Microsoft Graph API Java connector
|
Connectors continue to be released outside the IDM release. For the latest documentation, refer to the OpenICF documentation. |
The Microsoft (MS) Graph API Java connector uses the Microsoft Graph SDK for Java and the Authentication Providers for the Microsoft Graph Java SDK. Unlike the PowerShell connector for Azure, the MS Graph API connector is a Java connector, and does not need .NET RCS to run. As a Java connector, the MS Graph API connector functions like any standard IDM connector.
The MS Graph API connector can read, search, and fetch data from Microsoft Azure, when Azure is the authoritative data source, and can provision to Azure, when IDM is the authoritative data source.
The MS Graph API connector is bundled with IDM, and available from the ForgeRock Download Center. The connector bundles all its dependencies.
Before you start
Before you can use the connector, you must register an application with Azure. You need a Microsoft Azure subscription to complete this procedure:
-
Log in to the MS Azure portal as an administrative user.
-
Under Azure services , select App registrations.
-
On the Register an application page, enter a name for the application; for example, FR-Connector.
-
Select the supported account types, and enter a Redirect URI.
The redirect URI is the IDM URI that Azure should redirect to after successful authentication; for example,
https://idm.example.com:8443/. -
On the new registration page for your application, make a note of the Application (client) ID and the Directory (tenant) ID. You will need these to configure the connector:
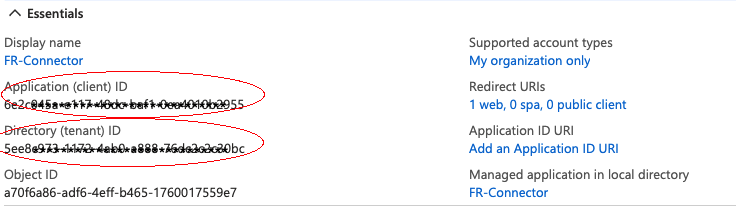
-
Generate a client secret:
-
Select Certificates & secrets > New client secret .
-
Enter a description, select an expiration date, and click Add.
-
Copy the client secret Value:
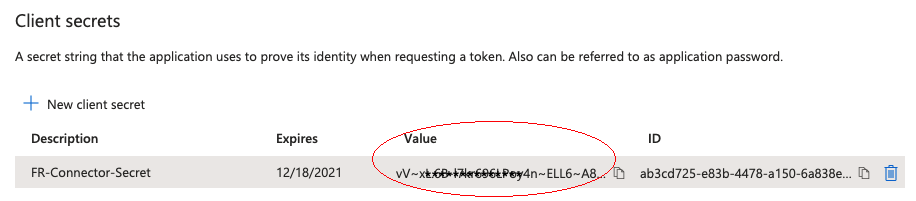
You will not be able to retrieve the client secret in cleartext after you exit this screen. -
-
Set the API permissions:
-
Select API permissions, click Microsoft Graph, and then click Application permissions.
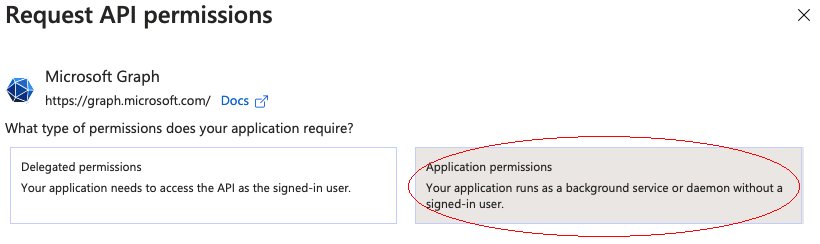
-
From the User item, select the following permissions:
-
User.Export.All -
User.ManageIdentities.All -
User.Read.All -
User.ReadWrite.All
-
-
From the Group item, select the following permissions:
-
Group.Create -
Group.Read.All -
Group.ReadWrite.All
-
-
From the Directory item, select the following permissions:
-
Directory.Read.All -
Directory.ReadWrite.All
-
-
Click Add permissions .
