Step 2. Configure connection properties
In this step, you configure the kotlin-central-login-oidc sample to connect to the OAuth 2.0 application you created in PingOne, using OIDC login.
-
In Android Studio, open the
sdk-sample-apps/android/kotlin-central-login-oidcproject you cloned in the previous step. -
In the Project pane, switch to the Android view.
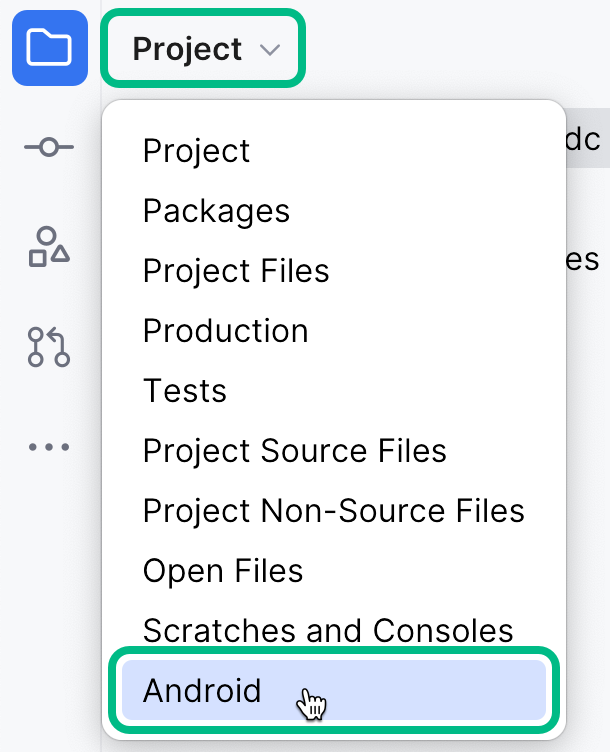 Figure 1. Switching the project pane to Android view.
Figure 1. Switching the project pane to Android view. -
In the Android view, navigate to app > kotlin+java > com.example.app, and open
Config.kt. -
Edit the default values provided in the
PingConfigclass with the values from your PingOne server:PingConfigclass default valuesdata class PingConfig( var discoveryEndpoint: String = "https://openam-sdks.forgeblocks.com/am/oauth2/realms/alpha/.well-known/openid-configuration", var oauthClientId: String = "AndroidTest", var oauthRedirectUri: String = "org.forgerock.demo:/oauth2redirect", var oauthSignOutRedirectUri: String = "", var cookieName: String = "5421aeddf91aa20", var oauthScope: String = "openid profile email address") )- discoveryEndpoint
-
The
.well-knownendpoint from your OAuth 2.0 application in PingOne.How do I find my PingOne .well-known URL?
To find the
.well-knownendpoint for an OAuth 2.0 client in PingOne:-
Log in to your PingOne administration console.
-
Go to Applications > Applications, and then select your OAuth 2.0 client.
For example, sdkPublicClient.
-
On the Overview tab, expand the Connection Details section, and then copy the OIDC Discovery Endpoint value.
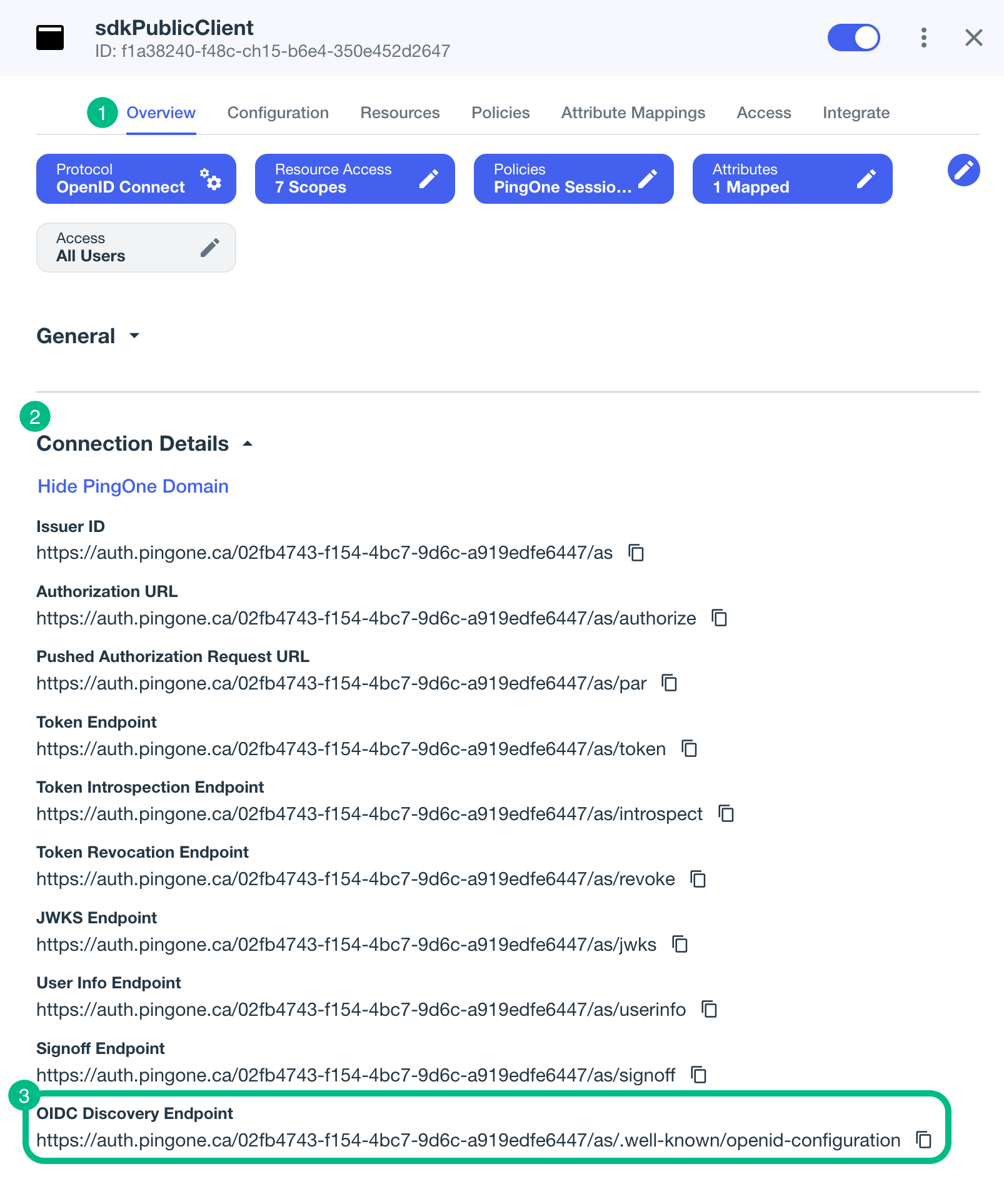
For example,
https://auth.pingone.com/3072206d-c6ce-ch15-m0nd-f87e972c7cc3/as/.well-known/openid-configuration -
- oauthClientId
-
The client ID from your OAuth 2.0 application in PingOne.
For example,
6c7eb89a-66e9-ab12-cd34-eeaf795650b2 - oauthRedirectUri
-
The
redirect_urias configured in the OAuth 2.0 client profile.This value must exactly match a value configured in your OAuth 2.0 client.
For example,
org.forgerock.demo://oauth2redirect - oauthSignOutRedirectUri
-
Leave this property empty.
It signals that the SDK can use the ID token to end the user’s session, and does not need to open and return from a web page to perform log out.
