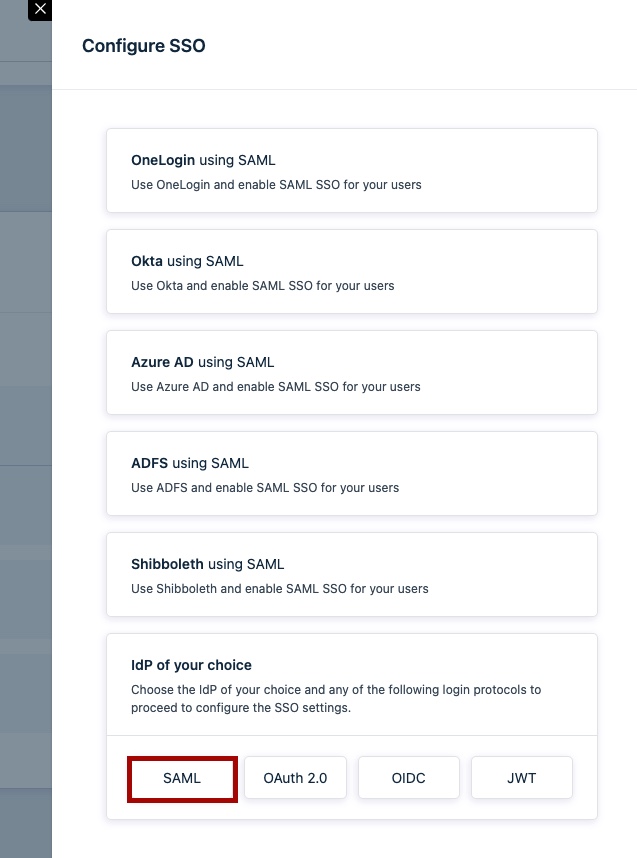
-
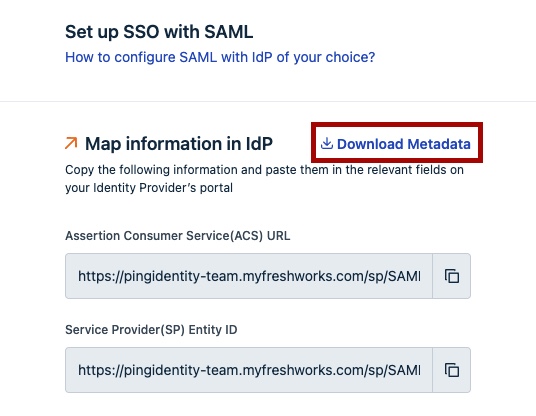
On the Set up SSO with SAML page, in the Map information in IdP section, make a note of the Assertion Consumer Services (ACS) URL and Service Provider (SP) Entity ID values. You will need them later.
Click Download Metadata.
Configure SSO in PingOne
-
In PingOne, go to Connections → Applications.
-
Click the + icon next to Applications.
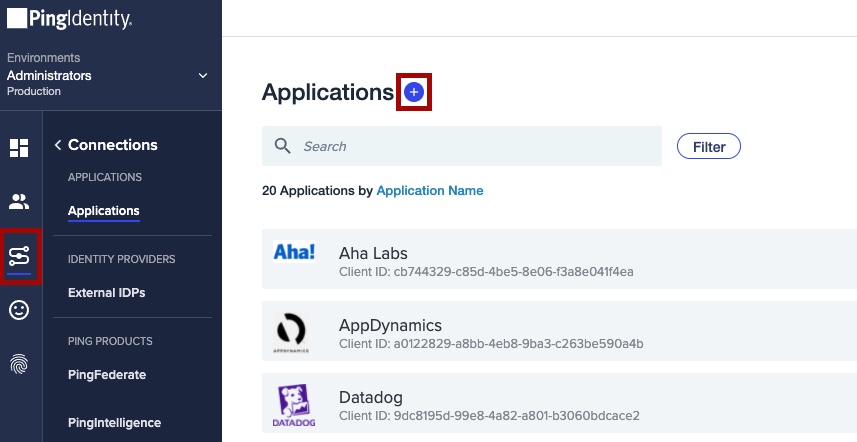
You will use the settings displayed in Step 5 of the previous procedure to begin configuring Freshworks within PingOne.
