Supported browsers
The following browsers are supported in PingOne Advanced Identity Cloud:
| Browser | Version |
|---|---|
Google Chrome |
Latest stable version of full-desktop browser |
Firefox |
Latest stable version of full-desktop browser |
Safari |
Latest stable version of full-desktop browser |
Microsoft Edge |
Latest stable version of full-desktop browser |
|
Ping Identity does not provide support for these browsers:
Ping Identity optimizes its platform for modern browsers to ensure the best user experience, security, and performance. If you encounter issues while using the Ping Identity platform, ensure you use a supported, up-to-date browser for the optimal experience. |
|
While Advanced Identity Cloud works with all supported browsers, administrative activity works best using Google Chrome. |
Security and compliance
PingOne Advanced Identity Cloud provides full tenant isolation in a multi-tenant cloud service by using individual trust zones. Each customer’s environment is a dedicated trust zone that shares no code, data, or identities with other customers’ environments. This prevents any accidental or malicious commingling. All data is encrypted, at rest and in transmission, to prevent unauthorized access and data breaches.
Certifications and compliance
SOC 2 Type 2

Ping Identity is SOC 2 Type 2-certified. This confirms that Ping Identity’s information security practices, policies, procedures, and operations meet the SOC 2 standards for security, availability, and confidentiality. Our adherence to these standards is externally validated by an independent third party annually.
Our SOC 2 report is available to customers under an NDA on the Ping Identity Support Portal.
ISO 27001, 27017 and 27018

Ping Identity’s information security management system (ISMS) has been independently assessed and certified to the ISO 27001 standard. Ping Identity has included ISO 27017 and ISO 27018 into its certified ISMS and has also achieved independent certifications validating that the controls and implementation guidance relevant to those standards are in place and operational.
The scope of Ping Identity’s ISMS covers all major offices used in the development of Ping Identity products, all of our product offerings, both standalone on-premises products and our cloud services (PingOne, PingOne Advanced Services, and Advanced Identity Cloud), as well as all supporting infrastructure, systems, and internal processes.
Our ISO 27001 certificate is available in the Shellman Certificate Directory by searching for Ping Identity.
CSA STAR (Level 2)

Ping Identity’s cloud offerings are certified as meeting the criteria of the Cloud Security Alliance Cloud Controls Matrix (Version 4). Our CSA STAR (Level 2) Attestation demonstrates Ping Identity’s commitment to high standards and industry-accepted cloud security controls and transparency of our security posture.
Our attestation and the CSA Consensus Assessments Initiative Questionnaire are available on the CSA STAR (Level 2) Registry Page.
HIPAA and HITECH

The Health Insurance Portability and Accountability Act (HIPAA) is the US national standard for health information security and privacy that governs the use and disclosure of sensitive protected health information (PHI).
Advanced Identity Cloud complies with HIPAA security standards, as well as the breach notification requirements of the Health Information Technology for Economic and Clinical Health (HITECH) Act. Learn more about how Ping Identity supports HIPAA compliance.
Trusted Information Security Assessments Exchange

The Trusted Information Security Assessment Exchange (TISAX) is an assessment and exchange mechanism for the information security of enterprises governed by ENX on behalf of the German VDA. The exchange allows recognition of assessment results among the participants. TISAX can be accessed by active participants through https://enx.com/tisax. TISAX and TISAX results are not intended for general public use.
ForgeRock Inc. and ForgeRock Ltd. (Ping Identity) are active TISAX participants with assessment results available through the ENX portal - Tisax assessment results, under scope ID: SZZMC3 and assessment ID: AZ5YYL-1.
Security white paper
Learn more about our security practices in our security white paper.
Identity Cloud penetration testing and load testing policy
Ping Identity has a strict policy on the penetration testing and load testing of your PingOne Advanced Identity Cloud infrastructure and applications.
The policy exists for the following reasons:
- Preserves platform stability
-
The policy preserves platform stability for all Ping Identity customers.
Unscheduled testing can cause severe problems, as it can initially be indistinguishable from a real problem or a DoS attack. It can set off alarms, cause service shutdowns, add services to denylists, and prevent the support team from taking remedial actions. It can also disproportionally occupy our support team, delaying our response to other Ping Identity customers with pressing support problems.
- Regulates testing
-
The policy regulates how testing is approached so that it is realistic and manageable.