You must have enabled the Terminate User Session by ID Token setting when creating the OAuth 2.0 client in PingOne if you leave this property empty.
- cookieName
-
Set this property to an empty string. PingOne servers do not require this setting.
- oauthScope
-
The scopes you added to your OAuth 2.0 application in PingOne.
For example,
openid profile email phone
The result resembles the following:
PingConfigclass example valuesdata class PingConfig( var discoveryEndpoint: String = "https://auth.pingone.com/3072206d-c6ce-ch15-m0nd-f87e972c7cc3/as/.well-known/openid-configuration", var oauthClientId: String = "6c7eb89a-66e9-ab12-cd34-eeaf795650b2", var oauthRedirectUri: String = "org.forgerock.demo://oauth2redirect", var oauthSignOutRedirectUri: String = "", var cookieName: String = "", var oauthScope: String = "openid profile email phone" ) -
Optionally, specify which of the configured policies PingOne uses to authenticate users.
In
/app/kotlin+java/com.example.app/centralize/CentralizeLoginViewModel, in thelogin(fragmentActivity: FragmentActivity)function, add anacr_valuesparameter to the authorization request by using thesetAdditionalParameters()method:fun login(fragmentActivity: FragmentActivity) { FRUser.browser().appAuthConfigurer() // Add acr values to the authorization request .authorizationRequest{ it.setAdditionalParameters( mapOf( "acr_values" to "<Policy IDs>" ) ) } .customTabsIntent { it.setColorScheme(CustomTabsIntent.COLOR_SCHEME_DARK) }.appAuthConfiguration { appAuthConfiguration → } .done() .login(fragmentActivity, object : FRListener<FRUser> { override fun onSuccess(result: FRUser) { state.update { it.copy(user = result, exception = null) } } override fun onException(e: Exception) { state.update { it.copy(user = null, exception = e) } } } ) }Replace <Policy IDs> with either a single DaVinci policy by using its flow policy ID, or one or more PingOne policies by specifying the policy names, separated by spaces or the encoded space character
%20.Examples:
- DaVinci flow policy ID
-
"acr_values" to "d1210a6b0b2665dbaa5b652221badba2" - PingOne policy names
-
"acr_values" to "Single_Factor%20Multi_Factor"
For more information, refer to Editing an application - OIDC.
-
Save your changes.