PingOne Advanced Identity Cloud documentation
Single-page edition
All PingOne Advanced Identity Cloud docs on a single HTML page. Use this for text searches, or to make a PDF.
PingOne Advanced Identity Cloud
PingOne Advanced Identity Cloud is a SaaS-based digital identity and access management (IAM) solution designed for workforce, consumer, and B2B identities. Ping Identity handles the deployment, management, upgrades, and monitoring of the platform’s various software components, ensuring a seamless and secure experience.
With Advanced Identity Cloud, you can manage the complete lifecycle of identities including:
-
Flexible and extensible user journeys
-
Real-time identity synchronization between cloud and on premises
-
Policy enforcement using PingGateway
-
Device-profiling authentication in user journeys using Ping SDKs
And much more...
Start here
About the getting started guide
Understand the purpose and structure of this guide
Key concepts
Learn about key Advanced Identity Cloud concepts
Getting help
Get help with Advanced Identity Cloud
Task 1: Get access to your tenant
Get access to your Advanced Identity Cloud tenant
Task 2: Explore the platform
Explore the Advanced Identity Cloud consoles
Task 3: Add end users
Add your first end users
Task 4: Design self-registration experiences
Enable users to sign up to applications and services
Task 5: Design user authentication experiences
Enable users to authenticate to applications and services
Task 6: Enable customer account recovery
Enable users to recover their accounts
Task 7: Enable customer profile management
Enable users to manage their profiles
Task 8: Add basic branding
Add basic branding to your end user screens
Task 9: Integrate an OIDC application
Integrate an OpenID Connect (OIDC) application for single sign-on (SSO)
Task 10: Next steps
Get going with Advanced Identity Cloud
Advanced Identity Cloud analytics dashboard
PingOne Advanced Identity Cloud analytics dashboard provides a comprehensive snapshot of your Advanced Identity Cloud system usage. You can use the dashboard to gain valuable insights on your tenants:
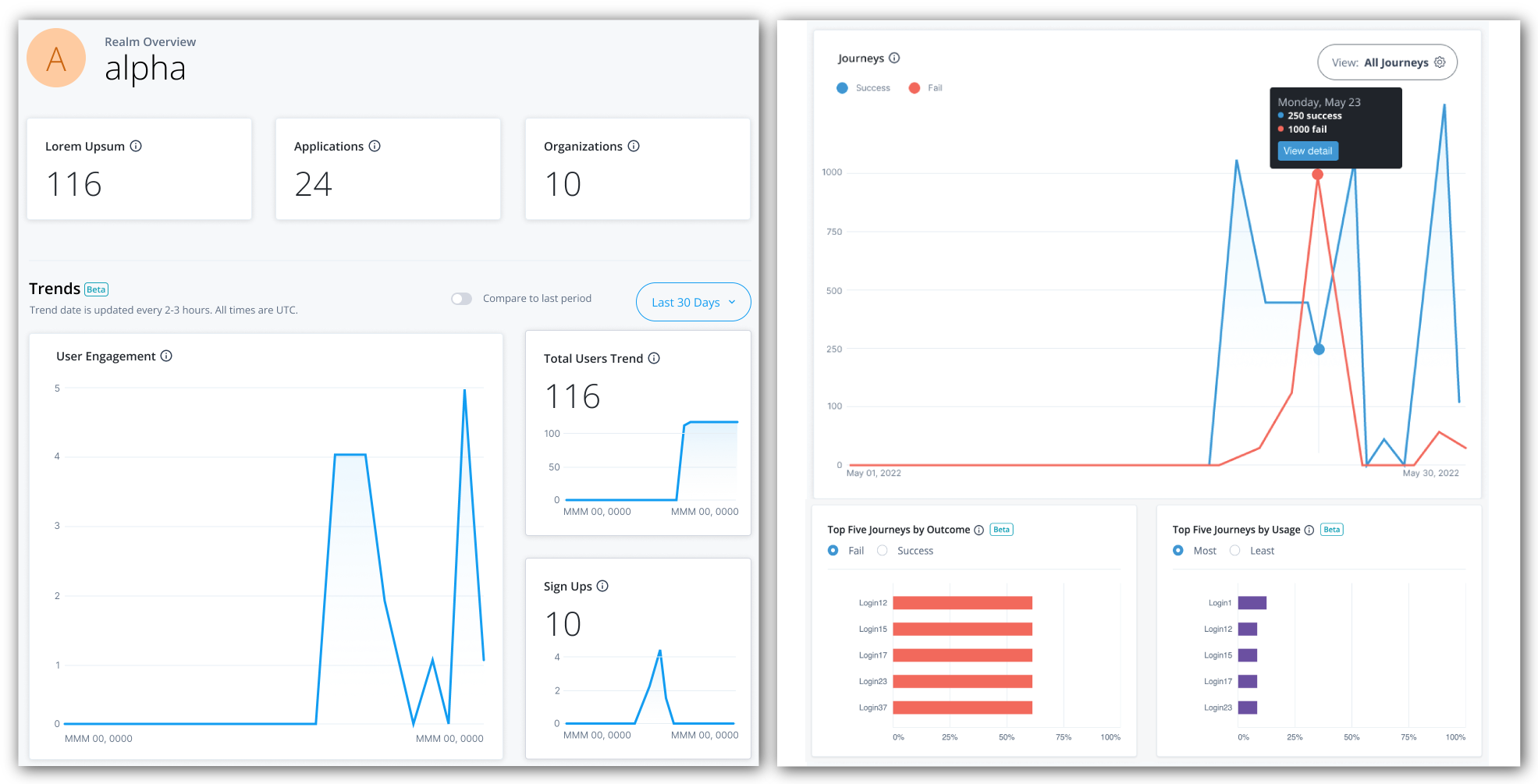
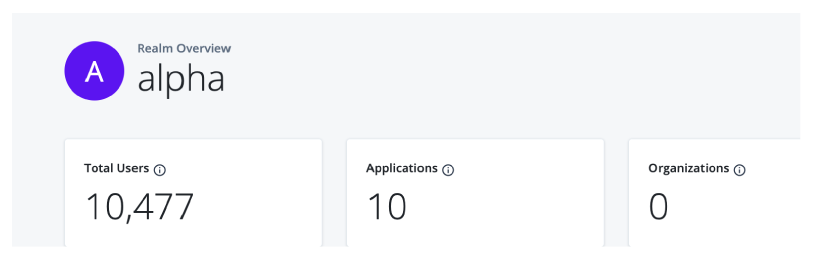
Monitor the number of users and engagements
At the top of the Identity Cloud analytics dashboard, there is a summary of total number of users, applications, and organizations in your realm. These realm usage totals are summarized as follows:
-
Total Users. Displays the total count of active and inactive users in this realm.
-
Applications. Displays the total number of current applications in this realm.
-
Organizations. Displays the total number of organizations in this realm.
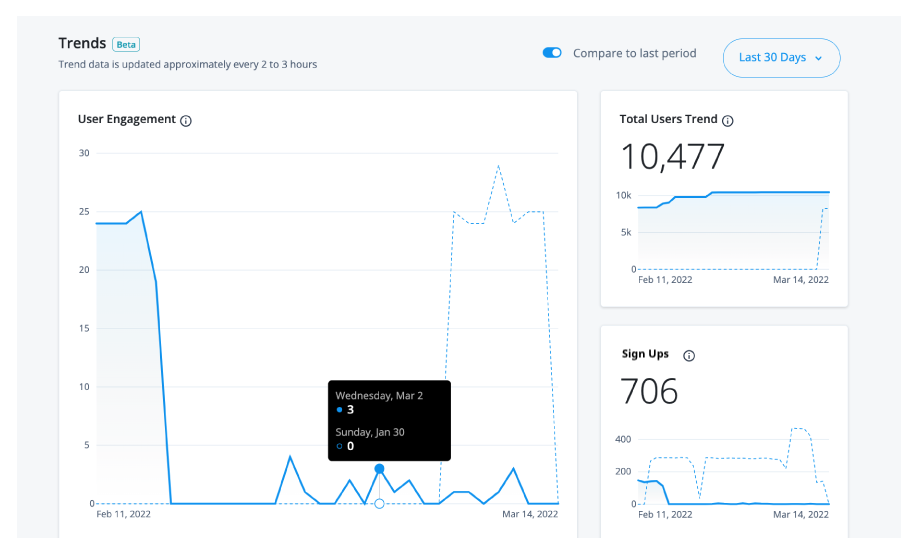
Below the realm usage totals, Identity Cloud analytics dashboard displays three trendline charts: user engagements, total users, and new users. These trendline charts are updated every two to three hours and are summarized as follows:
-
User Engagement. Displays the trendline of the number of user engagements within a given time period; by default, the last 30 days. A user engagement is counted when a user is involved in an identity operation within the given time period. An identity operation can be any of the following:
-
Sign-in/authentication
-
Token refresh (for example, token issuance, validation, and refresh)
-
Password creation or change
A user who has multiple user engagements within a given time period is counted once.
-
-
Total Users Trend. Displays the trendline for total users (active and inactive) during the time period in this realm.
The total users trend number may differ from the Total Usersnumber at the top of the page as the data depends on the selected time period and the update frequency. For example, new users who have been added to the system within the last hour may not appear yet on the page. -
Sign Ups. Displays the trendline for new user sign-ups during the time period in this realm.
Filter timelines
Each chart displays the usage numbers for the current time period, expressed as solid lines; the dotted lines display
the numbers for the previous time period. For example, if the time period is Last 30 days, the solid line displays
the numbers over the last 30 days from today’s date; the dotted line displays the previous 30-day numbers.
To compare the numbers for a specific date, hover over a point on either line to display the numbers for the current and the previous time periods.
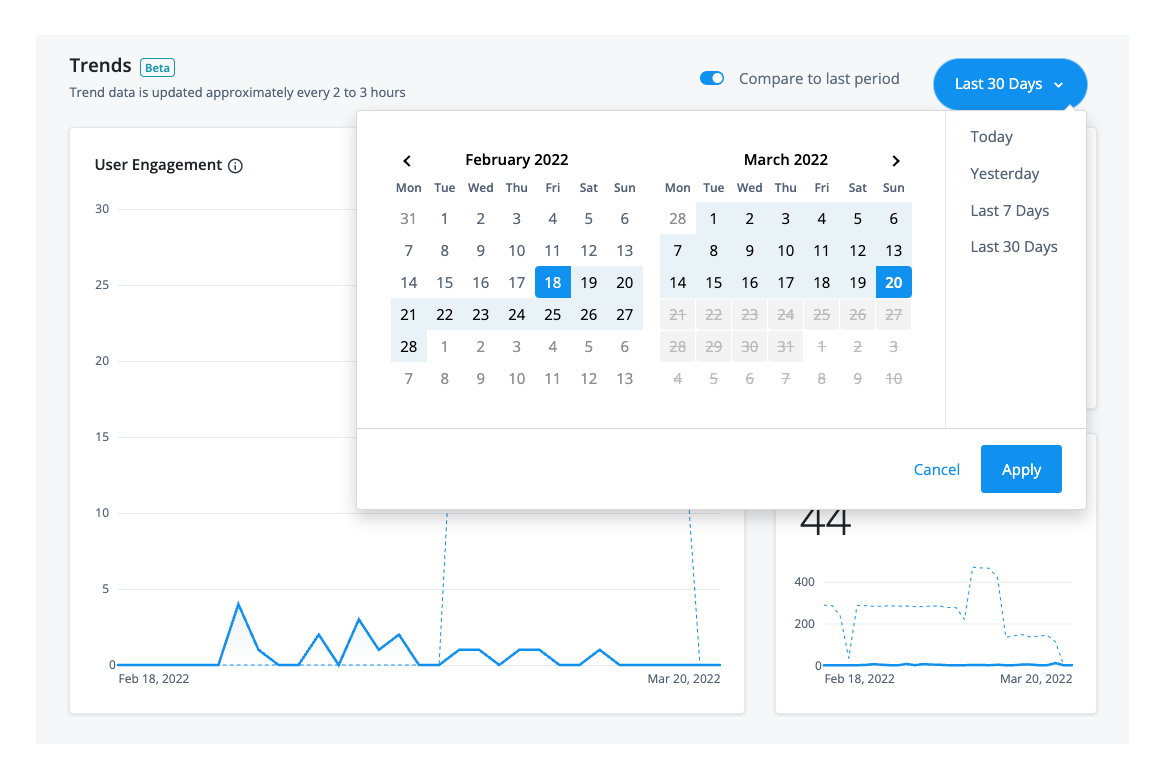
By default, the Identity Cloud analytics dashboard displays the number of engagements, total users, and new user sign-ups for a 30-day period, you can filter the output by changing the time period.
Change the time period for the trendline charts
-
Click Last 30 days, and select one of the following time periods:
-
Today. Displays the numbers for
today,12:00 a.m. to the current time. -
Yesterday. Displays the numbers for
yesterday,12:00 a.m. to 12:00 p.m. on the previous day. -
Last 7 Days. Displays the numbers for the last seven days from today’s date.
-
Last 30 Days. Displays the last 30 days from today’s date. This is the default time period.
All dates and time periods are based on UTC time.
-
-
Click Apply to save your changes.
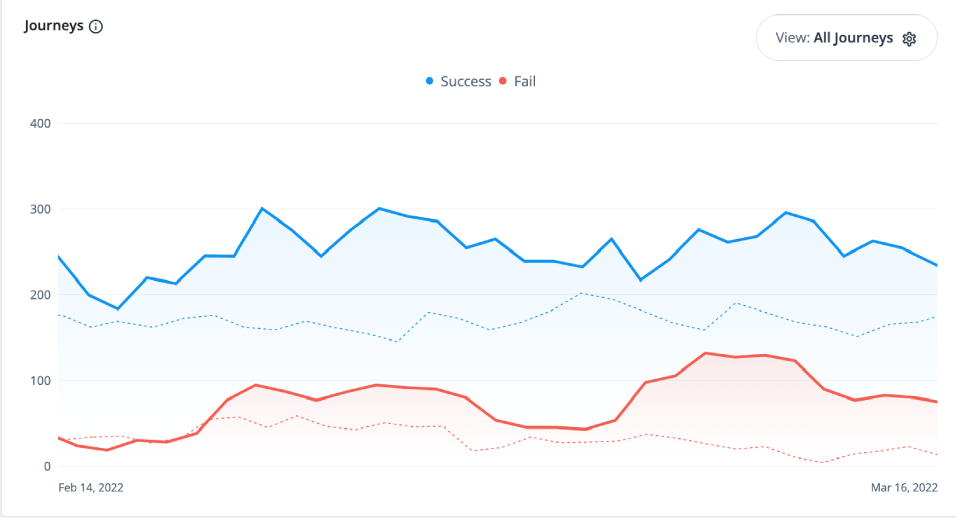
Monitor journeys
You can refer to a chart on the number of successful and failed journey outcomes within your realm on the Identity Cloud analytics dashboard. Scroll down the Identity Cloud analytics dashboard page to refer to the Journeys graph.
By default, the Identity Cloud analytics dashboard displays the aggregation of all successful and failed journeys on the Advanced Identity Cloud. These aggregations express four different types of information:
-
Blue lines indicate successful journey outcomes.
-
Red lines indicate failed journey outcomes.
-
Solid lines indicate the journey outcomes that occurred within the current selected time period.
-
Dotted lines indicate the journey outcomes in the previous time period.
| The journey usage is not counted if the journey is used as a node in another journey. |
The Identity Cloud analytics dashboard also lets you filter the chart by journey type. The available journeys are listed on the Advanced Identity Cloud Journeys page and includes any custom journeys that you may have configured. For example:
-
EvaluateRisk
-
ForgottenUsername
-
Login (default)
-
PasswordGrant
-
ProgressiveProfile
-
Registration
-
ResetPassword
-
Sample Tree
-
UpdatePassword
The categories are:
-
Authentication
-
Password Reset
-
Progressive Profile
-
Registration
-
Username Reset
| The journeys and categories options come from any tag that you have selected. |
Access journey pass/fail details
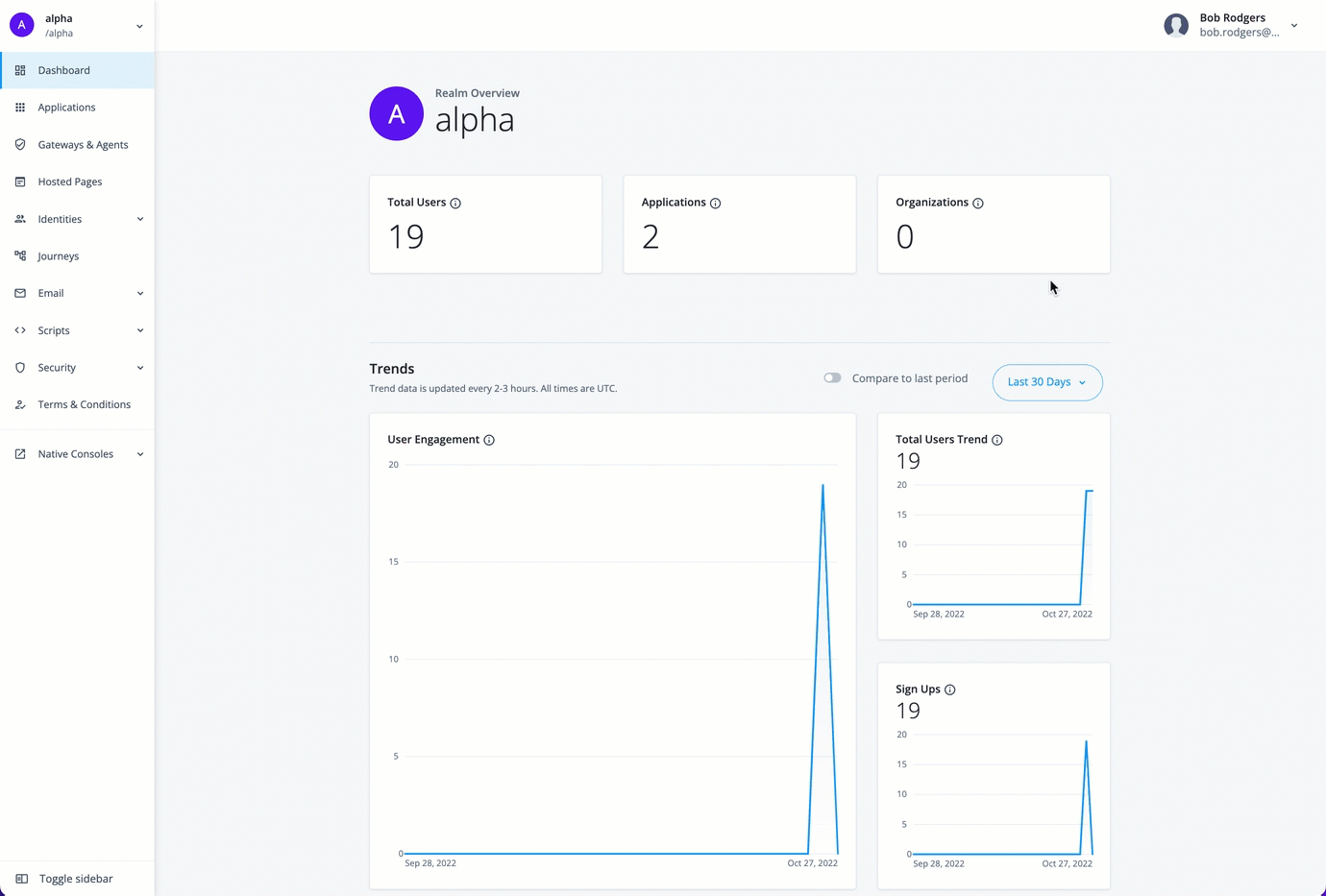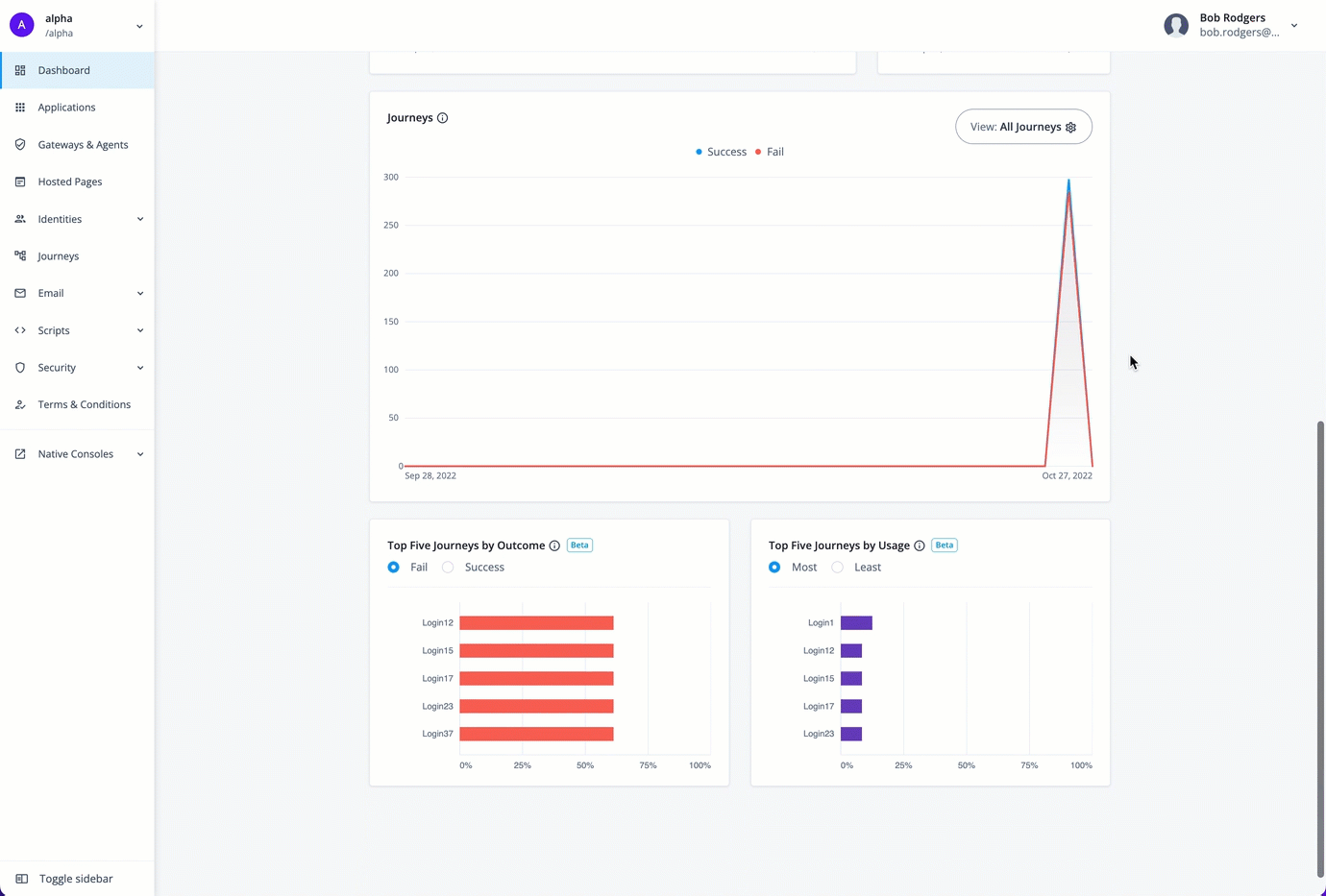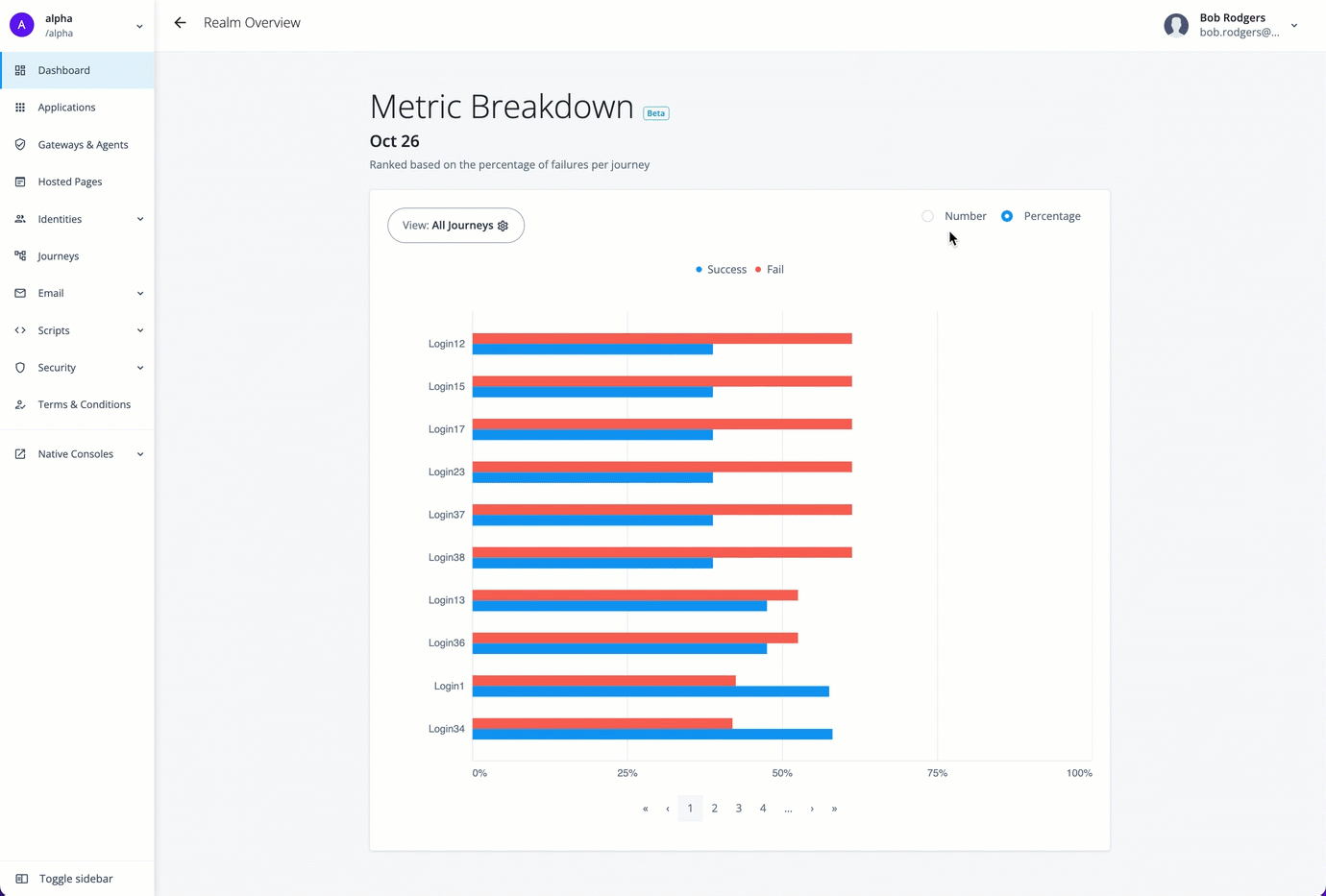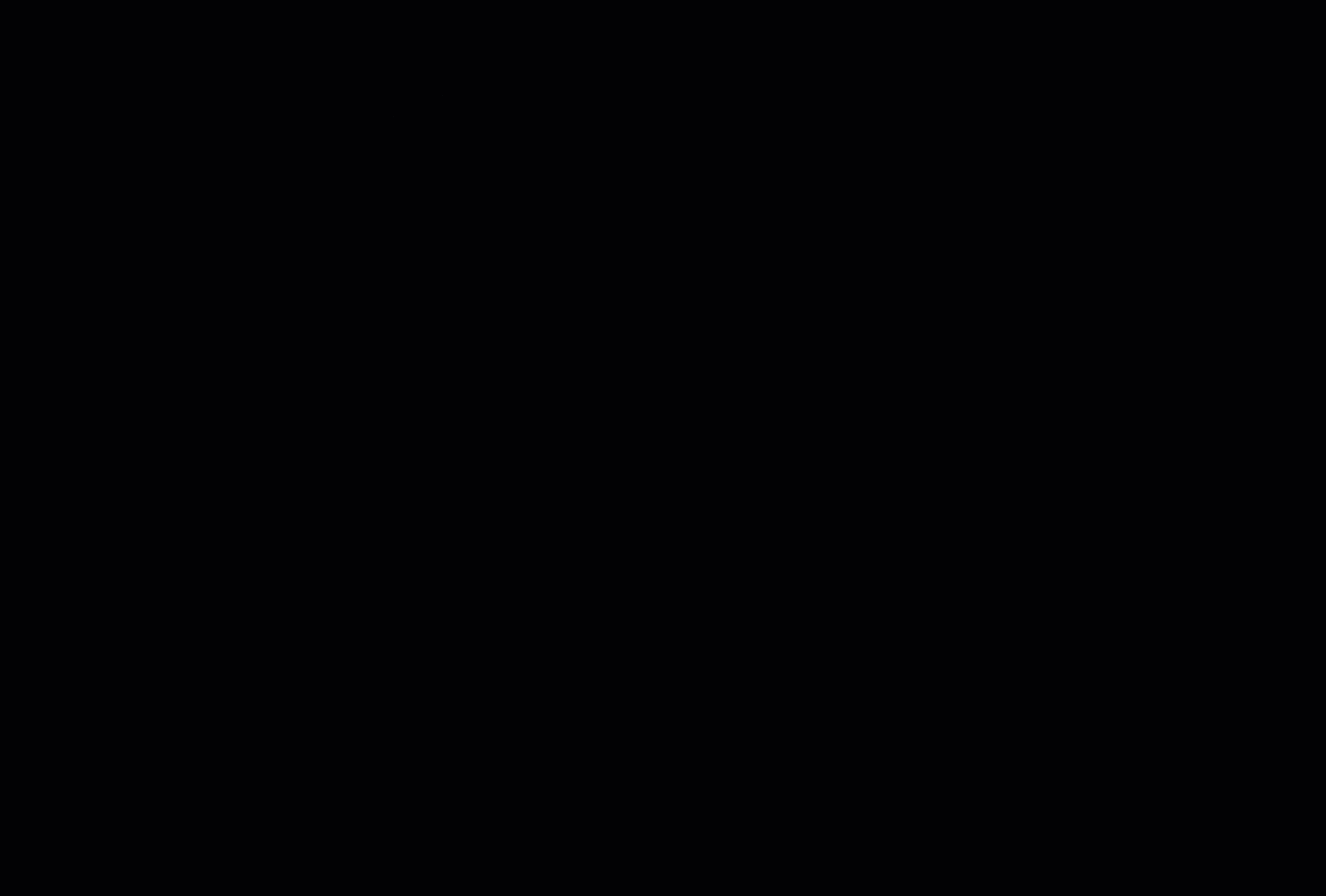
The Journeys chart also lets you drill down at specific points on a trendline to access its details, or metric breakdown. Red lines indicate failed journeys. Blue lines indicate successful journeys.
For example, you can use the Metric Breakdown page to review the journeys for the selected date, sorted by a ranking of percentage failures (default). The percentage is calculated for each journey as the total outcomes passed or failed, and then sorted in descending order from the highest failed journey by percentage to the lowest failed journey by percentage.
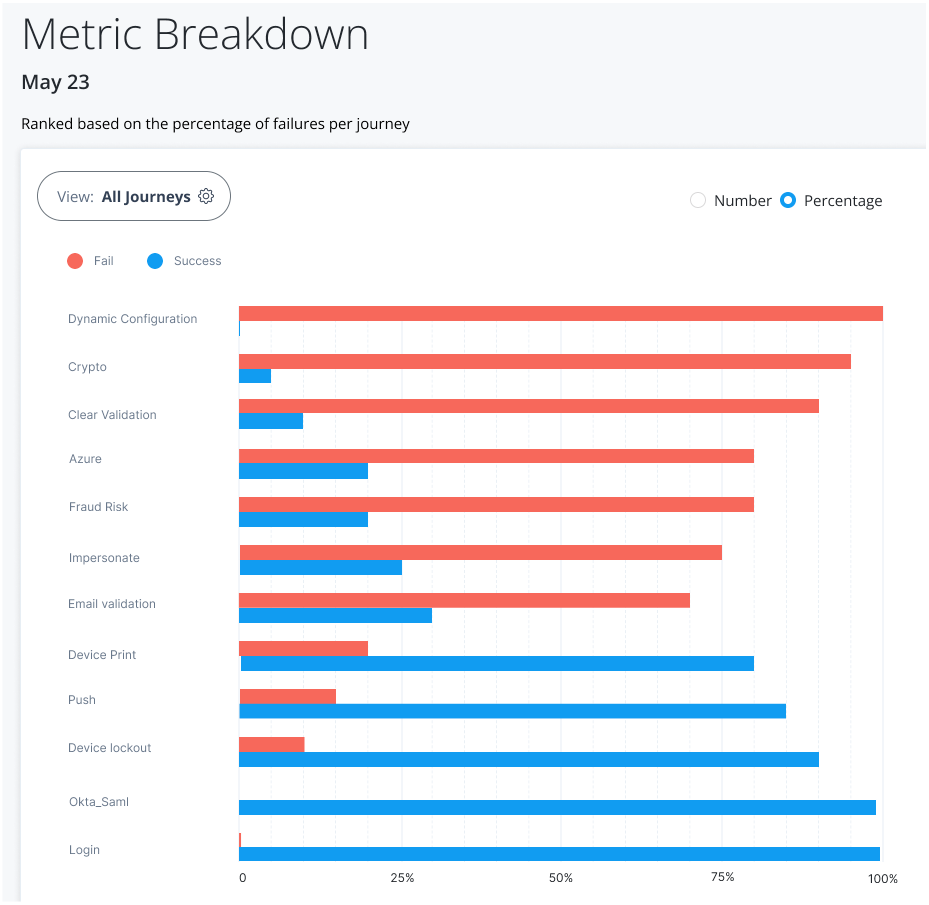
The Metric Breakdown page also lets you sort the journeys by number ranking. Number indicates the actual number of successful or failed outcomes for each journey.
The following table provides an example of how the analytics dashboard ranks by percentage and by number:
| Journey | Total Outcomes | Passed | Failed | Percentage Rank | Number Rank |
|---|---|---|---|---|---|
A |
900 |
630 |
270 (30%) |
2 |
1 |
B |
100 |
50 |
50 (50%) |
1 |
2 |
C |
100 |
80 |
20 (20%) |
3 |
3 |
| Timeouts are not displayed in the Journey outcomes. |
Access the metric breakdown page
-
On the Journeys chart, hover anywhere over a trendline to view the successful or failed outcomes for that date, and then click View detail. The Metric Breakdown page appears with more insights on the individual journeys. By default, All Journeys and Percentage are selected.
-
On the Metric Breakdown page, click Number to display the number of failed and successful journeys sorted by rank.
Click to show how to access the metric breakdown page
Top Five Journeys by Outcome and Top Five Journeys by Usage widgets
The Identity Cloud analytics dashboard displays two additional widgets providing trendlines into your journeys: Top Five Journeys by Outcome and Top Five Journeys by Usage. The Top Five Journeys by Outcome widget displays the top five journeys ranked by percentage failed or successful. The default selection is Fail. You can change the selection to Success to display top five successful journeys.
The Top Five Journeys by Usage widget displays the top five most or least used journeys. By default, the most used journeys are selected. Each bar chart provides the percentage usage of the journey in the given time period based on the outcomes only. For each journey, the calculation is based on the total number of outcomes for the journey divided by the total number of all journey outcomes in the time period.
| The widgets only display the journey outcomes for the selected time period. The x-axis denotes the percentage outcomes in the journey. |
Access top five journeys by outcome and top five journeys by usage
-
On the Top Five Journeys by Outcome widget, the widget displays the top five failed journeys by default. Click Success to display the top five successful journeys.
-
On the Top Five Journeys by Usage widget, the widget displays the most used journeys by default. Click Least to display the least used journeys.
Notice
The analytics dashboard service provides key insights and trends with respect to successful or failed journey outcomes, number of users, user engagement, number of new users (sign-ons), applications, and organizations. By leveraging this functionality, Ping Identity customers can better understand their usage of the Advanced Identity Cloud. This functionality also allows Ping Identity to maintain accurate billing information with respect to such use.
All data Ping Identity collects for the purposes of providing the analytics dashboard service is anonymized using industry standard practices. The purpose is to ensure that the data does not contain any personally identifiable information, and further, so it cannot be re-identified. This includes, but is not limited to, a one-way SHA-256 hashing function that returns a hexadecimal representation of a UUID. This ensures that no personally identifiable information is used by Ping Identity, or any other third-party or system.
Data residency
When you sign up for PingOne Advanced Identity Cloud, you specify the region where you want your data to reside. This is key in helping you meet data residency compliance requirements while letting you place data as close to your users as possible.
Advanced Identity Cloud uses pre-configured ranges of IP addresses in Google Cloud Platform (GCP) regions. The IP addresses are not exclusive to Ping Identity.
Regions
The tables in this section show all the region abbreviations for the data regions that Advanced Identity Cloud uses. The region abbreviations are used in the naming convention of your tenant environment FQDNs.
The tables also indicate secondary backup regions when available.
Canada
| Region | Abbreviation | Backup region |
|---|---|---|
Montréal (northamerica-northeast1) |
nane1 |
A different region within Canada. |
United States
| Region | Abbreviation | Backup region |
|---|---|---|
Oregon (us-west1) |
usw1 |
A different region within the United States. |
Los Angeles (us-west2) |
usw2 |
A different region within the United States. |
Iowa (us-central1) |
usc1 |
A different region within the United States. |
South Carolina (us-east1) |
use1 |
A different region within the United States. |
North Virginia (us-east4) |
use4 |
A different region within the United States. |
Brazil
| Region | Abbreviation | Backup region |
|---|---|---|
São Paulo (southamerica-east1) |
sae1 |
Regional selection is available. For more information, contact your Ping Identity representative. |
Europe
| Region | Abbreviation | Backup region |
|---|---|---|
Finland (europe-north1) |
en1 |
A different region within Europe. |
Belgium (europe-west1) |
ew1 |
A different region within Europe. |
London (europe-west2) |
ew2 |
A different region within Europe. |
Frankfurt (europe-west3) |
ew3 |
A different region within Europe. |
Netherlands (europe-west4) |
ew4 |
A different region within Europe. |
Zurich (europe-west6) |
ew6 |
A different region within Europe. |
Paris (europe-west9) |
ew9 |
A different region within Europe. |
Middle East
| Region | Abbreviation | Backup region |
|---|---|---|
Doha (me-central1) |
mec1 |
Regional selection is available. For more information, contact your Ping Identity representative. |
Dammam (me-central2) |
mec2 |
Regional selection is available. For more information, contact your Ping Identity representative. |
Asia
| Region | Abbreviation | Backup region |
|---|---|---|
Singapore (asia-southeast1) |
ase1 |
Regional selection is available. For more information, contact your Ping Identity representative. |
Jakarta (asia-southeast2) |
ase2 |
Regional selection is available. For more information, contact your Ping Identity representative. |
Hong Kong (asia-east2) |
ae2 |
Regional selection is available. For more information, contact your Ping Identity representative. |
Development, staging, and production tenant environments
Each PingOne Advanced Identity Cloud account includes a development, a staging, and a production tenant environment. These three environments let you build, test, and deploy your IAM applications:
| Tenant Environment | Description | ||
|---|---|---|---|
Development |
Used for building and adding new features.
|
||
Staging |
Used for testing development changes, including stress tests and scalability tests with realistic deployment settings. |
||
Production |
Used for deploying applications into operation for end users. |
Manage configuration
Advanced Identity Cloud has two types of configuration, dynamic and static. Learn more about the difference between them in What kind of configuration changes can my company make?.
You can change dynamic configuration in any environment, but you can only change static configuration in your development environment. Advanced Identity Cloud therefore uses a promotion model to move static configuration changes through the three environments.
Promote static configuration
The development environment is mutable. This means that you can make static configuration changes to the environment through one of the admin UIs or through the REST API.
The staging and production environments are not mutable. This means that you cannot make static configuration changes to these environments directly. Instead, you must move the changes from the development environment to the staging environment by running a promotion, then move the changes from the staging environment to the production environment by running a further promotion.
In situations where you want a static configuration value (such as an authentication token) to be distinct in each environment, you can set the value as an ESV in each environment, then insert the ESV placeholder into your configuration, then move the configuration to your staging and production environments by running sequential promotions. Learn more in Configure placeholders to use with ESVs.
| Tenant environment | Mutable | Make static configuration changes |
|---|---|---|
Development |
Yes |
|
Staging |
No |
|
Production |
No |
Sandbox tenant environment
|
Advanced Identity Cloud add-on capability
Contact your Ping Identity representative if you want to add a sandbox environment to your PingOne Advanced Identity Cloud subscription. Learn more in Add-on capabilities. |
A sandbox tenant environment is a standalone environment separate from your group of development, staging, and production tenant environments. It tracks the rapid release channel, which lets you test the newest features and fixes from Ping Identity before they reach your other environments. It’s mutable like your development environment, but because changes can’t be promoted, you have more freedom to test various use cases. You can run experiments without worrying about accidentally promoting your changes to your upper environments.
For example, you can create user journeys and test them before deciding which one you’d like to use in your development environment. You can safely do this in a sandbox environment because nothing in that environment is part of the promotion process. This means you don’t need to worry about cleaning up unused user journeys.
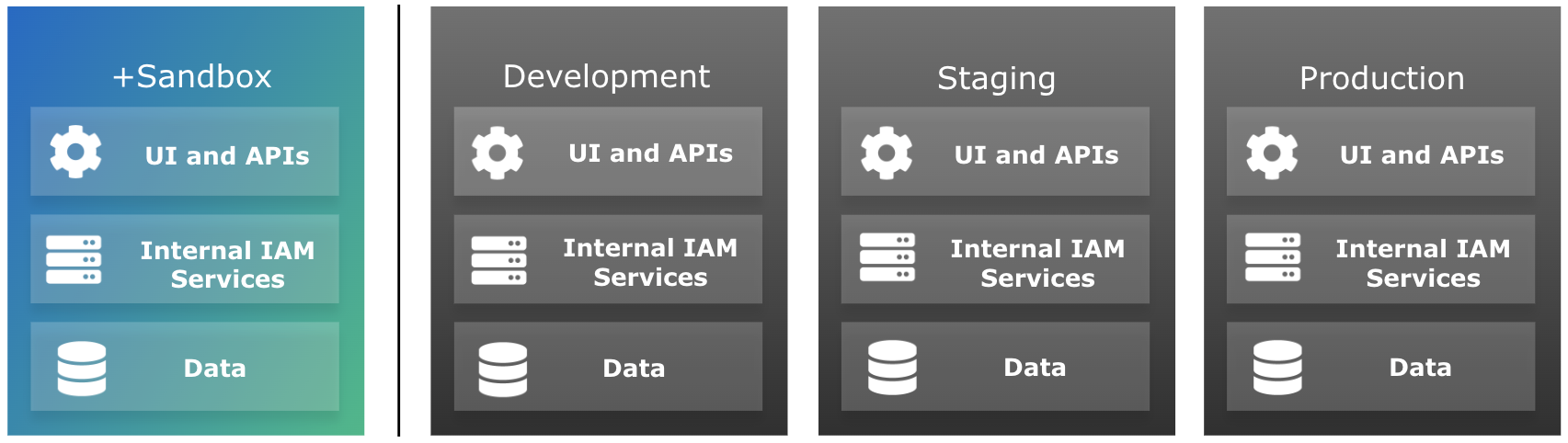
Sandbox usage guidelines
There are some important guidelines to note when using a sandbox environment. In particular, the environment should not be used for load testing, and it should not contain personally identifiable information (PII):
| Feature | Description | ||
|---|---|---|---|
Production use |
No |
||
Static & dynamic configuration |
Mutable via the UI and REST APIs |
||
Configuration promotion |
No |
||
Max number of identity objects |
10,000 identity objects
|
||
Log retention |
30 days |
||
Monitored via Statuspage.io |
No |
||
SLA |
N/A (support provided at lowest priority level, see below) |
||
Personally identifiable information (PII) |
No |
||
Load testing |
No |
||
Level of support |
Business hours Monday–Friday (excluding public holidays in Australia, Singapore, France, United Kingdom, United States, and Canada) |
UAT tenant environment
|
Advanced Identity Cloud add-on capability
Contact your Ping Identity representative if you want to add a UAT environment to your PingOne Advanced Identity Cloud subscription. Learn more in Add-on capabilities. |
A user acceptance testing (UAT) tenant environment is an additional environment that you can add into your standard promotion group of development, staging, and production tenant environments. It has the same capabilities as your staging environment, allowing you to test your development changes in a production-like environment.
Having a UAT environment in addition to your staging environment lets you perform different kinds of testing in parallel; for example, you could perform user acceptance testing in your UAT environment alongside load testing in your staging environment (or the other way around if you prefer).
You can add as many UAT environments as you need to your promotion group of environments. They are inserted into the self-service promotion process before the staging environment:
-
If you add one UAT environment, the revised promotion order is development > UAT > staging > production:
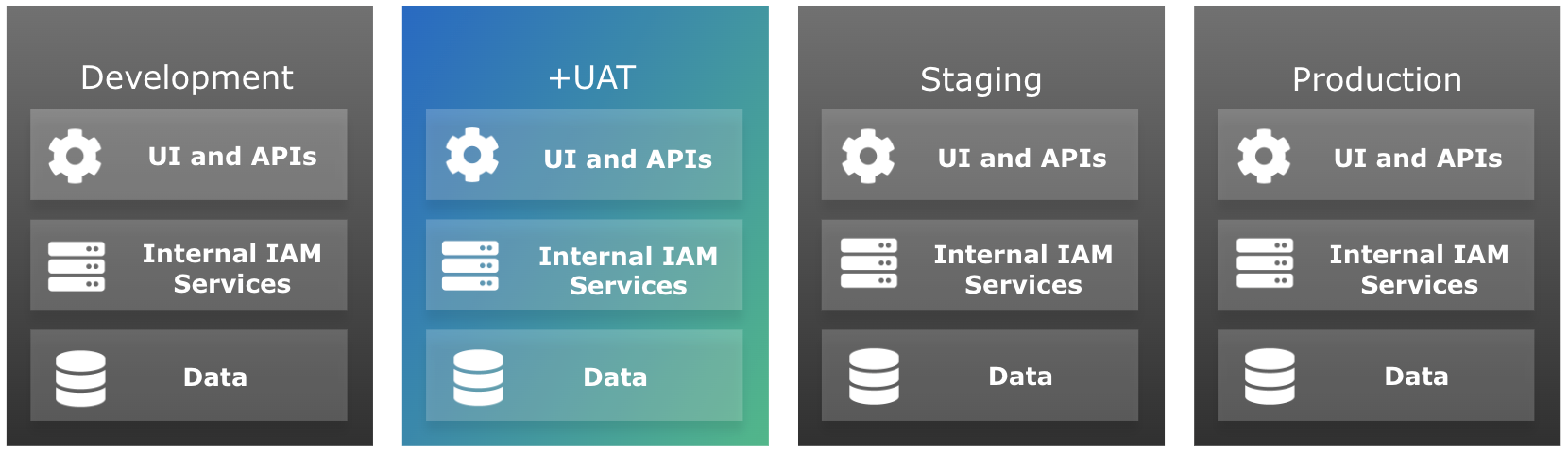
-
If you add a second UAT environment, the revised promotion order is development > UAT > UAT2 > staging > production:
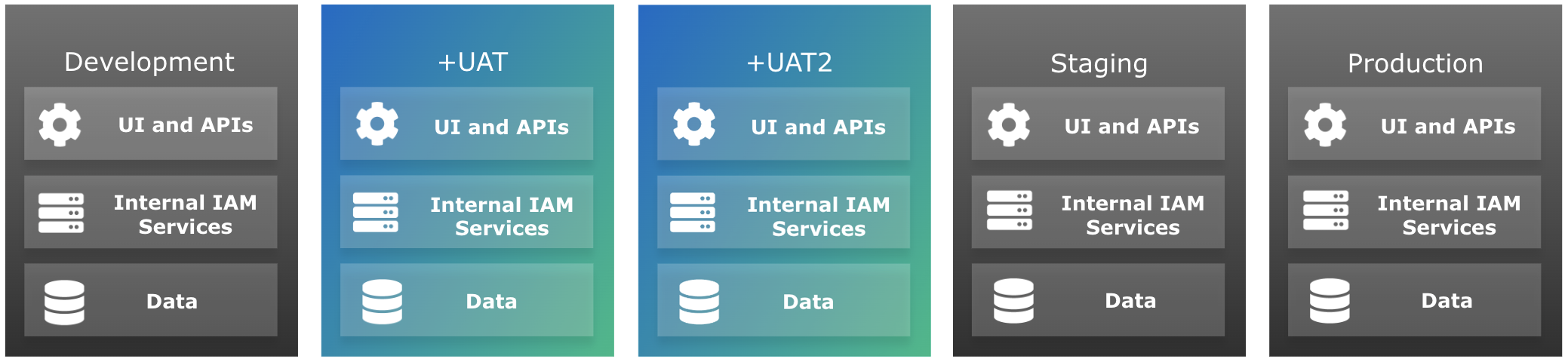
-
The promotion order is revised in the same way for each additional UAT environment you add. For example, if you add a third and a fourth UAT environment, the revised promotion order is development > UAT > UAT2 > UAT3 > UAT4 > staging > production.
Set up tenant administrators
A new UAT environment is set up with an initial super administrator (as specified to your Ping Identity representative when requesting the environment).
You can set up additional tenant administrators in the same way as you did for your development, staging, and production environments. Learn more in Invite tenant administrators.
Set up configuration
Existing customers
A new UAT environment contains no configuration; Ping Identity does not copy any configuration from your existing environments.
You need to promote your configuration from your development environment to your UAT environment. Observe the following warnings:
-
Make sure you promote from your development environment to your UAT environment before you promote from your UAT environment to your staging environment; otherwise, you will overwrite the configuration in your staging environment.
-
Make sure the configuration in your development environment matches the configuration in your staging environment, as this configuration eventually gets promoted through your UAT environment to your production environment.
-
Make sure all required ESVs are created in your UAT environment.
New customers
A new UAT environment contains no configuration, but neither does a new development, staging, or production environment. Therefore, your only additional consideration is that there is an extra environment inserted into the promotion process between your development environment and your staging environment.
You need to configure your development environment before you can promote to your UAT environment. Learn more about managing environments and promoting configuration between them in Introduction to self-service promotions.
Outbound static IP addresses
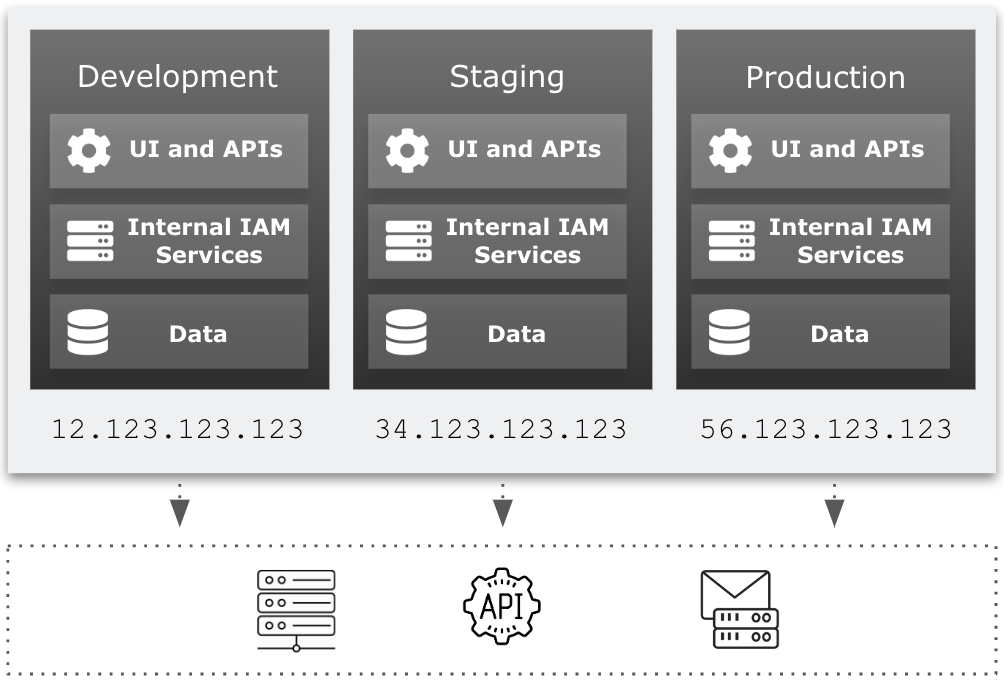
Ping Identity allocates outbound static IP addresses to each of your development, staging, and production tenant environments (and to any sandbox[1] and UAT[2] tenant environments). This lets you identify network traffic originating from PingOne Advanced Identity Cloud and from individual environments within Advanced Identity Cloud.
Having static IP addresses for outbound requests lets you implement IP allowlisting in your enterprise network. Some examples of IP allowlisting are:
-
Adding IP addresses to your firewall settings to restrict access to your internal APIs
-
Adding IP addresses to your email server settings so emails sent from Advanced Identity Cloud are not marked as spam
FAQ
Why would I need to know my outbound static IP addresses?
You can add them to an allowlist that restricts access to your network infrastructure, adding an extra layer of access security. For example, you may want to allow only Advanced Identity Cloud to make API calls to an SMTP server inside your network.
How are outbound static IP addresses being introduced?
-
Outbound static IP address functionality is available and enabled by default if your tenant environments were created on or after the following dates:
For these tenant environments, learn more in How can I find out what my outbound static IP addresses are?
-
Outbound static IP address functionality is available but not enabled if your tenant environments were created between the following dates:
For these tenant environments, learn more in How do I enable outbound static IP addresses for my tenants?.
-
Outbound static IP address functionality is not available if your tenant environments were created before May 10, 2022.
For these tenant environments, the functionality will become available in 2024. For more information, contact your Ping Identity representative.
How can I find out what my outbound static IP addresses are?
Outbound static IP address functionality is available and enabled by default if your tenant environments were created on or after the following dates:
You can view your outbound static IP addresses in your tenant global settings.
How do I enable outbound static IP addresses for my tenants?
Outbound static IP address functionality is available but not enabled if your tenant environments were created between the following dates:
To enable outbound static IP addresses and get your IP addresses:
-
Click Create a case.
-
Follow the steps in the case submission wizard by selecting your account and contract and answering questions about your tenant environments.
-
On the Please answer the following questions to help us understand the issue you’re facing page, enter the following details, and then click Next:
Field Value What product family is experiencing the issue?
Select PingOne Advanced Identity Cloud
What specific product is experiencing the issue?
Select Configuration
What version of the product are you using?
Select NA
What Hostname(s) or Tenant ID(s) does this apply to?
Enter a comma-separated list of FQDNs for the relevant tenant environments.
-
On the Tell us about the issue page, enter the following details, and then click Next:
Field Value Provide a descriptive title for your issue
Enter
Enable outbound static IP addressesDescribe the issue below
Enter
Enable outbound static IP addresses -
Click Submit.
-
Ping Identity support enables outbound static IP addresses and provides you with the IP addresses.
Tenant environment release information
Advanced Identity Cloud tenant environments each provide the following information about their status in the release process:
-
The current release version for that environment. This is available in all tenant environments.
-
The date and time of the next scheduled regular channel release to that environment. This is available in tenant environments that share promoted configuration (development, UAT[2], staging, and production).
You can only view information about the next scheduled release using the API.
View release information using the admin console
The easiest way to view the release versions of your tenant environments is to use the admin console.
In the Advanced Identity Cloud admin console in any tenant environment, choose one of the following:
-
Open the TENANT menu (upper right), then go to Tenant Settings > Details. The release version is displayed under Identity Cloud Version.
-
Scroll to the bottom of a page. The release version is displayed in the page footnotes.
The admin console does not display page footnotes in editors. For example, in the journey or hosted pages editors.
View release information using the API
You can use the API to view release information about your tenant environments. You might want to do this for these reasons:
-
To create monitoring alerts when release information changes.
-
To track the release information of your tenant environments in a single dashboard.
-
To track the seven-day deferral period for the next regular channel release to your production environment (if you’ve opted in to release deferral).
Release API endpoint
Advanced Identity Cloud provides the Release API endpoint to let you track release information.
Authenticate to the release API endpoint
To authenticate to the release API endpoint, use an access token created with the following scope:
| Scope | Description |
|---|---|
|
Full access to the release API endpoint. |
View release information
To view the release information in any tenant environment:
-
Get an access token created with the
fr:idc:release:*scope. -
Get the release information from the
/environment/releaseendpoint:$ curl \ --request GET 'https://<tenant-env-fqdn>/environment/release' \(1) --header 'Authorization: Bearer <access-token>' (2)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <access-token> with the access token. -
The response format depends on the type of tenant environment:
-
For sandbox[1] environments:
Show response
{ "currentVersion": "15374.0", (1) }1 The current release version of the tenant environment. -
For environments that share promoted configuration (development, UAT[2], staging, and production):
Show response
{ "currentVersion": "15158.7", (1) "nextUpgrade": "2024-10-29T14:00:00Z" (2) (3) }1 The current release version of the tenant environment. 2 The date and time of the next scheduled regular channel release to the tenant environment. 3 If you have opted in to release deferral, nextUpgradeshows a date and time in your production environment that reflects your seven-day deferral period.
-
Tenant settings
PingOne Advanced Identity Cloud provides you with a unified view of your tenant’s customer, workforce, and device profiles. Use the Advanced Identity Cloud admin console to manage all aspects of your tenant including realms, identities, applications, user journeys, and password policy.
You can review tenant details and access global settings for your tenant by opening the account menu in the top right of the Advanced Identity Cloud admin console, then clicking the Tenant Settings menu option.
View tenant details
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
No |
Yes |
Yes |
Yes |
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).
-
Click Tenant Settings.
-
Click Details.
-
Tenant Name
The identifier assigned to the tenant during onboarding and registration. This identifier is not configurable. -
Environment Tag
The type of tenant environment. The possible values are: -
Identity Cloud Version
The release version the environment is on. -
Region and Backup Region
The regions where your data resides.
-
Invite and view tenant administrators
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
No |
No |
No |
Yes |
Click the Admins tab on the Tenant Settings page to access options to:
Manage federated access
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
No |
No |
No |
Yes |
Click the Federation tab on the Tenant Settings page to access options to:
Access global settings
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
No |
Yes |
Yes |
Yes |
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).
-
Click Tenant Settings.
-
Click Global Settings.
-
Content Security Policy
Learn more in Secure hosted pages with Content Security Policy. -
Cookie
Learn more in Session cookie name and Manage cookie domains using the admin console. -
Cross-Origin Resource Sharing (CORS)
Learn more in Allow cross-domain requests with CORS. -
Environment Secrets and Variables
Learn more in Manage ESVs using the admin console. -
IP Addresses
View the outbound static IP addresses from your tenant. -
Log API Keys
You’ll need this to extract log data.-
Click On, then click the arrow.
-
In the Log API Keys dialog box, click + New Log API Key.
-
In the New Log API Key dialog box, provide a name, and then click Create key.
-
Identity Cloud generates an
api_key_idand anapi_key_secretfor you to copy and paste. -
Click Done.
-
-
Service Accounts
Learn more in Service accounts. -
SSL Configurations
Learn more in Manage server certificates using the admin console. -
End User UI
Learn more in Advanced Identity Cloud hosted pages.
-
Tenant administrator settings
Tenant administrator groups
There are four groups of users that can access a tenant admin console:
-
Tenant administrator: Users in this group can manage realm settings and most tenant settings except for those related to managing other tenant administrators. All tenant administrator identities get the same realm permissions, and these are not configurable.
-
Super administrator: Users in this group are tenant administrators with the following elevated permissions:
-
Invite tenant administrators.
-
Grant super administrator privileges to tenant administrators.
-
Revoke super administrator privileges from tenant administrators.
-
Enable federated access for a tenant.
-
Enforce federated access for some or all administrators in a tenant.
-
-
Tenant auditor: Users in this group are tenant administrators with read-only permissions. They can access the same settings, configuration, and data as a tenant administrator but cannot modify them.
-
Brand administrator: Users in this group are tenant administrators with permissions to only manage hosted pages settings. They can create and modify branding themes, set default themes, and apply themes to realms but don’t have access to any other tenant settings or realm settings.
The tenant provisioning process initially creates a single super administrator.
Tenant administrator sessions
Sessions in the top-level realm are subject to the following non-configurable timeout settings:
-
The maximum session time-to-live (TTL) is 120 minutes.
-
The maximum session idle timeout is 30 minutes.
When either timeout is reached, the tenant administrator must sign on again to access the Advanced Identity Cloud admin console.
| The session timeout settings for the Alpha and Bravo realms are configurable. Learn more in Session termination. |
Register to access a tenant admin console
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
Yes |
Yes |
Yes |
Yes |
If you are added as a tenant administrator to an Advanced Identity Cloud tenant, you receive an email that prompts you to complete the registration process.
-
When you receive the Complete your Ping Identity Advanced Identity Cloud registration email, click Complete Registration.
-
Perform one of the following sets of steps:
-
To use your email and password to register with Advanced Identity Cloud, on the Complete Registration page:
-
Enter your email address, first name, last name, and your password.
-
Click Next.
-
Choose a country of residency, accept Ping Identity’s privacy policy, and click Next.
-
Choose to set up 2-step verification or skip this option. The Advanced Identity Cloud dashboard should now display.
-
-
To use Microsoft Azure or AD FS to register with Advanced Identity Cloud, on the Complete Registration page:
-
Choose to continue with Microsoft Azure or AD FS.
-
Enter your credentials and log in.
-
Choose a country of residency, accept Ping Identity’s privacy policy, and click Next. The Advanced Identity Cloud dashboard should now display.
-
-
Sign on to a tenant admin console
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
Yes |
Yes |
Yes |
Yes |
You can access the sign-on page of a tenant admin console using the following URL:
https://<tenant-env-fqdn>/login/admin
For example, if your tenant environment FQDN is "openam-mycompany-ew2.id.forgerock.io", use the URL "https://openam-mycompany-ew2.id.forgerock.io/login/admin".
Upon successful authentication, you are automatically switched to the Alpha realm.
Multiple failed authentication attempts cause Advanced Identity Cloud to lock a tenant administrator’s account. Learn more about unlocking an account in Unlock a tenant administrator’s account.
Edit your own tenant administrator profile
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
Yes |
Yes |
Yes |
Yes |
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right), and click your username.
-
On your tenant administrator profile page:
-
To edit your name or email address, click Edit Personal Info.
Provide the information, then click Save. -
In the Sign-in & Security card:
-
To change your username, click Update.
-
Enter your current password, then click Next.
-
Enter your new username, then click Next.
You’ll receive an email confirming your username has been changed.
-
-
To change your password, click Reset.
-
Enter your current password, then click Next.
-
Enter your new password, then click Next.
You’ll receive an email confirming your password has been changed.
-
-
By default, 2-Step Verification is enabled.
Learn more in Manage tenant administrator 2-step verification.
-
-
To view the social identity providers you can use to log into your account, view the Social Sign-in card.
-
To view the devices that have accessed your account, view the Trusted Devices card.
-
To view the applications you have granted access to your account, view the Authorized Applications card.
-
To download your account data, in the Account Controls card, beside Download your data, click the downward pointing arrow, and click Download.
-
To delete your account data, in the Account Controls card, beside Delete account, click the downward pointing arrow, and click Delete Account.
-
Invite tenant administrators
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
No |
No |
No |
Yes |
Send invitations to people when you want to authorize them to view or manage settings for your tenant.
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).

-
Click Invite admins.
-
In the Invite Admins dialog box, enter a comma-separated list of email addresses for the people you want to authorize.
-
Grant people specific administrator access using one of the following actions:
-
Select Super Admin
-
Select Tenant Admin
-
Select one or both of Tenant Auditor and Brand Admin.
-
-
Click Send Invitations.
Advanced Identity Cloud sends an email to each address, containing instructions to set up an administrator account.
After each invitee completes the instructions in the invitation email, they become a super administrator, tenant administrator, or tenant auditor (depending on your choice in step 4).
View the tenant administrators list
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
No |
No |
No |
Yes |
From the tenant administrators list, you can invite, deactivate, or delete other tenant administrators.
-
In the tenant admin console, click the tenant name to expand the settings menu.
-
Click Tenant Settings > Admins.
-
To invite a new tenant administrator:
-
Click + Invite Admins.
-
Follow steps 3–4 in the invite tenant administrators instructions above.
-
-
To deactivate a tenant tenant administrator:
-
Find a tenant administrator with the label Active.
-
Click More (), and select Deactivate.
-
-
To delete a tenant administrator, click More (), and select Delete.
When you deactivate a tenant administrator, their status changes, but they remain on the list of tenant administrators.
When you delete a tenant administrator, their username is removed from the list of tenant administrators, and permissions are removed from their user profile. This operation cannot be undone!
-
Unlock a tenant administrator’s account
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
No |
No |
No |
Yes |
If Advanced Identity Cloud locks out one of your company’s tenant administrators due to multiple failed sign-on attempts, the account can be unlocked by a super administrator.
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right), and click your username.
-
Click Tenant Settings > Admins.
-
Find the entry for the tenant administrator who was locked out.
-
In the same row, click More () and choose Activate.
If you are the only super administrator in your organization and your account is locked, create a support case in the Ping Identity Support Portal.
Modify a tenant administrator’s group
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
No |
No |
No |
Yes |
To modify a tenant administrator’s group
-
Go to Tenant Settings > Admins.
-
Click a tenant administrator.
-
In the Group section, click Edit.
-
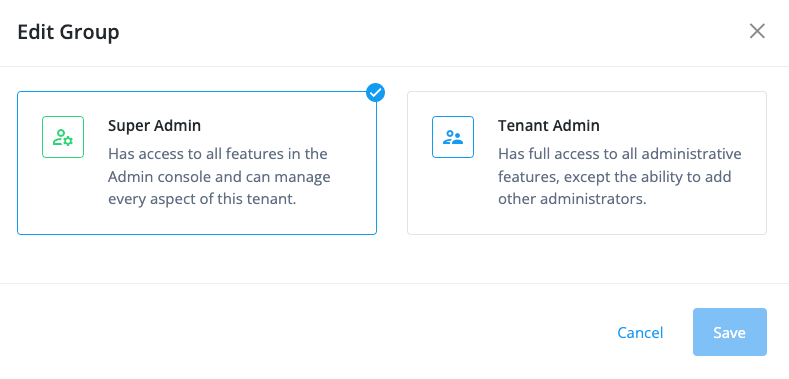
On the Edit Group page:
-
Select one of the following options:
-
To grant super administrator access, select Super Admin.
-
To grant tenant administrator access, select Tenant Admin.
-
-
Select one or both of the following options:
-
To grant tenant auditor access, select Tenant Auditor.
-
To grant brand administrator access, select Brand Admin.
-
-
-
Click Save.
Manage tenant administrator 2-step verification
| Brand administrators[3] | Tenant auditors[4] | Tenant administrators | Super administrators[5] | |
|---|---|---|---|---|
Action allowed? |
Yes |
Yes |
Yes |
Yes |
2-step verification, also known as multifactor authentication (MFA), prevents unauthorized actors from signing on as a tenant administrator by asking for a second factor of authentication.
Advanced Identity Cloud provides tenant administrators with the following second factor options:
-
ForgeRock Authenticator
Lets you register the following authenticator applications:-
PingID mobile app
-
ForgeRock Authenticator
-
Any third-party authenticator application that supports the Time-Based One-Time Password (TOTP) open standard. For example, Google Authenticator or Salesforce Authenticator.
-
-
Security Key or Touch ID
Lets you register an authenticator device such as the fingerprint scanner on your laptop or phone. Learn more in MFA: Authenticate using a device with WebAuthn.
Register for 2-step verification
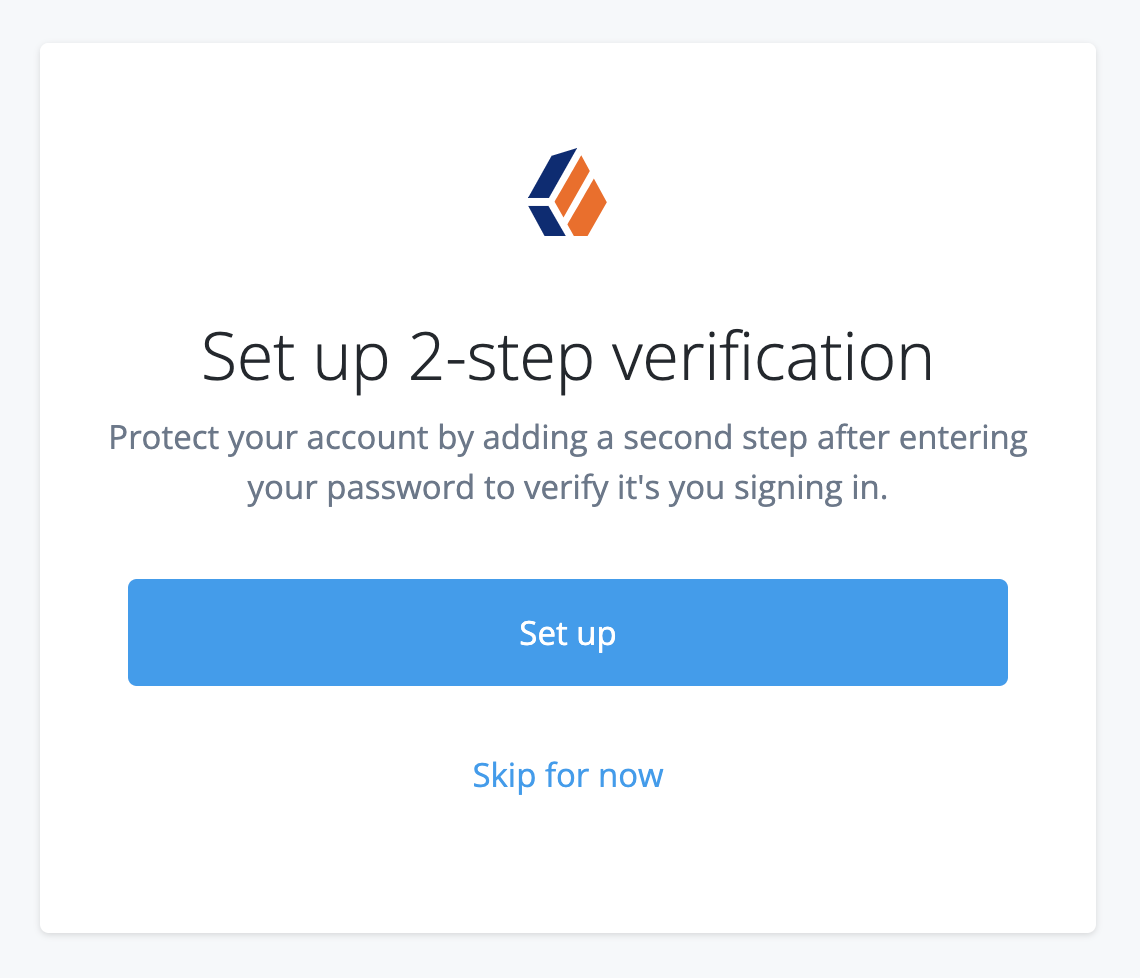
You can register for 2-step verification when you sign on to the Advanced Identity Cloud admin console for the first time:
-
Click Set up to let Advanced Identity Cloud guide you through the device registration process.
The ForgeRock Authenticator option also lets you register any TOTP compliant third-party authenticator application. -
Alternatively, click Skip for now to temporarily skip registration for 2-step verification. You’ll be asked to register again the next time you sign on.
The option to skip registration for 2-step verification is a deprecated feature, and soon 2-step verification will be mandatory in all tenants. To understand if this affects you, read the Tenant administrator mandatory 2-step verification FAQ.
Manage verification codes
During registration for 2-step verification, Identity Cloud displays 10 verification codes.
| Be sure to copy the codes and store them in a secure location. |
-
You’ll use the verfication codes as recovery codes if you cannot use your registered device to sign in.
-
You can use each verification code only once. Then, the code expires.
-
If, for some reason, you need to re-register a device, first delete your previously registered device.
Change 2-step verification options
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right) and choose your tenant administrator username.
-
On your tenant administrator profile page, find 2-Step Verification and click Change.
The 2-Step/Push Authentication page lists devices you’ve registered for MFA.
To delete a device, click its More () menu, and choose Delete.
-
When you delete a device from the list, 2-step or push authentication is disabled. You cannot undo the delete operation.
-
Once you sign off and attempt to sign back on again, you will be asked if you want to set up a second factor.
-
ESVs
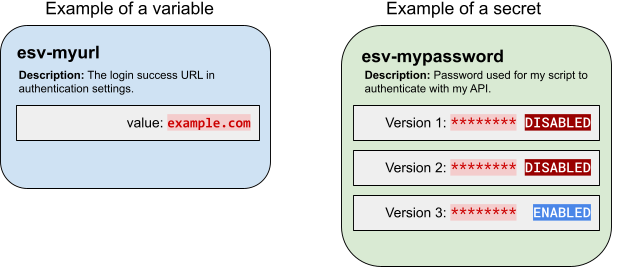
Environment secrets and variables (ESVs) let you individually configure your sandbox[1], development, UAT[2], staging, and production tenant environments in PingOne Advanced Identity Cloud.
Use variables to set values that need to be different for each tenant environment. For example, an authentication node might need one URL in your development environment, but a different URL in your production environment.
Use secrets to set values that need encrypting. The values may or may not need to be different for each tenant environment. For example, an MFA push notification node might need an authorization password to use an external SMS service.
| ESV data is held in a global service and not subject to regional data storage. You therefore must not store personally identifiable information (PII) in ESVs. You are responsible for ensuring that your use of ESVs complies with all applicable data protection laws and regulations. |
| ESVs are an Advanced Identity Cloud only feature. In particular, ESV secrets should not be confused with secrets in the self-managed PingAM or PingIDM products. |
Variables
Use ESV variables to set configuration values that need to be different for each tenant environment.
Variables are simple key-value pairs. Unlike secrets, they are not versioned. They should not contain sensitive values. The value of a variable must not exceed a maximum length of 65535 bytes (just under 64KiB).
You can reference ESV variables from configuration placeholders or scripts after you:
-
Create or update the variables using the variables APIs or the Advanced Identity Cloud admin console.
-
Restart Advanced Identity Cloud services using the restart API or by applying updates in the Advanced Identity Cloud admin console.
Other ways of restarting Advanced Identity Cloud services, such as by running a promotion, won’t load ESV changes. This makes it easier to identify issues caused by ESV changes.
The following table shows how to reference an ESV variable with the name esv-my-variable:
| Context | How to reference | Access as soon as set |
|---|---|---|
Configuration placeholders |
|
|
Scripts |
|
|
Variable expression types
You must use the expressionType parameter to set an expression type when you create an ESV variable. This
lets Advanced Identity Cloud correctly transform the value of the ESV variable to match the configuration property expression type
when substituting it into configuration.
The expression type is set when the ESV variable is created, and it cannot be modified.
Before the expressionType parameter was introduced, it was only possible to set expression types from
within configuration, using expression level syntax; for example, {"$int": "&{esv.journey.ldap.port|1389}"}.
The expressionType parameter supplements this expression level syntax and allows the ESV type
to be identified without inspecting configuration.
Make sure the expression type that you set in configuration matches the expression type that you set in the ESV expressionType parameter.
|
| Expression type | Description | Examples | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
String value (default) |
|
||||||||||||
|
JSON array |
|
||||||||||||
|
JSON object |
|
||||||||||||
|
Boolean value |
|
||||||||||||
|
Integer value |
|
||||||||||||
|
This type can transform any number value (integers, doubles, longs, and floats). |
|||||||||||||
|
Comma-separated list |
|
Existing ESVs will be migrated to use the expressionType parameter. If any existing ESVs contain
combined types, they will be split into separate ESVs by the migration process.
|
Secrets
Use ESV secrets to set configuration values that need encrypting. The values may or may not need to be different for each tenant environment.
You can reference ESV secrets from configuration placeholders or scripts after you:
-
Create or update the secrets using the secrets APIs or the Advanced Identity Cloud admin console.
-
Restart Advanced Identity Cloud services using the restart API or by applying updates in the Advanced Identity Cloud admin console.
Other ways of restarting Advanced Identity Cloud services, such as by running a promotion, won’t load ESV changes. This makes it easier to identify issues caused by ESV changes.
You can reference secrets that are signing and encryption keys by mapping them to secret labels. Secrets referenced by secret label mappings can be accessed as soon as the ESV is set; restarting Advanced Identity Cloud services is not required.
The following table shows how to reference an ESV secret with the name esv-my-secret:
| Context | How to reference | Access as soon as set |
|---|---|---|
Configuration placeholders |
|
|
Scripts |
|
|
Signing and encryption keys |
Secret versions
Instead of having a single value, ESV secrets have one or more secret versions, each containing their own value. By design, the value of a secret version cannot be read back after it has been created. The value of a secret version must not exceed a maximum length of 65535 bytes (just under 64KiB).
To create a new secret version, its value must be different from the value of the latest secret version. If you try to create a new secret version with the same value as the latest version, the existing version is retained and no changes are made.
You can enable or disable secret versions by setting their status field to ENABLED or DISABLED using the REST API or clicking the Active toggle in the admin console.
The latest version of a secret must be enabled for it to be used in your configuration.
The following rules ensure that a secret always has at least one enabled version:
-
When you create a secret, the first version of the secret is automatically created and is enabled.
-
You cannot disable the latest version of a secret.
-
You cannot delete the latest version of a secret if the previous version is disabled.
| Secret versions are an important feature of key rotation. Learn more in Rotate keys in mapped ESV secrets. |
Encoding format
You can use the encoding parameter to set an encoding format when you create an ESV secret:
| Encoding format | Description |
|---|---|
|
Use this format for secrets that are not keys, such as passwords. |
|
Use this format for asymmetric keys; for example, a public and private RSA key pair. Learn more in Generate an RSA key pair. |
|
Use this format for AES keys; for example, an AES-256 key. Learn more in Generate an AES or HMAC key. |
|
Use this format for HMAC keys; for example, a HMAC-SHA-512 key. Learn more in Generate an AES or HMAC key. |
Control access to secrets
There are 3 contexts where you can access an ESV secret:
-
From configuration placeholders; learn more in Configure placeholders to use with ESVs.
-
From scripts; learn more in Use ESVs in scripts.
-
From mapped secret labels (for signing and encryption keys); learn more in Use ESVs for signing and encryption keys.
However, if the secret contains a signing and encryption key, you may want to restrict access from
configuration placeholder and script contexts. To do this, you can use the useInPlaceholders
boolean parameter when you create the secret:
| Context | Unrestricted access | Restricted access |
|---|---|---|
|
|
|
Configuration placeholders |
|
|
Scripts |
|
|
Mapped secret labels |
|
|
| You can only set restricted access using the API. The UI currently creates secrets only with unrestricted access. |
Preconditions to delete an ESV
Before you delete an ESV, you may need to remove references to it from your environment:
-
You cannot delete an ESV if it is referenced in a configuration placeholder. You must first remove the placeholder from configuration. Learn more in Delete an ESV referenced by a configuration placeholder.
-
You cannot delete an ESV if it is referenced in a script. You must first remove any scripts that reference the ESV.
-
You cannot delete an ESV if it is referenced in an orphaned script[6]. You must first remove any orphaned scripts. You can do this by running a self-service promotion (which automatically cleans up orphaned scripts).
ESV naming
ESV API naming convention
The names of secrets and variables need to be prefixed with esv- and can only contain
alphanumeric characters, hyphens, and underscores; for example, esv-mysecret-1 or
esv-myvariable_1. The maximum length, including prefix, is 124 characters.
ESV legacy naming convention and API compatibility
Before the introduction of the ESV API endpoints, if ESVs were defined on your behalf as part of
the promotion process, they were prefixed with byos-. Advanced Identity Cloud uses compatibility behavior to
let you still use these legacy ESVs. The compatibility behavior depends on how far the legacy ESVs
were promoted through your development, staging, and production tenant environments:
- Development, staging, and production environments
-
If you promoted a legacy ESV to all your tenant environments, it will have been duplicated during the ESV migration process, so will be available in the API using the new
esv-prefix.For example,
byos-myvariable123will appear asesv-myvariable123. Scripts that reference the legacy ESV will still work; bothbyos-myvariable123andesv-myvariable123resolve to the same ESV. - Development and staging environments only
-
If you never promoted a legacy ESV to your production environment, it will have been ignored during the ESV migration process. However, you can still use the ESV API to create it in your production environment, as the compatibility behaviour looks for new ESVs that have a naming format like a legacy ESV (
byos-<hash>-<name>). So any ESVs that are created with a naming format ofesv-<hash>-<name>will also automatically create abyos-<hash>-<name>duplicate.For example, creating a new ESV called
esv-7765622105-myvariablewill automatically create another ESV calledbyos-7765622105-myvariable. Scripts that reference the legacy ESV will still work; bothbyos-7765622105-myvariableandesv-7765622105-myvariableresolve to the same ESV.
Manage ESVs using the API
You can find background information on ESVs in PingOne Advanced Identity Cloud in ESVs.
ESV API endpoints
Advanced Identity Cloud provides these API endpoints for ESVs:
| If you plan to delete an ESV using the variables or secrets API endpoints, you may first need to remove references to it from your environment. Learn more in Preconditions to delete an ESV. |
Authenticate to ESV API endpoints
To authenticate to ESV API endpoints, use an access token created with one of the following scopes:
| Scope | Description |
|---|---|
|
Read, create, update, delete, and restart access to ESV API endpoints. |
|
Read access to ESV API endpoints. |
|
Create, update, and delete access to ESV API endpoints. |
|
Restart access to ESV API endpoints. |
|
Service account access tokens granted the |
Manage ESVs using the admin console
You can find background information on ESVs in PingOne Advanced Identity Cloud in ESVs.
Create variables
-
In the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > Environment Secrets & Variables.
-
Click the Variables tab.
-
Click + Add Variable.
-
In the Add a Variable modal window, enter the following information:
Name
Enter a variable name. Learn more in ESV naming.
Variable names cannot be modified after the variable has been created. Type
Select a variable expression type.
Description
(Optional) Enter a description of the purpose of the variable.
Value
Enter a variable value.
If the variable value is JSON, you can optionally click the JSON toggle to turn on JSON validation. You can find the toggle above the top right of the field.
-
Click Save to create the variable.
Update variables
-
In the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > Environment Secrets & Variables.
-
Click the Variables tab.
-
Find a variable in the paginated list of variables, then click + Update for that variable.
-
In the Update Variable modal window:
-
At the top, you can optionally click Add a Description to update the variable description:
-
Click the Add a Description link to open a secondary modal.
-
In the Edit Variable Description secondary modal window, enter the following information:
Description
Enter a new or updated description of the purpose of the variable.
-
Click Save Description to update the variable description and close the secondary modal.
-
-
Below that, you will see the read-only Configuration Placeholder field. The placeholder value is derived from the variable name. You can optionally use the clipboard widget to copy the placeholder value.
-
Below that, you can optionally click Edit to update the variable value:
-
Click the Edit link to open a secondary modal.
-
In the Edit Variable Value secondary modal window, enter the following information:
Value
Enter a new variable value.
If the variable value is JSON, you can optionally click the JSON toggle to turn on JSON validation. You can find the toggle above the top right of the field.
-
Click Save Value to update the variable value and close the secondary modal.
-
-
Below that, you will see the read-only Type field. The variable type cannot be modified.
-
-
Click Done to close the modal.
Delete variables
| Before you delete a variable, you may need to remove references to it from your environment. Learn more in Preconditions to delete an ESV. |
-
In the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > Environment Secrets & Variables.
-
Click the Variables tab.
-
Find a variable in the paginated list of variables, then click the Delete Variable icon on the right-hand side.
-
In the Delete Variable? modal window, click Delete.
Create secrets
-
In the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > Environment Secrets & Variables.
-
Click the Secrets tab.
-
Click + Add Secret.
-
In the Add a Secret modal, choose one of the following secret types:
-
Secret: A plaintext or JSON secret such as a password or API key.
-
PEM-Encoded Secret: A key or certificate that has been formatted according to the Privacy-Enhanced Mail (PEM) standard. Use for keys, certificates, certificate chains, or certificate signing requests (CSRs).
-
Base64-Encoded HMAC Key: A Hash-based Message Authentication Code (HMAC) key that has been encoded using base64. Use for secrets needed to verify the authenticity and integrity of data. For example, when verifying OAuth 2.0 access tokens.
-
Base64-Encoded AES Key: An Advanced Encryption Standard (AES) key that has been encoded using base64. Use for secrets needed to encrypt and decrypt data. For example, when storing sensitive information like credit card numbers.
The secret’s type can’t be modified after the secret has been created. -
-
Click Next.
-
In the next modal, enter the following information:
Name
Enter a secret name. Learn more in ESV naming.
Description
(Optional) Enter a description of the purpose of the secret.
Value
Choose one of the following based on the secret type you selected earlier:
- Secret
-
Enter a secret value.