For example, a load testing plan would not be approved if it created and deleted large numbers of identities and entitlements for each test, as this is a hugely expensive operation, but not a realistic pattern of behavior.
- Avoids unnecessary testing
-
The policy helps you avoid unnecessary testing.
Ping Identity already directly tests Advanced Identity Cloud infrastructure and applications on your behalf, using code scans, penetration tests, and automated load tests. This ensures that testing is consistent and that results can be compared over time.
The penetration testing is done by a third party, in line with industry best practice. The results of the penetration testing are shared with you, with the time-consuming analysis and elimination of false positives already done by our engineers.
Policy
Policy rules
-
You are not permitted to directly test Advanced Identity Cloud infrastructure and applications. In particular, this applies to DoS or DDoS attacks. Ping Identity already does this on your behalf.
-
You are permitted to indirectly test Advanced Identity Cloud infrastructure and applications as part of a wider test of your own infrastructure and applications.
-
You are permitted to perform penetration testing and load testing only against your staging and UAT[1] environments.
-
You are permitted to perform penetration testing and load testing only up to a maximum of 2 weeks per test plan.
-
You are permitted to perform load testing only up to the license volume limits listed in the Test plan information section.
-
You are not permitted to use the built-in SMTP server as the email provider. If you have any email-dependent journeys, you must configure your own external email service as the email provider.
-
You are not permitted to perform penetration testing or load testing without Ping Identity’s prior written consent.
-
You are not permitted to authorize a third party to perform penetration testing or load testing without Ping Identity’s prior written consent.
-
To obtain Ping Identity’s prior written consent you must create a test plan and have it reviewed and approved by Ping Identity.
-
You must provide at least 2 weeks' notice of the testing start date.
Policy summary
| Development environment | Staging and UAT[1] environments | Production environment | ||||
|---|---|---|---|---|---|---|
|
|
|
Create a test plan
-
Click Create a case.
-
Follow the steps in the case submission wizard by selecting your account and contract and answering questions about your tenant environments.
-
On the Please answer the following questions to help us understand the issue you’re facing page, enter the following details, and then click Next:
Field Value What product family is experiencing the issue?
Select PingOne Advanced Identity Cloud
What specific product is experiencing the issue?
Select Configuration
What version of the product are you using?
Select NA
-
On the Tell us about the issue page, enter the following details, and then click Next:
Field Value Provide a descriptive title for your issue
Enter one of the following:
-
Submit a load testing request -
Submit a penetration testing request
Describe the issue below
Enter the following details:
-
The hostname of your staging environment
-
Within a maximum permitted duration of 2 weeks, the dates and times that you intend to do the testing.
-
-
Click Submit.
Test plan information
| Information | Description |
|---|---|
Testing strategy |
Describe the strategy you intend to follow when testing your own infrastructure and applications.
Your load testing plan should also avoid unrealistic patterns such as the setup and teardown of large numbers of identities for each load test. |
Origin of testing |
Confirm if the testing will originate from an external source over the internet or from an internal source within your Advanced Identity Cloud tenant environments. If originating from an external source, you must also supply IP addresses. |
Named contact |
Provide a named point of contact in your testing team in case Ping Identity requires the testing to be stopped due of unforeseen impacts. |
Vulnerability discovery |
Confirm that in the unlikely event that a vulnerability is discovered in Advanced Identity Cloud infrastructure or applications:
|
Identity Cloud product lifecycle and releases
PingOne Advanced Identity Cloud releases new features, updates functionality and fixes bugs on a continual cadence. Ping Identity aims to deliver features and functionality that will be the most useful, complete and intuitive for customers. In order to deliver on this goal we have several stages to our release lifecycle.
Early access
Participating in Early Access programs allow customers to provide feedback and collaborate with Ping Identity in designing future capabilities in the product.
Select customers are invited to provide feedback on new features. Customers are encouraged to give feedback and have an active say in product direction; product management and customer success will work with you to gather feedback. Features may be unstable, changed in backward-incompatible ways, and are not guaranteed to be released. We will use all reasonable efforts to communicate breaking changes to customers participating in the program.
Beta
Beta features give customers advanced insights into up-and-coming product capabilities with extra time to prepare to adopt the feature and provide design feedback to the product team. Generally speaking, functionality is stable and meets security and quality expectations but please note that a beta feature is not officially supported for production use.