-
-
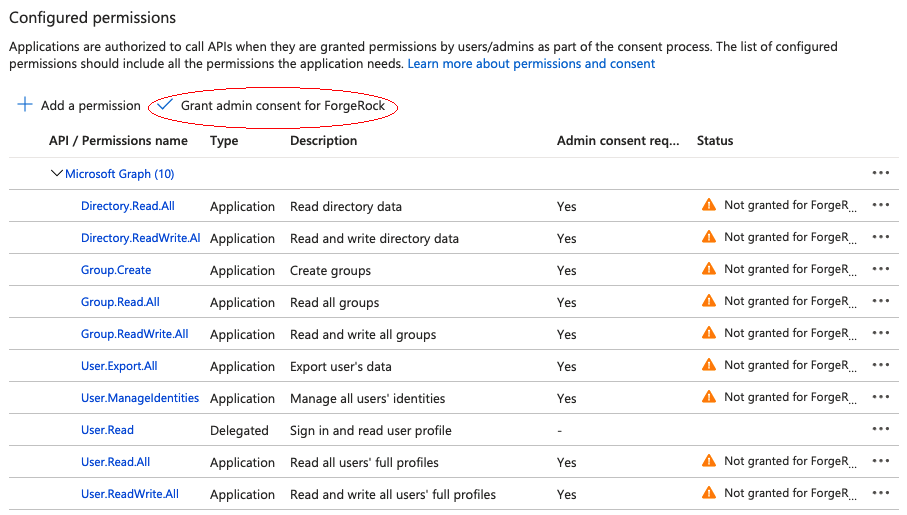
Grant admin consent for the API permissions:
On the Configured permissions page, Grant admin consent for org-name, then click Yes.
Configure the MS Graph API connector
IDM bundles version 1.5.20.15 of the MS Graph API connector in the openidm/connectors directory. Alternatively, download the connector .jar file from the ForgeRock Download Center
Create a connector configuration using the admin UI:
-
From the navigation bar, click Configure > Connectors.
-
On the Connectors page, click New Connector.
-
On the New Connector page, type a Connector Name.
-
From the Connector Type drop-down list, select MSGraphAPI Connector - 1.5.20.15.
-
Complete the Base Connector Details.
-
Click Save.
Alternatively, copy the sample connector configuration file from /path/to/openidm/samples/example-configurations/provisioners/provisioner.openicf-azuread.json to your project’s conf/ directory.
Set at least the Azure tenant, clientId and clientSecret in the configurationProperties. For example:
"configurationProperties" : {
"tenant" : "your tenant ID",
"clientId" : "your client ID",
"clientSecret" : "your client secret"
}Test the MS Graph API connector
Start IDM, if it is not running. Then use these examples to test that the connector is configured correctly and operating as expected:
Check the Connector Configuration
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request POST \
"http://localhost:8080/openidm/system?_action=test"
{
"name": "azuread",
"enabled": true,
"config": "config/provisioner.openicf/azuread",
"connectorRef": {
"bundleVersion": "[1.5.19.0,1.6.0.0]",
"bundleName": "org.forgerock.openicf.connectors.msgraphapi-connector",
"connectorName": "org.forgerock.openicf.connectors.msgraphapi.MSGraphAPIConnector"
},
"displayName": "MSGraphAPI Connector",
"objectTypes": [
"subscribedSku",
"team",
"user",
"__ALL__",
"group"
],
"ok": true
}
A status of "ok": true indicates that the connector is configured correctly.
List User Entries
This command retrieves a list of users in your Azure tenant. You can also use any system-enabled filter, such as those described in Construct Queries:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request GET \
"http://localhost:8080/openidm/system/azuread/user?_queryId=query-all-ids"
{
"result": [
{
"_id": "c48be8cc-5846-4059-95e8-a7acbf6aec31"
},
{
"_id": "c7fe57e2-3159-45e1-b67a-435232fd88d9"
},
{
"_id": "9e714b5c-345a-430c-93f5-d8c6f9a2f225"
},
...
],
...
}
Return a User Entry
This command retrieves a specific user entry from your Azure tenant:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request GET \
"http://localhost:8080/openidm/system/azuread/user/c48be8cc-5846-4059-95e8-a7acbf6aec31"
{
"_id": "c48be8cc-5846-4059-95e8-a7acbf6aec31",
"surname": "Jensen",
"displayName": "Babs Jensen",
"memberOf": [
"036f288c-6f71-41ae-9d09-6a68c8ba315b"
],
"mail": "babs.jensen@example.onmicrosoft.com",
"onPremisesExtensionAttributes": {
...