The field obscures the secret value by default. You can optionally click the visibility toggle () to view the secret value as you enter it.
If the variable value is JSON, you can optionally click the JSON toggle to turn on JSON validation. You can find the toggle above the top right of the field.
- PEM-encoded secret
-
Enter a PEM-encoded value. Ensure that the value includes the appropriate PEM headers and footers, such as
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----.For an example of how to create a PEM-encoded certificate, refer to Generate an RSA key pair.
- Base64-encoded HMAC key
-
Enter a base64-encoded HMAC key value.
For an example of how to create a base64-encoded HMAC key, refer to Generate an AES or HMAC key.
- Base64-encoded AES key
-
Enter a base64-encoded AES key value.
For an example of how to create a base64-encoded AES key, refer to Generate an AES or HMAC key.
Use in Placeholders
Select this checkbox to make the secret available to configuration placeholders and scripts. For guidance on how to use this setting, refer to Control access to secrets.
The secret’s name and Use in Placeholders selection can’t be modified after the secret has been created. -
Click Save to create the secret.
Update secrets
-
In the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > Environment Secrets & Variables.
-
Click the Secrets tab.
-
Find a secret in the paginated list of secrets, then click + Update or Updated for that secret.
-
In the Update Secret modal window:
-
At the top, you can optionally click Add a Description to update the secret description:
-
Click the Add a Description link to open a secondary modal.
-
In the Edit Secret Description secondary modal window, enter the following information:
Description
Enter a new or updated description of the purpose of the secret.
-
Click Save Description to update the secret description and close the secondary modal.
-
-
Below that, you will see the read-only Configuration Placeholder field. The placeholder value is derived from the secret name. You can optionally use the clipboard widget to copy the placeholder value.
-
Below that, you will see the secret versions interface, which shows a paginated list of secret versions for the secret:
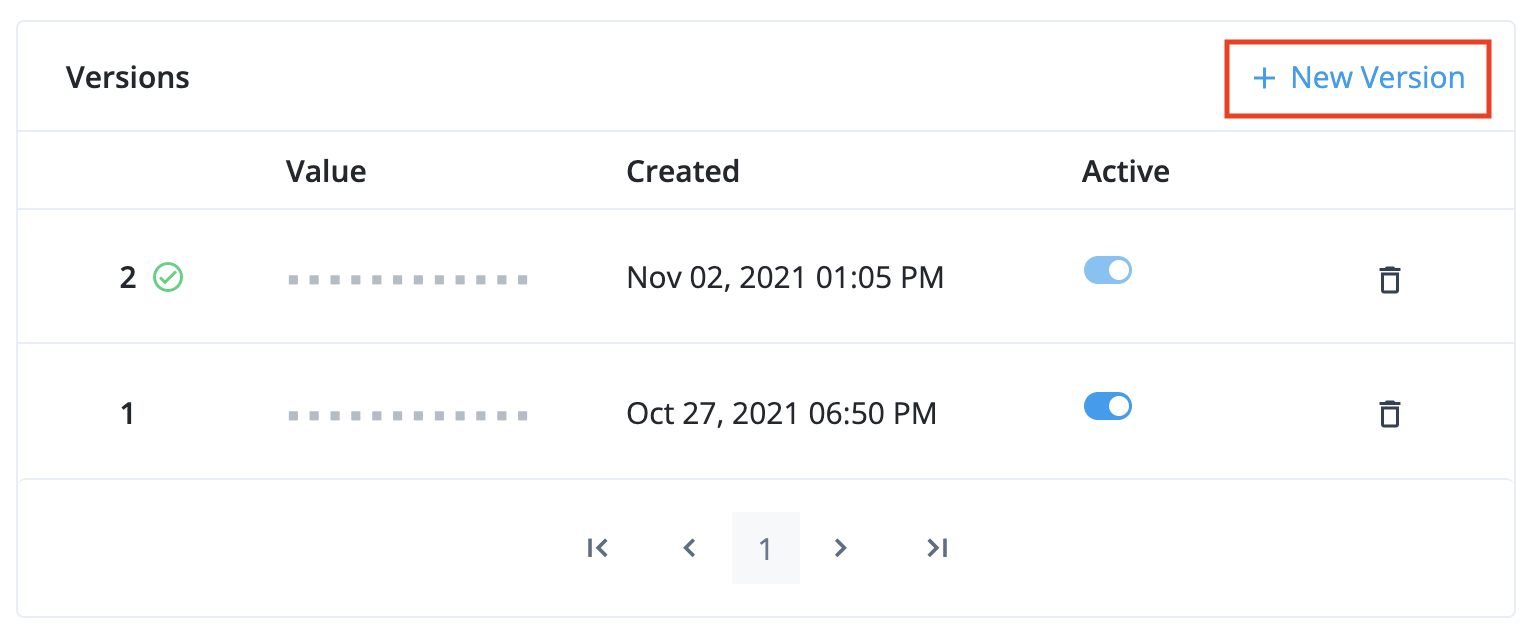
Learn more about the rules for enabling, disabling, and deleting secret versions in Secret versions. -
To add a new secret version, click + New Version to open a secondary modal.
-
In the Create a New Secret Version secondary modal window:
-
At the top, you will see the readonly Secret field, which contains the secret name.
-
Below that, enter the following information:
Value
Enter a secret value.
The field obscures the secret value by default. You can optionally click the visibility toggle () to view the secret value as you enter it.
If the variable value is JSON, you can optionally click the JSON toggle to turn on JSON validation. You can find the toggle above the top right of the field.
-
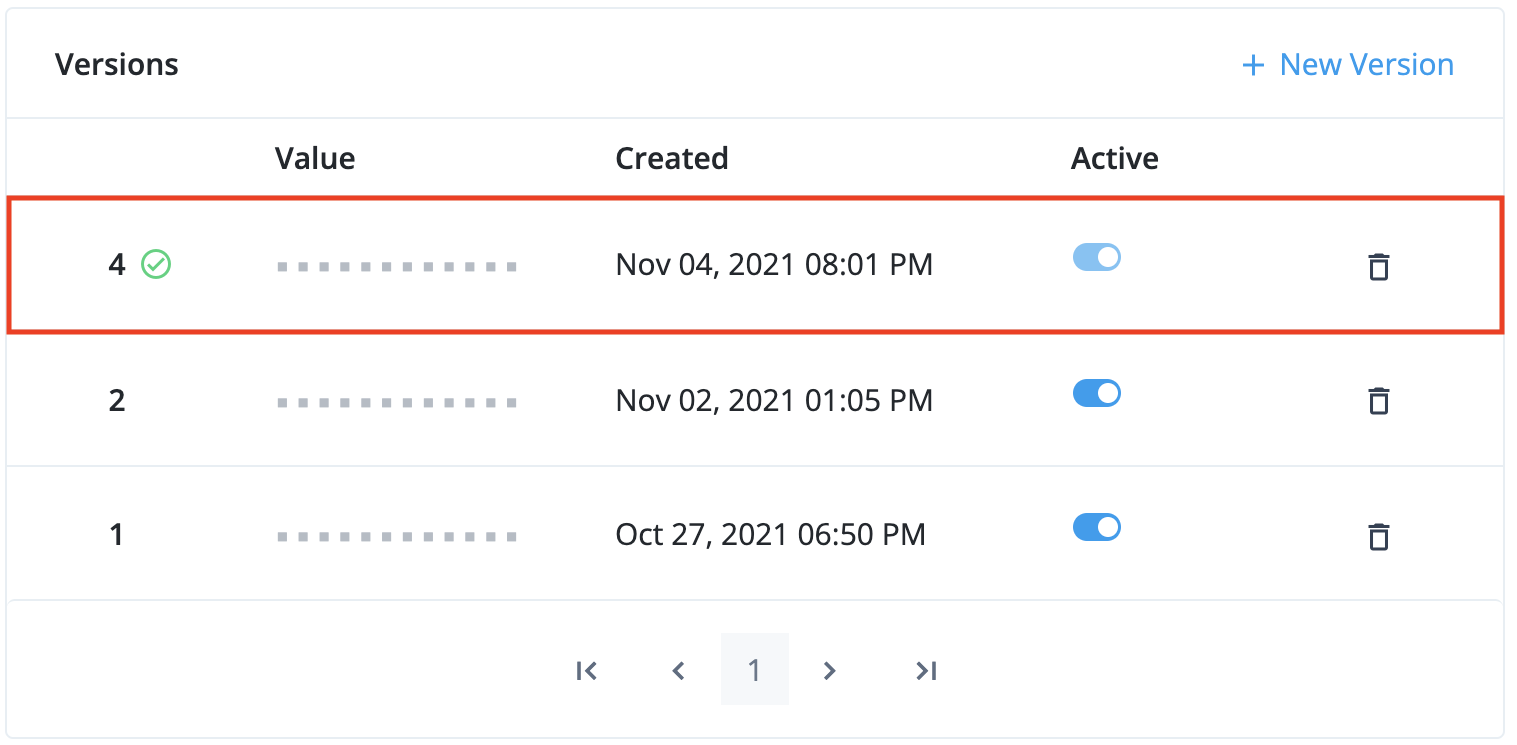
Then, click the + Add Version button to create the secret version and close the secondary modal.
-
-
The new secret version should now be visible at the top of the the secret versions interface:
-
Click Done to close the modal.
-
-
Delete secrets
| Before you delete a secret, you may need to remove references to it from your environment. Learn more in Preconditions to delete an ESV. |
-
In the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > Environment Secrets & Variables.
-
Click the Secrets tab.
-
Find a secret in the paginated list of variables, then click the Delete Secret icon on the right-hand side.
-
In the Delete Secret? modal window, click Delete.
Apply updates
When one or more ESVs have been created or updated by any of the tenant administrators, the ESV entry screen displays a banner telling you how many updates are waiting to be applied:
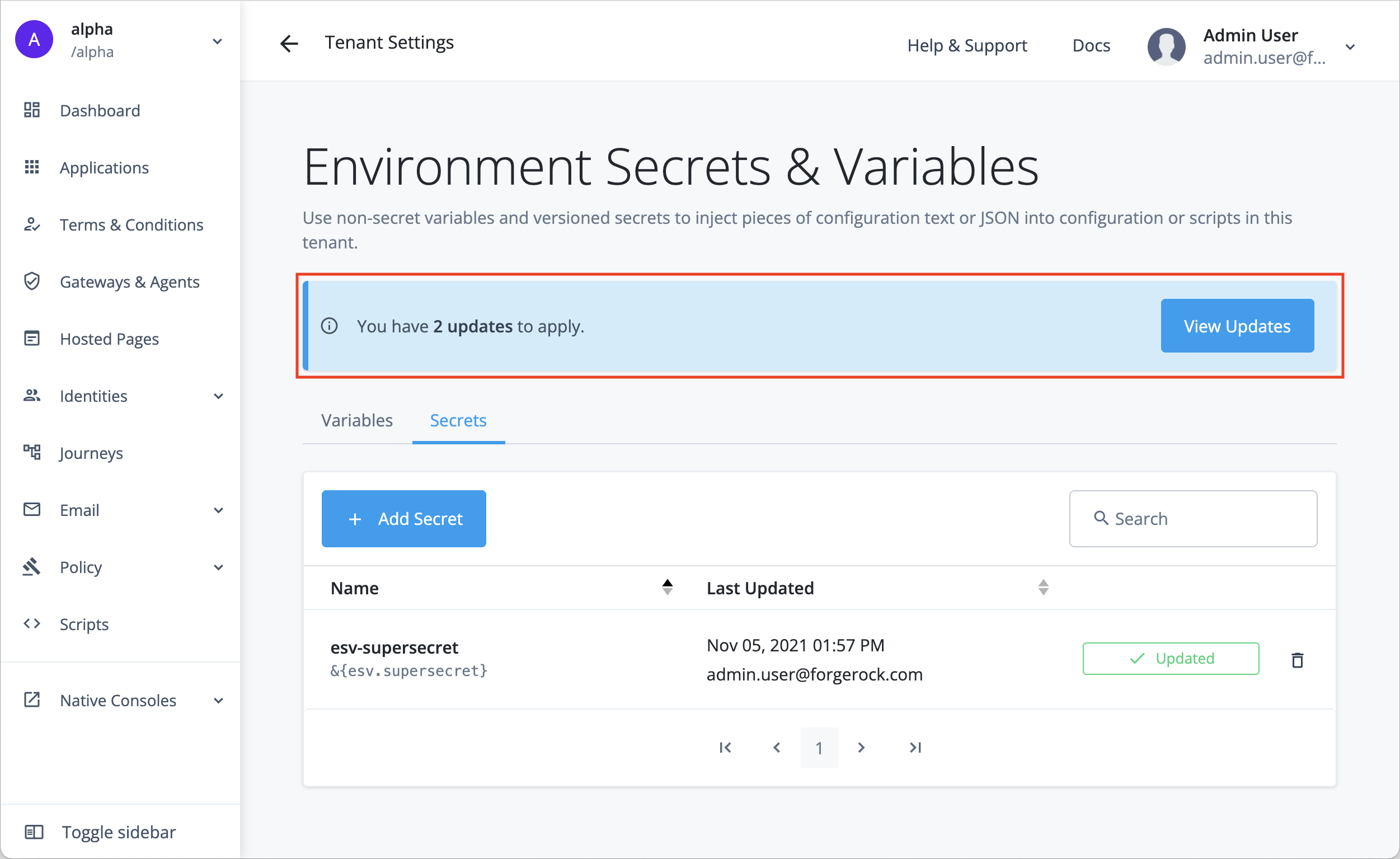
To apply any pending updates:
-
Click the View Updates button in the update banner.
-
In the Pending Updates modal, review the list of ESVs that have been updated, then click Apply n Updates.
Before you apply any updates, make sure you’ve made all the ESV changes you need. Applying the updates restarts the tenant’s services and disables ESV management in the admin console for all tenant administrators for approximately 10 minutes. -
In the Apply n Updates? confirmation modal, click Apply Now.
The tenant’s services restart and the updates are applied. While this happens, the banner changes color from blue to orange, and ESV management in the admin console is disabled for you and all other tenant administrators.
When the update is complete, the banner is no longer visible, and ESV management in the admin console is enabled again.
Use ESVs in scripts
PingOne Advanced Identity Cloud lets scripts access ESVs directly, without the need for you to restart Advanced Identity Cloud services or request a promotion first.
|
Ensure that your scripts use the full reference for ESVs; for example Referencing a non-existent ESV in a script, even within comments, can lead to system errors. Ensure that all ESVs mentioned in the script are valid and exist. Ping Identity recommends that you establish a review and testing process for all scripts. |
AM scripts
To access an ESV with the name esv-my-variable in an AM script, use:
systemEnv.getProperty("esv.my.variable")
Learn more about using the systemEnv binding in
ESVs in scripts.
IDM scripts
To access an ESV with the name esv-my-variable in an IDM script, use:
identityServer.getProperty("esv.my.variable")
Learn more about using the identityServer variable in
The identityServer variable.
Use ESVs for signing and encryption keys
PingOne Advanced Identity Cloud lets you store signing and encryption keys in ESV secrets, then map them to secret labels. Each secret label represents an authentication feature in Advanced Identity Cloud, such as signing OAuth 2.0 client access tokens.
Advanced Identity Cloud can directly access keys stored in a mapped ESV secret, there is no need to restart Advanced Identity Cloud services.
You can rotate keys stored in a mapped ESV secret by adding new secret versions to the ESV. The key in the latest secret version is used to sign new access tokens, then subsequently validate them. Keys in older secret versions (that are still enabled) are still used to validate existing access tokens.
You can also rotate SAML 2.0 certificates using ESV secrets. Learn more in Rotate SAML 2.0 certificates using ESVs
Secret labels
Secret labels (also known as secret IDs or purposes) represent authentication features in Advanced Identity Cloud that
need a signing or encryption key. For example, to sign an OAuth 2.0 client access token with an
HMAC key, you would use the secret label am.services.oauth2.stateless.signing.HMAC.
For a full list of secret labels, learn more in Secret labels.
Secret labels with fixed names
Most secret labels represent an authentication feature that requires only a single secret per
realm. These secret labels have fixed names as they require only a single mapping per realm to
override them. An example of a secret label with a fixed name is am.services.oauth2.stateless.token.encryption,
the label for the secret used to encrypt client-side access tokens issued in the realm.
Secret labels with identifiers
Some secret labels represent an authentication feature that could require multiple instances per
realm, such as OAuth 2.0 clients. The names of these secret labels contain a configurable portion,
known as the identifier, to support multiple override mappings per realm. An example of a secret
label with an identifier is am.applications.oauth2.client.<identifier>.secret.
Authentication features that support secret labels with identifiers provide a
Secret Label Identifier field that lets you define the identifier value. The value of
the identifier must be alphanumeric, can also contain periods (but not at the start or end), and
must not contain spaces. When you create an instance of the authentication feature and define a
Secret Label Identifier, Advanced Identity Cloud creates a new secret label; for example, if you
create a new OAuth 2.0 client and define the Secret Label Identifier as "salesforce",
Advanced Identity Cloud creates the secret label am.applications.oauth2.client.salesforce.secret.
You can then map the secret label to an ESV secret. If you don’t create a mapping, the authentication feature falls back to a manually entered password.
|
In the case of OAuth 2.0 clients, Advanced Identity Cloud defines four secret labels for each client. In the example above, Advanced Identity Cloud creates the following secret labels:
Continuing the example, Advanced Identity Cloud tries to find a mapping for any of the four secret labels, before falling back to a manually entered password. Learn more in Authenticate OAuth 2.0 clients. |
Map ESV secrets to secret labels
In each realm, each secret label is mapped to a default secret key. You cannot
access these default secret keys. However, you can override the default key mappings. To do this, map
a secret label to an ESV secret in a realm’s ESV secret store.
To store a key in an ESV secret, then map it to a secret label:
-
Create an ESV secret, containing the value of your new signing or encryption key:
For examples of how to generate asymmetric and symmetric keys, learn more in:
-
To use the admin console, follow the steps in Create secrets.
-
To use the API:
-
Create an access token for the appropriate realm. Learn more in Get an access token.
-
Create the ESV secret:
Show request
$ curl \ --request PUT 'https://<tenant-env-fqdn>/environment/secrets/<secret-name>' \(1) --header 'Authorization: Bearer <access-token>' \(2) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: protocol=1.0;resource=1.0' \ --data-raw '{ "encoding": "<encoding-format>",(3) "useInPlaceholders": false,(4) "valueBase64": "<base64-encoded-key>"(5) }'1 Replace <secret-name> with an appropriate secret name; for example, esv-oauth2-signing-key. Learn more in ESV naming.2 Replace <access-token> with the access token. 3 Replace <encoding-format> with one of the following: -
pemfor asymmetric keys. -
base64hmacorbase64aesfor symmetric keys.
Learn more in Encoding format.
4 Ensure that useInPlaceholdersis set tofalse. Learn more in Control access to secrets.5 Replace <base64-encoded-key> with your new signing or encryption key, encoded as a Base64 string. Show response
{ "_id": "esv-oauth2-signing-key", "activeVersion": "", "description": "", "encoding": "base64hmac", "lastChangeDate": "2022-01-28T13:25:40.515Z", "lastChangedBy": "23b299e8-90d4-406e-9431-80faf25bc7c0", "loaded": true, "loadedVersion": "", "useInPlaceholders": false } -
-
-
-
In the Advanced Identity Cloud admin console, click Native Consoles > Access Management.
-
In the AM native admin console, go to Realm > Secret Stores.
-
Click the ESV secret store, then click Mappings.
-
Click + Add Mapping, then enter the following information:
Secret Label
Select a secret label; for example
am.services.oauth2.stateless.signing.HMAC.aliases
Enter the name of the ESV secret you created in step 1, including the
esv-prefix; for example,esv-oauth2-signing-key. Then click Add.Only add a single ESV alias. The UI lets you add additional aliases, but this is a legacy mechanism for key rotation. Instead, rotate ESV keys by adding new secret versions to the ESV. Learn more in Rotate keys in mapped ESV secrets. -
Click Create.
Rotate keys in mapped ESV secrets
You can rotate keys stored in a mapped ESV secret by manipulating the enabled status of its secret versions:
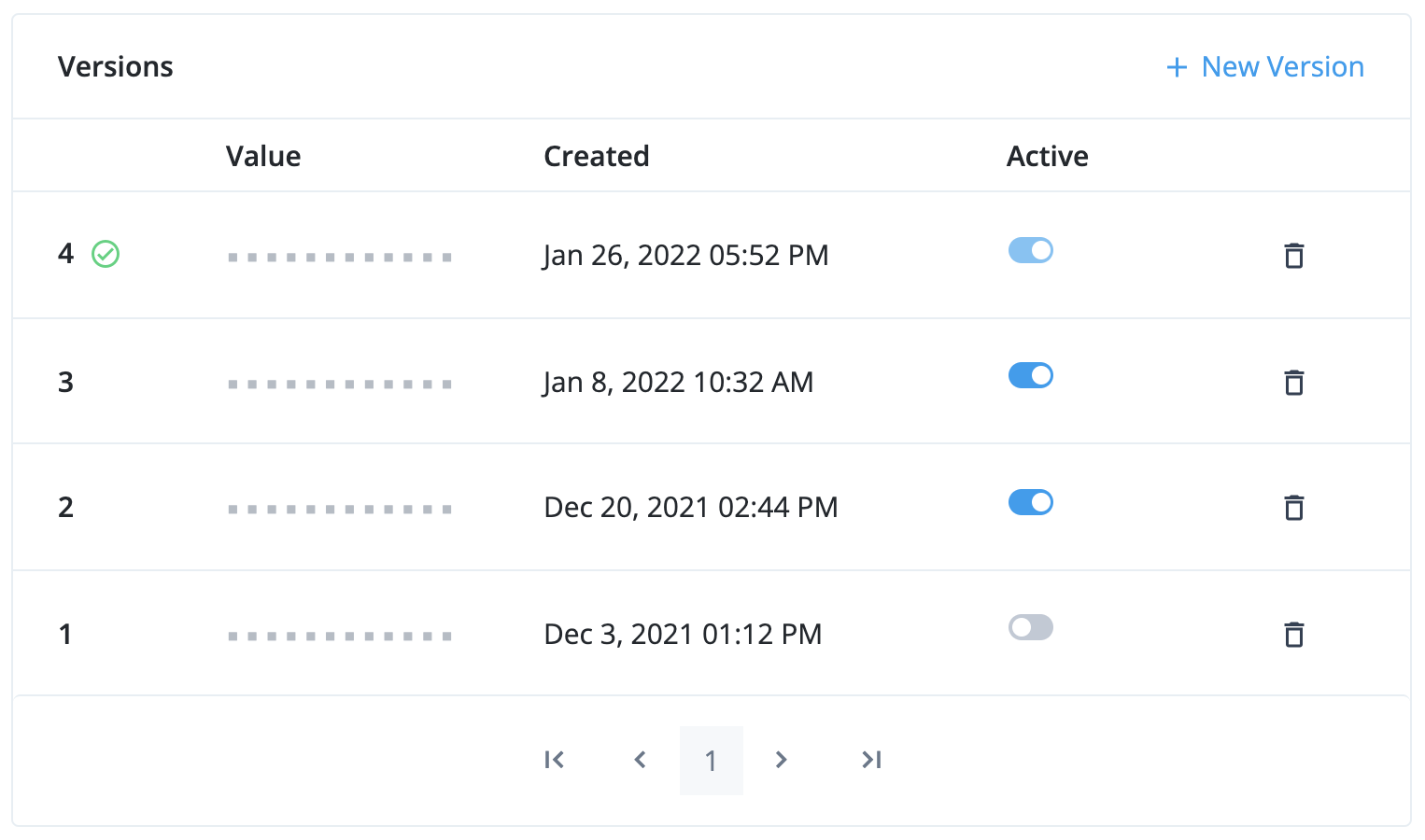
- Version 4
-
This is the latest secret version. It is enabled and cannot be disabled. It is used to sign new tokens. Existing tokens signed by this key are still valid.
- Version 3 and version 2
-
These are older secret versions. They are still enabled. Existing tokens signed by these keys are still valid.
- Version 1
-
This is an older secret version. It is disabled. Existing tokens signed by this key are not valid.
Rotate SAML 2.0 certificates using ESVs
Generate an RSA key pair
To generate an RSA key pair to use in an ESV:
-
Run the following command to generate a private key:
$ openssl genrsa -out private-key.pem -
Then, generate a public key using the private key:
$ openssl req -new -x509 -key private-key.pem -out public-key.pem -days 365 -subj /CN=idcloud -
Combine the private key and public key into a key pair:
$ cat private-key.pem public-key.pem > key-pair.pem -
If you intend to use an API request to create the ESV:
-
Encode the key pair into
base64:$ openssl enc -base64 -A -in key-pair.pem -out key-pair-base64.pemThe file
key-pair-base64.pemnow contains abase64encoded key pair value. -
You can now use this value in the
valueBase64property of the JSON body of the API request. Refer to step 1b in Map ESV secrets to secret labels for an example.
-
Generate an AES or HMAC key
To generate an AES or HMAC key to use in an ESV:
-
Run the following command:
$ head -c<bytes> /dev/urandom | openssl enc -base64 -A -out key.txt(1)1 Replace <bytes> with your required key length; for example, 512. Summary of command:
-
Generates a random number using
/dev/urandom -
Truncates the random number to your required key length using
head -
Encodes the truncated random number into
base64usingopenssl
-
-
If you intend to use an API request to create the ESV:
-
Encode the key into
base64again:$ openssl enc -base64 -A -in key.txt -out key-base64.txtThe file
key-base64.txtnow contains abase64encoded key value. -
You can now use this value in the
valueBase64property of the JSON body of the API request. Refer to step 1b in Map ESV secrets to secret labels for an example.
-
Configure placeholders to use with ESVs
PingOne Advanced Identity Cloud lets you reference ESVs from configuration placeholders. This lets you use different configuration values for the development, staging, and production environments at runtime.
For example, suppose you wanted to set a different email sender for each environment. You would
set the configuration value of the email sender to an ESV with different values in each
environment; for example, dev-mycompany@example.com (development),
staging-mycompany@example.com (staging), and mycompany@example.com (production). Then, you
would insert the ESV configuration placeholder into your configuration instead of a literal value.
| Configuration placeholders that reference an undefined ESV cause promotions to fail. Learn more in Configuration integrity checks. |
Set up configuration placeholders to reference an ESV
-
In your development environment:
-
Create the ESV using one of the following:
-
Create a variable or create a secret using the Advanced Identity Cloud admin console.
-
Create a variable or create a secret using the API (learn more in Manage ESVs using the API).
-
-
Insert the ESV configuration placeholder into your configuration. Learn more in:
-
-
In your staging environment:
-
Repeat step 1a for your staging environment. Ensure the ESV name is the same as you set up in the development environment.
-
Run a promotion to move the configuration change from your development environment to your staging environment. Learn more in:
-
-
In your production environment:
-
Repeat step 1a for your production environment. Ensure the ESV name is the same as you set up in the development environment.
-
Run a further promotion to move the configuration change from your staging environment to your production environment.
-
If you want to add more ESVs later, repeat the steps above and use a further series of promotions.
| Configuration placeholders can only be inserted into static configuration. You can find more information on what static configuration is and which areas of configuration are classified as static in the promotion FAQs. |
Update an ESV referenced by a configuration placeholder
-
Update the ESV using one of the following:
-
Update a variable or add a new secret version to a secret using the API (learn more in Manage ESVs using the API).
-
Update a variable or add a new secret version to a secret using the Advanced Identity Cloud admin console.
-
Restart Advanced Identity Cloud services
If you update an ESV referenced by a configuration placeholder, you also need to restart Advanced Identity Cloud services. This substitutes the updated secret or variable into the corresponding configuration placeholder.
-
Restart Advanced Identity Cloud services using one of the following:
-
Restart using the API (learn more in Manage ESVs using the API).
-
Apply updates using the Advanced Identity Cloud admin console.
-
Delete an ESV referenced by a configuration placeholder
-
Remove the ESV configuration placeholder from your configuration in the development environment. Refer to:
-
Run a promotion to move the configuration change from the development environment to the staging environment. Refer to:
-
Run a further promotion to move the configuration change from the staging environment to the production environment.
-
Delete the ESV in each of the development, staging, and production environments using one of the following:
-
Delete a variable or delete a secret using the Advanced Identity Cloud API (learn more in Manage ESVs using the API).
-
Delete a variable or delete a secret using the Advanced Identity Cloud admin console.
-
Define and promote an ESV
An example of using a variable would be to define a URL that a user is redirected to after logging
in. In each environment, the URL would need a different value; for example, dev-www.example.com
(development), staging-www.example.com (staging), and www.example.com (production).
To define and promote the variable:
-
Decide on a variable name; for example,
esv-myurl. Learn more in ESV naming. -
Set an ESV variable in each of the development, staging, and production environments. To do this, choose one of the following options:
-
Use the Advanced Identity Cloud admin console to create the variable, then apply the update.
-
Use the variables API endpoint to create the variable, then use the restart API endpoint to restart Identity Cloud services.
-
-
Insert the ESV configuration placeholder into your configuration in the development environment. For the example variable
esv-myurlfrom step 1, the placeholder would be called&{esv.myurl}. Refer to:Configuration placeholders can only be inserted into static configuration. Learn more in promotion FAQs. -
Run a promotion to move the configuration change from the development environment to the staging environment. Refer to:
-
Run a promotion to move the configuration change from the staging environment to the production environment.
The following illustration demonstrates the process:
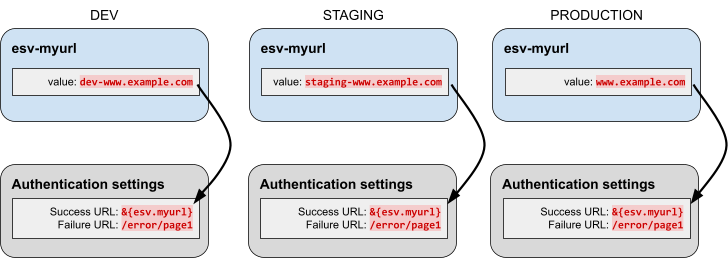
Manage configuration placeholders using the API
PingOne Advanced Identity Cloud lets you add placeholders to your configuration so you can reference the value of an ESV variable or an ESV secret instead of defining a static value.
For example, if you created an ESV variable named esv-email-provider-port, you could reference its value by adding a placeholder of {"$int" : "&{esv.email.provider.port}"} to your configuration.
To set a default value in a configuration placeholder, include it after a vertical bar. For example, the following expression sets a default email provider port of 465: {"$int" : "&{esv.email.provider.port|465}"}. If no ESV is set, the default value of 465 is used instead.
If you add a placeholder to your configuration and do not set a corresponding ESV or specify a default value, you will not be able to complete a successful promotion.
A configuration property can include a mix of static values and placeholders. For example, if you set esv-hostname to id, then &{esv.hostname}.example.com evaluates to id.example.com.
Examples
Insert ESV placeholders into tenant email provider configuration
This example shows how to configure placeholders in your tenant email provider configuration. Learn more in Email provider.
| The configuration is using an SMTP external email provider, but the same approach can be used to update an MS Graph API external email provider. |
-
Get an access token that has the
fr:idm:*scope. -
Get the email provider configuration:
Show request
$ curl \ --request GET 'https://<tenant-env-fqdn>/openidm/config/external.email' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(2)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <access-token> with the access token created in step 1. Show response
{ "_id": "external.email", "auth": { "enable": true, "password": "changeit", "username": "example.user" }, "connectiontimeout": 30000, "debug": false, "from": "\"Example User\" <example.user@example.com>", "host": "smtp.example.com", "port": 465, "smtpProperties": [], "ssl": { "enable": true }, "starttls": { "enable": false }, "threadPoolSize": 21, "timeout": 30000, "writetimeout": 30000 } -
Create a local copy of the email provider configuration from step 2, then substitute in ESV placeholders:
{ "auth": { "enable": true, "password": "&{esv.email.provider.password}", (1) "username": "&{esv.email.provider.username}" (2) }, "connectiontimeout": 30000, "debug": false, "from": "\"Example User\" <&{esv.email.provider.from.email}>", (3) "host": "&{esv.email.provider.host}", (4) "port": { "$int": "&{esv.email.provider.port}" (5) }, "smtpProperties": [], "ssl": { "enable": { "$bool": "&{esv.email.provider.use.ssl}" (6) } }, "starttls": { "enable": false }, "threadPoolSize": 21, "timeout": 30000, "writetimeout": 30000 }1 Substitution for ESV placeholder &{esv.email.provider.password}.2 Substitution for ESV placeholder &{esv.email.provider.username}.3 Substitution for ESV placeholder &{esv.email.provider.from.email}.4 Substitution for ESV placeholder &{esv.email.provider.host}5 Substitution for ESV placeholder &{esv.email.provider.port}.6 Substitution for ESV placeholder &{esv.email.provider.use.ssl}.The following table summarizes the ESVs that correspond with the above placeholders:
ESV name ESV type Expression type Example value esv-email-provider-passwordSecret
n/a
esv-email-provider-usernameVariable
String
example.user
esv-email-provider-from-emailVariable
String
example.user@example.com
esv-email-provider-hostVariable
String
smtp.example.com
esv-email-provider-portVariable
Integer
465
esv-email-provider-use-sslVariable
Boolean
true
-
Update the email provider configuration:
Show request
$ curl \ --request PUT 'https://<tenant-env-fqdn>/openidm/config/external.email' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>' \(2) --data-raw '<email-provider-configuration>'(3)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <access-token> with the access token created in step 1. 3 Replace <email-provider-configuration> with the local copy of the email-provider configuration modified in step 3. Show response
{ "_id": "external.email", "auth": { "enable": true, "password": "&{esv.email.provider.password}", "username": "&{esv.email.provider.username}" }, "connectiontimeout": 30000, "debug": false, "from": "\"Example User\" <&{esv.email.provider.from.email}>", "host": "&{esv.email.provider.host}", "port": { "$int": "&{esv.email.provider.port}" }, "smtpProperties": [], "ssl": { "enable": { "$bool": "&{esv.email.provider.use.ssl}" } }, "starttls": { "enable": false }, "threadPoolSize": 20, "timeout": 30000, "writetimeout": 30000 }
Insert ESV placeholders into CORS configuration
This example shows how to configure placeholders in your tenant CORS configuration. Learn more in Allow cross-domain requests with CORS.
-
Get an access token that has the
fr:am:*scope. -
Get the CORS configuration:
Show request
$ curl \ --request POST 'https://<tenant-env-fqdn>/am/json/global-config/services/CorsService/?_action=nextdescendents' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(2)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <access-token> with the access token created in step 1. Show response
{ "result": [ { "maxAge": 600, "exposedHeaders": [], "acceptedHeaders": [ "accept-api-version", "x-requested-with" ], "allowCredentials": true, "acceptedMethods": [ "GET", "POST", "PUT", "DELETE" ], "acceptedOrigins": [ "https://example.org", "https://example.com", "https://openam-example.forgeblocks.com" ], "enabled": true, "_id": "example-cors-config", (1) "_type": { "_id": "configuration", "name": "Cors Configuration", "collection": true } } ] }1 The ID of the CORS configuration; in this example it is example-cors-config. -
Create a local copy of the CORS configuration from step 2, then substitute in an ESV placeholder:
{ "maxAge": 600, "exposedHeaders": [], "acceptedHeaders": [ "accept-api-version", "x-requested-with" ], "allowCredentials": true, "acceptedMethods": [ "GET", "POST", "PUT", "DELETE" ], "acceptedOrigins": { "$array": "&{esv.cors.accepted.origins}" (1) }, "enabled": true, "_id": "example-cors-config", "_type": { "_id": "configuration", "name": "Cors Configuration", "collection": true } }1 Substitution for ESV placeholder &{esv.cors.accepted.origins}.The following table summarizes the ESV that corresponds with the above placeholder:
ESV name ESV type Expression type Example value esv-cors-accepted-originsVariable
Array
["https://example.org","https://example.com","https://openam-example.forgeblocks.com"]
-
Update the CORS configuration:
Show request
$ curl \ --request PUT 'https://<tenant-env-fqdn>/am/json/global-config/services/CorsService/configuration/<cors-id>' \(1)(2) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>' \(3) --data-raw '<cors-configuration>'(4)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <cors-id> with the CORS configuration ID you found in step 2. For example, example-cors-config.3 Replace <access-token> with the access token created in step 1. 4 Replace <cors-configuration> with the local copy of the CORS configuration modified in step 3. Show response
{ "_id": "example-cors-settings", "_rev": "1594160724", "maxAge": 600, "exposedHeaders": [], "acceptedHeaders": [ "accept-api-version", "x-requested-with" ], "allowCredentials": true, "acceptedMethods": [ "GET", "POST", "PUT", "DELETE" ], "acceptedOrigins": { "$array": "&{esv.cors.accepted.origins}" }, "enabled": true, "_type": { "_id": "configuration", "name": "Cors Configuration", "collection": true } }
Insert ESV placeholders into the secondary configuration of a PingOne worker service
This example shows how to configure placeholders in the secondary configuration of a PingOne worker service. Learn more in Use PingOne Protect for risk-based authentication and fraud detection.
-
Get an access token that has the
fr:am:*scope. -
Get the PingOne worker service secondary configurations:
Show request
$ curl \ --request POST 'https://<tenant-env-fqdn>/am/json/realms/root/realms/alpha/realm-config/services/pingOneWorkerService?_action=nextdescendents' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(2)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <access-token> with the access token created in step 1. Show response
{ "result": [ { "clientId": "faa04878-01ae-439c-8f22-162c2e0b03c0", "clientSecretPurpose": "pingoneworkeraic", "apiUrl": "https://api.pingone.eu/v1", "authUrl": "https://auth.pingone.eu", "environmentId": "219617c6-02d8-4428-977d-5acc6fc0543e", "_id": "PingOne Worker", (1) "_type": { "_id": "workers", "name": "PingOne Worker AIC", "collection": true } } ] }1 The ID of the PingOne worker service secondary configuration. In this example, it’s PingOne Worker AIC. -
Create a local copy of the PingOne worker service secondary configuration from step 2, then substitute in ESV placeholders:
{ "result": [ { "clientId": "&{esv.pingone.worker.client.id}", (1) "clientSecretPurpose": "pingoneworkeraic", "apiUrl": "https://api.pingone.eu/v1", "authUrl": "https://auth.pingone.eu", "environmentId": "&{esv.pingone.environment.id}", (2) "_id": "PingOne Worker", "_type": { "_id": "workers", "name": "PingOne Worker AIC", "collection": true } } ] }1 Substitution for ESV placeholder &{esv.pingone.worker.client.id}.2 Substitution for ESV placeholder &{esv.pingone.environment.id}.The following table summarizes the ESVs that correspond with the above placeholders:
ESV name ESV type Expression type Example value esv-pingone-worker-client-idVariable
String
faa04878-01ae-439c-8f22-162c2e0b03c0
esv-pingone-environment-idVariable
String
219617c6-02d8-4428-977d-5acc6fc0543e
-
Update the PingOne worker service secondary configuration:
Show request
$ curl \ --request PUT 'https://<tenant-env-fqdn>/am/json/realms/root/realms/alpha/realm-config/services/pingOneWorkerService/workers/<pingone-worker-secondary-configuration-id>' \(1)(2) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>' \(3) --data-raw '<pingone-worker-secondary-configuration>'(4)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <pingone-worker-secondary-configuration-id> with the PingOne worker service configuration ID you found in step 2, ensuring that any spaces are URL encoded. For example, PingOne%20Worker%20AIC.3 Replace <access-token> with the access token created in step 1. 4 Replace <pingone-worker-secondary-configuration> with the local copy of the CORS configuration modified in step 3. Show response
{ "clientId": "&{esv.pingone.worker.client.id}", "clientSecretPurpose": "pingoneworkeraic", "apiUrl": "https://api.pingone.eu/v1", "authUrl": "https://auth.pingone.eu", "environmentId": "&{esv.pingone.environment.id}", "_id": "PingOne Worker AIC", "_type": { "_id": "workers", "name": "PingOne Worker", "collection": true } }
Insert ESV placeholders into journey node configuration
This example shows how to configure placeholders in an LDAP decision node, but the approach can be adapted to configure placeholders in any journey node.
-
Get an access token that has the
fr:am:*scope. -
Get the configuration of the journey that contains the LDAP decision node so you can extract the ID of the node:
Show request
$ curl \ --request GET 'https://<tenant-env-fqdn>/am/json/realms/root/realms/<realm>/realm-config/authentication/authenticationtrees/trees/<journey-name>' \(1)(2)(3) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(4)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <realm> with the realm that contains the journey that contains the LDAP decision node. For example, alpha.3 Replace <journey-name> with the name of the journey that contains the LDAP decision node. For example, UpdatePassword.4 Replace <access-token> with the access token created in step 1. Show response
{ "_id": "ldapJourney", "_rev": "1341035508", "identityResource": "managed/alpha_user", "uiConfig": { "categories": "[]" }, "entryNodeId": "76e74888-73e1-46e2-aa33-5e4c8b07ccec", "nodes": { "76e74888-73e1-46e2-aa33-5e4c8b07ccec": { "x": 249, "y": 171.015625, "connections": { "outcome": "c12abfe7-ae71-42e6-a6b3-e8f4d4d05549" }, "nodeType": "PageNode", "displayName": "Page Node" }, "2082c1ad-f5ad-4b6d-aada-dd4fff4dc6f3": { (1) "x": 510, "y": 181.015625, "connections": { "CANCELLED": "e301438c-0bd0-429c-ab0c-66126501069a", "EXPIRED": "e301438c-0bd0-429c-ab0c-66126501069a", "FALSE": "e301438c-0bd0-429c-ab0c-66126501069a", "LOCKED": "e301438c-0bd0-429c-ab0c-66126501069a", "TRUE": "70e691a5-1e33-4ac3-a356-e7b6d60d92e0" }, "nodeType": "LdapDecisionNode", "displayName": "LDAP Decision" } }, "staticNodes": { "startNode": { "x": 50, "y": 250 }, "70e691a5-1e33-4ac3-a356-e7b6d60d92e0": { "x": 792, "y": 181 }, "e301438c-0bd0-429c-ab0c-66126501069a": { "x": 795, "y": 307 } }, "enabled": true }1 The ID of the LdapDecisionNodenode; in this example, it is2082c1ad-f5ad-4b6d-aada-dd4fff4dc6f3. -
Get the configuration of the LDAP decision node:
Show request
$ curl \ --request GET 'https://<tenant-env-fqdn>/am/json/realms/root/realms/<realm>/realm-config/authentication/authenticationtrees/nodes/LdapDecisionNode/<node-id>' \(1)(2)(3)(4) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(5)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <realm> with the realm that contains the journey that contains the LDAP decision node. For example, alpha.3 The node name specified is LdapDecisionNode.4 Replace <node-id> with the node ID you found in step 2. For example, 2082c1ad-f5ad-4b6d-aada-dd4fff4dc6f3.5 Replace <access-token> with the access token created in step 1. Show response
{ "_id": "2082c1ad-f5ad-4b6d-aada-dd4fff4dc6f3", "_rev": "-752122233", "searchFilterAttributes": [ "mail" ], "userProfileAttribute": "uid", "primaryServers": [ "userstore-0.userstore:1389", "userstore-1.userstore:1389", "userstore-2.userstore:1389" ], "ldapConnectionMode": "LDAP", "trustAllServerCertificates": false, "heartbeatInterval": 10, "returnUserDn": true, "searchScope": "SUBTREE", "heartbeatTimeUnit": "SECONDS", "secondaryServers": [], "ldapOperationsTimeout": 0, "userCreationAttrs": [], "minimumPasswordLength": 8, "accountSearchBaseDn": [ "o=example" ], "adminPassword": null, "adminDn": "uid=admin", "beheraEnabled": true, "_type": { "_id": "LdapDecisionNode", "name": "LDAP Decision", "collection": true }, "_outcomes": [ { "id": "TRUE", "displayName": "True" }, { "id": "FALSE", "displayName": "False" }, { "id": "LOCKED", "displayName": "Locked" }, { "id": "CANCELLED", "displayName": "Cancelled" }, { "id": "EXPIRED", "displayName": "Expired" } ] } -
Create a local copy of the node configuration from step 3, then substitute in ESV placeholders:
{ "searchFilterAttributes": [ "mail" ], "userProfileAttribute": "uid", "primaryServers" : { "$list": "&{esv.journey.ldap.primary.servers}" (1) }, "ldapConnectionMode": "LDAP", "trustAllServerCertificates": false, "heartbeatInterval": { "$int": "&{esv.journey.ldap.heartbeat.interval}" (2) }, "returnUserDn": true, "searchScope": "SUBTREE", "heartbeatTimeUnit": "&{esv.journey.ldap.heartbeat.unit}", (3) "secondaryServers": [], "ldapOperationsTimeout": 0, "userCreationAttrs": [], "minimumPasswordLength": 8, "accountSearchBaseDn": [ "o=example" ], "adminPassword": { "$string": "&{esv.journey.ldap.password}" (4) }, "adminDn": "&{esv.journey.ldap.username}", (5) "beheraEnabled": { "$bool": "&{esv.journey.ldap.behera.enabled}" (6) }, "_type": { "_id": "LdapDecisionNode", "name": "LDAP Decision", "collection": true }, "_outcomes": [ { "id": "TRUE", "displayName": "True" }, { "id": "FALSE", "displayName": "False" }, { "id": "LOCKED", "displayName": "Locked" }, { "id": "CANCELLED", "displayName": "Cancelled" }, { "id": "EXPIRED", "displayName": "Expired" } ] }1 Substitution for ESV placeholder &{esv.journey.ldap.primary.servers}.2 Substitution for ESV placeholder &{esv.journey.ldap.heartbeat.interval}.3 Substitution for ESV placeholder &{esv.journey.ldap.heartbeat.unit}.4 Substitution for ESV placeholder &{esv.journey.ldap.password}.5 Substitution for ESV placeholder &{esv.journey.ldap.username}.6 Substitution for ESV placeholder &{esv.journey.ldap.behera.enabled}.The following table summarizes the ESVs that correspond with the above placeholders:
ESV name ESV type Expression type Example value esv-journey-ldap-primary-serversVariable
List
userstore-0.userstore:1389,userstore-1.userstore:1389,userstore-2.userstore:1389
esv-journey-ldap-heartbeat-intervalVariable
Integer
10
esv-journey-ldap-heartbeat-unitVariable
String
SECONDS
esv-journey-ldap-passwordSecret
n/a
changeit
esv-journey-ldap-usernameVariable
String
uid=myadmin
esv-journey-ldap-behera-enabledVariable
Boolean
false
-
Update the configuration of the LDAP decision node:
Show request
$ curl \ --request PUT 'https://<tenant-env-fqdn>/am/json/realms/root/realms/<realm>/realm-config/authentication/authenticationtrees/nodes/LdapDecisionNode/<node-id>' \(1)(2)(3)(4) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>' \(5) --data-raw '<node-configuration>'(6)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <realm> with the realm that contains the journey that contains the LDAP decision node. For example, alpha.3 The node name specified is LdapDecisionNode.4 Replace <node-id> with the node ID you found in step 2. For example, 2082c1ad-f5ad-4b6d-aada-dd4fff4dc6f3.5 Replace <access-token> with the access token created in step 1. 6 Replace <node-configuration> with the local copy of the node configuration modified in step 4. Show response
{ "_id": "2082c1ad-f5ad-4b6d-aada-dd4fff4dc6f3", "_rev": "1359037709", "searchFilterAttributes": [ "mail" ], "userProfileAttribute": "uid", "primaryServers": { "$list": "&{esv.journey.ldap.servers}" }, "ldapConnectionMode": "LDAP", "trustAllServerCertificates": false, "heartbeatInterval": { "$int": "&{esv.journey.ldap.heartbeat.interval}" }, "returnUserDn": true, "searchScope": "SUBTREE", "heartbeatTimeUnit": "&{esv.journey.ldap.heartbeat.unit}", "secondaryServers": [], "ldapOperationsTimeout": 0, "userCreationAttrs": [], "minimumPasswordLength": 8, "accountSearchBaseDn": [ "o=example" ], "adminPassword": { "$string": "&{esv.journey.ldap.password}" }, "adminDn": "&{esv.journey.ldap.username}", "beheraEnabled": { "$bool": "&{esv.journey.ldap.behera.enabled}" }, "_type": { "_id": "LdapDecisionNode", "name": "LDAP Decision", "collection": true }, "_outcomes": [ { "id": "TRUE", "displayName": "True" }, { "id": "FALSE", "displayName": "False" }, { "id": "LOCKED", "displayName": "Locked" }, { "id": "CANCELLED", "displayName": "Cancelled" }, { "id": "EXPIRED", "displayName": "Expired" } ] }
Insert an ESV placeholder into an LDAP connector
This example shows how to configure a placeholder for an LDAP connector configured with the password for an LDAP server.
When a connector is created, Advanced Identity Cloud stores any secret or password in the connector’s configuration as an encrypted object. If the encrypted object is promoted, it cannot be unencrypted in an upper environment because the encryption keys are different in each environment. Therefore, the encrypted object must be stored in an ESV secret and replaced in the configuration with an ESV placeholder.
-
Get an access token that has the
fr:idm:*scope. -
Get the configuration of the LDAP connector:
Show request
$ curl \ --request GET 'https://<tenant-env-fqdn>/openidm/config/provisioner.openicf/<connector-id>' \(1)(2) --header 'Content-Type: application/json' \ --header 'Authorization: Bearer <access-token>'(3)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <connector-id> with the name of your connector. For example, myldapconnector.3 Replace <access-token> with the access token created in step 1. Show response
{ "_id": "provisioner.openicf/myldapconnector", "configurationProperties": { "accountObjectClasses": [ "top", "person", "organizationalPerson", "inetOrgPerson" ], "accountSearchFilter": null, "accountSynchronizationFilter": null, "accountUserNameAttributes": [ "uid" ], "attributesToSynchronize": [], "baseContexts": [ "ou=identities" ], "baseContextsToSynchronize": [ "ou=identities" ], "blockSize": "100", "changeLogBlockSize": "100", "changeNumberAttribute": "changeNumber", "credentials": { (1) "$crypto": { "type": "x-simple-encryption", "value": { "cipher": "AES/CBC/PKCS5Padding", "data": "hfJKTFhe+c6wozK/OEKMEw==", "iv": "G/1aF6oKS5/bzlkEzsmK0A==", "keySize": 16, "mac": "QSp/OAIEPWp9vkDhyZtK5Q==", "purpose": "idm.config.encryption", "salt": "6gSguT4PDQdKsPOrcItx7Q==", "stableId": "openidm-sym-default" } } (2) }, "failover": [], "filterWithOrInsteadOfAnd": false, "groupMemberAttribute": "uniqueMember", "groupObjectClasses": [], "groupSearchFilter": null, ... }, ... }1 Opening bracket of the encrypted object containing the connector’s password. 2 Closing bracket of the encrypted object containing the connector’s password. -
Create a local copy of the connector configuration from step 2, then substitute in an ESV placeholder for the encrypted object:
{ "_id": "provisioner.openicf/myldapconnector", "configurationProperties": { "accountObjectClasses": [ "top", "person", "organizationalPerson", "inetOrgPerson" ], "accountSearchFilter": null, "accountSynchronizationFilter": null, "accountUserNameAttributes": [ "uid" ], "attributesToSynchronize": [], "baseContexts": [ "ou=identities" ], "baseContextsToSynchronize": [ "ou=identities" ], "blockSize": "100", "changeLogBlockSize": "100", "changeNumberAttribute": "changeNumber", "credentials": "&{esv.connector.ldap.password}", (1) "failover": [], "filterWithOrInsteadOfAnd": false, "groupMemberAttribute": "uniqueMember", "groupObjectClasses": [], "groupSearchFilter": null, ... }, ... }1 Substitution of ESV placeholder &{esv.connector.ldap.password}for the encrypted object.The following table summarizes the ESV that corresponds with the above placeholder and contains the encrypted object from the connector configuration returned in step 2:
ESV name ESV type Expression type Example value esv-connector-ldap-passwordSecret
n/a
{"$crypto": {"type": "x-simple-encryption", "value": {"cipher": "AES/CBC/PKCS5Padding", "data": "hfJKTFhe+c6wozK/OEKMEw==", "iv": "G/1aF6oKS5/bzlkEzsmK0A==", "keySize": 16, "mac": "QSp/OAIEPWp9vkDhyZtK5Q==", "purpose": "idm.config.encryption", "salt": "6gSguT4PDQdKsPOrcItx7Q==", "stableId": "openidm-sym-default"}}}
-
Update the connector configuration:
Show request
$ curl \ --request PUT 'https://<tenant-env-fqdn>/openidm/config/provisioner.openicf/<connector-id>' \(1)(2) --header 'Content-Type: application/json' \ --header 'Authorization: Bearer <access-token>'\(3) --data-raw '<connector-configuration>'(4)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <connector-id> with the name of your connector. For example, myldapconnector.3 Replace <access-token> with the access token created in step 1. 4 Replace <connector-configuration> with the local copy of the connector configuration modified in step 3. Show response
{ "_id": "provisioner.openicf/myldapconnector", "configurationProperties": { "accountObjectClasses": [ "top", "person", "organizationalPerson", "inetOrgPerson" ], "accountSearchFilter": null, "accountSynchronizationFilter": null, "accountUserNameAttributes": [ "uid" ], "attributesToSynchronize": [], "baseContexts": [ "ou=identities" ], "baseContextsToSynchronize": [ "ou=identities" ], "blockSize": "100", "changeLogBlockSize": "100", "changeNumberAttribute": "changeNumber", "credentials": "&{esv.connector.ldap.password}", "failover": [], "filterWithOrInsteadOfAnd": false, "groupMemberAttribute": "uniqueMember", "groupObjectClasses": [], "groupSearchFilter": null, ... }, ... }
Manage configuration placeholders using the admin console
PingOne Advanced Identity Cloud lets you add placeholders to your configuration so you can reference the value of an ESV variable or an ESV secret instead of defining a static value.
For example, if you created an ESV variable named esv-ldap-minimum-password-length, you
could reference its value in a journey by adding the placeholder &{esv.ldap.minimum.password.length}
to the Minimum Password Length field of an LDAP Decision node.
Admin console support for configuration placeholders
The Advanced Identity Cloud admin console has full support for viewing and removing placeholders. However, it supports adding placeholders only to these features:
-
Journeys
-
Federation IdPs for tenant administrators
To add placeholders to configuration outside these areas, use the API. Learn more in Manage configuration placeholders using the API.
| In some areas of the Advanced Identity Cloud admin console, entering a placeholder into a field makes the field read-only, and creates the impression that you can add a placeholder to the field. However, this isn’t valid and won’t work as expected. |
Add a configuration placeholder to a field
| If you create a new ESV in a separate tab or window, you may also need to reload the page you are working on to display the new ESV in a field’s variable list. |
-
(Optional) Create a new ESV by following steps 1a and 1b in Set up configuration placeholders to reference an ESV.
-
In the Advanced Identity Cloud admin console, identify the insertable placeholder field to which you want to add a placeholder.
-
Click on the field’s token icon ().
-
The UI displays a list of ESVs with a compatible variable expression type for the field; for example, for a field that expects a boolean value, the list contains only ESV variables with a
boolexpression type:
The UI combines ESV secrets and ESV variables of expression type stringinto one list. This combined list displays for password fields and for text fields that expect a string value. -
(Optional) To filter the ESVs displayed in the list, enter a value in the field with a search icon ().
-
Select an ESV from the list.
-
The UI displays the selected placeholder and changes the field to a read-only placeholder field.
-
(Optional) To edit the placeholder:
-
Click on the field’s clear icon ().
-
The UI reverts the field to an insertable placeholder field.
-
Repeat steps 2–7 above.
-
-
Save the page that contains the field. This adds the placeholder to your configuration.
Delete a configuration placeholder for a field
-
In the Advanced Identity Cloud admin console, identify the read-only placeholder field for which you want to delete a placeholder.
-
Click on the field’s clear icon ().
-
The UI reverts the field to an insertable placeholder field.
-
(Optional) Set a new regular input value for the field.
-
Save the page that contains the field. This removes the placeholder from your configuration and replaces it with a regular input value.
Placeholder field states
Insertable
Fields into which you can add a placeholder are insertable. If a field is insertable, a token icon () displays when you hover your cursor over the field or when you focus on the field:
-
For text, password, select, and tag fields, the icon is displayed inside the field on the right-hand side:
-
For checkboxes, the icon is displayed outside the field to the right-hand side:

-
For key-value fields, the icon is displayed to the right-hand side of the key-value field name:

Until you add a configuration placeholder, insertable placeholder fields behave the same as regular input fields.
Read-only
When you add a configuration placeholder to a placeholder field, it becomes read-only:
-
For text, password, select, and tag fields, the placeholder displays inside the field, the field is grayed out, and the field value cannot be edited. The only part of the field that is interactive is the field’s clear icon () on the right-hand side:
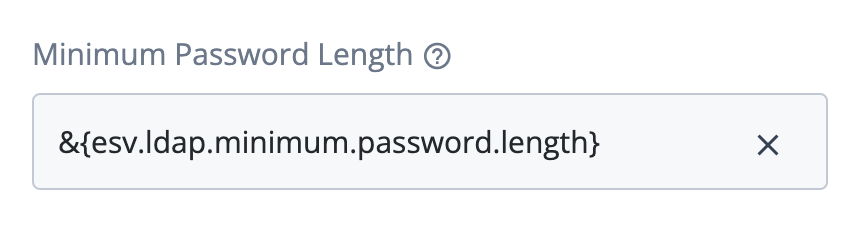
-
For checkboxes, the checkbox is replaced with a read-only text field below the checkbox label:
-
For key-value fields, the field name, controls, and summary are replaced entirely with a read-only text field. The read-only text field includes the key-value field name above the placeholder:
Key-value field conversion example
An example of a key-value field is the Page Header field in the Page Node.
The following screenshot shows the Page Header field populated with en and fr keys containing locale-specific messages:
To convert this data to an ESV, use the object type ESV variable and set the value as a JSON object:
{
"en":"Sign in",
"fr":"Se connecter"
}Introduction to self-service promotions
PingOne Advanced Identity Cloud lets you run self-service promotions to move static configuration between a sequential pair of tenant environments, either from the development environment to the staging environment (staging promotion), or from the staging environment to the production environment (production promotion).
| Non-sequential promotions (between the development environment and the production environment) are not supported. |
If you promote configuration that accidentally causes instability or errors, Advanced Identity Cloud lets you run a self-service rollback to restore an upper environment to its previous configuration.
You can run a promotion or a rollback using the following options:
-
Manage self-service promotions using the API (promotion and rollback)
-
Manage self-service promotions using the admin console (promotion only)
The Advanced Identity Cloud configuration model
The following video summarizes the concepts of the Advanced Identity Cloud configuration model:
Static and dynamic configuration
Learn about the difference between static and dynamic configuration in these FAQs:
Lower and upper environments
In a sequential pair of environments, we refer to the lower environment (the configuration source), and the upper environment (the configuration destination). The terms lower environment and upper environment therefore refer to different environments, depending on which environment you are promoting to.
Standard promotion group of environments
A standard promotion group of environments consists of a development, staging, and production environment. If you have any sandbox environments, they aren’t included in this standard promotion group because it’s not possible to promote to or from a sandbox environment.
For a standard promotion group of development, staging, and production tenant environments, the lower and upper environments are:
| Development environment |
Staging environment |
Production environment |
|
|---|---|---|---|
Staging promotion |
lower |
upper |
|
Production promotion |
lower |
upper |
Key:
-
lower = lower environment (configuration source)
-
upper = upper environment (configuration destination)
Additional UAT environments
If you add any UAT environments to your promotion group of environments, they are inserted into the promotion process before the staging environment:
-
If you add one UAT environment, the revised lower and upper environments are:
Development
environmentUAT
environmentStaging
environmentProduction
environmentUAT promotion
lower
upper
Staging promotion
lower
upper
Production promotion
lower
upper
-
If you add a second UAT environment, the revised lower and upper environments are:
Development
environmentUAT
environmentUAT2
environmentStaging
environmentProduction
environmentUAT promotion
lower
upper
UAT2 promotion
lower
upper
Staging promotion
lower
upper
Production promotion
lower
upper
-
The lower and upper environments are revised in the same way for each additional UAT environment you add.
Environment locking
|
Locking an environment prevents configuration changes that could disrupt a promotion or a rollback; however, all authentication flows continue to work as normal. |
Before you run a promotion or a rollback, you must lock the lower and upper environments. This prevents anyone else from locking either of those environments, which ensures only one promotion or rollback can be run at the same time in the same set of development, staging, and production environments.
Locking the lower and upper environments also blocks access to the ESV API in those environments. This prevents anyone else from accidentally disrupting a promotion or rollback by manipulating ESV configuration values. If the lower environment is also the development environment, then most Advanced Identity Cloud API endpoints are also restricted.
When a promotion or a rollback is complete, you must unlock the lower and upper environments to return the environments back to full functionality.
Configuration integrity checks
When you run a promotion or a rollback, Advanced Identity Cloud performs integrity checks on your static configuration to protect the stability of the upper environment.
Integrity check for missing ESVs
| Promotion | Rollback | |
|---|---|---|
Checked? |
Yes |
Yes |
This integrity check looks for ESVs referenced in your static configuration, but not set in the upper environment.
Advanced Identity Cloud runs this integrity check on the whole configuration, not just configuration changes.
Integrity check for encrypted secrets
| Promotion | Rollback | |
|---|---|---|
Checked? |
Yes |
No |
This integrity check looks for encrypted secrets embedded directly in your static configuration. It is best practice to store encrypted secrets in an ESV secret and update your configuration to reference the ESV secret instead.
Advanced Identity Cloud runs this integrity check on the whole configuration, not just configuration changes.
Manage self-service promotions using the API
You can find background information on self-service promotions in PingOne Advanced Identity Cloud in Introduction to self-service promotions.
Lower and upper environments
Before you run any promotions API requests, you must know which tenant environment is the lower environment and which is the upper environment. Learn more in Lower and upper environments.
The API uses a pull model to promote configuration, so most API commands must be run against the upper environment.
Reports
| Report type | Description |
|---|---|
Dry-run promotion report |
A promotion report generated after a dry-run promotion. It provides a full list of configuration changes that will be promoted between a lower and an upper environment. |
Promotion report |
A promotion report generated after a promotion. It provides a full list of configuration changes that were promoted between a lower and an upper environment. |
Provisional rollback report |
A rollback report generated before rollback. It provides a full list of configuration changes that will be reverted from the upper environment. |
Rollback report |
A rollback report generated after a rollback. It provides a full list of configuration changes that were reverted from the upper environment. |
Promotions API endpoints
Advanced Identity Cloud provides these API endpoints for promotions:
To authenticate to promotions API endpoints, use an
access token created with the
fr:idc:promotion:* scope.
The following diagram summarizes how promotions API commands are used to run a promotion. Learn more in Run a promotion.
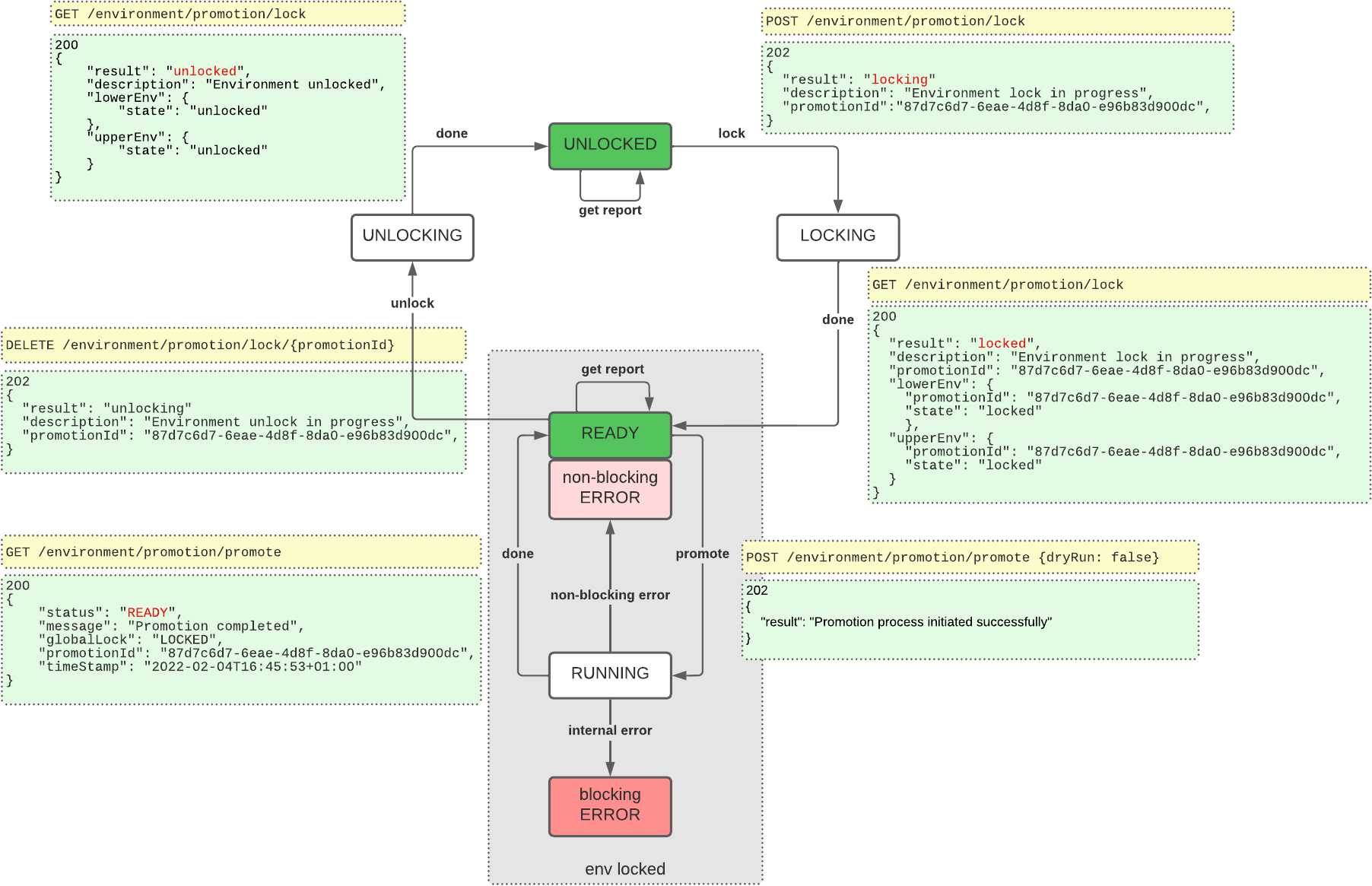
Monitor progress when you lock or unlock environments, start a promotion, or start a rollback
When you use API commands to lock environments, unlock environments, start a promotion, or start a rollback, you trigger asynchronous processes in your environments. You can monitor the progress of these asynchronous processes by checking their state or status until they have completed. You do this by running further API commands and analyzing their responses.
Check the lock state
To check the lock state during the lock environments or unlock environments processes, use the /environment/promotion/lock/state endpoint:
curl \
--request GET 'https://<tenant-env-upper-fqdn>/environment/promotion/lock/state' \(1)
--header 'Content-Type: application/json' \
--header 'Accept-API-Version: resource=1.0' \
--header 'Authorization: Bearer <access-token>'(2)| 1 | Replace <tenant-env-upper-fqdn> with the FQDN of the upper environment. |
| 2 | Replace <access-token> with an access token for the upper environment (learn more in
Get an access token). |
Learn how to analyze the response from this endpoint in Lock environments.
Check the promotion status
To check the promotion status after you start a promotion, use the /environment/promotion/promote endpoint:
curl \
--request GET 'https://<tenant-env-upper-fqdn>/environment/promotion/promote' \(1)
--header 'Content-Type: application/json' \
--header 'Accept-API-Version: resource=1.0' \
--header 'Authorization: Bearer <access-token>'(2)| 1 | Replace <tenant-env-upper-fqdn> with the FQDN of the upper environment. |
| 2 | Replace <access-token> with an access token for the upper environment (learn more in
Get an access token). |
Learn how to analyze the response from this endpoint during a promotion in Run a promotion.
Check the rollback status
To check the rollback status after you start a rollback, use the /environment/promotion/promote endpoint, as described in
Check the promotion status.
Learn how to analyze the response from this endpoint during a rollback in Run a rollback.
Lock environments
Before you run a promotion or a rollback, you must lock the upper and lower environments.
Task 1: Check that the environments are unlocked
-
Check the lock state to confirm that both environments are unlocked. This is indicated in the response when
resulthas a value ofunlocked:{ "description": "Environment unlocked", "lowerEnv": { "state": "unlocked" }, "result": "unlocked", "upperEnv": { "state": "unlocked" } }
Task 2: Lock the environments
|
Locking an environment prevents configuration changes that could disrupt a promotion or a rollback; however, all authentication flows continue to work as normal. |
-
To lock the environments, use the
/environment/promotion/lockendpoint to create a lock request:curl \ --request POST 'https://<tenant-env-upper-fqdn>/environment/promotion/lock' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(2)1 Replace <tenant-env-upper-fqdn>with the FQDN of the upper environment.2 Replace <access-token>with an access token for the upper environment (learn more in Get an access token).-
If the lock request is successful, the response
resulthas a value oflocking:{ "description": "Environment lock in progress", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "result": "locking" } -
If the lock request is rejected, the response
codehas a value of409.-
In the example below the lock request was rejected because a lock already exists:
{ "code": 409, "message": "Environment is already locked for promotion 791eb03a-7ec1-42ae-ae84-ed142cf52688" }To resolve this:
-
If another member of your team is already running a promotion:
-
Wait until the team member has completed their promotion and has released the lock.
-
Start the promotion steps again.
-
-
If the lock has accidentally been left in place, and no one else is running a promotion:
-
Unlock the environments using the promotion ID stated in the error message.
-
Start the promotion steps again.
-
-
-
In the example below the lock request was rejected because Ping Identity locked the environment:
{ "code": 409, "message": "Environment is locked by {forgerock_name} for maintenance. Retry later." }Ping Identity typically locks an environment so that Ping Identity support engineers can investigate an issue or perform maintenance. To resolve this, wait until Ping Identity releases the lock.
-
-
If the lock request causes an unexpected error, the response
codehas a value of500.{ "code": 500, "message": "<internal-error-message>" }To resolve this, open a support case with Ping Identity support. Learn more in Resolve environment errors that are preventing a promotion or a rollback.
-
-
Check the lock state to confirm that the lock is in progress. This is indicated in the response when
resulthas a value oflocking:{ "description": "Environment lock in progress", "lowerEnv": { "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "state": "locking" }, "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "result": "locking", "upperEnv": { "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "state": "locking" } } -
Check the lock state as many times as you need until both environments are locked. This is indicated in the response when
resulthas a value oflocked:{ "description": "Environment locked", "lowerEnv": { "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "state": "locked" }, "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "result": "locked", "upperEnv": { "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "state": "locked" } }
Run a promotion
Task 1: (Optional) Check how a promotion will affect deferred release status
If you’ve opted in to release deferral and intend to promote to your production environment, first check whether a deferred release is currently active. This ensures you understand how your promotion aligns with the seven-day deferral period, and lets you plan the upgrade at a time that works best for your organization.
To understand how a promotion will affect an active deferred release, use the /environment/promotion/info endpoint.
-
Run the following command against the production environment:
curl \ --request GET 'https://<tenant-env-upper-fqdn>/environment/promotion/info' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(2)1 Replace <tenant-env-upper-fqdn>with the FQDN of the upper environment.2 Replace <access-token>with an access token for the upper environment (learn more in Get an access token).Example response
{ "activePromotionId": "ba594bbe-a589-4676-80a4-42975a56f5b6", "promotionWouldTriggerReleaseUpgrade": true } -
Analyze the response to check if a promotion will trigger a release upgrade.
-
If
promotionWouldTriggerReleaseUpgradehas a value offalse, a promotion won’t trigger a release upgrade. You can proceed with the self-service promotion and move to the next task. -
If
promotionWouldTriggerReleaseUpgradehas a value oftrue, a promotion will trigger a release upgrade. You have two options:-
If your organization has completed its evaluation of the deferred release and is ready to promote it, you can proceed with the self-service promotion and move to the next task.
-
Otherwise, raise a support case in the Ping Identity Support Portal so that Ping Identity support can run the promotion on your behalf without triggering a release upgrade. Learn more in Support-assisted deployment options.
-
-
Task 2: Lock the environments
Follow the instructions in Lock environments.
Task 3: Check that a promotion isn’t already running
Check the promotion status to confirm that a promotion is not already running. This is
indicated in the response when status has a value of READY:
{
"status": "READY",
"message": "Environment ready for promotion",
"blockingError": false,
"globalLock": "LOCKED",
"promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740",
"timeStamp": "2024-06-12T17:12:32Z",
"type": "promotion"
}Task 4: Run a dry-run promotion
When you’re ready to run a promotion, perform a dry-run promotion first. This lets you identify potential problems with missing ESVs or encrypted secrets without promoting any changes to the upper environment.
To run a dry-run promotion, follow the steps in Task 5: Run the promotion, but in
step 1, set the dryRun flag to true:
--data-raw '{
"dryRun": true
}'|
If there are any scripts awaiting promotion, ensure that they do not emit any personally identifiable information (PII) of your end users into Advanced Identity Cloud logs. Ping Identity recommends that you establish a review and testing process for all scripts to prevent PII leaking out of your Advanced Identity Cloud tenant environments. |
Task 5: Run the promotion
-
To run a promotion, use the
/environment/promotion/promoteendpoint:curl \ --request POST 'https://<tenant-env-upper-fqdn>/environment/promotion/promote' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>' \(2) --data-raw '{ "dryRun": false (3) }'1 Replace <tenant-env-upper-fqdn>with the FQDN of the upper environment.2 Replace <access-token>with an access token for the upper environment (learn more in Get an access token).3 The dryRunflag is set tofalsein the request body.{ "result": "Promotion process initiated successfully" } -
Check the promotion status to confirm that the promotion is in progress. This is indicated in the response when
statushas a value ofRUNNING:{ "status": "RUNNING", "message": "Prepare config", "blockingError": false, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:14:13Z", "type": "promotion" } -
Check the promotion status as many times as you need until the promotion is complete.
-
If the promotion is still running, the response
statushas a value ofRUNNING:{ "status": "RUNNING", "message": "Promote configuration", "blockingError": false, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:15:51Z", "type": "promotion" } -
If the promotion failed but is recoverable, the response
statushas a value ofERROR, and the responseblockingErrorhas a value offalse.-
In the example below, the promotion failed an integrity check for missing ESVs.
{ "status": "ERROR", "message": "Missing ESVs", "blockingError": false, "missingESVs": [ "email.from" ], "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:19:31Z", "type": "promotion" }To resolve this:
-
For each ESV in
missingESVs, add an ESV into the upper environment. -
Start the promotion steps again.
-
In the example below, the promotion failed an integrity check for encrypted secrets.
{ "status": "ERROR", "message": "Found encrypted values in the AM/IDM configuration", "blockingError": false, "globalLock": "LOCKED", "encryptedSecrets": [ "* am/services/realm/root-alpha/persistentcookiedecisionnode/1.0/organizationconfig/default/dd35c42f-177e-4633-9107-373214858fa7.json:10" ], "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:19:31Z", "type": "promotion" }To resolve this:
-
If the encrypted secret is in your configuration by accident:
-
Create an ESV secret containing the encrypted secret in each of the development, staging, and production environments.
-
Update your configuration to reference the new ESV secret.
-
Start the promotion steps again.
-
If the encrypted secret is in your configuration deliberately, you can bypass this check:
-
Follow the steps in Task 5: Run the promotion, but in step 1, set the
ignoreEncryptedSecretsflag totrue:--data-raw '{ "dryRun": false, "ignoreEncryptedSecrets": true }'
-
-
-
-
If the promotion failed and is not recoverable, the response
statushas a value ofERROR, and the responseblockingErrorhas a value oftrue:{ "status": "ERROR", "message": "Failed to promote config", "blockingError": true, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:19:31Z", "type": "promotion" }If you run the promotion again after a blocking error, the following response displays:
{ "code": 409, "message": "Environment is blocked from a previous failed promotion or rollback" }To resolve this, open a support case with Ping Identity support. Learn more in Resolve environment errors that are preventing a promotion or a rollback.
-
If Advanced Identity Cloud services are restarting, the response
statushas a value ofRUNNING, and the responsemessagehas a value ofWaiting for workloads to restart:{ "status": "RUNNING", "message": "Waiting for workloads to restart", "blockingError": false, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:32:06Z", "type": "promotion" }This part of the promotion can take several minutes. It does not apply to dry-run promotions, where Advanced Identity Cloud services do not need to be restarted.
-
If the promotion is complete, the response
statushas a value ofREADY, and the responsemessagehas a value ofPromotion completed:{ "status": "READY", "message": "Promotion completed", "blockingError": false, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:40:29Z", "type": "promotion" }If no changes have been promoted, the
messagehas a value ofPromotion completed (no change).
-
Task 6: View the promotion report
-
To view a report for the most recent promotion, use the
/environment/promotion/reportendpoint.curl \ --request GET 'https://<tenant-env-upper-fqdn>/environment/promotion/report' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>' \(2)1 Replace <tenant-env-upper-fqdn>with the FQDN of the upper environment.2 Replace <access-token>with an access token for the upper environment (learn more in Get an access token).{ "createdDate": "2024-06-12T17:32:05Z", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "report": { "IDMConfig": [ { "configChange": { "added": [ "Forgotten Username" ] }, "configItem": "Email > Templates", "fileDestinationPattern": "idm/conf/emailTemplate-*.json", "fileName": "displayName", "type": "single" } ] }, "reportId": "c41286bb-30cd-4109-ba9d-dc4788b6a75c", "reportName": "Report_2024-06-12T17-32+00Z_dryrun=false_8acd3a87-2272-450f-a3b3-1eb222108740", "type": "promotion" }In the example above, the promotion report shows that email template configuration was promoted.
-
To view a report from before the most recent promotion, learn more in View previous promotion or rollback reports.
Task 7: Unlock the environments
Follow the instructions in Unlock environments.
Run a rollback
Task 1: (Optional) Check how a rollback will impact a release upgrade
If you’ve opted in to release deferral and intend to run a rollback on your production environment, check with your team if the promotion you’re rolling back triggered a release upgrade.
-
If the promotion you’re rolling back didn’t trigger a release upgrade, you can proceed with the self-service rollback and move to the next task.
-
If the promotion you’re rolling back did trigger a release upgrade, you have two options:
-
If you want to roll back both the promotion and the release upgrade, raise a support case in the Ping Identity Support Portal so that Ping Identity support can run the rollback on your behalf.
-
Otherwise, if you want to roll back only the promotion and keep the release upgrade, you can proceed with the self-service rollback and move to the next task.
-
Task 2: Lock the environments
Follow the instructions in Lock environments.
Task 3: Check that a promotion isn’t already running
Check the promotion status to confirm that a promotion isn’t already running. This is
indicated in the response when status has a value of READY:
{
"status": "READY",
"message": "Environment ready for promotion",
"blockingError": false,
"globalLock": "LOCKED",
"promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740",
"timeStamp": "2024-06-12T17:12:32Z",
"type": "promotion"
}Task 4: Get a provisional rollback report
To get a provisional rollback report, use the /environment/promotion/report/provisional-rollback endpoint:
curl \
--request GET 'https://<tenant-env-upper-fqdn>/environment/promotion/report/provisional-rollback' \(1)
--header 'Content-Type: application/json' \
--header 'Accept-API-Version: resource=1.0' \
--header 'Authorization: Bearer <access-token>'(2)| 1 | Replace <tenant-env-upper-fqdn> with the FQDN of the upper environment. |
| 2 | Replace <access-token> with an access token for the upper environment (learn more in
Get an access token). |
{
"createdDate": "2024-06-12T17:32:05Z",
"promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740",
"report": {
"IDMConfig": [
{
"configChange": {
"added": [
"Forgotten Username"
]
},
"configItem": "Email > Templates",
"fileDestinationPattern": "idm/conf/emailTemplate-*.json",
"fileName": "displayName",
"type": "single"
}
]
},
"reportId": "c41286bb-30cd-4109-ba9d-dc4788b6a75c",
"reportName": "Report_2024-06-12T17-32+00Z_dryrun=false_8acd3a87-2272-450f-a3b3-1eb222108740",
"type": "provisional-rollback"
}Task 5: Run the rollback
-
To run a rollback, use the
/environment/promotion/rollbackendpoint:curl \ --request POST 'https://<tenant-env-upper-fqdn>/environment/promotion/rollback' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>' \(2) --data-raw '{}'1 Replace <tenant-env-upper-fqdn>with the FQDN of the upper environment.2 Replace <access-token>with an access token for the upper environment (learn more in Get an access token).{ "result": "Rollback process initiated successfully" } -
Check the rollback status to confirm that the rollback is in progress. This is indicated in the response when
statushas a value ofRUNNING:{ "status": "RUNNING", "message": "Prepare config", "blockingError": false, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:14:13Z", "type": "rollback" } -
Check the rollback status as many times as you need until the rollback is complete.
-
If the rollback is still running, the response
statushas a value ofRUNNING:{ "status": "RUNNING", "message": "Rollback configuration", "blockingError": false, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:15:51Z", "type": "rollback" } -
If the rollback failed but is recoverable, the response
statushas a value ofERROR, and the responseblockingErrorhas a value offalse.-
In the example below, the rollback failed an integrity check for missing ESVs.
{ "status": "ERROR", "message": "Missing ESVs", "blockingError": false, "missingESVs": [ "email.from" ], "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:19:31Z", "type": "rollback" }To resolve this:
-
For each ESV in
missingESVs, re-add the ESV into the upper environment. -
Start the rollback steps again.
-
-
If the rollback failed and is not recoverable, the response
statushas a value ofERROR, and the responseblockingErrorhas a value oftrue:{ "status": "ERROR", "message": "Failed to rollback config", "blockingError": true, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:19:31Z", "type": "rollback" }If you run the rollback again after a blocking error, the following response displays:
{ "code": 409, "message": "Environment is blocked from a previous failed promotion or rollback" }To resolve this, open a support case with Ping Identity support. Learn more in Resolve environment errors that are preventing a promotion or a rollback.
-
If Advanced Identity Cloud services are restarting, the response
statushas a value ofRUNNING, and the responsemessagehas a value ofWaiting for workloads to restart:{ "status": "RUNNING", "message": "Waiting for workloads to restart", "blockingError": false, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:32:06Z", "type": "rollback" }This part of the rollback can take several minutes.
-
If the rollback is complete, the response
statushas a value ofREADY, and the responsemessagehas a value ofPromotion completed:{ "status": "READY", "message": "Rollback completed", "blockingError": false, "globalLock": "LOCKED", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "timeStamp": "2024-06-12T17:40:29Z", "type": "rollback" }
-
Task 6: Unlock the environments
Follow the instructions in Unlock environments.
Unlock environments
After you run a promotion or a rollback, you must unlock the upper and lower environments.
-
To unlock the environments, use the
/environment/promotion/lockendpoint:curl \ --request DELETE 'https://<tenant-env-upper-fqdn>/environment/promotion/lock/<promotion-id>' \(1) (2) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(3)1 Replace <tenant-env-upper-fqdn>with the FQDN of the upper environment.2 Replace <promotion-id>with thepromotionIdcreated when you initially locked the environments.3 Replace <access-token>with an access token for the upper environment (learn more in Get an access token).{ "description": "Environment unlock in progress", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "result": "unlocking" } -
Check the lock state as many times as you need until both environments are unlocked. This is indicated in the response when
resulthas a value ofunlocked:{ "description": "Environment locked", "lowerEnv": { "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "state": "locked" }, "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "result": "locked", "upperEnv": { "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "state": "locked" } }
View previous promotion or rollback reports
-
To view a list of previous promotion or rollback reports, use the
/environment/promotion/reportsendpoint:curl \ --request GET 'https://<tenant-env-upper-fqdn>/environment/promotion/reports' \(1) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(2)1 Replace <tenant-env-upper-fqdn>with the FQDN of the upper environment.2 Replace <access-token>with an access token for the upper environment (learn more in Get an access token).[ { "createdDate": "2024-06-12T12:00:29Z", "dryRun": true, "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "reportId": "57aabe7d-4e8c-4fbb-8a13-2fc7d1cb4d52", "type": "promotion" }, { "createdDate": "2024-06-12T17:32:05Z", "dryRun": false, "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "reportId": "c41286bb-30cd-4109-ba9d-dc4788b6a75c", "type": "promotion" }, { "createdDate": "2024-06-12T13:56:10Z", "dryRun": true, "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "reportId": "df893dee-e952-489c-b94d-8c9ebf36e9a5", "type": "promotion" } ] -
To view individual reports, use the
/environment/promotion/reportendpoint and supply areportIdfrom the response in the previous step:curl \ --request GET 'https://<tenant-env-upper-fqdn>/environment/promotion/report/<report-id>' \(1) (2) --header 'Content-Type: application/json' \ --header 'Accept-API-Version: resource=1.0' \ --header 'Authorization: Bearer <access-token>'(3)1 Replace <tenant-env-upper-fqdn>with the FQDN of the upper environment.2 Replace <report-id>with areportId; for example,c41286bb-30cd-4109-ba9d-dc4788b6a75c.3 Replace <access-token>with an access token for the upper environment (learn more in Get an access token).{ "createdDate": "2024-06-12T17:32:05Z", "promotionId": "8acd3a87-2272-450f-a3b3-1eb222108740", "report": { "IDMConfig": [ { "configChange": { "added": [ "Forgotten Username" ] }, "configItem": "Email > Templates", "fileDestinationPattern": "idm/conf/emailTemplate-*.json", "fileName": "displayName", "type": "single" } ] }, "reportId": "c41286bb-30cd-4109-ba9d-dc4788b6a75c", "reportName": "Report_2024-06-12T17-32+00Z_dryrun=false_8acd3a87-2272-450f-a3b3-1eb222108740", "type": "promotion" }
Resolve environment errors that are preventing a promotion or a rollback
To resolve environment errors that are preventing a promotion or a rollback, open a support case:
-
Click Create a case.
