Secure the Authenticator app using policies
You can distribute the ForgeRock Authenticator app to your users so that they can participate in multi-factor authentication journeys. To help ensure the security of the app—and therefore your system—you can enable Authenticator app policies.
The Combined MFA Registration node can apply authenticator app policies during registration of client devices.
These policies can perform checks on the client device. For example, that the device has not been rooted or jailbroken, or verify the use of biometrics on the device.
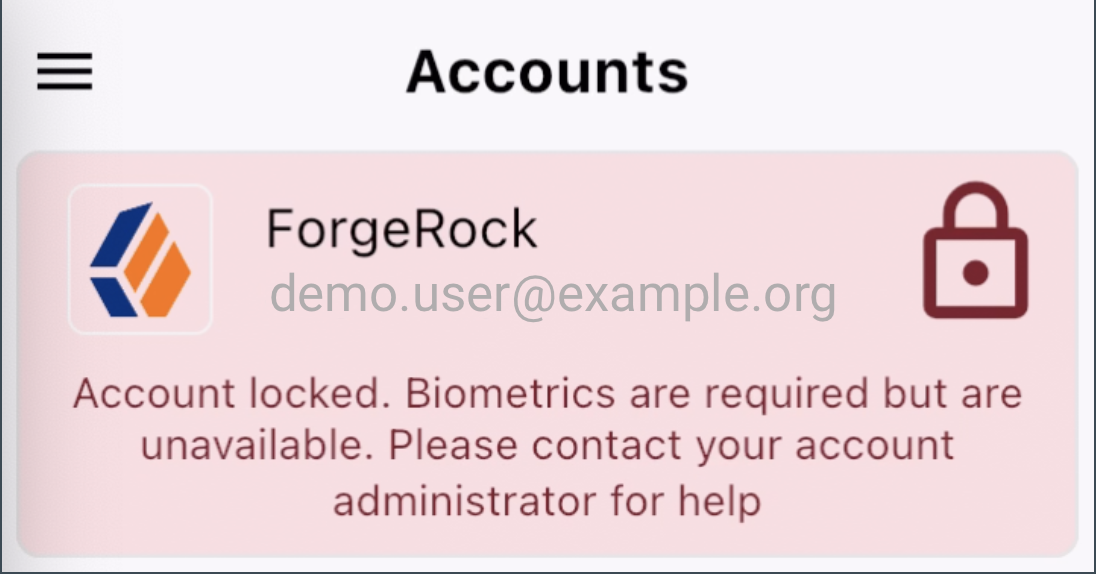
If the conditions of the policy are not met, the account cannot be registered in the Authenticator app. If the conditions of the policies applied to the account are breached anytime after successful registration, the account is locked, and MFA is blocked:
Available policies
The Authenticator app supports the following policies by default:
- Require biometrics
-
Policy name:
biometricAvailableRequire the device uses biometric sensors to unlock the operating system.
- Device tampering detection
-
Policy name:
deviceTamperingRequire the device has not been tampered with, for example, if it has root access or is jailbroken.
This policy applies if the tampering likelihood score returned by the device to the Authenticator app exceeds the provided
scoreparameter, which is a number between0and1.0. The higher the score, the more likely it is that the device has been tampered with.
Enable Authenticator app policies
Use the JSON Authenticator Policies property in the Combined MFA Registration node to enable policies.
Specify the policies and their parameters to apply to the device being registered in JSON format, as follows:
{
"policyName" : { policyParameters | empty }
}Example:
{
"biometricAvailable": { },
"deviceTampering": {
"score": 0.8
}
}Next steps
You can add support for app policies in your own Android and iOS applications, by using the Ping (ForgeRock) Authenticator module.
For more information, refer to Integrate authenticator app policies.