Upcoming features
Customers receive notifications of new and upcoming features at least a week in advance of a release. The notifications provide customers with high-level information on changes or new functionality.
Limited availability
Features are available for production use and are fully functional and supported; however, they are available only to a select set of customers.
General availability
Features are available for production use and are fully functional and supported. They are available to all customers.
Migration dependent features
Features are not backward compatible and require a tenant migration before they can be used. Learn more in Migration dependent features.
Bug fixes and low impact changes
On an ongoing basis, Ping Identity makes bug fixes and low impact changes as necessary to Advanced Identity Cloud. These types of fixes are deployed as necessary. You can monitor these in the Regular channel changelog and Rapid channel changelog. You can also subscribe to the RSS feeds mentioned at the start of the two changelog pages.
Deprecation and end of life
To maintain both security and quality in Advanced Identity Cloud, we periodically have to modify or remove functionality.
Learn more in Deprecation Notices.
Deprecated features
A feature or behavior (or API endpoint) flagged for deprecation means it is no longer actively enhanced and is minimally maintained. Tenants using the feature at the time of deprecation will continue to have access to the feature until it reaches end of life, at which point customers will no longer have access to the feature. We know deprecation disruptions are inconvenient, and as such, we attempt to limit the frequency of deprecations and to pair them with alternative options and migration recommendations where available.
Deprecation notification
Deprecation information is posted to the Advanced Identity Cloud documentation. Deprecation notices typically include a date the feature or behavior reaches end of life. Our policy is to flag a feature for deprecation with at least 12 months advance notice prior to end of life whenever possible to allow a 12 month migration window.
Periodically, and in case of emergency (critical vulnerabilities or changes required by applicable law or third-party certification standards), we may accelerate this time frame. In such cases, we will provide as much prior notice as is reasonable under the circumstances.
Migration dependent features
Certain PingOne Advanced Identity Cloud features require changes to your tenant environments before they can be introduced. In such cases, Ping Identity defines a migration strategy for the feature. Some examples of feature migration strategies are:
-
Updating the format of your static configuration
-
Updating the way your automated applications are configured
-
Restricting the new feature only to tenants built after the feature is introduced
Current migration dependent features
| Feature | Effective date | Summary |
|---|---|---|
Two-factor authentication (2FA) profile attributes |
2025-01-09 |
Ping Identity has introduced five multivalue (array) strings to existing Alpha and Bravo realm user identities in Advanced Identity Cloud:
The five multivalue (array) strings are not enabled by default. To enable, refer to 2FA profile attributes. |
Additional indexed strings |
2024-11-12 |
Ping Identity has introduced 15 additional indexed strings which can be used as general purpose extension attributes. The 15 indexed strings are not enabled by default. To enable them, learn more in Enable additional indexed strings. |
Outbound static IP addresses |
2023-04-18 |
${forgerock.name} has introduced outbound static IP addresses to each of your tenant environments. Outbound static IP addresses are enabled by default in tenants created on or after April 18, 2023. To enable in tenants created before that date, you can raise a support ticket. Learn more in Outbound static IP addresses. |
Tenant administrator mandatory 2-step verification |
2023-02-03 |
${forgerock.name} has deprecated the option to let Advanced Identity Cloud tenant administrators skip 2-step verification. Customers can continue to use the skip option in their tenants, but this functionality will be removed from Advanced Identity Cloud on April 2, 2024. Learn more in Tenant administrator mandatory 2-step verification FAQ. |
Application management |
2023-01-12 |
${forgerock.name} has introduced an improved application management UI to Advanced Identity Cloud. The UI is only available in tenants created on or after January 12, 2023. Learn more in Application management migration FAQ. |
Event hooks |
2023-01-12 |
${forgerock.name} has introduced event hooks to Advanced Identity Cloud. This feature is only available in tenants created on or after January 12, 2023. Learn more in Event hooks migration FAQ. |
Group identity |
2022-11-29 |
${forgerock.name} has introduced a group identity to simplify the management of permissions and authorizations for collections of users. The group identity is enabled by default in tenants created on or after November 29, 2022. Tenants created before that date can follow an upgrade path to enable it. Learn more in Group identity migration FAQ. |
Tenant administrator mandatory 2-step verification FAQ
How is 2-step verification changing?