},
"usageLocation": "FR",
"userType": "Member",
"identities": [
{
"signInType": "userPrincipalName",
"issuerAssignedId": "00991235@example.onmicrosoft.com",
"issuer": "example.onmicrosoft.com"
}
],
"businessPhones": [],
"createdDateTime": "2020-11-20T11:09:15Z",
"accountEnabled": true,
"userPrincipalName": "00991235@example.onmicrosoft.com",
"proxyAddresses": [
"smtp:00991235@example.onmicrosoft.com",
"SMTP:babs.jensen@example.onmicrosoft.com"
],
"imAddresses": [],
"passwordPolicies": "None",
"mailNickname": "00991235",
"givenName": "Babs",
"__NAME__": "00991235@example.onmicrosoft.com"
}
Create Users or Groups
This command creates a new user in your Azure tenant:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request POST \
--header "content-type: application/json" \
--data '{
"surname": "Carter",
"displayName": "Steve Carter",
"givenName": "Steve",
"userType": "Member",
"accountEnabled": true,
"mailNickname": "00654321",
"userPrincipalName": "00654321@forgedemo.onmicrosoft.com",
"__PASSWORD__": "MyPassw0rd"
}' \
"http://localhost:8080/openidm/system/azuread/user?_action=create"
{
"_id": "9fa6c765-0872-45f6-8714-1dcd1ed94859",
"surname": "Carter",
"displayName": "Steve Carter",
"memberOf": [],
"onPremisesExtensionAttributes": {
"extensionAttribute14": null,
...
},
"userType": "Member",
"identities": [
{
"signInType": "userPrincipalName",
"issuerAssignedId": "00654321@example.onmicrosoft.com",
"issuer": "example.onmicrosoft.com"
}
],
"businessPhones": [],
"createdDateTime": "2020-12-18T13:23:58Z",
"accountEnabled": true,
"userPrincipalName": "00654321@example.onmicrosoft.com",
"proxyAddresses": [],
"imAddresses": [],
"mailNickname": "00654321",
"givenName": "Steve",
"__NAME__": "00654321@example.onmicrosoft.com"
}
Update Entries
This command changes the password for the user created previously:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request PATCH \
--header "content-type: application/json" \
--data '[ {
"operation": "replace",
"field": "__PASSWORD__",
"value": "MyNewPassw0rd"
} ]' \
"http://localhost:8080/openidm/system/azuread/user/9fa6c765-0872-45f6-8714-1dcd1ed94859"
{
"_id": "9fa6c765-0872-45f6-8714-1dcd1ed94859",
"surname": "Carter",
"displayName": "Steve Carter",
"memberOf": [],
"onPremisesExtensionAttributes": {
"extensionAttribute14": null,
...
},
"userType": "Member",
"identities": [
{
"signInType": "userPrincipalName",
"issuerAssignedId": "00654321@forgedemo.onmicrosoft.com",
"issuer": "forgedemo.onmicrosoft.com"
}
],
"businessPhones": [],
"createdDateTime": "2020-12-18T13:23:58Z",
"accountEnabled": true,
"userPrincipalName": "00654321@forgedemo.onmicrosoft.com",
"proxyAddresses": [],
"imAddresses": [],
"mailNickname": "00654321",
"givenName": "Steve",
"__NAME__": "00654321@forgedemo.onmicrosoft.com"
}
Delete Users and Groups
This command deletes the user created previously:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request DELETE \
"http://localhost:8080/openidm/system/azuread/user/9fa6c765-0872-45f6-8714-1dcd1ed94859"
{
"_id": "9fa6c765-0872-45f6-8714-1dcd1ed94859",
"surname": "Carter",
"displayName": "Steve Carter",
"memberOf": [],
"onPremisesExtensionAttributes": {
"extensionAttribute14": null,
...