-
On the New Application page, click Advanced Configuration.
-
In the Choose Connection Type list, on the SAML line, click Configure.
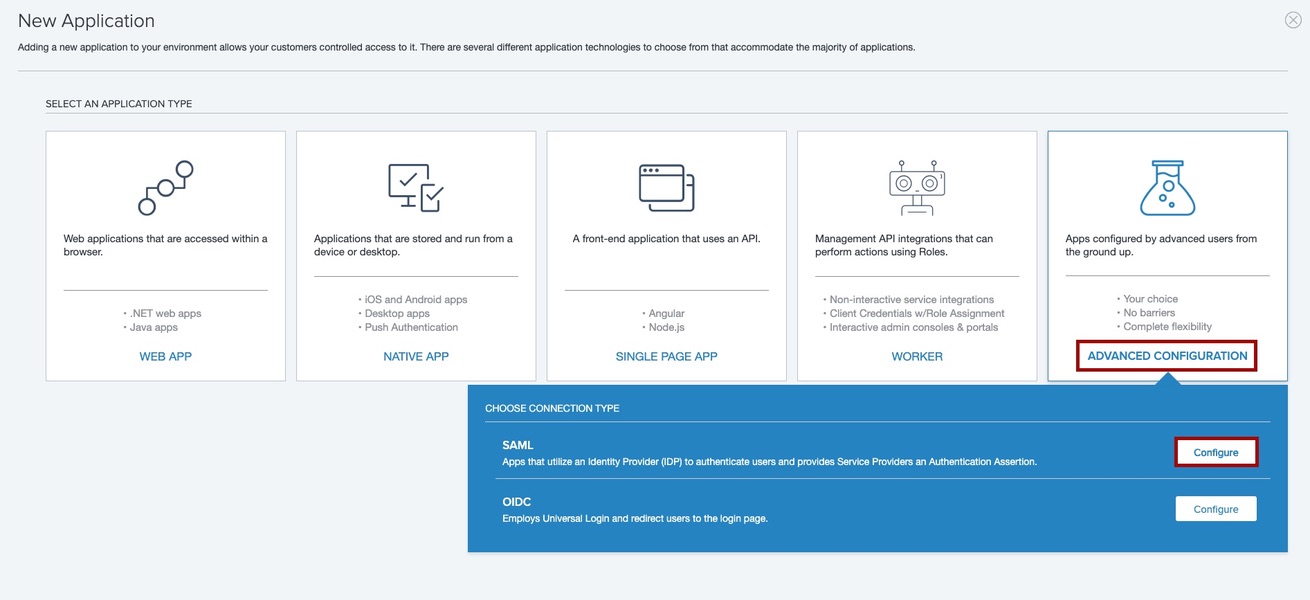
-
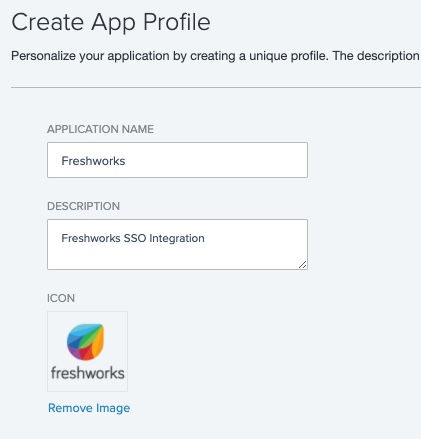
In Create App Profile, enter the values for:
-
Application Name (Required)
-
Description (Optional)
-
Icon (Optional)
-
-
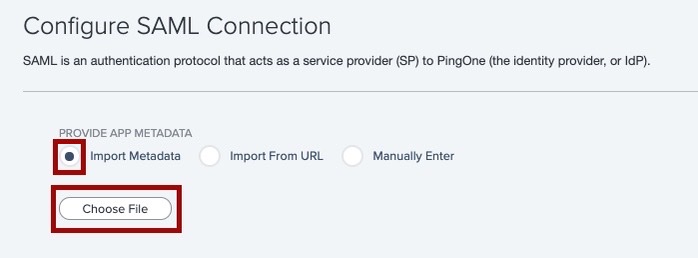
On the Configure SAML Connection page, in the Provide App Metadata section, click Import Metadata.