Ping Identity is making 2-step verification mandatory for all PingOne Advanced Identity Cloud tenant administrators.
The option to skip registration for 2-step verification is deprecated and will be removed a year after the deprecation notification date (Friday, February 3, 2023), following the Advanced Identity Cloud deprecation and end of life policy.
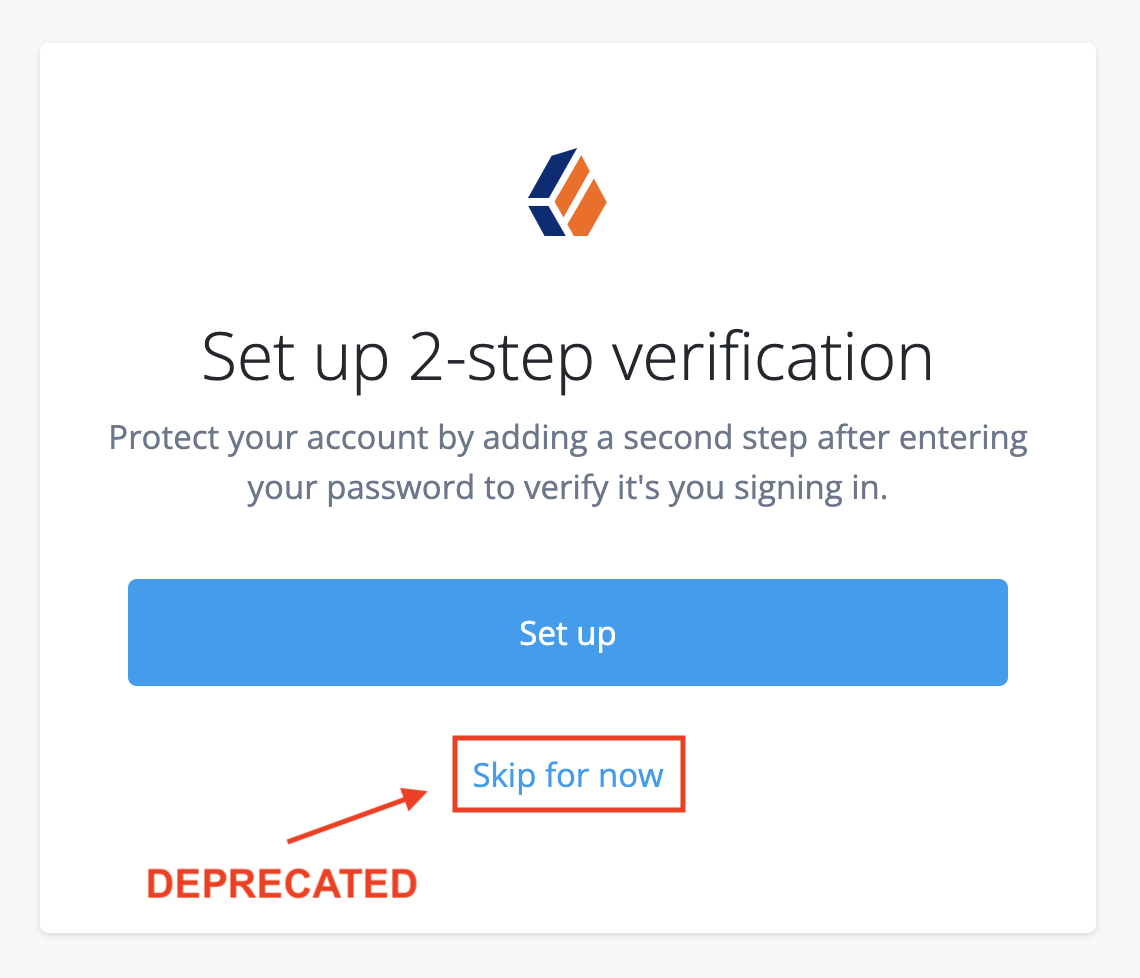
After the option to skip registration is removed, any tenant administrator that has not already set up 2-step verification will be forced to do so the next time they sign in. Advanced Identity Cloud guides the tenant administrator through the device registration process, with no assistance needed from Ping Identity support.
Will the change to mandatory 2-step verification affect me?
Yes, this change affects all customers. You have until the deprecation end-of-life date (Tuesday, April 2, 2024) to update your tenants to make 2-step verification mandatory for all tenant administrators.