-
Follow the steps in the case submission wizard by selecting your account and contract and answering questions about your tenant environments.
-
On the Please answer the following questions to help us understand the issue you’re facing page, enter the following details, and then click Next:
Field Value What product family is experiencing the issue?
Select PingOne Advanced Identity Cloud
What specific product is experiencing the issue?
Select Tenant Settings
What version of the product are you using?
Select NA
Which component is affected?
Select Self-Service Promotion
What Hostname(s) or Tenant ID(s) does this apply to?
Enter a comma-separated list of FQDNs for the relevant tenant environments.
-
On the Tell us about the issue page, enter the following details, and then click Next:
Field Value Provide a descriptive title for your issue
Enter one of the following:
-
Resolve environment errors preventing a self-service promotion -
Resolve environment errors preventing a self-service rollback
Describe the issue below
Enter the following details:
-
The error type, either:
-
An error has occurred during a self-service promotion to the development/staging/production environment -
An error has occurred during a self-service rollback from the staging/production environment
-
-
The error code and message (API users only).
-
-
Click Submit.
Revert configuration in your development environment
To revert configuration in your development environment, open a support case:
-
Click Create a case.
-
Follow the steps in the case submission wizard by selecting your account and contract and answering questions about your tenant environments.
-
On the Please answer the following questions to help us understand the issue you’re facing page, enter the following details, and then click Next:
Field Value What product family is experiencing the issue?
Select PingOne Advanced Identity Cloud
What specific product is experiencing the issue?
Select Configuration
What version of the product are you using?
Select NA
What Hostname(s) or Tenant ID(s) does this apply to?
Enter a comma-separated list of FQDNs for the relevant tenant environments.
-
On the Tell us about the issue page, enter the following details, and then click Next:
Field Value Provide a descriptive title for your issue
Enter
Select Restore from backupDescribe the issue below
Enter the following details:
-
The FQDN of the upper environment from the promotion you need to revert.
-
The date when you last had stable configuration, using the format YYYY-MM-DD.
-
-
Click Submit.
Manage self-service promotions using the admin console
You can find background information on self-service promotions in PingOne Advanced Identity Cloud in Introduction to self-service promotions.
Lower and upper environments
Before you run a promotion using the admin console, you must know which tenant environment is the lower environment and which is the upper environment. Learn more in Lower and upper environments.
The admin console uses a push model to promote configuration, so you need to run a promotion from the admin console in the lower environment. However, you also need to have a tenant administrator account in the upper environment, as the admin console in the lower environment needs to authenticate to the upper environment.
When a promotion is complete, you can view a report in the lower environment. You can also view the report in the upper environment.
Promotions functionality in the lower environment
In the lower environment, the admin console lets you:
-
View changes awaiting promotion to the upper environment
-
Promote changes to the upper environment
-
View history of promotions sent to the upper environment
This lower environment functionality exists in your development and staging environments only. It does not exist in your production environment, as that environment does not send promotions to another environment.
View changes awaiting promotion to the upper environment
-
In the Advanced Identity Cloud admin console of the lower environment, open the TENANT menu (upper right)
-
Click Promote configuration to open the Promotion tab in the Tenant Settings page.
-
The Promotion tab shows the following information:
-
A summary of the promotion status for the environment:
-
Your development environment shows information about promoting from your development environment to your staging environment:
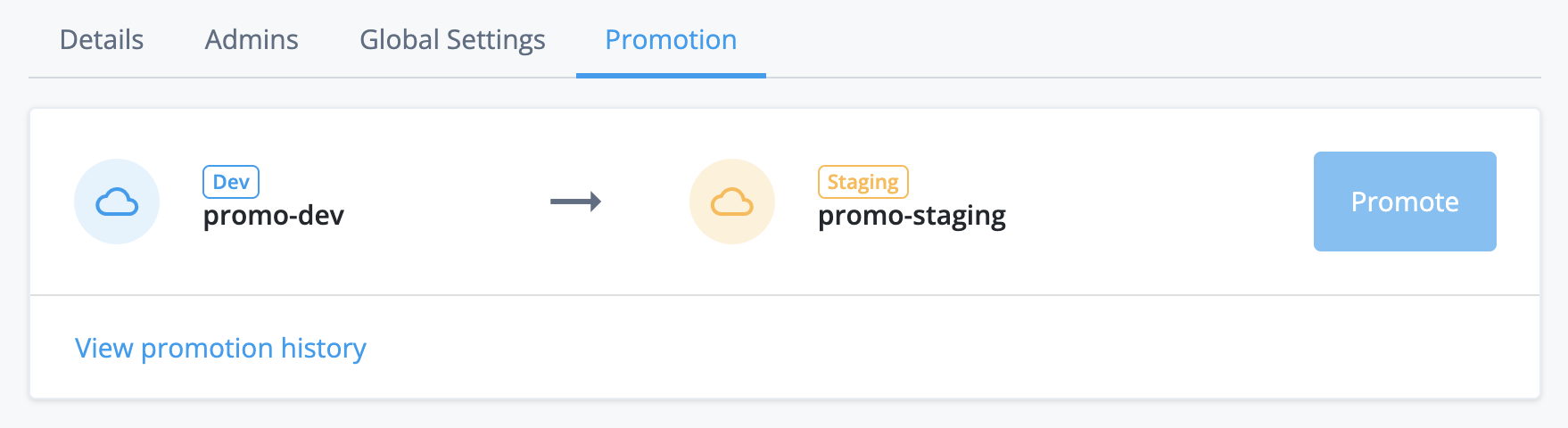
If you have a UAT[2] environment, your development environment promotes to your UAT environment instead. The revised promotion order is development → UAT → staging. If you have a second UAT environment, the revised promotion order is development → UAT → UAT2 → staging.
Learn more in Additional UAT environments.
-
Your staging environment shows information about promoting from your staging environment to your production environment:
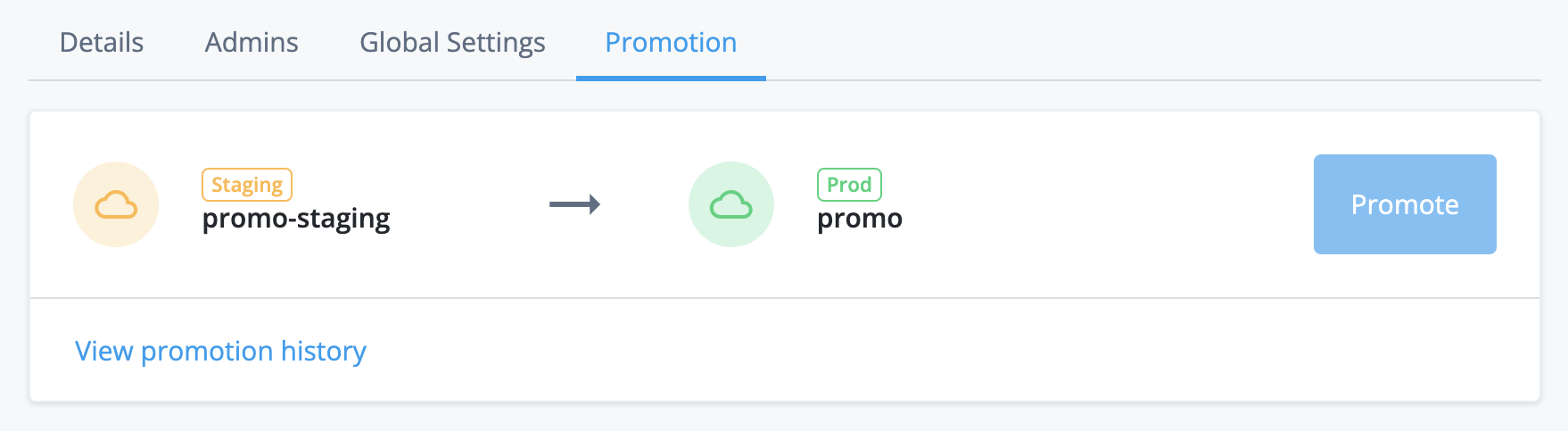
-
-
A summary of any changes to static configuration made by you or other tenant administrators.
For example, in the screenshot below, the admin console indicates that two configuration changes have been made—one to a journey and one to an email template:
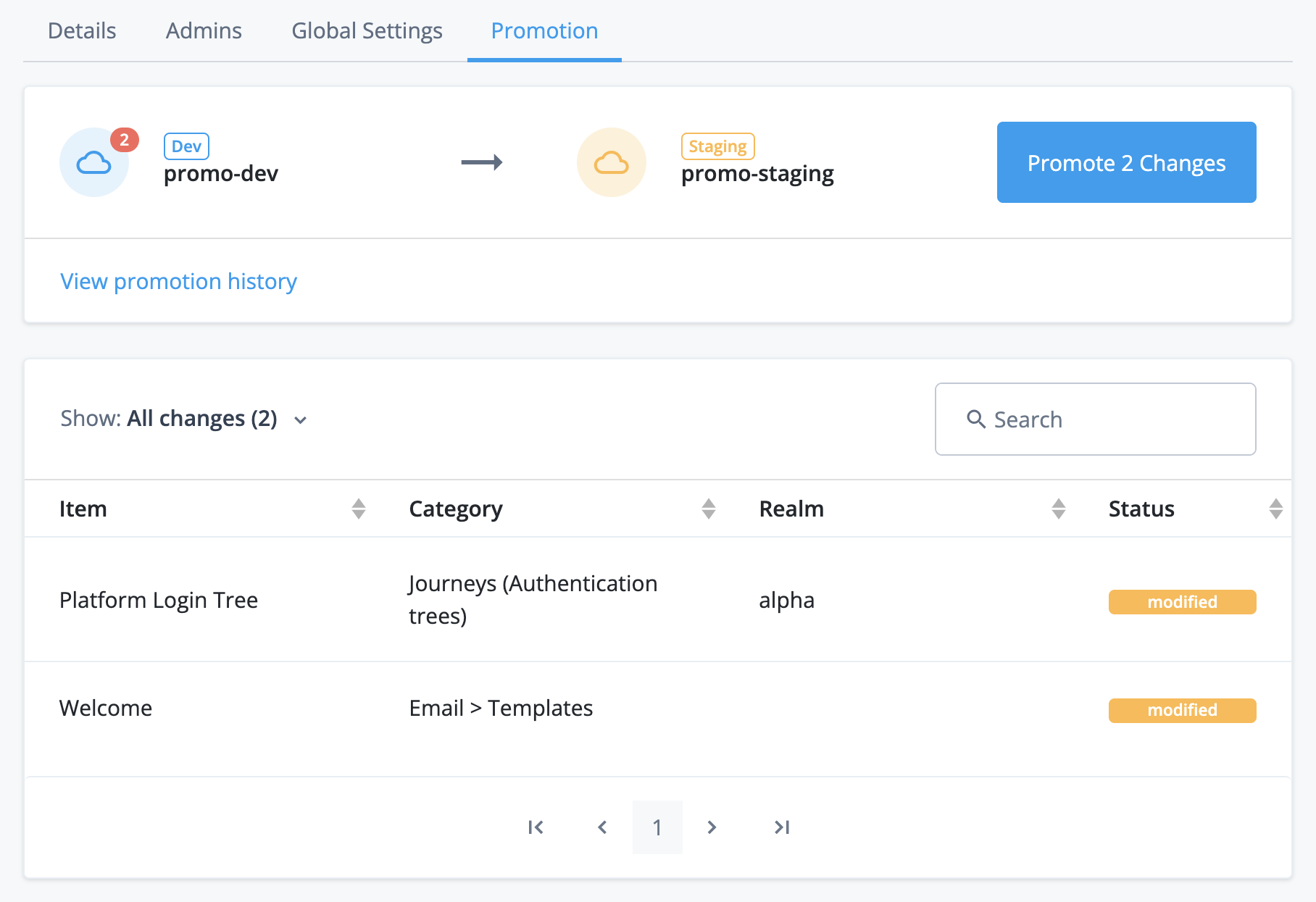
-
Sign in to the upper environment
When you run a promotion or view promotion history, the admin console in the lower environment shows a sign-in screen for the upper environment. This lets the admin console in the lower environment authenticate to the upper environment using your upper environment tenant administrator account.
In your development environment, the sign-in screen title is Sign in to Staging:
In your staging environment, the sign-in screen title is Sign in to Production:
| If you have a UAT[2] environment, your development environment shows a sign-in screen to your UAT environment instead. Learn more in Additional UAT environments. |
To sign in:
-
Check your browser settings:
-
Ensure your browser has third-party cookies enabled for your tenant domain:
-
For Chrome, follow the instructions under the "Change your cookie settings" section in this support article: https://support.google.com/chrome/answer/95647.
-
For other supported browsers, consult the browser’s documentation.
-
-
Ensure your browser is not in incognito mode.
If your browser does not have third-party cookies enabled or is in incognito mode, authentication to the upper environment will fail without an error message and redisplay the sign-in screen. -
-
Click Sign in to Staging (from your development environment) or Sign in to Production (from your staging environment) to open a pop-up browser window showing the sign-in screen for the upper environment:
-
Enter the credentials of your tenant administrator account for the upper environment.
-
Click Next.
-
Complete the authentication journey to the upper environment:
-
If 2-step verification is already enabled for your tenant administrator account, follow the UI prompts to provide your second authentication factor.
-
If 2-step verification is not yet enabled for your tenant administrator account:
-
Click Set up.
-
Follow the UI prompts to set up a second authentication factor for your tenant administrator account.
-
Follow the UI prompts to provide your second authentication factor.
-
-
Otherwise, if 2-step verification is not mandatory in the upper environment, you can click Skip for now to defer the setup of 2-step verification.
-
-
After you have successfully authenticated, the pop-up browser window closes automatically.
-
Promote changes to the upper environment
|
If you’ve opted in to release deferral, the deployment of the new regular channel release to your production environment is triggered by the first promotion to that environment during the seven-day deferral period. This means that you must pause promotions to your production environment until you’ve validated the new release in your lower environments. |
-
In the Advanced Identity Cloud admin console of the lower environment, open the TENANT menu (upper right)
-
Click Promote configuration.
-
Review the static configuration changes that are awaiting promotion. Learn more in View changes awaiting promotion to the upper environment.
If there are any scripts awaiting promotion, ensure that they do not emit any personally identifiable information (PII) of your end users into Advanced Identity Cloud logs.
Ping Identity recommends that you establish a review and testing process for all scripts to prevent PII leaking out of your Advanced Identity Cloud tenant environments.
-
Click Promote n Changes.
-
If the admin console shows a sign-in screen for the upper environment, follow the steps in Sign in to the upper environment.
-
In the Lock Tenants? screen, click Lock and Continue to lock the lower and upper environments.
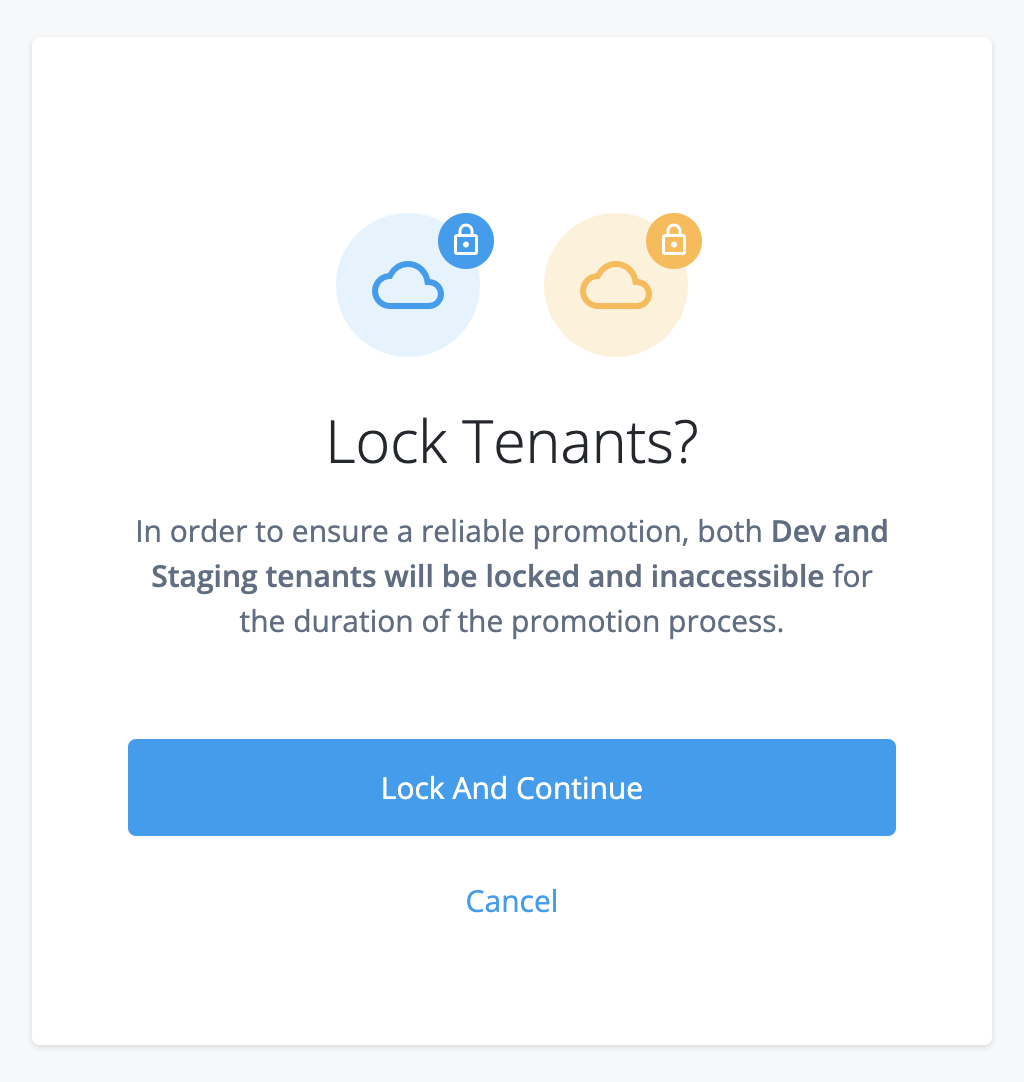
Allow 1–2 minutes for the locking process to complete. When the environments are locked, the admin console has restricted functionality.
Locking an environment prevents configuration changes that could disrupt a promotion; however, all authentication flows continue to work as normal.
-
In the Review Promotion screen, check the static configuration changes that are awaiting promotion.
-
If you want to cancel the promotion:
-
Click Cancel Promotion.
This unlocks the lower and upper environments. Allow 1–2 minutes for the unlocking process to complete.
-
-
If you want to proceed with the promotion:
-
Click Start Promotion
-
In the Start Promotion? modal window:
-
If your static configuration contains directly embedded encrypted secrets that you have yet to store in ESVs, check Ignore Encrypted Secrets to bypass the integrity check for encrypted secrets.
-
Click Start Promotion again.
-
This promotes the static configuration changes from the lower environment to the upper environment. At the end of the promotion process, Advanced Identity Cloud services are restarted in the upper environment, and both environments are automatically unlocked. Allow 10–45 minutes for these combined processes to complete.
If the admin console shows an error message during the promotion process, learn more in the following: -
-
-
When the promotion completes you have a choice of actions:
-
Click View report to view the promotion immediately in the promotion history.
-
Click Done to return to the Promotion tab.
-
View history of promotions sent to the upper environment
-
In the Advanced Identity Cloud admin console of the lower environment, open the TENANT menu (upper right)
-
Click Promote configuration.
-
Click View promotion history.
-
If the admin console shows a sign-in screen for the upper environment, follow the steps in Sign in to the upper environment.
-
In the Promotion History page, click a promotion date in the left menu to review a report:
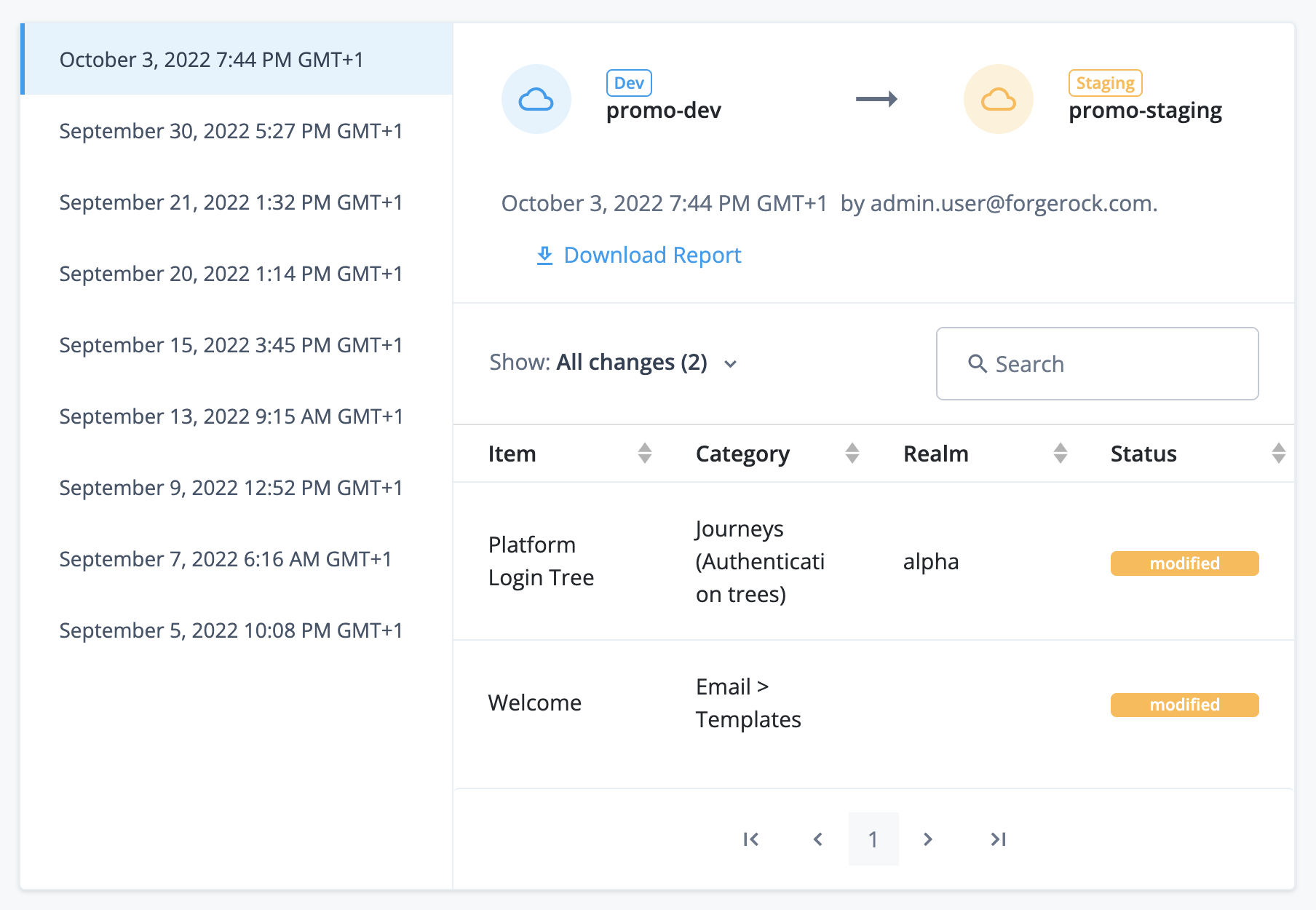
Promotions functionality in the upper environment
In the upper environment, the admin console lets you:
-
View a history of promotions received from the lower environment
This upper environment functionality exists in your staging and production environments only. It does not exist in your development environment, as that environment does not receive promotions from another environment.
View history of promotions received from the lower environment
-
In the Advanced Identity Cloud admin console of the upper environment, open the TENANT menu (upper right)
-
Click Tenant settings.
-
Click the Details tab.
-
Click View updates.
-
In the Tenant Updates page, click a promotion date in the left menu to review a report.
Learn more in the screenshot in View history of promotions sent to the upper environment.
Restricted functionality
When you run a promotion and lock the upper and lower environments, the admin console restricts some functionality under Tenant Settings > Promotion until the environments are unlocked.
Restricted functionality in the lower environment
In the lower environment, the admin console has the following restricted functionality:
-
The left menu is hidden.
-
The page header shows Tenant Locked on the left.
-
The page header shows a restricted drop-down list on the right.
If you sign off and immediately sign back on, you are redirected back to Tenant Settings > Promotion.
Other tenant administrators who are signed on and working in other parts of the admin console do not have this restricted functionality. They are not redirected to Tenant Settings > Promotion unless they sign off and immediately sign back on while the upper and lower environments are locked.
Troubleshooting
Resolve failed integrity check for missing ESVs
When you run a promotion, the admin console may show an error message that you have missing ESVs:
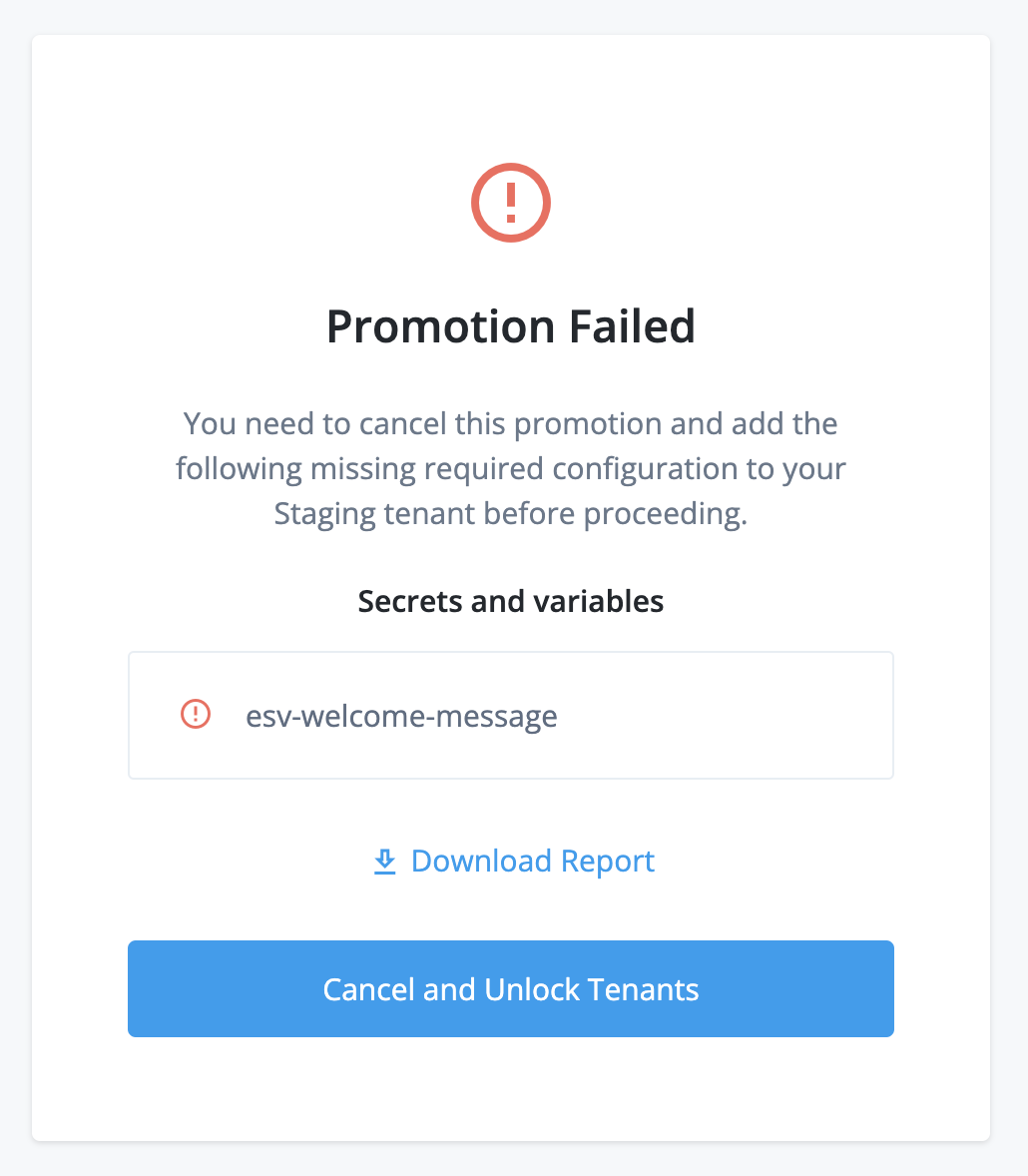
This happens when the upper environment failed an integrity check for missing ESVs.
To resolve this:
-
Click Download Report to download a CSV report of the affected configuration.
-
Click Cancel and Unlock Tenants. This unlocks the lower and upper environments. Allow 1–2 minutes for the unlocking process to complete.
-
For each ESV in the report, create an equivalent ESV in the upper environment.
-
Start the promotion steps again.
Resolve failed integrity check for encrypted secrets
When you run a promotion, the admin console may show an error message that you have encrypted secrets in your configuration:
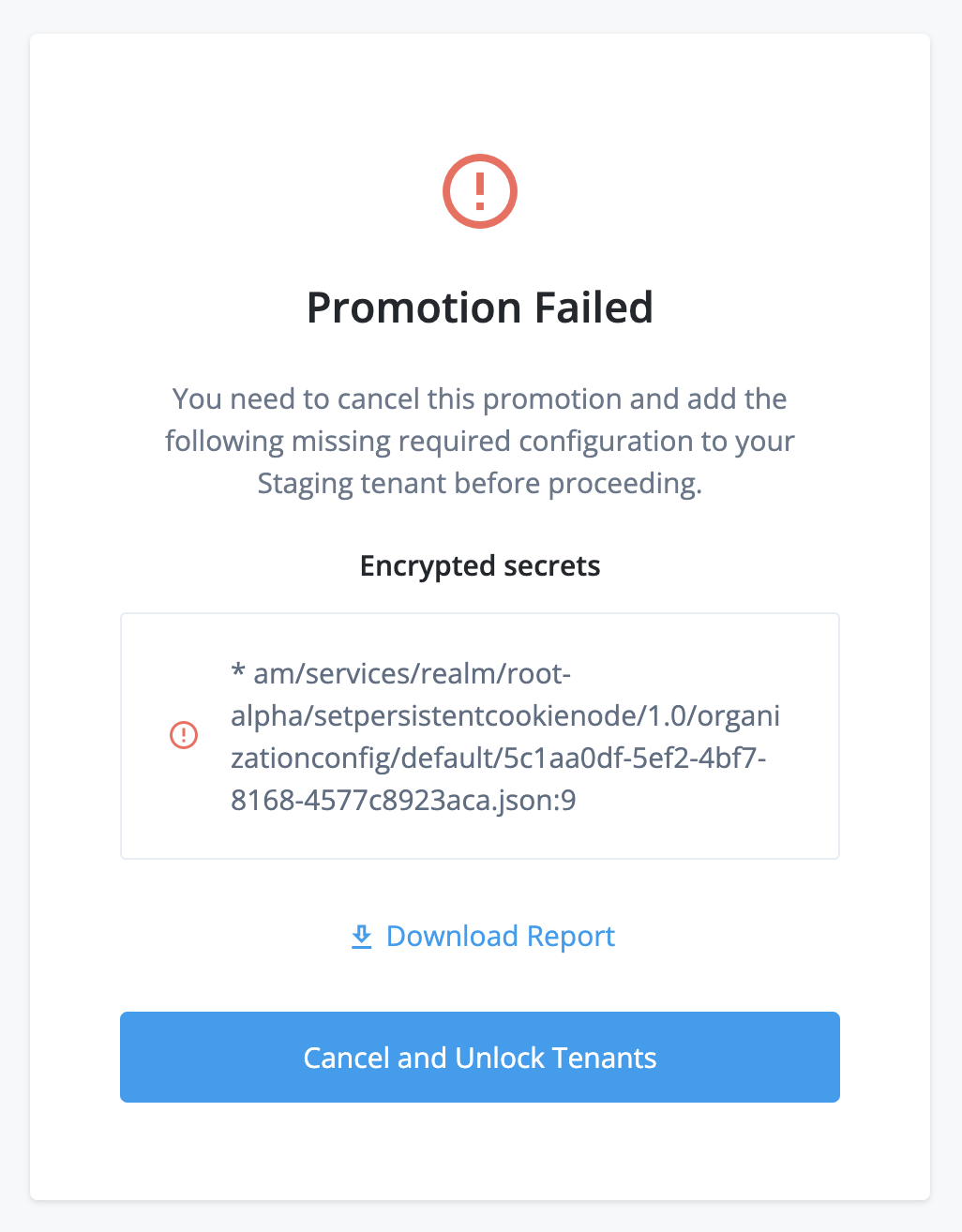
This happens when your lower environment configuration failed an integrity check for encrypted secrets.
To resolve this:
-
Click Download Report to download a CSV summary of the affected configuration.
-
Click Cancel and Unlock Tenants. This unlocks the lower and upper environments. Allow 1–2 minutes for the unlocking process to complete.
-
For each encrypted secret in the report:
-
Create an ESV secret containing the encrypted secret in each of the development, staging, and production environments.
-
Update your configuration to reference the new ESV secret.
-
-
Start the promotion steps again.
Resolve tenant locked errors
When you run a promotion, the admin console may show an error message that your tenant is locked:
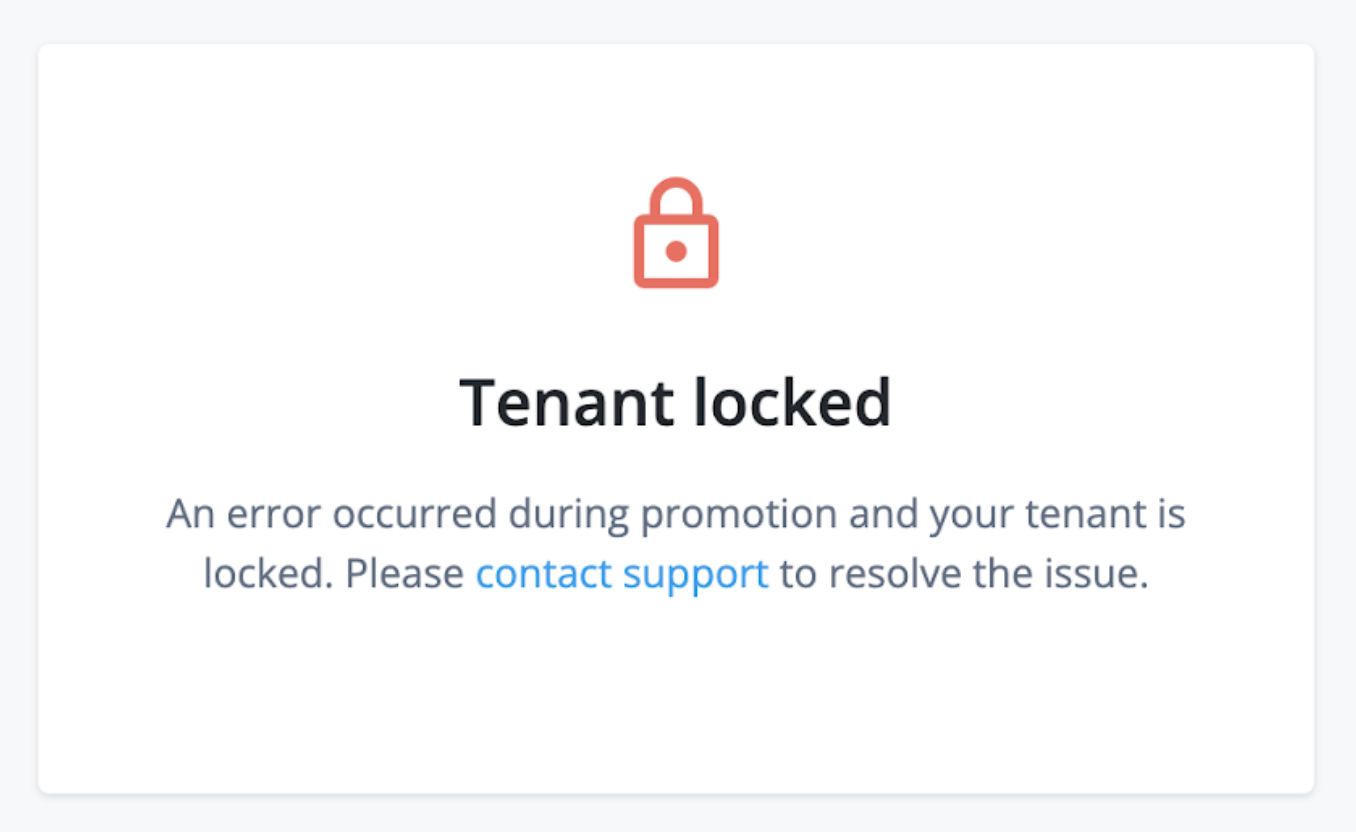
This happens when a previous promotion failed and left the environments in an error state that cannot be automatically resolved.
To resolve environment errors that are preventing a promotion or a rollback, open a support case:
-
Click Create a case.
-
Follow the steps in the case submission wizard by selecting your account and contract and answering questions about your tenant environments.
-
On the Please answer the following questions to help us understand the issue you’re facing page, enter the following details, and then click Next:
Field Value What product family is experiencing the issue?
Select PingOne Advanced Identity Cloud
What specific product is experiencing the issue?
Select Tenant Settings
What version of the product are you using?
Select NA
Which component is affected?
Select Self-Service Promotion
What Hostname(s) or Tenant ID(s) does this apply to?
Enter a comma-separated list of FQDNs for the relevant tenant environments.
-
On the Tell us about the issue page, enter the following details, and then click Next:
Field Value Provide a descriptive title for your issue
Enter one of the following:
-
Resolve environment errors preventing a self-service promotion -
Resolve environment errors preventing a self-service rollback
Describe the issue below
Enter the following details:
-
The error type, either:
-
An error has occurred during a self-service promotion to the development/staging/production environment -
An error has occurred during a self-service rollback from the staging/production environment
-
-
The error code and message (API users only).
-
-
Click Submit.
Revert a promotion
You can revert a promotion using the API. Learn more in Run a rollback.
Revert configuration in your development environment
To revert configuration in your development environment, open a support case:
-
Click Create a case.
-
Follow the steps in the case submission wizard by selecting your account and contract and answering questions about your tenant environments.
-
On the Please answer the following questions to help us understand the issue you’re facing page, enter the following details, and then click Next:
Field Value What product family is experiencing the issue?
Select PingOne Advanced Identity Cloud
What specific product is experiencing the issue?
Select Configuration
What version of the product are you using?
Select NA
What Hostname(s) or Tenant ID(s) does this apply to?
Enter a comma-separated list of FQDNs for the relevant tenant environments.
-
On the Tell us about the issue page, enter the following details, and then click Next:
Field Value Provide a descriptive title for your issue
Enter
Select Restore from backupDescribe the issue below
Enter the following details:
-
The FQDN of the upper environment from the promotion you need to revert.
-
The date when you last had stable configuration, using the format YYYY-MM-DD.
-
-
Click Submit.
Service accounts
PingOne Advanced Identity Cloud provides service accounts to let you request access tokens for most REST API endpoints;
for example, you may need an access token to use the REST API endpoint
/openidm/managed/alpha_user to get a list of identities.
You create a new service account in the Advanced Identity Cloud admin console, which provides you with credentials
(a service account ID and a private key). You use the credentials to obtain an access token from a
built-in OAuth 2.0 public client using the JWT profile for OAuth 2.0 authorization grant flow. You
can then use the access token as a bearer token in the Authorization HTTP header for each API request.
Manage service accounts
A tenant administrator can manage service accounts in these ways:
-
To use the Advanced Identity Cloud admin console, learn more in Manage service accounts using the admin console.
-
To use the Advanced Identity Cloud REST API with a tenant administrator access token, learn more in the article A scripted approach for creating and using service accounts in PingOne Advanced Identity Cloud.
Only a tenant administrator account has the privileges to create, modify, or delete service accounts.
You create service accounts in each environment; they are not promotable.
Service account scopes
When you create a service account, you choose which scopes it can grant to the access tokens it creates. You should always choose the minimum number of scopes needed.
Scopes for AM and IDM APIs in Advanced Identity Cloud
| Scope | Purpose | Reference |
|---|---|---|
|
Access to |
|
|
Access to |
|
Service account access tokens granted the |
Scopes for Advanced Identity Cloud environment APIs
| Scope | Purpose | Reference |
|---|---|---|
|
Access to certificate API endpoints |
|
|
Read-only access to certificate API endpoints. Use this scope if you only need to list certificates. |
|
|
Access to Content Security Policy API endpoints |
Content Security Policy API endpoint |
|
Full access to cookie domain API endpoints. |
|
|
Access to custom domain endpoints |
Custom domains API endpoint |
|
Access to ESV API endpoints |
|
|
Read-only access to ESV API endpoints. Use this scope if you only need to list ESVs. |
|
|
Create, update, and delete access to ESV API endpoints |
|
|
Access to ESV API endpoint to restart Advanced Identity Cloud services |
|
|
Access to promotions API endpoints |
|
|
Access to release management API endpoints |
Release management API endpoint |
|
Access to SSO cookie API endpoints |
SSO cookie API endpoint |
|
Access to log event exporter API endpoints |
Scopes for Advanced Identity Cloud APIs under development
The following scopes grant access to API endpoints that are under development and will imminently be released to the rapid channel.
| Scope | Purpose | Reference |
|---|---|---|
|
Access to analytics API endpoints |
|
|
Access to dataset deletion API endpoints |
|
|
Access to mTLS (mutual TLS) API endpoints |
Scopes for add-on capability APIs
The following scopes grant access to API endpoints in Add-on capabilities.
| Scope | Purpose | Reference |
|---|---|---|
|
Full access to Proxy Connect API endpoints. Use this scope to view, create, activate, deactivate, or delete rules. |
|
|
Read-only access to Proxy Connect API endpoints. Use this scope if you only need to view rules. |
|
|
Write access to Proxy Connect API endpoints. Use this scope to create, activate, deactivate, or delete rules. |
|
|
Access to IGA API endpoints |
|
|
Access to WS-Federation API endpoints |
Used by the Advanced Identity Cloud admin console for the Microsoft 365 application. |
Restricted scopes
The following scopes are restricted, so the API endpoints under them are not accessible using a service account access token. Learn how to access API endpoints using a tenant administrator access token in the article A scripted approach for creating and using service accounts in PingOne Advanced Identity Cloud.
| Scope | Purpose | Reference |
|---|---|---|
|
Access to federation API endpoints |
Federation API endpoint |
Get an access token using a service account
To get an access token using a service account, learn more in Authenticate to Advanced Identity Cloud REST API with access token.
| You can also create a script to get a service account access token within your journeys. This approach lets you use the access token in API calls in a Scripted Decision node in Advanced Identity Cloud. Learn more in Get an access token in a journey for an example. |
Manage service accounts using the admin console
View service accounts
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).

-
Click Tenant settings.
-
Click Global Settings.
-
Click Service Accounts. The page displays existing service accounts for your tenant.
Create a new service account
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).
-
Click Tenant settings.
-
Click Global Settings.
-
Click Service Accounts.
-
Click New Service Account.
-
Enter a Name and optional Description for the service account.
-
In the Scopes section, select the scopes that the service application can grant to an access token. Learn more in Service account scopes.
-
Click Save.
-
When the 'Service account successfully created!' message shows:
-
Make a note of the service account ID, found in the ID field.
-
Click Download Key to download the service account private key.
You must download the private key at this point as it will not be available again.
-
-
Click Done.
| To get an access token using a service account, learn more in Authenticate to Advanced Identity Cloud REST API with access token. |
Modify a service account
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).
-
Click Tenant settings.
-
Click Global Settings.
-
Click Service Accounts.
-
Click the ellipsis on the right of a service account and select Edit.
-
You can change the Name or optional Description.
-
In the Scopes section, you can change the scopes that the service application can grant to an access token. Learn more in Service account scopes.
Before removing scopes that the service application can grant to an access token, make sure you identify which of your integrations are dependent upon those scopes; otherwise those integrations will fail the next time they request an access token. -
Click Save.
Regenerate a key for a service account
| Before regenerating a key, make sure you identify which of your integrations are dependent upon it to sign JWTs, as all those integrations need to be updated with the new key. |
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).
-
Click Tenant settings.
-
Click Global Settings.
-
Click Service Accounts.
-
Click the ellipsis on the right of a service account and select Regenerate Key.
-
On the Regenerate Key dialog box, click Regenerate Key.
-
When the 'Key successfully created!' message is shown:
-
Click Download Key to download the new service account private key.
You must download the private key at this point as it will not be available again.
-
-
Click Done.
Delete a service account
| Before deleting a service account, make sure none of your integrations are dependent upon its key to sign JWTs; otherwise those integrations will fail the next time they request an access token. |
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).
-
Click Tenant settings.
-
Click Global Settings.
-
Click Service Accounts.
-
Click the ellipsis on the right of a service account and select Delete.
-
On the Delete Service Account page, click Delete Service Account.
Monitor your tenant
PingOne Advanced Identity Cloud lets you monitor uptime status and system performance.
|
Advanced Identity Cloud also provides APIs for extracting log data. Learn more in Get audit and debug logs. |
Monitor uptime status
Tenant status page
Use your tenant status page to monitor uptime and historical trends for your production environment.
The tenant status page shows individual statuses for these services:
-
Access management
-
Identity management
-
UI
| If you don’t have access to this page, follow the instructions in Get status page access credentials for additional tenant administrators. |
Manage access to your tenant status page
Get status page access credentials for the initial tenant administrator
If you are the initial tenant administrator, you should have received status page credentials when your tenant was set up.
If you have lost or forgotten those credentials, follow the instructions in Get status page access credentials for additional tenant administrators.
Get status page access credentials for additional tenant administrators
If monitoring Advanced Identity Cloud uptime status is part of a tenant administrator’s role, create a support case in the Ping Identity Support Portal to request that the administrator receive access to the tenant status page.
-
You can request access on behalf of one or more tenant administrators, including yourself.
-
In the request, provide the email address of each tenant administrator you want to have status page access.
Remove status page access for tenant administrators
If you want to remove status page access for one or more tenant administrators, create a support case in the Ping Identity Support Portal. In the request, provide the email address of each tenant administrator from which you want to remove access.
Access your tenant status page
| If you don’t have access to this page, follow the instructions in Get status page access credentials for additional tenant administrators. |
-
Identify your tenant domain name by removing the protocol and any trailing slash from your tenant FQDN.
Example:
openam-mycompany-mytenant-usw1.id.forgerock.io -
Obtain your tenant status page URL by appending your tenant domain name to the Advanced Identity Cloud status page URL, https://status.id.forgerock.io.
Example: https://status.id.forgerock.io/openam-mycompany-mytenant-usw1.id.forgerock.io
-
Open your tenant status page URL in a browser.
-
On the sign-on page, enter your status page credentials.
-
Click Authenticate.
Your tenant status page opens, showing real-time status information for your production tenant environment:
View incident reports in your production tenant environment
You can view current and past service incidents on the status page, but only if the Ping Identity SRE team manually created the incident. This typically happens during an internal incident where we’ve identified an issue affecting your tenant and want to keep you informed.
| The status page doesn’t include detailed incident reports. However, it does provide a historical list of incidents that were posted. |
Filter your status page to show service incidents in your production tenant environment:
-
Click View historical uptime.
-
Select the Incidents tab.
-
For the production environment, click Filter Components, then select one or more Advanced Identity Cloud services.

-
Click Filter Components again to view the incident reports.
Monitor system performance
Monitor using health check endpoint
Use the HTTP response codes from the /monitoring/health endpoint to integrate your tenant
environment with external monitoring tools such as Pingdom.
$ curl 'https://<tenant-env-fqdn>/monitoring/health'This endpoint returns the following HTTP response status codes:
- 200
-
Indicates all critical services in an environment are healthy. This status code also shows the informational message
OK. - 503
-
Indicates one or more critical services in an environment are not healthy. This status code also shows the informational message
Service Unavailable.
Monitor using Prometheus endpoints
Advanced Identity Cloud provides monitoring endpoints you can use with Prometheus.
| Endpoint | Description |
|---|---|
|
Produces Prometheus-formatted metrics for Access Management. Learn which AM metrics are available in AM Prometheus metrics. |
|
Produces Prometheus-formatted metrics for Identity Management Learn which IDM metrics are available in the self-managed documentation: |
|
Advanced Identity Cloud adds a |
You must obtain API credentials to authenticate to the /monitoring/prometheus/am and
/monitoring/prometheus/idm endpoints. Learn more in
Authenticate to Advanced Identity Cloud REST API with API key and secret.
You can download and run a Docker-based example of a Grafana dashboard. The demo requires that you have Docker Desktop installed, and requires macOS.
To try the demo:
-
Download and extract the PingOne Advanced Identity Cloud Monitoring Demo ZIP file.
-
Edit the
setup_monitoring_config.shfile:-
In the
TENANT_DOMAINvariable, enter the domain name of your tenant.Do not include the protocol, and do not add a trailing slash.
For example:
TENANT_DOMAIN="openam-mycompany-mytenant-usw1.id.forgerock.io" -
In the
API_KEY_IDandAPI_KEY_SECRETvariables, enter the API credentials you obtained earlier.For example:
API_KEY_ID="b977d5724ef...562e4c57" API_KEY_SECRET="d3628be865ce152f49...870e5fd3506c4" -
Save your changes.
-
-
Run the
setup_monitoring_config.shscript.The Shell script will set up the following config files:
Config File Description prometheus/prometheus.ymlThe script populates the tenant domain and API credentials.
docker/docker-compose.ymlThe script populates the working directory path.
-
Run the following Docker command:
docker-compose -f docker/docker-compose.yml up
The command downloads a Prometheus Docker image and configures it for your tenant. It also downloads a Grafana Docker image, and configures it to use the Prometheus image as a data source.
-
When the command output for the "grafana_1" container displays a message that contains "HTTP Server Listen", open http://localhost:3000 in a web browser.
-
Log in with username
admin, passwordadmin. -
Enter a new password to use for the administrator, or click Skip.
-
On the Grafana Home page, select Dashboards in the left-side hamburger menu.
The Dashboards page appears.
-
Select AM Overview to view the AM overview dashboard:
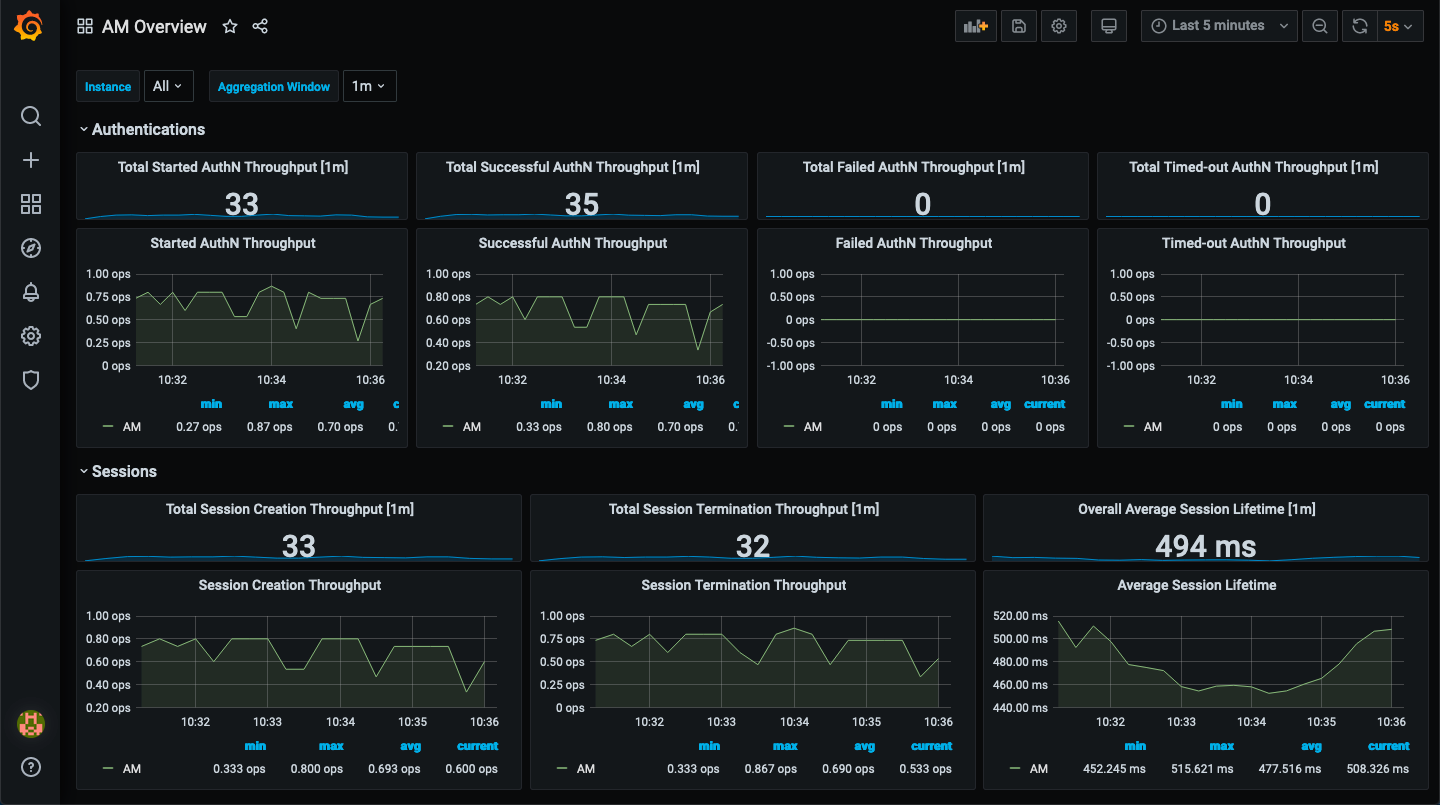
-
Select IDM Sample Dashboard to view the IDM sample dashboard.
-
Go to http://localhost:9090 to view the Prometheus dashboard.
Get audit and debug logs
PingOne Advanced Identity Cloud provides audit and debug logs to help you manage your tenant:
-
Use audit logs to investigate user and system behavior.
-
Use debug logs to investigate any issues that can arise in production.
You can access logs using one of the following methods:
-
Direct log access using REST API: Retrieve log events directly from the
/monitoring/logsREST API endpoint. With this method, you access each of your tenant environments individually and use REST API filters to refine log results. Learn more in Retrieve log entries using REST API. -
External monitoring tool using log streaming: Use the
/environment/telemetry/*REST API endpoints to configure each of your tenant environments to steam logs to an external monitoring tool or Security Information and Event Management (SIEM) for real-time security monitoring and error detection. This method lets you access a single external tool and use its interface to refine log results. You can integrate with Splunk or an OpenTelemetry-compatible SIEM such as Grafana Cloud, Datadog, or New Relic. Learn more in Stream logs to an external monitoring tool. -
Advanced Identity Cloud admin console: Monitor log entries in the admin console. This beta feature is limited to development and sandbox[1] environments. Learn more in Monitor log entries in the admin console.
Advanced Identity Cloud stores logs in various log sources. When you retrieve or stream logs, you’ll need to specify which sources you’re interested in.
Advanced Identity Cloud stores logs for 30 days.
Email provider
PingOne Advanced Identity Cloud uses email provider configuration to support email-dependent end-user journeys. For example, registration and password reset end-user journeys usually include an email component.
By default, Advanced Identity Cloud configures the email provider with default values to connect to a built-in SMTP server. At the start of your onboarding process, this lets you quickly create and test email-dependent journeys using the ready-to-use email templates.
During your onboarding process, you need to update the email provider configuration to use your own external email service in order to provide robust email delivery to your end users.
Email provider configuration changes made in one realm are applied to both realms.
Built-in SMTP server
The built-in SMTP server is preconfigured in Advanced Identity Cloud and enabled by default in your tenant development and sandbox[1] environments.
|
The built-in SMTP server is for testing purposes only and has the following limitations:
In your staging, UAT[2], and production tenant environments, you must update the email provider configuration to use your own external email provider. |
External email services
Advanced Identity Cloud supports two external email service types:
- SMTP
-
-
Send emails through your own SMTP server or a third-party email service such as Amazon SES.
-
Can only be configured in mutable environments:
-
Use the admin console or API to set literal values for testing.
-
Use the API to set ESV placeholders to make the configuration compatible with promotion.
-
-
Use this configuration type for sending email to international email addresses.
-
- MS Graph API
-
-
Send emails using the MS Graph API
sendMailendpoint. -
Can only be configured in mutable environments:
-
Not configurable using the admin console.
-
Use the API to set literal values for testing or set ESV placeholders to make the configuration compatible with promotion.
-
-
International email addresses
To use international email addresses, you must:
-
Use SMTP as the provider type.
-
The SMTP provider must support international email addresses.
-
Configure
mail.mime.allowutf8=trueusing the REST API or the UI. Learn more insmtpPropertiessub-properties.
Configure an email provider across your tenant environments
The high-level process to set up an email provider across your tenant environments is as follows:
-
In your development environment:
-
Create and test a journey that uses an email node. By default, the email provider uses the built-in SMTP server to test the email node.
-
When you’re satisfied with your test results:
-
Configure the email provider configuration to use an SMTP or MS Graph API external email service. Use the instructions in Configure a mutable environment to use an email provider.
-
Verify that your email templates work with the external email service.
-
-
When you’re satisfied that your external email provider is working correctly:
-
Insert ESV placeholders into the email provider configuration to make it compatible with the promotion process.
-
Verify that your email templates work with the updated ESV configuration.
-
-
-
Determine the promotion order of your tenant environments. This will depend on whether you have a standard promotion group of environments or whether you also have additional UAT environments.
-
In promotion order, for each of the tenant environments in your promotion group, perform the following steps:
-
Create the same ESVs in the tenant environment as you created in step 1c. Ensure the ESV values are correct for the tenant environment.
-
Run a promotion to move the configuration changes to the tenant environment from its respective lower tenant environment. Learn more in:
-
-
(Optional) If you have sandbox[1] environments, repeat steps 1b and 1c for each sandbox environment.
Configure a mutable environment to use an email provider
In your development or sandbox[1] tenant environments, configure the email provider to use your own external email service:
-
For SMTP, you can use the admin console or API.
-
For MS Graph API, you can only use the API.
|
Using the admin console
-
In the Advanced Identity Cloud admin console, go to Email > Provider.
-
On the Email Provider page, enable Use my own email provider.
-
Enter details in the following fields:
From Address
Email address of the organization or individual sending the email.
Example:
mycompany@example.com.From Name
Name of sending organization.
Host
Hostname or IP address of your SMTP server.
Port
Port number of your SMTP server.
Many SMTP servers require the use of a secure port such as 465 or 587. Many ISPs flag email from port 25 as spam.
Default value is
587.Username
Username for your SMTP server account.
Password
Password for your SMTP server account.
-
Click Show advanced settings, and edit the options and fields:
Socket Connection Timeout (ms)
Elapsed time before Advanced Identity Cloud times out due to unsuccessful socket connection to the SMTP server. A setting of
0disables this timeout.The default is
300000ms (5 minutes).Socket Write Timeout (ms)
Elapsed time before Advanced Identity Cloud times out because client can’t write to the SMTP server. A setting of
0disables this timeout.The default is
300000(5 minutes).Socket Timeout (ms)
Elapsed time before Advanced Identity Cloud times out due to inactivity. A setting of
0disables this timeout.The default is
300000(5 minutes).Use STARTTLS
-
If enabled, and if the SMTP server supports the STARTTLS command, then Advanced Identity Cloud switches to a TLS-protected connection before issuing any login commands.
-
If the SMTP server does not support STARTTLS, the connection continues without the use of TLS.
Enabled by default.
Use SSL
If enabled, Advanced Identity Cloud uses SSL to connect to the SMTP server.
Disabled by default.
Allow UTF-8
If enabled, adds support for UTF-8 (Non-ASCII) characters in the local part of email addresses (everything before the
@character).Disabled by default.
Do not set this property unless your SMTP provider supports UTF-8 characters. Learn more in International email addresses.
-
-
To test your configuration, click Send Test Email.
-
In the Send Test Email dialog box, enter your own email address.
-
Click Send.
If the test is successful, you’ll get a test email in your email inbox.
-
-
To save the email provider configuration, click Save.
Using the API
You can edit the email service over REST at the openidm/config/external.email endpoint. The following example submits an email configuration over REST:
curl \
--header "Authorization: Bearer <access-token>" \(1)
--header "Accept-API-Version: resource=1.0" \
--header "Content-Type: application/json" \
--request PUT \
--data '{
"host" : "smtp.gmail.com",
"port" : 587,
"debug" : false,
"auth" : {
"enable" : true,
"username" : "admin",
"password" : "Passw0rd"
},
"from" : "admin@example.com",
"timeout" : 300000,
"writetimeout" : 300000,
"connectiontimeout" : 300000,
"starttls" : {
"enable" : true
},
"ssl" : {
"enable" : false
},
"smtpProperties" : [
"mail.smtp.ssl.protocols=TLSv1.2",
"mail.smtps.ssl.protocols=TLSv1.2",
"mail.mime.allowutf8=true"
],
"threadPoolSize" : 20
}' \
"https://<tenant-env-fqdn>/openidm/config/external.email"| 1 | Replace <access-token> with an access token that has the fr:idm:* scope.
Learn more in Get an access token. |
Sample email configuration
This sample email configuration sets up the email provider:
-
SMTP
-
MS Graph API
{
"host" : "smtp.gmail.com",
"port" : 587,
"debug" : false,
"auth" : {
"enable" : true,
"username" : "xxxxxxxx",
"password" : "xxxxxxxx"
},
"timeout" : 300000,
"writetimeout" : 300000,
"connectiontimeout" : 300000,
"starttls" : {
"enable" : true
},
"ssl" : {
"enable" : false
},
"smtpProperties" : [
"mail.smtp.ssl.protocols=TLSv1.2",
"mail.smtps.ssl.protocols=TLSv1.2",
"mail.mime.allowutf8=true"
],
"threadPoolSize" : 20
}{
"type" : "msgraph",
"mailEndpoint" : "https://graph.microsoft.com/v1.0/users/example@myTenant.onmicrosoft.com/sendMail",
"from" : "example@myTenant.onmicrosoft.com",
"auth" : {
"enable" : true,
"type" : "oauth2",
"clientId" : "clientId",
"clientSecret" : "clientSecret",
"tokenEndpoint" : "https://login.microsoftonline.com/myTenant.onmicrosoft.com/oauth2/v2.0/token",
"scope" : [
"https://graph.microsoft.com/.default"
]
},
"timeout" : 300000,
"writetimeout" : 300000,
"connectiontimeout" : 300000,
"threadPoolSize" : 20
}Revert the email provider to use the built-in SMTP server
If you need to revert the email provider to use the built-in SMTP server:
-
In the Advanced Identity Cloud admin console, go to Email > Provider.
-
On the Email Provider page, disable Use my own email provider.
-
Click Save.
|
The built-in SMTP server is for testing purposes only and has the limitations noted at the top of this page. |
Email templates
PingOne Advanced Identity Cloud provides preconfigured email templates for common end-user journeys.
You can customize email templates using Markdown language. Advanced Identity Cloud uses a parser to let you preview your markup.
|
Email templates use Handlebars expressions to reference
object data dynamically. For example, to reference the |
Create a new email template
-
In the Advanced Identity Cloud admin console, go to Email > Templates.
-
On the Email Templates page, click + New Template.
-
Provide the following details:
-
Template Name: Display name for the template.
-
From Address: Enter an email address for the group or individual sending the email.
-
From Name: Enter a name for the group or individual sending the email.
-
Description: A brief description of the template.
-
-
Click Save. The new email opens in the email editor.
-
Learn more in Edit an email template.
|
When you reference an email template, such as in a node or script, you must use its unique template ID. Advanced Identity Cloud generates this ID from the template’s original name (converted to camelCase). The ID is immutable, meaning it won’t change even if you rename the template later. You can find the template ID in the Advanced Identity Cloud admin console URL when editing the template.
For example, the template ID for the Forgotten Username template is |
Edit an email template
-
In the Advanced Identity Cloud admin console, go to Email > Templates.
-
On the Email Templates page, click a template name to open the email editor.
-
To change the wording in the email template, edit the Markdown text in the left window on the page. You can also:
-
Add, modify, or delete locales to suit your end-user audience. Learn more in Manage email template locales.
-
Repeat step 3 for each template locale.
-
To edit the template styles, click Styles, and edit the CSS style code.
-
To view available variables that you can use in the template, click Variables, and view the content on the Available Properties page. Click Done.
-
To edit the template settings, click the More () icon at the top right of the page, and select Settings.
-
Provide the following details:
-
Template Name: Display name for the template.
-
From Address: Enter an email address for the group or individual sending the email.
-
From Name: Enter a name for the group or individual sending the email.
-
Description: Enter a brief description of the template.
-
-
Click Update.
-
Click Save. This saves content changes in all template locales.
Add an image to an email template
-
Upload your image to a hosted service, such as a content delivery network (CDN), so it is available over HTTPS. Local image paths are not permitted.
-
In the Advanced Identity Cloud admin console, go to Email > Templates.
-
On the Email Templates page, click a template name to open the email editor.
-
Edit the Markdown text to reference your image:
-
To add an image at full size:
For example, the Markdown would look like this for an image hosted at
https://example.com/image.extwhere the alt text isthis is an example image: -
To add an image and resize it in pixels:
 -
To add an image and resize it as a percentage:

-
-
Click Save.
Use HTML formatting in an email template
Although you can’t see HTML formatting in the editor, you can use inline HTML to format your email. Learn more in Markdown Syntax: Inline HTML.
-
In the Advanced Identity Cloud admin console, go to Email > Templates.
-
On the Email Templates page, click a template name to open the email editor.
-
Edit the Markdown text:
-
Specify HTML tags to format your content. For example:
<h1>Reset Password</h1> -
To add a table, include both the
<thead>and<tbody>tags; otherwise the table will not convert correctly to Markdown when saved. For example:<table> <thead> <tr> <th>Header 1</th> <th>Header 2</th> <th>Header 3</th> </tr> </thead> <tbody> <tr> <td>Cell Text 1</td> <td>Cell Text 2</td> <td>Cell Text 3</td> </tr> </tbody> </table>
-
-
Click Styles, and add CSS styles for the tag to format it as required. For example:
h1 { font-family: Arial, Helvetica, sans-serif; color: #f96700; background-color: #032b75; font-size: 25px; padding: 10px; } -
Click Save.
After saving your changes, the inline HTML tags are converted to Markdown, but the CSS styles for the tags persist. The CSS styles apply to all locales.
| Alternatively, you can click Advanced Editor and modify the template in HTML. However, if you swap to the Advanced Editor, you cannot change back to Markdown. |
Use ESV variables in an email template
You can use ESV variables in email templates to dynamically present different text, images, or links depending on the specific tenant environment.
You can find background information on ESVs in PingOne Advanced Identity Cloud in ESVs.
| To add ESV variables to an email template, you must use the Advanced Editor. After you have swapped to the Advanced Editor, you cannot change back to Markdown. |
Add ESV variables to an email template
-
Create the ESV variables to use in the email template:
-
Create the variables using the Advanced Identity Cloud admin console or variables APIs.
-
Restart Advanced Identity Cloud services by applying updates in the Advanced Identity Cloud admin console or using the restart API.
-
-
In the Advanced Identity Cloud admin console, go to Email > Templates.
-
On the Email Templates page, click a template name to open the email editor.
-
Click Advanced Editor.
-
Add the placeholder for one or more ESV variables. For example:
&{esv.my.variable} -
Click Save.
-
In step 1, add these two ESV variables:
-
esv-test-link, with a value ofhttps://test.example.com -
esv-test-image, with a value ofhttps://example.com/image.ext
-
-
In step 5, add the link and image:
-
Add the link using the ESV placeholder, where the link text is the URL, for example:
<p>For more information, go to our website: &{esv.test.link}</p>You can also add the link using the <a>tag with thehrefattribute. This is useful if you want to display different link text. -
Add the image using the ESV placeholder, for example:
<p> <img src="&{esv.test.image}"> </p>
The preview in the left window shows the ESV placeholder and an image placeholder rather than the actual link and image as these are only resolved when the email is sent.
-
Manage email template locales
You can create email content for different locales. When an email is sent during an end-user journey, Advanced Identity Cloud automatically selects the appropriate email template based on the value of the accept-language header, typically derived from the language set in the end user’s browser.
Use the browser’s developer tools to check the value set in the accept-language header.
|
When sending email templates, you can use a script to override the language set in the end user’s accept-language header. Use the sendTemplate action in your script and set the language in the params._locale object property. The language specified in the script takes precedence over the end user’s browser language. Learn more in Send email templates using a script.
|
The locale selector in the top left of the email template editor displays the current template’s locale in the format Locale: code, where code is a
ISO-639-1 language code, for example, en or de. Some preconfigured email templates, such as the registration template, already include content for the en (default) and fr locales.
To manage email template locales:
-
In the Advanced Identity Cloud admin console, go to Email > Templates.
-
On the Email Templates page, click a template name to open the email editor.
-
Switch, add, modify, or delete a locale:
-
To switch locale:
-
Click Locale: code.
-
Select a locale.
-
-
To add a locale:
-
Click Locale: code.
-
Click Add Locale to open the Add Locale modal.
-
Enter a ISO-639-1 language code in the Code field.
-
(Optional) Select Make Default to make the new locale the default for this template.
-
Click Save to add the new locale to the template, populated with a copy of the content from the default locale. The changes apply immediately without saving the main template.
-
-
To modify a locale:
-
Click Locale: code.
-
Click the locale’s edit icon () to open the Edit Locale modal.
-
To change the locale, enter a ISO-639-1 language code in the Code field.
-
To make the locale the default locale for the template, select Make Default.
-
Click Save to close the modal window. Any changes apply immediately without saving the main template.
-
-
To delete a locale:
-
Click Locale: code.
-
Click the locale’s edit icon () to open the Edit Locale modal.
-
Click Delete Locale to delete the locale and its content. The deletion applies immediately without saving the main template.
-
-
Delete an email template
|
Deleting an email template cannot be undone. |
-
In the Advanced Identity Cloud admin console, go to Email > Templates.
-
On the Email Templates page, click the More () icon adjacent to any template.
-
Select Delete.
-
In the dialog box, click Delete.
Manage email templates
-
In the Advanced Identity Cloud admin console, go to Email > Templates.
-
On the Email Templates page, click the More () icon adjacent to any template, and do any of the following:
-
To disable a template, click Deactivate.
-
To enable a template, click Activate.
-
To duplicate a template, click Duplicate.
-
In the Duplicate Template window, enter the following details:
-
Template Name: Display name for the template.
-
From Address: Enter an email address for the group or individual sending the email.
-
From Name: Enter a name for the group or individual sending the email.
-
Description: A brief description of the template.
-
-
Click Save.
-
-
Allow cross-domain requests with CORS
Cross-origin resource sharing (CORS) lets user agents make cross-domain server requests. In PingOne Advanced Identity Cloud, you can configure CORS to allow browsers from trusted domains to access Advanced Identity Cloud protected resources. For example, you might want a custom web application running on your own domain to get an end-user’s profile information using the Advanced Identity Cloud REST API.
By default, CORS is configured to let the Ping SDKs access Advanced Identity Cloud. You can add additional CORS configurations that let other APIs or SDKs access Advanced Identity Cloud.
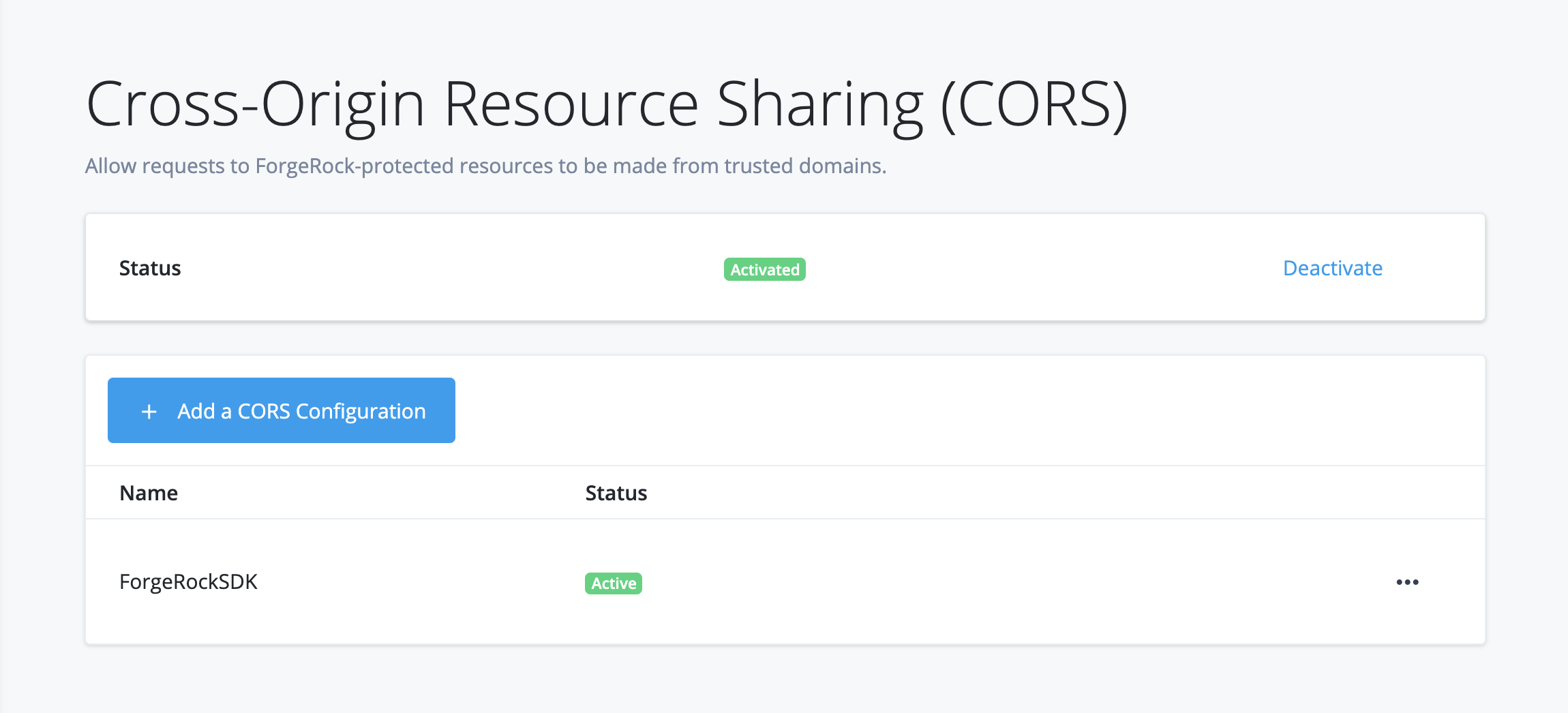
Configure CORS using ESVs
-
In your development environment:
-
Use the Advanced Identity Cloud admin console to set up one or more CORS configurations for your environment:
You can create as many configurations as you need. The active configurations are combined to form the entire set of rules for resource sharing in your environment.
-
For each CORS configuration:
-
If the
acceptedOriginsfield contains hard-coded configuration, use the Advanced Identity Cloud REST API to replace the value of theacceptedOriginsfield with an ESV array. Learn more in Insert ESV placeholders into CORS configuration. -
If the
acceptedOriginsfield already contains an ESV array, no action is needed.
-
-
Check that the CORS configuration is working as expected in your development environment.
-
-
In your staging environment:
-
If you created any new ESV arrays in step 1b, create corresponding ESVs with the same names in your staging environment.
-
Run a promotion to move the configuration change from your development environment to your staging environment. Refer to:
-
Check that the CORS configuration is working as expected in your staging environment.
-
-
In your production environment:
-
If you created any new ESV arrays in step 1b, create corresponding ESVs with the same names in your production environment.
-
Run a promotion to move the configuration change from your staging environment to your production environment.
-
Check that the CORS configuration is working as expected in your production environment.
-
Create a new CORS configuration
-
In your development environment, open the TENANT menu (upper right), and choose Tenant settings.
-
On the Tenant Settings page, click Global Settings > Cross-Origin Resource Sharing (CORS).
-
Click + New CORS Configuration.
-
On the New CORS Configuration dialog box, choose a configuration type.
Ping SDKs
Choose this option when you want to work with the Ping SDKs.
Advanced Identity Cloud pre-configures accepted origins, methods, and headers for you. You can modify the configuration in the next step.Custom
Choose this option when you want to use your own SDK, APIs, or other software components.
-
Click Next.
-
In the New CORS Configuration dialog box, provide CORS details.
Name
Enter a display name. Use only numerals, letters, and hyphens (-).
Accepted Origins
Required. Accepted origins that will be allowed to make requests to Advanced Identity Cloud from your application in a cross-origin context. Wildcards are not supported. Each value should be identical to the origin of the CORS request.
Example:https://myapp.example.com:443Accepted Methods
Defaults are
POSTandGET. The set of (non-simple) accepted HTTP methods allowed when making CORS requests to Advanced Identity Cloud. Use only uppercase characters.Accepted Headers (optional)
Accepted header names when making requests from the above specified trusted domains.
Header names are case-insensitive. By default, the following simple headers are explicitly accepted:Cache-Control,Content-Language,ExpiresLast-Modified,Pragma.
If you don’t specify values for this element, then the presence of any header in the CORS request, other than the simple headers listed above, will cause the request to be rejected. -
(Optional) Click Show advanced settings to display further CORS configuration settings:
Exposed Headers (optional)
Add the response header names that Advanced Identity Cloud returns.
The header names are case-insensitive. User agents can make use of any headers that are listed in this property, as well as these simple response headers:Cache-Control,Content-Language,Expires,Last-Modified,Pragma, andContent-Type. User agents must filter out all other response headers.Enable Caching
Max age is the maximum length of time, in seconds, that the browser is allowed to cache the pre-flight response. The value is included in pre-flight responses, in the Access-Control-Max-Age header.
Allow Credentials
Enable this property if you send Authorization headers as part of the CORS requests, or need to include information in cookies when making requests.
When enabled, AM sets the Access-Control-Allow-Credentials: true header.
-
Click Save CORS Configuration.
Activate or deactivate a CORS configuration
-
To activate or deactivate all CORS configurations:
-
In your development environment, open the TENANT menu (upper right), and choose Tenant settings.
-
On the Tenant Settings page, click Global Settings > Cross-Origin Resource Sharing (CORS).
-
On the CORS Configurations page, in the upper right side, click Activate or Deactivate.
-
-
To deactivate an individual CORS configuration:
-
In your development environment, open the TENANT menu (upper right), and choose Tenant settings.
-
On the Tenant Settings page, click Global Settings > Cross-Origin Resource Sharing (CORS).
-
On the CORS Configurations page, find the name of the configuration you want to deactivate.
-
Click its More () menu, and choose Deactivate.
-
Edit a CORS configuration
-
In your development environment, open the TENANT menu (upper right), and choose Tenant settings.
-
On the Tenant Settings page, click Global Settings > Cross-Origin Resource Sharing (CORS).
-
On the CORS Configurations page, find the name of the configuration you want to edit.
-
Click its More () menu, and choose Edit.
TLS, secrets, signing, trust, and encryption
PingOne Advanced Identity Cloud was built with security in mind:
-
Inbound network traffic is always TLS encrypted.
-
Secrets — for example, credentials to connect to external services—can be specified in your developer, staging, and production environments.
-
Keys and certificates are used to generate, sign, validate, and encrypt tokens, such as SAML 2.0 assertions and client-based access tokens.
-
Incoming SAML 2.0 assertions require trust relationships with the SAML 2.0 providers.
-
Advanced Identity Cloud data is encrypted at rest.
This page describes the default implementations for each of these security factors. It also describes customization options, if they’re available.
TLS encryption
By default, your Advanced Identity Cloud tenant uses Google-managed certificates for TLS encryption.
If you prefer, Advanced Identity Cloud lets you use your own, self-managed certificates instead of using the Google-managed certificates.
Learn more about configuring your tenant to use a self-managed certificate in Self-managed certificates.
Secrets
When you configure Advanced Identity Cloud, the secrets you provide in your development environment normally don’t change when you promote your environment to staging and production. However, in some situations, you might want the three environments to use different secrets.
For example, you might want Advanced Identity Cloud to log in to an external system, such as an OTP provider. However, you need Advanced Identity Cloud to use different credentials depending on whether it’s accessing the OTP provider from the development, staging, or production environment.
Environment secrets and variables (ESVs) let you configure different secrets in your Advanced Identity Cloud development, staging, and production environments. In the preceding example, instead of hard-coding a single set of credentials for the OTP provider in the Advanced Identity Cloud admin console, you could configure ESVs that hold the credentials. Then, the desired credentials to the OTP provider would be used depending on which Advanced Identity Cloud environment was running.
Learn more in Define and promote an ESV.
Signing keys and certificates
By default, Advanced Identity Cloud generates a set of secret labels in each Advanced Identity Cloud realm. Each secret label corresponds to functionality in Advanced Identity Cloud that requires a signing key or certificate. For a full list of secret labels, learn more in Secret labels.
Advanced Identity Cloud lets you override the generated secret labels. First, create an ESV secret that holds the key or certificate. Then, map the secret in the secret store of the desired realm.
Learn more in Use ESVs for signing and encryption keys.
Trust relationships with SAML 2.0 providers
If your Advanced Identity Cloud tenant has trust relationships with one or more SAML 2.0 providers, the tenant might receive SAML assertions signed by a certificate. The certificate might itself be signed by a certificate authority (CA). For Advanced Identity Cloud to trust this type of SAML assertion, the CA’s public certificate must be installed in Advanced Identity Cloud.
You can add a CA’s public certificate to your Advanced Identity Cloud configuration by creating a support case in the Ping Identity Support Portal.
Realm settings
Realms are administrative units that group configurations and identities together so that you can manage different sets of identities and applications within the same PingOne Advanced Identity Cloud tenant.
Each realm is fully self-contained and operates independently of other realms within a tenant; the identities and applications in one realm can’t access those in another realm.
A typical example of realm management is when a company divides its identities into two realms: one for employees and one for customers, each having a distinct set of identities and registered applications.
Manage realm settings
-
In the Advanced Identity Cloud admin console, open the Realm menu (upper left).
-
Go to Realm Settings > Details.
-
On the Details page:
-
The Status bar indicates whether the realm is Active or Inactive.
-
To take the realm out of service, click Deactivate.
When a realm is deactivated, users and devices contained in the realm will not be able to access its applications. Identity and app information is still registered to your identity platform. -
Name: The realm name is non-configurable.
-
(Optional) DNS Aliases: Alternative display names for the realm’s URL.
-
Use Client-based Sessions: Enable this option to allow signing and encryption of the JWT in the global session service.
-
-
To configure a custom domain name, click Custom Domains. Learn more in Configure customer-friendly domain names.
When you’re satisfied with your changes, click Save.
Override realm authentication attributes
It’s useful to override realm authentication attributes when you want to adjust the core authentication properties of a realm. For example, you may want to extend the time limit for responding to an authentication verification email.
Under Native Consoles > Access Management, go to Authentication > Settings.
For detailed property information, learn more in Core authentication attributes.
Alpha and Bravo realms
The Alpha and Bravo realms are the two default realms that are included as part of an PingOne Advanced Identity Cloud tenant. These realms are configurable, unlike the top-level realm that Advanced Identity Cloud configures for tenant administrator identities.
|
Advanced Identity Cloud does not support more than two realms in the same tenant. |
The Alpha and Bravo realms are nearly identical, with the exception of delegated administration.
End-user sign-in
End users access their sign-in page using a URL that specifies the realm they belong to. For example:
-
Alpha realm end users: https://<tenant-env-fqdn>/am/XUI/?realm=alpha&authIndexType=service&authIndexValue=Login
-
Bravo realm end users: https://<tenant-env-fqdn>/am/XUI/?realm=bravo&authIndexType=service&authIndexValue=Login
Tenant administrators cannot authenticate using these realm-specific login URLs. Learn more in Sign on to a tenant admin console.