Upload the metadata downloaded previously and click Import.
After import, all necessary fields are populated automatically, except for the Assertion Validity Duration.
-
In the Assertion Validity Duration field, enter a valid duration value (in seconds), such as 3600.
-
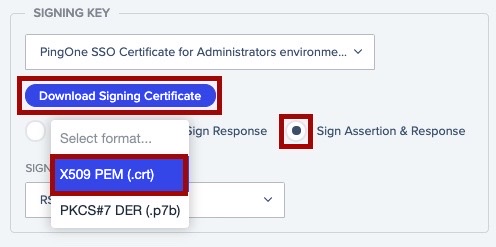
In the Signing Key section, select Download Signing Certificate and download in the X509 PEM (.crt) format.
Make sure that Sign Assertion & Response is selected, then click Save and Continue.
-
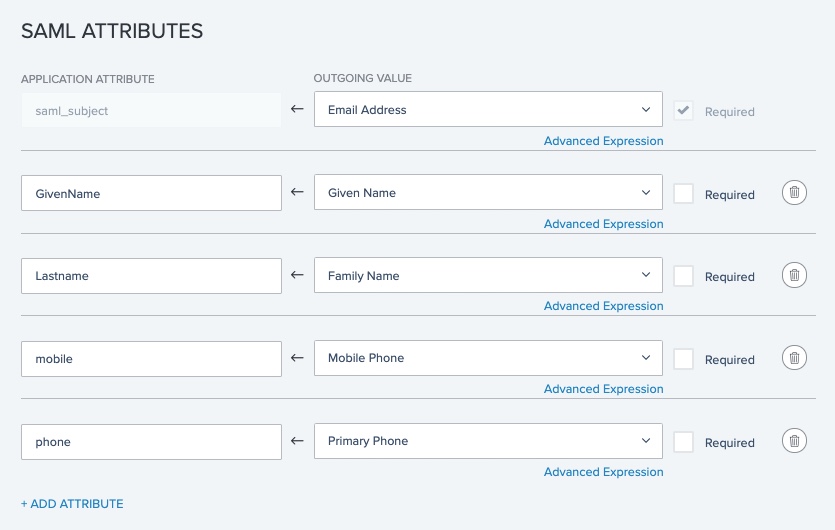
On the Attribute Mapping page, enter the values for the following attributes:
-
Email Address = saml_subject
-
givenName
-
LastName
-
mobile
-
phone
-
-
Click Save and Close to finalize the creation of the application.
-
After you create the application, click the toggle next to the application to enable it.
-
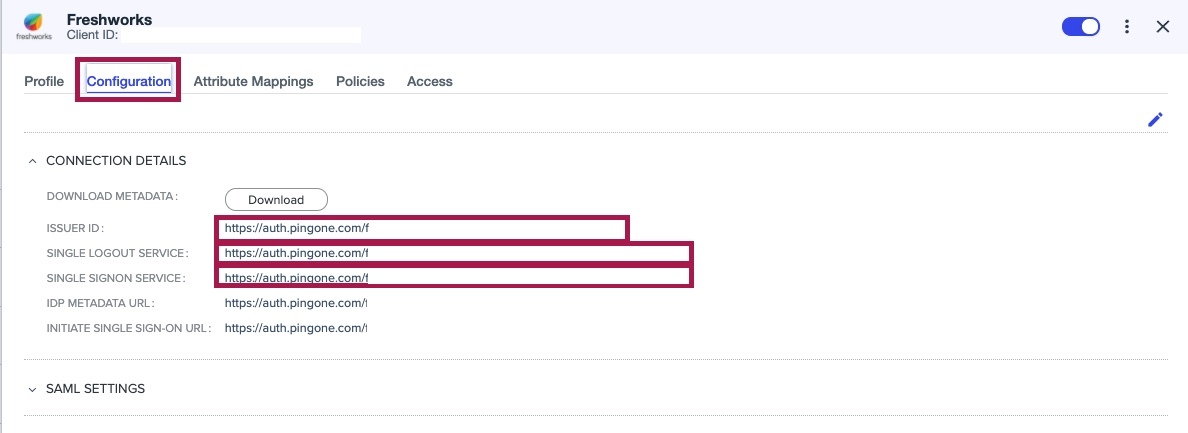
Select Configuration and copy the following values for later use.
-
Issuer ID
-
Single Logout Service (Optional)
-
Single SignOn Service
-
Integrate SAML SSO with Freshworks and PingOne
-
In Freshworks, go to Set up SSO with SAML and paste the information from the previous step into the below locations:
-
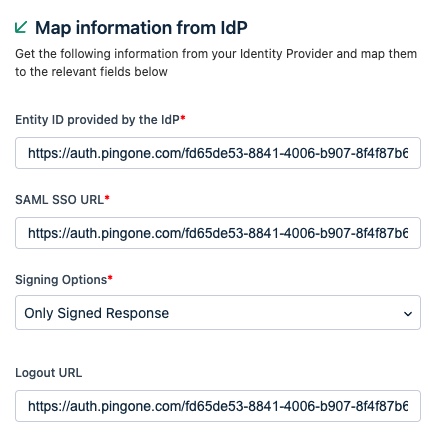
Entity ID provided by the IdP = the Issuer ID value from PingOne
-
SAML SSO URL = the Single SignOn Service value from PingOne
-
Logout URL = the Single Logout Service value from PingOne (Optional)
-
-
Upload the X509 certificate that you downloaded previously. Open the downloaded file with a text editor and copy and paste the certificate into the Security certificate field, then select Configure SSO.
You must include the
BEGIN CERTIFICATEandEND CERTIFICATEtext as part of the certificate upload.
-
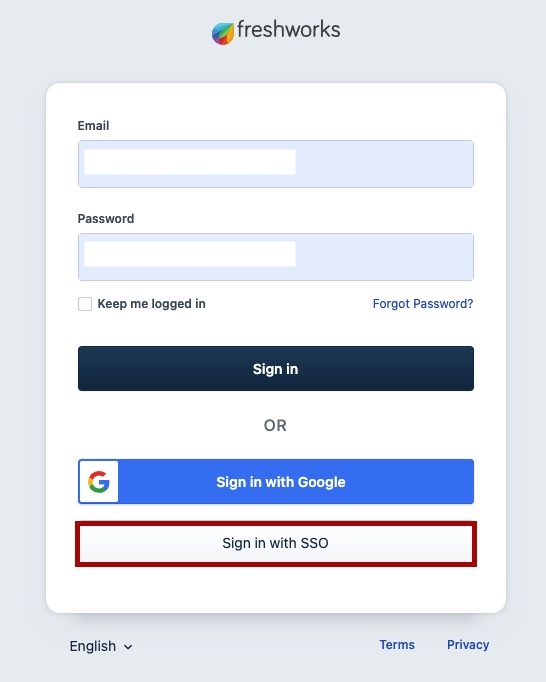
Sign out of your Freshworks account, then click the Sign in with SSO to sign on.
You’re proxied into your account, finalizing the configuration.
Create and assign identities in PingOne
Before you can test the integration, create and assign identities in PingOne. If you’ve already assigned identities and groups in PingOne, move on to Test the integration.