How do I prepare my tenants to support 2-step verification?
If you have any automation that relies on the skip option to authenticate to Advanced Identity Cloud APIs, it must be updated to use a service account to get an access token.
| After 2-step verification is enforced, any automation that depends on the skip option will fail authentication. |
How do I enable mandatory 2-step verification for my tenants?
-
Make sure you have updated any automation that authenticates to Advanced Identity Cloud APIs to use a service account. Learn more in How do I prepare my tenants to support 2-step verification?.
-
Open a support case with Ping Identity support:
-
Click Create a case.
-
Follow the steps in the case submission wizard by selecting your account and contract and answering questions about your tenant environments.
-
On the Please answer the following questions to help us understand the issue you’re facing page, enter the following details, and then click Next:
Field Value What product family is experiencing the issue?
Select PingOne Advanced Identity Cloud
What specific product is experiencing the issue?
Select Configuration
What version of the product are you using?
Select NA
-
On the Tell us about the issue page, enter the following details, and then click Next:
Field Value Provide a descriptive title for your issue
Enter
Enforce 2-step verification for tenant administratorsDescribe the issue below
Enter a comma-separated list of FQDNs for your sandbox[2], development, UAT[1], staging, and production tenant environments.
-
Click Submit.
-
Ping Identity support turns on the enforcement of 2-step verification for your tenant administrators and then asks you to verify that everything is working as expected.
Application management migration FAQ
Application management allows you to manage the security and access of common and custom relying-party applications and SAML 2.0 applications directly from PingOne Advanced Identity Cloud. This functionality is most commonly used to manage data and system access for employees within an organization, commonly referred to as workforce identity and access management.
How is application management changing?
Ping Identity has improved application management by introducing a single UI interface to the Advanced Identity Cloud admin console that manages all aspects of an application relevant to Advanced Identity Cloud. This replaces the previous arrangement, which required a combination of actions across the Advanced Identity Cloud admin console, AM admin console, and IDM admin console. In addition, Ping Identity has introduced an application catalog to speed up application configuration for common use cases.
How is the improved application management UI being introduced?
The improved application management UI is only available in tenants created on or after January 12, 2023.
What documentation should I use?
-
For tenants created on or after January 12, 2023, learn more in Application management (current).
-
For tenants created before January 12, 2023, learn more in Application management (legacy).
Event hooks migration FAQ
What has changed?
Ping Identity has introduced event hooks to PingOne Advanced Identity Cloud to let you trigger scripts during various stages of an identity object lifecycle.
How are event hooks being introduced?
Event hooks are only available in tenants created on or after January 12, 2023.
Does this affect any other features?
Yes. If you have not upgraded your tenant to enable groups, event hooks are not available for group identities. Learn more in Group identity migration FAQ.
Group identity migration FAQ
What has changed?
Ping Identity has introduced a group identity to PingOne Advanced Identity Cloud to simplify the management of permissions and authorizations for collections of users.
How is the group identity being introduced?
Tenants created on or after November 29, 2022 have the group identity enabled by default. Tenants created before that date can follow an upgrade path to enable it; learn more in Enable groups.
Does this affect any other features?
Yes. If you have not upgraded your tenant, event hooks are not available for group identities.
What documentation should I use?
Learn more in Group management.
Add-on capabilities
Add-on capabilities are features or integrated products that enhance PingOne Advanced Identity Cloud, but are not part of the standard offering. They can each be added to your tenant environments for an additional subscription; contact your Ping Identity representative to arrange this.