Delegated administration
In the Alpha realm, you can set up internal roles for delegated administration using a custom set of privilege attributes.You can then assign those internal roles to users so that Alpha realm users can act as delegated administrators and perform actions on the custom set of attributes specified by the role.
The Bravo realm does not support delegated administration.
Assign internal roles
You can assign the internal roles in two different ways using the Advanced Identity Cloud admin console:
-
To add an internal role to a user, go to Identities > Manage > Realm - Users. Select a user, then select the Authorization Roles tab, then click + Add Authorization Roles.
-
To add a user to an internal role, go to Identities > Manage > Internal Roles. Select a role, then select the Members tab, then click + Add Members.
In the Bravo realm, while you can set up internal roles for delegated administration, you cannot use them. Also, you cannot add a user to an internal role, and even though it appears possible to add an internal role to a user, this will not correctly link the user to the role. If you attempt this, the user will not be listed in the internal role Members tab.
The following table summarizes these differences:
| Action | Alpha Realm | Bravo Realm |
|---|---|---|
Create internal role for the purposes of delegated administration |
||
Add user to internal role |
||
Add internal role to user |
|
Configure customer-friendly domain names
PingOne Advanced Identity Cloud lets you configure access to your tenant environments using one or more custom domains. Custom domains let you replace the default forgerock.io domain with a customer-friendly URL that reflects your company name or brand:
-
Configure the Alpha and Bravo realms to use a custom domain for hosted pages and your customer-facing applications.
-
Configure the top-level realm to use a custom domain for the admin console and your administrative applications.
Consider the following points when you customize a domain name:
-
You can set a custom domain name only at the realm level.
-
You can set multiple custom domain names per realm.
-
Don’t use your top-level domain name. This is because you must set up a CNAME record for each custom domain, but CNAME records aren’t permitted alongside other record types, including any A, NS, TXT, or SOA record types that belong to a top-level domain.
-
Wrong:
mycompany.com -
Right:
id.mycompany.com
Learn more in section 2.4 of RFC 1912.
-
Configure a custom domain
-
Create a CNAME record with your DNS provider that points your custom domain to your Advanced Identity Cloud tenant environment’s FQDN. For example:
Type Name Data CNAME
customers.mycompany.com
openam-mycompany.forgerock.io
-
If your custom domain already has CAA records, add additional CAA records to ensure that Advanced Identity Cloud can generate Google-managed SSL certificates. Learn more in Specify the CAs that can issue your Google-managed certificate. For example:
Type Name Data CAA
customers.mycompany.com
letsencrypt.org 0 issue
CAA
customers.mycompany.com
pki.goog 0 issue
-
Create a self-managed certificate.
-
This step is required if your custom domain relies on private DNS or you route your HTTP traffic through a WAF service.
-
This step is optional if your custom domain relies on public DNS.
-
-
Add the custom domain to your realm. Learn more in:
-
Manage custom domains using the admin console (supports Alpha and Bravo realms only)
-
Manage custom domains using the API (supports Alpha, Bravo, and top-level realms)
-
-
Configure the cookie domain for the custom domain using the instructions in Control cookie scope for custom domains.
-
The custom domain should now be successfully configured:
-
If your custom domain relies on public DNS, and you don’t have a self-managed SSL certificate, Advanced Identity Cloud adds the custom domain to a Google-managed SSL certificate:
-
If this is the first custom domain you’ve added to any of the realms in your tenant, Advanced Identity Cloud creates a second Google-managed SSL certificate and adds the custom domain to the Subject Alternative Name (SAN) field of the certificate. It creates a second certificate so that the first Google-managed SSL certificate continues to serve the default tenant FQDN without interruption.
-
If this is the second or subsequent custom domain you’re adding to any realm in your tenant, Advanced Identity Cloud adds the custom domain to the SAN field of the second Google-managed SSL certificate.
It can take up to 30 minutes to provision or reprovision the second Google-managed SSL certificate. -
-
The custom domain name is added to the realm settings.
-
The FQDN for your custom domain name is mapped to server defaults.
-
The custom domain name is added to the Redirection URIs field of the
end-user-uiOAuth 2.0 client. Learn more in Configure OAuth clients.
-
-
Confirm that the custom domain is working as expected:
-
To confirm that Advanced Identity Cloud is serving traffic over HTTPS (TLS) for your custom domain name, in a browser, go to your custom domain location. For example, go to
https://id.mycompany.com. -
Confirm that URL paths work for both tenant domain and custom domain. You should be able to access the same resources using both domains.
Example endpoints for the Alpha realm:
-
Access management:
-
https://<tenant-env-fqdn>/am/json/realms/root/realms/alpha/authenticate -
https://<custom-domain-fqdn>/am/json/realms/root/realms/alpha/authenticate
-
-
Identity management:
-
https://<tenant-env-fqdn>/openidm/managed/alpha_user/<uuid> -
https://<custom-domain-fqdn>/openidm/managed/alpha_user/<uuid>
-
This doesn’t apply to the OIDC configuration discovery endpoint. -
-
To test hosted pages or the Advanced Identity Cloud admin console, use an incognito or private browser window:
-
If you added the custom domain to an Alpha or Bravo realm, access an end-user URL. For example:
https://id.mycompany.com/login/?realm=/alpha#/. -
If you added the custom domain to the top-level realm, access an administrator URL. For example:
https://id.mycompany.com/login/?realm=/#/.
-
-
If your custom domain relies on public DNS, it can take up to 48 hours for domain name changes to propagate. If you try to use the new domain name to access your website, error messages might display until the changes take effect. If error messages still display after 48 hours, make sure your Advanced Identity Cloud domain name settings are correct.
-
Verify a custom domain in Google
If you use Google as a social login IdP, you must use your domain to configure the redirect URL fields of your OAuth 2.0 apps. This might create prompts from Google to verify your domain with your domain provider. For information about how to verify your domain, learn more in Verify your site ownership on the Google Search Console.
Access OIDC configuration discovery endpoint
When you configure a custom domain, the OIDC configuration discovery endpoint URL changes:
| Domain context | Endpoint URL | ||
|---|---|---|---|
Default domain |
|
||
Custom domain |
|
Control cookie scope for custom domains
Advanced Identity Cloud lets you configure the cookie domains of your custom domains so you can control which applications have access to the cookies you create.
By default, when you add a custom domain to an environment, no cookie domain is set for it. You must explicitly configure its cookie domain to suit your deployment. You can configure it in these ways:
-
Set it to use a single subdomain (for example,
sso.mycompany.co.uk). This ensures cookies can be set or modified only by applications running on that subdomain. -
Set it to use more than one subdomain. This lets you set cookies on one subdomain (for example,
sso.mycompany.co.uk) but makes them available to an application running on a different subdomain (for example,banking.mycompany.co.uk). -
Set it to use a domain (for example,
mycompany.co.uk). This lets you set cookies at the domain level so they’re available to legacy applications yet to be migrated to Advanced Identity Cloud.
Learn how to set cookie domains in:
| Advanced Identity Cloud always writes cookies to the default tenant environment FQDN of each of your environments. This is not configurable to ensure you retain access to your environments. |
Manage cookie domains using the API
You can find background information on cookie domains in PingOne Advanced Identity Cloud in Control cookie scope for custom domains.
Cookie domains API endpoint
Advanced Identity Cloud provides the Cookie Domains API endpoint to manage cookie domains.
Authenticate to the cookie domains API endpoint
To authenticate to the cookie domains API endpoint, use an access token created with the following scope:
| Scope | Description |
|---|---|
|
Full access to the cookie domains API endpoint. |
View cookie domains
Advanced Identity Cloud always writes cookies to your default tenant FQDN to ensure you retain access. Make a
GET request to the /environment/cookie-domains endpoint to view the other domains or subdomains
where your tenant environment writes cookies.
To view the cookie domain configuration in any tenant environment:
-
Get an access token created with the
fr:idc:cookie-domain:*scope. -
Get the cookie domain configuration from the
/environment/cookie-domainsendpoint:$ curl \ --request GET 'https://<tenant-env-fqdn>/environment/cookie-domains' \(1) --header 'Authorization: Bearer <access-token>' (2)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <access-token> with the access token. Show response
{ "domains": [ "sso.mycompany.co.uk", "banking.mycompany.co.uk" ] }
Update cookie domains
Advanced Identity Cloud always writes cookies to your default tenant FQDN to ensure you retain access. Make a
PUT request to the /environment/cookie-domains endpoint to set or update the other domains or
subdomains where your tenant environment writes cookies.
To update the cookie domain configuration in any tenant environment:
-
Review the existing cookie domain configuration. Learn more in View cookie domains.
-
Adapt the cookie domain configuration to suit your use case. Learn more in Control cookie scope for custom domains.
Before removing a domain or subdomain from the configuration, you must first update any existing applications that rely on cookies set using that domain or subdomain. -
Get an access token created with the
fr:idc:cookie-domain:*scope. -
Replace the existing cookie domain configuration with the cookie domain configuration you adapted in step 2:
$ curl \ --request PUT 'https://<tenant-env-fqdn>/environment/cookie-domains' \(1) --header 'Authorization: Bearer <access-token>' \(2) --header 'Content-Type: application/json' \ --data '<cookie-domains-configuration>' (3)1 Replace <tenant-env-fqdn> with the FQDN of your tenant environment. 2 Replace <access-token> with the access token. 3 Replace <cookie-domains-configuration> with a JSON array of cookie domains; for example, the following configuration adds a new subdomain account.mycompany.co.ukto the configuration example used in View cookie domains.{ "domains": [ "sso.mycompany.co.uk", "banking.mycompany.co.uk", "account.mycompany.co.uk" ] }Show response
{ "domains": [ "sso.mycompany.co.uk", "banking.mycompany.co.uk", "account.mycompany.co.uk" ] }An asynchronous process updates the environment’s cookie domain configuration. This process can take up to 10 minutes to complete.
Manage cookie domains using the admin console
You can find background information on cookie domains in Control cookie scope for custom domains.
Advanced Identity Cloud always writes cookies to your default tenant FQDN to ensure you retain access. Use the Advanced Identity Cloud admin console to view or edit the other domains or subdomains where your tenant environment writes cookies.
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right).
-
Click Tenant Settings.
-
Click Global Settings, then click Cookie.
-
Review the cookie domains configured in the Additional Cookie Domains field:
-
Each cookie domain is displayed in the field as a tag:
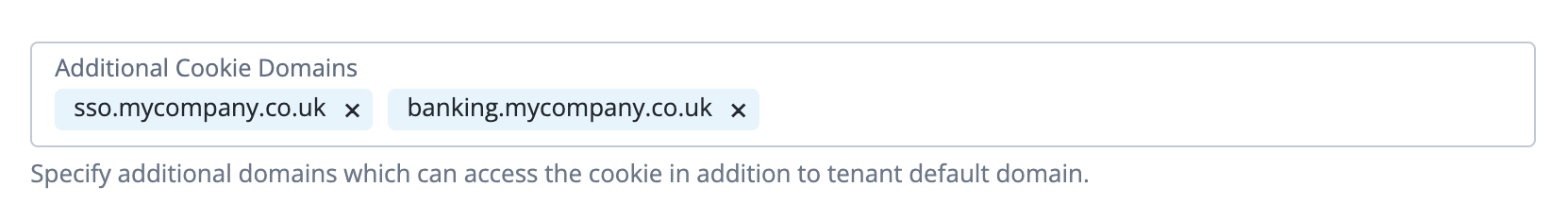
-
To add a cookie domain:
-
Click inside the Additional Cookie Domains field to give it focus and display a text prompt below the tags.
-
Enter a cookie domain value (for example,
account.mycompany.co.uk). -
Click an area outside the text prompt (or press enter) to create a tag for the new cookie domain value.
-
-
To delete a cookie domain, click the close icon () on the right of the cookie domain’s tag.
Before removing a domain or subdomain from the configuration, you must first update any existing applications that rely on cookies set using that domain or subdomain.
-
-
If you made changes in the previous step, click Save to confirm them.
An asynchronous process updates the environment’s cookie domain configuration. This process can take up to 10 minutes to complete.
Application management (legacy)
|
The topics in this section are for tenants created before January 12, 2023. Learn more in Application management migration FAQ. |
Your applications act as clients to PingOne Advanced Identity Cloud. Ping Identity uses both OAuth 2.0 and OpenID Connect protocols to protect your applications. When you register a supported application or service, Advanced Identity Cloud sets the OAuth 2.0 grant type based on the type of application you’re registering. Advanced Identity Cloud also sets OpenID Connect default options for you. You can customize configuration in the application’s client profile.
To get started, first register your application or service to your tenant. Then, create a client profile for the application or service.
You can view and manage all your applications on the Applications page of the Advanced Identity Cloud admin console.
| The Advanced Identity Cloud admin console supports a maximum of 500 applications. |
Register an application or service
-
In the Advanced Identity Cloud admin console, go to Applications, and click + Add Application.
-
In the New Consumer App dialog box, choose the application type you want to register:
-
In the Web Application Credentials dialog box, enter a Client ID to be displayed in the Applications list, and if shown, enter a Client Secret.
-
Click Create Application.
Create a client profile
-
In the Advanced Identity Cloud admin console, click Applications.
-
In the Applications list, find the application name, then click More (), and choose Edit.
-
Review read-only Client Credentials:
Client Credentials
Discovery URI
AM URL base for OpenID Provider Configuration.
Default: http://openam.example.com:8088/openam/oauth2Client ID
Identifier used to register your client with AM’s authorization server, and then used when your client must authenticate to AM.
Client Secret
Password used to register your client with AM’s authorization server, and then used when your client must authenticate to AM.
-
Edit General Settings:
General Settings
Name
Specify a client name to display to the resource owner when the resource owner is asked to authorize client access to protected resources.
App Logo URI
Specify the location of your custom logo image file.
Description
Specify a client description to display to the resource owner when the resource owner is asked to authorize client access to protected resources.
Sign-in URLs
Custom URL for handling sign on. Overrides the default sign-on page.
Sign-out URLs
Custom URL for handling sign off. Example: https://client.example.com:8443/am/XUI/?realm=/#logout.
Grant Types
Specify the set of OAuth 2.0 grant types, also known as grant flows, allowed for this client:
- Authorization Code
-
(default) Instead of requesting authorization directly from the user, your client application or service directs the user to an authorization server (Advanced Identity Cloud).
- Back Channel Request
-
- Implicit
-
The client is issued an access token directly. No intermediate credentials (such as an authorization code) are issued. This grant type can potentially pose a security risk. Learn more in Implicit grant.
- Resource Owner Password Credentials
-
Username and password can be used directly as an authorization grant to obtain an access token. The credentials should only be used when there is a high degree of trust between the user and the client application or service.
- Client Credentials
-
Used when the client acts on its own behalf or requests access to protected resources based on previously-arranged authorization.
- Refresh Token
-
Credentials used to obtain access tokens.
- Device Code
-
Authorizes a client device, such as a smarthome thermostat, to access its service on an end user’s behalf. For example, the end user could log in to the thermostat service using a cell phone to enter a code displayed on the thermostat.
- SAML 2.0
-
Leverages the REST-based services provided by AM’s OAuth 2.0 support. Maintains existing SAML 2.0 federation implementation.
Scopes
Specify scopes that display to the resource owner when they authorize client access to protected resources.
The
openidscope is required. -
Edit Advanced Settings:
Access
Add Default Scopes
Scopes to be set automatically when tokens are issued. The
openidscope is required.Add Response types
Specify the response types that the client uses. The response type value specifies the flow that determines how the ID token and access token are returned to the client. By default, the following response types are available:
-
︎
code. Specifies that the client application requests an authorization code grant. -
token. Specifies that the client application requests an implicit grant type and requests a token from the API. -
id_token. Specifies that the client application requests an ID token. -
code token. Specifies that the client application requests an access token, access token type, and an authorization code. -
token id_token. Specifies that the client application requests an access token, access token type, and an ID token. -
code id_token. Specifies that the client application requests an authorization code and an ID token. -
code token id_token. Specifies that the client application requests an authorization code, access token, access token type, and an ID token.
Add Claims
Claims can be entered as simple strings, such as
name,email,profile, orsub. Or, as a pipe-separated string in the format:scope|locale|localized description. For example,name|en|Full name of user.Allow wildcard ports in redirect URLs
Specify whether AM allows the use of wildcards (* characters) in the redirection URI port to match one or more ports.
The URL configured in the redirection URI must be either localhost, 127.0.01, or ::1. For example, http://localhost:*/, https://127.0.0.1:80*/, or https://[::1]:*443/.
Enable this setting, for example, for desktop applications that start a web server on a random free port during the OAuth 2.0 flow.
Authentication
Token Endpoint
Authentication MethodAuthentication method client uses to authenticate to AM.
Choose one:-
client_secret_basic. Clients authenticate using the HTTP Basic authentication scheme after receiving a client_secret value. -
client_secret_post. Clients authenticate by including the client credentials in the request body after receiving a client_secret value. -
private_key_jwt. Clients sign a JSON web token (JWT) with a registered public key.
Token Endpoint Authentication Method (Client Type)
-
Confidential clients can maintain the confidentiality of their credentials. For example, a web application runs on a server where its credentials are protected.
-
Public clients run the risk of exposing their passwords to a host or user agent. For example, a JavaScript client running in a browser may be accessible to the public.
Implied Consent
When enabled, the resource owner will not be asked for consent during authorization flows. The OAuth2 Provider must also be configured to allow clients to skip consent.
OAuth 2.0 Mix-Up Mitigation active
Enable this setting only if this OAuth 2.0 client supports the OAuth 2.0 Mix-Up Mitigation draft; otherwise AM will fail to validate access token requests received from this client.
Add Default ACR values
Default Authentication Context Class Reference values. Specify strings that will be requested as Voluntary Claims by default in all incoming requests.
Add Request URIs
Specify request_uri values that a dynamic client would pre-register.
Client JWT Bearer
Public KeyA base64-encoded X509 certificate in PEM format used to obtain the client’s JWT bearer public key. The client uses the private key to sign client authentication and access token request JWTs, while AM uses the public key for verification.
Subject Type
Default value is public.
-
Choose pairwise if you want each client to receive a different subject value. This prevents correlation between clients.
-
Choose public if you want each client to receive the same subject value.
Default Max Age
Enable this option to enforce a default maximum age of ten minutes. If the user session is not currently active, and if more than ten minutes have passed since the user last authenticated, then the user must be authenticated again.
Use Certificate-Bound Access Tokens
Enable this option if you want access tokens issued to this client to be bound to an X.509 certificate. When enabled, access tokens will use the X.509 certificate to authenticate to the
access_tokenendpoint.Token Lifetimes
Authorization code lifetime (seconds)
The time an authorization code is valid for.
Default value: 120Access token lifetime (seconds)
The time an access token is valid for, in seconds
If you set the value to 0, the access token will not be valid. A maximum lifetime of 600 seconds is recommended. Default value: 3600Refresh token lifetime (seconds)
The time a refresh token is valid for.
If this field is set to -1, the refresh token will never expire. Default value: 604800JWT token lifetime (seconds)
The amount of time the JWT is valid for. Default value: 3600
Consent Screen
Add Display Name
Custom user-facing title. In this example, MyClient.
Add Display Description
User-facing instruction text. In this example, "This application is requesting the following information:"
Add Privacy Policy URI
URI containing the client’s privacy policy documentation. The URI is displayed as a link in the consent page.

Client Management
Access Token
Specify the
registration_access_tokenvalue that you provide when registering the client, and then subsequently, when reading or updating the client profile.Session Management
Client Session URI
Specify the relying party (client) URI to which the OpenID Connect Provider sends "session changed" notification. Message is sent using the HTML 5 postMessage API.
Endpoint Response Formats
User info response format
Specify the output format from the
userinfoendpoint.
The supported output formats are:-
(default) User info JSON response format.
-
User info encrypted JWT response format.
-
User info signed JWT response format.
-
︎ User info signed then encrypted response format.
Token introspection response format
Specifies the format of the token introspection response. The possible values for this property are:
-
JSON response format
-
Signed JWT response format
-
Signed then encrypted JWT response format
Signing and Encryption
Public key selector
Select the public key for this client, which comes from the JWKs_URI, manual JWKs, or X.509 field.
JSON Web Key URI
The URI that contains the client public keys in JSON web key format.
JSON Web Key
Raw JSON web key value containing the client public keys.
ID Token Encryption Public Key
Base64-encoded public key for encrypting ID tokens.
Enable ID Token Encryption
When enabled, encryption uses the algorithm with which the ID token must be encrypted. Default algorithm value is RSA1_5 (RSAES-PKCS1-V1_5).
-
-
Click Save.
Supported application types
When you register an application or service, Advanced Identity Cloud automatically sets the optimal configuration for you. To change the default settings, edit the client profile.
Native / SPA
Native applications are developed for specific platforms or devices. Examples include the applications on mobile phones and applications dedicated to the macOS platform.
Single-page applications (SPAs) are OAuth 2.0 clients that run in a user’s web browser.
SPAs use PKCE to verify the client because SPAs do not have a way to secure the client_secret value.
PKCE stands for Proof Key Code Exchange; a security standard explained in the IETF specification
Proof Key for Code Exchange by OAuth Public Clients.
For a deep dive on how ForgeRock implements PKCE for native and SPA applications, learn more in Authorization code grant with PKCE.
Web
Web applications are OAuth 2.0 clients that run on a web server. End users (resource owners) access web applications using a web browser. The application makes API calls using a server-side programming language. The end user has no access to the OAuth 2.0 client secret or any access tokens issued by the authorization server.
Service
Machine-to-machine (M2M) applications interact with an API and no user involvement is necessary. The application can ask for an access token without involving a user in the process. A smart meter that tracks your utility usage and wearable devices that gather and communicate health data use services and M2M applications.
OAuth 2.0 and OpenID Connect
Advanced Identity Cloud uses OAuth 2.0 and OpenID Connect to protect your applications.
OAuth 2.0
Advanced Identity Cloud provides an authorization service in the OAuth 2.0 authorization flow. OAuth 2.0 lets you set up access to your resources without sharing end-user account information. For a deep dive, learn more in RFC6749.
|
You may encounter domain validation prompts when using forgeblocks.com and id.forgerock.io domains as redirect URLs in your Google OAuth 2.0 applications. To resolve this, you must use a custom domain, and then set up domain verification with Google. |
|
You could encounter
A custom domain acts as a realm DNS alias, so when it is used as a redirect URL, Advanced Identity Cloud implicitly knows which realm to use. |
OpenID Connect
OpenID Connect (OIDC) provides an identity layer on top of OAuth 2.0. OIDC lets a client make assertions about the user’s identity and their means of authentication. For a deep dive, learn more in OIDC grant flows.
What’s in the client profile
Changing the client profile settings requires a working knowledge of OAuth 2.0, its grant types, and its components. If no one has given you direction on how to configure the client profile, you’ll want to read up on some basic concepts.
Scopes
Scopes limit your client application’s access to end users' resources. For a deep dive on how scopes work, learn more in Scopes.
Grant types
Grant types, also known as grant flows, describe how your application or service access gets an access token. Learn more about grant types in OAuth 2.0 grant flows.
Claims
Claims convey information about the end user to your client application or service. For a deep dive on claims, learn more in the Claims.
Access tokens
Your applications and services use access tokens when making requests on behalf of a user. Tokens provide proof that your application or service is authorized to access the end user’s data. For a deep dive on access tokens, learn more in Advanced Identity Cloud as authorization server.
Keys
Keys protect sensitive information that Advanced Identity Cloud needs to both send and receive. You can store keys in ESV secrets, then use them in OAuth 2.0 authentication flows by mapping the ESVs to secret labels.
Test SAML 2.0 SSO using JSP flows
|
The topics in this section are for tenants created before January 12, 2023. Learn more in Application management migration FAQ. |
SAML 2.0 helps organizations to share(or federate) identities and services without having to manage the identities or credentials themselves.
These instructions describe how to launch an SP-initiated JSP flow to test SAML 2.0 SSO. PingOne Advanced Identity Cloud acts as the authentication service provider (SP) in a circle of trust (CoT). For this test, a self-managed AM instance acts as the identity provider (IDP).
Task 1: Set up an SP and an IDP
-
Set up the Advanced Identity Cloud AM instance as a service provider:
-
In the AM native admin console, go to
Realm Name > Applications > Federation > Entity Providers. -
Click + Add Entity Provider > Hosted, and add a hosted entity provider:
-
Entity ID: Enter a unique identifier. Example: Cloud-SP.
-
Service Provider Meta Alias: Provide an SP alias. Example:
cloud-sp.
-
-
Export the SP metadata to an XML file. Example export metadata URL:
https://<tenant-FQDN>/am/saml2/jsp/exportmetadata.jsp?entityid=<SP-Entity-ID>&realm=/alpha.
-
-
Set up the self-managed AM instance as an identity provider:
-
In the AM self-managed admin console, go to
Top Level Realm > Applications > Federation > Entity Providers. -
Click + Add Entity Provider > Hosted, and add a hosted entity provider:
-
Entity ID: Enter a unique identifier. Example: AM-IDP.
-
Meta Alias: Provide an IDP alias. Example:
am-idp.
-
-
Export the IDP metadata to an XML file. Example export metadata URL:
https://<IDP-host-FQDN>/am/saml2/jsp/exportmetadata.jsp?entityid=<IDP-Entity-ID>.
-
-
In the Advanced Identity Cloud AM instance, add a remote entity provider by importing the IDP metadata:
-
In the AM native admin console, go to
Realm Name > Authentication > Federation > Entity Providers. -
Click + Add Entity Provider > Remote.
-
Import the IDP metadata.
-
-
In the self-managed AM instance, add a remote entity provider by importing the SP metadata:
-
In the AM self-managed admin console, go to:
Top Level Realm > Authentication > Federation > Entity Providers. -
Click + Add Entity Provider > Remote.
-
Import the SP metadata.
-
-
Create a user profile on the SP and IDP:
-
SP: In the AM native admin console, go to Identities and add a user identity.
-
IDP: In the AM self-managed admin console, go to Identities and add a user identity.
-
Task 2: Create an SP circle of trust
-
In the Advanced Identity Cloud AM instance, create a circle of trust:
-
In the AM native admin console, go to
Realm Name > Applications > Federation > Circles of Trust. -
Click + Add Circle of Trust.
-
On the New Circle of Trust page, provide a name, then click Create.
-
On the CoT page, provide CoT details.
CoT details:
-
Description: Enter a unique identifier.
-
Entity Providers: Choose the entity IDs for the SP and IDP.
Examples:Cloud-SPAM-IDP
-
-
Click Save Changes.
-
-
In the Advanced Identity Cloud AM instance, create a federation module:
-
In the AM native admin console, go to
Realm Name > Authentication > Modules. -
On the Modules page, click Add Module. Enter module details:
-
Name: Must be named
Federation. -
Type: Must be type
Federation.
-
-
Click Save Changes.
-
-
In the Advanced Identity Cloud AM instance, configure the page the browser displays upon successful SSO:
-
In the AM native admin console, go to
Realm Name > Applications > Federation > Entity Providers. -
In the
Cloud-SPentity provider page, select the Advanced tab. -
In the Relay State URL List field, add the target URL for the SP end-user sign-in page.
Example:https://<tenant-FDQN>/enduser/?realm=alpha#/dashboard. -
Click Save Changes.
-
Task 3: Create an IDP circle of trust
-
In the AM self-managed admin console, go to
Top Level Realm > Applications > Circles of Trust. -
Click + Add Circle of Trust.
-
On the New Circle of Trust page, provide a name, then click Create.
-
On the CoT page, provide CoT details.
CoT details:
-
Description: Enter a unique identifier.
-
Entity Providers: Choose the entity IDs for the SP and IDP.
Examples:Cloud-SPAM-IDP.
-
-
Click Save Changes.
Task 4: Test SAML 2.0 SSO
-
In a browser, go the JSP URL to launch an SP-initiated JSP flow. Example:
https://<tenant-FQDN>/am/saml2/jsp/spSSOInit.jsp?realm=/alpha/&metaAlias=/alpha/cloud-sp&idpEntityID=AM-IDP&binding=urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST&NameIDformat=urn:oasis:names:tc:SAML:2.0:nameid-format:persistent&RelayState=https://<tenant-FQDN>/enduser/?realm=alpha#/dashboard. -
On the IDP sign-in page, enter the user’s credentials:
Keep this session open. The IDP authenticates the user, then the browser redirects the user back to the SP sign-in page.
-
On the SP sign-in page, enter the user’s credentials:
After this second successful authentication, the user’s SP identity is linked to, or federated with, the user’s IDP identity.
The browser redirects to the SP end-user page.
-
Sign the user out of both the SP and IDP.
-
Go to the IDP end-user sign-in page, and enter the user’s credentials.
When the user is successfully authenticated, the browser redirects to the SP end-user page specified in Relay State URL List.
Gateways & agents
Integrate PingOne Advanced Identity Cloud with PingGateway and policy agents to secure access to your web resources.
PingGateway
PingGateway integrates your web applications, APIs, and microservices with Advanced Identity Cloud. PingGateway enforces security and access control without modifying your applications or the containers where they run—whether on premises, in a public cloud, or in a private cloud.
Based on reverse proxy architecture, PingGateway intercepts client requests and server responses. In this process, PingGateway enforces user or service authentication and authorization to HTTP traffic. Advanced Identity Cloud acts as the authentication and authorization provider.
PingGateway can also conduct deep analysis, then throttle and transform requests and responses when necessary.
Learn more in the PingGateway Guide for Advanced Identity Cloud. In particular, refer to these detailed instructions and examples:
Policy agents
Policy agents are PingAM add-on components. They operate as policy enforcement points (PEPs) for websites and applications.
Policy agents natively plug into web or applications servers. The agents intercept inbound requests to websites, and interact with AM to:
-
Ensure that clients provide appropriate authentication.
-
Enforce AM resource-based policies.
Use Web Agents to protect services and web resources hosted on a web or proxy server. Use Java Agents to protect resources hosted on application or portal servers.
Although both agents enforce authentication and authorization to protected resources, they differ in the way they derive policy decisions and enforce them.
For examples of how to transition from on-premises access management to Advanced Identity Cloud without changing the architecture of the agent-based model, learn more in these guides:
- Web Agent Example
- Java Agent Example
Password policy
Configure a password policy in PingOne Advanced Identity Cloud when you want a customized rule for creating valid sign-in passwords. The password policy applies to end users who sign in to your registered apps within a realm.
|
You can configure only one password policy per realm. |
By default, Advanced Identity Cloud password policy is set to the minimum security requirements established by the National Institute of Standards and Technology (NIST). Any changes you make to the password policy must conform to requirements contained in their guidelines. Learn more in NIST Digital Identity Guidelines.
Configure a password policy
-
In the Advanced Identity Cloud admin console, go to Security > Password Policy.
-
Choose the realm the password policy will apply to.
-
Edit password policy details.
Password length
When enabled, the policy requires a password with the specified minimum number of characters. No maximum.
Cannot include
Options to restrict the use of any of the following in the policy:
-
More than two consecutive characters (Example: aaaaaa)
-
Commonly used passwords (Examples: qwerty or 12345678)
-
Values in certain user attributes:
-
In the Forbidden Realm realm - User attributes list, select user attributes to validate passwords against.
-
In the Minimum n characters for each attribute field, enter a substring length between 3 - 64 to use when validating passwords against user attribute values. The default is 5 characters.
-
Must contain
When enabled, the policy requires the use of a specified 1 - 4 of the following:
-
Upper case letter
-
Lower case letter
-
Number
-
Space, pipe, or special character:
( ! " # $ % & ' ( ) * + , - . / : ; < = > ? @ [ \ ] ^ _ ` { } ~ ) .
Cannot reuse
When enabled, the policy restricts the end user from reusing their current password and the specified number of previously set passwords.
For example, if you set this value to 3, the end user can’t reuse their current password or any of their last three passwords. The end user must create a new password that is different from any of those four passwords.
Force password change
When enabled, the policy forcibly expires each end-user password after the specified number of days, months, or years have elapsed from when the password was set.
To handle expired passwords in an end-user journey, use theExpiredoutcome in the Identity Store Decision node.Refer to the considerations in Force end-user password changes before using this policy setting. -
-
Click Save.
Force end-user password changes
You can combine a password policy and the Identity Store Decision node to expire end-user passwords in a journey; the Force password change policy setting lets you define an expiry time interval, which is measured for each end user from when their password was last set.
If you are introducing such a policy for the first time, you may want to process your end users in batches in order to improve messaging about the changes. The following sections describe two high-level strategies to achieve this.
|
If you are considering forcing your end users to change their passwords, review the NIST Digital Identity Guidelines. In particular, NIST no longer recommends scheduled password changes; learn more in Usability Considerations by Authenticator Type. The NIST guidelines are continually refined, so you should keep them in mind when setting password policy. |
Strategy 1: Target segments of end users
Adapt the end-user login journey to use dynamic groups or user properties to target a segment of end users to reset their password.
Advantage: You can segment users any way you like. For example, you may have a set of end users who could struggle with a password reset. You could add a property to each end user in the set and initially exclude end users with that property from a password reset. Then, at a later time, remove the exclusion when support is available for those end users.
Disadvantage: Creating new dynamic groups with large numbers of end users can incur a significant performance cost.
Strategy 2: Target oldest passwords first
Adapt the end-user login journey to target all end users to reset their password, but initially set a very long expiry time interval to target the oldest passwords first. Then periodically reduce the expiry time interval to eventually target all passwords.
Advantage: This strategy segments end users by the date of their last password reset. Additionally, end users with the oldest passwords are targeted first.
Password timestamps
Password timestamps let you view or query when a user password was last changed and when it is set to expire.
The following timestamp fields and properties are available:
| Field name on the user page | Property name in the managed object configuration |
|---|---|
Password Last Changed Time |
|
Password Expiration Time |
|
passwordLastChangedTimecurl \
--header "Authorization: Bearer <access-token>" \
--header "Accept-API-Version: resource=1.0" \
--request GET \
"https://<tenant-env-fqdn>/openidm/managed/realm-name_user?_queryFilter=passwordLastChangedTime%20ge%20%222024-01-01T21:22:06.274Z%22&_fields=_id"
{
"result": [
{
"_id": "453a73a9-3f50-4b04-8115-f3915fd1dd89",
"_rev": "fa876a46-82e6-4a11-a3f4-6b4919815ea4-5851"
}
],
...
}Journey nodes
This page lists the authentication nodes available for you to use in PingOne Advanced Identity Cloud journeys.
| You can also create your own custom nodes if none of the available nodes meet your business needs. |
|
Even though they appear in the UI, the following nodes are incompatible with Advanced Identity Cloud and their reference documentation isn’t provided:
|
Multi-factor authentication nodes
Use the following nodes to configure journeys with multi-factor authentication capabilities:
Risk management authentication nodes
Use the following nodes to examine the perceived risk and act on it:
Behavioral authentication nodes
Use the following nodes to adjust the behavior of authentication journeys:
Contextual authentication nodes
Use the following nodes to change the journey or set a cookie based on the authentication context:
Federation authentication nodes
Use the following nodes to configure journeys with federation capabilities:
Identity management authentication nodes
Use the following nodes to perform identity management during an authentication journey:
Journeys
PingOne Advanced Identity Cloud comes with pre-configured end-user journeys. A journey is an end-to-end workflow invoked by an end user or device. Advanced Identity Cloud provides templates for common end-user journeys; for example, account registration and sign-in.
Journeys are made up of nodes, which define actions taken during authentication. Each node performs a single task during authentication, for example, collecting a username or making a simple decision based on a cookie.
The following table describes how you can configure journeys to customize the authentication experience for end users.
| Task | Resources |
|---|---|
Modify the layout and appearance of journeys. |
Use the Hosted pages. |
Modify the journey templates. |
|
Create a custom journey. |
|
Set a default journey. |
Configure Advanced Identity Cloud to display a default journey to end users. |
Create journeys based on device context. |
Use the Ping SDKs to configure device profiling authentication. |
Customize the outcome of an authentication journey with JavaScript. |
Use the auth scripting editor to create and manage scripts that run during the course of the authentication journey. You can create and include script types such as the following: Learn more in auth script types. |
Configure an application journey |
Associate an authentication journey with a SAML 2.0 app or an OAuth 2.0/OIDC app to let users authenticate with a specific journey as part of the federation process. Learn more in: |
Always run journeys |
When you create a journey, you have the option to configure the journey to always run. This setting lets you enforce journeys to always run regardless of any existing user sessions or whether the journey is initiated over REST or by redirect. Enable this option when you create custom journeys. |
Authentication templates
Login
Create a basic Login journey for end users to authenticate and sign in to an app or service with a username and password.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys > Login.
-
Hover over the journey schematic, and click Edit.
-
Enter information for each node in the journey:
Learn about available nodes in Journey nodes or how to create your own node in custom nodes.
-
To test the journey, copy the Preview URL, and paste the URL into a browser using incognito mode.
-
When you’re satisfied with your journey, click Save.
Learn more about the Login journey in Login with self-service.
|
If you implement account lockout using the Account Lockout node, it creates a persistent lockout on user accounts. User accounts can be unlocked by a tenant administrator. Advanced Identity Cloud also supports configurable persistent and duration account lockout. Learn more in Account lockout. |
Device profiling
Use the ForgeRock SDK to create journeys that let inanimate objects authenticate based on device context. Cell phones and smartwatches are examples of devices that have their own identities. Device context provides Advanced Identity Cloud with information about how or where a device is used to authenticate.
For detailed instructions, learn more in Configure device profiling authentication.
User self-service templates
Registration
Create a registration journey to let end users create their own account for an app or service.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys > Registration.
-
Hover over the journey schematic, and click Edit.
-
Enter information for each node in the journey:
Learn about all available nodes in Journey nodes.
-
To test the journey, copy the Preview URL, and paste the URL into a browser using incognito mode.
-
When you’re satisfied with your journey, click Save.
Learn more about the Registration journey in User self-registration.
Progressive profile
Create a Progressive Profile journey to trigger a conditional event in the journey.
The default journey triggers a reminder to set preferences for receiving news and special offers. The reminder is displayed only if the end user logs in three times without selecting preferences. If the end user makes no selection, the reminder expires and is not displayed again. If the end user selects one or more options, the preferences get set in the end user’s profile.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys > Progressive Profile.
-
Hover over the journey schematic, and click Edit.
-
Enter information for each node in the journey:
Learn about all available nodes in Journey nodes.
-
To test the journey, copy the Preview URL, and paste the URL into a browser using incognito mode.
-
When you’re satisfied with your journey, click Save.
Learn more about the Progressive Profile journey in Progressive profile.
Update password
Create an Update Password journey to let end users change their passwords. End users may be required to change passwords at regular intervals or if a password is compromised.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys > Update Password.
-
Hover over the journey schematic, and click Edit.
-
Enter information for each node in the journey:
Learn about all available nodes in Journey nodes.
-
To test the journey, copy the Preview URL, and paste the URL into a browser using incognito mode.
-
When you’re satisfied with your journey, click Save.
Learn more about the Update Password journey in Password updates.
Reset password
Create a Reset Password journey to let end users change their existing passwords. End users typically reset their passwords when they’ve forgotten the password they set.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys > Reset Password.
-
Hover over the journey schematic, and click Edit.
-
Enter information for each node in the journey:
Learn about all available nodes in Journey nodes.
-
To test the journey, copy the Preview URL, and paste the URL into a browser using incognito mode.
-
When you’re satisfied with your journey, click Save.
Learn more about the Reset Password journey in Password reset.
Forgotten username
Create a Forgotten Username journey to let end users retrieve their username from their user account data.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys > Forgotten Username.
-
Hover over the journey schematic, and click Edit.
-
Enter information for each node in the journey:
Learn about all available nodes in Journey nodes.
-
To test the journey, copy the Preview URL, and paste the URL into a browser using incognito mode.
-
When you’re satisfied with your journey, click Save.
Learn more about the Forgotten Username journey in Username recovery.
Custom journeys
Create a custom journey when none of the ready-to-use templates suits your needs.
-
In the Advanced Identity Cloud admin console, click Journeys > Journeys.
-
Click + New Journey.
-
Enter journey details:
-
Name: Name to display in the Journeys list.
-
Identity Object: Identifier for the user or device to authenticate.
-
(Optional) Description: Summarize end user interaction.
-
(Optional) Tags: For organizing journeys to make them easier to find.
-
-
(Optional) Enable journey options:
-
Default journey for end users: Sets this journey as the default.
-
Override theme: Specify a custom theme for this journey.
-
Run journey for all users regardless of current session: Configure the journey to execute regardless of any existing user sessions or whether the journey is initiated over REST or by redirect. Always running a journey doesn’t necessarily require the user to authenticate every time.
For example, if you configure an authentication journey to first check for a valid session and a known device profile, the user could proceed directly to the successful outcome as long as they pass the checks. Alternatively, configure a journey to require multi-factor authentication every time.
You can’t configure a journey to always run when it’s set as the default journey.
Also, to prevent unexpected behavior in the authentication flow, don’t configure a journey to always run when it’s mapped to the default ACR.
Learn more in Configure an authentication journey to always run.
-
Inner Journey: Prevent the journey from being used outside of its parent journey.
Learn more in Disable direct access through a child journey.
-
-
Click Create journey.
-
Use the journey editor to create your custom journey.
Drag nodes from the palette and arrange them on the blank canvas. -
Provide information for each node, and connect nodes.
Learn about all available nodes in Journey nodes.
-
To test the journey, copy the Preview URL, and paste the URL into a browser using incognito mode.
-
When you’re satisfied with your journey, click Save.
Default journey
Advanced Identity Cloud displays the default journey to end users when they access a default webpage URL. For example, application webpages commonly display a sign-in link. When the end user clicks the link, the Login journey is invoked by default.
Set a default end-user journey as follows:
-
Set a new journey as the default:
-
In the Advanced Identity Cloud admin console, click Journeys > New Journey.
-
On the New Journey page, enable the option Default journey for end users.
-
-
Set an existing journey as the default:
-
In the Advanced Identity Cloud admin console, click Journeys > Journeys to view the list of journeys.
-
Select a journey, and click and Set as default.
-
Deactivate journeys
Deactivate a journey to prevent end users using it to authenticate. If you deactivate it, you can reactivate it at any time.
For example, if you are building a new journey in your development environment and you need to run a promotion, you can deactivate the journey prior to the promotion so that there’s no risk of the journey being discovered and used by end users in your upper environments and potentially allowing insecure access. You can activate the journey in your development environment again after a promotion.
Ping Identity recommends you deactivate any default journeys not in use. Learn more in Deactivate unused or insecure journeys.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys to view the existing journeys list.
-
Find the journey.
-
Click its More () menu:
-
To deactivate the journey, choose Deactivate, then in the Deactivate Journey dialog, click Deactivate.
-
To activate the journey, choose Activate.
-
You can also deactivate and activate a journey using the More () menu in the journey editor.
Duplicate journeys
Duplicate a journey to preserve a template for future use. For example, if you are testing a journey, start with a duplicate. Give the duplicate journey a unique name.
Create a duplicate journey in the following ways:
-
Click Journeys > Journeys to view the existing journeys list. Find the template name. Then, click its More () menu, and choose Duplicate.
-
In the Journey editor, click More (), and choose Duplicate.
Export journeys
You can export journeys, including all dependencies like nodes, inner journeys, and scripts of any type apart from library scripts.
Use this feature to export journeys from one environment, such as a development environment, to another.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys.
-
Check the checkbox beside one or more journeys.
-
Click Export.
-
View the information on the Export Journeys page.
-
Click Export.
Import journeys
You can import journeys, including all dependencies such as nodes, inner journeys, and scripts, and scripts of any type apart from library scripts.
Use this feature to import a journey from one environment, such as a development environment, to another.
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys, and click Import.
-
Download or skip back up:
-
Download a backup of your existing journeys so that you can restore them in case of error or unexpected behavior during or after import:
-
To view the backup summary, click Show backup summary.
-
Click Download Backup.
-
-
Skip the download:
-
Click Skip Backup.
-
In the dialog box, click Skip Backup again.
-
-
-
Configure the import:
-
On the Import Journeys page, browse to and select a JSON file that contains the journey’s configurations to import.
-
Select the identity object that the journey authenticates.
-
In the Conflict Resolution section, choose how the system resolves import conflicts:
-
Overwrite all conflicts (default)
-
Manually pick conflict resolution
-
-
Click Next.
-
Review the information on the Import Summary page.
-
Click Start Import.
-
On the Import Complete page, click Done.
-
Annotate journeys
You can annotate a journey using comments and sticky notes. Annotations help you share information when multiple tenant administrators work on the same journey.
Comments
Use comments to have a conversation with other tenant administrators about a journey. Comments are associated with specific nodes in a journey and only one comment can be added per node. You can reply to comments multiple times and delete them if necessary. Comments and replies are visible to all tenant administrators. Comments and replies are saved automatically.
-
In the Advanced Identity Cloud admin console, go to Journeys, and click a journey name to open it in the journey editor.
-
To add a comment:
-
In the journey editor, click the Comment icon ().
-
In the journey schema, click the node to which you want to add a comment. A comment field displays with the placeholder text Add a comment.
-
In the comment field, enter your comment, then click the arrow icon (). The comment is added to the node. A comment bubble displays on the top right of the node to indicate that it has a comment. The comment bubble shows the initials of the tenant administrator who made the comment.
-
-
To set a color for a comment:
-
In the journey schema, click a comment bubble on a node. This opens the comment pane.
-
Click a colored circle at the top of the comment pane. This sets the color of the comment bubble, the comment, and any replies. Setting colors makes it easier to distinguish between multiple comment bubbles on the node.
-
-
To reply to a comment:
-
In the journey schema, click a comment bubble on a node. This opens the comment pane.
-
Click the field with the placeholder text Reply, enter your reply, then click the arrow icon (). You can reply to a comment multiple times, creating a thread of replies.
-
(Optional) To delete a reply, click the ellipsis icon () beside it, then click Delete.
-
-
To delete a comment and all its replies:
-
In the journey schema, click a comment bubble on a node. This opens the comment pane.
-
Click the ellipsis icon () at the top of the comment pane, then click Delete.
-
Sticky notes
Use sticky notes to add reminders or other information about a journey. Sticky notes aren’t associated with specific nodes in a journey. Sticky notes are visible to all tenant administrators. Each tenant administrator can add multiple sticky notes. Sticky notes are saved automatically.
-
In the Advanced Identity Cloud admin console, go to Journeys, and click a journey name to open it in the journey editor.
-
To add a sticky note:
-
In the journey editor, click the Add Sticky Note icon ().
-
In the journey schema, click anywhere outside a node. An empty sticky note displays and automatically takes focus.
-
Enter your comment, then click anywhere outside the sticky note to save it.
-
-
To edit a sticky note:
-
Click a sticky note to open it for editing. The sticky note automatically takes focus.
-
Edit the text, then click anywhere outside the sticky note to save it.
-
-
To set a color for a sticky note:
-
Click a sticky note to open it for editing.
-
Click a colored circle at the top of the sticky note.
-
-
To delete a sticky note:
-
Click a sticky note to open it for editing.
-
Click the ellipsis icon () at the top of the sticky note, then click Delete.
-
Delete journeys
Deleting a journey is a permanent operation. You won’t be able to retrieve it after it’s deleted.
Delete a journey in the following ways:
-
In the Advanced Identity Cloud admin console, go to Journeys > Journeys, and check the checkbox beside one or more journeys. Click Delete Journeys.
-
In the Journey editor, click More (), and choose Delete.
| You can’t delete a journey if it’s referenced by a SAML 2.0 app or an OAuth 2.0 client. |
Debug end-user journeys
You can debug end-user journeys in your PingOne Advanced Identity Cloud development environment as you create them. By setting a journey to debug mode, you can view information stored in shared, transient, and secure state, as you navigate the journey. This lets you confirm that information is being passed correctly from node to node in the journey.
Enable debug mode
Enable debug mode to log debug information as you navigate a journey.
-
In the Advanced Identity Cloud admin console, go to Journeys, and select a journey.
-
Hover over the journey schematic, and click Edit.
-
In the journey editor, click the debug button (on the top right of the toolbar). The Debug panel opens.
-
In the Debug panel, enable Debug mode.
-
Select Enable Debug Popup to display debug logs as you navigate the journey. Learn more in view debug information in a popup window.
-
Click Save to save your journey with debug mode enabled.
|
View debug information in a pop-up window
View debug log output in a separate pop-up window, as you navigate a journey.
-
In the Advanced Identity Cloud admin console:
-
In the journey editor, copy the end-user journey URL from the Preview URL field (on the right, above the top toolbar).
-
In a new incognito browser window (or a separate browser):
-
Go to the end-user journey URL that you copied in the previous step.
-
The browser window should display an initial debug step in a new pop-up window. The pop-up window’s title is Debug Popup.
-
-
If the pop-up window doesn’t display, your browser might be blocking it:
-
Unblock it by following the instructions for your browser:
-
For Chrome, follow the instructions under the "Allow pop-ups and redirects from a site" section in this support article: https://support.google.com/chrome/answer/95472.
-
For other supported browsers, consult the browser’s documentation.
-
-
Refresh the browser window. The pop-up window should now display. If it doesn’t display, repeat the previous step and ensure that your browser isn’t blocking pop-ups.
-
-
Arrange the browser window and the pop-up window so that they’re both clearly visible.
-
Navigate the journey in the browser window, and monitor the debug output for each step in the pop-up window.
Shared, transient, and secure state
- Shared state
-
Used by nodes to store non-sensitive information required during the authentication flow.
- Transient state
-
Used by nodes to store sensitive information that Advanced Identity Cloud encrypts on round trips to the client.
- Secure state
-
Used by nodes to store decrypted transient state.
|
When debug mode is enabled, debug nodes are temporarily inserted between each node in the journey. Because debug nodes can change the state of node information, inserting them between each node in the journey can cause a problem if a later node expects to access information in a specific state. An example is when a node adds a password to transient state. The following debug node reads that password from transient state, which removes it. The next node in the journey expects to read the password from transient state, and when it tries to do so, this fails and causes an error. |
Journey solutions
The Ping Identity Marketplace includes prebuilt sample journeys for PingOne Advanced Identity Cloud, all certified by Ping Identity. These journeys provide a starting point for common identity use cases, helping you accelerate journey development. You can download and use them as templates to create your own user journeys.
Threat detection with PingOne Protect journey
The Ping Identity Marketplace includes a prebuilt authentication journey with threat detection to protect against threats such as fraudulent sign-on attempts.
The journey is intended as a template. Review and adapt it to meet your organization’s specific security policies and business requirements before deploying to a production environment.
| Journey name | Version | Download |
|---|---|---|
Authentication Journey with Threat Detection |
2.0 |
This guide details the prerequisites and configuration steps to implement this solution in your Advanced Identity Cloud tenant.
Learn more about Threat detection using PingOne Protect.
About the threat detection journey
This solution uses a parent journey and inner journeys to evaluate the risk level of a user’s sign-on attempt.
Example use case
A company needs to identify and prevent fraudulent authentication when an end user attempts to sign on from an unusual geographical location. The goal is to reduce fraud while ensuring a frictionless experience for legitimate users.
With the Advanced Identity Cloud authentication with threat detection journey, the user’s geographical location is evaluated as part of a real-time threat detection process. If a user attempts to sign on from a location that exceeds a defined radius from the user’s expected location, it’s considered medium or high risk, depending on the extent of the deviation. The user is either prompted to step up with multi-factor authentication (MFA) or is denied access. If authentication is blocked or requires further verification, the user is notified by email or SMS to confirm that the attempt was legitimate.
Journey components
The threat detection journey includes one parent journey and seven inner journeys that work together to handle the authentication and threat detection flow.
| Journey | Description | Configuration required? | ||
|---|---|---|---|---|
Threat Detection Journey with PingOne Protect (parent journey) |
Orchestrates the overall flow. It initializes variables, presents the sign-on page, calls the appropriate inner journeys, and records the final outcome for machine learning.
|
Yes |
||
Threat Detection - Inner Journey |
Uses the PingOne Protect nodes to initialize the SDK, capture user behavior signals, and evaluate risk. |
Yes |
||
MFA Device Registration - Inner Journey |
Manages the flow for registering a new MFA device, if required. |
Yes |
||
MFA Authentication - Inner Journey |
Handles the MFA challenge when a user needs to step up their authentication. |
Yes |
||
OATH Registration - Inner Journey |
Sets the registration flow for OATH-based MFA. |
No |
||
Push MFA Method Registration - Inner Journey |
Sets the registration flow for push-based MFA. |
No |
||
WebAuthn MFA Method Registration - Inner Journey |
Sets the registration flow for WebAuthn-based MFA. |
No |
||
Combined OATH And PUSH MFA Methods Registration - Inner Journey |
Sets the registration flow for OATH and push MFA. |
No |
Show the Threat Detection Journey with PingOne Protect (parent journey)
-
a A Scripted Decision node containing the initialize variables used in the authentication flow.
-
b The first call to the PingOne Protect Threat Detection - Inner Journey
-
c The second call to the PingOne Protect Threat Detection - Inner Journey for risk evaluation
-
d A call to the MFA Authentication - Inner Journey
-
e A call to the MFA Device Registration - Inner Journey
Task 1: Prepare your tenant environment
First, ensure you have the necessary prerequisites, then perform the required setup tasks in your tenant environment.
Before you begin
To implement the sample threat detection journey, you must have:
-
Tenant administrator access to your Advanced Identity Cloud development environment.
-
PingOne Protect enabled in your PingOne environment. Learn more in Getting started with PingOne Protect.
-
PingOne Protect integrated with Advanced Identity Cloud. Learn more in Integrate with PingOne Protect for risk evaluations.
-
Your PingOne Worker Service ID. This is required to connect to your PingOne instance and send it the necessary data to make risk evaluations. Learn more in Create a worker application in PingOne.
-
For MFA:
-
An SMTP email server. Required for email-based MFA.
-
If you’re using Twilio for phone-based MFA, a Twilio account with access to Twilio Verify.
-
-
Social authentication configured in your Advanced Identity Cloud environment. Learn more in Social authentication.
The sample journey uses Google and Facebook for social sign-on, but you can configure and enable any of the supported social identity providers. You can also disable social sign-on if you don’t need it in your authentication flow. -
A basic understanding of journeys and the Scripted Decision node.
Setup tasks
To get the journey working, you’ll first need to perform some setup tasks in your Advanced Identity Cloud tenant environment.
Add custom attributes to the alpha_user managed object
Several additional user attributes are required by the threat detection user journey. These attributes store information about the user’s verified email, geographical location, operating system (OS), and MFA devices.
Add the following custom attributes to the alpha_user managed object.
Learn more in Customize user identities using custom attributes.
| Name | Label | Type | Description |
|---|---|---|---|
|
|
String |
Confirms the user has verified their email address. |
|
|
String |
The city from which the user attempts to authenticate. This attribute is used in the |
|
|
String |
The state from which the user attempts to authenticate. This attribute is used in the |
|
|
String |
The OS of the device from which the user attempts to authenticate. |
|
|
Array |
Sets, fetches, and displays the user’s registered MFA devices. |
|
|
String |
The most recent MFA device registered by the user, used in the |
(Optional) Set an ESV variable for PingOne Protect analysis
The Prerequisites & Init Variables node in the parent journey contains a script that uses the protectAnalysisRequired variable to determine if PingOne Protect analysis is enabled. By default, this variable is set to true within the script.
To override this variable and control how PingOne Protect analysis is performed in different environments, you can set an Environment Secret & Variable (ESV) variable.
-
In the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > Environment Secrets & Variables.
-
Click the Variables tab.
-
Click + Add Variable.
-
In the Add a Variable modal, enter the following information:
Name
p1-protect-analysis-requiredType
stringDescription (optional)
PingOne Protect analysis requiredValue
true -
Click Save to create the variable.
-
Restart Advanced Identity Cloud services by applying updates in the Advanced Identity Cloud admin console.
Create the email templates
You’ll need to create the following email templates, which are used by Scripted Decision nodes to send emails at various points in the threat detection journey.
| Email template | Description | Example email body |
|---|---|---|
accountDisabled |
Email sent when PingOne Protect detects critical risk associated with the account. |
Show example |
deviceRegistration |
Email sent when the user registers a new MFA device. |
Show example |
suspiciousActivity |
Email sent when PingOne Protect detects some risk associated with the account. |
Show example |
welcome |
Email sent when a new user account is created. |
Show example |
otp |
Email containing the user’s one-time passcode (OTP). |
Show example |
Lean more about creating email templates in Email templates.
Create a logger library script for OTP
If you’re using OTP emails in your journey flow, you must create a library script. This script creates a logger, which is needed for OTP functionality to track and debug the process of sending OTP emails.
-
In the Advanced Identity Cloud admin console, go to Scripts > Auth Scripts, then click + New Script.
-
Select Other > Library and click Next.
-
Enter a script name and description, and paste the following script into the JavaScript field:
function XLogger(env) { this.logger = env.logger; this.scriptName = env.scriptName; this.logPrefix = "***" + env.scriptName + ": "; this.debug("logger initialised"); } XLogger.prototype.debug = function (message) { this.logger.debug(this.logPrefix.concat(message)); }; XLogger.prototype.warn = function (message) { this.logger.warn(this.logPrefix.concat(message)); }; XLogger.prototype.error = function (message) { this.logger.error(this.logPrefix.concat(message)); }; module.exports.XLogger = XLogger; -
Click Save to save the script.
Task 2: Download and import the journey
Download the journey
-
Go to Authentication Journey with Threat Detection on the Ping Identity marketplace.
-
Click Download Integration to download a file called
Authentication Journey with Threat Detection.json. This JSON file contains the parent journey and inner journeys, scripts, and email templates required for the authentication flow.
Import the journey
-
In the Advanced Identity Cloud admin console, go to Journeys, and click Import.
-
Click either Download Backup or Skip Backup. Learn more in Import journeys.
-
On the Import Journeys page, browse to and select
Authentication Journey with Threat Detection.json. -
Select
Alpha realm usersbecause the journey is configured for the alpha realm. -
In the Conflict Resolution section, choose how the system resolves import conflicts:
-
Overwrite all conflicts (default)
-
Manually pick conflict resolution
-
-
Click Next.
-
Click Start Import.
-
On the Import Complete page, click Done.
-
On the left panel of the Journeys page, click
Threat Detection (8)to view the threat detection journeys and inner journeys.
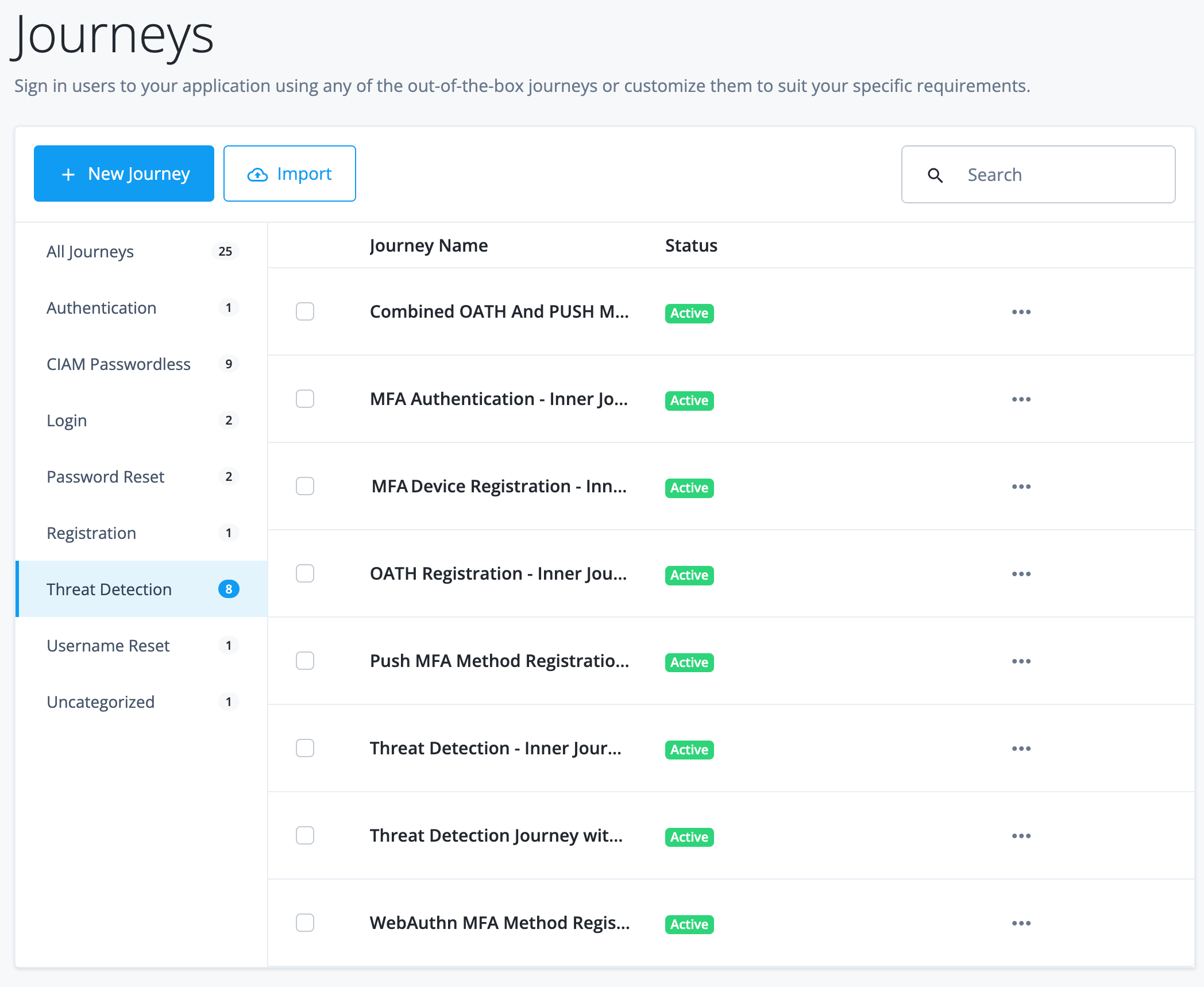
Task 3: Configure the journey components
Configure the Threat Detection Journey with PingOne Protect (parent journey)
-
On the Journeys page, click
Threat Detection Journey with PingOne Protectand click Edit. -
In the journey editor, configure the journey as follows:
-
If you have configured social identity providers other than Google and Facebook, enable social identity providers.
-
Click Save.
| To save your progress, periodically click Save in the top right of the journey editor. Failure to do this results in losing your work if the page reloads or if you lose your network connection. |
Review and set the initialize variables
The Threat Detection Journey with PingOne Protect includes a Scripted Decision node containing the initialize variables used later in the authentication flow. This script lets you:
-
Set the allowed MFA types:
FIDO2,OATH,PUSH,EMAIL,SMS,VOICE. -
Enable or disable PingOne Protect analysis.
-
Enable or disable magic link.
To review and set the initial variables:
-
Click the Prerequisites & Init Variables node.
-
In the Script field, click the Pencil icon () to open the
Threat Detection - Initialize Variablesscript. -
Review the script and make changes if needed.
-
Click Save and Close.
| You don’t need to update the values in the Script Outputs field of the Prerequisites & Init Variables node. |
Enable social identity providers
-
Click the Page node and then click the Select Identity Provider node.
-
In the Filter Enabled Providers field, add or remove the social identity providers as needed. Only the social identity providers listed here will be presented to the end user when signing on.
The social provider names must exactly match the names in your social authentication configuration, including the case. -
Click Save.
Configure the Threat Detection - Inner Journey
-
On the Journeys page click
Threat Detection - Inner Journeyand click Edit. -
In the journey editor, configure the journey as follows:
-
Click the PingOne Protect Initialize node.
-
In the PingOne Worker Service ID field, select the ID of the PingOne worker service for connecting to PingOne. Learn more in PingOne Protect Initialize node.
-
Click the Auth: PingOne Protect Evaluation node and enter the following:
-
PingOne Worker Service ID: Select the ID of the PingOne worker service for connecting to PingOne.
-
(Optional) Risk Policy Set ID: Enter the ID of the risk policy in PingOne. Learn more in PingOne Protect Evaluation node
-
-
Click the Reg: PingOne Protect Evaluation node and enter the following:
-
PingOne Worker Service ID: Enter the ID of the PingOne worker service for connecting to PingOne.
-
(Optional) Risk Policy Set ID: Enter the ID of the risk policy in PingOne. Learn more in PingOne Protect Result node.
-
-
-
Click Save.
Configure the MFA Device Registration - Inner Journey
This configuration is required if SMS or VOICE are opted in the allowedMFATypes array in the Threat Detection - Initialize Variables script in the Prerequisites & Init Variables node in the parent journey.
-
On the Journeys page, click
MFA Device Registration - Inner Journeyand click Edit. -
In the journey editor, update the required fields in the following nodes:
-
Click Save.
Configure the MFA Authentication - Inner Journey
This configuration is required if EMAIL, SMS, or VOICE are opted in the allowedMFATypes array in the Threat Detection - Initialize Variables script in the Prerequisites & Init Variables node in the parent journey.
-
On the Journeys page, click
MFA Authentication - Inner Journeyand click Edit. -
In the journey editor, update the required fields in the following nodes:
-
Click Save.
Task 4: Validate the journey
There are various paths the end user might go down, depending on the PingOne Protect risk evaluation and the MFA methods configured in the journey. For example, a user identified as low risk can sign on without MFA. However, for medium or high-risk sign-on attempts, the journey prompts the user to choose an MFA method, which could involve registering a new device. If a user signing on for the first time is identified as high risk, the registration attempt is blocked.
Before validating the journey, make sure you have a test user in the alpha realm.
To authenticate using an OTP, the user must have a registered authenticator app.
Test a medium-risk sign-on
These steps demonstrate a sign-on attempt by an end user identified as medium risk.
-
In the Advanced Identity Cloud admin console, go to Journeys and click Threat Detection Journey with PingOne Protect`.
-
In the Preview URL field, click and paste the URL into an incognito window.
The hosted pages displays the Sign In screen.
-
Enter the test user’s username and password and click Next.
A page displays prompting the user to select their preferred authentication method for MFA.
-
Select
OATHand click Next.
-
Enter the OTP from the test user’s app, and click Submit
You are signed on to the hosted account pages as the test user.
Best practices
This sample journey provides a strong foundation for threat detection. When preparing to use it in a production environment, consider the following best practices:
-
Treat as a template: Remember that this is a sample journey. Always adapt and harden it to meet your specific security policies and business requirements before deploying to production.
-
Use Environment Secrets & Variables (ESVs): Avoid hardcoding sensitive information like API keys and IDs directly in your journey scripts. Use ESVs to manage these values securely.
-
Test extensively: Validate all possible user paths, including low, medium, and high-risk scenarios, as different MFA registration and authentication flows. Ensure the user experience is smooth and the security responses are correct for each case.
-
Review PingOne Protect policies: Fine-tune your risk policies in PingOne Protect to align with your organization’s risk tolerance.
Sign on (login) with self-service
Incorporate self-service into your Advanced Identity Cloud journeys to let end users create and manage their own accounts, while you control the available features.
The Ping Identity Marketplace includes a prebuilt login with self-service journey. This sample journey lets end users sign on using a social identity provider (IdP), such as Google or Facebook, or the username and password of an account in the Advanced Identity Cloud datastore. If the end user doesn’t already have an account, they can create one using their social identity credentials.
The journey also includes progressive profiling. On their third successful sign-on attempt, end users are prompted to review their marketing preferences.
You can download the sample journey and import it into your Advanced Identity Cloud tenant. You can then modify the journey as needed to meet your requirements.
Example use case
A company wants to simplify sign-on and reduce friction by allowing end users to sign on with their Google or Facebook accounts. Additionally, they want to remind end users to review their preferences for receiving news and special offers, ensuring more personalized experiences while staying compliant with data protection regulations.
Before you begin
To implement the sample journey, you must have:
-
Tenant administrator access to your Advanced Identity Cloud development environment.
-
Social authentication configured in your Advanced Identity Cloud environment. Learn more in Social authentication.
The sample journey uses Google and Facebook for social sign-on, but you can configure and enable any of the supported social IdPs. -
A basic understanding of journeys.
-
A test end user in the
alpharealm. Learn more in Create test users and roles.
Tasks
Task 1: Download the sample journey
-
In the Ping Identity Marketplace, go to Login with Self-Service Journey.
-
Click Download to download the
Login with Self-Service Journey.jsonfile. This JSON file contains the journeys and scripts required for the authentication flow.
Task 2: Import the sample journey into Advanced Identity Cloud
-
In the Advanced Identity Cloud admin console, go to Journeys, and click Import.
-
Click either Download Backup or Skip Backup. Learn more in Import journeys.
-
On the Import Journeys page, browse to and select
Login with Self-Service Journey.json. -
Select Alpha realm - Users because the journey is configured for the Alpha realm.
-
In the Conflict Resolution section, choose how the system resolves import conflicts:
-
Overwrite all conflicts (default)
-
Manually pick conflict resolution
The progressive profile journey in the download matches the default journey included with Advanced Identity Cloud. If you’ve modified the default journey and want to retain your changes, select Manually pick conflict resolution and ensure it isn’t overwritten. -
-
Click Next.
-
Click Start Import.
-
On the Import Complete page, click Done.
-
On the left panel of the Journeys page, click Login to view the imported journeys:
-
Login with self-service journey (parent)
-
ProgressiveProfile (inner journey). Learn more about this journey in Progressive profile.
-
Login with self-service journey
The Login with self-service journey lets end users sign on using either a social IdP (such as Google or Facebook) or by entering their username and password. If they don’t already have an Advanced Identity Cloud account, end users can create one using their social identity credentials. During this process, they must create a local password and accept the current terms and conditions.
The journey includes an Inner Tree Evaluator node that links to a progressive profile journey. With this journey, end users are prompted to review and update their marketing preferences on their third successful login.
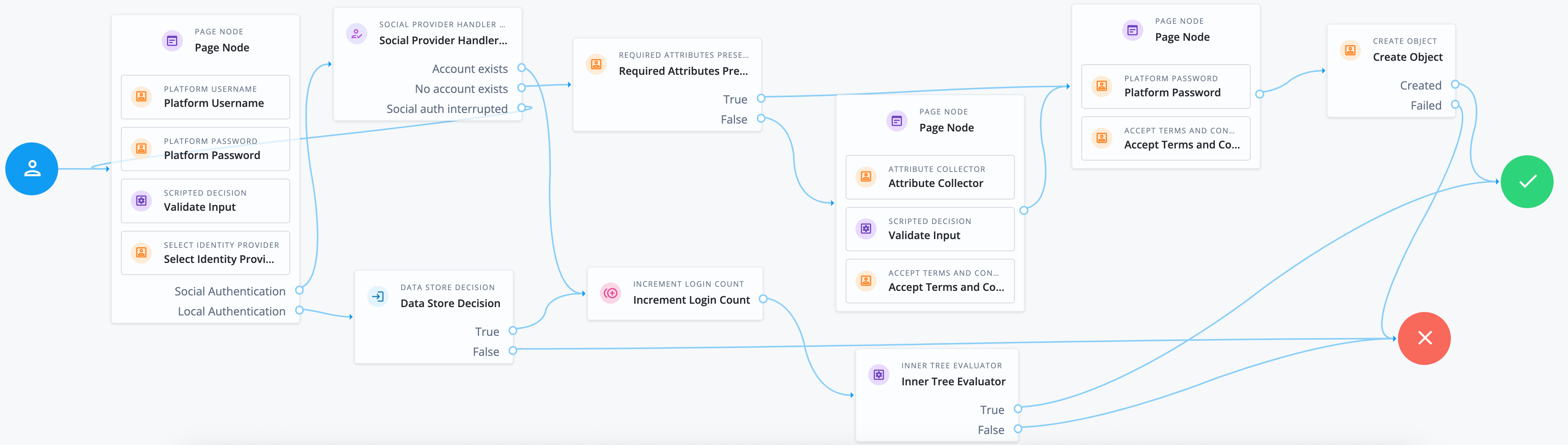
The Login with self-service journey uses the following nodes:
| Node | Description | ||
|---|---|---|---|
Combines the following nodes onto a single page for display to the user:
|
|||
Attempts to authenticate a user with an IdP they selected in the Select Identity Provider node. |
|||
Checks the specified identity resource in the underlying identity service and determines if all attributes required to create the specified object exist within the shared node state. |
|||
Combines the following nodes onto a single page for display to the user if they entered the required attributes:
|
|||
Combines the following nodes onto a single page for display to the user if they didn’t enter the required attributes:
|
|||
Checks that the credentials provided during local authentication match the ones stored in the realm datastore. |
|||
If an account already exists for the user, increments the successful sign-on count property. |
|||
Initiates the progressive profile inner journey. Learn more in Progressive profile. |
|||
Creates the user’s account. |
Validation
This validation step demonstrates multiple sign-ons by an end user using their Advanced Identity Cloud username and password. On the third sign-on attempt, the end user is prompted to review and confirm their marketing preferences.
Steps
-
In the Advanced Identity Cloud admin console, go to Journeys and click
Login with self-service. -
In the Preview URL field, click and paste the URL into an incognito window.
The hosted pages displays the Sign On screen.

-
Enter the test end user’s username and password, and click Next.
You are signed on to the hosted account pages as the test end user.
-
Sign off from the Advanced Identity Cloud end-user UI:
-
Click the test end user’s name in the upper-right corner of the hosted account pages.
-
Select Sign Out.
The page you’re directed to when you sign off is the default journey in the realm, not the Login with self-service journey. Learn more in Journeys.
-
-
Repeat steps 1 - 4 to sign on and sign off a second time.
-
Repeat steps 1 - 3 to sign on a third time. On the third sign-on attempt, you’re presented with a page for selecting preferences for receiving news and special offers.
-
Select the test end user’s marketing preferences and click Next to sign on to the hosted account pages.
-
If the end user makes no selection, the reminder expires and isn’t displayed again.
-
If the end user selects one or more options, the preferences are set in the end user’s profile.
-
Advanced Identity Cloud identity schema
PingOne Advanced Identity Cloud uses a default identity schema to organize users, roles, assignments, groups, organizations, and applications. The following diagram shows the identity schema relationships:

Learn more about the Advanced Identity Cloud identity schema in Summary of the identity schema.
You can customize the default identity schema to your business needs in the following ways:
-
Create custom attributes to store identity information specific to your business.
-
Create indexable custom attributes that let you search your identities and create customized segments.
-
Create organizations to structure your identities in a flexible and performant way.
For examples of customizing the Advanced Identity Cloud identity schema, learn more in Use cases for customizing the identity schema.
Summary of the identity schema
-
Users, roles, assignments, groups, organizations, and applications form the default identity schema. Their relationships are also part of the default schema.
-
Users are hybrid identity objects:
-
Their default attributes are explicitly defined in the schema with indexes also explicitly defined for these attributes:
-
givenName -
mail -
passwordLastChangedTime -
passwordExpirationTime -
sn -
userName
-
-
You can add custom attributes to them. However, the attributes are stored in an unindexed JSON data structure.
-
If you need a custom attribute for a user to be searchable, use an indexed general purpose extension attribute instead of a custom attribute.
-
-
Roles, assignments, groups, and organizations are generic identity objects:
-
None of their attributes are explicitly defined in the schema, and instead they are entirely stored in an indexed JSON data structure.
-
You can add custom attributes to them, and they will also be indexed.
-
-
You can create custom identity objects. These custom identity objects are also generic. This means that they are entirely stored in an indexed JSON data structure.
-
Applications are also generic identity objects. However, you should not alter these in any way as they are reserved for modification by Ping Identity to support workforce use cases. You should not add custom attributes to them, repurpose their default attributes, or reconcile data into them.
|
The following table summarizes the identity schema:
| Identity object | Type | Indexes on default attributes? | Indexes on custom attributes? |
|---|---|---|---|
Users |
Hybrid |
Yes (where defined) |
No |
Roles |
Generic |
Yes (all) |
Yes (all) |
Applications |
Generic |
Yes (all) |
n/a (customer modifications not supported) |
Custom |
Generic |
n/a |
Yes (all) |
Use cases for customizing the identity schema
The following are examples of how you might customize the default schema to support a media service:
-
Add a custom attribute for membership level to user identities to support subscription-level access or rate limiting. For example, the membership levels might be "gold", "silver", and "bronze".
-
Add a custom attribute for registration level to user identities to support access to premium content or to support progressive profiling in journeys. For example, the registration levels might be "guest", "pending", and "registered".
-
Adapt a general purpose extension attribute to be a searchable user attribute for date of birth to support age-restricted access. Use the attribute to support delegated administration for different age segments, allowing separate users to administrate adults and children.
-
Create organizations to structure user relationships between family members to support parental control.
The following are examples of how you might customize the default schema to support workforce:
-
Add custom attributes for job code, department number, or cost center to user identities to support the automatic provisioning of birthright roles.
-
Add custom attributes for external ID and metadata to user identities to support synchronisation using System for Cross-domain Identity Management (SCIM).
Customize user identities
You can customize user identities by adding your own attributes. This lets you store more useful information about each user such as the user’s department, cost centers, application preferences, device lists, and so on.
Advanced Identity Cloud offers the following strategies to customize user identities:
Customize user identities using custom attributes
You can create new custom attributes directly on user identities. Custom attributes on user identities must be
prefixed with custom_; for example, custom_department.
| Advanced Identity Cloud does not support searching on user identity custom attributes, which can sometimes render an environment unresponsive. Instead, if you need to make a particular user identity attribute searchable, use an indexed extension attribute. Learn more in Customize user identities using general purpose extension attributes. |
Create user identity custom attributes
To create a user identity custom attribute:
-
In the Advanced Identity Cloud admin console, click Native Consoles > Identity Management.
-
Go to Configure > Managed Objects.
-
Click Alpha_user or Bravo_user.
-
Click + Add a Property. This scrolls the page to the bottom and automatically focuses on the Name input field.
-
In the Name input field, enter a new attribute name prefixed with
custom_; for example, entercustom_department. -
In the Label input field, optionally enter a display name for the new attribute.
-
Click Save.
Access user identity custom attributes in scripts
To access a user identity custom attribute called custom_department in a Scripted Decision node:
-
Configure the Identity Store Decision node:
-
Make sure the Identity Store Decision node is placed before the Scripted Decision node in your journey.
-
Select the Username as Universal Identifier checkbox in the Identity Store Decision node’s configuration. This ensures that the user’s UUID is stored in the
usernamenode state variable.
-
-
Edit the script used by the Scripted Decision node:
-
To access the custom attribute using access management script functions, use the attribute
fr-idm-custom-attrs. This contains a JSON object of all custom attributes, so it needs to be parsed to access individual attributes.-
Next-generation
-
Legacy
If your script uses the next-generation script engine:
var uuid = nodeState.get('username'); var customAttrsRaw = idRepository.getIdentity(uuid).getAttributeValues('fr-idm-custom-attrs')[0]; var customAttrs = JSON.parse(customAttrsRaw); var department = customAttrs.custom_department;If your script uses the legacy script engine:
var uuid = nodeState.get('username').asString(); var customAttrsRaw = idRepository.getAttribute(uuid, 'fr-idm-custom-attrs').toArray()[0]; var customAttrs = JSON.parse(customAttrsRaw); var department = customAttrs.custom_department;Learn more in Access profile data.
-
-
To access the custom attribute using identity management script functions, use the specific attribute name
custom_department.-
Next-generation
-
Legacy
If your script uses the next generation script engine:
var uuid = nodeState.get('username'); var userAttrs = openidm.read('managed/alpha_user/' + uuid, null, ['custom_department']); var department = userAttrs.custom_department;If your script uses the legacy script engine, the
openidmbinding isn’t available. Ping Identity recommends that you upgrade your script to use the next generation script engine.Learn more in Access IDM scripting functions.
-
-
Delete user identity custom attributes
To delete a user identity custom attribute:
-
Delete all data stored in the custom attribute for all users, then run a full reconciliation.
If you don’t delete all data stored in the custom attribute before deleting the attribute, you might see errors when running subsequent reconciliations. -
In the Advanced Identity Cloud admin console, click Native Consoles > Identity Management.
-
Go to Configure > Managed Objects.
-
Click Alpha_user or Bravo_user.
-
In the list of attributes, find the row for the custom attribute that you want to delete:
-
Click the row’s cross icon ().
-
In the Delete Property confirmation modal, click Confirm.
-
Customize user identities using general purpose extension attributes
You can use the general purpose extension attributes that already exist on user identities. These attributes are predefined as part of the default identity schema. The following extension attributes are indexed, so you can use them as searchable attributes:
-
Generic Indexed String 1–20
-
Generic Indexed Multivalue 1–5
-
Generic Indexed Date 1–5
-
Generic Indexed Integer 1–5
To use an extension attribute:
-
In the Advanced Identity Cloud admin console, click Native Consoles > Identity Management.
-
In the IDM admin console, go to Configure > Managed Objects.
-
Click Alpha_user or Bravo_user.
-
Find an extension attribute that has one of the following default labels:
-
Generic Indexed String 1–20 or Generic Unindexed String 1–5
-
Generic Indexed Multivalue 1–5 or Generic Multivalue String 1–5
-
Generic Indexed Date 1–5 or Generic Date String 1–5
-
Generic Indexed Integer 1–5 or Generic Integer String 1–5
If you need to make the attribute searchable, make sure you use an indexed extension attribute.
-
-
Click the pen icon () to edit the attribute.
-
In the Readable Title input field, enter a custom label. For example,
Department. -
Click Save.
Roles and assignments
Roles and assignments let you create an entitlements structure that fits the needs of each realm in PingOne Advanced Identity Cloud.
Identity architects usually build the entitlements structure, and can also use the native AM and IDM consoles to put more complex entitlements in place.
Once your entitlements structure is in place, you can use the Advanced Identity Cloud admin console to:
-
Add new user profiles, device profiles, or roles
-
Add assignments to roles
-
Make changes to existing user profiles, device profiles, roles, or assignments
-
Provision identities with role-based permissions
Roles
Roles define privileges for user and device identities. Roles let you automatically update privileges in numerous identity profiles. All role members receive the same permissions you’ve defined for the role. When you change the privileges for that role, you change the permissions for all role members.
When you add a role to an identity profile, the user or device becomes a member of the role. A user or device can belong to many roles.
A role won’t work until you link it to at least one assignment. During the authorization process, Advanced Identity Cloud evaluates permissions based on:
-
Roles a user or device belongs to
-
Assignments attached to their roles
Internal roles
Internal roles, also called authorization roles, control access to your identity platform. You use internal roles to authorize administrators to manage your tenant or identities contained in it.
External roles
External roles, also called provisioning roles, give users and devices the permissions they need to access apps and services. You use external roles to let employees access intranet applications. You can also use external roles to let your customers and their end users access web services and mobile apps in your tenant.
Assignments
You create an assignment when you want to give a user or device permission to access a resource they need to do a job. A resource might be any application or service, data contained in a document or a database, or a device such as a printer or cell phone.
An assignment won’t work without a role. A role-assignment relationship is not fully formed until you do two things:
Assignment linked to role
Link an assignment to a role. Advanced Identity Cloud grants the permissions defined in the assignment to all members of the linked role.
Assignment mapped to attribute
Map your tenant assignment to an attribute stored in an external system. An external system can be, for example, an intranet Reporting App with its own database of user accounts.
In this illustration, Bina’s Accountant II role links to three assignments. During data store sync, Advanced Identity Cloud provisions her Reporting App user account based on assignment-attribute mappings:
| Mapping From Assignment Attribute | Mapping To Reporting App | Description and Provisioning Outcome |
|---|---|---|
Assignments: Reporting App |
UserName |
The mapping sets the value of Bina’s Name ("Bina Raman") in the UserName attribute in the Reporting App. |
Assignments: Operations Reports |
Reports: Operations |
The mapping adds the value "Operations" to the Reports attribute in the Reporting App. |
Assignments: Sales Reports |
Reports: Sales |
The mapping adds the value "Sales" to the Reports attribute in the Reporting App. |
You can create any number of assignments in your tenant. You can link an assignment to one or more external roles. You cannot link assignments to internal roles.
How provisioning works
When you add a user or device to a role, Advanced Identity Cloud updates the user or device profile with the role information. The update gives, or provisions, the user or device with the permissions that come with the role and its assignments.
Here’s a simple entitlement schema example:
- Roles
-
Accountant-I
Accountant-II - Accountant-I Assignments
-
Reporting App
Operations Reports - Accountant-II Assignments
-
Reporting App
Operations Reports
Sales Reports
Sam and Bina are co-workers. Their identity profiles are provisioned with permissions based on the entitlements schema example.
-
Sam is a member of the Accountant I role.
The Accountant I role assignments give Sam permission to use the Reporting app to access only Operations Reports. -
Bina is a member of the Accountant II role.
The Accountant II role assignments give Bina permission to use the Reporting app to access both Operations Reports and Sales Reports.
|
For a deep dive, learn more in the following documents: |
Organizations
Create organizations in PingOne Advanced Identity Cloud when you want to group identities to suit your business needs.
For example, you can build an organization structure modeled after your brand hierarchy. This lets you control access to business applications with tailored sign-on experiences. You can also use organizations to delegate user administration.
Organization use case
Here’s an example to help explain organization concepts. MightyBank is a conglomeration of independently-operated banks. MightyBank organizes its business units into two locales based on banking regulations associated with each locale. Within a business unit, each bank brand is a self-contained organization.