},
"userType": "Member",
"identities": [
{
"signInType": "userPrincipalName",
"issuerAssignedId": "00654321@forgedemo.onmicrosoft.com",
"issuer": "forgedemo.onmicrosoft.com"
}
],
"businessPhones": [],
"createdDateTime": "2020-12-18T13:23:58Z",
"accountEnabled": true,
"userPrincipalName": "00654321@forgedemo.onmicrosoft.com",
"proxyAddresses": [],
"imAddresses": [],
"mailNickname": "00654321",
"givenName": "Steve",
"__NAME__": "00654321@forgedemo.onmicrosoft.com"
}
Manage user licenses
The MS Graph API connector lets you list the available licenses in your Azure data source, and manage those licenses for specific users:
List Available Licenses in Azure
This command lists the values of the read-only subscribedSku object. For more information about this object class, see the corresponding Microsoft documentation:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request GET \
"http://localhost:8080/openidm/system/azuread/subscribedSku?_queryFilter=true"
{
"result": [
{
"_id": "5ee8xxxx-xxxx-xxxx-xxxx-76dc2c2c30bc_f245ecc8-xxxx-xxxx-xxxx-xxxx114de5f3",
"prepaidUnits": {
"warning": 0,
"enabled": 1,
"suspended": 0
},
"skuId": "f245ecc8-xxxx-xxxx-xxxx-xxxx114de5f3",
"skuPartNumber": "O365_BUSINESS_PREMIUM",
"capabilityStatus": "Enabled",
"appliesTo": "User",
"consumedUnits": 1,
"__NAME__": "O365_BUSINESS_PREMIUM",
"servicePlans": [
{
"servicePlanName": "RMS_S_BASIC",
"provisioningStatus": "PendingProvisioning",
"appliesTo": "Company",
"servicePlanId": "31cxxxxxxxxxxxxxxxxxxxxxxxxxxx122"
},
{
"servicePlanName": "POWER_VIRTUAL_AGENTS_O365_P2",
"provisioningStatus": "PendingProvisioning",
"appliesTo": "User",
"servicePlanId": "041xxxxx-xxxx-xxxx-xxxx-xxxxxxxxxaee"
},
{
"servicePlanName": "CDS_O365_P2",
"provisioningStatus": "PendingProvisioning",
"appliesTo": "User",
"servicePlanId": "95bxxxxx-xxxx-xxxx-xxxx-xxxxxxxxx95a"
},
...
]
}
],
...
}
List a User’s Licenses
Each user object can include a read-only licenses property that contains an array of objects (maps).
This command lists a specific user’s licenses:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--request GET \
"http://localhost:8080/openidm/system/azuread/user/c48be8cc-5846-4059-95e8-a7acbf6aec31?_fields=licenses"
{
"_id": "c48be8cc-5846-4059-95e8-a7acbf6aec31",
"licenses": [
{
"skuPartNumber": "O365_BUSINESS_PREMIUM",
"servicePlans": [
{
"servicePlanName": "RMS_S_BASIC",
"provisioningStatus": "PendingProvisioning",
"appliesTo": "Company",
"servicePlanId": "31cxxxxx-xxxx-xxxx-xxxx-xxxxxxxxx122"
},
{
"servicePlanName": "POWER_VIRTUAL_AGENTS_O365_P2",
"provisioningStatus": "PendingProvisioning",
"appliesTo": "Company",
"servicePlanId": "041xxxxx-xxxx-xxxx-xxxx-xxxxxxxxxaee"
},
{
"servicePlanName": "CDS_O365_P2",
"provisioningStatus": "PendingProvisioning",
"appliesTo": "Company",
"servicePlanId": "95bxxxxx-xxxx-xxxx-xxxx-xxxxxxxxx95a"
},
...
