Configuring SAML SSO with Jamf Pro and PingOne for Enterprise
Enable Jamf Pro sign-on from the PingOne for Enterprise console (IdP-initiated sign-on) and direct JAMF Pro sign-on using PingOne for Enterprise (SP-initiated sign-on) with single logout (SLO).
Before you begin
-
Link PingOne for Enterprise to an identity repository containing the users requiring application access.
-
Populate Jamf Pro with at least one user to test access.
-
You must have administrative access to PingOne for Enterprise.
Add the Jamf Pro application to PingOne for Enterprise
-
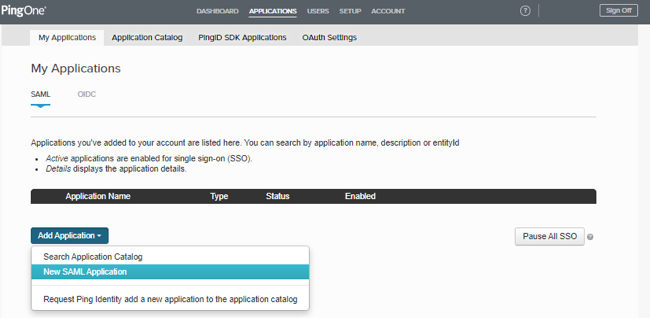
Sign on to PingOne for Enterprise and go to Applications → My Applications.
-
On the SAML tab, click Add Application.
-
Enter
Jamf Proas the application name. -
Enter a suitable description.
-
Choose a suitable category.
-
Click Continue to Next Step.
-
Enter the following values:
Field Value Assertion Consumer Service (ACS)
https://your-instance.jamfcloud.com/saml/SSOEntity ID
https://your-instance.jamfcloud.com/saml/metadataSingle Logout (SLO) Endpoint
https://your-instance.jamfcloud.com/saml/SingleLogoutSingle Logout Binding Type
POST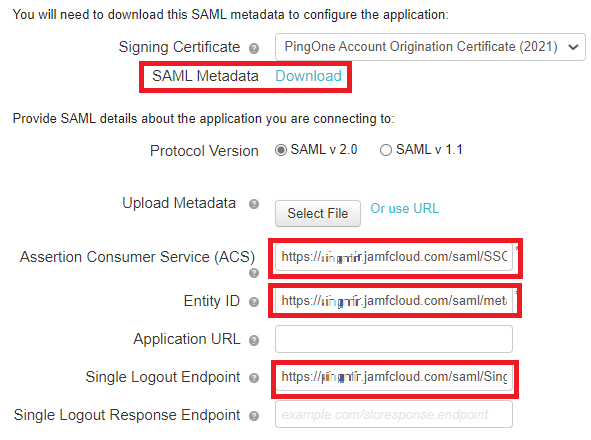
-
On the SAML Metadata line, click Download.
-
Click Continue to Next Step.
-
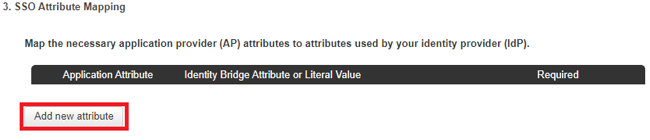
Click Add new attribute.
-
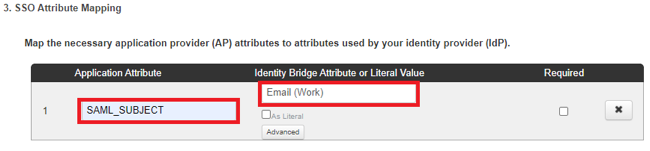
Add the SAML_SUBJECT attribute and map it to your email attribute.
-
Click Continue to Next Step.
-
Click Add for each user groups that should have access to JAMF Pro.