The following wording identifies add-on capabilities in the Advanced Identity Cloud documentation:
|
Advanced Identity Cloud add-on capability
Contact your Ping Identity representative if you want to add this feature to your Advanced Identity Cloud subscription. |
Current add-on capabilities
| Capability | Summary |
|---|---|
Advanced Reporting |
Lets you create custom reports on activity in your Advanced Identity Cloud tenant environment. You can query a number of metrics to create useful reports for your company. Learn more in Advanced Reporting. |
PingOne Identity Governance |
Lets you centrally administer and manage user access to applications and data across your organization to support regulatory compliance. Learn more in About Identity Governance. |
Proxy Connect |
Lets you configure a proxy service, such as a web application firewall (WAF) or a content delivery network (CDN), in front of your Advanced Identity Cloud tenant environments. Learn more in Configure a proxy service with Proxy Connect. |
Sandbox tenant environment |
Standalone environment that lets you experiment with new configuration or test new use cases without affecting other environments. Learn more in Sandbox tenant environment. |
Secure Connect |
Lets you connect to PingOne Advanced Identity Cloud directly from your private network without using the public internet. Learn more in Create private network connections with Secure Connect. |
UAT tenant environment |
Additional environment that you can choose to add into your standard promotion group of development, staging, and production tenant environments. It has the same capabilities as your staging environment, allowing you to test your development changes in a production-like environment. Learn more in UAT tenant environment. |
High availability and disaster recovery
High availability
Ping Identity provides high availability (HA) to PingOne Advanced Identity Cloud by:
-
Deploying Google Kubernetes Engine (GKE) clusters across multiple availability zones (AZs) within a region to create regional redundancy. In the event of physical hardware failure within a particular zone, workloads are automatically redistributed to other zones.
For a full list of supported regions, learn more in Data residency. -
We monitor your environments and appropriately scale each one to meet expected demands.
Disaster recovery
Ping Identity provides disaster recovery (DR) to PingOne Advanced Identity Cloud by:
-
(All data regions) Taking hourly backups of data stored within each region. In the event of data corruption, you can restore the datastore, including user identities and the identity schema, to any point within the 30-day retention period. The available restore points are determined by the hourly backup schedule, which defines the recovery point objective (RPO). Learn more in Comparison of environment characteristics.
-
Backing up data to a different region. In case of a major outage in a particular region, Ping Identity can restore service in a backup region. For details about the availability of backup in specific data regions, learn more in Regions.
Deprecation notices
For information about the PingOne Advanced Identity Cloud product lifecycle and deprecation, learn more in Deprecation and end of life.
Autonomous Access
- Notification date
-
November 18, 2024
Ping Identity has deprecated Autonomous Access. The product will reach end of life on October 31, 2025. During the deprecation period, Ping Identity will not provide new patches, updates, or new features for Autonomous Access.
To support our Autonomous Access customers, we’re providing migration assistance to PingOne Protect. This advanced threat detection solution leverages machine learning to analyze authentication signals and detect abnormal online behavior. PingOne Protect is a well-established product trusted by hundreds of customers worldwide.
The Autonomous Access documentation has moved to the documentation archive at https://docs.pingidentity.com/archive/.
- End-of-life date
-
October 31, 2025
Duo authentication node
- Notification date
-
March 5, 2024
${forgerock.name} has deprecated the Duo authentication node because Duo has deprecated Traditional Duo Prompt that is used by the Duo node.
${forgerock.name} created Duo Universal Prompt node in anticipation of this depreciation. You should use Duo Universal Prompt node instead of Duo node (Deprecated).
- End-of-life date
-
September 30, 2024
Introspect endpoint GET requests and URL query string parameters
- Notification date
-
July 19, 2023
${forgerock.name} has deprecated the following behaviors of the OAuth 2.0
introspectendpoint in Advanced Identity Cloud:-
Accept GET requests
-
Accept data in POST requests from URL query string parameters
You can continue to use these behaviors, but they will be removed on July 19, 2024. Instead, when using the OAuth 2.0
introspectendpoint, you should use POST requests and pass data in the POST request body. -
- End-of-life date
-
July 19, 2024
Health check endpoints
- Notification date
-
June 13, 2023
${forgerock.name} has deprecated the following Advanced Identity Cloud health check endpoints:
-
/am/isAlive.jsp -
/am/json/health/live -
/am/json/health/ready -
/openidm/info/ping
You can continue to use the endpoints, but they will be removed on June 13, 2024. You should update any external monitoring to use the Advanced Identity Cloud
/monitoring/healthendpoint instead. Learn more in Monitor using health check endpoint. -
- End-of-life date
-
June 13, 2024
Skip option for 2-step verification registration for Advanced Identity Cloud tenant administrators
- Notification date
-
February 3, 2023
${forgerock.name} has deprecated the option to let Advanced Identity Cloud tenant administrators skip 2-step verification. You can continue to use the skip option in your tenants, but this functionality will be removed from Advanced Identity Cloud on April 2, 2024. Learn more in Tenant administrator mandatory 2-step verification FAQ.