],
"id": "c8noxxxxsEqoxxxxLCwwxxxxRfKvxxxxth8nxxxx5fM",
"skuId": "f24xxxxx-xxxx-xxxx-xxxx-xxxxxxxxx5f3"
}
]
}
Add and Remove a User’s Licenses
You cannot manipulate a user’s licenses property directly, because it is read-only. To add or remove licenses for a user, set the addLicenses or removeLicenses properties when you create or update the user.
|
The connector does not currently support PATCH |
This command updates an existing user entry to add a license with the `skuId`f24xxxxx-xxxx-xxxx-xxxx-xxxxxxxxx5f3:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--header "Content-Type: application/json" \
--header "If-None-Match: *" \
--request PUT \
--data '{
"addLicenses": [
{
"skuId": "f24xxxxx-xxxx-xxxx-xxxx-xxxxxxxxx5f3"
}
]
}' \
"http://localhost:8080/openidm/system/azuread/user/c48be8cc-5846-4059-95e8-a7acbf6aec31"
This command updates the user entry to remove the license with `skuId`f24xxxxx-xxxx-xxxx-xxxx-xxxxxxxxx5f3:
curl \
--header "X-OpenIDM-Username: openidm-admin" \
--header "X-OpenIDM-Password: openidm-admin" \
--header "Accept-API-Version: resource=1.0" \
--header "Content-Type: application/json" \
--header "If-Match: *" \
--request PUT \
--data '{
"removeLicenses": "f24xxxxx-xxxx-xxxx-xxxx-xxxxxxxxx5f3"
}' \
"http://localhost:8080/openidm/system/azuread/user/c48be8cc-5846-4059-95e8-a7acbf6aec31"
Synchronize accounts between IDM and Azure
To use the MS Graph API connector to synchronize accounts between IDM and Azure, set up a mapping between the two data stores.
You can use the sample configuration file at /path/to/openidm/samples/sync-with-azuread/conf/sync.json as a starting point.
OpenICF Interfaces Implemented by the MSGraphAPI Connector
The MSGraphAPI Connector implements the following OpenICF interfaces. For additional details, see OpenICF interfaces:
- Authenticate
-
Provides simple authentication with two parameters, presumed to be a user name and password.
- Create
-
Creates an object and its
uid. - Delete
-
Deletes an object, referenced by its
uid. - Schema
-
Describes the object types, operations, and options that the connector supports.
- Script on Connector
-
Enables an application to run a script in the context of the connector.
Any script that runs on the connector has the following characteristics:
-
The script runs in the same execution environment as the connector and has access to all the classes to which the connector has access.
-
The script has access to a
connectorvariable that is equivalent to an initialized instance of the connector. At a minimum, the script can access the connector configuration. -
The script has access to any script arguments passed in by the application.
-
- Search
-
Searches the target resource for all objects that match the specified object class and filter.
- Sync
-
Polls the target resource for synchronization events, that is, native changes to objects on the target resource.
- Test
-
Tests the connector configuration.
Testing a configuration checks all elements of the environment that are referred to by the configuration are available. For example, the connector might make a physical connection to a host that is specified in the configuration to verify that it exists and that the credentials that are specified in the configuration are valid.
This operation might need to connect to a resource, and, as such, might take some time. Do not invoke this operation too often, such as before every provisioning operation. The test operation is not intended to check that the connector is alive (that is, that its physical connection to the resource has not timed out).
You can invoke the test operation before a connector configuration has been validated.
- Update
-
Updates (modifies or replaces) objects on a target resource.
MSGraphAPI Connector Configuration
The MSGraphAPI Connector has the following configurable properties:
Basic Configuration Properties
| Property | Type | Default | Encrypted(1) | Required(2) |
|---|---|---|---|---|
|
|
|
|
Yes |
The Azure AD tenant name or id |
||||
|
|
|
|
Yes |
The clientID used by the connector during the OAuth flow |
||||
|
|
|
Yes |
No |
The client secret used by the connector during the OAuth flow |
||||
|
|
|
|
No |
The Http proxy host |
||||
|
|
|
|
No |
The Http proxy port |
||||
|
|
|
|
No |
The Http proxy user name |
||||
|
|
|
Yes |
No |
The Http proxy user password |
||||
|
|
|
|
No |
If set to true, the Azure object will be deleted permanently on delete operation. |
||||
|
|
|
|
No |
Define throttling for read operations either per seconds ("30/sec") or per minute ("100/min"). |
||||
|
|
|
|
No |
Define throttling for write operations (create/update/delete) either per second ("30/sec") or per minute ("100/min"). |
||||
(1) Whether the property value is considered confidential, and is therefore encrypted in IDM.
(2) A list of operations in this column indicates that the property is required for those operations.