This diagram depicts MightyBank’s hierarchy of realms and organizations for identity management:
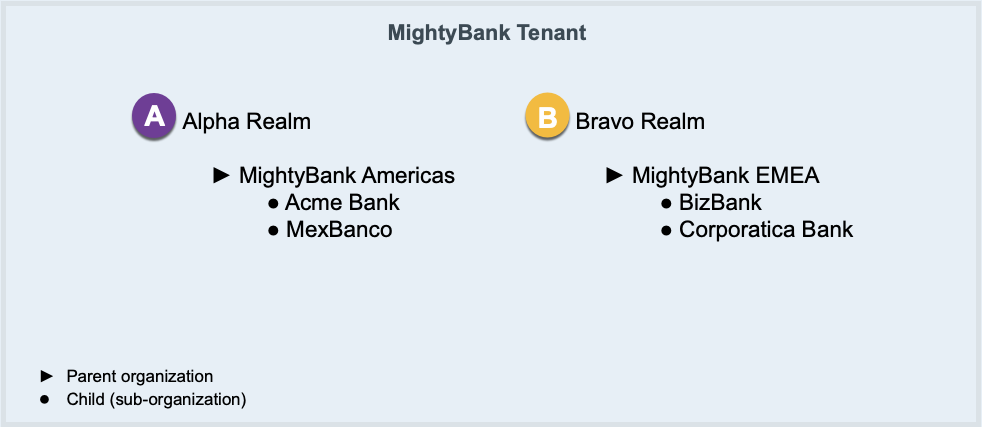
MightyBank organized their Advanced Identity Cloud tenant similarly to their business units. The Alpha realm contains MightyBank identities in the Americas. The Bravo realm contains MightyBank identities in Europe, the Middle East, and Africa (EMEA). Identities represent all employees, contractors, partners, vendors, customers—anyone who conducts business for or with MightyBank.
Each organization in the hierarchy has a designated owner. An owner can create child organizations, or sub-organizations. Owners can also add administrators to their organizations and sub-organizations.
Organization administrators manage user identities within organizations. Administrators also delegate administration to individual users through roles and assignments.
Users who belong to an organization are known as members of the organization.
Top-level organizations
Only Advanced Identity Cloud tenant administrators can create top-level organizations. In this example, Sam Carter is an Advanced Identity Cloud tenant administrator. Sam has created a top-level organization in each realm.
Sam can view and manage all identities within both the Alpha and Bravo realms:
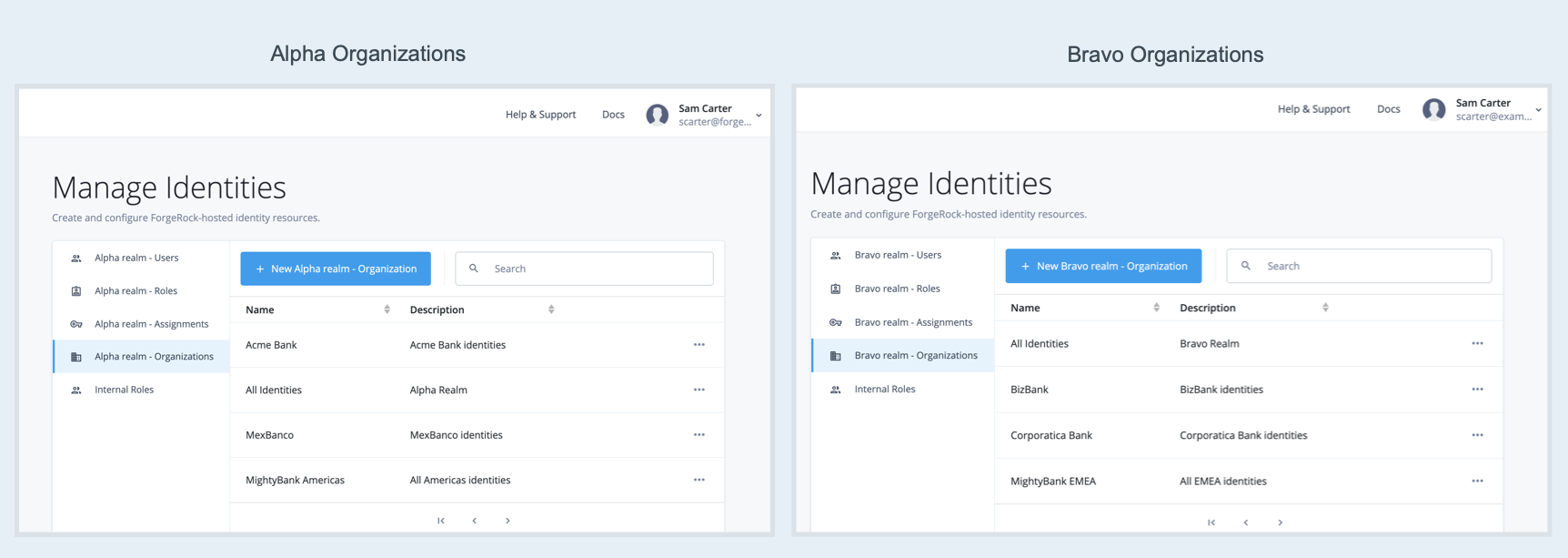
Sam delegates organization administration by setting up organization owners, who in turn set up organization administrators.
Owners
The main job of organization owners is to create organizations and sub-organizations. They also designate users, within the organizations they own, as administrators. Users who are authorized to manage identities within organizations are called organization administrators.
In this example, Sam designated Alma as owner of the top-level organization in the Alpha realm. Alma grouped identities into sub-organizations. One sub-organization contains Acme Bank identities. A second sub-organization contains MexBanco identities.
Alma is authorized to manage the MightyBank Americas organization, and all its sub-organizations.
Organization owners can do the following, but only within the organizations and sub-organizations they own:
-
Add an administrator to an organization or sub-organization.
-
An owner can add an existing user profile to a sub-organization only if the user already belongs to a parent organization.
-
An owner can create a new user profile in a sub-organization if the user doesn’t already belong to a parent organization.
-
In this example, before Alma can add a user profile to the Acme Bank organization, the user must belong to MightyBank Americas, the parent organization. If a user doesn’t belong to the parent organization, then Alma can open the Acme Bank organization, and create a new user profile directly in the organization.
Administrators
The main job of organization administrators is to manage user identities within an organization or sub-organization.
In this example, Alma designated Barbara as the administrator for MightyAmericas. Barbara is authorized to manage all identities in the MightyAmericas organization, and in all of its sub-organizations.
Barbara then delegated administration to two employees in the Acme Bank organization, and two employees in the MexBanco organization. These delegated administrators share responsibility for managing identities.
Organization administrators can do the following, but only within the organizations they are authorized to manage:
-
Delegate user identity administration through roles and assignments.
-
An administrator can add an existing user profile to an organization only if the user already belongs to a parent organization.
-
An administrator can create a new user profile in an organization if the user doesn’t already belong to a parent organization.
-
In this example, before an administrator can add a user profile to the Acme Bank organization, the user profile must already belong to MightyBank Americas, the parent organization. If a user profile does not already belong in MightyBank Americas, then the administrator can open the Acme Bank organization and create a new user profile directly in the organization.
Each organization administrator can manage user profiles, but in only the organization they’re authorized to manage.
More information
-
For steps to create and manage organizations using Advanced Identity Cloud admin console, learn more in Organizations on the Manage identities page.
-
For a deep dive into organizations, learn more in Organizations.
-
To manage organizations using the REST API, learn more in Manage organizations over REST.
-
To add the organization model to your environment, learn more in How do I get the organization model in my Advanced Identity Cloud environment?.
-
For a deep dive into roles and assignments, learn more in Authorization and roles and Use assignments to provision users.
Manage identities
A PingOne Advanced Identity Cloud tenant can contain data about people (such as employees, customers, or vendors) and devices (such as cell phones or printers), each of which has a unique combination of defining attributes. Advanced Identity Cloud stores these attributes in identity profiles.
In an identity profile, roles and assignments define the type and extent of access permissions given to users and devices. Advanced Identity Cloud uses roles and assignments to provision identity profiles with permissions.
For quick takes, learn more in About roles and assignments and How provisioning works. To view a list of tenant administrators, learn more in View the tenant administrators list. To view realm settings, learn more in Realm settings.
Note that identity resources are grouped by realm. If you can’t find a resource, make sure that you’re looking in the right realm.
Users
A user is a person, such as a customer, employee, or vendor, whose identity profile is stored in a tenant. A user identity profile is also called a user profile.
For a deep dive into Advanced Identity Cloud user identities, learn more in Manage identities.
Create a user profile
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Users and New Alpha realm - User.
-
On the New Alpha realm - User page, enter information for the user, and then click Save. For a list of user attributes, learn more in User identity attributes and properties reference.
Edit a user profile
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Users, and click on a username.
-
Edit information for the user, and then click Save. For a list of user attributes, learn more in User identity attributes and properties reference.
Reset a user password
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Users, and click on a username.
-
Click Reset Password.
-
Enter a new password, and click Reset Password to save the new password.
Delete a user
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Users, and click on a username.
-
At the bottom of the page, click Delete Alpha realm - User. The Delete operation cannot be undone.
Add an application to a user
When you add an application to a user, Advanced Identity Cloud automatically provisions an account for them in the target application.
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Users, and click a username.
-
Click the Applications tab.
-
Click + Add Application.
-
On the Account Details page, in the Application drop-down field, select an application.
-
Click Assign. Afterward, in the Users & Roles tab, the Assignment column shows the user has a Direct assignment to the application.
Manage trusted devices
| To populate the Trusted Devices tab, add the Device Profile Collector node to your authentication journeys to collect end-user device information. |
You can view and delete the list of trusted devices on a user account.
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Users, and click a username.
-
Click the Trusted Devices tab to view a list of devices that the end user has used to sign on to their account.
-
Click a device from the list to open its Device Details modal window. The modal displays device information such as operating system and browser. The modal may also display location information for the device if the Device Profile Collector node is configured to collect it and if the end user consented to the information being collected by their browser.
-
Choose one of the following options:
-
To close the modal, click Done.
-
To remove the device from the list of trusted devices:
-
Click Remove device.
-
In the Delete Device? modal window, click Delete.
-
-
Roles
Create an external role
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha Realm - Roles and New Alpha realm - Role.
-
On the role page, enter the following information for the role, and then click Next:
-
Name: Unique identifier to display in the roles list.
-
Description: String to describe the role, such as Sales.
-
-
(Optional) Assign the role only to identities with specified attributes:
-
On the Dynamic Alpha realm - role Assignment page, use the slider to create a conditional filter for the role.
-
Use the choosers to specify conditions that an identity must meet.
-
(Optional) Click Advanced Editor to create a query-based condition.
-
Click Next.
-
-
(Optional) Assign the role only at specified times:
-
On the Time Constraint page, use the slider to enable a start and end date during which the role is active.
-
Use the calendar, clock choosers, and time zone offset.
-
Click Save.
-
Edit an external role
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha Realm - Roles, and click on a role name.
-
Add managed assignments to the role:
-
On the role page, click Managed Assignments and Add Managed Assignments.
-
Select a managed assignment from the drop-down list, and click Save.
-
-
Add members to the role:
-
On the role page, click Role Members and Add Role Members.
-
Select an identity from the members list.
-
(Optional) Use the slider to assign the role only at specified times, and then add the dates, times, and timezone offset.
-
-
Change the time constraints or conditions of a role.
-
On the Internal Role page, click Settings.
-
In Time Constraint or Condition, click Set Up to edit the parameters, and then click Save.
-
Add an application to a role
When you add an application to a role and then assign a user to the role, Advanced Identity Cloud automatically provisions the user in the target application.
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha Realm - Roles, and click on a role name.
-
Click the Applications tab.
-
Click + Add Application.
-
On the Account Details page, in the Application drop-down field, select an application.
-
Click Assign. Afterward, in the Users & Roles tab, the Assignment column shows the user has a Role-based assignment to the application.
Create an internal role
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
Click Internal Roles.
-
Click + New Internal Role.
-
In the New Internal role screen, enter role details:
-
Name: Unique identifier to display in the Roles list.
-
Description (optional): String that’s meaningful to your organization.
Examples: Employee, Customers, Sales Department, and Europe.
-
-
Click Next.
-
To choose an identity object that the role should grant permissions to, on the Internal role Permissions dialog, choose an identity object.
-
To add the identity, click Add.
-
Set the permission for the identity:
-
View: Grant the identity object view access.
-
Create: Grant the identity object create access.
-
Update: Grant the identity object update access.
-
Delete: Grant the identity object delete access.
-
-
To add another identity, repeat the above three steps.
-
Click Next.
-
To optionally assign a user to a role based on specific attributes, on the Dynamic Internal role Assignment screen:
-
Enable A conditional filter for this role.
-
Use the choosers and drop-down lists to specify conditions for assigning a user to a role.
-
To create a query-based condition, click Advanced Editor, and edit the query code.
-
Click Next.
-
-
To assign a role on a temporary basis, on the Time Constraint screen:
-
Enable Set a start and end date during which this role will be active.
-
Use the calendar and date pickers to define when the role is in effect:
-
Specify the time zone to be used for the start date/time and end/date you specified. Choose a time zone relative to Greenwich Mean Time (GMT). GMT is the same as Universal Time Coordinated (UTC).
-
To view a worldwide list of offset times, click Time zones chart to calculate the offset time.
-
-
-
Click Save.
Edit an internal role
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Internal Roles, and click on a role name.
-
To edit role details:
-
Click the Details tab.
-
Edit the Name field and possibly the Description field.
-
Click Save.
-
-
To edit a privilege:
-
Click the Privileges tab.
-
Click a privilege.
-
Edit the privilege details.
-
Click Save.
-
-
To add a privilege:
-
Click the Privileges tab.
-
Click + Add Privileges.
-
To choose an identity that this role should grant administration privileges to, use the drop-down list field to choose an identity object.
-
To add the identity, click Add.
-
Set the permission for the identity:
-
View: Grant the identity object view access.
-
Create: Grant the identity object create access.
-
Update: Grant the identity object update access.
-
Delete: Grant the identity object delete access.
-
-
To add another identity, repeat the above three steps.
-
Click Save.
-
-
To edit a member:
-
Click the Members tab.
-
Click a member.
-
Edit the member’s information.
-
Click Save.
-
-
To add a member:
-
Click the Members tab.
-
Click + Add Members.
-
Use the drop-down field to choose a member.
-
Click Save.
-
-
To set a start and end date for when the role is active:
-
On the Internal Role page, click Settings.
-
In the Time Constraint section, click Set Up.
-
Enable Set a start and end date during which this role will be active.
-
Set the time parameter fields.
-
Click Save.
-
-
To set a conditional filter for the role:
-
On the Internal Role page, click Settings.
-
In the Condition section, click Set Up.
-
Enable A conditional filter for this role.
-
Set the condition fields.
-
Click Save.
-
-
To use JSON to configure internal role details, privileges, and other information:
-
On the Internal Role page, click Raw JSON.
-
Edit the JSON sample.
-
-
For a deep dive into roles, learn more in Roles.
Assignments
For a quick take, learn more in Assignments. For a deep dive into roles and assignments, learn more in Use assignments to provision users.
Create a mapping
Before you create an assignment, make sure that you have a mapping, or create a mapping as described in this section.
A mapping specifies a relationship between an object and its attributes, in two data stores. Learn more in Resource mapping.
-
In the Advanced Identity Cloud admin console, go to Native Consoles > Identity Management. The Identity Management console is displayed.
-
Click Create Mapping, and add a mapping using information from Configure mappings using the admin UI.
Create an assignment
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Assignments and New Alpha realm - Assignments.
-
On the assignment page, enter the following information for the assignment, and then click Next:
-
Name: Unique identifier to display in the assignments list.
-
Description: String to describe the assignment, such as Sales reporting.
-
Mapping: Select a mapping to which the assignment applies.
-
-
(Optional) Add an attribute to map to the target system. Learn more in provision an attribute in the target data store.
-
On the Assignment Attributes page, click Add an Attribute.
-
Select an attribute from the drop-down list, and enter a value for the attribute. The attribute-value pair is synchronized with user accounts in the target data store.
-
(Optional) Click , and in the Assignment Operation window specify how Advanced Identity Cloud synchronizes assignment attributes on the target data store:
-
On assignment
-
Merge with target: The attribute value is added to any existing values for that attribute.
-
Replace target: The attribute value overwrites any existing values for that attribute. The value from the assignment becomes the authoritative source for the attribute.
-
-
On unassignment
-
Remove from target: The attribute value is removed from the system object when the user is no longer a member of the role, or when the assignment itself is removed from the role definition.
-
No operation: Removing the assignment from the user’s effectiveAssignments has no effect on the current state of the attribute in the system object.
-
-
-
-
Click to add the assignment, and then click Save.
-
(Optional) Add an event script.
Groovy scripts are not supported. -
One the Alpha realm - Assignment page, click Add an event script.
-
Choose whether to trigger the script on assignment or unassignment.
-
Enter the script in the text box or upload it.
-
(Optional) Define custom variables to pass to your script. To enter variables in JSON format, use the JSON slider.
-
Click Save.
-
-
(Optional) Add managed roles to the assignment
-
On the Alpha realm - Assignment page, click the Manage Roles tab, and click Add Manage Roles.
-
Select a managed role from the drop-down list, and click Save.
-
Organizations
For a quick take, learn more in Organizations.
Organizations can be managed in the following ways:
-
By tenant administrators, using the REST APIs:
Before you can use the IDM REST APIs, you’ll have to get an access token and authenticate to the IDM API server. Learn more in Accessing the IDM REST APIs.
For examples of API calls for organizations, learn more in Manage Organizations Over REST.
-
By tenant administrators, using the Advanced Identity Cloud admin console as described on this page.
-
By organization owners and organization administrators, using the hosted account pages as described on this page.
Import identities into an organization
You can build organizations in different ways. For example, you can start with a parent organization that contains all user identities, and then build your organization hierarchy. Alternatively, you can start with a hierarchy of empty organizations, and then add users. Whatever approach you take, at some point you’ll have to import identities into an organization.
| Tenant administrators | Organization owners | Organization administrators |
|---|---|---|
Only tenant administrators can import identities into an organization.
For this example, it is assumed that the following items already exist:
-
A .csv file containing 100 user identities
-
A parent organization with no members
-
In the Advanced Identity Cloud admin console, go to Identities > Import.
-
On the Bulk Import page, click New Import.
-
On the Upload CSV page, select Alpha realm - Users, and then click Next.
-
In the Upload CSV page, Enter the following information and then click Next:
-
CSV File: Browse to your file
-
Match Using: Add a property name to use for a unique record match
-
-
When the Import Complete dialog box is displayed, and you can confirm that the import was successful, click Done.
You can confirm the import in the following ways:
-
Go to Identities > Manage > Alpha realm - Users, and open any user profile. Click Organizations to which I Belong, and make sure that the organization you created is displayed.
-
Go to Identities > Manage > Alpha realm - Organizations, and make sure that the organization you created is displayed.
-
Click the name of the organization you created, click Members, and then make sure that all the imported user identities are displayed.
-
Create a parent organization
| Tenant administrators | Organization owners | Organization administrators |
|---|---|---|
Only tenant administrators can create a parent organization.
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Organizations and New Alpha realm - Organizations.
-
On the New Alpha realm - Organizations page, enter a name for the organization. Uppercase, lowercase, alphanumeric, special characters, and white spaces are allowed.
-
Click Save.
-
In the organization page, change the name, add a description, or assign a parent organization. To designate this organization as the parent, leave the Parent Organization field blank.
-
Click Save.
Create an organization owner
| Tenant administrators | Organization owners | Organization administrators |
|---|---|---|
Only tenant administrators can create an organization owner.
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Organizations and click on an organization name.
-
Click Owner and Add Owner.
-
In the Add Owner page, select an identity from the drop-down list.
Make sure that the organization owner is not also an organization member. This can result in giving the organization administrator greater control of the organization than its owner. -
Click Save.
Create an organization administrator
| Tenant administrators | Organization owners | Organization administrators |
|---|---|---|
-
Tenant administrators can create an organization administrator in any organization.
-
Organization owners can create organization administrators only within organizations or sub-organization where they are owner.
-
Organization administrators cannot create other organization administrators.
-
On the Manage Identities page, click Alpha realm - Organizations and click on an organization name.
-
Click Administrators and Add Administrators.
-
In the Add Administrators page, select a user from the drop-down list. The user must already belong to the organization.
-
Click Add Administrators. The username is displayed in the members list.
Create a sub-organization
| Tenant administrators | Organization owners | Organization administrators |
|---|---|---|
-
Tenant administrators can create sub-organizations within any organization.
-
Organization owners can create sub-organizations only within organizations or sub-organizations where they are owner.
-
Organization administrators can create sub-organizations only within organizations or sub-organizations where they are administrator.
Tenant administrators
| Tenant administrators can view all organizations. |
Follow the steps in to create a parent organization, and then set a parent organization that is:
-
An existing organization
-
One level of hierarchy higher than this child organization
Organization owners and organization administrators
| Organization owners and organization administrators can view only the organizations and sub-organizations that they own or administrate. |
-
In the hosted account pages, go to Alpha realm - Organizations and New Alpha realm - Organizations.
-
On the New Alpha realm - Organizations, page enter a name for the organization. Uppercase, lowercase, alphanumeric, special characters, and white spaces are allowed.
-
Click Save.
-
In the organization page, optionally change the name, and add a description.
-
Assign a parent organization that is One level of hierarchy higher than this child organization.
-
Click Save.
|
While privileges for default attributes are automatically included when setting up a sub-organization, custom attributes need to be manually added to your privileges configuration before creating the sub-organization. Do this by adding the custom attribute to the |
Edit an organization or sub-organization
| Tenant administrators | Organization owners | Organization administrators |
|---|---|---|
-
Tenant administrators can edit any organization or sub-organization.
-
Organization owners can edit only organizations or sub-organization where they are owner.
-
Organization administrators can edit only organizations or sub-organizations where they are administrator.
Tenant administrators
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Organizations and click on an organization name.
-
In the organization page, change the name, add a description, or assign a parent organization.
Uppercase, lowercase, alphanumeric, special characters, and white spaces are allowed in the organization name.
To designate this organization as the parent, leave the Parent Organization field blank.
-
Click Save.
Organization owners and organization administrators
-
In the hosted account pages, go to Alpha realm - Organizations, and click on an organization name.
-
In the organization page, change the name, add a description, or assign a parent organization.
Uppercase, lowercase, alphanumeric, special characters, and white spaces are allowed in the organization name.
To designate this organization as the parent, leave the Parent Organization field blank.
-
Click Save.
Add or create organization members
| Tenant administrators | Organization owners | Organization administrators |
|---|---|---|
-
Tenant administrators can access all members of all organizations.
-
Organization owners can access only members of organizations they own.
-
An organization owner can add a user profile to their organization only if the user profile exists inside their ownership area.
-
An organization owner can create a new user profile as a member of their organization.
-
-
Organization administrators can access only members in their administrative area.
-
An organization administrator can add a user profile to their organization only if the user profile exists inside their administrative area.
-
An organization administrator can create a new user profile as a member of their organization.
-
Add a member to an organization
Tenant administrators
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Organizations and click on an organization name.
-
On the organization page, click Members and Add Members.
-
Select an identity from the members list, and then click Save. The username or usernames you added are now displayed in the members list.
Organization owners and organization administrators
-
In the hosted account pages, go to Alpha realm - Organizations.
-
Follow steps in the tenant administrator instructions.
Create a new user profile in an organization
Tenant administrators
-
Add a user profile, as described in Create a user profile.
-
In the user profile, click Organizations to which I Belong and Add Organizations to which I Belong.
-
In the add organization dialog box, choose one or more organizations from the drop-down list, and click Save.
Organization owners and organization administrators
-
In the hosted account pages, go to Alpha realm - Users.
-
Follow steps in the tenant administrator instructions.
Delete an organization
| Tenant administrators | Organization owners | Organization administrators |
|---|---|---|
-
Tenant administrators can delete any organization or sub-organization.
-
Organization owners can delete only organizations or sub-organizations where they are owner.
-
Organization administrators can delete only organizations or sub-organization where they are administrator.
Tenant administrators
-
In the hosted account pages, go to Identities > Manage.
-
On the Manage Identities page, click Alpha realm - Organizations and click on an organization name.
-
On the organization page, click Delete Alpha realm - Organization.
This operation cannot be undone.
Organization owners and organization administrators
-
In the Advanced Identity Cloud end-user UI, go to Manage.
-
Follow steps in the tenant administrator instructions.
Sync identities
Before you can sync identities with a remote server or use load balancing and failover in PingOne Advanced Identity Cloud, you must register a remote server with your tenant.
Connectors can read data in your tenant and in external resources (an app or service that runs on a server outside your tenant). Use connectors to convert your identity profiles, as well as user accounts in a resource server, into a format that both data stores can use.
| Advanced Identity Cloud provides built-in connectors for synchronization with data stores in other cloud services. |
Process overview
Before you can make a connection, you must register a remote connector server with your tenant. You also need to have a connector service up and running.
To configure connectors that aren’t built in to Advanced Identity Cloud, complete this list of tasks in order:
-
Change the client secret by resetting it.
-
Download a remote server from Backstage.
-
Install and configure a connector, if needed.
You can also create a connector configuration over REST. -
Configure the remote server to connect to Advanced Identity Cloud (optional).
-
Create a mapping between identities in Advanced Identity Cloud and identities in your identity resource server.
-
Secure RCS access between Advanced Identity Cloud and RCS client mode.
-
(Optional) If you plan to set up load balancing or failover, then register a remote server cluster.
For troubleshooting advice, learn more in the knowledge base article How do I troubleshoot the Java Remote Connector Service (RCS)?.
Tasks
Task 1: Register a remote server
-
To create a connector server in your development or sandbox[1] environments:
-
In the Advanced Identity Cloud admin console, go to Identities > Connect > Connector Servers.
-
Click + New Connector Server.
-
In the New Connector Server dialog box:
-
Enter a Name for the connector server. Use only lowercase letters, numbers, underscores, or hyphens. No other special characters or spaces are allowed.
-
Choose how you want your remote server (configured in later steps) to connect to the connector server:
-
By default, the connector server is configured to use a built-in OAuth 2.0 client called RCSClient. Your remote server uses the RCSClient credentials to connect.
-
(Optional) Select the Create a new OAuth Client checkbox to create a specific OAuth 2.0 client. The connector server uses this specific OAuth 2.0 client instead of RCSClient. Your remote server uses the credentials of the specific OAuth 2.0 client to connect.
-
Enter a Client ID for the specific OAuth 2.0 client. Use only lowercase letters, numbers, underscores, or hyphens. No other special characters or spaces are allowed.
-
Enter a Client Secret for the specific OAuth 2.0 client and note the value you entered.
-
-
-
-
Click Save.
-
-
To create a connector server in your UAT[2], staging, or production environments:
-
Follow the instructions in step 1 to create a connector server in your development environment.
-
Run a series of promotions to promote the connector server configuration from your development environment to your upper environments.
-
Task 2: Reset the client secret
-
Skip to Task 3: Download a remote server if either of these conditions apply:
-
If you selected the Create a new OAuth Client checkbox when creating the connector server in the previous step.
-
If you already know the client secret of the RCSClient.
-
-
In the Advanced Identity Cloud admin console, go to OAuth2 Clients.
-
Click RCSClient.
-
Click Reset to change the client secret.
RCSClient is a built-in OAuth 2.0 client that’s the default client for connector servers in Advanced Identity Cloud. If you reset its client secret, you must update the configuration of any remote connectors configured to use it to connect to the tenant environment. -
In the Reset Client Secret dialog box, enter a strong password.
-
Read the warning, and then click Save.
Task 3: Download a remote server
You’re directed to the
IDM Cloud Connectors download page. You must sign in to Backstage to view this page and download the connectors.
-
Download the Remote Connector Server to the host that will run the connector server.
Ping Identity recommends using the Java version of the Remote Connector Server. Only download the .NET version if you need to use a PowerShell connector. Learn about the differences between the RCS types in Install a Remote Connector Server (RCS).
You can run the connector server on the same host as the identity resource server or you can run it on a different host. For example, you could run the connector server on a host that’s dedicated to only connectors.
Task 4: Install and configure a connector
If the connector you want to use isn’t bundled with the remote server you downloaded in task 2, you’ll need these instructions. Follow the instructions in the ICF documentation to download and install the remote connector you need.
After you complete the Next Steps, click Done.
Task 5: Configure a remote server
-
Unpack the OpenICF package you downloaded from the IDM Connectors download page.
-
Edit the
ConnectorServer.propertiesfile.ConnectorServer.propertiesdetails:-
Add the OAuth2 Client credentials used to obtain an OAuth2 token. The client uses the Client Credentials grant type.
-
connectorserver.clientId=<client-id>-
If you chose to create a specific OAuth 2.0 client in Task 1: Register a remote server, enter that client’s client ID.
-
Otherwise, enter
RCSClient.
-
-
connectorserver.clientSecret=<client-secret>-
If you chose to create a specific OAuth 2.0 client in Task 1: Register a remote server, enter that client’s client secret.
-
Otherwise, enter the client secret for
RCSClient.
-
-
-
Uncomment these settings and edit them for your tenant:
-
connectorserver.url
This is the Advanced Identity Cloud OpenICF endpoint.
Usewssover HTTPS so the client can receive a bearer token through OpenID.-
In UAT[2], staging, and production environments, use three URLs in a space-delimited list[7]. Example:
connectorserver.url=wss://<tenant-env-fqdn>/openicf/0 wss://<tenant-env-fqdn>/openicf/1 wss://<tenant-env-fqdn>/openicf/2 -
In a development environment, use only one URL. Example:
connectorserver.url=wss://<tenant-env-fqdn>/openicf/0
-
-
connectorserver.connectorServerName=<remote-server-name>
This is the remote server name you set through the Advanced Identity Cloud admin console. Be sure the name includes only lowercase letters and numerals. No special characters or spaces are allowed. -
connectorserver.pingPongInterval=60
The WebSocket Ping/Pong interval (seconds). -
connectorserver.housekeepingInterval=20
The WebSocket connections housekeeping interval (seconds). -
connectorserver.groupCheckInterval=60
WebSocket groups check interval, in seconds. -
connectorserver.webSocketConnections=3
Specifies the number of sockets the connector server establishes and maintains to each Advanced Identity Cloud (IDM) backend instance. -
connectorserver.connectionTtl=300
WebSocket connection’s time to live (seconds). -
connectorserver.newConnectionsInterval=10
Time between new connections (seconds). -
connectorserver.tokenEndpoint=https://<tenant-env-fqdn>/am/oauth2/realms/root/realms/alpha/access_token
Token endpoint to retrieve access token. -
connectorserver.scope=fr:idm:*
OAuth2 token scope. -
connectorserver.loggerClass=org.forgerock.openicf.common.logging.slf4j.SLF4JLog
You don’t need to set the
connectorserver.usesslproperty; the remote server determines connection security from the value of theconnectorserver.urlproperty. -
-
-
When you’re satisfied with your changes, save the file.
-
Start the remote server on the OAuth 2.0 client:
-
Linux
-
Windows
bin/ConnectorServer.sh /runbin\ConnectorServer.bat /run -
-
To verify the connection is working, view the remote server status in the Remote Servers list.
Task 6: Create a mapping
Create a mapping between identities in Advanced Identity Cloud and identities in your identity resource server.
-
In the Advanced Identity Cloud admin console, go to Native Consoles > Identity Management.
-
In the IDM admin console, click Create Mapping.
For detailed information and instructions, learn more in Configure a resource mapping.
After you’ve tested your mapping configuration per the instructions, you can make connections for synchronizing and provisioning user profiles.
Task 7: Secure RCS access
Secure the openicf WebSocket endpoint used for communication between Advanced Identity Cloud and RCS client mode.
You can specify the authorization roles allowed to connect to the openicf servlet for each RCS instance to ensure that RCS access to Advanced Identity Cloud is protected and can only be accessed by trusted RCS clients. The openicf servlet in your access configuration lets you manage authorization for the openicf endpoint.
Learn more in Secure RCS access.
Task 8: Register a server cluster
This is optional. Use a cluster of remote servers when you want to set up load balancing or failover among multiple resource servers.
-
In the Advanced Identity Cloud admin console, go to Identities > Connect > Server Clusters.
-
Click + New Server Cluster.
-
Provide Server Cluster Details:
-
Name: Identifier to display in the Server Clusters list.
-
Algorithm:
-
Choose Failover if you want requests to be redirected to a designated server only when the primary server fails.
-
Choose Round Robin if you want to continuously load-balance among two or more servers regardless of service status.
-
-
-
Click Next.
-
In the Choose Servers dialog box, enable the connectors you want to include in the server cluster.
Every connector associated with a server cluster must have an identical set of JAR files and scripts in its /path/to/openicf/lib directory. All JAR files must be on the same version. If you make any changes to the JAR files and scripts in this directory, you must propagate the changes to all the other connectors in the server cluster.
-
Click Create Cluster.
Synchronize passwords
You can synchronize hashed user passwords from your PingDS deployment into Advanced Identity Cloud, allowing end users to authenticate with their existing DS password. The method documented here relies on an LDAP connector configured to synchronize accounts from your DS servers. It treats the hashed password as a simple string during synchronization, similar to any other LDAP attribute. It doesn’t use the DS password synchronization plugin.
This feature depends on having compatible one-way hash password storage schemes in Advanced Identity Cloud and in your DS password policies. DS servers in Advanced Identity Cloud verify user-provided plaintext passwords against the password hash, just as the DS servers in your deployment.
-
Verify that your DS service stores the passwords you want to synchronize only with DS password storage schemes that are also enabled in Advanced Identity Cloud.
The following DS password storage schemes are enabled in Advanced Identity Cloud:
-
Bcrypt
-
PBKDF2
-
PBKDF2-HMAC-SHA256
-
PBKDF2-HMAC-SHA512
-
PBKDF2-HMAC-SHA512T256 (for interoperability only)
-
Salted SHA-256
-
Salted SHA-512
-
SCRAM-SHA-256
-
SCRAM-SHA-512
-
-
Verify that account synchronization works properly from your DS service to Advanced Identity Cloud.
For example, modify a test user’s entry in your DS server and check that the corresponding account in Advanced Identity Cloud is updated correctly after reconciliation runs.
-
In the Advanced Identity Cloud admin console, go to Native Consoles > Identity Management, and configure the LDAP connector to synchronize
userPasswordattributes as strings:-
Delete
__PASSWORD__from the list of LDAP connector properties. -
Add
userPasswordwith Native type:stringand Run as User enabled.
-
-
In the native IDM admin console, configure the mapping from your remote DS system resource to Advanced Identity Cloud managed users:
-
Map
userPasswordin your remote DS system resource topasswordin managed users. -
Set the transformation script for the synchronization to the following inline script:
// Set the text of DS userPassword as the value of the password: if (source != null) { var base64 = Packages.org.forgerock.util.encode.Base64url; decodedTarget = new Packages.java.lang.String(base64.decode(source)); target = decodedTarget; }
-
-
Verify that password synchronization is working correctly.
For example, modify a test user’s password in your DS server, and check that the user can authenticate in Advanced Identity Cloud after reconciliation runs.
About Advanced Identity Cloud connectors
Apps and services that run and store data outside your tenant exist as external resources relative to Advanced Identity Cloud.
Advanced Identity Cloud provides connectors to synchronize your identity profiles with data stored in your resource servers.
Connectors work differently based on the capabilities of the connected resource server. For a summary of supported connectors and their capabilities, learn more in ICF documentation.
Syncing and provisioning
Here’s how Advanced Identity Cloud synchronizes user data. In this diagram, an identity resource server hosts an app and a data store containing user accounts. The resource server also hosts a connector server. The connector server runs a connector.
When you edit a user’s account on the resource server, the connector makes the change in the user’s profile in your tenant.
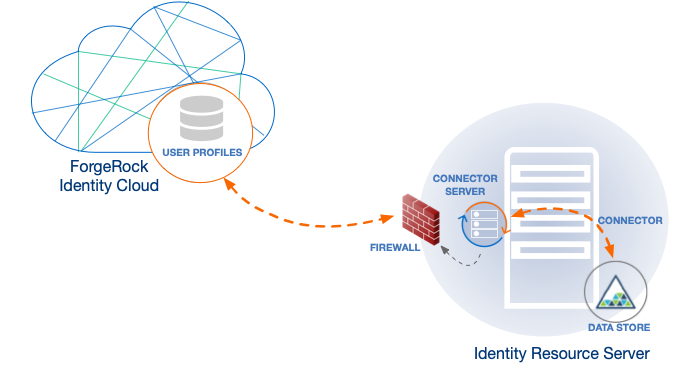
The opposite also happens. When you edit a user’s profile in your tenant, the connector makes the change in the user’s account in your resource server. For a quick take on Advanced Identity Cloud syncing and provisioning, refer to a related example in "Assignments".
Data reconciliation
Advanced Identity Cloud reconciles data when changes occur in your identity profiles or in user accounts stored in resource servers.
An Advanced Identity Cloud connector first compares an identity profile to its corresponding user account in the resource server. If conflicting information exists, Advanced Identity Cloud resolves the conflicts based on your preferences. Then Advanced Identity Cloud updates both the identity profile and the user account.
Load balancing and failover
Use a connector server cluster (a cluster of connector servers) when you want to set up load balancing or failover. A connector server cluster connects to multiple resource servers.
When you configure the connector server cluster for load balancing, Advanced Identity Cloud distributes incoming authentication or authorization requests among the clustered servers. The connector service determines where a request is directed. Request traffic flows evenly, and no single connector works faster or more slowly than others in the server cluster. This ensures requests are handled with the greatest efficiency.
When you configure connector servers for failover, if one resource server stops, then your Advanced Identity Cloud redirects requests to a standby resource server. This ensures your end users don’t experience a loss of service. When the stopped resource server restarts, Advanced Identity Cloud directs requests to the restarted server.
Deactivate the RCS OAuth 2.0 client
The RCS OAuth 2.0 client is activated by default. If you do not need to synchronize your tenant data using a connector, you can deactivate the client:
-
In the Advanced Identity Cloud admin console, go to OAuth2 Clients.
-
Click RCSClient.
-
Click Active, then select Inactive.
-
The client is immediately deactivated.
If you deactivate the RCS OAuth 2.0 client, you can reactivate it at any time.
Bulk import identities
You can use a CSV file to bulk import identities into PingOne Advanced Identity Cloud. This is useful when you want to add a large number of identities to a role or assignment in a single operation.
Import identities in bulk
Before you begin:
You’ll need a CSV file containing the identity profiles you want
to import. The file must comply with this CSV template example:
CSV template example
{
"_id": "template",
"header": "\"userName\",\"givenName\",\"sn\",\"mail\",\"description\",\"accountStatus\",\"telephoneNumber\",
\"postalAddress\",\"address2\",\"city\",\"postalCode\",\"country\",\"stateProvince\",\"preferences/updates\",
\"preferences/marketing\""
}
Be sure to use commas as separators. Any other separator may cause errors.
Learn more about generating this file in Import bulk data.
-
In the Advanced Identity Cloud admin console, go to Identities > Import.
-
On the Import Identities page, click + New Import.
-
On the New Import dialog box, select the realm-target you want to import to.
Tell me more
The target can be any managed object such as a user, role, or assignment defined within a realm. For example, you could import ten user profiles to the Bravo realm - Roles target. The imported roles are added to the
bravo_rolemanaged object in Advanced Identity Cloud. -
Click Next.
-
(Optional) If you haven’t already generated a CSV file, click CSV Template. to download an example file.
If you use this file:
-
Replace the attributes in this file with attributes in your identity resource server.
-
Delete all unused attributes.
-
-
Enter the name of the CSV file to upload.
-
Choose a property Advanced Identity Cloud can use to match an entry in the CSV file to an identity profile in your realm-target.
Tell me more
For example, you could choose the username property. If username
bjensenexists in your CSV file, Advanced Identity Cloud tries to verify that a user profile with the usernamebjensenalso exists in your tenant. If verified, then Advanced Identity Cloud updates the entirebjensenuser profile. If no match is found, then Advanced Identity Cloud creates a user profile forbjensen. -
Click Next.
The Import Complete dialog box indicates real-time import progress. When the import is complete, Advanced Identity Cloud displays the number of new, updated, unchanged, and failed imports.
-
(Optional) To download a CSV file containing a list of identity profiles that failed to import, click Download CSV.
-
Click Done.
Constrain identity queries in the UI
PingOne Advanced Identity Cloud lets you constrain queries in two ways when managing identities with the Advanced Identity Cloud admin console:
-
By requiring all Advanced Identity Cloud admin console users to provide a minimum number of characters when searching for identities.
-
By forbidding delegated administrators from sorting and searching resource collections.
Constraining how the Advanced Identity Cloud admin console can be used can improve overall Advanced Identity Cloud performance because the constraints forbid queries that might inadvertently use a large amount of computing resources.
|
If you encounter slow or failed searches when searching for users in the IDM admin UI, learn more in Searching for users in the UI is very slow in Advanced Identity Cloud. |
Require a minimum length search string
You can require Advanced Identity Cloud administrators to enter a minimum length string when querying identities using the Advanced Identity Cloud admin console. This setting also disables sorting search results unless a minimum length string has been specified in the search box.
Applying this setting can speed up the time it takes to retrieve records from large identity data sets.
This setting only affects queries performed in the Advanced Identity Cloud admin console. It does not affect Advanced Identity Cloud REST API queries.
To apply the setting:
-
In the Advanced Identity Cloud admin console, go to Identities > Configure to access the Configure Identities page.
-
Click on an identity profile. For example, if you want to configure the UI for managing identities in the Alpha realm, click Alpha realm - User.
-
Enter a number greater than zero in the Minimum Characters field.
-
Click Save.
To verify that the setting is in effect:
-
Go to Identities > Manage.
-
Select the identity profile that corresponds to the one you configured when you applied the setting.
-
Click one of the column titles at the top of the search results to attempt to sort the results.
You should not be able to sort the results. Sorting by column should have been disabled.
-
Specify a string in the Search field that has fewer characters than the minimum number of characters you specified in the profile’s configuration. Then, press Enter.
The search operation should not be permitted.
-
Specify a string in the Search field that has the minimum number of characters you specified in the profile’s configuration. Then, press Enter.
The search operation should be permitted.
-
Click one of the column titles at the top of the search results to sort the results.
Sorting the search results should now be permitted.
Forbid sorting or searching resource collections
A resource collection is a set of identities that has a relationship with another identity. For example:
-
All the users with a particular role assignment
-
All the users who are members of an organization
You can forbid Advanced Identity Cloud delegated administrators from sorting resource collections and performing searches within resource collections in the Advanced Identity Cloud admin console.
This setting only affects delegated administrators using the hosted account pages. It does not affect tenant administrators using the Advanced Identity Cloud admin console.
To apply the setting:
-
In the Advanced Identity Cloud admin console, go to Identities > Configure to access the Configure Identities page.
-
Click on an identity profile. For example, if you want to configure the UI for managing identities in the Alpha realm, click Alpha realm - User.
-
Click the Disable sorting and searching on grids that use this object as a resource collection toggle.
-
Click Save.
To verify that the setting is in effect:
-
Sign off from Advanced Identity Cloud.
-
Sign on to Advanced Identity Cloud as a delegated administrator.
-
Select an identity profile that has a relationship with the profile you configured when you applied the setting.
For example, if you disabled sorting and search for Alpha realm - User grids, then you could select Alpha realm - organization because organizations have members (which are users).
-
Find the name of an organization for which you’re the delegated administrator.
-
Click its More () menu, and choose Edit.
-
Click Members to bring up the collection of users that are members of your organization.
-
Click First Name to attempt to sort the identities by first name.
Sorting the search results should not be permitted.
User identity attributes and properties reference
You might need to work with user identity attributes in PingOne Advanced Identity Cloud for the following reasons:
-
To customize the identity attribute display names shown in the user profile in the UI
-
To reference the identity attributes in scripts and API calls
|
The attribute and property names are not consistent between the underlying AM and IDM services. To address this, the reference tables depict the equivalent attribute. |
Using the reference tables
-
If you write scripts for AM that access user profiles, then use AM attribute names. User profile script examples: OAuth2 access token modification; OIDC claims; decision node scripts for authentication journeys (trees).
-
If you write scripts for IDM that access managed objects, then use IDM property names. Managed object script examples:
onUpdate,onCreate,onDelete, and so forth. -
If you use APIs to access managed objects or user profiles:
-
Calls to
/amAPIs must use AM attribute names. -
Calls to
/openidmAPIs must use IDM property names.
-
|
If you use the IDM admin console to change the display name of a property, the change is reflected in both the IDM admin console and the Advanced Identity Cloud admin console; however, on the API side and in scripts, the generic names remain unchanged. |
Reference tables
Basic user attributes
| Display Name | IDM Property | AM Attribute |
|---|---|---|
Username[8] |
|
|
Common Name |
|
|
Display Name |
|
|
Password |
|
|
Status |
|
|
First Name[8] |
|
|
Last Name[8] |
|
|
Email Address[8] |
|
|
Description |
|
|
Telephone Number |
|
|
Address 1 |
|
|
City |
|
|
State/Province |
|
|
Postal Code |
|
|
Country |
|
|
Additional user attributes
| Description | IDM Property | AM Attribute |
|---|---|---|
Alias list |
|
|
Applications |
|
|
Applications I Own |
|
|
Assigned dashboard |
|
|
Assignments |
|
|
Consented Mappings |
|
|
Custom attributes |
|
|
Direct Reports |
|
|
Manager |
|
|
Authorization Roles |
|
not available[10] |
Effective Assignments |
|
|
Effective Applications |
|
|
Effective Groups |
|
|
Effective Roles |
|
|
Groups |
|
|
KBA |
|
|
Preferences |
|
|
Profile image |
|
|
Provisioning Roles |
|
|
Organizations I Administer |
|
|
Organizations I Own |
|
|
Organizations to which I Belong |
|
|
|
|
|
|
|
|
Task Proxies[12] |
|
n/a |
Task Principals[12] |
|
|
| Description | IDM Property | AM Attribute |
|---|---|---|
Notifications |
|
|
Revision |
|
|
User Metadata |
|
|
UUID |
|
|
General purpose extension attributes
Strings
| Display Name | IDM Property | AM Attribute |
|---|---|---|
Generic Indexed String 1 |
|
|
Generic Indexed String 2 |
|
|
Generic Indexed String 3 |
|
|
Generic Indexed String 4 |
|
|
Generic Indexed String 5 |
|
|
Generic Indexed String 6[13] |
|
|
Generic Indexed String 7[13] |
|
|
Generic Indexed String 8[13] |
|
|
Generic Indexed String 9[13] |
|
|
Generic Indexed String 10[13] |
|
|
Generic Indexed String 11[13] |
|
|
Generic Indexed String 12[13] |
|
|
Generic Indexed String 13[13] |
|
|
Generic Indexed String 14[13] |
|
|
Generic Indexed String 15[13] |
|
|
Generic Indexed String 16[13] |
|
|
Generic Indexed String 17[13] |
|
|
Generic Indexed String 18[13] |
|
|
Generic Indexed String 19[13] |
|
|
Generic Indexed String 20[13] |
|
|
Generic Unindexed String 1 |
|
|
Generic Unindexed String 2 |
|
|
Generic Unindexed String 3 |
|
|
Generic Unindexed String 4 |
|
|
Generic Unindexed String 5 |
|
|
Multivalues
| Display Name | IDM Property | AM Attribute |
|---|---|---|
Generic Indexed Multivalue 1 |
|
|
Generic Indexed Multivalue 2 |
|
|
Generic Indexed Multivalue 3 |
|
|
Generic Indexed Multivalue 4 |
|
|
Generic Indexed Multivalue 5 |
|
|
Generic Unindexed Multivalue 1 |
|
|
Generic Unindexed Multivalue 2 |
|
|
Generic Unindexed Multivalue 3 |
|
|
Generic Unindexed Multivalue 4 |
|
|
Generic Unindexed Multivalue 5 |
|
|
Dates
| Display Name | IDM Property | AM Attribute |
|---|---|---|
Generic Indexed Date 1 |
|
|
Generic Indexed Date 2 |
|
|
Generic Indexed Date 3 |
|
|
Generic Indexed Date 4 |
|
|
Generic Indexed Date 5 |
|
|
Generic Unindexed Date 1 |
|
|
Generic Unindexed Date 2 |
|
|
Generic Unindexed Date 3 |
|
|
Generic Unindexed Date 4 |
|
|
Generic Unindexed Date 5 |
|
|
Integers
| Display Name | IDM Property | AM Attribute |
|---|---|---|
Generic Indexed Integer 1 |
|
|
Generic Indexed Integer 2 |
|
|
Generic Indexed Integer 3 |
|
|
Generic Indexed Integer 4 |
|
|
Generic Indexed Integer 5 |
|
|
Generic Unindexed Integer 1 |
|
|
Generic Unindexed Integer 2 |
|
|
Generic Unindexed Integer 3 |
|
|
Generic Unindexed Integer 4 |
|
|
Generic Unindexed Integer 5 |
|
|
Multivalue 2FA profile attributes
| Display Name | IDM Property | AM Attribute |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Overview
PingOne Advanced Identity Cloud end users experience and regularly interact with user interfaces (UIs) and user self-service capabilities.
Advanced Identity Cloud provides different UI customization options depending on the needs of your organization.
Advanced Identity Cloud end users can manage their own data, reset their password, retrieve their username, and more. The robust capabilities of Advanced Identity Cloud allows you to customize the end user screens, the applications they have access to, and the data they have access to. User self-service journeys by defining journeys and configuring the information end users can access, manage, and the actions they can take.
End-user UX options for authentication journeys and account management
When you integrate your applications with PingOne Advanced Identity Cloud, you must provide your end users with a UX (user experience) that handles authentication journeys and account management.
Advanced Identity Cloud provides these end-user UX options:
Advanced Identity Cloud hosted pages
Use Advanced Identity Cloud’s built-in and fully-featured UIs with no development work.
Ping (ForgeRock) Login Widget
Use a widget to integrate authentication journeys easily into your client-side JavaScript web applications.
Ping SDKs
Use SDKs for web, Android, or iOS applications. Integrate the SDK into Advanced Identity Cloud using the REST API.
Advanced Identity Cloud REST API
Build your own custom UIs without any Ping Identity prebuilt components and integrate with Advanced Identity Cloud REST API.
The options are not mutually exclusive, and you may need a combination of them to meet your company’s requirements. For a quick take on which option is most suitable for you, learn more in Compare end-user UX options.
UX options
Advanced Identity Cloud hosted pages
Advanced Identity Cloud hosted pages provide OOTB UIs for the following:
-
End-user journeys, such as sign on, registration, and password reset
-
End-user account activities, such as managing profile information, viewing application access, and viewing roles and entitlements
This is the most straightforward end-user UX option since all the necessary capabilities are readily available.
Hosted pages can be customized with themes. Themes let you adjust layouts and add company logos, headers, and footers. They also let you change the colors of buttons, links, backgrounds, and more. You can create multiple themes in a realm, set the default theme for the realm, and assign specific themes to different end-user journeys.
Hosted pages are useful if you have limited theming needs or want to try new registration or authentication flows without integrating them into an application. The hosted pages UI is designed for web applications and isn’t supported in native applications.
This UX option only lets you use centralized journey flows in your applications, with embedded journey flows not supported. Specifically, Ping Identity does not support embedding hosted pages in HTML frames.
This is the only UX option that supports SAML journey flows that use Advanced Identity Cloud as the IdP.
Learn more in Hosted pages.
Ping (ForgeRock) Login Widget
The Ping (ForgeRock) Login Widget provides an OOTB UI for end-user authentication journeys, such as sign on, registration, and password reset. It doesn’t provide a UI for account management.
The Login Widget is low-code and framework-agnostic; it can be initiated with a few lines of code and can be easily integrated into any modern JavaScript application. It does not currently support server-side rendering (SSR), including Node.js.
The Login Widget provides OOTB support for localization, social login, WebAuthn, passkey, device profile, token management, and compliance with WCAG standards. It is highly themeable and customizable with CSS and Javascript.
Learn more in Ping (ForgeRock) Login Widget.
Ping SDKs
The Ping SDKs let you develop your own custom UI for web, Android, or iOS applications. You then integrate it with your Advanced Identity Cloud tenant using the REST API.
Each SDK provides an OOTB UI module that allows you to prototype your custom UI; however, it is only provided as a starting point, and it is not intended for production use.
This option offers a lot of flexibility if you want to customize the behavior, layout, and theming of the UI, or want to support Android and iOS applications. Using it requires a higher level of technical skill than the previous options.
SDKs can use centralized and embedded journey flows.
Learn more in Ping SDKs.
Advanced Identity Cloud REST API
The most flexible UX option is to build your own custom UIs and integrate with the Advanced Identity Cloud REST API. However, this is also the most complex and time-consuming UX option, as you need to build everything yourself without any Ping Identity prebuilt components.
In addition, you will also need deep identity implementation experience, including an understanding of how to securely store tokens locally.
Learn more in Advanced Identity Cloud REST API.
Ping Identity Platform login and end-user UIs (deprecated)
| Ping Identity no longer recommends or supports this UX option due to the complexity of configuring the distributable packages. For a quick take on alternative options, learn more in Compare end-user UX options. |
Ping Identity also provides the hosted pages UIs as distributable packages, known as the platform login and end-user UIs. You can self-host one or both of the UIs and configure them to use your Advanced Identity Cloud tenant.
This UX option offers flexibility if you want to customize the layout of the UIs or customize the theming beyond what the hosted pages provide. The UIs support web applications but not native applications.
This UX option also lets you use both centralized and embedded journey flows in your applications.
For background information about the platform end-user and login UIs, learn more in Platform UIs.
Compare end-user UX options
You can find background information on UX options in PingOne Advanced Identity Cloud in End-user UX options for authentication journeys and account management.
Compare development effort against flexibility
The choice of end-user UX option is a balance between development effort and flexibility; the more flexible the option, the more complex and time-consuming it is to develop and implement:
Compare specific features
More specifically, the end-user UX option you choose will be based on a combination of these features:
| Feature | Hosted pages | Login Widget | SDKs | APIs |
|---|---|---|---|---|
OOTB end-user authentication journey UI |
Yes |
Yes |
No |
No |
OOTB end-user authentication journey support |
Yes |
Yes |
Yes |
No |
OOTB end-user account management UI |
Yes |
No |
No |
No |
Hosted by |
Ping Identity |
You |
You |
You |
Theming |
Limited |
Some limitations |
No limitation |
No limitation |
Pixel-perfect implementation of design mockups |
No |
No |
Yes |
Can be developed |
Web application (browser) |
Yes |
Yes |
Prototype UI only |
Can be developed |
Native applications (Android, iOS) |
No |
No |
Prototype UI only |
Can be developed |
Localization |
Yes |
Yes |
N/A |
Can be developed |
Yes |
No |
Yes |
Can be developed |
|
No |
Yes |
Yes |
Can be developed |
|
SAML supported |
Yes |
No |
No |
Can be developed |
CAPTCHA supported |
Yes |
Yes |
Yes |
Can be developed |
QR codes supported |
Yes |
Yes |
Yes |
Can be developed |
WebAuthn supported |
Yes |
Yes |
Yes |
Can be developed |
Passkey supported |
Yes |
Yes |
Yes |
Can be developed |
Device profile supported |
N/A |
Yes |
Yes |
Can be developed |
Token management supported |
No |
Yes |
Yes |
Can be developed |
WCAG compliance |
Not always 100% |
Yes |
N/A |
Can be developed |
Social login |
Yes |
Apple, Facebook, Google only |
Apple, Facebook, Google only |
Can be developed |
Include third-party CSS and JS |
No |
Yes |
Yes |
Can be developed |
End-user UX journey flows
Journey flows define the sign-on experience for end users. The End-user UX options available in PingOne Advanced Identity Cloud offer two journey flows:
Not every end-user UX option supports both centralized and embedded journey flows. Learn more in Compare end-user UX options for more information.
Centralized journey flows
Centralized journey flows redirect end users to an external page to sign in. This is a common experience for most users. This approach is considered the security best practice for Advanced Identity Cloud, ensuring all your applications and websites can share the same, centralized authentication processes.
An example of a centralized journey flow is Google G Suite, where an end user is redirected to the same authentication page no matter which application they’re trying to access.
The following video shows a centralized journey flow with Ping SDKs:
Use the hosted pages and the SDK end-user UX options to implement centralized journey flows.
Embedded journey flows
Embedded journey flows offer a more traditional sign-on experience, as end users are not redirected to an external page.
Embedded journey flows aren’t considered to be a security best practice for the following reasons:
-
Individual applications have access to end user’s credentials.
-
Individual applications have access to the authorization grant.
-
Each application must manually build in security during the sign-on process.
The following video shows an embedded journey flow with Ping SDKs:
Use the Login Widget and the SDK end-user UX options to implement embedded journey flows.
Hosted pages
The hosted pages feature in Advanced Identity Cloud provides a pre-built, cloud-hosted user interface that you can use out-of-the-box for common identity operations, significantly accelerating your deployment and development time. Instead of building every sign-on, registration, and self-service profile page from scratch, Advanced Identity Cloud hosts these pages for you.
Advanced Identity Cloud offers two types of hosted pages:
-
Hosted journey pages: These pages guide an end user through an authentication journey. You can use them for sign-on, registration, multi-factor authentication (MFA) enrollment and verification, password reset processes, or any other authentication flow defined in a journey.
-
Hosted account pages: These pages are accessed by end users after they’ve successfully authenticated, allowing them to manage their own profile and security settings. You can also use them to allow delegated administration, enabling end users to manage other end users' profiles based on the permissions you assign.
Hosted journey pages example page
|
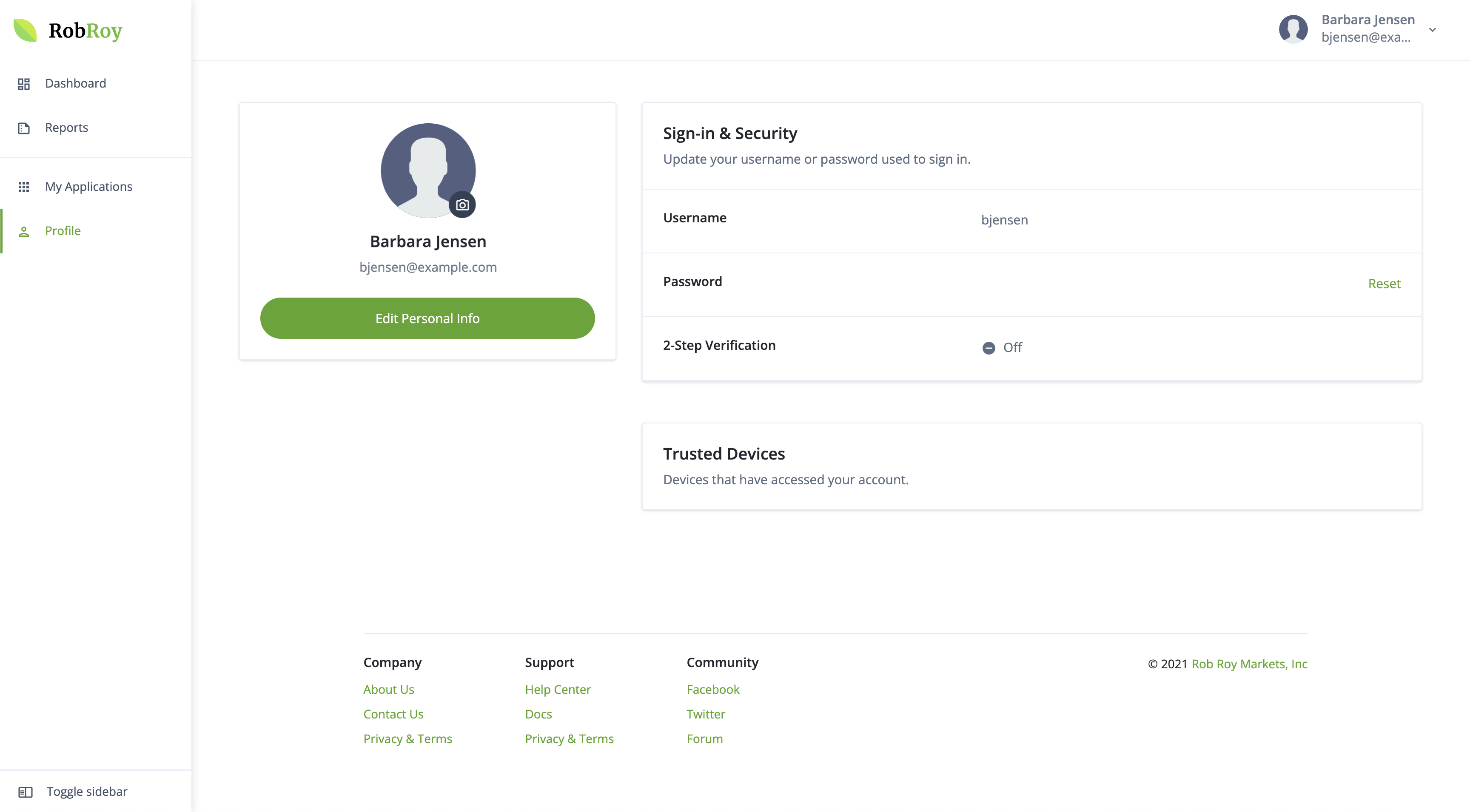
Hosted account pages example page
|
The look and feel of the hosted pages can be customized in each realm to match your company’s branding guidelines using an easy-to-use editor in the Advanced Identity Cloud admin console:
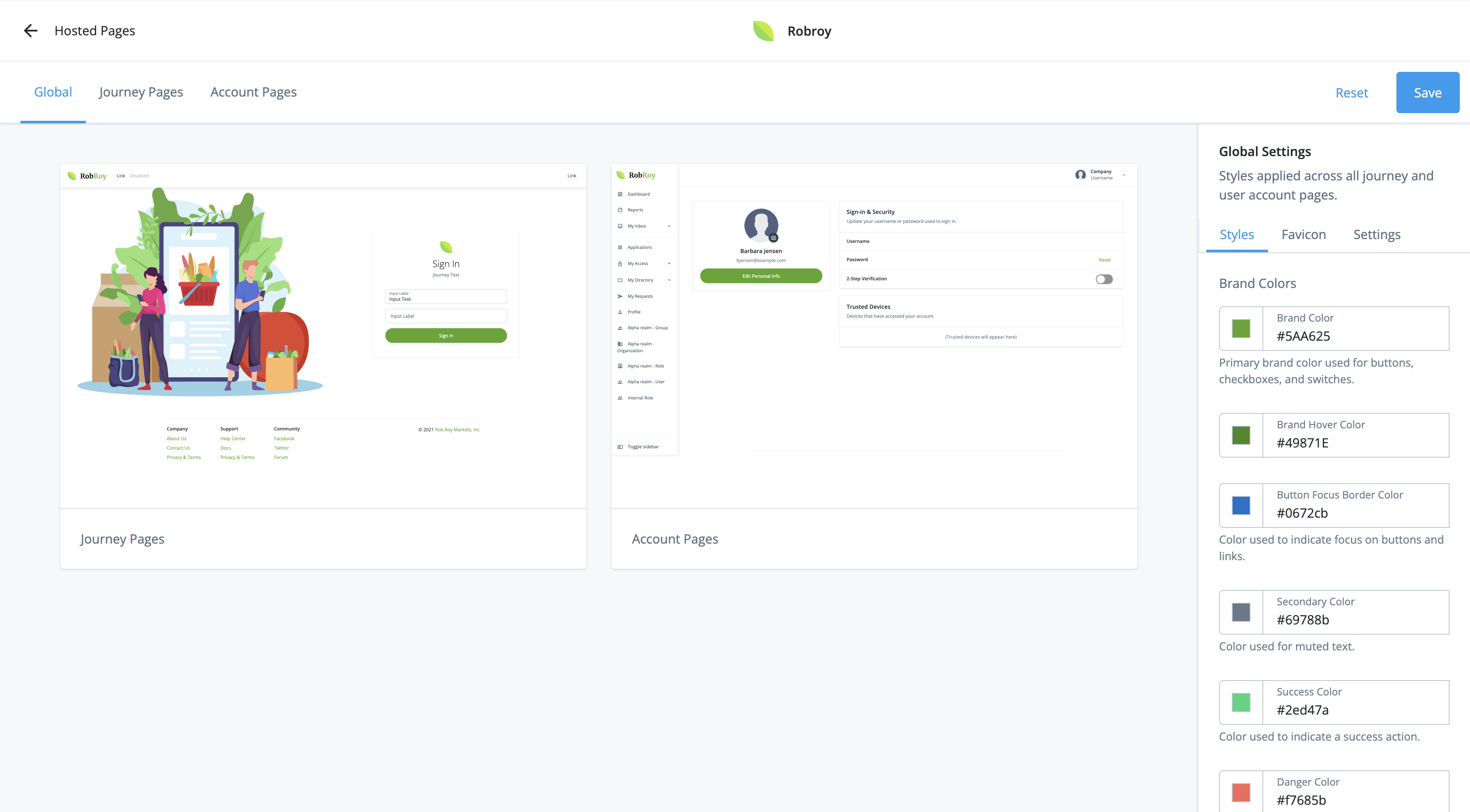
Key features and customization
While they are pre-built, hosted pages are highly customizable to ensure they match your brand.
-
Theming and branding: You can create and apply themes to customize the look and feel (colors, fonts, layout, logos) to meet your company’s branding guidelines. This allows the pages to look like a seamless part of your application.
-
Localization: Hosted pages support multiple languages (localization), allowing you to serve users in different regions with their preferred language.
-
Configurability: Within the Advanced Identity Cloud admin console, you can configure what information is displayed and which actions users are allowed to take.
-
Easy integration: They are the simplest UX option to implement, as they are part of the cloud service.
-
Security: Hosted pages are maintained and updated by Ping Identity, ensuring they adhere to the latest security standards and best practices.
Learn how to customize and use hosted pages
-
Customize hosted pages: Customize the look and feel of the sign-on (journey) pages. This includes logos, headers, footers, the layout of the overall page, and the actions and information your end users have access to in the hosted account pages.
-
Localize hosted pages: Support different languages in the hosted pages with localization.
-
Configure hosted account pages: Configure hosted account pages for end-user profile management.
Sign on as an end user using hosted pages
To sign on to the hosted account pages for a realm:
-
Access the
Loginjourney using one of the following URL formats:-
If you are using the tenant domain, use one of these URL formats, replacing <realm> with the value
alphaorbravo:-
Full URL format:
https://<tenant-env-fqdn>/am/XUI/?realm=<realm>&authIndexType=service&authIndexValue=Login -
Shortcut URL format:
https://<tenant-env-fqdn>/enduser/?realm=<realm>
-
-
If you are using a custom domain, use one of these URL formats:
-
Full URL format:
https://<custom-domain-fqdn>/am/XUI/?authIndexType=service&authIndexValue=Login -
Shortcut URL format:
https://<custom-domain-fqdn>/enduser/
-
-
-
Enter sign-on credentials.
-
Click Next. The end user is signed on to the hosted account pages.
Deactivate hosted journey pages
You can use the Ping SDKs or APIs to create and host your own custom journeys. If you do this, Ping Identity recommends that you deactivate the hosted journey pages to ensure there is no risk of unauthorized access to the sign-on, registration, or password reset pages by a malicious user.
Deactivating hosted journey pages disables them in both the Alpha and Bravo realms. You cannot deactivate hosted journey pages for just one realm.
| Hosted journey pages can be deactivated independently of hosted account pages. |
When you deactivate the hosted journey pages, Advanced Identity Cloud displays the following web page to unauthorized end users:
After you deactivate the default hosted journey pages, you can still administer the tenant environment while preventing unauthorized access to default journey information.
For an explanation about how hosted pages integrate with the default journey, learn more in Journeys.
Deactivate hosted account pages
Hosted account pages are activated by default. If you deactivate them, you can reactivate them at any time.
You can use the Ping SDKs or APIs to create and host your own custom account pages. If you do this, Ping Identity recommends that you deactivate the hosted account pages to ensure there is no risk of unauthorized access to end-user profile information by a malicious user.
Deactivating hosted account pages disables them in both the Alpha and Bravo realms. You cannot deactivate hosted account pages for just one realm.
| Hosted account pages can be deactivated independently of hosted journey pages. |
When you deactivate the hosted account pages, Advanced Identity Cloud displays the following web page to unauthorized end users:
After deactivating the default end-user profile, you can still use the hosted end-user journey UI while denying unauthorized access to end-user profiles. Your customers manage only their own profiles or delegate administration using your application.
-
In the Advanced Identity Cloud admin console, open the TENANT menu (upper right), and go to Tenant Settings > Global Settings.
-
Click End User UI.
-
On the End User UI page, do one of the following:
-
To activate hosted pages, beside Hosted Account Pages, click Activate. The Global Settings toggle displays the status as Active.
-
To deactivate hosted pages, beside Hosted Account Pages, click Deactivate. The Global Settings toggle displays the status as Inactive.
-
The change takes effect immediately.
|
When you deactivate hosted pages, all hosted pages associated with your tenant are deactivated. |
Customize hosted pages
Themes let you customize the look and feel of Advanced Identity Cloud hosted journey and account pages, including the information presented to end users and the actions they can take.
Notes on themes:
-
Advanced Identity Cloud realms have a default theme that includes the colors of buttons and links, typefaces, and so on. This default theme applies to the hosted journey and account pages. You can add custom themes so that your end users are presented with screens specific to their authentication journey.
-
Custom themes let you create a different look and feel for each brand that you support, including logos, favicon, headers, footers, scripted tags, and the actions and information end users can see.
-
A theme is followed throughout an authentication journey. This means that if an end user signs on through the hosted journey pages with a specific theme, the remaining pages in the journey will have that same theme.
Add a custom theme
In the Advanced Identity Cloud admin console:
-
Select Hosted Pages > + New Theme.
To duplicate an existing theme, click its ellipsis icon () and then click Duplicate. -
Enter a theme name that describes the theme’s purpose; for example, the brand associated with an authentication journey.
-
Click Save.
-
Use the tabs and options to customize various aspects of the theme:
Tab Option What you can customize Global
Styles
You can customize:
-
Brand Colors: This includes colors for buttons, checkboxes, switches, high-level alert actions, and success actions.
-
Typography: The font applied to all journeys and customer-facing pages.
-
Buttons: The colors of buttons and their radius.
-
Links: The color of links, including when you hover over them and the option to bold all links.
-
Switches: The background color.
Favicon
Favicon logo displayed for all journey and account pages. You can localize the favicon. Learn more in Localize the favicon and theme logo.
Settings
The theme name and any journey(s) using this theme.
From this screen, you can select journeys to apply to your theme. Journey Pages
Styles
You can customize:
-
Page Background: This includes the color of the journey background as well as a background image (optional).
-
Sign-in Card: Customize the styles of the card in the center of the journey page where end users enter their credentials. This includes the card colors, field colors, card shadow, border radius, and if the input text labels should be placed above or inside the input field.
-
Global Styles: These are the styles you set in the Global tab. Modifying this section from the Journey Pages updates the Global tab styles.
Logo
Logo to display for sign-on and registration pages. The displaying of the logo is optional. You can localize the logo. Learn more in Localize the favicon and theme logo.
Layout
This includes:
-
Layout: The position of the sign-on card on the page.
-
Button Position: The position of the button inside the sign-on card.
-
Header: Place a header above the sign-on card. Learn more in Custom headers and footers.
-
Add a skip to main content link in the header for accessibility: Add a button that lets screen readers skip header content.
-
Focus Options: Choose how the tab key behaves in relation to the header:
-
Always focus on header: The tab index is set to the beginning of the header and the first tab key press by an end user focuses on the first link in the header.
-
Always focus on card: The tab index is advanced to the sign-on card and the first tab key press by an end user focuses on the first link or field in the sign-on card.
-
Focus on header for initial step - focus on card for subsequent steps: On the initial browser page load of a journey, the first tab key press by an end user focuses on the first link in the header. On each subsequent browser page load as the journey progresses, the first tab key press by an end user focuses on the first link or field in the sign-on card.
-
-
-
Footer: Place a footer below the sign-on card. Learn more in Custom headers and footers.
-
Error Heading Fallback: Turn off the error heading that displays as a fallback if there is no heading in the page content.
-
Remember Me: Add a checkbox to the sign-on card that lets end users choose to have their username remembered and prepopulated. If checked, the UI stores an end-user’s username in local storage after their next sign-on attempt.
The optional Label field lets you specify a custom label to display to the end user to replace the default label of Remember Me.
-
Scripted Tags: Add HTML scripted tags to journey pages.
Account Pages
Styles
This includes customizing the colors of:
-
The left end-user Navigation pane.
-
The Top Bar where the user logs out.
-
The Page Styles that present user information.
-
The Cards that are contained within the page that display various information.
-
Global Settings: These are the styles you set in the Global tab. Modifying this section from the Account Pages updates the Global tab styles.
Logo
Logo to display on customer-facing pages
Layout
This includes:
-
Navigation: Configure the visibility, ordering, grouping, and icons of menu items in the hosted account pages left menu. You can also add custom menu items. Learn more in Customize the account pages menu.
-
Footer: Place a footer below all account pages. Learn more in Custom headers and footers.
-
Profile Page: Learn more in Configure visible information and end-user actions.
-
Scripted Tags: Add HTML scripted tags to account pages.
-
-
Click Save.
-
(Optional) Configure the new theme as the default theme for the realm:
The default theme is the theme that’s used when you don’t apply a specific theme to an authentication journey.
-
In the Advanced Identity Cloud admin console, go to Hosted Pages.
-
In the list of themes, click the new theme’s ellipsis icon () and then click Set as Realm Default.
-
| Customize a theme for hosted pages also demonstrates how to customize the look and feel of the hosted pages to match your company’s branding . |
Localize the favicon and theme logo
To localize the favicon or theme logo:
-
On the Global, Journey Pages, or Account Pages tabs, click the Favicon or Logo tabs from the right pane.
-
Click the favicon or logo .
-
Click + Specify a Locale.
-
In the Locale field, enter the ISO 639-1 (2 letter country code) for the language. For example, for French the value would be
fr. -
Click Add.
-
In the Favicon URL field or the Logo URL field, enter the URL for the favicon or logo.
The images must be publicly accessible. -
To set alternative text for the logo, in the Alt Text field, enter alternate text.
-
Click Update.
-
Click Save.
Apply a custom theme to a journey
In the Advanced Identity Cloud admin console:
-
Select Journeys.
-
Select the journey to apply the custom theme.
-
Click Edit.
-
Click ... > Edit Details.
-
Select Override theme.
-
Select the custom theme that you want to apply to this journey, then click Save.
|
Theme definitions and the mappings between authentication journeys and themes are stored in
Advanced Identity Cloud as configuration objects. They are therefore "static" in terms of Advanced Identity Cloud promotion.
If you add a new theme or logo, your change must go through the promotion process. Theme
selection can be dynamic, however. If you set a theme in a page node during a journey, for
example, by setting |
Custom headers and footers
Each theme lets you configure localized custom headers and footers:
| Header | Footer | |
|---|---|---|
Journey pages |
||
Account pages |
n/a |
Headers and footers can take HTML or inline CSS to insert links, classes, and other elements. Scripting isn’t supported in headers and footers.
The account footer is separate from the journey footer. This lets you set up different buttons, links, and other elements, that display to an end user after they sign on.
Enable headers and footers for a theme
-
In the Advanced Identity Cloud admin console, go to Hosted Pages, then select a theme.
-
Select either Journey Pages or Account Pages.
-
In the panel on the right-hand side, click Layout.
-
Find the Header section (journey pages only), then enable the switch.
-
Find the Footer section, then enable the switch.
-
Edit headers and footers
-
Follow the steps above to find the appropriate Header or Footer section, then click the preview to open the editor.
-
If you do not need localized content, edit the HTML as appropriate, then go to step 4.
-
If you need localized content:
-
Add as many locales as you need. Learn more in Localize headers and footers.
-
Use the locale selector to change locales, and edit the HTML in each locale as appropriate.
-
-
Click Save.
Localize headers and footers
-
Follow the steps above to find the appropriate Header or Footer section, then click the preview to open the editor.
-
To add an initial locale for the existing header or footer content:
-
Click + Specify a Locale to open a secondary modal.
-
In the Add a Locale secondary modal, enter a locale identifier; for example,
fr(French), orfr-ca(French - Canada). -
Click Add to add the locale and close the secondary modal.
-
The + Specify a Locale link will now be replaced by a locale selector, with the new locale preselected.
-
-
To add an additional locale:
-
Click the locale selector, then click + Add Locale to open a secondary modal.
-
In the Add a Locale secondary modal, enter a locale identifier; for example,
es(Spanish), ores-ar(Spanish - Argentina). -
Click Add to add the locale and close the secondary modal.
-
The new locale will now be available in the locale selector, and be preselected. The header or footer content for the new locale will be a copy of the header or footer content from the initial locale.
-
Translate the header or footer content for the new locale.
-
-
Repeat step 3 for as many locales as you need.
-
Click Save.
Configure actions and information for end users
Hosted journey pages
You can configure the following self-service features to control the actions and information displayed to end users when they sign on:
Configure terms and conditions
Configure the terms and conditions your end users must accept before they can complete a registration journey. Learn more in Terms and conditions.
Configure privacy and consent
Configure the external resources your end users can choose to share their data with. Learn more in Privacy and consent.
Configure security questions
Configure the security questions your end users answer during a registration journey and can later use during a reset journey to verify their identity. Learn more in Security questions.
Hosted account pages
You can control the information displayed and the actions end users can take from the hosted account pages. Learn more in:
Configure visible information and end-user actions
Your end users can only see the information and take actions that you configure.
To configure the information users can see and the actions they can take:
-
In the Advanced Identity Cloud admin console, go to Hosted Pages.
-
Select a theme or click + New Theme.
If you create a new theme, enter a Name for the theme and click Save.
-
Click the Account Pages tab. This refers to the Advanced Identity Cloud admin console pages.
-
In the panel on the right-hand side, click Layout.
-
The Profile Information section determines the actions and information end users can see. Select or deselect any of the following:
Profile page component Description Personal Information
Lets end users view and update their personal data. The attributes displayed depend on settings at the property level. Learn more in User identity attributes and properties reference.
You can prevent end users from updating specific personal data. Learn more in Prevent end users from editing specific personal data.
Sign-in & Security
Enable any of the following:
-
Password: Allow end users to update their password. Uses an existing session. This correlates to the default journey UpdatePassword.
To change the journey used for password updates:
-
In the Advanced Identity Cloud admin console, select Native Consoles > Access Management.
-
In the left navigation pane, click Services.
-
Select Self Service Trees.
-
In the updatePassword field, enter the name of the journey.
-
Click Save Changes.
-
-
Security Questions: Lets end users reset their security questions on their profile.
-
2-step verification: If an end user has registered a device for two-factor/MFA, this option displays as enabled.
If enabled, an additional Change button displays to end users. End users can select this button to rename their device(s) or delete their device(s) from Advanced Identity Cloud.
Social Sign-In
Lets end users view the social providers that have authenticated with, such as Google or Facebook.
For details on letting end users connect to social providers from their profile page, learn more in Social authentication. After you configure social providers and create the journey, add it as the connectSocial journey for the realm:
-
In the Advanced Identity Cloud admin console, select Native Consoles > Access Management.
-
In the left navigation pane, click Services.
-
Select Self Service Trees.
-
Add a connectSocial field whose value is the name of the journey.
-
Click Save Changes.
Trusted Devices
Lets end users view the devices that have been used to sign on to their account. End users can update the name of the device.
To populate the Trusted Devices tab, add the Device Profile Collector node to your authentication journeys to collect end-user device information. Authorized Applications
Lets end users view and manage the applications that have access to their personal information.
Preferences
Lets end users view and set preferences for communication. For example, an end user can select if they want to receive emails regarding special offers and services.
Consent
Lets end users view and manage how their data is shared with third parties.
Account Controls
Lets end users download the data Advanced Identity Cloud has about them in a JSON format and lets end users delete their account (identity) information.
-
-
Click Save.
Prevent end users from editing specific personal data
End users can view their Advanced Identity Cloud personal data by selecting Profile > Edit Personal Info in the hosted account pages.
When you enable personal information for end users in the theme, all Advanced Identity Cloud properties are marked as User Editable. This means end users can view and update all their personal data directly in the hosted account pages. However, you might want to prevent end users from updating certain data. For example, email addresses could require verification, which can’t be guaranteed if end users can modify them.
To prevent end users from updating specific personal data:
-
In the Advanced Identity Cloud admin console, select Native Consoles > Identity Management.
-
Select Configure > Managed Objects from the top tabs.
-
Click the user identity to update, for example Alpha_user.
-
On the Properties tab, select the property to modify.
-
On the Details tab, select Show advanced options.
-
Deselect the User Editable option.
-
Click Save. The property is no longer editable by end users.
-
Repeat steps 4 - 7 for every property you want to prevent end users from updating.
| You can hide a property from the personal data in the hosted account pages by deselecting the Viewable option. However, this hides the property of the user identity from both end users and tenant administrators. |
Use script tags in hosted pages
You can include script tags in hosted pages to integrate third-party scripts such as customer analytics.
-
In the Advanced Identity Cloud admin console, go to Hosted Pages, then select a theme.
-
Select either Journey Pages or Account Pages.
-
In the panel on the right-hand side, click Layout.
-
Find the Script Tags section.
-
In the HTML field, enter your script code. The following example adds a script for the OneTrust cookie consent service:
<script type="text/javascript" charset="UTF-8" src="https://cdn.cookielaw.org/scripttemplates/otSDKStub.js" data-domain-script="<account-id>"></script>(1) <script type="text/javascript"> function OptanonWrapper() {}; </script>1 In this example, <account-id>needs replacing with a OneTrust account ID.-
Do not attempt to use scripts with nested nodes. All nodes must be at the same level.
-
The script code can include comments.
-
The script code can include all valid attributes listed here: https://developer.mozilla.org/en-US/docs/Web/HTML/Element/script#attributes.
-
The script code must be wrapped in
<script>tags.
-
-
Click Save.
-
-
Update the tenant’s Content Security Policy:
-
If the tenant has an active report-only policy, update it by adding the domain of the third-party script to the
script-srcpolicy directive. -
If the tenant has an active enforced policy, update it by adding the domain of the third-party script to the
script-srcpolicy directive.
-
Localize hosted pages
PingOne Advanced Identity Cloud lets you localize hosted pages to support the different languages of your
end users. Use ISO-639-1 language codes (for
example fr and de) to provide locale specific content in as many locales as you need.
Localize at feature level
Localize related features
You can localize the following features related to hosted journey and account pages:
| Feature | Description |
|---|---|
Hosted pages |
Learn more in Localize headers and footers and Localize the favicon and theme logo. |
Security questions |
Learn more in Security questions. |
Terms and conditions |
Learn more in Terms and conditions. |
Email templates |
Learn more in Email templates. |
Localize journey authentication nodes
You can individually localize authentication nodes that display content in hosted journey pages. For example, the Page node lets you add content to the Page Header property to display an initial journey message to end users. You can define as many localized versions of the message as you need:

Localize at UI level
You can localize static content and server messages in the hosted pages using translation configuration. Learn more in Localize tenant admin console and hosted pages.
Specify a preferred language for journey pages
By default, Advanced Identity Cloud localizes the content of journey pages using the value of the Accept-Language header, which is typically derived from the language settings in the end-user’s browser. You can override this behavior by appending a locale query parameter to the journey URL.
For example, to set the language to French, append locale=fr to the journey URL:
https://<tenant-env-fqdn>/am/XUI/?realm=/alpha&locale=fr&authIndexType=service&authIndexValue=LoginThe language used to localize journey pages is determined in the following order of priority:
-
The
localequery parameter in the journey URL (for example,&locale=fr). -
The language preference set in the end-user’s browser.
-
The default locale for hosted pages (
en), used when neither a query parameter nor a browser language is provided.
Hosted account pages
Hosted account pages are pre-built, customizable web pages that provide end users with self-service capabilities for managing their accounts after they’ve signed on. They’re a key part of the end-user experience and are designed to help you quickly set up common end-user self-service operations without needing to build your own custom web pages from scratch.