-
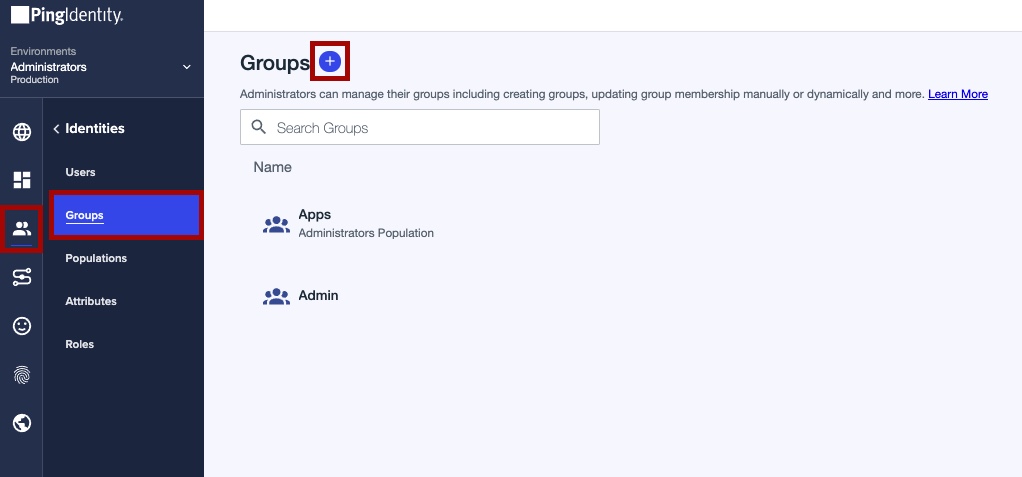
In PingOne, go to Identities → Groups and click the + icon next to Groups.
-
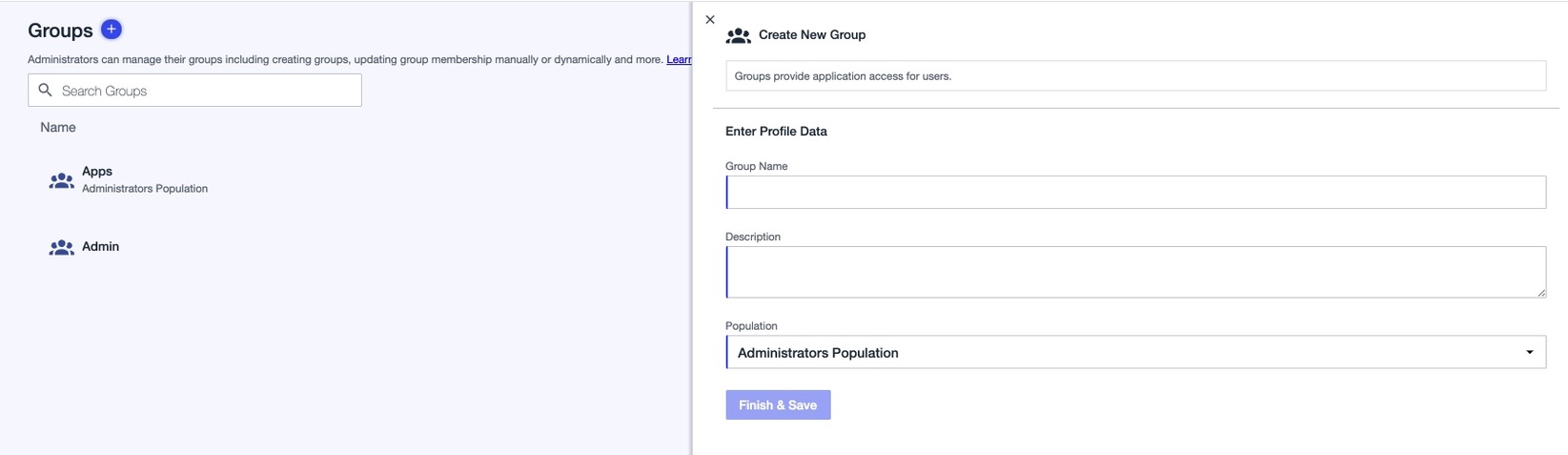
On the Create New Group page, enter values for the following:
-
Group Name (Required)
-
Description (Optional)
-
Population (Optional)
-
-
Click Finish & Save.