- End-of-life date
-
April 2, 2024
ForgeRock Identity Cloud Email Server Service
- Notification date
-
April 12, 2021
Built-in Email Server Service
${forgerock.name} no longer supports the default email provider settings for use in production. The default email provider settings will only be available for testing purposes. Current customers can continue to use the default email provider settings for production purposes, but this functionality will reach end of life on April 12, 2022. Customers should move to using their own email provider.
- End-of-life date
-
April 12, 2022
Groovy OIDC Custom Claims Script
- Notification date
-
April 20, 2021
${forgerock.name} will continue to support the Groovy version of the OIDC custom claims script until it is end of lifed on April 20th 2022. Current customers can continue to use the Groovy version of the OIDC custom claims script for production purposes, but this functionality will reach end of life on April 20, 2022.
- End-of-life date
-
April 20, 2022
Marketplace
The Marketplace lets you quickly and easily extend the capabilities of the PingOne Advanced Identity Cloud by integrating third party services into your applications or user journeys. Advanced Identity Cloud provides a subset of Marketplace integrations out of the box in your environment.
Your Advanced Identity Cloud tenant provides the following Marketplace nodes. You can find them under the Marketplace header in the Advanced Identity Cloud admin console’s drag-and-drop user journey editor.
| Integration | Use case |
|---|---|
Integrate with BioCatch scoring for identity proofing, continuous authentication, and fraud protection. The BioCatch platform develops behavioral biometric profiles of online users to recognize a wide range of human and non-human cybersecurity threats including malware, remote access trojans (RATs), and robotic activity (bots). |
|
Use Duo’s solution for adaptive authentication, bring your own device (BYOD) security, cloud security, endpoint security, mobile security, and two-factor authentication. |
|
Integrate with fingerprint.com to reduce fraud and improve customer experience. |
|
Enable a secure communication channel for Advanced Identity Cloud authentication journeys to communicate directly with the PingGateway. |
|
The HTTP Client node lets you make HTTP(S) requests to APIs and services external to Advanced Identity Cloud from within a journey. |
|
Integrate with the Daon IdentityX platform for MFA with mobile authentication or out-of-band authentication using a separate, secure channel. |
|
The iProov Authentication node integrates Advanced Identity Cloud authentication journeys with the Genuine Presence Assurance and Liveness Assurance] products from iProov. |
|
Integrate with Jumio identity verification to let you capture and submit your government-issued ID documents easily and securely. |
|
Interate with LexisNexis One Time Password (OTP) to use an out-of-band identity proofing method that provides stronger authentication for high-risk, high-value transactions. |
|
Integrates with Microsoft Intune to let you control features and settings on Android, Android Enterprise, iOS/iPadOS, macOS, and Windows 10/11 devices in your organization. |
|
Integrate with OneSpan Intelligent Adaptive Authentication (IAA) to help reduce fraud, improve customer experience, and meet compliance requirements. |
|
Integrate an Onfido check for identity verification, matching a user with their official identification documents. |
|
The PingOne node establishes trust between PingOne and Advanced Identity Cloud by leveraging a federated connection. The PingOne DaVinci API node executes an API call to PingOne DaVinci to launch a specific DaVinci flow. |
|
The PingOne Authorize node sends a decision request to a specified decision endpoint in your PingOne Authorize environment. |
|
The PingOne Credentials nodes use the PingOne Credentials service to implement digital wallet pairing, credential management, and credential verification. |
|
PingOne Protect is a centralized identity threat protection service, securing your digital assets against online fraud attempts, such as account takeover and fraudulent new account registration. |
|
The PingOne Verify service lets you configure and use PingOne Verify nodes to provide four types of secure user verification: |
|
The RSA SecurID node lets you use the RSA Cloud Authentication Service (RSA ID Plus) or RSA Authentication Manager from within an authentication journey on your Advanced Identity Cloud environment. |
|
Integrate with Secret Double Octopus (SDO) to provide high-assurance, passwordless authentication system. |
|
Integrate with SpyCloud service with Advanced Identity Cloud to assess if a user’s password is compromised. |
|
Integrate Lexis-Nexis ThreatMetrix decision tools and enable device intelligence and risk assessment in Advanced Identity Cloud. |
|
Leverage Twilio for second factor authentication during new account or sign on scenarios. |
| Check this list periodically as we continue to expand our integrations. |
For details on developing and troubleshooting journeys, learn more in: