Configuring Kong Gateway for PingAccess integration
Download, install, and configure the ping-auth plugin to set up a connection between Kong Gateway and PingAccess.
Before you begin
Install and start Kong Gateway. Learn more in the Kong Gateway documentation.
Steps
-
Download and extract the
ping-authplugin for Kong Gateway from https://luarocks.org/modules/pingidentity/kong-plugin-ping-auth. -
Install the
ping-authplugin using one of the following procedures:-
Via LuaRocks from the created ‘rock’: If you use this procedure, run the
luarocks install kong-plugin-ping-authcommand to install the plugin. -
Manually: Learn more in Kong’s installation guide.
-
-
After installation, load the plugin into Kong:
-
Edit the
pluginsproperty in thekong.conffile to include theping-authplugin.Example:
plugins = bundled,ping-auth -
Restart Kong Gateway to apply your changes.
-
To confirm that Kong loaded the plugin successfully, look for the debug-level message
Loading plugin: ping-authin Kong’serror.logfile.
You can find more information and configuration tips in Load the plugin and Verify loading the plugin in the Kong Gateway documentation.
-
-
Use the Kong Gateway UI or API to complete the configuration.
-
Kong Gateway UI
-
Kong Gateway API
Setting up Kong Gateway
Steps
-
In Kong Manager, select the Default workspace, then click Plugins.
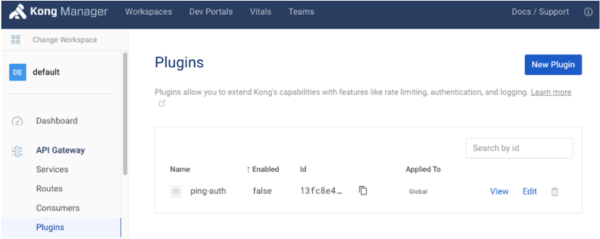
-
On the
ping-authline, click Edit -
On the Update ping-auth plugin page, click the toggle to enable the plugin.
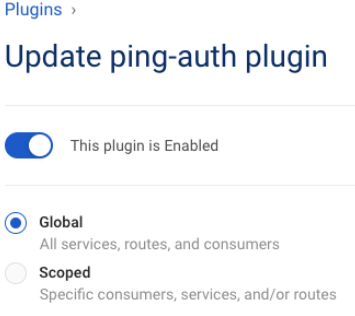
-
(Optional) If you want to enable the plugin for specific consumers, services, or routes, click Scoped and then enter Service, Route, and Consumer information as needed.
-
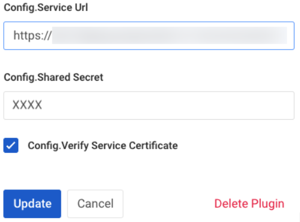
In the Config.Service URL field, enter the full URL for PingAccess, using the
https://<PINGACCESS_URL>:<SIDEBAND_PORT>/format.Example:
https://localhost:3020/
-
<PINGACCESS_URL>is the fully-qualified name of the machine running PingAccess. -
Don’t include
/sideband…in the path. -
The default sideband port is
3020, but you should check thesideband.http.portproperty in the PingAccessrun.propertiesfile to confirm that you haven’t configured a different value. Learn more in the Configuration file reference. -
The
sideband.http.enabledproperty must be set totruein the PingAccessrun.propertiesfile for theping-authplugin to communicate with PingAccess successfully.
-
-
In the Config.Shared Secret field, paste the shared secret you created in Configuring PingAccess for Kong Gateway integration.
Version 1.2.0 of the ping-authplugin supports referenceable secrets. For security reasons, store the shared secret in a vault supported by Kong. Learn more in Secrets Management and Environment Variables Vault in the Kong documentation. -
In the Config.Secret Header Name field, enter the name of the header that provides the shared secret.
The default value is
CLIENT-TOKEN. -
(Optional) Configure additional options in Kong Manager or the API:
You can find information on using the API to configure these fields in Create a plugin in the Kong Gateway admin API documentation. Option API Field Name Description Config.Connection KeepAlive Msconnection_keepAlive_msThe duration to keep the connection alive for reuse.
The default value is
6000.Config.Connection Timeout Msconnection_timeout_msThe duration to wait before the connection times out.
The default value is
10000.Config.Enable Debug Loggingenable_debug_loggingControls if requests and responses are logged at the debug level. The default value is
false.For log messages to show in the error.log, you must setlog_level = debugin thekong.conffile.Config.Verify Service Certificateverify_service_certificateControls whether the service certificate is verified.
This configuration option is intended for testing purposes. The default value is
true. -
Click Update, then click Update Plugin.
Next steps
Setting up Kong Gateway using the API
Steps
-
Include the following JSON object in a POST request to
https://<KONG_URL>/plugins:{ "name": "ping-auth", "enabled": true, "config": { "service_url": "https://<PINGACCESS_URL>:3020/", "shared_secret": "<SHARED_SECRET>", "secret_header_name": "<HEADER_NAME>" } }Use the following information to fill out the required fields in the Config section:
-
service_url: The full URL of the Ping policy provider, using thehttps://<PINGACCESS_URL>:<SIDEBAND_PORT>/format. The default value ishttps://localhost:3020/.-
<PINGACCESS_URL>is the fully-qualified name of the machine running PingAccess. -
Don’t include
/sideband…in the path. -
The default sideband port is
3020, but you should check thesideband.http.portproperty in the PingAccessrun.propertiesfile to confirm that you haven’t configured a different value. Learn more in the Configuration file reference. -
The
sideband.http.enabledproperty must be set totruein the PingAccessrun.propertiesfile for theping-authplugin to communicate with PingAccess successfully.
-
-
shared_secret: The shared secret used to authenticate this plugin to the policy provider. Paste the shared secret you created in Configuring PingAccess for Kong Gateway integration.Version 1.2.0 of the ping-authplugin supports referenceable secrets. For security reasons, store the shared secret in a vault supported by Kong. Learn more in Secrets Management and Environment Variables Vault in the Kong documentation. -
secret_header_name: The name of the header that provides the shared secret. The default value isCLIENT-TOKEN.
-
-
(Optional) Include additional fields in the POST request, making sure to adhere to the Kong API specification.
Learn more in Create a plugin in the Kong Gateway admin API documentation.
Option API Field Name Description Config.Connection KeepAlive Msconnection_keepAlive_msThe duration to keep the connection alive for reuse.
The default value is
6000.Config.Connection Timeout Msconnection_timeout_msThe duration to wait before the connection times out.
The default value is
10000.Config.Enable Debug Loggingenable_debug_loggingControls if requests and responses are logged at the debug level. The default value is
false.For log messages to show in the error.log, you must setlog_level = debugin thekong.conffile.Config.Verify Service Certificateverify_service_certificateControls whether the service certificate is verified.
This configuration option is intended for testing purposes. The default value is
true.