-
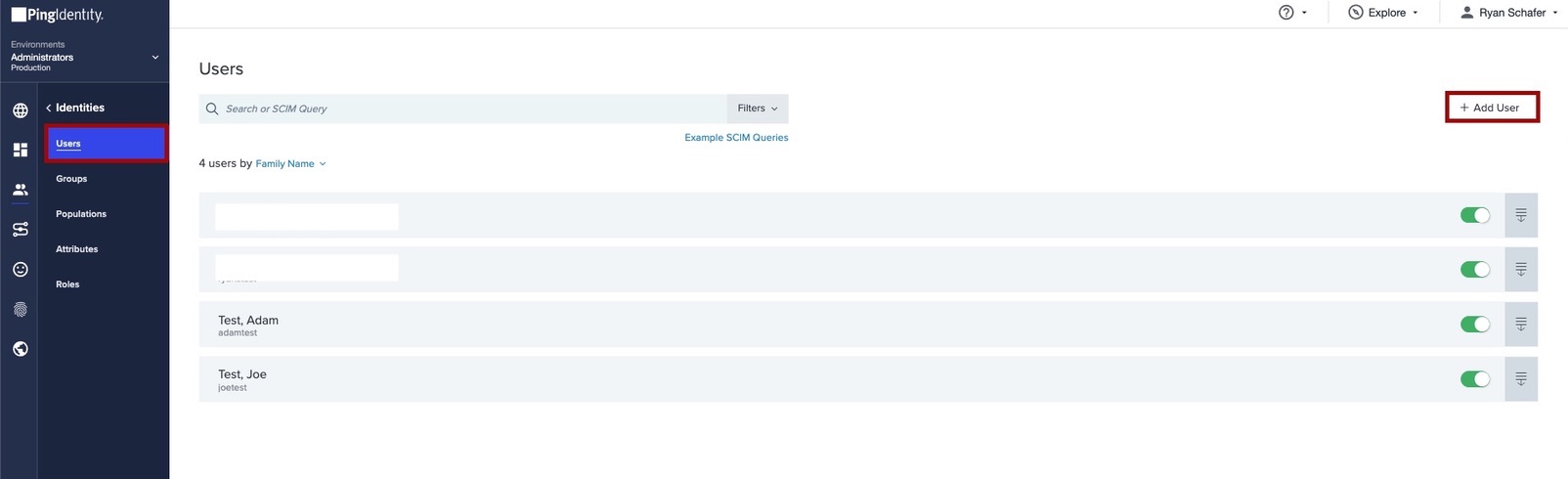
To add identities to the group, on the Identities tab, go to Users → + Add User.
-
On the Add User page, enter all the necessary information for a user.
Verify that the first name, last name, and email address are correct, as these are values passed in the SAML assertion.
-
Click Save.
-
Assign the user that you created to the group that you created previously.
Locate the user you created and do the following:
-
Expand the section for the user.
-
Select the Groups tab.
-
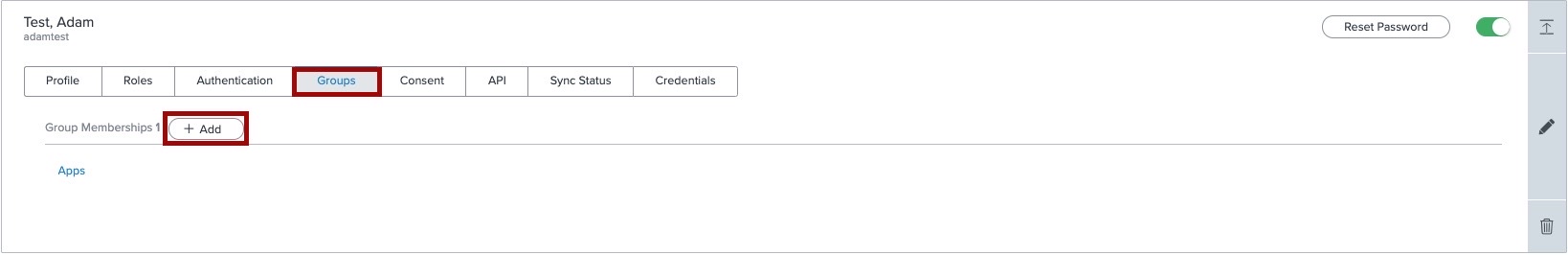
Click Add.