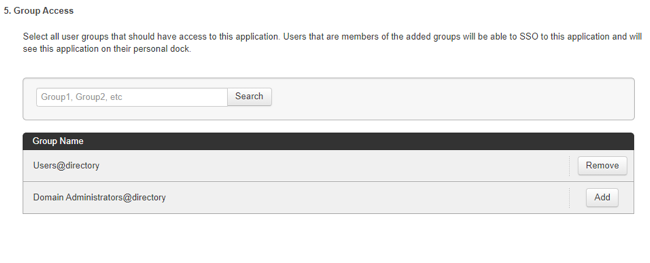
-
Click Continue to Next Step.
-
Click Finish.
Add the PingOne for Enterprise connection to JAMF Pro
-
Sign on to the Jamf Pro console as an administrator.
-
Click the Gear icon (]).
-
Go to System Settings → Single Sign-On.
-
Click the Edit icon.
-
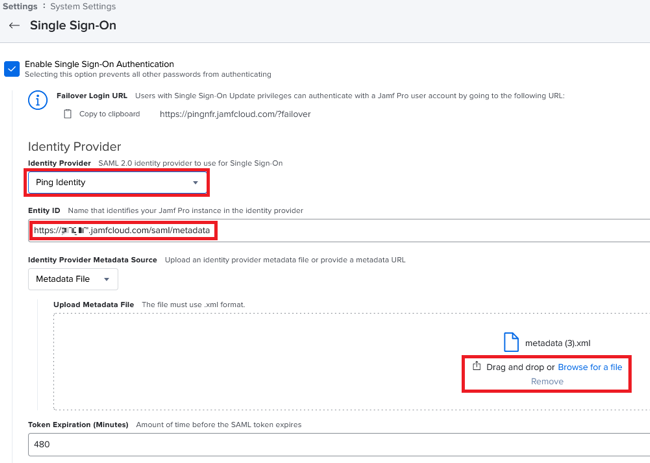
Select the Enable Single Sign-On Authentication check box.
-
In the Identity Provider list, select Ping Identity.
-
Confirm that the Entity ID value matches the value you set previously in PingOne for Enterprise.
-
In the Upload Metadata File section, upload the PingOne for Enterprise metadata file.
-
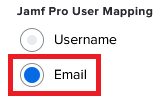
In the Jamf Pro User Mapping section, click Email.
-
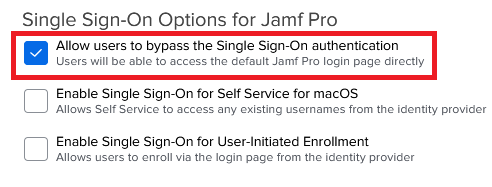
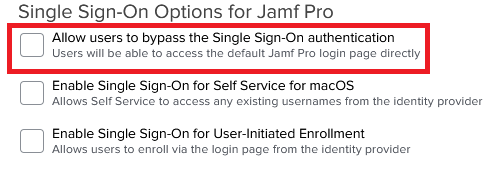
In the Single Sign-On Options for Jamf Pro section, select the Allow users to bypass the Single Sign-On authentication check box.
-
Click Save.
Test the PingOne for Enterprise identity provider (IdP)
-
Go to your Ping desktop as a user with Jamf Pro access.
To find the Ping desktop URL, in the PingOne admin console, go to Setup → Dock → PingOne Dock URL.
-
Complete the PingOne authentication.
You’re redirected to your Jamf Pro application.
Test the PingOne for Enterprise service provider (SP)
-
If you are using PingOne for Enterprise as the standard authentication method for Jamf Pro access, sign on to the Jamf Pro console as an administrator after you’ve completed PingOne for Enterprise IdP testing.
-
Go to Settings → System Settings → Single Sign-On and click Edit.

-
Clear the Allow users to bypass the Single Sign-On authentication check box.
-
Click Save.
-
Go to your Jamf Pro application.

You’re redirected to PingOne for Enterprise.
-
Enter your PingOne for Enterprise username and password.
After successful authentication, you’re redirected back to Jamf Pro.