-
-
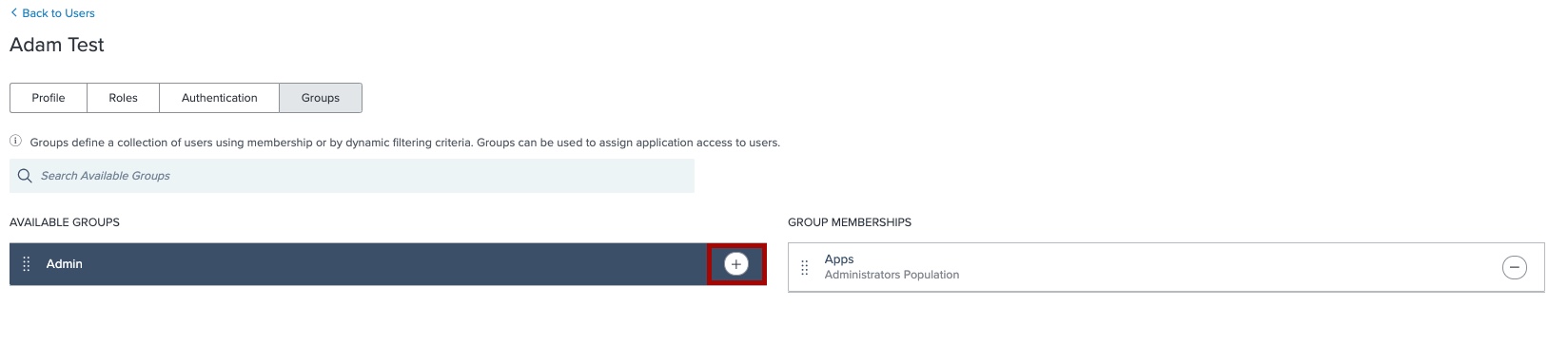
In the Available Groups section, select the group that you created and click the icon to add it to the user’s group memberships. Click Save.
-
On the Connections tab for the Freshworks application do the following:
-
Click the Access tab.
-
Click the Pencil icon to edit the configuration.

-
-
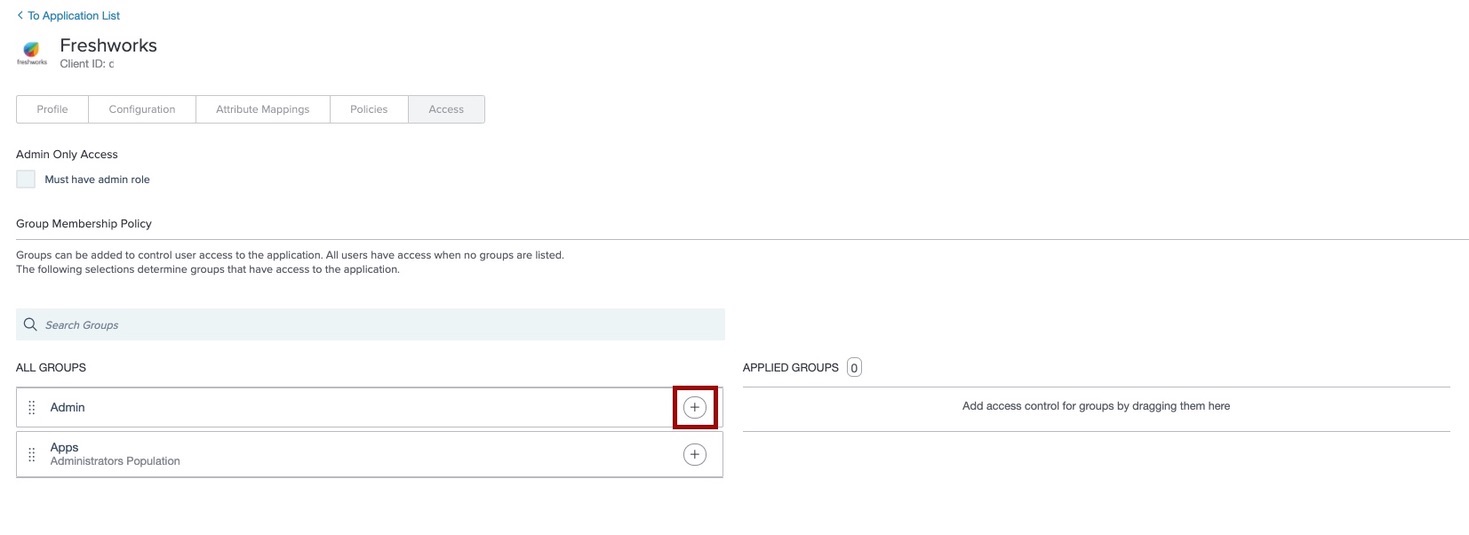
Select the group that you created and add it to the Applied Groups section. Click Save.
Test the integration
You’re now ready to test the integration.
-
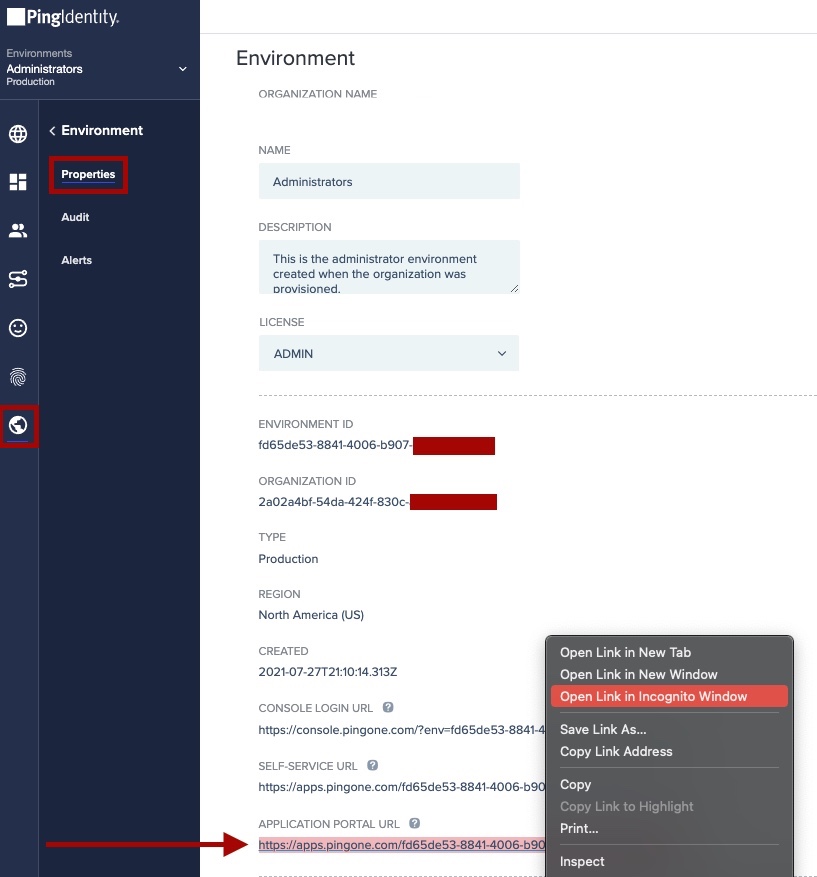
In the PingOne admin console, go to Dashboard → Environment Properties.
-
Right-click on the Application Portal URL and open it in a private browser session.
-
Sign on as the test user that you created and click the Freshworks tile.
You’re signed on to the user’s Freshworks account using SSO and testing is complete.