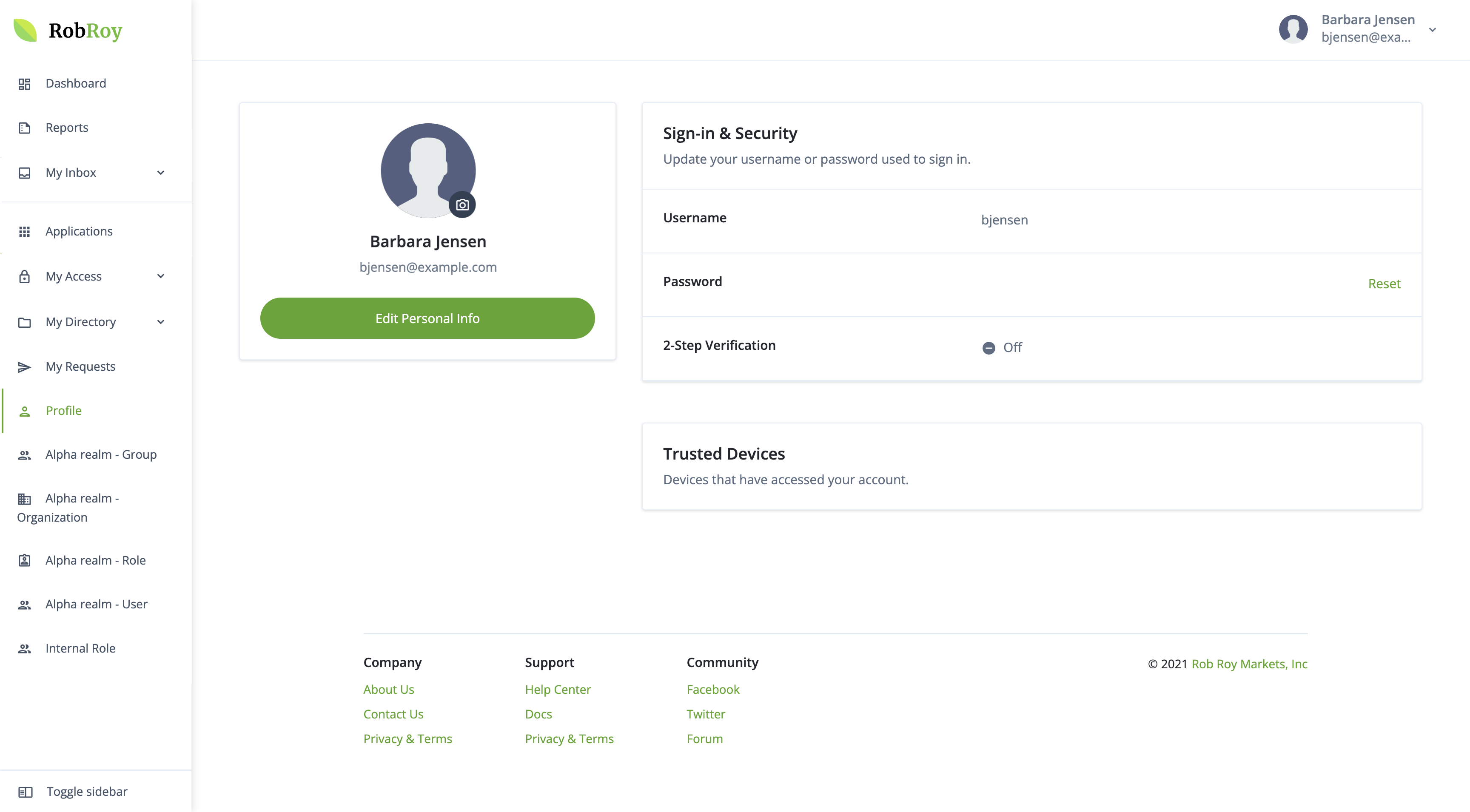
Summary of features
These pages allow authenticated end users to perform essential account management tasks. The specific features available depend on your Advanced Identity Cloud configuration, but commonly include:
-
Profile management: End users can view and update their personal information (for example, name, email address, address) if they’re configured to be editable.
-
Security management:
-
Password updates: Allowing end users to change their password.
-
Multi-factor authentication (MFA): Managing registered devices or two-step verification settings.
-
Security questions: Viewing or resetting their security questions.
-
-
Access and entitlement viewing: End users can see details about their access within integrated applications, which often includes:
-
My applications: Viewing and navigating to applications they have access to.
-
Roles and entitlements: Seeing the roles and specific privileges (entitlements) they have been assigned in onboarded target applications.
-
Account controls: Allowing end users to download or delete their own account data (if enabled).
-
-
Identity governance: With Identity Governance[1], end users can also:
-
Manage delegates: Assign individuals to handle their access reviews or other delegated items.
-
View direct reports: Managers can access the accounts, entitlements, and roles of their direct reports.
-
Manage requests: Create or view requests they have submitted for gaining access to an application, entitlement, or role.
-
Account pages menu
The hosted account pages include a navigation menu that provides easy access to the various self-service features.
The items displayed in the menu depend on a number of factors:
-
Availability and visibility: Menu items display based on their availability and visibility as follows:
-
Available as standard, visible by default to all end users.
-
Available as standard, visible based on the delegated administrator privileges of the end user.
-
Available and visible to all end users as part of an add-on capability, such as IGA[1].
-
-
Configuration: You can override the visibility of menu items through configuration settings to suit your company’s needs. This lets you hide certain menu items that are not relevant to your end users. For example, hiding the organization menu item from organization administrators whose regular job only requires managing users within the organization, but not the organization itself. Learn more in Change menu item visibility.
You can also change the order and grouping of menu items in the navigation menu, add custom menu items, and modify their icons to align with your branding.
Menu items available as standard
The following table summarizes the behavior of the menu items that are available as standard in the hosted account pages:
| Menu item | Visibility | Description |
|---|---|---|
Dashboard |
|
Displays tasks and information that require the end user’s attention. |
Applications |
Lets the end user view and access their applications. Displays SAML-based applications and Bookmark applications, but not OAuth 2.0 applications. |
|
Profile |
Lets the end user view and edit their account profile, including personal information. The actions available on this page vary depending on the configurations set in Configure actions and information for end users. |
|
Reports |
Lets the end user view any reports shared with them by a tenant administrator. |
|
Alpha realm - Assignment |
|
Lets the end user access the management interface for the identity type. |
Alpha realm - Group |
||
Alpha realm - Organization |
||
Alpha realm - Role |
||
Alpha realm - User |
||
Internal Role |
Menu items available with add-on capabilities
The following table summarizes the behavior of the menu items that are available with add-on capabilities in the hosted account pages:
| Menu item | Visibility | Description |
|---|---|---|
My Inbox Submenu items:
|
|
Displays all items assigned to an end user. This includes:
|
My Access Submenu items:
|
Lets the end user view the access they have in Advanced Identity Cloud and via applications. This includes:
Learn more in Request access to resources. |
|
My Directory Submenu items:
|
Lets the end user manage the delegates and direct reports (employees) they have. End users can perform the following actions:
|
|
My Requests |
Lets the end user view and create requests to access resources, such as target applications, entitlements, or roles. Learn more in Request access to resources. |
Customize the account pages menu
Enable delegated administrator menu items
By default, the menu items related to delegated administrator privileges (for example, Alpha realm - User) aren’t visible to end users.
These menu items become visible only when an end user is assigned to an internal role that has at least the view privilege for the corresponding identity type.
The following steps describe how to create an internal role with the necessary privileges to manage an identity type and assign it to an end user.
-
In the Advanced Identity Cloud admin console, go to Identities > Manage.
-
Click Internal Roles.
-
Click New Internal Role.
-
In the New Internal Role modal:
-
Enter a name for the internal role. For example,
Delegated Administrator. -
(Optional) Enter a description for the internal role.
-
Click Next.
-
-
In the Internal role Permissions modal:
-
In the Choose an identity object list, select an identity type. For example, Alpha realm - Users.
-
Click Add.
-
Select at least the View privilege and any additional privileges for the identity type using the Create, Update, and Delete options.
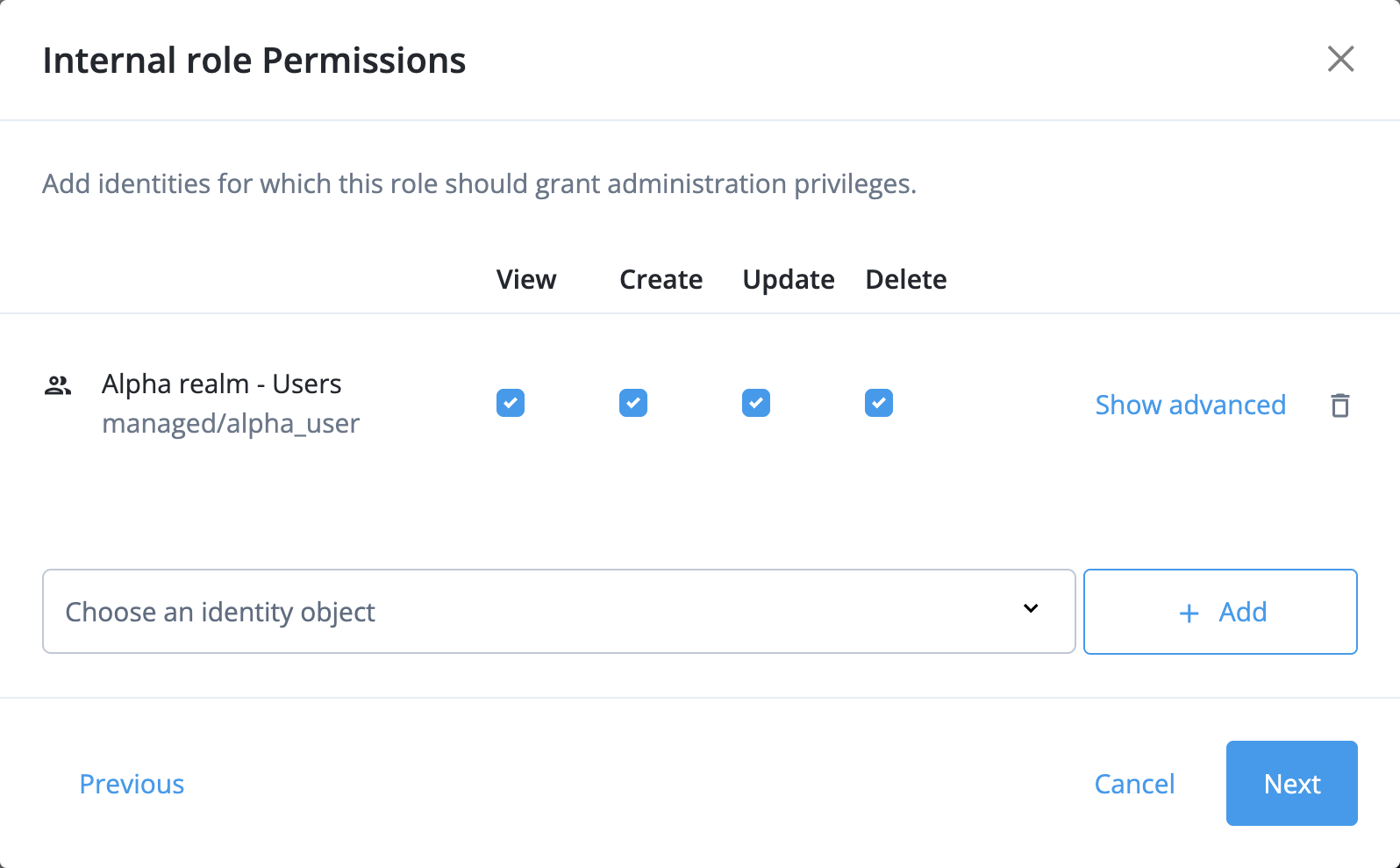
-
(Optional) Repeat the previous three steps to add additional identity types and their corresponding privileges as necessary.
-
Click Next.
-
-
In the Dynamic Internal role Assignment modal, click Next.
-
In the Time Constraint modal, click Save to create the internal role.
-
In the Internal Role page, click the Members tab, then click Add Members.
-
In the Add Members modal, select a user identity from the Members list that you want to assign the internal role to, then click Save.
The end user can now see the corresponding delegated administrator menu items in the hosted account pages navigation menu when they sign on.
|
For more complex delegated administration use cases, learn more in: |
Change the visibility of a menu item
Change the visibility of menu items to streamline the end-user experience.
-
In the Advanced Identity Cloud admin console, go to Hosted Pages, then select a theme.
-
Select Account Pages.
-
In the panel on the right-hand side, click Layout, then scroll to the Navigation section.
-
To hide a menu item:
-
Find the menu item you want to hide, and click its ellipsis icon ().
-
Click Delete. This removes the menu item from the navigation menu, although it remains available for re-adding later.
-
Click Save.
-
-
To show a previously hidden menu item:
-
Click the add icon ().
-
From the list of available menu items, select the menu item you want to show, then click Next.
-
Configure the menu item:
-
(Optional) Change the Label.
-
(Optional) Change the Icon Code. For a list of available icon codes, refer to Material Icons.
-
(Optional) If the menu item has submenu items, select which submenu items to include using the checkboxes under Dropdown Items. By default, all submenu items are selected.
-
-
Click Add.
-
(Optional) Click the menu item’s drag indicator icon () and drag the menu item to the desired position in the menu.
-
Click Save.
-
Change menu item order and grouping
Change the order and grouping of menu items in the navigation menu to suit your company’s needs.
-
In the Advanced Identity Cloud admin console, go to Hosted Pages, then select a theme.
-
Select Account Pages.
-
In the panel on the right-hand side, click Layout, then scroll to the Navigation section.
-
To reorder menu items:
-
Click a menu item’s drag indicator icon () and drag it to the desired position in the menu.
-
Repeat for any other menu items you want to reorder.
-
-
To group menu items:
-
(Optional) Add additional divider menu items to the menu:
-
Click the add icon ().
-
From the list of available menu items, select Divider, then click Next.
-
Repeat as necessary to add multiple divider menu items.
-
-
(Optional) Remove existing divider menu items that you don’t need:
-
Find the divider menu item you want to remove, and click its ellipsis icon ().
-
Click Delete.
-
-
Click the drag indicator icon () of a Divider menu item and drag it to the desired position in the menu to create a visual separation between groups of menu items. Repeat for any other Divider menu items you want to reposition.
-
Click Save.
-
Change menu item label and icon
Change the label or icon for your menu items to better align with your company’s branding.
-
In the Advanced Identity Cloud admin console, go to Hosted Pages, then select a theme.
-
Select Account Pages.
-
In the panel on the right-hand side, click Layout, then scroll to the Navigation section.
-
Find the menu item you want to change, and click its ellipsis icon ().
-
Configure the menu item:
-
(Optional) Change the Label.
-
(Optional) Change the Icon Code. For a list of available icon codes, refer to Material Icons.
-
(Optional) If the menu item has submenu items, select which submenu items to include using the checkboxes under Dropdown Items. By default, all submenu items are selected.
-
-
Click Save.
Add custom menu items
Add a custom menu item to link to other Ping Identity resources such as the PingOne Dock, PingOne self service, or a specific journey or flow. You can also link to resources in your company that end users may need to access.
-
In the Advanced Identity Cloud admin console, go to Hosted Pages, then select a theme.
-
Select Account Pages.
-
In the panel on the right-hand side, click Layout, then scroll to the Navigation section.
-
Click the add icon ().
-
From the list of available menu items, select Custom Link, then click Next.
-
Configure the menu item:
-
Enter a menu Label.
-
(Optional) Change the Icon Code. For a list of available icon codes, refer to Material Icons. Otherwise, the default link icon () is used.
-
Enter an absolute URL for the custom menu item. The URL opens in a new browser tab when the end user clicks the menu item.
-
Click Add.
-
-
(Optional) Click the menu item’s drag indicator icon () and drag the menu item to the desired position in the menu.
-
Click Save.
Ping SDKs
For an overview of all UI integration options, learn more in End-user UX options for authentication journeys and account management.
The Ping SDKs let you rapidly build applications against the PingOne Advanced Identity Cloud REST APIs.
Leverage Ping Identity’s identity best practices for token exchange, security, and the optimal OAuth 2.0 flow.
Ping SDKs are highly customizable and require a high level of technical skill; therefore, the SDK documentation is hosted separate from Advanced Identity Cloud documentation.
Integrate Ping SDKs with any of the following:
Upload provided files to integrate with Android or iOS apps
Associating a website(s) to your application is crucial when implementing Ping SDKs with Android or iOS applications. This allows you to share credentials or provide redirects within an application. Within the context of Ping SDKs, it is important to associate the SDKs with Android or iOS applications.
Google and Apple both provide ways assist in this process:
-
Android assetlinks.json - Establish trust between the application and a website(s) by automatically opening links for that domain.
-
iOS apple-app-site-association - Associate a website(s) with your application by having the associated domain file on your website and the appropriate entitlement in your application.
Upload an Android assetlinks.json file
To help you integrate your Android apps with PingOne Advanced Identity Cloud, you can upload an assetlinks.json file
to a tenant environment and access it through a custom domain associated with the environment. You
can do this for each custom domain in your set of environments.
As the configuration in your upper environments is immutable, you can only modify the content of
an assetlinks.json file in your development environment configuration. You must then promote any
configuration changes to your upper environments.
Ensure you have set up a
custom domain for
each environment and realm where you need to upload an assetlinks.json file.
|
High-level process
The high-level process to configure and promote an assetlinks.json file is as follows:
-
In your development environment, use the endpoint naming format
/openidm/config/fidc/assetlinks.<custom-domain-fqdn>to setassetlinks.jsoncontent in your configuration with an association to a custom domain. For example, for the custom domainid.mycompany.com, use the endpoint/openidm/config/fidc/assetlinks.id.mycompany.com. -
Promote the configuration to the upper environment that’s configured to use the custom domain; for example, if your production environment is configured to use the custom domain, you will need to promote to your staging environment, and then promote again to your production environment.
-
Access the
assetlinks.jsonfile from your custom domain using the endpoint/.well-known/assetlinks.json; for example, for the custom domainid.mycompany.com, use the URL https://id.mycompany.com/.well-known/assetlinks.json.
View an assetlinks.json file
Use a custom domain to view an assetlinks.json file. You don’t need to use an access token as
the file is publicly accessible.
Show request
$ curl \
--request GET 'https://<custom-domain-fqdn>/.well-known/assetlinks.json'(1)| 1 | Replace <custom-domain-fqdn> with a custom domain, for example id.mycompany.com. |
Show response
{
"relation": [
"delegate_permission/common.handle_all_urls",
"delegate_permission/common.get_login_creds"
],
"target": {
"namespace": "web",
"site": "https://id.mycompany.com"
}
}Upload or replace an assetlinks.json file
-
Refer to the High-level process for configuring and promoting an
assetlinks.jsonfile. -
In your development environment:
-
Set the
assetlinks.jsonfile contents in your configuration:Show request
$ curl \ --request PUT 'https://<tenant-env-fqdn>/openidm/config/fidc/assetlinks.<custom-domain-fqdn>' \(1) (2) --header 'Authorization: Bearer <access-token>' \(3) --header 'Content-Type: application/json' \ --data-raw '{(4) "data": [ { "relation": [ "delegate_permission/common.handle_all_urls", "delegate_permission/common.get_login_creds" ], "target": { "namespace": "web", "site": "https://id.mycompany.com" } } ] }'1 Replace <tenant-env-fqdn> with the domain of your development environment; for example, openam-mycompany.forgeblocks.com.2 Replace <custom-domain-fqdn> with the custom domain, for example id.mycompany.com.3 Replace <access-token> with the access token. 4 Replace the example assetlinks.jsonJSON content with your own JSON content. Note that the JSON content is wrapped in adataobject wrapper.Show response
{ "_id": "fidc/assetlinks.id.mycompany.com", "data": [ { "relation": [ "delegate_permission/common.handle_all_urls", "delegate_permission/common.get_login_creds" ], "target": { "namespace": "web", "site": "https://id.mycompany.com" } } ] } -
(Optional) Repeat the previous step for each additional custom domain that needs the
assetlinks.jsonfile uploading or replacing.
-
Run a series of promotions to add the development environment configuration to your upper environments. Learn more in:
-
Use your custom domain to view the assetlinks.json file. If you uploaded or replaced additional
assetlinks.jsonfiles, repeat this for each custom domain.
Delete an assetlinks.json file
-
Refer to the High-level process for configuring and promoting an
assetlinks.jsonfile. -
In your development environment:
-
Delete the
assetlinks.jsonfile contents from your configuration:Show request
$ curl \ --request DELETE 'https://<tenant-env-fqdn>/openidm/config/fidc/assetlinks.<custom-domain-fqdn>' \(1) (2) --header 'Authorization: Bearer <access-token>'(3)1 Replace <tenant-env-fqdn> with the domain of your development environment, for example openam-mycompany.forgeblocks.com.2 Replace <custom-domain-fqdn> with your custom domain, for example id.mycompany.com.3 Replace <access-token> with the access token. Show response
{ "_id": "fidc/assetlinks.id.mycompany.com", "data": [ { "relation": [ "delegate_permission/common.handle_all_urls", "delegate_permission/common.get_login_creds" ], "target": { "namespace": "web", "site": "https://id.mycompany.com" } } ] } -
(Optional) Repeat the previous step for each additional custom domain that needs the
assetlinks.jsonfile deleting.
-
Run a series of promotions to add the development environment configuration to your upper environments. Learn more in:
-
Use your custom domain to view the assetlinks.json file and check that it is empty. If you deleted additional
assetlinks.jsonfiles, repeat this for each custom domain.
Upload an iOS apple-app-site-association file
To help you integrate your iOS apps with PingOne Advanced Identity Cloud, you can upload an apple-app-site-association file
to a tenant environment and access it through a custom domain associated with the environment. You
can do this for each custom domain in your set of environments.
As the configuration in your upper environments is immutable, you can only modify the content of
an apple-app-site-association file in your development environment configuration. You must then promote any
configuration changes to your upper environments.
Ensure you have set up a
custom domain for
each environment and realm where you need to upload an iOS apple-app-site-association file.
|
High-level process
The high-level process to configure and promote an apple-app-site-association file is as follows:
-
In your development environment, use the endpoint naming format
/openidm/config/fidc/apple-app-site-association.<custom-domain-fqdn>to setapple-app-site-associationcontent in your configuration with an association to a custom domain; for example, for the custom domainid.mycompany.com, use the endpoint/openidm/config/fidc/apple-app-site-association.id.mycompany.com. -
Promote the configuration to the upper environment that’s configured to use the custom domain. For example, if your production environment is configured to use the custom domain, you will need to promote to your staging environment, and then promote again to your production environment.
-
Access the
apple-app-site-associationfile from your custom domain using the endpoint/.well-known/apple-app-site-association; for example, for the custom domainid.mycompany.com, use the URL https://id.mycompany.com/.well-known/apple-app-site-association.
View an apple-app-site-association file
Use a custom domain to view an apple-app-site-association file. You don’t need to use an access token as
the file is publicly accessible.
-
View the
apple-app-site-associationfile using aGETrequest:Show request
$ curl \ --request GET 'https://<custom-domain-fqdn>/.well-known/apple-app-site-association'(1)1 Replace <custom-domain-fqdn> with your custom domain; for example, id.mycompany.com.Show response
{ "applinks": { "details": [ { "appIDs": [ "XXXXXXXXXX.com.example.AppName" ], "components": [ { "/": "/reset/*", "comment": "Success after reset password journey" } ] } ] }, "webcredentials": { "apps": [ "XXXXXXXXXX.com.example.AppName" ] } }
Upload or replace an apple-app-site-association file
-
Refer to the High-level process for configuring and promoting an
apple-app-site-associationfile. -
In your development environment:
-
Set the
apple-app-site-associationfile contents in your configuration:Show request
$ curl \ --request PUT 'https://<tenant-env-fqdn>/openidm/config/fidc/apple-app-site-association.<custom-domain-fqdn>' \(1) (2) --header 'Authorization: Bearer <access-token>' \(3) --header 'Content-Type: application/json' \ --data-raw '{(4) "data": { "applinks": { "details": [ { "appIDs": [ "XXXXXXXXXX.com.example.AppName" ], "components": [ { "/": "/reset/*", "comment": "Success after reset password journey" } ] } ] }, "webcredentials": { "apps": [ "XXXXXXXXXX.com.example.AppName" ] } } }'1 Replace <tenant-env-fqdn> with the domain of your development environment; for example, openam-mycompany.forgeblocks.com.2 Replace <custom-domain-fqdn> with your custom domain; for example, id.mycompany.com.3 Replace <access-token> with your access token. 4 Replace the example apple-app-site-associationJSON content with your own JSON content.Show response
{ "_id": "fidc/apple-app-site-association.id.mycompany.com", "data": { "applinks": { "details": [ { "appIDs": [ "XXXXXXXXXX.com.example.AppName" ], "components": [ { "/": "/reset/*", "comment": "Success after reset password journey" } ] } ] }, "webcredentials": { "apps": [ "XXXXXXXXXX.com.example.AppName" ] } } } -
(Optional) Repeat the previous step for each additional custom domain that needs the
apple-app-site-associationfile uploading or replacing.
-
Run a series of promotions to add the development environment configuration to your upper environments. Learn more in:
-
Use your custom domain to view the apple-app-site-association file. If you uploaded or replaced additional
apple-app-site-associationfiles, repeat this for each custom domain.
Delete an apple-app-site-association file
-
Refer to the High-level process for configuring and promoting an
apple-app-site-associationfile. -
In your development environment:
-
Delete the
apple-app-site-associationfile contents from your configuration:Show request
curl \ --request DELETE 'https://<tenant-env-fqdn>/openidm/config/fidc/apple-app-site-association.<custom-domain-fqdn>' \(1) (2) --header 'Authorization: Bearer <access-token>'(3)1 Replace <tenant-env-fqdn> with the domain of your development environment, for example openam-mycompany.forgeblocks.com.2 Replace <custom-domain-fqdn> with your custom domain, for example id.mycompany.com.3 Replace <access-token> with the access token. Show response
{ "_id": "fidc/apple-app-site-association.id.mycompany.com", "data": { "applinks": { "details": [ { "appIDs": [ "XXXXXXXXXX.com.example.AppName" ], "components": [ { "/": "/reset/*", "comment": "Success after reset password journey" } ] } ] }, "webcredentials": { "apps": [ "XXXXXXXXXX.com.example.AppName" ] } } } -
(Optional) Repeat the previous step for each additional custom domain that needs the
apple-app-site-associationfile deleting.
-
Run a series of promotions to add the development environment configuration to your upper environments. Learn more in:
-
Use your custom domain to view the apple-app-site-association file and check that it is empty. If you deleted additional
apple-app-site-associationfiles, repeat this for each custom domain.
User self-service journeys
You must configure user self-service journeys in PingOne Advanced Identity Cloud before your end users can experience them. For example, you can configure journeys for password reset, username retrieval, and more.
Use cases for user self-service
To let end users manage their own accounts in Advanced Identity Cloud, you must configure the necessary settings. For example, if you want users to create their own identities by registering themselves with Advanced Identity Cloud, you need to create a journey that collects the required information. After creating the journey, you must test it and push the journey’s configuration to your production tenant.
The features end users can access depend on what you configure.
The following table references the self-service actions available to end users in Advanced Identity Cloud, provided they are configured. You can configure these self-service journeys:
| Use Case | Description |
|---|---|
Lets end users sign on by collecting a username and password. |
|
Lets end users recover their username. |
|
Lets end users reset their password. |
|
Lets end users update their password, after signing on and obtaining a session. |
|
Lets end users register their own identity in Advanced Identity Cloud. |
|
Lets end users authenticate using social providers, such as Google or Facebook. |
|
Asks users for more information based on a login count. |
|
Creates a journey to let end users sign on with a recovery code if they lose their device. |
For further use cases and questions about configuring the hosted account pages, learn more in FAQ: Advanced Identity Cloud hosted End User UI.
Auth scripting
You can use authentication and authorization (auth) scripting to modify default Advanced Identity Cloud behavior in many situations: client-side authentication, policy conditions, handling OpenID Connect claims, and others.
Use JavaScript for auth scripting in Advanced Identity Cloud. Groovy scripts are deprecated and will eventually be completely replaced with JavaScript scripts.
For JavaScript examples of all auth script types, review the sample scripts. Each sample script includes a list of available variables.
|
Scripts can potentially emit the personally identifiable information (PII) of your end users into Advanced Identity Cloud logs, and then into external services that consume Advanced Identity Cloud logs. Ping Identity recommends that you establish a review and testing process for all scripts to prevent PII leaking out of your Advanced Identity Cloud tenant environments. |
Auth script types
The auth script types available in Advanced Identity Cloud include the following:
Journeys
| Script type | Description | Information |
|---|---|---|
Configuration Provider Node |
Runs in a Configuration Provider node as a step in an authentication journey. |
|
Journey Decision Node |
Runs in a Scripted Decision node as a step in an authentication journey. |
OAuth2 / OIDC
| Script type | Description | Information |
|---|---|---|
OAuth2 Access Token Modification |
Modifies the key-value pairs contained within access tokens before they’re issued to a client. |
|
OAuth2 Evaluate Scope |
Retrieves and modifies scopes for OAuth 2.0 access token introspection. |
|
OAuth2 May Act |
Adds the |
|
OAuth2 Trusted JWT Issuer |
Dynamically retrieves the details of an issuer during the JWT profile for authorization grant. |
|
OAuth2 Validate Scope |
Modifies how Advanced Identity Cloud validates requested OAuth 2.0 scopes. |
|
OIDC Claims |
Modifies or overrides OIDC claims when issuing an ID token
or in the response from the |
SAML
| Script type | Description | Information |
|---|---|---|
SAML2 SP Adapter |
Modifies the processing of the authentication request on the SP. |
|
SAML2 IDP Adapter |
Modifies the processing of the authentication request on the IDP. |
|
SAML2 IDP Attribute Mapper |
Maps user-configured attributes to SAML attributes in the assertion returned by the IDP. |
|
SAML2 NameID Mapper |
Customize the value of the NameID attribute in the SAML assertion on the remote SP. |
Other
| Script type | Description | Information |
|---|---|---|
Client-side Authentication |
Runs on the client during authentication. |
|
Library |
Contains reusable functionality that can be imported into journey decision node scripts or other library scripts. |
|
Policy Condition |
Modifies authorization policy decisions. |
|
Social Identity Provider Profile Transformation |
Runs in a Social Provider Handler node. Adapts the fields received from a social identity provider to align with the fields expected by Advanced Identity Cloud. |
|
PingOne Verify Completion Decision Node |
Runs in a PingOne Verify Completion Decision node so that you can access information about the user’s PingOne Verify transactions. |
|
Some script types aren’t yet available in the Advanced Identity Cloud admin console. To view a list of all the script types, under Native Consoles > Access Management, go to Realms > Realm Name > Scripts and click New Script. |
Manage auth scripts
To manage your auth scripts, go to Realm > Scripts > Auth Scripts.
On the Scripts page, you can view a list of existing scripts. To edit, duplicate, or delete a script, click its More () menu.
The edit option in the More menu opens the script in a lightweight editor that features syntax highlighting and validation checking. You can maximize the editor to full screen to edit larger scripts:
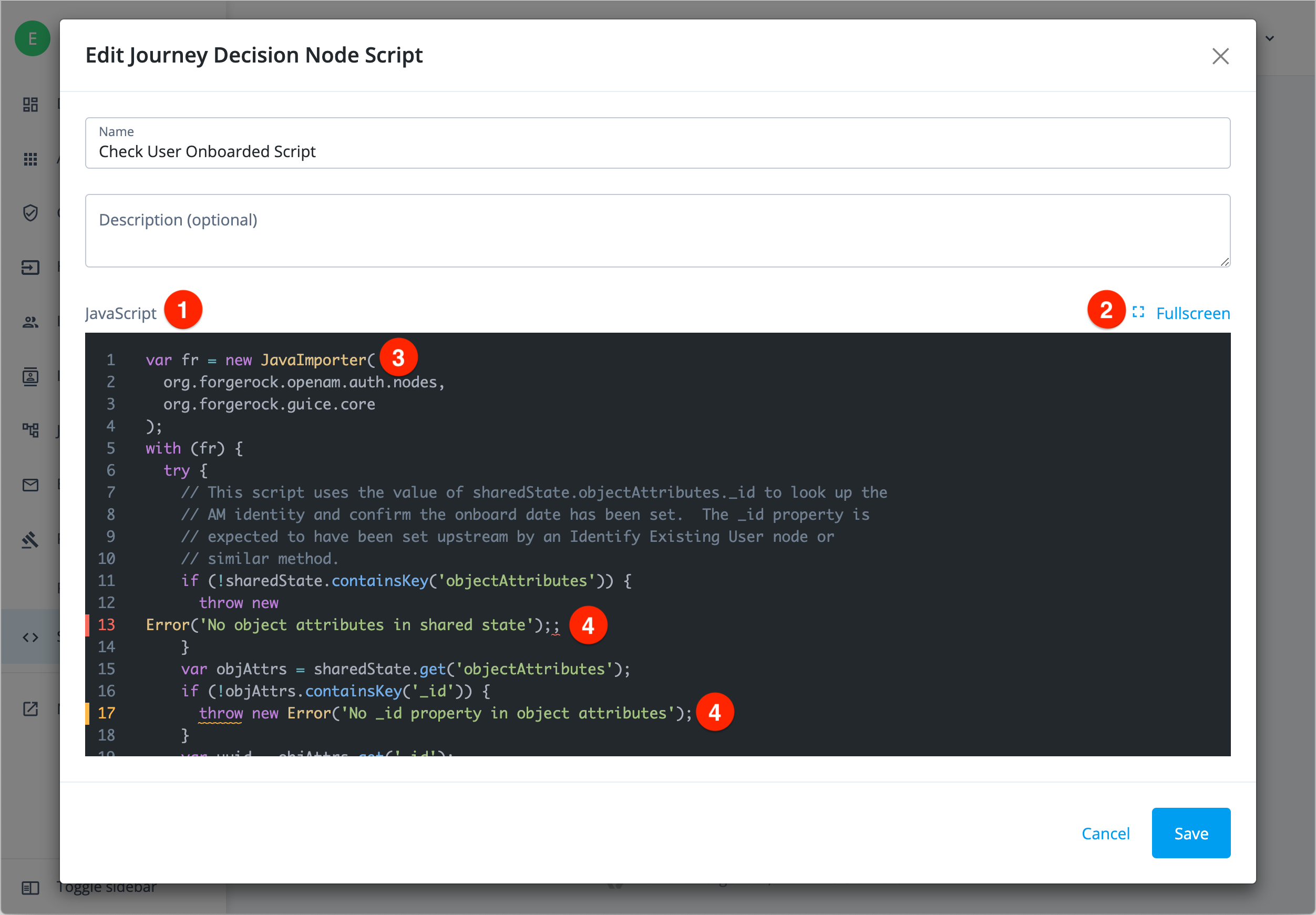
① JavaScript editor
② Fullscreen option
③ Syntax highlighting
④ Syntax error highlighting and validation checking
Create a new auth script
-
Go to Realm > Scripts > Auth Scripts, then click + New Script.
-
Choose an auth script type.
After you select a script type, the editor opens. The editor is prepopulated with a default script for that type, which is intended as a starting point for your custom script.
If you selected the wrong script type, click Previous to select a different script type.
-
If the next-generation script engine is available for the script type, such as for journey decision node scripts, Advanced Identity Cloud displays the Choose Script Engine page.
Select Legacy or Next Generation to set the script engine for your script.
-
Enter a unique Name and optional Description for the script, then click Save.
After you save a script, you can’t change its type.
Journey decision node scripts
Learn more about journeys in Journeys.
You can also create, edit, and validate journey decision node scripts directly from within a Scripted Decision node.
-
Go to Realm > Journeys.
-
Open a journey in the journey editor.
-
Find an existing scripted decision node or add a new one.
-
Select the scripted decision node to open the context pane on the right side.
-
The following screenshot shows where you can create a new journey decision node script ④ or edit an existing one ⑤:
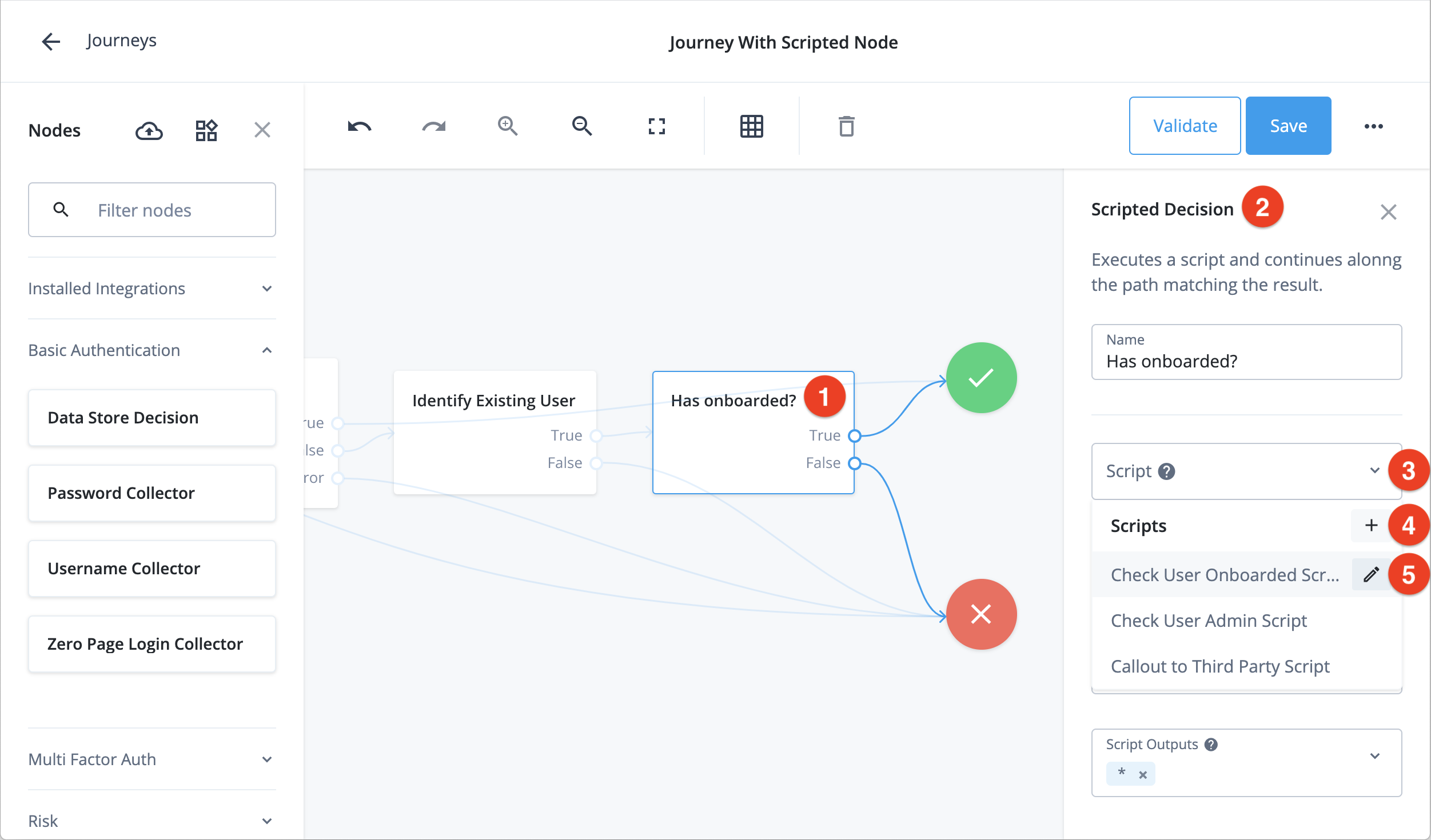
① Scripted decision node
② Context pane
③ Journey decision node script drop-down
④ Add new journey decision node script
⑤ Edit existing journey decision node script
Create a new journey decision node script
Add a new journey decision node script in the journey editor or from Realm > Scripts > Auth Scripts.
-
Select Legacy or Next Generation on the Choose Script Engine page.
Learn more about the enhanced scripting engine in Next-generation scripts.
-
If you create or edit a Next Generation script, click the Libraries icon in the top right to display the following side panel:
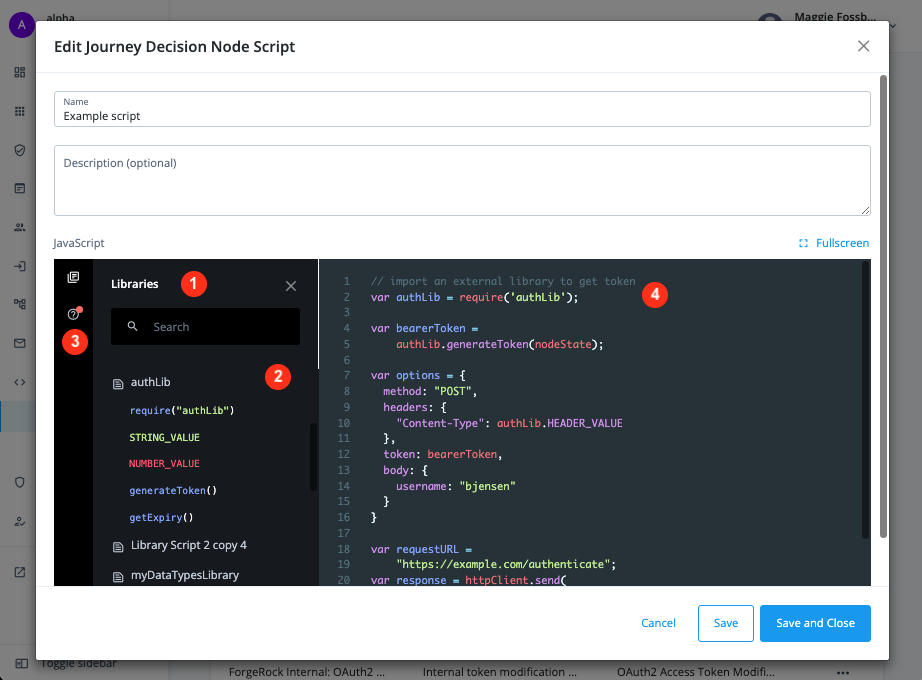
① View and search library scripts to import in your script.
② Click to expand a library script and view its exported methods and constants.
The font colors indicate the exported types:-
Blue for functions
-
Red for numbers
-
Green for strings
-
Orange for boolean types
-
Purple for objects / properties
③ Click the Docs icon to view links to context-related documentation.
A red dot denotes documentation updates.
④ Edit your script and import library scripts as necessary. -
-
Enter a unique Name and optional Description for the script, then click Save.
Custom endpoints
You can use custom endpoints to run arbitrary JavaScript code through the REST API. Custom endpoint scripts are extremely flexible and can extend Advanced Identity Cloud behavior in many ways:
-
Validate user input fields before storing them in a user profile.
-
Create utility functions, such as getting today’s date.
-
Mandate user input fields during registration to support delegated administration decisions.
-
Query identities with a particular relationship, such as being a member of an organization, and page the results.
You can consume custom endpoints within Advanced Identity Cloud or integrate them into your external UIs or system applications.
Custom endpoints scripting introduction
For an introduction to custom endpoints scripting, read the following:
To understand how to create identity object query expressions to use in the request.queryExpression property, learn more in Define and call data queries.
|
|
Scripts can potentially emit the personally identifiable information (PII) of your end users into Advanced Identity Cloud logs, and then into external services that consume Advanced Identity Cloud logs. Ping Identity recommends that you establish a review and testing process for all scripts to prevent PII leaking out of your Advanced Identity Cloud tenant environments. |
Manage custom endpoints
To manage your custom endpoints, go to Realm > Scripts > Custom Endpoints.
On the Custom Endpoints page, you can view a list of existing custom endpoints. To edit, duplicate, or delete a custom endpoint, click its More () menu.
The edit option in the More menu opens the custom endpoint script in a lightweight editor. The editor features syntax highlighting and validation checking. Maximize the editor to full screen to edit larger scripts:
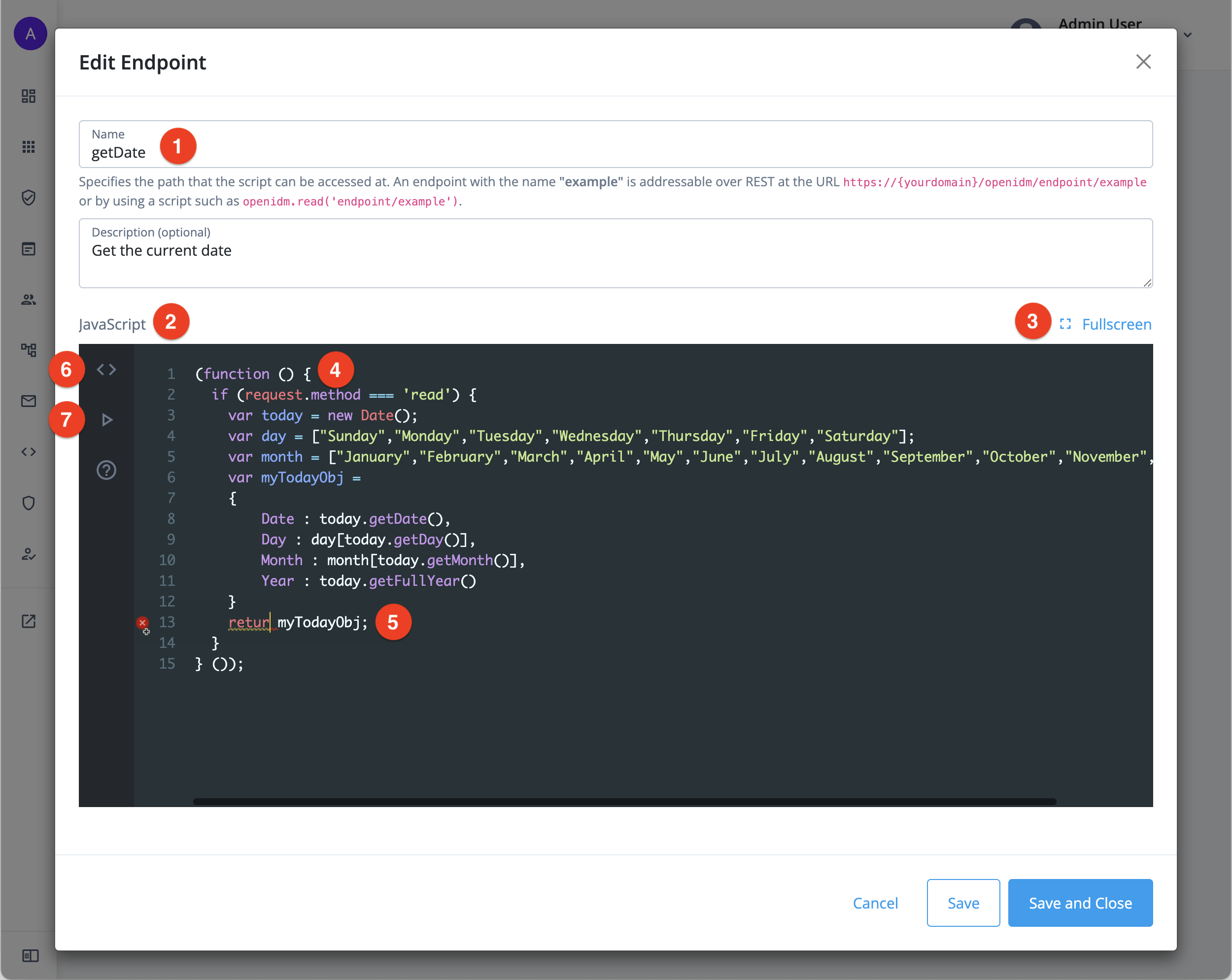
① Endpoint name
② JavaScript editor
③ Fullscreen option
④ Syntax highlighting
⑤ Validation checking
⑥ cURL request tab, learn more in Generate a cURL request for a custom endpoint
⑦ Test tab, learn more in Run a test request for a custom endpoint
Create a custom endpoint
-
Go to Realm > Scripts > Custom Endpoints, then click + New Script.
-
Enter a Name for your new endpoint; for example,
getDate.-
Access the new custom endpoint over HTTP at:
https://<tenant-env-fqdn>/openidm/endpoint/<name> -
Access the new custom endpoint in a script using:
openidm.read('endpoint/<name>')
-
-
(Optional) Enter a Description for your new endpoint; for example,
Get the current date. -
Next, use the editor to create your script. The editor is prepopulated with a default script, which is intended as a starting point for your custom script.
-
To test your script, click Save, then either:
-
When your testing is complete, click Save and Close.
Generate a cURL request for a custom endpoint
In the script editor:
-
Click the angled brackets icon (<>) to open the cURL Request tab.
-
In the Method field, choose an HTTP request method for the cURL request. Learn more about how HTTP request methods relate to the script
request.methodproperty values in this mapping table. -
(Optional) In the Body field, enter a JSON-formatted body for the cURL request (except when using the
GETHTTP request method). For example:{ "param1": "foo", "param2": "bar" }In the script, you can access the body using the request.contentproperty. The example above maps torequest.content.param1andrequest.content.param2. -
Click Generate to output the cURL request, which appears below your script. The cURL request is complete with an access bearer token and ready to run.
-
Click the copy icon () to copy the cURL request from the editor, then paste and run it in a terminal window.
Run a test request for a custom endpoint
In the script editor:
-
Click the triangle icon () to open the Test tab.
-
In the form field, enter a JSON-formatted configuration object for the cURL request. The form field is prepopulated with a default configuration object:
{ "request": { "method": "create" } }This default configuration object creates a request using the
POSTHTTP request method. Learn more about how HTTP request methods relate to the scriptrequest.methodvariable parameter values in this mapping table. -
(Optional) To supply a body with the request, add a
request.contentproperty:{ "request": { "method": "create", "content": { "param1": "foo", "param2": "bar" } } }In the script, you access the body using the request.contentproperty. The example above maps torequest.content.param1andrequest.content.param2. -
Click Run to run the cURL request. The result appears below the editor.
Authenticate to Advanced Identity Cloud REST API
The Advanced Identity Cloud REST API has two different authentication methods, depending on what you are trying to achieve:
-
Use an API key and secret for read-only operations.
Examples: Advanced Identity Cloud monitoring and logging. -
Use an access token for access management operations or identity management operations.
Examples: Setting up authentication journeys or policies; configuring user profiles, roles, or assignments.
Summary of authentication methods
The following table summarizes the REST API endpoints and their different authentication methods:
| REST endpoints | Authentication method |
|---|---|
|
Not applicable (publicly accessible endpoint) |
|
API key and secret. |
|
Access token |
Authenticate to Advanced Identity Cloud REST API with API key and secret
You will need an API key and secret to authenticate to the following Advanced Identity Cloud REST API endpoints:
-
/monitoring -
/logs
Summary of use:
-
Create an API key and secret in the Advanced Identity Cloud admin console.
-
Set the API key and secret as
x-api-keyandx-api-secretHTTP headers for each API request:x-api-key: <api-key> x-api-secret: <api-secret>
Get an API key and secret
-
In the Advanced Identity Cloud admin console, click the user icon, and then click Tenant Settings.
Show me where

-
On the Global Settings tab, click Log API Keys.
-
Click New Log API Key, provide a name for the key, and then click Create Key.
A dialog box appears containing the new keys:
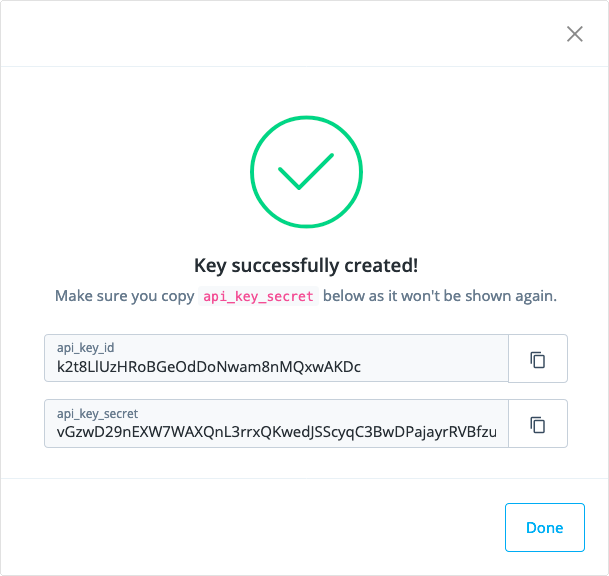
-
Store the
api_key_idandapi_key_secretvalues securely.You cannot view the api_key_secretvalue again once you click Done. -
Click Done.
Use an API key and secret
To use the API credentials, set them as x-api-key and x-api-secret HTTP headers:
Show request
$ curl \
--request GET 'https://<tenant-env-fqdn>/monitoring/logs/sources?_prettyPrint=true' \
--header 'x-api-key: <api-key>' \
--header 'x-api-secret: <api-secret>'Show response
{
"result": [
"am-access",
"am-activity",
"am-authentication",
"am-config",
"am-core",
"am-everything",
"idm-access",
"idm-activity",
"idm-authentication",
"idm-config",
"idm-core",
"idm-everything",
"idm-recon",
"idm-sync"
],
"resultCount": 14,
"pagedResultsCookie": null,
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": 1,
"remainingPagedResults": 0
}Authenticate to Advanced Identity Cloud REST API with access token
You need an access token to authenticate to the following Advanced Identity Cloud REST API endpoints:
-
/am/* -
/openidm/* -
/.well-known/* -
/environment/certificates,/environment/csrs(self-managed certificate endpoints) -
/environment/content-security-policy/* -
/environment/cookie-domains(cookie domains endpoint) -
/environment/custom-domains -
/environment/promotion/*(self-service promotion endpoints) -
/environment/proxy-connect/*(Proxy Connect endpoints) -
/environment/release(release endpoint) -
/environment/restart,/environment/secrets,/environment/variables(ESV endpoints) -
/environment/sso-cookie -
/environment/telemetry(log event exporter endpoints)
Summary of use:
-
Create a service account in the Advanced Identity Cloud admin console and download a private key.
-
Create a JSON Web Token (JWT) and sign it using the private key.
-
Create an access token using the JWT profile for OAuth 2.0 authorization grant flow.
-
Set the access token as a bearer token in the
AuthorizationHTTP header for each API request:Authorization: Bearer <access-token>
Get an access token
Prerequisites
You need the jose command-line tool to run some of the commands. The jose command-line tool is a C-language implementation of the Javascript Object Signing and Encryption (JOSE) standards. You can find installation instructions for your particular package manager in https://command-not-found.com/jose.
| The instructions won’t work using any of the Node.js tools called jose. Although they have the same name, they’re separate implementations of the JOSE standards. |
Task 1: Create a service account and download its private key
-
Follow the steps in Create a new service account.
-
In step 9, save the private key as a local file called
key.jwk. -
Note the ID for the service account you created. An example of an ID is
449d7e27-7889-47af-a736-83b6bbf97ec5.
-
Task 2: Create and sign a JWT
-
Set the following variables in your terminal, to be used as claims in a JWT payload:
-
Set
SERVICE_ACCOUNT_IDto hold the ID of the service account. For use in theiss(issuer) andsub(subject) claims.$ SERVICE_ACCOUNT_ID="<service-account-id>"(1)1 Replace <service-account-id>with the service account ID; for example,449d7e27-7889-47af-a736-83b6bbf97ec5. -
Set
AUDto hold the URL (including port number) where the JWT will be used to request the access token. For use in theaud(audience) claim.$ AUD='https://<tenant-env-fqdn>:443/am/oauth2/access_token' -
Set
EXPto hold a 15-minute expiration time for the JWT, expressed as a Unix timestamp. For use in theexp(expiration time) claim.$ EXP=$(($(date -u +%s) + 899))Service account access tokens have a non-configurable, fixed expiry of 899 seconds (15 minutes), so the previous example sets a timestamp value that matches the fixed expiry. Despite the expiry being non-configurable, you must supply the expclaim, set with a nominal future timestamp, to create an access token successfully. -
Set
JTIto hold a unique ID for the JWT. For use in thejti(JWT ID) claim.$ JTI=$(openssl rand -base64 16)
-
-
Combine the claims to create a payload for the JWT:
$ echo -n "{ \"iss\":\"${SERVICE_ACCOUNT_ID}\", \"sub\":\"${SERVICE_ACCOUNT_ID}\", \"aud\":\"${AUD}\", \"exp\":${EXP}, \"jti\":\"${JTI}\" }" > payload.json -
Sign the JWT using the private key you downloaded and saved as
key.jwkin step 1a:$ jose jws sig -I payload.json -k key.jwk -s '{"alg":"RS256"}' -c -o jwt.txt
Task 3: Get an access token using the JWT profile authorization grant
-
Request an access token from the
/oauth2/access_tokenendpoint using the JWT:$ curl \ --request POST ${AUD} \ --data "client_id=service-account" \(1) --data "grant_type=urn:ietf:params:oauth:grant-type:jwt-bearer" \(2) --data "assertion=$(< jwt.txt)" \(3) --data "scope=<scope>"(4)1 The client ID service-accounttargets the built-in OAuth 2.0 public client for service accounts. The client only allows the JWT profile for OAuth 2.0 authorization grant flow.Access the built-in OAuth 2.0 public client using the tenant FQDN. You cannot access it using an Alpha or Bravo realm alias URL or a custom domain URL. 2 The grant type urn:ietf:params:oauth:grant-type:jwt-bearerrepresents the JWT profile for OAuth 2.0 authorization grant flow.3 The assertionparameter is populated with the output of the signed JWT from step 2c.4 Replace <scope>with a scope or a space delimited set of scopes; for example,fr:idc:esv:*orfr:am:* fr:idm:*. Learn more in Service account scopes. The specified scopes must be the same as (or a subset of) the scopes that you assigned to the service account. -
Examine the response to find the access token, represented as
access_token:{ "access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9... ...8ECmkyDJKow8Qp_Tnp_lGNRJzLWi18iUGQrCTtxyTXw", "scope": "fr:am:* fr:idm:*", "token_type": "Bearer", "expires_in": 899 }
Use an access token
To use the access token with the REST API, set it as a bearer token in the Authorization HTTP header for each API request.
The following example uses the access token to get a list of identities:
Show request
$ curl \
--request GET 'https://<tenant-env-fqdn>/openidm/managed/<realm>_user?_fields=userName,givenName,sn,mail,accountStatus&_prettyPrint=true&_queryFilter=true' \(1)
--header 'Authorization: Bearer <access-token>'(2)| 1 | Replace <realm> with the realm where you created the access token. |
| 2 | Replace <access-token> with the access_token in the authentication response (learn more in Get an access token). |
Show response
{
"result": [
{
"_id": "f413db4c-cebd-4950-81e6-57bdb47921a4",
"_rev": "0000000016e6754b",
"userName": "exampleuser",
"accountStatus": "active",
"givenName": "Example",
"sn": "User",
"mail": "exampleuser@example.com"
},
{
"_id": "15249a65-8f9a-4063-9586-a2465963cee4",
"_rev": "0000000016e6754b",
"userName": "exampleuser2",
"accountStatus": "active",
"givenName": "Example",
"sn": "User",
"mail": "exampleuser2@example.com"
},
{
"_id": "30485bc4-fdbb-4946-8ce4-1a53c6824d92",
"_rev": "0000000016e6754b",
"userName": "exampleuser3",
"accountStatus": "active",
"givenName": "Example",
"sn": "User",
"mail": "exampleuser3@example.com"
}
],
"resultCount": 3,
"pagedResultsCookie": null,
"totalPagedResultsPolicy": "NONE",
"totalPagedResults": -1,
"remainingPagedResults": -1
}Advanced Identity Cloud Postman collection
Advanced Identity Cloud provides REST APIs to help you manage identities, authenticate to the system, monitor Advanced Identity Cloud, and more.
You can also use the AM and IDM APIs with Advanced Identity Cloud.
To help you quickly use and understand these REST APIs, Advanced Identity Cloud provides a Postman collection, containing example requests grouped into features.
Features include:
・Intelligent Access
・User Self-Service
・Session Management
・Identity Profiles
・Managed Identities
・Auditing/Monitoring
・OAuth 2.0 Flows
Download Postman and import the Advanced Identity Cloud collection
-
Download and install the Postman application.
-
Download the Advanced Identity Cloud Postman collection.
-
In Postman:
-
Go to File > Import... > Upload Files.
-
Browse to the collection JSON file you downloaded in the previous step, and then click Open.
-
Click Import to bring the collection into your workspace.
-
Create a service account and download its private key
To use the Advanced Identity Cloud Postman collection, you must create a service account that the requests in the collection can use to connect to your Advanced Identity Cloud instance.
Follow the steps in Create a new service account.
-
In step 9, save the private key as a local file called
key.jwk. -
Make a note of the ID for the service account you created.
An example of an ID is
449d7e27-7889-47af-a736-83b6bbf97ec5.
Proceed to the next section to learn how to enter these values into the collection, plus other settings necessary to use Postman with Advanced Identity Cloud.
Configure collection variables
The Advanced Identity Cloud Postman collection uses a number of configurable variables to populate the requests.
These variables are stored at the collection level. To view them, click on the top level of the collection menu labeled PingOne Advanced Identity Cloud Collection, and then select the Variables tab.
The variables are initially set with placeholder values that you must modify or replace. For example, the collection needs to know the Advanced Identity Cloud URL, as well as your admin access credentials.
To edit the variables, enter new values in the INITIAL VALUE column. Then click Save to make the edits permanent.
To understand which variables you need to edit before you can use the collection, learn more in Required variable values. To understand which variables you can optionally edit to customize the collection to suit your environment, learn more in Optional variable values.
You can then start using the collection.
|
You can also override the default collection-level variables by creating a Postman Environment. Use the same variable names as the Required variable values. This is useful if you have more than one Advanced Identity Cloud tenant, as you can configure the connection and username values as separate environments in Postman. You can also enter potentially sensitive values in an environment to keep them separate from the collection. This means you can share the collection without sharing your credentials. For information on creating a Postman Environment, learn more in Managing environments in the "Postman Learning Center". |
Required variable values
Before using the collection, you must provide the correct values for the following variables. You can provide the value at the collection level or add them at the environment level.
|
Ensure you use strong passwords for access credentials. |
Server URLs
platformUrl-
- Default
-
https://<tenant-env-fqdn> - Description
-
Specifies the root URL of your Advanced Identity Cloud.
amUrl-
- Default
-
https://<tenant-env-fqdn>/am - Description
-
Specifies the URL of the Access Management (AM) component of your Advanced Identity Cloud.
idmUrl-
- Default
-
https://<tenant-env-fqdn>/openidm - Description
-
Specifies the URL of the Identity Management (IDM) component of your Advanced Identity Cloud.
User credentials
postmanServiceAccountID-
- Default
-
Not set
- Description
-
Specifies the ID of the service account you created to allow the Postman collection access to your tenant.
The collection uses this ID when creating a JWT to sign, which it then uses to obtain an access token.
The JWT is generated when you run the Prerequisite requests.
- Example
-
c41515a8e-9c7d-4c37-4b2a-58c0fdea2080
postmanServiceAccountJWK-
- Default
-
Not set
- Description
-
Specifies the private key you downloaded as
key.jwkwhen you created the service account.Open the downloaded
key.jwkin a text editor, and then enter the entire JSON web key into the field in Postman, including the curly braces.The collection uses this key to sign a JWT token, which it then uses to obtain an access token.
The JWK is used to sign the JWT when you run the Prerequisite requests.
- Example
-
{ "d": "MsVF...dmvw", "dp": "0iic...jdrw", "dq": "BXja...4epQ", "e": "AQAB", "kty": "RSA", "n": "stO0...qNyU", "p": "3VoI-ZPcw", "q": "ztGg...EJBw", "qi": "NHkA...NV_Gw" }
postmanClientSecret-
- Default
-
Not set
- Description
-
Specifies the secret used by the OAuth 2.0 clients the collection creates.
You create these clients when you run the Prerequisite requests.
postmanDemoPassword-
- Default
-
Not set
- Description
-
Specifies the password used by the managed realm user the collection creates for demonstration purposes.
You create the realm user when you run the Prerequisite requests.
Logging API
logApiKey-
- Default
-
Not set
- Description
-
Specifies the API key used to access the monitoring endpoints.
Add this key to run the auditing and monitoring requests.
Learn more in Obtaining API Credentials.
- Example
-
0405de08ea73f1d84f
logApiSecret-
- Default
-
Not set
- Description
-
Specifies the API secret used to access the monitoring endpoints.
Add this key to run the auditing and monitoring requests.
Learn more in Obtaining API Credentials.
- Example
-
58932ad661ccf7ea5eda0b...a8d310e1676c9cac7f
Optional variable values
The collection uses the following additional variables that work using their default values; however, you can modify them.
List of optional variable values
postmanDemoUsername-
- Default
-
postmanDemoUser - Description
-
Specifies the username of the managed realm user the collection creates for demonstration purposes.
postmanDemoEmail-
- Default
-
demo.user@postman.example.com - Description
-
Specifies the email of the managed realm user the collection creates for demonstration purposes.
Enter an email address you have access to if you want to test the forgotten username or password flows in the user self-service section of the collection.
realm-
- Default
-
/realms/root/realms/alpha - Description
-
Specifies the realm that the majority of the requests in the collection use.
You must specify the entire hierarchy of the realm, starting at the root realm.
Prefix each realm in the hierarchy with the
realmskeyword. - Example
-
/realms/root/realms/customers/realms/europe.
cookieName-
- Default
-
Not set
- Description
-
Specifies the name of the session cookie the tenant uses to store session tokens.
The collection sets this value automatically when you run the first request in the Prerequisites folder.
loginJourney-
- Default
-
Login - Description
-
Specifies the authorization journey name to use.
For information on the default journeys that Advanced Identity Cloud provides, learn more in Login.
redirect_uri-
- Default
-
https://httpbin.org/anything - Description
-
Specifies the URI to which the OAuth 2.0 client will redirect the user upon a successful authentication request.
postmanConfidentialClientId-
- Default
-
postmanConfidentialClient - Description
-
Specifies the ID of the OAuth 2.0 private client.
postmanPublicClientId-
- Default
-
postmanPublicClient - Description
-
Specifies the ID of the OAuth 2.0 public client.
Hard-coded variable values
The collection uses the following additional variables that must not be modified.
List of hard-coded variable values
postmanUtilLib-
- Description
-
Contains the
postman-util-libutility library that the collection uses to sign requests and generate certain keys.Learn more in postman-util-lib on GitHub.
Use the collection
Before using the Advanced Identity Cloud Postman collection, you should run the Prerequisite requests. The requests configure your Advanced Identity Cloud with the necessary elements, such as OAuth 2.0 clients and managed users
Running the prerequisite requests
| Ensure you have configured the required collection variables as described in Configure collection variables before running the prerequisite requests. |
-
In Postman, with the Advanced Identity Cloud collection loaded, open the Prerequisites section.
-
Select the first request in the list, examine the details, and when you’re satisfied the request is properly formed, click Send.
Many of the requests have associated tests; for example, that the response code was
200. Postman displays the test results alongside the response to the request.Many of the requests set a global variable containing a value returned in the response for use in subsequent requests.
View the details of these in the Tests tab of a request. You can also view the values of these global variables by clicking Environment Quick Look ().
-
Repeat the previous step for each request in the Prerequisites folder.
When completed, Advanced Identity Cloud contains the following:
-
An alpha_user identity, named
postmanDemoUserby default, which demonstrates a number of user-related endpoints, such as identity profiles, and user self-service. -
Two OAuth 2.0 clients:
-
A client named
postmanConfidentialClient, which is used by the OAuth 2.0 requests to demonstrate a number of grant flows. -
A client named
postmanPublicClient, which is used by the OAuth 2.0 requests to demonstrate a number of grant flows.
-
If you need to recreate any of the above, or decide to alter the default values, run each of the steps in the Prerequisite folder again.
Running the requests
The requests in the collection are split into different features. To run the calls for a feature, open the relevant folder, and run each request in sequence.
The value in square brackets in the name shows what type of authentication the request requires:
[User]-
The request acts on a user’s data or profile.
These requests often authenticate as
postmanDemoUserin the collection. [fr:am:*]-
The request requires an access token that has the
fr:am:*scope so that it can perform access management related actions.These requests authenticate as the service account you created earlier.
[fr:idm:*]-
The request requires an access token that has the
fr:idm:*scope so that it can perform identity management related actions.These requests authenticate as the service account you created earlier.
Note that intelligent access and identity profiles have additional functionality. Refer to each section for details.
Intelligent access
There are scripts in the Intelligent Access requests that attempt to detect the callbacks that the first step returns, and sets the next request to handle it.
To view the details of this script:
-
Click on the top level of the collection menu (labelled PingOne Advanced Identity Cloud Collection), then select the Pre-request Scripts tab.
-
Within the tab, examine the
detectCallbacksscript.
When manually running through the steps, examine the response returned in the first call, and run the relevant next step. The collection is able to handle the following ready-to-use callbacks:
| Step | Callback |
|---|---|
Step 2a |
Username and password callbacks, together in a page node. |
Step 2b |
Validated create username and password callbacks, together in a page node. |
Step 2c |
Choice callbacks. |
Step 2d |
Text input callbacks. |
Step 2e |
Device profile callbacks. Learn more in Configure Device Profiling. |
Step 2f |
Progressive profile callbacks. |
Identity profiles
Some endpoints require the ID of an identity, rather than the username.
An example of this is when getting the OAuth 2.0 profiles a user has provided consent to.
When running the Identity Profiles requests, ensure you have also executed the request named Step 3: [User] Read session info and store ID in the Authenticate as "Postman Demo User" folder.
The result is stored in the demoUserId global variable.
Advanced Identity Cloud API reference
Many of the features available through Advanced Identity Cloud UIs are also available through REST APIs.
|
Some documented APIs aren’t active in all Advanced Identity Cloud tenants. The REST APIs have Evolving interface stability. This interface is continuing to evolve and so is subject to change in backwards-incompatible ways. All changes are documented at the time of release. |
API versions
To maintain compatibility between releases, many REST APIs are versioned (v1.0, v2.0, and so on).
The version number of a feature increases when Advanced Identity Cloud introduces breaking changes to an API.
Advanced Identity Cloud provides versions for these API aspects:
- resource
-
Any changes to the structure or syntax of a returned response result in a change to the resource version. For example, changing
errorMessagetomessagein a JSON response. - protocol
-
Any changes to the methods used to make REST API calls result in change to the protocol version. For example, changing
_actionto$actionin the required parameters of an API feature.
When an API is versioned, include resource versions in your REST calls
by setting the Accept-API-Version request header.
The following example requests resource version 2.0 and protocol version 1.0:
Accept-API-Version: resource=2.0, protocol=1.0
This header ensures you call the correct version of the API, avoiding unexpected behavior due to incompatible changes.
Advanced Identity Cloud REST API custom headers
Advanced Identity Cloud adds several custom headers to its REST API responses. These custom headers allow you to make logic decisions in your scripts and journeys. For example, you might use the country code in the X-Client-Region header to enforce MFA in a sign-on journey for clients originating from a specific country or set of countries.
Debugging
- X-ForgeRock-TransactionID
-
This header contains a unique value, such as
f89da9de-22f4-4e0b-8527-26b8d9c53d7b-request-1/0, that can be used to identify the current request and correlate it with Advanced Identity Cloud log entries from all log sources. Learn more in Filter logs for a specific request.
Advanced Identity Cloud adds a similar header X-Cloud-Trace-Context for tracing requests. This is used
internally by the Ping Identity support team. It’s also deprecated, so you shouldn’t use this header
in your integrations.
|
Client IP addresses
- X-Forwarded-For
-
This header contains a comma-separated list of originating IP addresses for the client.
-
If the request doesn’t have an
X-Forwarded-Forheader set before it connects to the tenant environment load balancer, the header is added to the request and contains the following IP addresses:X-Forwarded-For: <client-ip-address>, <load-balancer-ip-address>-
<client-ip-address>is the IP address of the client when it connects to the tenant environment load balancer. -
<load-balancer-ip-address>is the IP address of the tenant environment load balancer.
-
-
If the request already has an
X-Forwarded-Forheader set before it connects to the tenant environment load balancer, the header is modified to contain the following IP addresses:X-Forwarded-For: <existing-ip-address>, <client-ip-address>, <load-balancer-ip-address>-
<existing-ip-address>is the IP address theX-Forwarded-Forheader contains when the client connects to the tenant environment load balancer. -
<client-ip-address>is the IP address of the client when it connects to the tenant environment load balancer. -
<load-balancer-ip-address>is the IP address of the tenant environment load balancer.
-
There are security and privacy concerns associated with the use of this header. Learn more in the MDN doc X-Forwarded-For. -
- X-Trusted-Forwarded-For
-
This header contains a comma-separated list of trusted IP addresses for the client:
X-Trusted-Forwarded-For: <trusted-ip-address>, <client-ip-address>, <load-balancer-ip-address>-
<trusted-ip-address>is a trusted client IP address, verified by Ping Identity. -
<client-ip-address>is the IP address of the client when it connects to the tenant environment load balancer. -
<load-balancer-ip-address>is the IP address of the tenant environment load balancer.
-
- X-Real-IP
-
This header contains a trusted client IP address, verified by Ping Identity:
X-Real-IP: <trusted-ip-address>
For the X-Trusted-Forwarded-For and X-Real-IP headers, if the client is behind a reverse
proxy, the trusted client IP address contains the real IP address of the reverse proxy, not the client.
|
Learn more in Identify originating client IP addresses.
Client geolocation
- X-Client-Region
-
This header contains the country (or region) associated with the client’s IP address in the form of a two-letter region code, such as
USorFR. For most countries, these region codes correspond directly to ISO-3166-2 codes.
- X-Client-City
-
This header contains the name of the city where the client request originated. For example,
Mountain Viewfor Mountain View, California. There’s no canonical list of valid values for this header. The city names can contain ASCII letters, numbers, spaces, and the following characters:"!#$%&'*+-.^_`|~".
- X-Client-City-Lat-Long
-
This header contains the latitude and longitude of the city where the client request originated. For example,
37.386051,-122.083851for a request from Mountain View.
For the X-Client-Region, X-Client-City and X-Client-City-Lat-Long headers, if the
client is behind a reverse proxy, the geolocation information represents the reverse proxy, not
the client. If you require greater accuracy, Ping Identity recommends that you integrate an IP
lookup service into your end-user journeys.
|
Learn more in Identify client geolocation.
Other
- X-Forwarded-Proto
-
This header contains the HTTP protocol the client used to connect to the tenant environment load balancer. Possible values are
httporhttps. Learn more in the MDN doc X-Forwarded-Proto.
- X-Requested-With
-
This header contains the name of the originating web technology or platform. For example, most JavaScript frameworks set the value as
XMLHttpRequest. The header can be used to influence application behavior. For example, returning HTML data by default but returning JSON data for requests that set the value asXMLHttpRequest. The header can also be used to protect against CSRF attacks. Learn more in CSRF attacks.
Advanced Identity Cloud REST
Advanced Identity Cloud REST is a REST API framework defining common APIs to access web resources and collections of resources.
Resources
Endpoints generally return JSON-format resources, though resource formats can depend on the implementation.
Resources in collections can be found by their unique identifiers (IDs).
IDs are exposed in the resource URIs.
For example, if a service has a user collection under /users, you can access a user at /users/user-id.
The ID is also the value of the _id field of the resource.
Resources are versioned using revision numbers.
A revision is specified in the resource’s _rev field.
Revisions make it possible to figure out whether to apply changes
without resource locking and without distributed transactions.
Verbs
The Advanced Identity Cloud REST APIs use the following verbs, sometimes referred to collectively as CRUDPAQ. For details and HTTP-based examples of each, follow the links to the sections for each verb.
| Verb | Description |
|---|---|
Add a new resource with HTTP PUT or HTTP POST. |
|
Retrieve a single resource with HTTP GET. |
|
Replace an existing resource with HTTP PUT. |
|
Remove an existing resource with HTTP DELETE. |
|
Modify part of an existing resource with HTTP PATCH. |
|
Perform a predefined action with HTTP POST. |
|
Search a collection of resources with HTTP GET. |
Query parameters
Advanced Identity Cloud REST reserved query string parameter names start with an underscore (_).
Reserved query string parameters include, but are not limited to, the following names:
_action
_api
_countOnly
_crestapi
_fields
_mimeType
_pageSize
_pagedResultsCookie
_pagedResultsOffset
_prettyPrint
_queryExpression
_queryFilter
_queryId
_sortKeys
_totalPagedResultsPolicy
| Some parameter values are not safe for URLs; URL-encode parameter values as necessary. |
Extension points
The action verb is the main vehicle for extensions.
For example, to create a new user with HTTP POST rather than HTTP PUT, you might use /users?_action=create.
An endpoint can define additional actions.
For example, /tasks/1?_action=cancel.
A service can define stored queries to call by ID.
For example, /groups?_queryId=hasDeletedMembers.
Stored queries can call for additional parameters.
The parameters are also passed in the query string.
Which parameters are valid depends on the stored query.
Create
There are two ways to create a resource: HTTP POST or HTTP PUT.
To create a resource using POST,
perform an HTTP POST with the query string parameter _action=create and the JSON resource as a payload.
The service creates the identifier if not specified:
POST /users?_action=create HTTP/1.1
Host: example.com
Accept: application/json
Content-Length: ...
Content-Type: application/json
{ JSON resource }To create a resource using PUT, perform an HTTP PUT
with the case-sensitive identifier for the resource in the URL path and the JSON resource as a payload.
Optionally, include the If-None-Match: * header to prevent overwriting an existing object:
PUT /users/some-id HTTP/1.1
Host: example.com
Accept: application/json
Content-Length: ...
Content-Type: application/json
If-None-Match: *
{ JSON resource }The _id and the content of the resource depend on the endpoint.
The service is not required to use the _id the client provides.
The response to the create request indicates the resource location as the value of the Location header.
-
If you do include the
If-None-Match: *header, the request creates the object if it does not exist or fails if the object does exist. -
If you do not include the
If-None-Match: *header, the request creates the object if it does not exist or updates the object if it does exist. -
If you include the
If-None-Matchheader with any value other than*, the response is an HTTP 400 Bad Request error. For example, creating an object withIf-None-Match: revisionreturns a bad request error.
Parameters
You can use the following query string parameters:
| Parameter | Description |
|---|---|
|
Return only the specified fields in the body of the response. The If the |
|
Format the body of the response. |
Read
To retrieve a single resource, perform an HTTP GET on the resource by its case-sensitive identifier (_id)
and accept a JSON response:
GET /users/some-id HTTP/1.1
Host: example.com
Accept: application/jsonParameters
You can use the following query string parameters:
| Parameter | Description |
|---|---|
|
Return only the specified fields in the body of the response. The If the |
|
Some resources have fields containing multimedia resources, such as a profile photo. If the feature is enabled for the endpoint, read a single multimedia resource field by specifying the field and mime-type. The content type of the field value returned matches the mime-type. The body of the response is the multimedia resource Do not use the |
|
Format the body of the response. |
Update
To update a resource, perform an HTTP PUT
including the case-sensitive identifier (_id) as the final element of the path to the resource
and the JSON resource as the payload.
Use the If-Match: _rev header to verify the version you modify.
Use If-Match: * if the version does not matter.
PUT /users/some-id HTTP/1.1
Host: example.com
Accept: application/json
Content-Length: ...
Content-Type: application/json
If-Match: _rev
{ JSON resource }When updating a resource, include all the attributes to retain. Omitting an attribute in the resource amounts to deleting it unless it is not under the control of your application. Attributes not under the control of your application include private and read-only attributes. Virtual attributes and relationship references might not be under the control of your application.
| Parameter | Description |
|---|---|
|
Return only the specified fields in the body of the response. The If the |
|
Format the body of the response. |
Delete
To delete a single resource, perform an HTTP DELETE by its case-sensitive identifier (_id) and accept a JSON response:
DELETE /users/some-id HTTP/1.1
Host: example.com
Accept: application/jsonParameters
You can use the following query string parameters:
| Parameter | Description |
|---|---|
|
Return only the specified fields in the body of the response. The If the |
|
Format the body of the response. |
Patch
To patch a resource, send an HTTP PATCH request with an array of operation objects in the payload. Each operation object uses some combination of these fields:
operation-
The type of operation.
field-
The target field.
value-
The value to apply.
from-
The source field.
The service applies the PATCH operations in order.
PATCH /users/some-id HTTP/1.1
Host: example.com
Accept: application/json
Content-Length: ...
Content-Type: application/json
If-Match: _rev
{ JSON array of patch operations }PATCH operations work differently depending on the field types:
- Single-value
-
An object, string, boolean, or number.
- List semantics array
-
The elements are ordered, and duplicates are allowed.
- Set semantics array
-
The elements are not ordered, and duplicates are not allowed.
Whether an endpoint supports a specific operation depends on the implementation.
Add operation
The add operation ensures the target field contains the value provided, creating parent fields as necessary.
If the target field is single-valued, the value replaces the value of the target.
If the value is an array, the outcome depends on the type:
- List semantics arrays
-
If you
addan array of values, the operation appends the array to the existing list of values.If you
adda single value, specify an ordinal element in the target array, or use the{-}special index to add the value to the end of the list. - Set semantics arrays
-
The operation merges the value(s) in the patch with the existing set of values. Any duplicates in the array are removed.
As an example, start with the following list semantic array resource:
{
"fruits": ["orange", "apple"]
}The following add operation appends pineapple at the end of the array:
{
"operation": "add",
"field": "/fruits/-",
"value": "pineapple"
}The resulting resource is:
{
"fruits": ["orange", "apple", "pineapple"]
}Copy operation
The copy operation replaces the value(s) of the target field with the value(s) from the source field.
The following example replaces the value of another_mail with the value of mail:
[{
"operation": "copy",
"from": "mail",
"field": "another_mail"
}]If the source field value and the target field value are arrays, the result depends on whether the array has list semantics or set semantics. Learn more in Add operation.
Increment operation
The increment operation changes the value or values of the target field by the amount you specify.
The value must be a positive or negative number.
The target must be a single-valued number.
The following example adds 1000 to /user/payment:
[{
"operation": "increment",
"field": "/user/payment",
"value": "1000"
}]Move operation
The move operation removes existing values from the source and adds them to the target field.
The operation creates the target field if it does not exist.
The following example moves surname values to lastName:
[{
"operation": "move",
"from": "surname",
"field": "lastName"
}]To apply a move to an array, the source and target must have compatible semantics.
Learn more in Add operation.
Remove operation
The remove operation deletes values in the target field.
When no value is specified, the operation removes the field:
[{
"operation": "remove",
"field": "phoneNumber"
}]For arrays, the result depends on the semantics:
- List semantic arrays
-
Delete the specified element in the array.
The following example removes the first phone number (zero-based array index):
[{ "operation": "remove", "field": "/phoneNumber/0" }] - Set semantic arrays
-
Delete the specified values from the array.
The following example removes the specified phone number:
[{ "operation": "remove", "field": "/phoneNumber", "value": "+1 408 555 9999" }]
Replace operation
The replace operation removes existing values in the target, replacing them with the provided value(s).
The following example replaces existing telephoneNumber values with +1 408 555 9999:
[{
"operation": "replace",
"field": "/telephoneNumber",
"value": "+1 408 555 9999"
}]For list semantic arrays, you can target items by their indexes. As an example, start with the following resource:
{
"fruits": ["apple", "orange", "kiwi", "lime"]
}Apply the following operation:
[{
"operation": "replace",
"field": "/fruits/1",
"value": "pineapple"
}]The result is:
{
"fruits": ["apple", "pineapple", "kiwi", "lime"]
}Transform operation
The transform operation changes the field value based on a script or a data transformation command.
The following example applies the something.js script to the /objects value:
[{
"operation": "transform",
"field": "/objects",
"value": {
"script": {
"type": "text/javascript",
"file": "something.js"
}
}
}]Limitations
Some HTTP client libraries do not support the HTTP PATCH operation.
Make sure the library you use supports HTTP PATCH before using this REST operation.
For example, the Java method HttpURLConnection.setRequestMethod("PATCH") throws ProtocolException.
Parameters
You can use the following query string parameters:
| Parameter | Description |
|---|---|
|
Return only the specified fields in the body of the response. The If the |
|
Format the body of the response. |
Action
Actions are a means of extending Advanced Identity Cloud REST APIs and are defined by the resource provider. The actions you can use depend on the implementation.
The standard action indicated by _action=create is described in Create.
Parameters
You can use the following query string parameters. Other parameters depend on the specific action implementation:
| Parameter | Description |
|---|---|
|
Return only the specified fields in the body of the response. The If the |
|
Format the body of the response. |
Query
To query a resource collection, which you can think of as a resource container,
perform an HTTP GET and accept a JSON response including at least a _queryFilter or _queryId parameter.
These parameters cannot be used together.
GET /users?_queryFilter=true HTTP/1.1
Host: example.com
Accept: application/jsonThe endpoint returns the result as a JSON object including a results array
and other fields related to the query string parameters.
Parameters
You can use the following query string parameters:
| Parameter | Description |
|---|---|
|
Return only the specified fields in each element of the The If the |
|
The string is an opaque cookie to keep track of the position in the search results.
The service returns the cookie in the JSON response as the value of In the request Use this parameter with the The |
|
When The |
|
Return query results in pages of this size. After the initial request, use |
|
Format the body of the response. |
|
Query filters request entries matching the filter expression. You must URL-escape the filter expression. Learn more in Filter expressions. |
|
Specify a query by its identifier. Specific queries can take their own query string parameter arguments depending on the implementation. |
|
Sort the resources returned based on the specified field(s) in As ascending order is the default, including the The |
|
When a non-zero The
If no count policy is specified in the query, or if |
Filter expressions
Query filters request entries matching the filter expression. You must URL-escape the filter expression.
The string representation is summarized as follows:
Expr = OrExpr
OrExpr = AndExpr ( 'or' AndExpr ) *
AndExpr = NotExpr ( 'and' NotExpr ) *
NotExpr = '!' PrimaryExpr | PrimaryExpr
PrimaryExpr = '(' Expr ')' | ComparisonExpr | PresenceExpr | LiteralExpr
ComparisonExpr = Pointer OpName JsonValue
PresenceExpr = Pointer 'pr'
LiteralExpr = 'true' | 'false'
Pointer = JSON pointer
OpName = 'eq' | # equal to
'co' | # contains
'sw' | # starts with
'lt' | # less than
'le' | # less than or equal to
'gt' | # greater than
'ge' | # greater than or equal to
STRING # extended operator
JsonValue = NUMBER | BOOLEAN | '"' UTF8STRING '"'
STRING = ASCII string not containing white-space
UTF8STRING = UTF-8 string possibly containing white-spaceJsonValue components of filter expressions follow
RFC 7159: The JavaScript Object Notation (JSON) Data Interchange Format.
In particular, as described in section 7 of the RFC, the escape character in strings is the backslash character.
For example, to match the identifier test\, use _id eq 'test\\'.
In the JSON resource, the \ is escaped the same way: "_id":"test\\".
When using a query filter in a URL, notice the filter expression is part of a query string parameter.
URL-encoded the filter expression.
Learn more in
RFC 3986: Uniform Resource Identifier (URI): Generic Syntax.
For example, whitespace, double quotes ("), parentheses, and exclamation characters need URL encoding.
The following rules apply to URL query components:
query = *( pchar / "/" / "?" )
pchar = unreserved / pct-encoded / sub-delims / ":" / "@"
unreserved = ALPHA / DIGIT / "-" / "." / "_" / "~"
pct-encoded = "%" HEXDIG HEXDIG
sub-delims = "!" / "$" / "&" / "'" / "(" / ")"
/ "*" / "+" / "," / ";" / "="ALPHA, DIGIT, and HEXDIG are core rules of
RFC 5234: Augmented BNF for Syntax Specifications:
ALPHA = %x41-5A / %x61-7A ; A-Z / a-z
DIGIT = %x30-39 ; 0-9
HEXDIG = DIGIT / "A" / "B" / "C" / "D" / "E" / "F"As a result, a backslash escape character in a JsonValue component
is percent-encoded in the URL query string parameter as %5C.
To encode the query filter expression _id eq 'test\\', use _id+eq'test%5C%5C'+, for example.
A simple filter expression can represent a comparison, presence, or a literal value.
For comparison expressions use json-pointer comparator json-value, where the comparator is one of the following:
eq (equals)
co (contains)
sw (starts with)
lt (less than)
le (less than or equal to)
gt (greater than)
ge (greater than or equal to)
For presence, use json-pointer pr to match resources where:
-
The JSON pointer is present.
-
The value it points to is not
null.
Literal values include true (match anything) and false (match nothing).
Complex expressions employ and, or, and ! (not), with parentheses, (expression), to group expressions.
HTTP status codes
When working with a Advanced Identity Cloud REST API, client applications should expect at least the following HTTP status codes. Not all services necessarily return all status codes identified here:
- 200 OK
-
The request succeeded and a resource returned, depending on the request.
- 201 Created
-
The request succeeded and the resource was created.
- 204 No Content
-
The action request succeeded, and there was no content to return.
- 304 Not Modified
-
The read request included an
If-None-Matchheader, and the value of the header matched the revision value of the resource. - 400 Bad Request
-
The request was malformed.
- 401 Unauthorized
-
The request requires user authentication.
- 403 Forbidden
-
Access was forbidden during an operation on a resource.
- 404 Not Found
-
The specified resource could not be found, perhaps because it does not exist.
- 405 Method Not Allowed
-
The HTTP method is not allowed for the requested resource.
- 406 Not Acceptable
-
The request contains parameters that are not acceptable, such as a resource or protocol version that is not available.
- 409 Conflict
-
The request would have resulted in a conflict with the current state of the resource.
- 410 Gone
-
The requested resource is no longer available, and will not become available again. This can happen when resources expire.
- 412 Precondition Failed
-
The resource’s current version does not match the version provided.
- 415 Unsupported Media Type
-
The request is in a format not supported by the requested resource for the requested method.
- 428 Precondition Required
-
The resource requires a version, but no version was supplied in the request.
- 500 Internal Server Error
-
The service encountered an unexpected condition that prevented it from fulfilling the request.
- 501 Not Implemented
-
The resource does not support the functionality required to fulfill the request.
- 503 Service Unavailable
-
The requested resource was temporarily unavailable. The service may be disabled, for example.
Certification campaigns
In Identity Governance, certifying access means reviewing the data and access a user has, such as access to applications, the accounts in those applications, and more.
Steps to certify access
To certify access for users, you must:
-
Create templates: Allows you to configure the data you want to certify.
-
Run campaigns: After you create a template and are ready to kick off the review process, create a campaign.
-
Certify data and access by end users: After you start a campaign, the template-defined end users (certifiers) receive notifications to review the data. The certifiers' review of the data is referred to as an access review.
Certifications tab
Certifications and related features can be found by selecting Certification from the left navigation bar in the Advanced Identity Cloud admin console.
Three tabs display under Certification:
Overview tab
To access the Overview tab, from the Advanced Identity Cloud admin console, go to Certification > Overview.
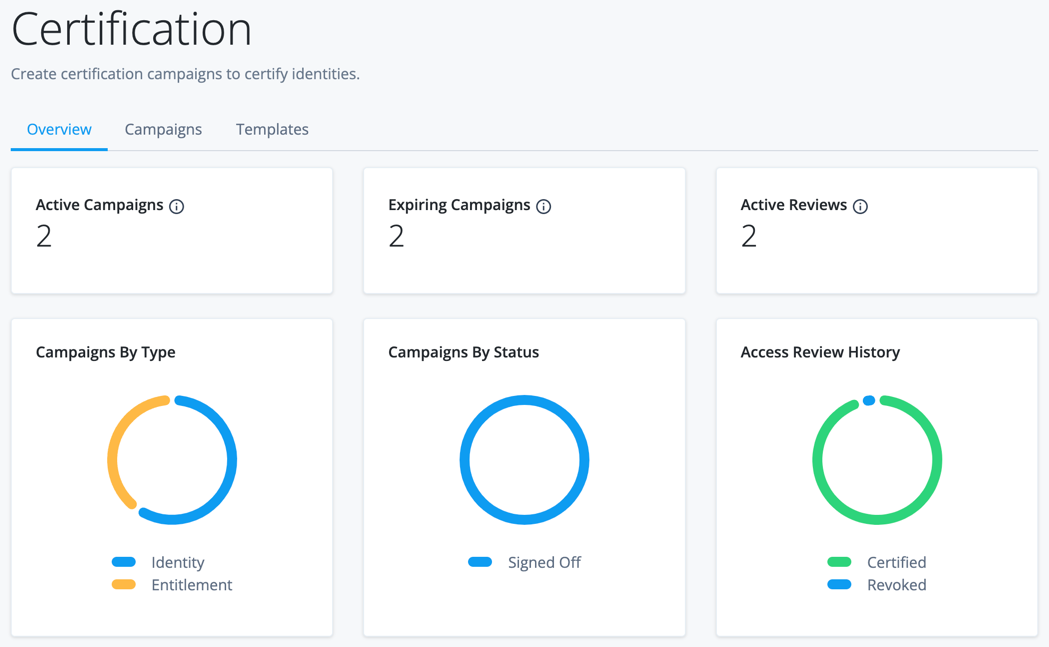
The Overview landing page displays various metrics that allow you to view items such as campaign status, active reviews, and campaigns by type.
You can hover your cursor over the charts to view the data details.
| Data Element | Description |
|---|---|
Active Campaigns |
The number of campaigns currently in progress. |
Expiring Campaigns |
The number of campaigns that expire in the next 2 weeks. |
Active Reviews |
The total amount of line items in access reviews that are in progress. A line item is a record for a certifier to review. For example, the user Barbara Jensen’s record that details their access to a particular application is a line item. |
Campaigns By Type |
A breakdown of the varying types of certifications. |
Campaigns By Status |
A breakdown of certifications by status. |
access review History |
The number of line items certified versus revoked from campaigns. |
Example of certifying access
As an example of certifying access, an end user wants to know what applications a specific user, Barbara Jenson, has access to. The end user could want to do this for several reasons, such as increasing the company’s security landscape by ensuring end users have accurate, appropriate access, or to comply with organizational, industry, or governmental policies. Barbara Jensen has an account and access to an application, called App A.
With Identity Governance, perform the following actions to achieve this:
-
Configure and assign end users (certifiers) in your company to review Barbara’s access to App A using templates.
-
Kick off the data review using campaigns. Campaigns are the active processes, where certifiers review the data. In this case, it is Barbara’s data. Certifiers are assigned to review the data in a campaign.
-
Certifiers review Barbara’s data and either certify (allow) or revoke (remove) the access to App A.
Configure data to review using templates
Templates are the first step in certifying access for users.
Templates are the underlying configurations of certifying access and define the data to review, who is responsible for the review, and when the data needs to be reviewed (on a periodic or ad hoc basis).
Often, organizations need to review the same data multiple times a year to ensure access is accurate. Templates make the certification process easier by saving the configuration settings used in the data review process.
Manage (create, duplicate, edit, or delete) templates on the Templates tab and schedule each campaign to run at a specific interval (if desired).
You can run templates on an ad-hoc or scheduled basis.
View saved templates
To view saved templates, from the Advanced Identity Cloud admin console, click Certification > Templates tab. The page displays saved templates.
| Field | Description |
|---|---|
Name |
The name of the template. |
Next run date |
A date displays when the template is configured to run according to a schedule. If the template runs ad-hoc, then (None Scheduled) displays. |
Status |
A template can be in one of the following states:
The general sequence of states are Creating → Unused → Active. |
Which certification template to choose
Identity Governance provides various certification templates to choose from. The underlying business objective you want to achieve determines which template type you choose.
The following scenarios show which template type to choose:
-
You want to review the template to certify or revoke access to applications (accounts). You can specify to review the entitlements or roles a user has. The primary certifier (reviewer) of the certification should be users' managers.
Identity Entitlement assignment Role membership Entitlement composition Notes Not every user has entitlements. If you want to review the applications users have access to, and include those users who don’t have entitlements, choose the identity certification.
-
You want to review to certify or revoke specific entitlements assigned to users in target applications. The primary certifier of the certification should be entitlement owners.
Identity Entitlement assignment Role membership Entitlement composition Notes The entitlement assignment certification is the best choice in this scenario. It provides entitlement owners the ability to review the access users have to their entitlements.
-
You want to review the template to certify or revoke a user’s role memberships. The primary certifier of the certification should be role owners.
Identity Entitlement assignment Role membership Entitlement composition Notes The role membership certification is the best choice in this scenario as it provides the ability to review roles and users who are assigned to roles in Advanced Identity Cloud.
-
You want to review the template to evaluate, review, and modify the definition of entitlements within the certification process.
Identity Entitlement assignment Role membership Entitlement composition Notes The entitlement composition certification is the best choice in this scenario because it enables reviewers to submit requests to change the entitlement definition, even independently of the certification decision, with options for drafting and deferring modification requests until sign off.
Create templates
Before you create a template, consider creating custom governance glossary attributes to enhance the data for onboarded target applications, entitlements, or roles. This will assist with template filtering and business decisions.
To create a template:
-
Navigate to the Certification > Templates tab.
-
Click New Template.
-
Select the template type:
-
Identity certification: Review and certify user accounts, entitlements, and access a user has on some or all applications. Primary reviewers are the users' managers, a single user, or users assigned to a role. Entitlements are the specific permissions given to an account in an target application. Each entitlement correlates to a permission.
-
Entitlement assignment certification: Review and certify entitlements and the users who have access to entitlements in target applications. Primary reviewers are entitlement owners, a single user, or users assigned to a role.
-
Role membership certification: Review and certify role memberships and the users who have access to roles in Advanced Identity Cloud. Primary reviewers are role owners, a single user, or users assigned to a role.
-
Entitlement composition certification: Review and certify technical details and glossary metadata of entitlements. Primary certifiers are user, role, entitlement owner, custom certifier.
-
-
Click Next.
To continue setting up the template you select, click on the preceding links in step 3.
Modify templates
You can modify various template items:
-
From the Advanced Identity Cloud admin console, go to Certification > Template tab.
-
Locate the template and click the ellipsis () to perform various actions:
To view additional templates, click the caret icons at the bottom of the table. Field Description Duplicate
Duplicate the template details to create a new template, and edit or modify as needed. The characters (copy) are appended to the newly duplicated template.
View Details
This option displays if the template has been run at least once. It provides a read-only view into the configurations on the template. After you run a template, you can’t change the configuration settings.
Edit Template
This option displays if you create the template, but never run it to create a campaign. In this case, you can edit or modify the template configuration.
Activate templates
Activate a template to kick off the review process (a campaign).
You can activate a template by:
-
Creating a schedule when you define the template.
-
Adding a schedule to the template after you define the template.
-
Running the template on an ad-hoc basis.
To activate a template:
-
From the Advanced Identity Cloud admin console, go to Certification > Template tab.
-
Locate the template and click to perform various actions:
To view additional templates, click the caret icons at the bottom of the table. Action Field Run Now
This activates the template and kicks off the review process (campaign). When selected, the active campaign displays in the Campaigns tab.
When you create a template, if you select Run on a schedule under the When to Certify section. The campaign runs on the set schedule and display on the Campaigns tab at the specified interval. Schedule Campaign
This option displays if you didn’t configure a schedule when creating the template. This creates a run schedule for the template.
Edit Schedule
This option displays if you did configure a schedule when creating the template, but you would like to modify the existing schedule.
Delete a template
|
You can only delete Unused certification templates through the UI. This deletion can’t be undone. A template becomes active after you use it to create a campaign. It remains active even if there are no campaigns attached to it. You can’t modify or delete an active template through the UI. If you must delete an active template, you can use the REST API. Learn more in REST API: delete certification template. |
To delete a template:
-
From the Advanced Identity Cloud admin console, go to Certification > Template tab.
-
Locate the template, check that the template is in an Unused state.
-
Click , and then click Delete. You can’t undo the deletion.
Identity certification
Select an identity certification type to certify user accounts and entitlements for specific applications.
Learn more in Create templates.
|
You must populate the Display Name Attribute on the target application User entity object in the Details tab. This allows each account pulled into Advanced Identity Cloud to display with a human-readable name. This is required for the data to properly display when a certifier (reviewer) reviewers their certification. Perform the following:
The following video shows an example: |
The following table lists the areas to configure for each campaign template type:
| Section | Description |
|---|---|
General details of the template, such as the name, description, and a default certifier. |
|
The items to be certified. |
|
The cadence in which the review process is kicks off (campaign). |
|
The end users responsible for certifying the items in the campaign. |
|
(Optional) Set up email notifications based on various events that take place during the certification process. |
|
(Optional) Various configurations to allow during the campaign, such as bulk actions on line items or self-certification. |
|
Summary of configured sections. |
Details
This section includes basic information about the template, such as the display name, description, owner, and staging process.
To complete this section, do the following:
-
From the Advanced Identity Cloud admin console, click Certification > Templates > + New Template.
-
Select Identity Certification.
-
Click Next.
-
Complete the following fields:
Field Description Name
The display name for the campaign. This campaign name displays on both the certifications tab and the end-user tasks dashboard.
You can define a date variable in the name of the campaign to know which campaign kicks off. Identity Governance uses moment.js to format the date.
For example, if you have a campaign scheduled to run every two weeks, appending the date to the name lets you know which campaign you are working on. The campaign name can include the date (year, month, day), time (hour, minute), and time of day (AM/PM):
Campaign name: {{YYYY-MM-DD-hh:mma}}When you kick off the template into a campaign, an example of the name is:
Campaign name — 2023-12-12-08:18pmAfter the campaign kicks off you can’t modify the name. Description
Enter a general description for the campaign. Your company should follow a descriptive convention to describe each of your campaign.
This field is limited to 1000 characters. Campaign Owner
Enter the owner of the campaign. Only campaign owners can fully control their campaigns, including certification decisions, certifier assignment changes, sign off, and more.
Enable Campaign Staging
Enable staging to set up the campaign in the system but not activate it in production. This option allows compliance officers to preview a campaign before it’s activated and exposed to end users. Compliance officers can inspect and review the content, decision items, and other details to determine whether to activate or delete it.
-
Click Next.
What to Certify
This sections lets you define the items to certify, including the organizations, users, applications, accounts, and entitlements.
To complete this section, do the following:
-
Complete the following fields:
Field Description Organizations
Filter any generated certification by organization. This feature only appears for identity certification campaigns.
-
All organizations
Include child organization
Click to include any suborganizations in the campaign.
Users
Certify one of the following:
-
All users
-
A single user
-
Users matching a filter: Create a filter to certify select users.
Accounts, Entitlements, Roles
Select at least one of the following:
-
Certify User Accounts.
-
Certify User Entitlements.
-
Certify User Roles.
Applications
Certify one of the following:
-
All applications
-
Specific applications: If you select this, an additional box displays to select which Applications to certify.
-
Applications matching a specific filter: Create a filter to certify specific applications.
If you create a governance glossary attribute and enhance the target application(s) with the attribute, you can filter on attribute(s) you create. Learn more in Create an application glossary attribute.
Accounts
Displays if you selected
Certify User Accounts.-
Select All accounts in selected applications if you selected Certify User Accounts.
Entitlements
Displays if you selected
Certify User Accounts.-
Certify one of the following if you selected Certify User Entitlements:
-
All entitlements
-
Entitlements matching a filter: Create a filter to certify specific entitlements.
If you create a governance glossary attribute and populate the attribute you create on the onboarded entitlement(s), you can filter on the attribute(s) you create. Learn more in Create an entitlement glossary attribute.
Roles
Displays if you selected
Certify User Roles.Certify one of the following if you selected Certify User Roles:
-
All roles
-
Roles matching a filter: Create a filter to certify specific roles.
If you create a governance glossary attribute and populate the attribute you create on roles, you can filter on the attribute(s) you create. Learn more in Create a role glossary attribute.
Exclude access granted only from a role
Enabled by default.
Excludes account and entitlement line items that are granted only through a role.
Identity Governance can’t certify or revoke an application or entitlement from an end user when they’re granted access through a role; therefore, excluding these line items can help reduce unnecessary information in the certification. Learn more in Decisions change based on how you grant access.
Exclude dynamically granted role memberships
Displays if you selected
Certify User Roles.Enabled by default if you are creating a role membership certification.
Exclude role line items that are granted to an end user through a condition.
Identity Governance can’t certify or revoke an end user being a member of a role through a condition; therefore, excluding these line items can help reduce unnecessary information in the certification. Learn more in Decisions change based on how you grant access.
(Optional) Show advanced filters
To certify accounts based on properties from the last certification decision made on a line item from the drop-down, select Filter by last certification decision.
A line item is a particular record for a certifier to review. For example, the user Barbara Jensen’s record that details their access to a particular application is a line item.
-
-
Click Next.
When to Certify
The When to Certify section lets the administrator specify when to kick off the review process (campaign) and what to do in the event the campaign expires.
To complete this section, do the following:
-
Complete the following fields:
Field Description Schedule
Define whether the template will kick off on a periodic basis. If selected, input various choices to define the schedule.
Check the Run on a schedule box to define a schedule for the template.
Options include:
-
Run Every: Run the certification every specified number of days, weeks, months, or years.
-
Start: Specify a date and start time when this campaign kicks off for the first time.
-
End: Run the certification on its defined periodic basis until this date and time is reached.
Campaign Duration
Specify the amount of time each access review (campaign) has before expiration. You can specify the duration in days, weeks, months, or years.
When Campaign Expires
Select a behavior to handle the open access review (campaign) line items when the campaign expires:
-
Close open items: Complete the items using the given information after the campaign expires. The administrator can select what decision to add to the item (certify, revoke, and allow exception to) and when that decision takes effect. The decision can take effect immediately or after a duration (in days).
-
Reassign to: Select a given user or role that the access review (campaign) is reassigned to after the expiration date. The campaign will not be closed.
-
Do Nothing: No action will be taken, and the line items will remain in progress.
-
-
Click Next.
Who will Certify
This section allows you to specify the users that review and make decisions about the items you defined in the What to Certify section.
To complete this section, do the following:
-
Complete the following fields:
Field Description Certifier Type
Specify who can review and certify user access by selecting one of the following:
-
User: Select a single user to review and make a decision on every record. When you select this, a Select user box displays. Select the user who will certify the campaign.
-
Role: Select a role that allows any of its members to review every record. When you select this, a Select a role box displays. Select a role from the list of the created roles in Advanced Identity Cloud.
-
Manager: The user’s manager becomes the certifier of their data (also known as a line item).
-
Organization Admin: Select an administrator for an organization who can certify their data.
Enable default certifiers
Select a certifier to assign in case an access review (campaign) line item isn’t assigned a certifier. For example, if the manager is the certifier and the user has no manager defined, then the default certifier will be assigned the access review for this user.
-
-
Click Next.
Notifications
This optional section allows you to send email notifications when one or more campaign events are triggered. For example, when a campaign is about to expire or when a certifier is reassigned.
To complete this section, do the following:
-
Define an email template for each selected notification. Each notification requires an associated email template. From the left navigation pane in the Advanced Identity Cloud admin console, go to Email > Templates. Learn more in Email templates.
There are preset email templates created for certification templates. Use these as a base, copy the email template, and customize them to suit your needs. To reference variables in your email templates for Identity Governance, the object is nested an additional level. The following table shows how to access these objects:
Item Usage User attributes
Use the syntax
object.user.userAttribute.Use the attributes available from the email template screen. Learn more in Email templates.
Manager attributes
Use the syntax
object.manager.managerAttribute.Use the attributes available from the email template screen. Learn more in Email templates.
If the manager is the certifier type in the Who will Certify section, use the same user attributes in the managerAttribute. For example, if you need to reference a user’s manager within the email, then use this object.Campaign attributes
Use the syntax
object.campaign.campaignAttribute.Available attributes are
nameandtype. -
Select any of the notification types:
Field Description Send initial notification
Send a notification any time a certifier is assigned to a line item.
Send reassign notification
Send to a new certifier when a line item in an access review (campaign) is reassigned or forwarded to them.
Send expiration notification
Send a reminder notification to the certifiers before a campaign expires. Select the number of days, before the campaign expires, to send the reminder.
To illustrate the expiration notification mechanism:
If the notification is set for three days prior to expiration, reviewers will receive an email when the campaign is three days away from the expiration date. If the deadline is extended by a week, the expiration date of the notification will be recalculated and sent three days before the new deadline, regardless of any previously sent notifications.
Send reminders
Send a notification to remind certifiers to take action on access review (campaign) line items. Select the number of days, weeks, months, or years to send the reminder.
Enable escalation
Send an escalation notification to specific recipients that certifiers have not completed their actions on a campaign. When selected, an additional Escalation Owner box displays. Select the number of days, weeks, months, or years and the user to send the escalation to.
-
Click Next.
Additional options
This optional section allows you to configure other options for a campaign, such as performing bulk certifications or reassigning tasks to another user or group.
To complete this section, do the following:
-
Complete the following optional fields:
Field Description Enable line item reassignment and delegation
Allow the certifier to reassign or forward a line item to another user.
When you select this box, you can choose the following options:
-
Forward - Allow certifiers to forward their access review (campaign) to another certifier. When forwarding an access review, other certifiers are removed from the access review in its entirety. Learn more in forward line items.
-
Reassign - Select the privileges the current certifier can assign to the new certifier:
-
Add Comment
-
Make Decision
-
Reassign/Forward
-
Sign off
Learn more in reassign line items.
-
Require justification on revoke
Require a mandatory comment or reason for the revocation.
Require justification on exception
Require a mandatory comment or reason for any allowed exception.
Allow exceptions
Allow certifiers to continue to certify line items assigned to them after the campaign expires. Select a duration in days, months, weeks, or years.
Allow bulk-decisions
Allow certifiers to make line item decisions in bulk.
This includes:
-
Making a decision (certify, revoke, exception).
-
If Enable line item reassignment and delegation is enabled, then you can bulk Reassign or Forward line items.
As an administrator, most access reviews require an in-depth look on each line item. This is to ensure accuracy of each item. Bulk-decisions allow for a certifier to make a decision on many items at once, which could lead to inaccurate data. Use caution when selecting this option. Allow partial sign-off
Allow a certifier to sign-off on an access review before their assigned line items have a decision made on them.
Process remediation
Revokes the end user’s access in the target application when a certifier revokes (denies) the line item. Select a workflow to run either immediately after revocation of access or after a duration.
To ensure end-user access is removed when revoking a line item, you must enable this property. -
-
Click Next.
Customization
This optional section allows you to configure the default table columns for the reviewers.
To complete this section, do the following:
-
Complete the following optional fields:
Field Description Application
Select a value for
application, such asDescriptionandName.Entitlement
Select a value for
entitlement, such asDescriptionandDisplay Name.Review
Enter
FlagsandCommentsto add fields to the access review table. -
Click Next.
Summary
The Summary section is the final section in creating a template. It gives a breakdown of each section in the template, allowing for a review.
Summary steps:
-
Review each section.
-
Click Save to complete the certification template.
Under the What to Certify review section, ensure that the Total Decision Items is greater than 0. If you identify that this is 0, this means that the template did not identify items to be certified. Therefore, if you create the campaign off of the template, the system will immediately cancel the campaign. If you identify this to be 0, go back to the What to Certify section and adjust your settings.
Entitlement assignment certification
Select an entitlement assignment certification type to certify the entitlements users have in specific applications.
Certifiers review each end user’s accounts and entitlements in every onboarded target application by reviewing line items. A line item is a record for a certifier to review. For example, the end user Barbara Jensen’s record in the certification table displays the entitlement details they have in a particular application.
If the entitlement line item has the decision of revoke, then the entitlement the end user has
in the application is removed when the certification is signed-off.
Learn more in Create templates.
|
You must populate the Display Name Attribute on the target application User entity object in the Details tab. This allows each account pulled into Advanced Identity Cloud to display with a human-readable name. This is required for the data to properly display when a certifier (reviewer) reviewers their certification. Perform the following:
The following video shows an example: |
The following table lists the areas to configure for each campaign template type:
| Section | Description |
|---|---|
General details of the template, such as the name, description, and a default certifier. |
|
The items to be certified. |
|
The cadence in which the review process is kicks off (campaign). |
|
The end users responsible for certifying the items in the campaign. |
|
(Optional) Set up email notifications based on various events that take place during the certification process. |
|
(Optional) Various configurations to allow during the campaign, such as bulk actions on line items or self-certification. |
|
Summary of configured sections. |
Details
This section includes basic information about the template, such as the display name, description, owner, and staging process.
To complete this section, do the following:
-
From the Advanced Identity Cloud admin console, click Certification > Templates > + New Template.
-
Select Entitlement Assignment Certification.
-
Click Next.
-
Complete the following fields:
Field Description Certification Name
The display name for the certification. This certification name displays on both the certifications tab and the end-user tasks dashboard.
Define a date variable in the name of the certification to know which campaign kicks off. Identity Governance uses moment.js to format the date.
For example, if you have a certification that’s scheduled to run every 2 weeks, appending the date to the name lets you know which campaign you are working on.
For example, the certification name can include the date (year, month, day), time (hour, minute), and time of day (AM/PM):
Campaign name: {{YYYY-MM-DD-hh:mma}}When you kick off a template into a campaign, an example of the name is:
Campaign name — 2023-12-12-08:18pmAfter the campaign kicks off you can’t modify the name. Description
Enter a general description for the certification. Your company should follow a descriptive convention to describe each of your certifications.
This field is limited to 1000 characters. Certification Owner
Enter the owner of the certification. Only certification owners can fully control their certifications, including certification decisions, certifier assignment changes, sign off, and more.
Enable Campaign Staging
Enable certification staging to set up the certification in the system but not activate it in production. This option allows compliance officers to preview a certification before it’s activated and exposed to end users. Compliance officers can inspect and review the content, decision items, and other details to determine whether to activate or delete it.
-
Click Next.
What to Certify
This section lets you define the items to certify, including the users, applications, accounts, and entitlements.
To complete this section, do the following:
-
Complete the following fields:
Field Description Entitlements
Certify one of the following:
-
All entitlements
-
Entitlements matching a filter: Create a filter to certify specific entitlements.
If you create a governance glossary attribute and enhance the onboarded entitlement(s) with the attribute, you can filter on the attribute(s) you create.
Learn more in the Manage governance glossary.
Applications
Certify one of the following:
-
All applications
-
Specific applications: If you select this, an additional box is displayed to select which Applications to certify.
-
Applications matching a specific filter: Create a filter to certify specific applications.
If you create a governance glossary attribute and enhance the target application(s) with the attribute, you can filter on the attribute(s) you create. Learn more in Manage governance glossary.
Users
Certify one of the following:
-
All users
-
A single user
-
Users matching a filter: Create a filter to certify select users.
Exclude access granted only from a role
Enabled by default.
Excludes entitlement line items that are granted only through a role.
Identity Governance can’t certify or revoke an entitlement from an end user when they’re granted access through a role; therefore, excluding these line items can help reduce unnecessary information in the certification. Learn more in Decisions change based on how you grant access.
(Optional) Show advanced filters
To certify accounts based on properties from the last certification decision made on a line item from the drop-down, select Filter by last certification decision.
A line item is a particular record for a certifier to review. For example, the user Barbara Jensen’s record that details their access to a particular application is a line item.
-
-
Click Next.
When to Certify
The When to Certify section lets the administrator specify when to kick off the review process (campaign) and what to do in the event the campaign expires.
To complete this section, do the following:
-
Complete the following fields:
Field Description Schedule
Define whether the template will kick off on a periodic basis. If selected, input various choices to define the schedule.
Check the Run on a schedule box to define a schedule for the template.
Options include:
-
Run Every: Run the certification every specified number of days, weeks, months, or years.
-
Start: Specify a date and start time when this campaign kicks off for the first time.
-
End: Run the certification on its defined periodic basis until this date and time is reached.
Campaign Duration
Specify the amount of time each access review (campaign) has before expiration. You can specify the duration in days, weeks, months, or years.
When Campaign Expires
Select a behavior to handle the open access review (campaign) line items when the campaign expires:
-
Close open items: Complete the items using the given information after the campaign expires. The administrator can select what decision to add to the item (certify, revoke, and allow exception to) and when that decision takes effect. The decision can take effect immediately or after a duration (in days).
-
Reassign to: Select a given user or role that the access review (campaign) is reassigned to after the expiration date. The campaign will not be closed.
-
Do Nothing: No action will be taken, and the line items will remain in progress.
-
-
Click Next.
Who will Certify
This section allows you to specify the users that review and make decisions about the items you defined in the What to Certify section.
To complete this section, do the following:
-
Complete the following fields:
Field Description Certifier Type
Specify who can review and certify user access by selecting one of the following:
-
User: Select a single user to review and make a decision on every record. When you select this, a Select user box displays. Select the user who will certify the campaign.
-
Role: Select a role that allows any of its members to review every record. When you select this, a Select a role box displays. Select a role from the list of the created roles in Advanced Identity Cloud.
-
Entitlement Owner: Select the user who manages the entitlement.
Enable default certifiers
Select a certifier to assign in case an access review (campaign) line item isn’t assigned a certifier. For example, if the manager is the certifier and the user has no manager defined, then the default certifier will be assigned the access review for this user.
-
-
Click Next.
Notifications
This optional section allows you to send email notifications when one or more campaign events are triggered. For example, when a campaign is about to expire or when a certifier is reassigned.
To complete this section, do the following:
-
Define an email template for each selected notification. Each notification requires an associated email template. From the left navigation pane in the Advanced Identity Cloud admin console, go to Email > Templates. Learn more in Email templates.
There are preset email templates created for certification templates. Use these as a base, copy the email template, and customize them to suit your needs. To reference variables in your email templates for Identity Governance, the object is nested an additional level. The following table shows how to access these objects:
Item Usage User attributes
Use the syntax
object.user.userAttribute.Use the attributes available from the email template screen. Learn more in Email templates.
Manager attributes
Use the syntax
object.manager.managerAttribute.Use the attributes available from the email template screen. Learn more in Email templates.
If the manager is the certifier type in the Who will Certify section, use the same user attributes in the managerAttribute. For example, if you need to reference a user’s manager within the email, then use this object.Campaign attributes
Use the syntax
object.campaign.campaignAttribute.Available attributes are
nameandtype. -
Select any of the notification types:
Field Description Send initial notification
Send a notification any time a certifier is assigned to a line item.
Send reassign notification
Send to a new certifier when a line item in an access review (campaign) is reassigned or forwarded to them.
Send expiration notification
Send a reminder notification to the certifiers before a campaign expires. Select the number of days, before the campaign expires, to send the reminder.
To illustrate the expiration notification mechanism:
If the notification is set for three days prior to expiration, reviewers will receive an email when the campaign is three days away from the expiration date. If the deadline is extended by a week, the expiration date of the notification will be recalculated and sent three days before the new deadline, regardless of any previously sent notifications.
Send reminders
Send a notification to remind certifiers to take action on access review (campaign) line items. Select the number of days, weeks, months, or years to send the reminder.
Enable escalation
Send an escalation notification to specific recipients that certifiers have not completed their actions on a campaign. When selected, an additional Escalation Owner box displays. Select the number of days, weeks, months, or years and the user to send the escalation to.
-
Click Next.
Additional options
This optional section allows you to configure other options for a campaign, such as performing bulk certifications or reassigning tasks to another user or group.
To complete this section, do the following:
-
Complete the following optional fields:
Field Description Enable line item reassignment and delegation
Allow the certifier to reassign or forward a line item to another user.
When you select this box, you can choose the following options:
-
Forward - Allow certifiers to forward their access review (campaign) to another certifier. When forwarding an access review, other certifiers are removed from the access review in its entirety. Learn more in forward line items.
-
Reassign - Select the privileges the current certifier can assign to the new certifier:
-
Add Comment
-
Make Decision
-
Reassign/Forward
-
Sign off
Learn more in reassign line items.
-
Require justification on revoke
Require a mandatory comment or reason for the revocation.
Require justification on exception
Require a mandatory comment or reason for any allowed exception.
Allow exceptions
Allow certifiers to continue to certify line items assigned to them after the campaign expires. Select a duration in days, months, weeks, or years.
Allow bulk-decisions
Allow certifiers to make line item decisions in bulk.
This includes:
-
Making a decision (certify, revoke, exception).
-
If Enable line item reassignment and delegation is enabled, then you can bulk Reassign or Forward line items.
As an administrator, most access reviews require an in-depth look on each line item. This is to ensure accuracy of each item. Bulk-decisions allow for a certifier to make a decision on many items at once, which could lead to inaccurate data. Use caution when selecting this option. Allow partial sign-off
Allow a certifier to sign-off on an access review before their assigned line items have a decision made on them.
Process remediation
Revokes the end user’s access in the target application when a certifier revokes (denies) the line item. Select a workflow to run either immediately after revocation of access or after a duration.
To ensure end-user access is removed when revoking a line item, you must enable this property. -
-
Click Next.
Customization
This optional section allows you to configure the default table columns for the reviewers.
To complete this section, do the following:
-
Complete the following optional fields:
Field Description Application
Select a value for
application, such asDescriptionandName.Entitlement
Select a value for
entitlement, such asDescriptionandDisplay Name.Review
Enter
FlagsandCommentsto add fields to the access review table. -
Click Next.
Summary
The Summary section is the final section in creating a template. It gives a breakdown of each section in the template, allowing for a review.
Summary steps:
-
Review each section.
-
Click Save to complete the certification template.
Under the What to Certify review section, ensure that the Total Decision Items is greater than 0. If you identify that this is 0, this means that the template did not identify items to be certified. Therefore, if you create the campaign off of the template, the system will immediately cancel the campaign. If you identify this to be 0, go back to the What to Certify section and adjust your settings.
Kick off data review process using campaigns
Campaigns are the second step in certifying access for users.
Once you create a template, and you are ready to start the review process, create a campaign.
After you start a campaign, the end users (certifiers), that are defined in the template, are notified to start reviewing the data. The process of certifiers reviewing data is called an access review.
When you kick off a campaign, through the ad-hoc (one-time) run under the Templates tab or through the schedule set in the template, the Certification tab displays the certification.
The following video shows an example:
To access campaigns, from the Advanced Identity Cloud admin console, click Certification > Campaigns tab.
View campaigns
The landing page/modal on the Campaigns tab displays Active campaigns.
To view campaigns that have a specific status, such as Closed or Canceled, click the Status drop-down and filter the status.
| To view additional campaigns, click the caret icons at the bottom of the table. |
Campaign statuses to filter
| Status | Description |
|---|---|
Active |
The campaign is in progress. In the Status column, this includes the In-progress, Expiring and Overdue states.
|
Expired |
The campaign expired. Advanced Identity Cloud triggers this status when you select When to Certify > When certification expires > Close open items > immediately in the template. |
Cancelled |
This campaign was canceled manually and is no longer in progress. In certain situations when there is an error creating the campaign from the template, a campaign might automatically go into this state. |
Completed |
The campaign finished as expected with no issues. |
Staged |
The campaign is staged and isn’t active. Learn more in the details section of creating a template. |
Campaign landing page columns
The campaigns listed on the landing page of the Campaigns tab consists of a table with various columns.
| Field | Description | ||
|---|---|---|---|
Name |
The name of the campaign. This name is generated from the template. |
||
Deadline |
The campaign completion date. |
||
Status |
The state the campaign is in. Learn more in Campaign statuses to filter. |
||
Progress |
The percent complete of the campaign.
|
| To filter a column, click the up/down icon (where applicable). |
Update deadline of campaign
The deadline (expiration) of a campaign can be updated after a campaign is ran.
To update the deadline:
-
From the Advanced Identity Cloud admin console, click Certifications.
-
Select the Campaigns tab.
-
Click next to the campaign to update the deadline.
-
Enter a new date.
-
Click Save.
View details of a campaign
From the Campaigns tab on the landing page, click the desired campaign to view more details.
The data the page displays depends on the certification type in the template.
The selected campaign includes two tabs:
Details tab
The Details tab includes graphical information about the campaign. For example, the percentage of completeness or the reviews currently in progress.
The information is broken out into various cards. The following table shows the various information by card.
Campaign details page
| Card/Title | Description |
|---|---|
Status |
Provides information about when the campaign expires. You can select Cancel Campaign to cancel the campaign. If the campaign status is Staged, you can select Activate to kick-off the campaign. |
Campaign Details |
Shows the percentage of the campaign complete, including the number of reviews completed versus the total amount of reviews, as well as general information about the campaign:
|
Users |
Pie chart. The number of new users versus previously certified users in the campaign. |
Decisions Breakdown |
Pie chart. A breakdown of the decisions made in the campaign by certifiers (certified, revoked, exception). |
Access by Application |
Pie chart. The number of accounts by application to be certified in the campaign. |
Users with no email address |
Numerical. The number of users that don’t have an email address on their profile. |
Certifiers with no email address |
Numerical. The number of certifiers (reviewers) that don’t have an email address on their profile. |
Access reviews tab
The Access Reviews tab contains information on the certifiers in the campaign. The certifiers could be an individual or a role. This includes the progress they have made on their reviews, as well as the ability to view the items each certifier is responsible for.
By default, the page displays the certifiers who are reviewing the access review, which is in the Active state.
To view other statuses, select the Status drop-down:
| Status | Description |
|---|---|
Active |
The certifier has line items on the campaign that don’t have a decision made on them. A line item is a record for a certifier to review. For example, the user Barbara Jensen’s record that details their access to a particular application is a line item. |
Expired |
The campaign has passed its deadline and the certifier has line items that don’t have a decision made on them. |
Completed |
The certifier has reviewed and made decisions on the line items assigned to them in their access review and signed off. |
You can use the search icon to search for a specific campaign by its name.
There are three columns in the Access Reviews tab:
-
Certifier: The individual or users assigned to a role responsible for a part of the campaign.
-
Status: The status of the campaign.
-
Progress: The progress the certifier has made in their reviews.
To view the percentage and number of items that are complete, hover over the progress icon.
Click the arrow icon on Certifier to filter alphabetically (ascending or descending).
To view additional features, such as forwarding a certifier’s items to another person or end users assigned to a role, click to the right of the table.
| To gain a detailed view of the items left for a certifier, click on their record in the table. The drilled-down view is the same view a certifier utilizes when completing their items for the campaign. Learn more in Run access reviews. |
Cancel existing campaign
You can only cancel a campaign that’s in the Active state (which includes the states Expiring and Overdue). Learn more in Campaign statuses to filter.
There are two ways to cancel a campaign:
-
When viewing campaigns from the Certifications > Campaigns landing page:
-
Click next to the campaign.
-
Click Cancel.
-
Click Cancel Campaign.
-
-
In the drill-down campaign view:
-
Click into a campaign.
-
Click Cancel Campaign.
-
Click Cancel Campaign again in the confirmation screen.
-
Run access reviews
Access reviews are the final step of certifying access for users.
After you kick off the data review process in a campaign, the data defined for review is sent to the end users you define in the template.
Certifying is the process of an end user reviewing the data assigned to them and making a decision on if access should be kept (certified) or removed (revoked) for each record. The data assigned to them is called an access review.
Notes on access reviews:
-
An access review consists of one or more line items or records to review and certify.
-
An end user who has an access review is considered a reviewer of the certification, also called a certifier.
-
Multiple certifiers can be assigned to review the same data.
-
When an end user is designated as a reviewer from a campaign, it displays under Inbox > Access Reviews or in the Dashboard landing page.
-
You define the certifiers when you create a template and kick off a campaign. A reviewer can also be added through forwarding or reassignment by certifiers and administrators.
-
Certifiers can change the decision a previous certifier made for a line item; however, changes can’t be made to a campaign after a decision is set and the campaign is signed off (completed). Additional changes require remediation through another campaign.
For example, if one certifier decides to certify the access for a line item, but another certifier decides to revoke access for it after, then the last certifier’s decision is the decision that prevails. Learn more in Access reviews.
Quick links
As there are various features that become enabled or disabled for end user access reviews depending on the configurations in the template, the following is a table to quick links in this page.
Details
| Item | Description |
|---|---|
A landing screen that shows access reviews that are assigned to an end user. This includes an explanation of the access review landing page columns. |
|
The screen where end users complete the access review of the line items for a campaign. A line item is a record for a certifier to review. For example, the user Barbara Jensen’s record that details their access to a particular application is a line item. This includes:
|
|
Filter campaign items that display data in different ways. |
|
Rearrange or hide the table columns. |
|
Provide a comment on a line item in the access review. Use cases include:
|
|
Make a decision to either certify access, revoke access, or provide an exception to access for a specified duration (you must enable the configurations in the template). |
|
View other reviewers assigned to a line item in the access review. |
|
An end user can reassign an item that’s assigned to them and define the permissions of the new assignee. There are two ways to reassign a line item: |
|
Remove prior reviewers and assign the line item to another individual(s). Full permissions on the item are given to the forwarded individual(s). There are two ways to forward a line item: |
|
Perform a bulk line item certification. Not recommended for every campaign as this will bypass much needed manual oversight on each item. |
View access review tasks
To view the access review tasks, from the Advanced Identity Cloud end-user UI, click Inbox > Access Reviews.
The landing screen on Access Reviews is a view of the active campaigns that have a task assigned to an end user.
To view campaigns that have a specific status, such as Closed or Canceled, click the Status drop-down and filter the status.
| To view additional tasks, click the caret icons at the bottom of the table. |
Campaign statuses to filter
| Status | Description |
|---|---|
Active |
The campaign is in progress. In the Status column, this includes the In-progress, Expiring and Overdue states.
|
Expired |
The campaign expired. Advanced Identity Cloud triggers this status when and end user selects When to Certify > When certification expires > Close open items > immediately in the template. |
Completed |
The campaign finished as expected with no issues. |
Access reviews landing page columns
The campaigns listed on the landing page of the Access Reviews tab consists of a table with various columns.
| Field | Description | ||
|---|---|---|---|
Name |
The name of the campaign. This name is generated from the template. |
||
Deadline |
The date in which the campaign must be completed. |
||
Status |
The state the campaign is in. Learn more in Campaign statuses to filter. |
||
Progress |
The percent complete of the campaign.
|
| To filter a column, click the up/down icon. |
To view additional features, such as forwarding a certifier’s items to another person or end users assigned to a role, click to the right of the table.
View individual access review line items
For an end user to review the line items they need to certify, click an access review (campaign).
The top section of the screen shows information about the access review including:
-
The Status metric shows the percentage of items to complete, as well as a numeric value of items that are complete versus the total amount of items.
-
The Decisions pie chart is shows the number of records certified versus revoked.
-
The Deadline is the campaign completion date. Click the View campaign details to view additional information such as the description of the campaign and the campaign owner.
Access review task columns
The columns in the line items table are:
| Field | Description |
|---|---|
User |
The user in Advanced Identity Cloud. |
Application |
The onboarded application the user has access to. |
Account |
The account in the application that correlates to a user in Advanced Identity Cloud. |
Entitlement |
The entitlement in the application the user has granted. |
Flags |
Information about how access was given. One or more of these flags can display on a line item:
|
Comment |
Comments that have been made on a record in a campaign. A number above the comment icon indicates the amount of comments left. |
Decision |
The action taken on a record in a certification. Options are:
|
|
To view information about a line item, click on the item under the column. For example, to review a user’s information in Advanced Identity Cloud for an identity certification type, click the user’s name and a modal window pops up displaying the information for review. The same is true for each single item in a row. The following video shows an example: |
| To view additional line items in the access review, click the caret icon at the bottom of the table. |
High-level reviewer steps
The following are typical steps when an end user certifies line items in an access review (campaign):
-
Click into a record and review information by clicking into each item in the row.
-
Add a comment if necessary (or mandatory if the campaign requires it).
-
Make a decision by selecting Certify access, Revoke access, or Allow an exception. The last reviewer on the item to make a decision is the decision that will prevail for the item.
-
Repeat steps 1 - 3 for each line item in the table.
-
Once an end user certifies every record, click Sign-off. Once this takes place, no changes can be made to the campaign as it acts as the final decision on a certification.
If Allow partial sign-off is enabled in the Additional Options section of the campaign template, then the line items don’t have to be completed before the task can be signed off. A gradual fashion can be used whereas a subset of the items can be signed off and the other items can be completed at a later date. Learn more in additional options. The following video shows an example:
Subsequent sections display various functions of the certifier process in detail.
Filter and group items
End users can filter and group items to make them more manageable when certifying.
The following video shows an example:
Filter items
Certifiers can manipulate the data presented on an access review.
To filter the items, click on the filter icon in the top right of the line items table. Once selected, there are two ways to filter:
-
By decision: Filter the table by the decision made on a line item, either Certified, Revoked, Exception Allowed, or No Decision.
-
By item attributes: Filter the table by a particular column item, such as a user. Click the item to filter on, then enter the appropriate value in the additional box that’s displayed.
Group items
Grouping items aggregates duplicate information.
For example, if a user has four entitlements, the campaign items table displays this as four separate records. In grouping by fields, the entitlements display as a sub-table under a record, reducing the redundancy of reviewing the same record’s information.
To group the items, click the Group By icon above the Filter icon.
When end users select an object to group by, for example, Account, the view of the table changes splitting the screen in half.
Customize table columns
An end user can modify the columns presented in the line items table.
For example, they may want to display additional user properties.
To customize columns:
-
Click the view column icon ().
-
Under Available Columns, click each section and select or deselect the columns to display.
-
Under Active Columns, rearrange the order of the columns by clicking the drag icon () and dragging each column to the desired order.
To delete an Active Column, click the delete icon (). -
Click Apply.
Add comment
Certifiers can leave a comment in an access review.
The comment could vary in nature due to a number of reasons:
-
A justification for the decision being made.
-
A comment about why the item is being reassigned.
-
A comment about why the item is being forwarded.
-
A comment from another certifier if there are multiple certifier on the line item(s).
| An auto-generated comment is created when an item is forwarded or reassigned. |
To add a comment:
-
To get to the comment box either:
-
Click the comment icon box.
-
Click next the item to comment on and click the Add Comment.
-
-
Enter the comment.
-
Click Add Comment.
| After a comment has been made and added to a line item, it can’t be removed. |
Make a decision (certify)
A decision is an action a certifier makes on a line item in an access review.

A certifier can do one of the following:
-
To Certify (keep) access, click the green checkmark icon.
-
To Revoke (deny) access, click the circle-backslash icon. After selecting this, a mandatory comment box displays to the certifier in which they must enter a reason for revoking the line item.
When the campaign is signed off, if the Process remediation configuration option is enabled in the Additional Options section of the template, then the line item will be removed from the onboarded application.
-
The clock icon is disabled unless you explicitly enable exceptions by marking Allow Exceptions (under Additional Options) as allowed.
You can also specify the duration for exceptions under Additional Options. Learn more in additional options.
A certifier can only make a decision once per line item, no matter the number of certifiers. The decision made by the last certifier on a line item is the decision that prevails. After an access review (campaign) is signed off, a decision can’t be modified.
Decisions change based on how you grant access
Depending on the certification type and how an end user is given access to a resource, the decisions a certifier can take on a line item changes:
| How you grant access | Cert type | Notes | ||
|---|---|---|---|---|
To an application or entitlement using a role. |
Identity |
Identity Governance can’t certify or revoke the line item if you assign an end user to an application or entitlement using a role. To remove the user from the application or entitlement, remove them from the role.
|
||
In the What to Certify
section of the template, you select to certify |
Identity |
Identity Governance can’t certify or revoke an end user being a member of a role through a condition. To remove the end user from the role, update them to no longer meet the condition. |
||
To an entitlement using a role. |
Entitlement |
Identity Governance can’t certify or revoke the line item if you assign an end user to an entitlement using a role. To remove an end user from an entitlement, when they’re granted access through a role, remove them from the role. |
||
Through a role with a condition. |
Role membership |
Identity Governance can’t certify or revoke an end user being a member of a role through a condition. To remove the end user from the role, update them to no longer meet the condition. |
For each situation, the following UI elements change:
-
The Revoke and Allow an Exception decisions are disabled.
-
The Certify text changes to Acknowledge.
-
The line item can’t be used with bulk certify.
View other certifiers
For each line item in the access review, certifiers have the ability to view the other certifiers. To view the certifiers, click next to the item and click View Reviewers.
From here an end user has the ability to:
Reassign an item
End users reassign a line item by adding another certifier to review the item. When a certifier adds another certifier, they specify the privileges of the certifier.
| To reassign an item, you must enable the configuration setting Enable line item reassignment > Reassign in the Additional Options section of the template. Learn more in additional options. |
There are two ways to reassign an item:
Reassign from view reviewers screen
-
On the item, click > View Reviewers.
-
Click Add a Reviewer.
-
Select to add either Add a user or Add a role to the line item.
-
Search for the individual or role and select it.
-
Select the privileges that the new end user or role will have on the line item. The privileges you can add are:
-
View: Allows another end user to view the line item.
-
Comment: Allows another end user to leave a comment on the line item.
-
Decide: Allows another end user to make a decision on the line item.
-
Assign/Forward: Allows another end user to reassign or forward the line item.
-
Sign off: Allows another end user to sign-off on the line item.
-
-
Click Reassign.
Reassign from bulk reassign
| The option for bulk certify and reassign must first be enabled in the Additional Options section of the template before bulk reassign can be utilized. Learn more in Bulk certify items. |
-
After selecting more than one item, click the Actions drop-down that shows and select Reassign.
-
In the modal, choose to reassign to Another user or to Users with assigned role to the line item.
-
Search for the individual or role and select it.
-
Select the privileges that the user or role will have on the line item. The privileges you can add are:
-
Click Reassign.
Forward an item
When end users forward a line item in an access review, the end user removes prior certifiers and assigns the line item to another end user or role. The new certifier(s) have full permissions on the line item.
There are two ways to forward an item:
Individual forwarding
-
On the line item, click > Forward.
-
In the modal, choose to forward the line item to Another user or to Users with assigned role.
-
Search for the individual or role.
-
End users leave a comment as to why they’re forwarding the line item.
-
Click Forward Item.
Bulk forwarding
-
Select more than one item using the checkbox next to the items in the left of the certification items table or check the Select All box.
-
Click the Actions list that’s displayed.
-
Select Forward.
-
A modal window is displayed.
-
Select if the line items should be forwarded to Another user or Users with assigned role.
-
Search for the individual or role.
-
End users leave a comment as to why they’re forwarding the line items.
-
Click Forward Item.
Bulk certify items
The bulk certification of line items allow for many items to undergo the certification process at once instead of one-by-one. This configuration setting isn’t enabled by default and should be used with caution. Most access reviews require an in-depth look into the accuracy of data and bulk certification circumvents this.
| To bulk certify line items, you must enable the configuration setting Allow Bulk Decisions in the Additional Options section of the template. Learn more in additional options. |
When end users select one or more items using the checkboxes, or they select All items (in the drop-down button of Select), an additional Actions drop-down button displays. End users click this button to view actions they can make in a bulk fashion.
| Under the Select drop-down button, end users can choose to select All items that under review, All on this page, or Deselect all items. |
The items that display under the Actions button vary depending on if the configuration settings that your administrator enables in the template, but can include:
-
Certify
-
Revoke
-
Allow an exception
-
Reassign
-
Forward
Access requests
In Identity Governance, end users can request access to resources, such as target applications, entitlements, or roles.
You define the resources end users can request by adding them to the access catalog.
An organization works with access requests as follows:
-
An Identity Governance administrator who can configure access requests. This includes defining which resources (applications, entitlements, and roles) end users can request in the access catalog.
-
After an administrator defines requestable resources in the access catalog, end users submit requests to gain or remove (managers only) access to resources using the hosted account pages.
-
Approvers approve or deny access requests: End users configured as the approver (designated owner) to review and approve or reject the request. The items that are displayed to the approver are known as request items.
Manage workflows
When you configure access requests, you can implement workflows, an end-to-end sequence of Identity Governance actions that result in either approving or rejecting an access request. You can configure workflows using the Advanced Identity Cloud’s workflow editor or REST APIs.
Workflows give complete flexibility over all access request types by allowing you to define custom workflow definitions. For example, when an end user requests access to an application, you can specify the actions Identity Governance takes for the access request to be approved or rejected.
These actions could include:
-
Requiring more than one approval for the request. You could require an end user’s manager and the application owner to approve the request before Identity Governance provisions access to the end user.
-
If the access request is rejected, send an email to the end user stating their access request has been denied.
|
The out-of-the-box Identity Governance workflows do not currently support the approval of
custom request types, like event-based requests.
In this case, you can use workflows with custom scripted nodes that can
handle event-based situations, such as |
Access request types
Identity Governance provides six out-of-the-box workflows for each access request type.
The following table displays the different access request types and out-of-the-box workflows:
| Access request type | Workflow name | Description |
|---|---|---|
Grant Application |
|
Request access to an application. |
Remove Application |
|
Request to remove access to an application for an end user. |
Grant Entitlement |
|
Request access to an entitlement (additional privilege inside an application). |
Remove Entitlement |
|
Request to remove access to an entitlement from an end user. |
Grant Role |
|
Request access to an Advanced Identity Cloud provisioning role. |
Remove Role |
|
Request to remove access to a role from an end user. |
Create workflows using the workflow editor
To manage workflows, from the Advanced Identity Cloud admin console, go to Workflows.
There is a default published workflow for each access request type.
Workflow editor canvas
When you click a workflow, a blank workflow canvas appears with workflow nodes in the left pane, which you can drag-and-drop onto the canvas.
View workflow in JSON
For technical users, Identity Governance provides the ability to view and download workflows using JSON. From the workflow editor canvas, toggle JSON. If you want to export the workflow JSON, click ellipsis (), and then Export. You can make adjustments and re-import the JSON into Identity Governance.
|
If you are exporting an out-of-box workflow, Identity Governance pulls the UUID of the users or roles from the environment and uses it in the JSON file. Make sure to reset or update the approver values in the Approver node in the JSON. |
Workflow nodes
When you define a workflow, you specify each task through a node.
Identity Governance provides several nodes that allow you to customize your workflow.
For information on how to place nodes in a workflow, learn more in workflow editor canvas.To use an If/else node or Switch node, you must set outcomes in the script.
| For a comprehensive example of using the following nodes, learn more in Workflow use cases. |
Approval node
Requires a user’s input in the workflow. Define:
-
User(s) to approve the access request
-
What to do when the request expires. The end user defines the expiration when they create the access request.
-
Notifications to send.
Outcomes
-
Approved -
Reject
Evaluation continues along the Approved outcome path
if any of the defined approvers approve the request.
Evaluation continues along the Reject outcome path if any of the defined
approvers reject the request.
Properties
| Property | Usage | ||
|---|---|---|---|
Approvers |
Select user(s) that must approve the access request.
|
||
Form |
Select dynamic forms or choose a specific form to present to the reviewer.
|
||
Expiration Settings |
The end user defines the expiration when they create the access request. Select one of the following:
|
||
Notification Settings |
Select which email notifications to send. By default all notifications are enabled. Select any of the following:
|
Email node
You can add an email node to your Identity Governance workflow that sends an email using a notification template.
Properties
| Property | Usage |
|---|---|
Name |
Add a display name for the email node. |
Notification Template |
Select a notification template for the email. To view an email template on the Identity Cloud analytics dashboard, go to Email > Templates.
|
Message substitution |
Pass message variables into your email node template. You can use the Message substitution field to pass in a variable:
|
Fulfillment node
The Fulfillment node assigns a fulfillment task to users, requiring them to
manually complete of a governance task. In this case, an authorized user reviews
the task details and marks it as complete. Workflows using the fulfillment node
should also include flows to suspend the process while waiting for a response.
Administrators can use the Fulfillment node in chain tasks or used in conjunction with the Switch node to implement serial or parallel flows.
The Fulfillment node enables the complete orchestration of end-to-end lifecycles and event-driven flows.
Properties
| Property | Usage | ||
|---|---|---|---|
Reviewers |
Select user(s) that must approve the access request.
|
||
Form |
Allow dynamic form selection or choose a specific form to present to the reviewer.
|
||
Expiration Settings |
The end user defines the expiration when they create the access request. Select one of the following:
|
||
Notification Settings |
Select which email notifications to send. By default all notifications are enabled. Select any of the following:
|
If/else node
| To use this node, there must be a preceding Script node that sets at least one outcome. |
Also referred to as an exclusive gateway, this node has the
outcomes validationSuccess and ValidationFailure.
After a condition evaluates to true, the node stops evaluating and takes that
outcome.
Outcomes
-
validationSuccess -
validationFailure
Evaluation continues along the validationSuccess outcome path when
the defined condition is met.
Evaluation continues along the validationFailure outcome path when
the defined condition is met.
Properties
| Property | Usage |
|---|---|
Outcomes |
Specify which outcome (defined in a preceding Script node) meets the condition. Set the following properties:
|
Script node
Write custom logic in a workflow with the Script node.
The logic you write depends on the task you are trying to achieve.
For example, you can write a script to set parameters to deny an access request, or you can write a script that sets outcomes you can use in conjunction with an If/else node or Switch node.
Outcomes
Single outcome path. However, you will often set outcomes in the script that you will use with the If/else node or Switch node.
Properties
| Property | Usage |
|---|---|
Script |
Define your custom logic by writing a JavaScript script.
|
Accessing access request-related data in scripts
When an access request is created, the relevant data is stored in a request object. The data accessible through the script node varies depending on the type of access request. For example, an application grant workflow contains information about the application whereas a role grant workflow contains information about the role.
Potential scenarios
|
The following scenarios reference the request object. To view all properties available in the request object, use the REST API endpoint Identity Governance attributes can be referenced using PingIDM functions,
such as reading a resource using |
For an application grant request, grab the application ID and name submitted in the request:
var content = execution.getVariables(); 1
var requestId = content.get('id');
var app = null;
var applicationName = null;
var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); 2
applicationId = requestObj.application.id;
app = openidm.read("managed/alpha_application/" + applicationId); 3
applicationName = app.name; 4-
1 To leverage the workflow process variables from when the request was created, grab the variables and put them into the
contentvariable. For an access request, the only variable passed is theid. -
2 Obtain information about the access request using a
/governanceendpoint. -
3 Using the
openidm.readfunction, grab all data associated to the application and store it in a local variable,app. -
4 Grab the application name.
For an application grant request, grab the value of the custom created glossary attribute, riskLevel:
var content = execution.getVariables(); 1
var requestId = content.get('id');
var appId = null;
var appGlossary = null;
var riskLevel = null;
var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); 2
appId = requestObj.application.id;
appGlossary = openidm.action('iga/governance/application/' + appId + '/glossary', 'GET', {}, {}); 3
riskLevel = appGlossary.riskLevel; 4-
1 To leverage the workflow process variables from when the request was created, grab the variables and put them into the
contentvariable. For an access request, the only variable passed is theid. -
2 Obtain information about the access request using a
/governance/requestsendpoint. -
3 Using the application
idgrabbed from theiga/governance/requestsendpoint, obtain information about the glossasry attributes for the application using theiga/governance/applicationendpoint. -
4 Grab the glossary attribute,
riskLevel, and store it in a local variable,riskLevel. The glossary nameriskLevelcomes from the name that you define when you create a glossary attribute.
For an application grant, access the requester user properties. In this scenario, access the frIndexedString1 property which correlates to a user’s line of business (LOB):
var content = execution.getVariables(); 1
var requestId = content.get('id');
var user = null;
var lineOfBusiness = null;
var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); 2
user = openidm.read("managed/alpha_user/" + requestObj.user.id); 3
lineOfBusiness = user.frIndexedString1; 4-
1 To leverage the workflow process variables from when the request was created, grab the variables and put them into the
contentvariable. For an access request, the only variable passed is theid. -
2 Obtain information about the access request using a
iga/governance/requestsendpoint. -
3 Using the
openidm.readfunction, put the user;s data into therequestervariable. -
4 Grab line of business the user is in, which is stored in the property
frIndexedString1.
For an entitlement grant request, grab the entitlement ID and name submitted in the request:
var content = execution.getVariables(); 1
var requestId = content.get('id');
var requestObj = null;
var entitlementName = null;
var entitlementId = null;
requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); 2
entitlementName = requestObj.descriptor.idx./entitlement.displayName; 3
entitlementId = requestObj.assignment.id; 4-
1 To leverage the workflow process variables from when the request was created, grab the variables and put them into the
contentvariable. For an access request, the only variable passed is theid. -
2 Obtain information about the access request using a
iga/governance/requestsendpoint. -
3 Grab the entitlement name from
requestObj. Theentitlement.displayNameis derived from the display name attribute on the application’s entitlement object. -
4 Grab the entitlement
idfrom therequestObj.The assignment.idis unique whereas theentitlement.idisn’t. The entitlement object is raw data from the application. Applications with the sameentitlement.idcan cause collisions if you referenceentitlement.idin your scripts. Therefore, make sure to reference theassignment.idwhen you want to reference an entitlement.
For a role grant request, grab the role ID and name submitted in the request:
var content = execution.getVariables(); 1
var requestId = content.get('id');
var requestObj = null;
var roleId = null;
var role = null;
var roleName = null;
requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); 2
roleId = requestObj.role.id;
role = openidm.read("managed/alpha_role/" + roleId); 3
roleName = role.name; 4-
1 To leverage the workflow process variables from when the request was created, grab the variables and put them into the
contentvariable. For an access request, the only variable passed is theid. -
2 Obtain information about the access request using a
iga/governance/requestsendpoint. -
3 Using the
openidm.readfunction, grab all data associated to the role and store it in a local variable,role. -
4 Grab the role name.
Switch node
| You must precede this node with a Script node that sets two or more outcomes. |
The Switch node (also referred to as an inclusive gateway) lets you script two or more conditional outcomes. Any or all conditions can be true.
The Switch node and If/else node both evaluate conditions. However, the Switch node continues evaluating conditions after one condition is met.
Properties
| Property | Usage | ||
|---|---|---|---|
Name |
The name of the node.
|
||
Outcomes |
Specify the outcome paths based on the output of the preceding Script node.
|
Require multiple approvals in parallel
You can use a switch node to evaluate multiple paths instead of nesting multiple If/else nodes. However, you can also use a Switch node to send multiple approval paths in parallel. For example, you can send an approval to the role owner of a role and to an end user’s manager at the same time. Only when both approvals are approved can the workflow proceed.
To achieve this:
-
There must be a proceeding Script node before the Switch node.
-
A switch node must set two or more outcomes with their respective scripts set to
true. -
Each outcome of the Switch node routes to an Approval node.
-
The
Approveoutcome of each Approval node must route to an additional Switch node. -
The additional Switch node must only have one outcome with the script set to
true.
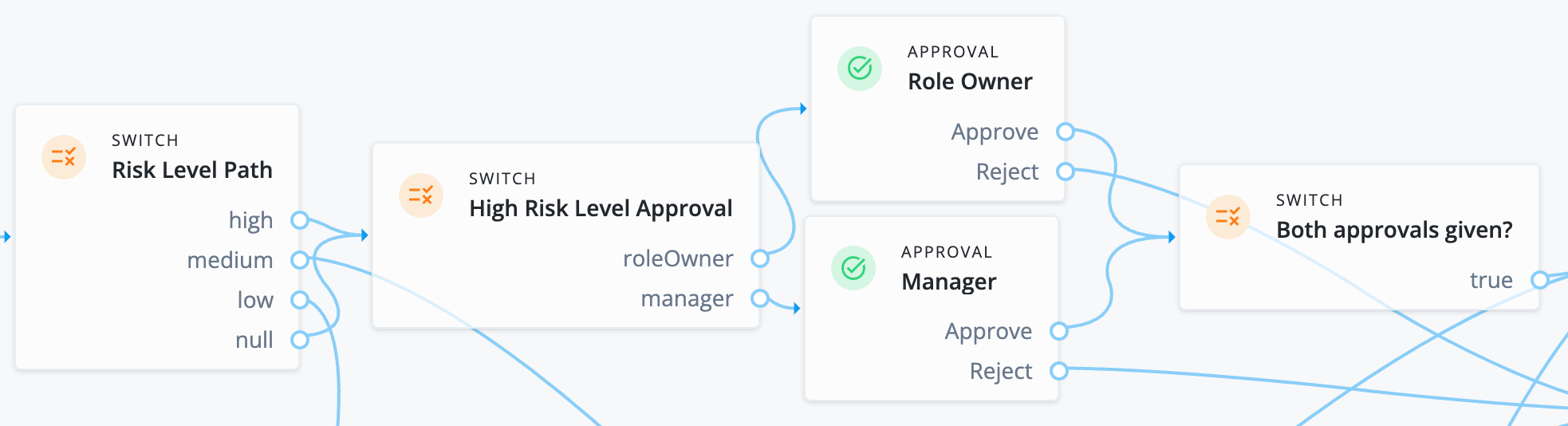
You can find a detailed example of using a Switch node for parallel paths in Role grant workflow example.
Violation node
Assigns a compliance violation task to users. Workflows using the Violation node can better route violation handling in your company.
You can use the node in chain tasks or used in conjunction with the Switch node to implement serial or parallel flows.
Properties
| Property | Usage |
|---|---|
Name |
Violation Task |
Actors |
Select user(s) who acts on the violation.
|
Expiration Settings |
Define what to do when the violation expires. Options are:
|
Notification Settings |
Select which email notifications to send. By default all notifications are enabled. Select any of the following:
|
Wait node
The Wait node pauses the workflow until a specified date and time. Identity Governance checks
the specified timestamp and sets the response of the node to RESUME at which
point, the workflow resumes.
The workflow author is expected to provide:
-
Name of the node
-
Resume date in a selected time or the variable to extract the resume date from
For example, the following workflow demonstrates how you can use the Wait node to grant temporary access to an application. The workflow grants access, pauses until the start date is established, and then automatically validates the application grant.

Properties
| Property | Usage |
|---|---|
Name |
Enter a name for the node. For example, enter |
Select a duration |
Enter the number and select the time periods to wait. Options are:
|
Request property |
Enter a path to a date property on the request object. For example, enter |
Workflow variable |
Enter the name of a custom workflow variable that stores the resume date. For example,
enter |
Workflow use cases
This section presents workflow use cases featuring workflow nodes. Learn more in Workflow nodes.
This section covers the following workflows use cases:
Application grant workflow
In this example, an administrator wants to create an application grant workflow that:
-
Requires the manager to approve the request. If an administrator sends a request, the request is auto-approved.
-
If approved, check what line of business (LOB) the application is in.
-
Based on the LOB, the workflow requires a separate approver to approve the request.
Assumptions
-
Each application has an application owner. An application owner is a user identity designated to manage the application. You populate this value for each target application.
-
You create an application glossary attribute LOB, and populate the LOB for each application. For this scenario, the LOBs are:
-
Sales -
Finance -
Human Resources
-
-
Your end users have a manager assigned to them. An administrator populates this property and it isn’t modifiable by the end user.
Example
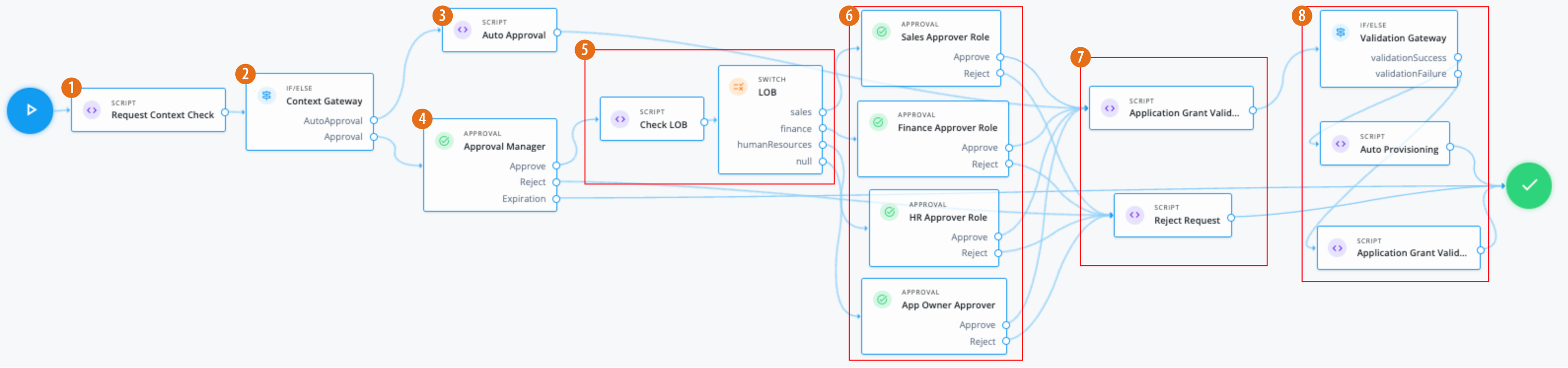
-
1 Use a Script node to do a context check for the request.
Click to display the request context check script
/* Script nodes are used to invoke APIs or execute business logic. You can invoke governance APIs or IDM APIs. You can find details in Manage workflows. Script nodes should return a single value and should have the logic enclosed in a try-catch block. Example: try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; } catch (e) { failureReason = 'Validation failed: Error reading request with id ' + requestId; } */ var content = execution.getVariables(); var requestId = content.get('id'); var context = null; var skipApproval = false; var lineItemId = false; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); if (requestObj.request.common.context) { context = requestObj.request.common.context.type; lineItemId = requestObj.request.common.context.lineItemId; if (context == 'admin') { skipApproval = true; } } } catch (e) { logger.info("Request Context Check failed "+e.message); } logger.info("Context: " + context); execution.setVariable("context", context); execution.setVariable("lineItemId", lineItemId); execution.setVariable("skipApproval", skipApproval); -
2 Use an IF/ELSE node to set the context gateway for auto approval or standard approval based on a manager review.
-
3 Use the Script node to run any auto approvals:
Click to display the auto approval script
var content = execution.getVariables(); var requestId = content.get('id'); var context = content.get('context'); var lineItemId = content.get('lineItemId'); var queryParams = { "_action": "update" } try { var decision = { "decision": "approved", "comment": "Request auto-approved due to request context: " + context } openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); } catch (e) { var failureReason = "Failure updating decision on request. Error message: " + e.message; var update = {'comment': failureReason, 'failure': true}; openidm.action('iga/governance/requests/' + requestId, 'POST', update, queryParams); } -
4 Using an Approval node, the manager of the end user must approve the request.
-
5 If approved, a Script node checks the application glossary attribute
lineOfBusiness(LOB) and sets the outcome based on the LOB of the application. Based on the outcome, the Switch node evaluates the LOB.Click to display check LOB script
var content = execution.getVariables(); var requestId = content.get('id'); var requestObj = null; var appId = null; var appGlossary = null; var lob = null; try { requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); appId = requestObj.application.id; } catch (e) { logger.info("Validation failed: Error reading application grant request with id " + requestId); } try { appGlossary = openidm.action('iga/governance/application/' + appId + '/glossary', 'GET', {}, {}); lob = appGlossary.lineOfBusiness || "default"; execution.setVariable("lob", lob); } catch (e) { logger.info("Could not retrieve glossary with appId " + appId + " from application grant request ID " + requestId); } -
3 If the LOB is:
-
sales: An Approval node requires members of the roleSales App Approverto approve the request. -
finance: An Approval node requires members of the roleFinance App Approverto approve the request. -
humanResources: An Approval node requires members of the roleHuman Resources App Approverto approve the request. -
null: An Approval node requires the application owner to approve the request.
-
-
7 If the required approvals are met, a Script node runs a validation check.
Click to display app grant validation script
logger.info("Running application grant request validation"); var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = null; var applicationId = null; var app = null; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; } catch (e) { failureReason = "Validation failed: Error reading request with id " + requestId; } // Validation 1 - Check application exists if (!failureReason) { try { app = openidm.read('managed/alpha_application/' + applicationId); if (!app) { failureReason = "Validation failed: Cannot find application with id " + applicationId; } } catch (e) { failureReason = "Validation failed: Error reading application with id " + applicationId + ". Error message: " + e.message; } } // Validation 2 - Check the user doesn't already have application granted // Note: this is done at request submission time as well, the following is an example of how to check user's accounts if (!failureReason) { try { var user = openidm.read('managed/alpha_user/' + requestObj.user.id, null, [ 'effectiveApplications' ]); user.effectiveApplications.forEach(effectiveApp => { if (effectiveApp._id === applicationId) { failureReason = "Validation failed: User with id " + requestObj.user.id + " already has effective application " + applicationId; } }) } catch (e) { failureReason = "Validation failed: Unable to check effective applications of user with id " + requestObj.user.id + ". Error message: " + e.message; } } if (failureReason) { logger.info("Validation failed: " + failureReason); } execution.setVariable("failureReason", failureReason);If any Approval node has the
Rejectoutcome, a Script node denies the request.Click to display reject request script
logger.info("Rejecting request"); var content = execution.getVariables(); var requestId = content.get('id'); logger.info("Execution Content: " + content); var requestIndex = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var decision = {'outcome': 'denied', 'status': 'complete', 'decision': 'rejected'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); -
8 If the If/Else node outcome is:
-
validationSuccess: A Script node provisions the application to the end user.Click to display auto provisioning script
logger.info("Auto-Provisioning"); var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = null; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); logger.info("requestObj: " + requestObj); } catch (e) { failureReason = "Provisioning failed: Error reading request with id " + requestId; } if(!failureReason) { try { var request = requestObj.request; var payload = { "applicationId": request.common.applicationId, "startDate": request.common.startDate, "endDate": request.common.endDate, "auditContext": {}, "grantType": "request" }; var queryParams = { "_action": "add" } logger.info("Creating account: " + payload); var result = openidm.action('iga/governance/user/' + request.common.userId + '/applications' , 'POST', payload,queryParams); } catch (e) { failureReason = "Provisioning failed: Error provisioning account to user " + request.common.userId + " for application " + request.common.applicationId + ". Error message: " + e.message; } var decision = {'status': 'complete', 'decision': 'approved'}; if (failureReason) { decision.outcome = 'not provisioned'; decision.comment = failureReason; decision.failure = true; } else { decision.outcome = 'provisioned'; } var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed."); } -
validationFailure: A Script node doesn’t provision the application to the end user.Click to display validation failure script
var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = content.get('failureReason'); var decision = {'outcome': 'not provisioned', 'status': 'complete', 'comment': failureReason, 'failure': true, 'decision': 'approved'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams);
-
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
Entitlement grant workflow
In this example, an administrator wants to create an entitlement grant workflow that:
-
An entitlement owner must approve the request. If an administrator sends a request, the request is auto-approved.
-
If approved, check if the entitlement is marked as
privileged.Companies can define what privilegedmeans in the glossary. However, usually, aprivilegedentitlement gives administrative rights to sensitive data, such as view access to quarterly reports before public release. -
If the entitlement is privileged or null, the end user’s manager must approve the request.
Assumptions
-
Each entitlement has an entitlement owner. An entitlement owner is a user identity designated to manage the entitlement.
-
You create a boolean entitlement glossary attribute ,
isPrivileged. This attribute is populated for each entitlement. -
Your end users have a manager assigned to them. An administrator populates this property and isn’t modifiable by the end user.
Example
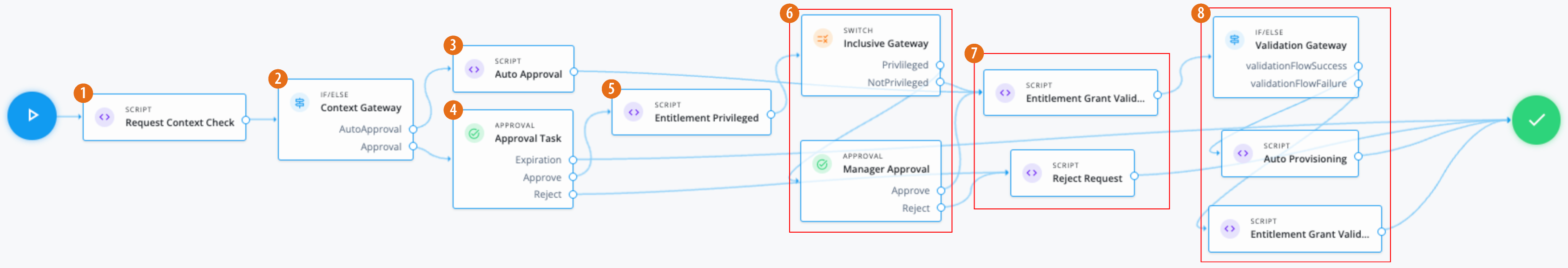
-
1 Use a Script node to do a context check for the request.
Click to display the request context check script
/* Script nodes are used to invoke APIs or execute business logic. You can invoke governance APIs or IDM APIs. Learn more in Manage workflows. Script nodes should return a single value and should have the logic enclosed in a try-catch block. Example: try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; } catch (e) { failureReason = 'Validation failed: Error reading request with id ' + requestId; } */ var content = execution.getVariables(); var requestId = content.get('id'); var context = null; var skipApproval = false; var lineItemId = false; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); if (requestObj.request.common.context) { context = requestObj.request.common.context.type; lineItemId = requestObj.request.common.context.lineItemId; if (context == 'admin') { skipApproval = true; } } } catch (e) { logger.info("Request Context Check failed "+e.message); } logger.info("Context: " + context); execution.setVariable("context", context); execution.setVariable("lineItemId", lineItemId); execution.setVariable("skipApproval", skipApproval); -
2 Use an IF/ELSE node to set the context gateway.
-
3 Use the Script node to run an auto approval:
Click to display the auto approval script
var content = execution.getVariables(); var requestId = content.get('id'); var context = content.get('context'); var lineItemId = content.get('lineItemId'); var queryParams = { "_action": "update" } var lineItemParams = { "_action": "updateRemediationStatus" } try { var decision = { "decision": "approved", "comment": "Request auto-approved due to request context: " + context } openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); } catch (e) { var failureReason = "Failure updating decision on request. Error message: " + e.message; var update = {'comment': failureReason, 'failure': true}; openidm.action('iga/governance/requests/' + requestId, 'POST', update, queryParams); } -
4 Using an Approval node, the entitlement owner must approve the request.
-
5 Use a Script node to check the value of the entitlement glossary attribute
isPrivilegedand set the outcome.Click to display the entitlement privileged script
var content = execution.getVariables(); var requestId = content.get('id'); var requestObj = null; var entId = null; var entGlossary = null; var entPriv = null; //Check entitlement exists and grab entitlement info try { requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); entId = requestObj.assignment.id; } catch (e) { logger.info("Validation failed: Error reading entitlement grant request with id " + requestId); } //Check glossary for entitlement exists and grab glossary info try { entGlossary = openidm.action('iga/governance/resource/' + entId + '/glossary', 'GET', {}, {}); // Sets entPriv based on the glossary contents, if present, otherwise defaults to true entPriv = (entGlossary.hasOwnProperty("isPrivileged")) ? entGlossary.isPrivileged : true; //Sets entPriv based on glossary contents, if present, otherwise defaults to false //entPriv = !!entGlossary.isPrivileged; execution.setVariable("entPriv", entPriv); } catch (e) { logger.info("Could not retrieve glossary with entId " + entId + " from entitlement grant request ID " + requestId); } -
6 Use a switch node to route outcomes based on the script. If the outcome is:
-
privileged(entPriv==true): An additional Approval node requires the end user’s manager to approve the request. -
notPrivileged(entPriv==false`): An additional approval isn’t required.
-
-
7 If the required approvals are met, the Script node runs a validation check.
Click to display the entitlement grant validation script
logger.info("Running entitlement grant request validation"); var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = null; var applicationId = null; var assignmentId = null; var app = null; var assignment = null; var existingAccount = false; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; assignmentId = requestObj.assignment.id; } catch (e) { failureReason = "Validation failed: Error reading request with id " + requestId; } // Validation 1 - Check application exists if (!failureReason) { try { app = openidm.read('managed/alpha_application/' + applicationId); if (!app) { failureReason = "Validation failed: Cannot find application with id " + applicationId; } } catch (e) { failureReason = "Validation failed: Error reading application with id " + applicationId + ". Error message: " + e.message; } } // Validation 2 - Check entitlement exists if (!failureReason) { try { assignment = openidm.read('managed/alpha_assignment/' + assignmentId); if (!assignment) { failureReason = "Validation failed: Cannot find assignment with id " + assignmentId; } } catch (e) { failureReason = "Validation failed: Error reading assignment with id " + assignmentId + ". Error message: " + e.message; } } // Validation 3 - Check the user has application granted if (!failureReason) { try { var user = openidm.read('managed/alpha_user/' + requestObj.user.id, null, [ 'effectiveApplications' ]); user.effectiveApplications.forEach(effectiveApp => { if (effectiveApp._id === applicationId) { existingAccount = true; } }) } catch (e) { failureReason = "Validation failed: Unable to check existing applications of user with id " + requestObj.user.id + ". Error message: " + e.message; } } // Validation 4 - If account doesn't exist, provision it if (!failureReason) { if (!existingAccount) { try { var request = requestObj.request; var payload = { "applicationId": applicationId, "startDate": request.common.startDate, "endDate": request.common.endDate, "auditContext": {}, "grantType": "request" }; var queryParams = { "_action": "add" } logger.info("Creating account: " + payload); var result = openidm.action('iga/governance/user/' + request.common.userId + '/applications' , 'POST', payload,queryParams); } catch (e) { failureReason = "Validation failed: Error provisioning new account to user " + request.common.userId + " for application " + applicationId + ". Error message: " + e.message; } } } if (failureReason) { logger.info("Validation failed: " + failureReason); } execution.setVariable("failureReason", failureReason);If any Approval node has the
Rejectoutcome, a Script node denies the request.Click to display the reject request script
logger.info("Rejecting request"); var content = execution.getVariables(); var requestId = content.get('id'); logger.info("Execution Content: " + content); var requestIndex = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var decision = {'outcome': 'denied', 'status': 'complete', 'decision': 'rejected'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); -
8 If the
If/elsenode outcome is:-
validationFlowSuccess: A Script node provisions the application to the end user.Click to display the auto provisioning script
logger.info("Auto-Provisioning"); var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = null; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); logger.info("requestObj: " + requestObj); } catch (e) { failureReason = "Provisioning failed: Error reading request with id " + requestId; } if(!failureReason) { try { var request = requestObj.request; var payload = { "entitlementId": request.common.entitlementId, "startDate": request.common.startDate, "endDate": request.common.endDate, "auditContext": {}, "grantType": "request" }; var queryParams = { "_action": "add" } var result = openidm.action('iga/governance/user/' + request.common.userId + '/entitlements' , 'POST', payload,queryParams); } catch (e) { failureReason = "Provisioning failed: Error provisioning entitlement to user " + request.common.userId + " for entitlement " + request.common.entitlementId + ". Error message: " + e.message; } var decision = {'status': 'complete', 'decision': 'approved'}; if (failureReason) { decision.outcome = 'not provisioned'; decision.comment = failureReason; decision.failure = true; } else { decision.outcome = 'provisioned'; } var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed."); } -
validationFlowFailure: A Script node doesn’t provision the application to the end user.Click to display the validation failure script
var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = content.get('failureReason'); var decision = {'outcome': 'not provisioned', 'status': 'complete', 'comment': failureReason, 'failure': true, 'decision': 'approved'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams);
-
|
Download the JSON file for this workflow here. For information on how to import or export workflows, learn more in workflow editor canvas. |
Role grant workflow
In this example, an administrator wants to create a role grant workflow that:
-
Checks the risk level of the role.
-
Separate approvals are required based on the risk level. Specifically, if the risk level is
high, send two approvals, in parallel, to the end user’s manager and the role owner.
Assumptions
-
Each role has a role owner. The role owner is a user identity designated to manage the role.
-
You create a role glossary attribute (string with enumerated value),
riskLevel, that has the following values:-
low -
medium -
highFor each role, this attribute is populated.
-
-
Your end users have a manager assigned to them. An administrator populates this property and isn’t modifiable by the end user.
Example
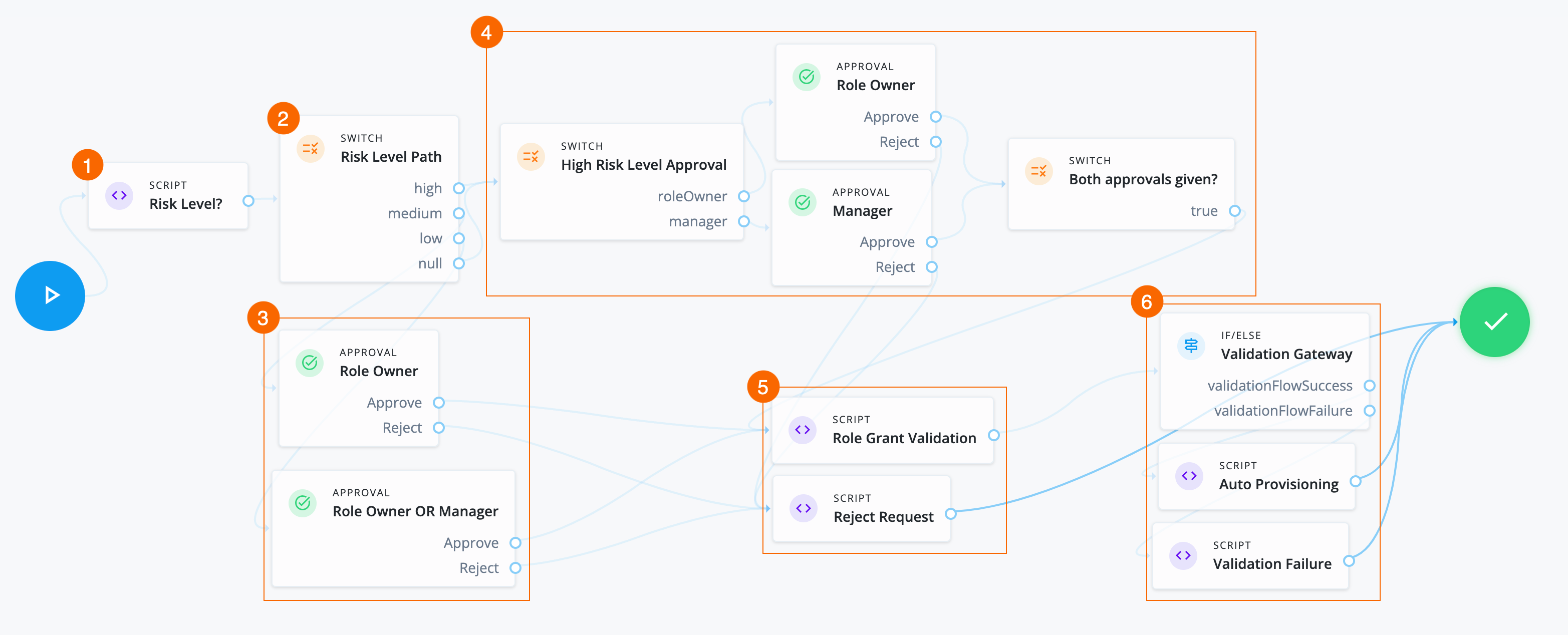
-
1 A Script node checks the value of the role glossary attribute
riskLeveland sets outcomes.Click to display risk level script
var content = execution.getVariables(); var requestId = content.get('id'); var requestObj = null; var roleId = null; var roleGlossary = null; var riskLevel = null; try { requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); riskId = requestObj.risk.id; } catch (e) { logger.info("Validation failed: Error reading role grant request with id " + requestId); } try { roleGlossary = openidm.action('iga/governance/role/' + roleId + '/glossary', 'GET', {}, {}); riskLevel = roleGlossary.riskLevel; execution.setVariable("riskLevel", riskLevel); } catch (e) { logger.info("Could not retrieve glossary with roleId " + roleId + " from role grant request ID " + requestId); } -
2 A Switch node determines the path to take based on the Script node.
-
3 If the risk level is:
-
low: An Approval node requires either the role owner or the end user’s manager to approve the request. -
medium: An Approval node requires the role owner to approve the request.
-
-
4 If the risk level is
highornullthen:-
A Switch node sends two approval tasks in parallel.
-
An Approval node requires the role owner to approve the request.
-
An Approval node requires the end user’s manager to approve the request.
-
A closing Switch node waits for both approvals before proceeding to provision the role.
-
-
5 If the required approvals are met, a Script node runs a validation check.
Click to display the Role Grant Validation script
logger.info("Running role grant request validation"); var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = null; var roleId = null; var role = null; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); roleId = requestObj.role.id; } catch (e) { failureReason = "Validation failed: Error reading request with id " + requestId; } // Validation 1 - Check role exists if (!failureReason) { try { role = openidm.read('managed/alpha_role/' + roleId); if (!role) { failureReason = "Validation failed: Cannot find role with id " + roleId; } } catch (e) { failureReason = "Validation failed: Error reading role with id " + roleId + ". Error message: " + e.message; } } if (failureReason) { logger.info("Validation failed: " + failureReason); } execution.setVariable("failureReason", failureReason);If any Approval node has the
Rejectoutcome, a Script node denies the request.Click to display Reject Request script
logger.info("Rejecting request"); var content = execution.getVariables(); var requestId = content.get('id'); logger.info("Execution Content: " + content); var requestIndex = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var decision = {'outcome': 'denied', 'status': 'complete', 'decision': 'rejected'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); -
6 If the If/else node outcome is:
-
validationFlowSuccess: A Script node provisions the application to the end user.Click to display Auto Provisioning script
logger.info("Auto-Provisioning"); var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = null; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); logger.info("requestObj: " + requestObj); } catch (e) { failureReason = "Provisioning failed: Error reading request with id " + requestId; } if(!failureReason) { try { var request = requestObj.request; var payload = { "roleId": request.common.roleId, "startDate": request.common.startDate, "endDate": request.common.endDate, "auditContext": {}, "grantType": "request" }; var queryParams = { "_action": "add" } var result = openidm.action('iga/governance/user/' + request.common.userId + '/roles' , 'POST', payload,queryParams); } catch (e) { failureReason = "Provisioning failed: Error provisioning role to user " + request.common.userId + " for role " + request.common.roleId + ". Error message: " + e.message; } var decision = {'status': 'complete', 'decision': 'approved'}; if (failureReason) { decision.outcome = 'not provisioned'; decision.comment = failureReason; decision.failure = true; } else { decision.outcome = 'provisioned'; } var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed."); } -
validationFlowFailure: A Script node doesn’t provision the application to the end user.Click to display Validation Failure script
var content = execution.getVariables(); var failureReason = content.get('failureReason'); var decision = {'outcome': 'not provisioned', 'status': 'complete', 'comment': failureReason, 'failure': true, 'decision': 'approved'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams);
-
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
Role remove workflow
In this example, an administrator wants to create a workflow that:
-
Handles a normal role removal access request.
-
Includes a context check for administrator-submitted requests.
-
Skips the approval task process and runs auto-approval and auto-deprovisioning scripts if the context check passes.
Assumptions
-
Each role has a role owner.
-
Notification settings and email templates exist.
-
Make sure to catch any error/failure conditions.
Example
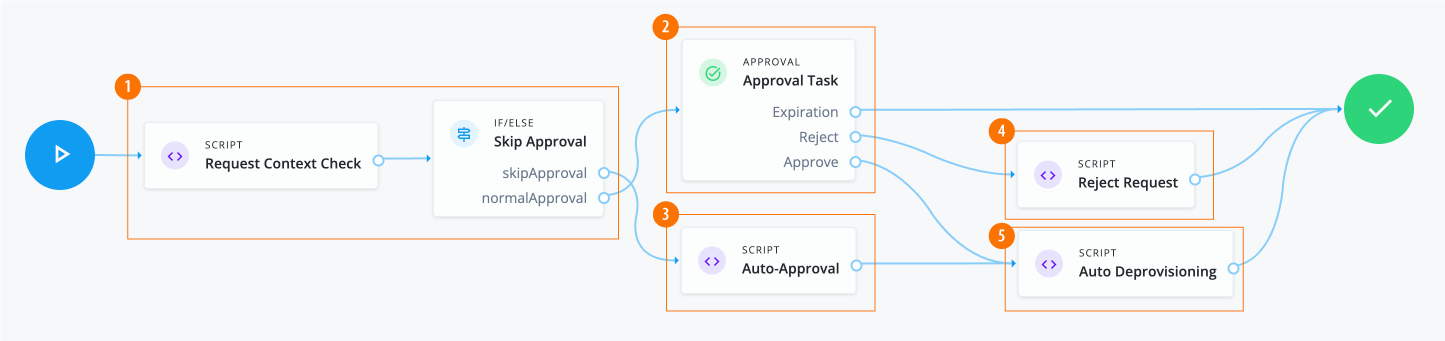
-
1 The Script node invokes the APIs and checks the context. If the context is
adminorcertification, it skips the manual approval process.Click to display request context check script
var content = execution.getVariables(); var requestId = content.get('id'); var context = null; var skipApproval = false; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); if (requestObj.request.common.context) { context = requestObj.request.common.context.type; if (context === 'admin' || context === 'certification') { skipApproval = true; } } } catch (e) {} logger.info("Context: " + context); execution.setVariable("context", context); execution.setVariable("skipApproval", skipApproval); -
2 The Approval node assigns an approval task to users and roles. The node chains tasks in conjunction with a Switch node to implement serial or parallel flows.
Click to display the approval task properties
Item Description Name
Approval TaskApprovers
Two options are available:
-
Add users and roles manually, such as
Role Ownerand defineApprovertype-
Approve
-
Reject
-
Forward
-
Modify
-
Comment
-
-
Define users using a script:
Form
Select a form to present to the reviewer:
-
Dynamic form selection. This selection is typically used for basic out-of-the-box workflows, like
BasicApplicationGrantand others. -
Choose a form. This selection is typically used for custom request type forms.
Expiration Settings
Options are:
-
Reject request
-
Reassign request
-
Do nothing
Notification Settings
Options are:
-
Assignment notification and email templates, such as
requestAssigned. -
Reassignment notification and email templates, such as
requestReassigned. -
Assignee reminders and email templates, such as
requestReminder.-
Sends every number of time periods, such as
3 day(s).
-
-
Escalation notifications and email templates, such as
requestEscalated.-
Send every number of day(s), such as
5 day(s). -
Send to
Send escalation totoUser, and selectUser.
-
-
Expiration notification and email templates, such as
requestExpired.-
Send the notification on the configured number of days before expiration.
-
-
-
3 Invokes the auto-approval script if
scriptApprovalis true.Click to display auto-approval script
var content = execution.getVariables(); var requestId = content.get('id'); var context = content.get('context'); var queryParams = { "_action": "update" } try { var decision = { "decision": "approved", "comment": "Request auto-approved due to request context: " + context } openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); } catch (e) { var failureReason = "Failure updating decision on request. Error message: " + e.message; var update = {'comment': failureReason, 'failure': true}; openidm.action('iga/governance/requests/' + requestId, 'POST', update, queryParams); } -
4 Runs a
RejectRequestscript whenApproval tasknode returns areject.Click to display
RejectRequestscriptlogger.info("Rejecting request"); var content = execution.getVariables(); var requestId = content.get('id'); logger.info("Execution Content: " + content); var requestIndex = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var decision = {'outcome': 'denied', 'status': 'complete', 'decision': 'rejected'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); -
5 Run Auto Deprovisioning script.
Click to display the auto deprovisioning script
logger.info("Auto-Deprovisioning"); var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = null; try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); logger.info("requestObj: " + requestObj); } catch (e) { failureReason = "Deprovisioning failed: Error reading request with id " + requestId; } if(!failureReason) { try { var request = requestObj.request; var payload = { "roleId": request.common.roleId, "startDate": request.common.startDate, "endDate": request.common.endDate, "auditContext": {}, "grantType": "request" }; var queryParams = { "_action": "remove" } var result = openidm.action('iga/governance/user/' + request.common.userId + '/roles' , 'POST', payload,queryParams); } catch (e) { failureReason = "Deprovisioning failed: Error deprovisioning role to user " + request.common.userId + " for role " + request.common.roleId + ". Error message: " + e.message; } var decision = {'status': 'complete', 'decision': 'approved'}; if (failureReason) { decision.outcome = 'not provisioned'; decision.comment = failureReason; decision.failure = true; } else { decision.outcome = 'provisioned'; } var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed."); }
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
Violation workflow
In this example, an administrator creates a workflow that:
-
Processes a single violation task.
-
If the violation outcome is
Remediate, it remediates the violation, validates the result, and removes the entitlements. -
If the violation outcome is
Allow, it creates an exception. -
If the violation outcome is
expiration, it goes to a manual decision using the fulfillment node. -
If the end user tasked with the manual fulfillment approves of the various outcomes, the workflow is complete.
-
If the end user tasked with the manual fulfillment denies the resulting outcomes, the workflow calls a reject requests script, and loops back for another manual confirmation.
Example
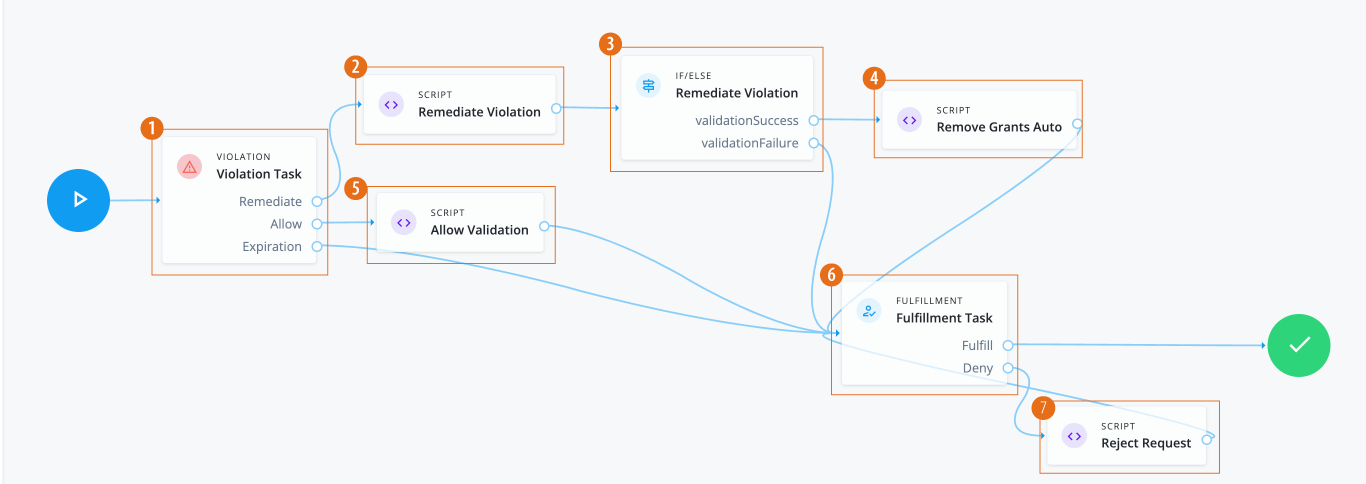
-
1 The Violation node routes the violation to the appropriate outcome. Options are:
Remediate,Allow, andExpiration. -
2 The Remediate Violation Script node gets the context information for the violation and sets the
remediationResponse.Click to display Remediate Violation script
logger.info("Remediating violation"); var content = execution.getVariables(); var violationId = content.get('id'); var remediation = content.get('remediation'); logger.info("Remediating violation - violationId: " + violationId + ', remediation payload: ' + remediation); var remediationContent = null; var remediationResponse = openidm.action('iga/governance/violation/' + violationId + '/remediate', 'POST', remediation); logger.info("Remediating response: " + remediationResponse); remediationContent = remediationResponse.decision.remediation; execution.setVariable("remediation", remediationContent); -
3 The Remediate Violation IF/ELSE node routes successful validations to an auto remove script node and validation failures to a failure handling node.
-
4 The Remove Grants Auto script node removes the entitlement grants that caused the violation.
Click to display Auto Remove Entitlement Grants script
logger.info("Removing grants automatically"); var content = execution.getVariables(); var violationId = content.get('id'); var failureReason = null; var phaseName = content.get('phaseName'); var violationObj; logger.info("Removing entitlement grants for violation " + violationId + " with phase name " + phaseName); try { violationObj = openidm.action('iga/governance/violation/lookup/' + violationId, 'GET', {}, {}); } catch (e) { failureReason = "Removing entitlement grants failed: Error reading violation with id " + violationId + ". Error message: " + e.message; } if (!failureReason) { var remediation = violationObj.decision.remediation; var failedDeprovisioning = false; var deprovisionedIds = []; for(var grant of violationObj.violatingAccess) { if (!remediation.grantIds.includes(grant.compositeId)) { continue; } var userId = violationObj.user.id; logger.info("Removing entitlement grant: " + grant.compositeId + ", user: " + userId + ", violation: " + violationId); try { var payload = { entitlementId: grant.assignment.id }; logger.info('Payload to remove grant: ' + JSON.stringify(payload)); var queryParams = { "_action": "remove" } var result = openidm.action('iga/governance/user/' + userId + '/entitlements', 'POST', payload,queryParams); execution.setVariables(result); logger.info("Deprovisioned " + grant.assignment.id + " successfully, user " + userId + + ", violation: " + violationId); deprovisionedIds.push(grant.compositeId); } catch (e) { failureReason = failureReason + ". Removing grants failed: Error deprovisioning entitlement" + grant.assignment.id + " from user. Error message: " + e.message + "."; failedDeprovisioning = true; } } if (!failedDeprovisioning) { openidm.action('iga/governance/violation/' + violationId + '/remediation/status/complete', 'POST', {}); } else { failureReason = failureReason + ". Grants removed: " + deprovisionedIds; } } if (failureReason) { var update = { 'comment': failureReason }; openidm.action('iga/governance/violation/' + violationId + '/comment', 'POST', update, {}); } -
5 The Allow Violation script node logs the information. If a failure arises, Identity Governance posts the failure with the reason.
Click to display Allow Violation script node
logger.info("Allowing violation"); var content = execution.getVariables(); var violationId = content.get('id'); var phaseName = content.get('phaseName'); logger.info("Violation to be allowed: " + violationId + " with phase name " + phaseName); var failureReason = null; try { var allowResponse = openidm.action('iga/governance/violation/' + violationId + '/allow', 'POST', {}); logger.info("Violation " + violationId + " was allowed successfully.");} catch (e) { failureReason = "Failed allowing violation with id " + violationId + ". Error message: " + e.message; } if (failureReason) { var update = { "comment": failureReason }; try { openidm.action('iga/governance/violation/' + violationId + '/phases/' + phaseName + '/comment', 'POST', update, {}); } catch (e) { openidm.action('iga/governance/violation/' + violationId + '/comment', 'POST', update, {}); } } -
6 The Fulfillment node requests a manual completion of the task by an authorized end user, typically during review time. If successful, the task is fulfilled, and the workflow is complete.
-
7 The Reject Request script node retrieves the
requestID, logs the rejection, and sends a reject request.Click to display Reject Request script
logger.info("Rejecting request"); var content = execution.getVariables(); var requestId = content.get('id'); logger.info("Execution Content: " + content); var requestIndex = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var decision = {'outcome': 'denied', 'status': 'complete', 'decision': 'rejected'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams);
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
User create event workflow - send email
In this example, an administrator creates a workflow that:
-
Sends an email notification to the new user when a user create event occurs.
-
Copies their manager, as well, if present.
Example
-
1 The Script node sends email to the new user and cc’s to the user’s manager.
Click to display send email script
logger.info("Running user create event role workflow - send email"); var content = execution.getVariables(); var requestId = content.get('id'); // Read event user information from request object try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var userObj = requestObj.request.common.blob.after; var userDisplayName = userObj.givenName + " " + userObj.sn + " (" + userObj.userName + ")"; var body = { subject: "New user created: " + userDisplayName, to: userObj.mail, body: "New user created: " + userDisplayName + ".", object: {} }; if (userObj && userObj.manager && userObj.manager.mail) { body.cc = userObj.manager.mail }; openidm.action("external/email", "send", body); } catch (e) { logger.info("Unable to send new user creation email"); } // Update event request as final var decision = {'status': 'complete', 'outcome': 'fulfilled', 'decision': 'approved'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed.");
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
User create event workflow - catalog lookup
In this example, an administrator creates a workflow that:
-
Submits a request to add the
Data AnalystandSecurityroles to a newly created user when a user create event occurs. -
Looks up the two roles in the catalog.
Example
-
1 The Script node looks up two roles in the catalog. If the roles are present in the catalog, the script generates a request for roles.
Click to display
Submit Request for Rolesscriptlogger.info("Running user create event role workflow"); var content = execution.getVariables(); var requestId = content.get('id'); var failureReason = null; var userObj = null; var userId = null; // Read event user information from request object try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); userObj = requestObj.request.common.blob.after; userId = userObj.userId; } catch (e) { failureReason = "Validation failed: Error reading request with id " + requestId; } // Define roles to request var roleNames = [ "Data Analyst", "Security" ]; // Look up roles in catalog var operand = []; for (var index in roleNames) { operand.push({operator: "EQUALS", operand: { targetName: "role.name", targetValue: roleNames[index] }}) } var body = { targetFilter: {operator: "OR", operand: operand}}; var catalog = openidm.action("iga/governance/catalog/search", "POST", body); var catalogResults = catalog.result; // Define request catalogs key var catalogBody = []; for (var idx in catalogResults) { var catalog = catalogResults[idx]; catalogBody.push({type: "role", id: catalog.id}) } // Define request payload var requestBody = { priority: "low", accessModifier: "add", justification: "Request submitted on user creation.", users: [ userId ], catalogs: catalogBody }; // Create requests try { openidm.action("iga/governance/requests", "POST", requestBody, {_action: "create"}) } catch (e) { failureReason = "Unable to generate requests for roles"; } // Update event request as final var decision = failureReason ? {'status': 'complete', 'outcome': 'cancelled', 'decision': 'rejected', 'comment': failureReason, 'failure': true} : {'status': 'complete', 'outcome': 'fulfilled', 'decision': 'approved'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed.");
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
User create event workflow - request two roles
In this example, an administrator creates a workflow that submits a separate request to add two roles to the newly created user. The script is triggered when a user create event occurs.
Example
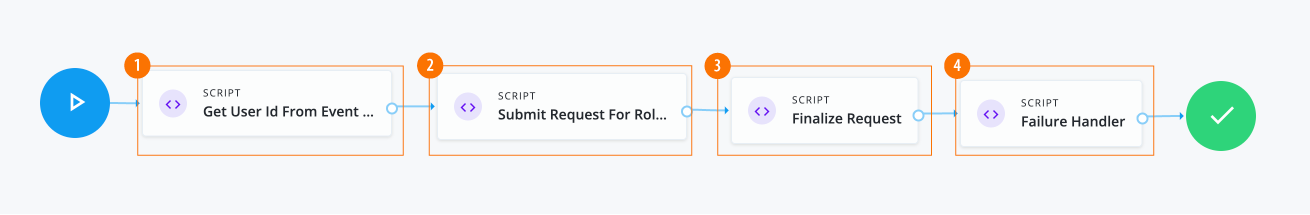
-
1 The Script node gets a user ID from the event request and returns the user object.
Click to display
Get User ID from event requestscriptlogger.info("Get User Id From Event Request: UserCreateEventWithSteps"); var content = execution.getVariables(); var requestId = content.get('id'); // Read event user information from request object try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var userObj = requestObj.request.common.blob.after; execution.setVariable("userId", userObj.userId); } catch (e) { execution.setVariable("failureState", "Validation failed: Error reading request with id " + requestId); } -
2 The Script node makes a call to create the request. The payload contains two catalog IDs for the
Data AnalystandSecurityroles.Click to display
Submit request for rolesscriptlogger.info("Submit Role Requests: UserCreateEventWithSteps"); var content = execution.getVariables(); var userId = content.get('userId'); var failureState = content.get('failureState'); // Define request payload if (!failureState) { var requestBody = { priority: "low", accessModifier: "add", justification: "Request submitted on user creation: UserCreateEventWithSteps.", users: [ userId ], catalogs: [ { type: "role", id: "b9224b9ae535c9eab3f493dc206ac689dc9f6733b417d0def37f8969bef3e95dad7c812e4585056f698c7b3eb15c970dfa939eca8217741af187978359af13df"}, { type: "role", id: "e7ec51656c6f5ca297d82772a681e3069d8a7c24c04f15afaa8060856e17ad6e76f88bdeb635d4dc8c3d8faa462f376189322e85df379ae0721fcb2d28d1a222"} ] }; // Create requests try { openidm.action("iga/governance/requests", "POST", requestBody, {_action: "create"}) } catch (e) { execution.setVariable("failureState", "Unable to generate requests for roles"); } } -
3 The Script node completes the request.
Click to display
Finalize requestscriptlogger.info("Finalize Request: UserCreateEventWithSteps"); var content = execution.getVariables(); var requestId = content.get('requestId'); var failureState = content.get('failureState'); if (!failureState) { try { // Update event request as final var decision = {'status': 'complete', 'outcome': 'fulfilled', 'decision': 'approved'} var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed."); } catch (e) { execution.setVariable("failureState", "Unable to finalize request."); } } -
4 The Script node handles any failures.
Click to display
Failure handlerscriptlogger.info("Failure Handler: UserCreateEventWithSteps"); var content = execution.getVariables(); var requestId = content.get('requestId'); var failureReason = content.get('failureReason'); // Update event request as final if (failureReason) { var decision = {'status': 'complete', 'outcome': 'cancelled', 'decision': 'rejected', 'comment': failureReason, 'failure': true} var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed."); }The User create event with email workflow example, User create event with catalog lookup workflow example, and User create event with two roles workflow example examples present
User createevent workflows. However, you can also adjust the workflows forUser updateevents. For example, in theUser createexamples, the user object returns the current or after state of the user:var userObj = requestObj.request.common.blob.afterUpdate events also have access to the before (or pre-update) state by referencing the object, which you can also use in your scripts.
var userObj = requestObj.request.common.blob.before
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
User offboarding workflow
In this example, an administrator creates a workflow that triggers a series of offboarding tasks when a user update occurs, such as a status, manager, or department change.
The offboarding tasks include:
-
Setting up a replacement user ID for the inactive user. Depending on the case, the replacement user is the manager or former manager.
-
Setting up a replacement user ID as a delegate for the inactive user.
-
Replacing all instances of other users delegating to the inactive user with replacement user ID.
-
Replacing the inactive user with the replacement user ID as an app owner.
-
Replacing the inactive user with the replacement user ID as an entitlements owner.
-
Replacing the inactive user with the replacement user ID as a role owner.
-
Replacing the inactive user with the replacement user ID as an access request approver.
-
Replacing the inactive user with the replacement user ID as a violations approver.
Assumptions
-
Human Resources confirms the user’s change in status, manager, or department and has activated offboarding tasks to stakeholders.
Example
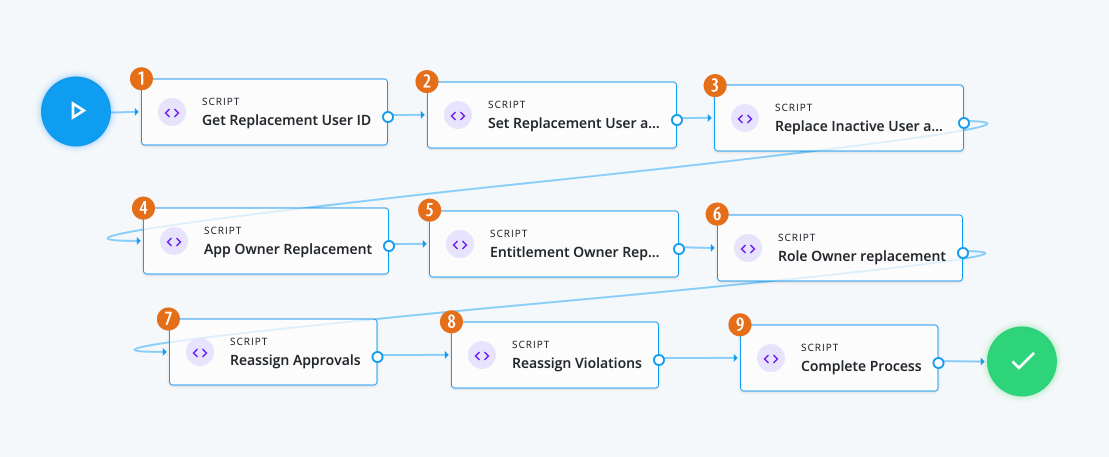
-
1 The Script node reads the event user information, including manager data from the request object.
Click to display the Get Replacement User ID script
// Insert logic to set ID of user who will be replacing inactive user logger.info("Getting ID of user who will be replacing inactive user."); var content = execution.getVariables(); var requestId = content.get('id'); // Read event user information from request object try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var previousUserObj = requestObj.request.common.blob.before; var currentUserObj = requestObj.request.common.blob.after; var userId = currentUserObj.id; var replacementId = null; // Check current value of manager, or previous manager if not present, to find a replacement user ID if (currentUserObj && currentUserObj.manager) { replacementId = currentUserObj.manager.id; } else if (previousUserObj && previousUserObj.manager) { replacementId = previousUserObj.manager.id; } execution.setVariable('userId', userId); execution.setVariable('replacementId', replacementId); } catch(e) { logger.info("Unable to get replacement user ID for inactive user " + userId); } -
2 The Script node adds the replacement user as a delegate for the inactive user so that they can act on their tasks.
Click to display Set Replacement User as Inactive User script
// Adding the Replacement User as a delegate for the Inactive User so that they will be able to act on their tasks var content = execution.getVariables(); var userId = content.get('userId'); var replacementId = content.get('replacementId'); // Read event user information from request object try { if (replacementId) { logger.info("Adding " + replacementId + " as inactive user " + userId + "'s delegate"); var payload = { proxyIds: [ "managed/user/" + replacementId ]}; var proxyUpdate = openidm.action('iga/governance/user/' + userId + '/set-proxy', 'POST', payload, {}); logger.info("Added " + replacementId + " as a delegate for inactive user " + userId); } } catch(e) { logger.info("Unable to add delegate for inactive user " + userId); } -
3 The Script node replaces all instances of other users delegating to the inactive user with the replacement user.
Click to display the Replace Inactive User as delegate script
// Replacing all instances of others delegating to the inactive user with replacement user // Before script: User A and User B both delegate to inactive User // After script: User A and User B both delegate to replacement User var content = execution.getVariables(); var userId = content.get('userId'); var replacementId = content.get('replacementId'); try { if (replacementId) { logger.info("Replacing instances of users delegating to inactive user " + userId + " with " + replacementId); // Get the list of users delegating to inactive user var inactiveUser = openidm.query("managed/alpha_user/" + userId + '/taskPrincipals', { _queryFilter: 'true' }, [ '_refResourceId' ]); var usersDelegatingToInactiveUser = inactiveUser.result; // Set the payloads var removePayload = { proxyIds: [ "managed/user/" + userId ]}; var addPayload = { proxyIds: [ "managed/user/" + replacementId ]}; // For each delegate, remove the inactive user and add the replacement user for (var i = 0; i < usersDelegatingToInactiveUser.length; i++) { var delegatingUserId = usersDelegatingToInactiveUser[i]._refResourceId; openidm.action("iga/governance/user/" + delegatingUserId + "/remove-proxy", "POST", removePayload, {}); openidm.action("iga/governance/user/" + delegatingUserId + "/set-proxy", "POST", addPayload, {}); } logger.info("Replaced instances of users delegating to inactive user " + userId + " with " + replacementId); } } catch(e) { logger.info("Unable to replace instances of users delegating to inactive user " + userId + " with " + replacementId); } -
4 The Script node invokes the APIs and executes business logic.
Click to display the App Owner Replacement script
/* Script nodes are used to invoke APIs or execute business logic. You can invoke governance APIs or IDM APIs. Learn more in https://docs.pingidentity.com/pingoneaic/identity-governance/administration/workflow-configure.html. Script nodes should return a single value and should have the logic enclosed in a try-catch block. Example: try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; } catch (e) { failureReason = 'Validation failed: Error reading request with id ' + requestId; } */ var content = execution.getVariables(); var userId = content.get('userId'); var replacementId = content.get('replacementId'); var queryFilter = {"_queryFilter": "true"} var removeBody = []; var addBody = []; var applications = openidm.query('managed/alpha_user/' + userId + '/ownerOfApp', queryFilter, []); for(var app of applications['result']){ removeBody.push({ "operation": "remove", "field": "/ownerOfApp", "value": { "_ref": app._ref, "_refProperties": { "_id": app._id, "_rev": app._rev }, "_refResourceCollection": "managed/alpha_application", "_refResourceId": app._refResourceId } }) addBody.push({ "operation": "add", "field": "ownerOfApp/-", "value": { "_ref": app._ref, "_refProperties": {} } }) } openidm.patch('managed/alpha_user/'+ userId, null, removeBody) openidm.patch('managed/alpha_user/'+ replacementId, null, addBody) -
5 The Script node replaces the entitlement owner.
Click to display the Entitlement Owner Replacement script
/* Script nodes are used to invoke APIs or execute business logic. You can invoke governance APIs or IDM APIs. Learn more in https://docs.pingidentity.com/pingoneaic/identity-governance/administration/workflow-configure.html. Script nodes should return a single value and should have the logic enclosed in a try-catch block. Example: try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; } catch (e) { failureReason = 'Validation failed: Error reading request with id ' + requestId; } */ var content = execution.getVariables(); var userId = content.get('userId'); var replacementId = content.get('replacementId'); var targetFilter = {"targetFilter": { "operator": "EQUALS", "operand": { "targetName": "entitlementOwner.id", "targetValue": userId } }} var entitlements = openidm.action('iga/governance/resource/search', 'POST', targetFilter, {}); for(var entitlement of entitlements['result']){ var body = openidm.action('iga/governance/resource/' + entitlement.id + '/glossary', 'GET', {}, {}) body.entitlementOwner = "managed/user/" + replacementId; openidm.action('iga/governance/resource/' + entitlement.id + '/glossary', 'PUT', body, {}) } -
6 The Script node replaces the role owner.
Click to display the Role Owner Replacement script
/* Script nodes are used to invoke APIs or execute business logic. You can invoke governance APIs or IDM APIs. Learn more in https://docs.pingidentity.com/pingoneaic/identity-governance/administration/workflow-configure.html. Script nodes should return a single value and should have the logic enclosed in a try-catch block. Example: try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; } catch (e) { failureReason = 'Validation failed: Error reading request with id ' + requestId; } */ var content = execution.getVariables(); var userId = content.get('userId'); var replacementId = content.get('replacementId'); var targetFilter = {"targetFilter": { "operator": "EQUALS", "operand": { "targetName": "glossary.idx./role.roleOwner", "targetValue": "managed/user/"+ userId } }} var results = openidm.action('iga/governance/catalog/search', 'POST', targetFilter, {}); for(var result of results['result']){ var body = openidm.action('iga/governance/role/' + result.role.id + '/glossary', 'GET', {}, {}) body.roleOwner = "managed/user/" + replacementId; openidm.action('iga/governance/role/' + result.role.id + '/glossary', 'PUT', body, {}) } -
7 The Script node reassigns approvals.
Click to display the Reassign Approvals script
/* Script nodes are used to invoke APIs or execute business logic. You can invoke governance APIs or IDM APIs. Learn more in https://docs.pingidentity.com/pingoneaic/identity-governance/administration/workflow-configure.html. Script nodes should return a single value and should have the logic enclosed in a try-catch block. Example: try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; } catch (e) { failureReason = 'Validation failed: Error reading request with id ' + requestId; } */ var content = execution.getVariables(); var userId = content.get('userId'); var replacementId = content.get('replacementId'); var targetFilter = { "targetFilter": { "operator": "AND", "operand": [ { "operator": "EQUALS", "operand": { "targetName": "decision.actors.active.id", "targetValue": "managed/user/" + userId } }, { "operator": "EQUALS", "operand": { "targetName": "decision.status", "targetValue": "in-progress" } } ] } } var results = null var params = { "_pageSize": 100, "_pageNumber": 0 } do{ results= openidm.action('iga/governance/requests/search', 'POST', targetFilter, params); for(var result of results['result']){ var phaseName = null; var actors = []; for(var user of result.decision.actors.active){ if(user.id === "managed/user/"+ userId){ phaseName = user.phase; actors.push({"id": "managed/user/" + replacementId, "permissions": user.permissions}) } } for(var user of result.decision.actors.active){ if(user.phase === phaseName && user.id !== "managed/user/"+ userId){ actors.push({"id": user.id, "permissions": user.permissions}) } } var body = { "updatedActors": actors }; if(phaseName){ openidm.action('/iga/governance/requests/' + result.id + '/phases/' + phaseName + '/reassign', 'POST', body, {}) } } } while (results.result.length > 0) -
8 The Script node reassigns violations.
Click to display the Reassign Violations script
/* Script nodes are used to invoke APIs or execute business logic. You can invoke governance APIs or IDM APIs. Learn more in https://docs.pingidentity.com/pingoneaic/identity-governance/administration/workflow-configure.html. Script nodes should return a single value and should have the logic enclosed in a try-catch block. Example: try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); applicationId = requestObj.application.id; } catch (e) { failureReason = 'Validation failed: Error reading request with id ' + requestId; } */ logger.info('Script Task 3'); logger.info('User Task'); var content = execution.getVariables(); var userId = content.get('userId'); var replacementId = content.get('replacementId'); var targetFilter = { "targetFilter": { "operator": "AND", "operand": [ { "operator": "EQUALS", "operand": { "targetName": "decision.actors.active.id", "targetValue": "managed/user/" + userId } }, { "operator": "EQUALS", "operand": { "targetName": "decision.status", "targetValue": "in-progress" } } ] } } var results = null var params = { "_pageSize": 10, "_pageNumber": 0 } do{ results = openidm.action('iga/governance/violation/search', 'POST', targetFilter, params); if(results['result'].length > 0){ for(var result of results['result']){ var phaseName = null; var actors = []; for(var user of result.decision.actors.active){ if(user.id === "managed/user/"+ userId){ phaseName = user.phase; actors.push({"id": "managed/user/" + replacementId, "permissions": user.permissions}) } } for(var user of result.decision.actors.active){ if(user.phase === phaseName && user.id !== "managed/user/"+ userId){ actors.push({"id": user.id, "permissions": user.permissions}) } } var body = { "updatedActors": actors }; if(phaseName){ openidm.action('/iga/governance/violation/' + result.id + '/phases/' + phaseName + '/reassign', 'POST', body, {}) } } } } while(results.result.length > 0) -
9 The Script node completes the process and sets the ID of the user, replacing the inactive user.
Click to display the Complete Process script
// Insert logic to set ID of user who will be replacing inactive user logger.info("Completing request workflow."); var content = execution.getVariables(); var requestId = content.get('id'); // Read event user information from request object try { var requestObj = openidm.action('iga/governance/requests/' + requestId, 'GET', {}, {}); var decision = {'status': 'complete', 'decision': 'approved', 'outcome': 'fulfilled'}; var queryParams = { '_action': 'update'}; openidm.action('iga/governance/requests/' + requestId, 'POST', decision, queryParams); logger.info("Request " + requestId + " completed."); } catch(e) { logger.info("Error finalizing user inactive workflow") }
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
Workflow using custom request type and form
In this example, an administrator wants to create a custom request type called Create New User to add new employees or contractors
to the system. Administrators or form creators need to carry out the following tasks:
After these tasks, the approver receives the request and can start processing the approval.
Assumptions
-
Each application has an application owner. An application owner is a user identity designated to manage the application. You populate this value for each target application.
-
You have designated an end user or a test user who can approve the request.
-
You have configured notifications to the end user or test user to receive the emails.
Example
Task 1: Create a custom request type
The initial task is to create a custom request type, Create New User that lets an administrator add a new user to the system.
The Create New User request type has the following nonmodifiable properties:
-
userName. Username of the new user.
-
givenName. First name of the new user.
-
sn. Last name of the new user.
-
mail. Email address of the new user.
-
Create a custom request type called
createUserusing the API. Enter the following command using curl to create your custom request type:Details
curl --location 'http://<hostname>/iga/governance/requestTypes' \ --header 'Authorization: Bearer <access-token>' \ --header 'Content-Type: application/json' \ --data '{ "id": "createNewUser", "schemas": { "custom": [ { "_meta": { "type": "system", "displayName": "Create User", "properties": { "userName": { "isRequired": true, "isInternal": false, "isMultiValue": false, "display": { "name": "User Name", "isVisible": true, "order": 1, "description": "The userName of the new user" } }, "givenName": { "isRequired": true, "isInternal": false, "isMultiValue": false, "display": { "name": "First Name", "isVisible": true, "order": 2, "description": "The first name of the new user" } }, "sn": { "isRequired": true, "isInternal": false, "isMultiValue": false, "display": { "name": "Last Name", "isVisible": true, "order": 3, "description": "The last name of the new user" } }, "mail": { "isRequired": true, "isInternal": false, "isMultiValue": false, "display": { "name": "Email Address", "isVisible": true, "order": 4, "description": "The email address of the new user" } } } }, "properties": { "userName": { "type": "text" }, "givenName": { "type": "text" }, "sn": { "type": "text" }, "mail": { "type": "text" } } } ] }, "workflow": { "id": "createNewUser", "type": "bpmn" }, "validation": { "source": "var validation = {\"errors\" : [], \"comments\" : []}; if (request.custom.userName == undefined || request.custom.givenName == undefined || request.custom.sn == undefined || request.custom.mail == undefined) { validation.errors.push(\"Must include all of userName, givenName, sn, and mail fields.\");} validation;" }, "custom": true, "displayName": "Create User", "uniqueKeys": [ "custom.userName" ], "notModifiableProperties": [] }'
-
Task 2: Create a form for the custom request type
Using the admin console
-
In the Advanced Identity Cloud admin console, click Governance > Forms.
-
In the New Form modal, click Custom request form, and then click Next.
-
In the Custom request form modal, enter the following:
Field Description Form
Enter a descriptive name for your form.
Description (optional)
Enter a general description for your form.
Request Type (optional)
Select a custom request type from the list. In this example, select Create User.
You can only assign one form to each request type. Use this form for request creation
Click this option to make this form available to the end user when creating new requests of this request type. If unchecked, the request type only provides form field key suggestions during the form design process. For this example, leave this checkbox unchecked.
After you create your form, you can go back and make edits to any of the previous form settings by clicking the ellipsis() in the top right, and then click Settings.
-
Use the Forms editor to create a form for your custom request type. For example, drag-and-drop four text fields onto the canvas for the fields and label them:
User Name,E-mail address,First Name, andLast Name.-
On the Forms editor canvas, drag-and-drop the Text node to the canvas, and fill in the properties in the right pane for the
User Namefield:User name text field properties
Field Description Key
Enter the key for the text string. You can retrieve this key from the curl step under the
schemasentry. For example, entercustom.userNameas the key.Label
Enter a general label for this text field. For example, enter
User Name.Description
Enter help text for the text field. The description appears below your text field.
Required
Click if this text field is required. In this example, click Required.
Read Only
Click to make the field non-editable.
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. For this example, enter
6.Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. For this example, enter
0.Use validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
Regex
Enter a regular expression to validate the text field.
Error message
Enter an error message when the regular expression fails.
-
On the Forms editor canvas, drag-and-drop the Text node to the canvas, and fill in the properties in the right pane for the
E-mail addressfield:E-mail address text field properties
Field Description Key
Enter the key for the text string. You can retrieve this key from the curl step under the
schemasentry. For example, entercustom.mailas the key.Label
Enter a general label for this text field. For example, enter
E-mail address.Description
Enter help text for the text field. The description appears below your text field.
Required
Click if this text field is required. In this example, click Required.
Read Only
Click to make the field non-editable.
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. For this example, enter
6.Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. For this example, enter
0.Use Validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
Regex
Enter a regular expression to validate the text field.
Error message
Enter an error message when the regular expression fails.
-
On the Forms editor canvas, drag-and-drop the Text node to the canvas, and fill in the properties in the right pane for the
First Namefield:First name text field properties
Field Description Key
Enter the key for the text string. You can retrieve this key from the curl step under the
schemasentry. For example, entercustom.givenNameas the key.Label
Enter a general label for this text field. For example, enter
First Name.Description
Enter help text for the text field. The description appears below your text field.
Required
Click if this text field is required. In this example, click Required.
Read Only
Click to make the field non-editable.
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. For this example, enter
6.Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. For this example, enter
0.Use validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
Regex
Enter a regular expression to validate the text field.
Error message
Enter an error message when the regular expression fails.
-
On the Forms editor canvas, drag-and-drop the Text node to the canvas, and fill in the properties in the right pane for the
Last Namefield:Last name text field properties
Field Description Key
Enter the key for the text string. You can retrieve this key from the curl step under the
schemasentry. For example, entercustom.snas the key.Label
Enter a general label for this text field. For example, enter
Last Name.Description
Enter help text for the text field. The description appears below your text field.
Required
Click if this text field is required. In this example, click Required.
Read Only
Click to make the field non-editable.
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. For this example, enter
6.Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. For this example, enter
0.Use validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
Regex
Enter a regular expression to validate the text field.
Error message
Enter an error message when the regular expression fails.
-
-
Click Save.
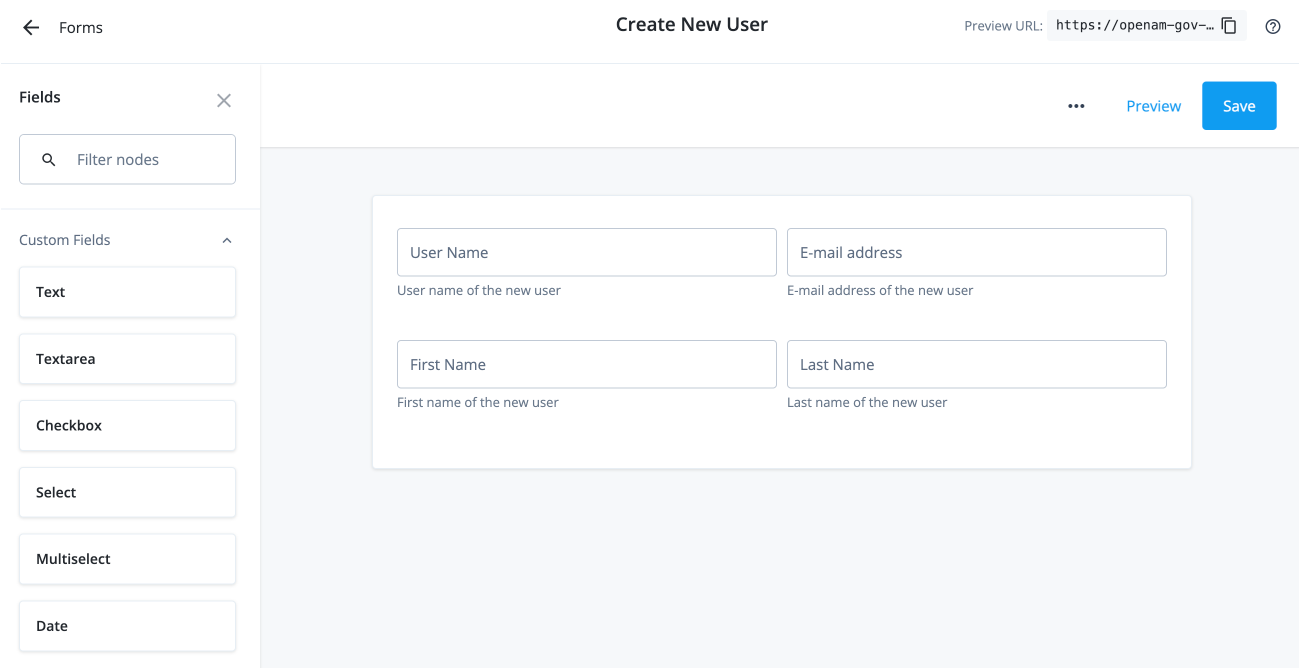
Using the API
-
Enter the following curl command to create your form for the custom request type:
Details
curl --location 'http://<hostname>/iga/governance/requestForms' \ --header 'Authorization: Bearer <access-token>' \ --header 'Content-Type: application/json' \ --data '{ "name": "Create New User", "type": "request", "description": "Form for creation of a new user", "categories": { "applicationType": null, "objectType": null, "operation": "create" }, "form": { "fields": [ { "id": "dd155b12-fb27-44e5-b4d6-476587b31a71", "model": "custom.userName", "type": "string", "label": "User Name", "description": "User name of the new user", "validation": { "required": true }, "layout": { "columns": 6, "offset": 0 } }, { "id": "88c73e69-86b1-453f-878b-527ceddeccf4", "model": "custom.mail", "type": "string", "label": "E-mail address", "description": "E-mail address of the new user", "validation": { "required": true }, "layout": { "columns": 6, "offset": 0 } }, { "id": "683892f9-2c13-41c7-a1cc-fcf38d7d0183", "model": "custom.givenName", "type": "string", "label": "First Name", "description": "First name of the new user", "validation": { "required": true }, "layout": { "columns": 6, "offset": 0 } }, { "id": "76fd5526-2ade-42a9-9b03-b6899e65aa31", "model": "custom.sn", "type": "string", "label": "Last Name", "description": "Last name of the new user", "validation": { "required": true }, "layout": { "columns": 6, "offset": 0 } } ] } }' -
Enter the following curl command to assign the form to the custom request type.
Details
curl --location 'http://<hostname>/iga/governance/requestFormAssignments?_action=assign' \ --header 'Authorization: Bearer <access-token>' \ --header 'Content-Type: application/json' \ --data '{ "formId": "b309b500-112c-4e6d-b832-a902f91362a3", "objectId": "requestType/createNewUser" }'
Task 3: Create a workflow to use the custom request type and form
Create a new workflow called Create New User to use the custom request type and form.
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
Task 4: Submit the custom request
You can enter a curl command to submit a Create New User request.
curl --location 'https://<hostname>/iga/governance/requests/createNewUser' \
--header 'Authorization: Bearer <access-token>' \
--header 'Content-Type: application/json' \
--data-raw '{
"custom": {
"userName": "acabby",
"givenName": "Amy",
"sn": "Cabby",
"mail": "amy.cabby@example.com"
}
}'Example Response
{
"id": "d289d1dd-b376-4860-a3d9-db3dd29702b2",
"requester": {
"givenName": "Joe",
"id": "managed/teammember/ce6ef368-c050-4131-bc07-32aa4f58a785",
"mail": "joe.admin@example.com",
"sn": "Admin",
"userName": "jadmin"
},
"requestType": "createNewUser",
"request": {
"custom": {
"userName": "acabby",
"givenName": "Amy",
"sn": "Cabby",
"mail": "amy.cabby@example.com"
},
"_rev": 1,
"common": {
"isDraft": false,
"context": {
"type": "request"
}
}
},
"decision": {
"status": "in-progress",
"decision": null,
"type": "request",
"outcome": null,
"startDate": "2024-09-09T15:53:49+00:00",
"completionDate": null,
"deadline": null,
"comments": [],
"actors": {
"active": [
{
"givenName": "Frank",
"id": "managed/teammember/ce6ef368-c050-4131-bc07-32aa4f58a785",
"mail": "frank.york@exampe.com",
"sn": "York",
"userName": "fyork",
"permissions": {
"approve": false,
"comment": true,
"modify": false,
"forward": false,
"reject": false,
"cancel": false,
"fulfill": false,
"deny": false
}
}
],
"inactive": [],
"actorTags": [
"activeId=managed%2Fteammember%2Fce6ef368-c050-4131-bc07-32aa4f58a785&phase=",
"phase=&activeId=managed%2Fteammember%2Fce6ef368-c050-4131-bc07-32aa4f58a785"
]
}
}
}Approver Task: Process the request
-
After the administrator submits the request, the approver (for example, "Frank York") receives a notification email.
-
The approver logs in to the Advanced Identity Cloud end-user UI and clicks Pending Approvals.
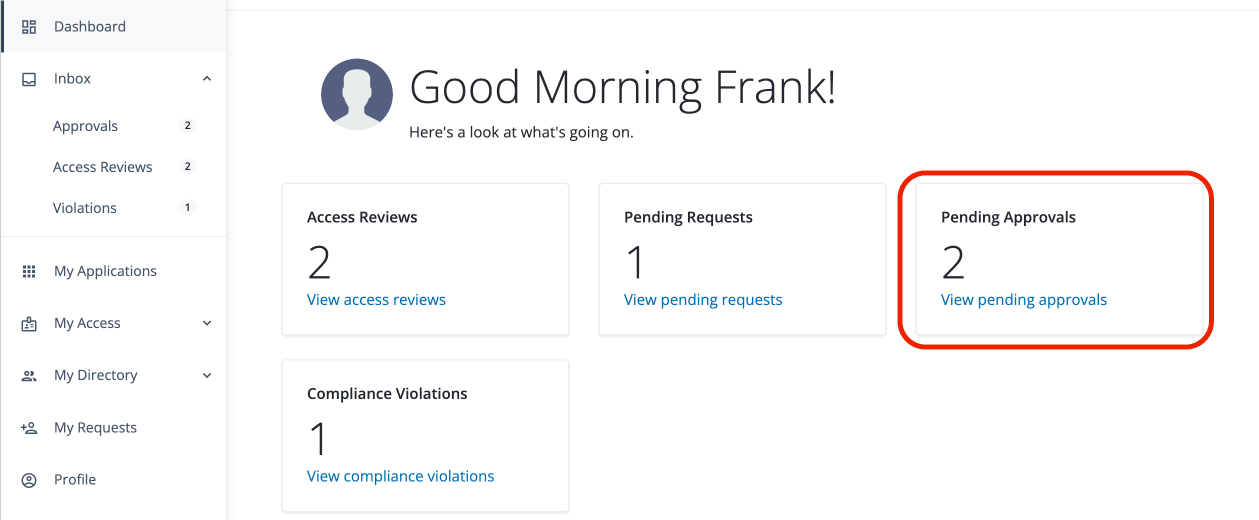
-
The approver can carry out different tasks: click Approve, Reject, or ellipsis () to Forward, Add Comment, or View Details.
-
The approver clicks View Details.
Workflow to create an Organization custom request type and form
In this example, an administrator wants to create a custom request type called Create Organization to add new organizations
to the system. Administrators and form creators need to carry out the following tasks:
After these tasks, the approver receives the request and can start reviewing it.
Assumptions
-
You have designated an end user who can function as an approver and review the request.
-
You have configured notification emails to alert the approver of incoming requests.
Example
Task 1: Create an organization request type
The initial task is to create a custom request type, Create Organization that lets an administrator add a new organization to the system.
-
Create a custom request type called
Create Organizationusing the API. Enter the following command using curl to create your custom request type:Details
curl --location 'http://<hostname>/iga/governance/requestTypes' \ --header 'Authorization: Bearer <access-token>' \ --header 'Content-Type: application/json' \ --data '{ "id": "createOrganization", "schemas": { "common": [ { "_meta": { "type": "system", "displayName": "commonRequest", "properties": { "justification": { "isRequired": false, "isInternal": true, "display": { "name": "Justification", "isVisible": true, "order": 3, "description": "The reason for the request" } }, "externalRequestId": { "isRequired": false, "isInternal": true, "isChangable": false, "display": { "name": "External Request ID", "isVisible": true, "order": 4, "description": "The external ID for the request" } }, "requestIdPrefix": { "isRequired": false, "isInternal": true, "display": { "name": "Request ID prefix", "isVisible": true, "order": 5, "description": "Prefix for the request ID" } }, "isDraft": { "isRequired": false, "isInternal": true }, "priority": { "isRequired": false, "display": { "name": "Priority", "isVisible": true, "order": 6, "description": "The priority of the reqeust" }, "text": { "defaultValue": "low" } }, "expiryDate": { "isRequired": false, "isInternal": true, "display": { "name": "Request expiration date", "isVisible": true, "order": 7, "description": "User provided date on which the request will cancel" } }, "context": { "isRequired": false, "isInternal": true, "isMultiValue": false, "display": { "name": "Context", "isVisible": true, "order": 1, "description": "The context of the request" } }, "workflowId": { "isRequired": false, "isInternal": true, "isChangable": false, "display": { "name": "BPMN workflow ID", "isVisible": true, "order": 7, "description": "The ID key of the BPMN workflow" } }, "blob": { "isRequired": false, "isInternal": true } } }, "properties": { "justification": { "type": "text" }, "externalRequestId": { "type": "text" }, "requestIdPrefix": { "type": "text" }, "isDraft": { "type": "boolean" }, "priority": { "type": "text" }, "expiryDate": { "type": "text" }, "context": { "type": "object" }, "workflowId": { "type": "text" }, "blob": { "type": "object" } } } ], "custom": [ { "_meta": { "type": "system", "displayName": "Create Organization", "properties": { "name": { "isRequired": true, "isInternal": false, "isMultiValue": false, "display": { "name": "Name", "isVisible": true, "order": 1, "description": "The name of the organization" } }, "description": { "isRequired": false, "isInternal": false, "isMultiValue": false, "display": { "name": "Description", "isVisible": true, "order": 2, "description": "The description of the organization being created" } }, "parent": { "isRequired": false, "isInternal": false, "isMultiValue": false, "display": { "name": "Parent Organization", "isVisible": true, "order": 3, "description": "The ID of the parent organization for this organization" } }, "admins": { "isRequired": false, "isInternal": false, "isMultiValue": true, "display": { "name": "Organization Administrators", "isVisible": true, "order": 4, "description": "The IDs of the users who will be this organization’s admins" } }, "includeSelfAdmin": { "isRequired": false, "isInternal": false, "isMultiValue": false, "display": { "name": "Include Self as Admin", "isVisible": true, "order": 4, "description": "If selected, include requester as an organization admin" } } } }, "properties": { "name": { "type": "text" }, "description": { "type": "text" }, "parent": { "type": "text" }, "admins": { "type": "text" }, "includeSelfAdmin": { "type": "boolean" } } } ] }, "workflow": { "id": "createOrganization", "type": "bpmn" }, "validation": { "source": "var validation = {\"errors\" : [], \"comments\" : []}; if (request.custom.name == undefined) { validation.errors.push(\"Must include all name field.\");} validation;" }, "custom": true, "displayName": "Create Organization", "uniqueKeys": [ "custom.name" ], "notModifiableProperties": [] }'
Task 2: Create a form for the organization request type
-
In the Advanced Identity Cloud admin console, click Governance > Forms.
-
In the New Form modal, click Custom request form, and then click Next.
-
In the Custom request form modal, enter the following:
Field Description Form
Enter a descriptive name for your form. In this example, enter:
Create Organization.Description (optional)
Enter a general description for your form. In this example, enter:
Form used to create a new organization.Request Type (optional)
Click and select a request type for the form. In this example, enter:
Create Organization.You can only assign one form to each request type. Use this form for request creation
Click this option to make this form available to the end user when creating new requests of this request type. If unchecked, the request type only provides form field key suggestions during the form design process. For this example, leave this checkbox unchecked.
After you create your form, you can go back and make edits to any of the previous form settings by clicking the ellipsis() in the top right, and then click Settings.
-
Use the Forms editor to create a form for your custom request type. For example, drag-and-drop five form fields onto the canvas for the fields and label them:
-
On the Forms editor canvas, drag-and-drop the Text node to the canvas, and fill in the properties in the right pane for the
Organization Namefield:Organization nametext field propertiesField Description Key
Enter the key for the text string. You can retrieve this key from the example in Task 1 under the
schemasentry. For example, entercustom.nameas the key.Label
Enter a general label for this text field. For example, enter
User Name.Description
Enter help text for the text field. The description appears below your text field. Enter
Name of the organization.Required
Click if this text field is required. In this example, click Required.
Read Only
Click to make the field non-editable. In this example, skip this step.
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. For this example, use the default (12 columns).
Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. For this example, use the default (
0).Use validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
-
On the Forms editor canvas, drag-and-drop the Textarea node to the canvas, and fill in the properties in the right pane for the
Descriptionfield:Descriptiontextarea field propertiesField Description Key
Enter the key for the text string. You can retrieve this key from the example in Task 1 under the
schemasentry. For example, entercustom.descriptionas the key.Label
Enter a general label for this text field. For example, enter
Description.Description
Enter help text for the text field. The description appears below your text field.
Required
Click if this text field is required. In this example, skip this step.
Read Only
Click to make the field non-editable. In this example, skip this step.
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. For this example, use the default (12 columns).
Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. For this example, use the default (
0).Use Validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
-
On the Forms editor canvas, drag-and-drop the Select node to the canvas, and fill in the properties in the right pane for the
Parent Organizationfield:Parent OrganizationSelect field propertiesField Description Key
Enter the key for the text string. You can retrieve this key from the example in Task 1 under the
schemasentry. For example, entercustom.parentas the key.Label
Enter a general label for this text field. For example, enter
Parent Organization (optional).Description
Enter help text for the text field. The description appears below your text field.
Required
Click if this text field is required. In this example, skip this step.
Read Only
Click to make the field non-editable. In this example, skip this step.
Options
Click one of the following to populate the Select field entries: Enumerated or Object.
-
Click Enumerated to manually set enumerated values in the Select field.
-
Click the icon.
-
In the Add Option modal, do the following:
-
Value: enter a value for the option field. For example, if you want to add a menu of administrators, go Identities > Manage. Search for an administrator to pull up their information. On the user’s page, click Raw JSON. Copy the user’s id, for example,
94080e61-f6a5-4bd0-bfc4-d26d6ae5c1b8and enter the ID into the Value field. -
Label: enter a label for the option field. Enter the user’s name, for example,
Cleo Patrascu. -
Click Selected by default to make the option a default enumerated value for the field.
-
Click Add.
-
Repeat the steps to add additional users.
-
-
Click Object to get a list of options taken from the API.
-
Select one of the following object types:
-
User
-
Role
-
Organization
-
Application
-
Entitlement
For example, if you want to create a
Parent Organizationselect field, select Organization. -
-
Click Save.
-
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. In this example, use the default (12).
Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. For this example, enter
0.Use validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
Regex
Enter a regular expression to validate the text field.
Error message
Enter an error message when the regular expression fails.
-
-
On the Forms editor canvas, drag-and-drop the Select node to the canvas, and fill in the properties in the right pane for the
Organization Adminsfield:Organization AdminsSelect field propertiesField Description Key
Enter the key for the text string. You can retrieve this key from the example in Task 1 under the
schemasentry. For example, entercustom.adminsas the key.Label
Enter a general label for this text field. For example, enter
Organization Admins (optional).Description
Enter help text for the text field. The description appears below your text field.
Required
Click if this text field is required. In this example, skip this step.
Read Only
Click to make the field non-editable. In this example, skip this step.
Options
Click one of the following to populate the Select field entries: Enumerated or Object.
-
Click Enumerated to manually set enumerated values in the Select field.
-
Click the icon.
-
In the Add Option modal, do the following:
-
Value: enter a value for the option field. For example, if you want to add a menu of administrators, go Identities > Manage. Search for an administrator to pull up their information. On the user’s page, click Raw JSON. Copy the user’s ID, for example,
94080e61-f6a5-4bd0-bfc4-d26d6ae5c1b8and enter the ID into the Value field. -
Label: enter a label for the option field. Enter the user’s name, for example,
Cleo Patrascu. -
Click Selected by default to make the option a default enumerated value for the field.
-
Click Add.
-
Repeat the steps to add additional users.
-
-
Click Object to get a list of options taken from the API.
-
Select one of the following object types:
-
User
-
Role
-
Organization
-
Application
-
Entitlement
For example, if you want to create a
Parent Organizationselect field, select Organization. -
-
Click Save.
-
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. In this example, use the default (12).
Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. In this example, use the default (0).
Use validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
-
-
On the Forms editor canvas, drag-and-drop the Checkbox node to the canvas, and fill in the properties in the right pane for the
Include yourself as administratorfield:Include yourself as administratorCheckbox field propertiesField Description Key
Enter the key for the text string. You can retrieve this key from the example in Task 1 under the
schemasentry. For example, entercustom.includeSelfAdminas the key.Label
Enter a general label for this text field. For example, enter
Include yourself as administrator.Description
Enter help text for the text field. The description appears below your text field.
Read Only
Click to make the field non-editable. In this example, skip this step.
Provide Default Value
Click Provide Default Value to assign a default value for this text field. In this example, skip this step.
Columns
Enter the number of columns for this text field. Values are from 1 to 12. In this example, use the default (12).
Offset
Enter the number of columns to offset from the left for this text field. Values are from 0 to 11. In this example, use the default (0).
Use validation
Click if you want to validate the text field using a regular expression. In this example, skip this step.
-
-
Click Preview to review your form.
-
Click Save.
Task 3: Create a workflow to use the organization request type and form
|
Download the JSON file for this workflow here. Learn more about how to import or export workflows in workflow editor canvas. |
Task 4: Submit the organization request
You can enter a curl command to submit a Create Organization request.
curl --location 'https://<hostname>/iga/governance/requests/createOrganization?_action=publish' \
--header 'Authorization: Bearer <access-token>' \
--header 'Content-Type: application/json' \
--data '{
"custom": {
"name": "IGA Organization",
"description": "Organization for all IGA members.",
"parent": "a27172ad-8adf-425e-a93f-ebd7c7aaa776",
"admins": [
"c51d9ee1-43b3-49d1-8742-cbb33842a5cc",
"e140e883-8ec7-4201-889d-f77ea118fcf3",
"adeb08c0-f3b7-44eb-a31a-a31fba305a40"
],
"includeSelfAdmin": false
},
"common": {
}
}'|
Currently, you must include the |
Workflow for entitlement grant with custom approvers
In this example, an administrator wants to create a basic entitlement grant workflow that uses a custom list of approvers in the Approval node.
Administrators need to carry out the following tasks:
Example
Task 1: Create a custom glossary property
The initial task is to create a custom entitlement glossary property, Approvers, that lets an administrator set a custom list of approvers.
-
In the Advanced Identity Cloud admin console, click Governance > Glossary.
-
Click Entitlement and then Entitlement Glossary Item.
-
In the Add Entitlement Glossary Item modal, enter the following, and click Save.
Field Description Name
Enter a label for the entitlement glossary item. For example,
approvers.Display Name
Enter a display name for the entitlement glossary item. For example,
Approvers.Description (optional)
Enter a general description for the glossary item.
Type
Select User.
Multi-Valued
Click Multi-Valued.
Enumerated Values
Leave disabled.
Task 2: Create a workflow with custom approvers
Create a new workflow called Basic Entitlement Grant Custom Approvers.
|
Download the JSON file for this workflow here. Learn more about importing or exporting workflows in workflow editor canvas. |
Basic entitlement grant temporal workflow
Identity Governance supports temporal workflows, which let you schedule when a user’s access begins and ends. For example, you can grant a contractor access to an application that starts on their first day and automatically ends when their contract expires.
To build these time-based workflows, you use the Wait node to pause the workflow until the specified start or end date has been established.
Administrators need to carry out the following task:
Example
Task: Create a workflow with the Wait node
Create a new workflow called Basic Entitlement Grant Temporal.
|
Download the JSON file for this workflow here. Learn more about importing or exporting workflows in workflow editor canvas. |
Request access to resources
After you configure access requests, end users can request access to resources (applications, entitlements, and roles) on the Advanced Identity Cloud end-user UI. An end user can request access to resources for themselves or for others. They can also request access to multiple resources in the same request.
Access request landing page
The access request landing page displays the access requests an end user submits for themselves and for others.
Learn how to Sign on as an end user.
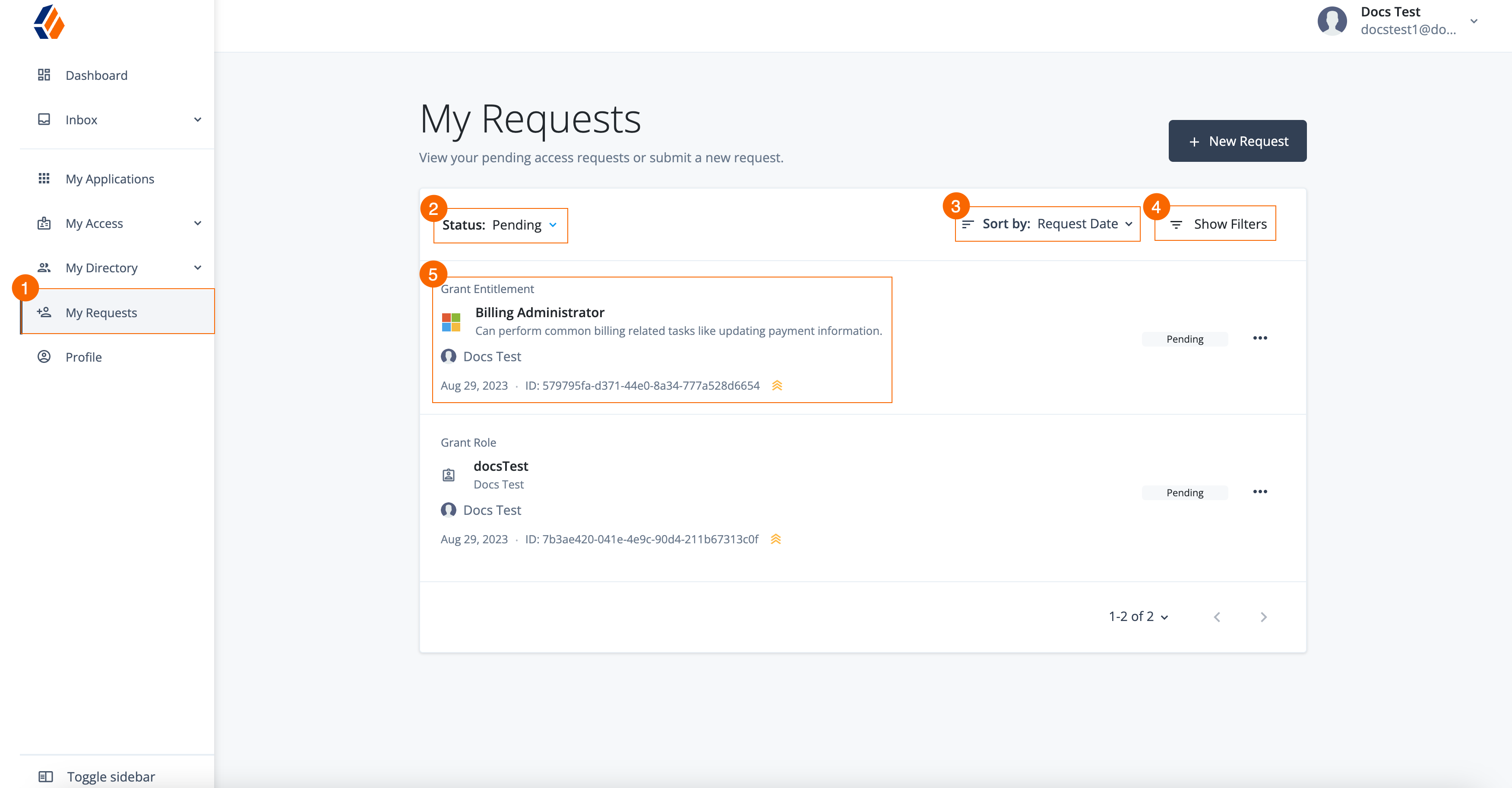
-
1 Click My Requests from the Advanced Identity Cloud end-user UI to display the access requests landing page.
-
2 Filter access requests by status:
-
Pending: The access request is pending approval by the approver(s).
-
Completed: The approver has either
ApprovedorRejectedthe request. Click a request to view the approver’s decision. -
Canceled: Requests that expire or you cancel.
-
-
3 Click Sort By and sort the request by an attribute in ascending or descending order.
-
4 Click Show Filters to filter by attributes or priority. An end user sets the priority when they create the request.
-
5 To view the details of a submitted request, click the request.
Create request
There are many options an end user can select when creating a request.
The following sections breakout the request process for readability purposes.
Start request
-
From the access request landing page, click New Request.
-
Select one of the following:
-
Myself: Create a request for yourself.
-
Other Users: Select up to 10 users to submit a request for.
-
-
Click Next.
A page to select resources displays.
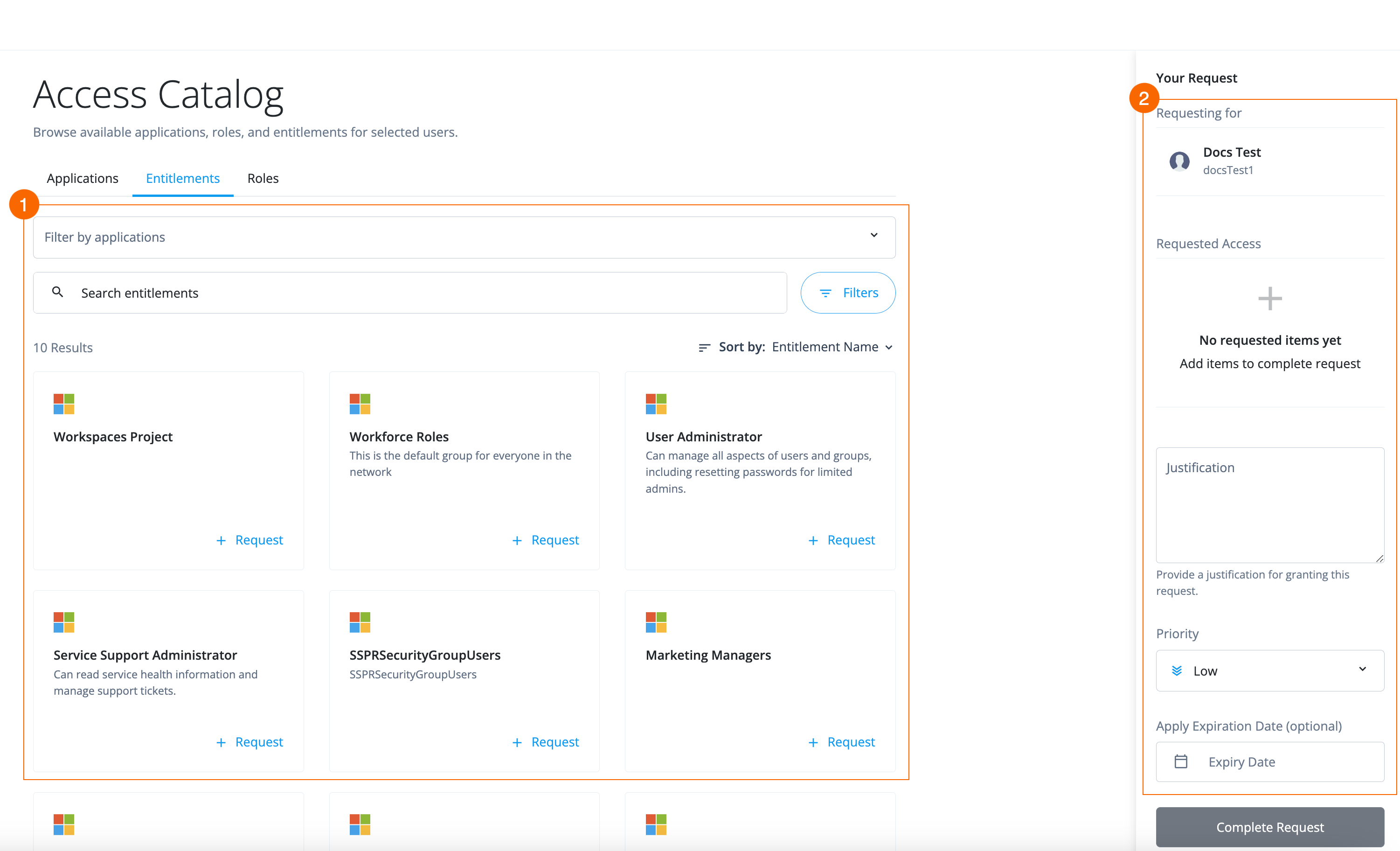
-
1 Search, sort, and select resources to add to the access request.
-
2 End users review current access and the resources they’ve selected, add a justification for the access, set a priority of the request, and optionally add an expiration date.
Select resources
End users can select a combination of up to 10 applications, entitlements, or roles in the same request.
There are three types of resources: applications, entitlements, and roles.
On each tab, an end user can:
-
Search for a resource in the search bar.
-
Filter on resources using attributes.
Learn more in create and configure glossary attributes.
-
Sort returned results by owner or resource name in ascending or descending order.
The following steps explore going through each resource tab to select which resources an end user wants. However, it isn’t necessary to click through each resource tab.
To select resources:
-
From the Applications tab, click Request next to each application to search for and select the desired applications.
If an end user selects a resource they already have access to or if the request is in a pending state, an error code is generated:
The following user(s) either already have the requested item assigned or in a pending request. Choose another item to request for the selected user(s).The message also appears if other users are submitting on behalf of the end user.
-
Click the Entitlements tab. Entitlements are specific privileges in applications.
-
Search for and select desired entitlements. To do this, click Request next to each entitlement.
Select applications in the Filter by application field to display entitlements that pertain to a specific application. -
Click the Roles tab.
-
Search for and select desired roles. To do this, click Request next to each role.
Enter request details and submit request
The request details pane is where an end user reviews the resources selected in the request and enters information, such as justification.
-
In the right pane, under Requesting for, click the user(s) name to view their current access.
-
Under Requested Access, review the resources selected.
-
Fill out the following fields:
-
Justification: Enter a reason for requesting access to the selected resources.
-
Priority: Select one of the following:
The priority levels bear no meaning in Identity Governance. Your company determines the value assigned to the request. -
Low
-
Medium
-
High
-
-
Apply Expiration Date: (Optional) Expire (cancel) the access request if it isn’t approved or rejected by the approver(s) by the specified date.
For example, an end user might need access to a resource by the end of the week, and if they don’t get the access by that time, then they don’t need the permission anymore.
-
Access Start Date: (Optional) Enter the date when you want the access to be granted.
-
Access End Date: (Optional) Enter the date when you want the access to be revoked.
Use access start date and access end date to control the duration for which the access is granted. After approval, access won’t be granted until the access start date and won’t be revoked until the access end date.
-
-
Click Complete Request. The end user is redirected to the access request landing page.
After the end user submits a request, a Request IDdisplays on each resource the end user requests access to. TheRequest IDtracks the request from the end user requesting access to the approver approving or rejecting access.
Request to remove access
Managers can remove access from their direct reports through a remove access request for accounts (applications), roles, and entitlements.
When a manager submits the remove access request, the approver(s) of the resource approve or reject the remove access request.
To submit a remove access request:
-
Sign on as an end user and navigate to My Directory > Direct Reports.
Learn more in direct reports.
-
Click any of the following tabs:
-
Accounts (applications)
-
Entitlements
-
Roles: For roles, if the Assignment column has the value of
rule-based, you can’t request to revoke the role. Rule-based indicates that the role is assigned to a user if a specified condition is met.
-
-
Click the ellipsis icon () next to the desired resource, and click Revoke.
-
Next, fill out the following fields:
-
Justification: Enter a reason for revoking access to the selected resources.
-
Priority: Select one of the following:
The priority levels don’t affect how Identity Governance processes requests. your company determines the value assigned to the request. -
Low
-
Medium
-
High
-
-
Apply Expiration Date: Optional. Expire (cancel) the remove access request if the approver(s) haven’t approved or rejected it by the specified date.
-
-
Click Submit Request.
Approve access
When an end user submits an access request, designated owners (approvers) must grant approval for the provisioning of resources.
The items on which approvers review and make decisions are referred to as request items.
Approvers review and make decisions on items referred to as request items in the Advanced Identity Cloud end-user UI.
For more information, learn more in Sign on as an end user and navigate to Inbox > Approvals.
Access request types
End users and managers can submit different access request types, such as removing and adding access requests.
The access request type breaks out the request items displayed to approvers.
The following table describes the access request types:
| Access request type | Description |
|---|---|
Grant Application |
End user requests access to an application. |
Remove Application |
End user’s manager requests to remove an application from an end user. |
Grant Role |
End user requests access to an Advanced Identity Cloud provisioning role. |
Remove Role |
End user’s manager requests to remove a role from an end user. |
Grant Entitlement |
End user requests access to an entitlement (an additional privilege inside an application). |
Remove Entitlement |
End user’s manager requests to remove an entitlement from an end user. |
|
The access request type is indicated at the top of each request item. 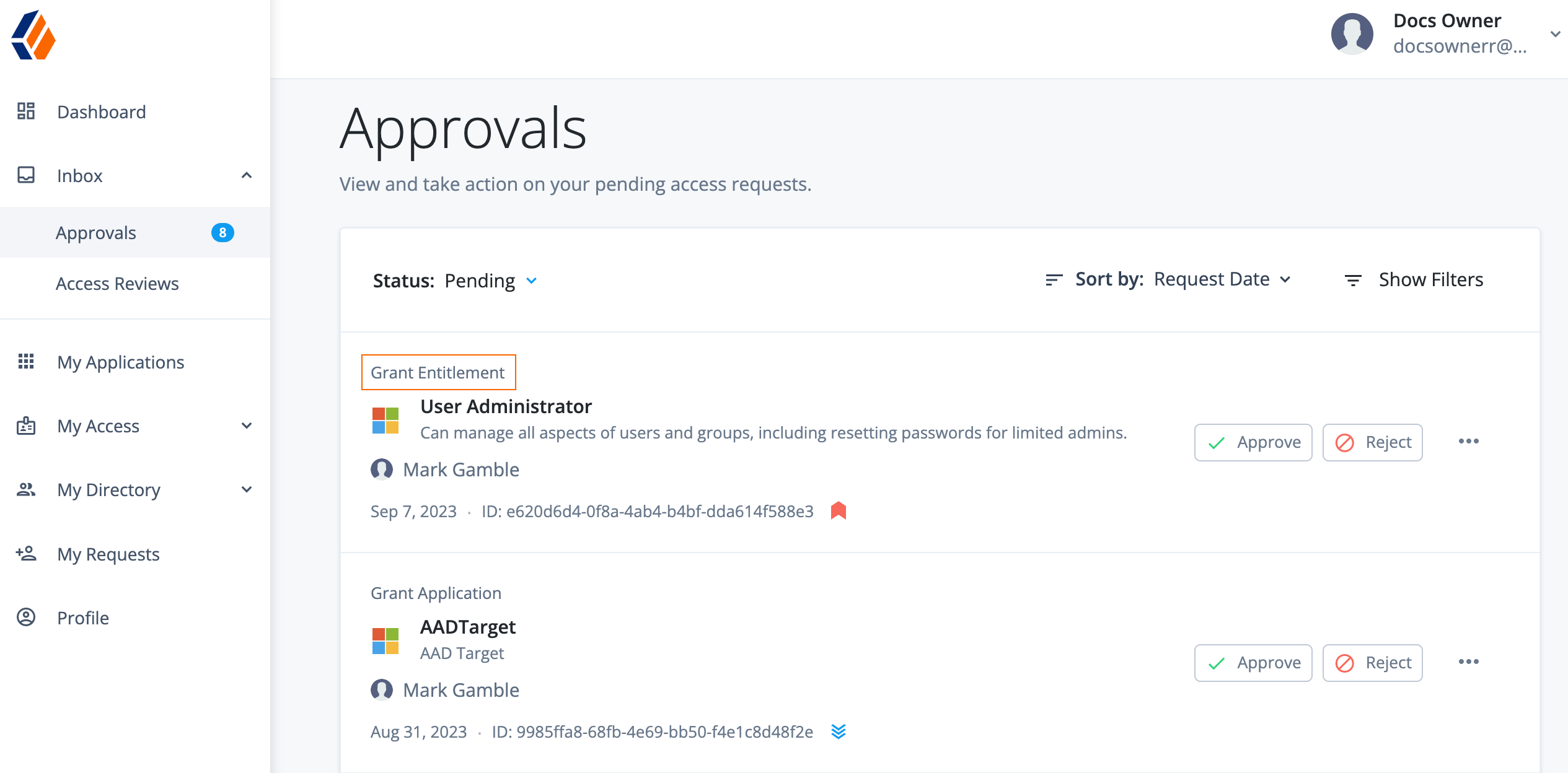
|
|
When end users enter an entitlement request, end users will see a warning message if the request results in a Segregation of Duties (SoD) violation.
End users can click View Details to review the entitlements on the Violations Found modal. The end user has the option to click Submit with Violation or Close the modal. |
Approve, reject, or forward a request item
The access request details of a request item include the requested resource(s), justification, and submission date.
Click a request item to view the details and take action, such as approve or reject.
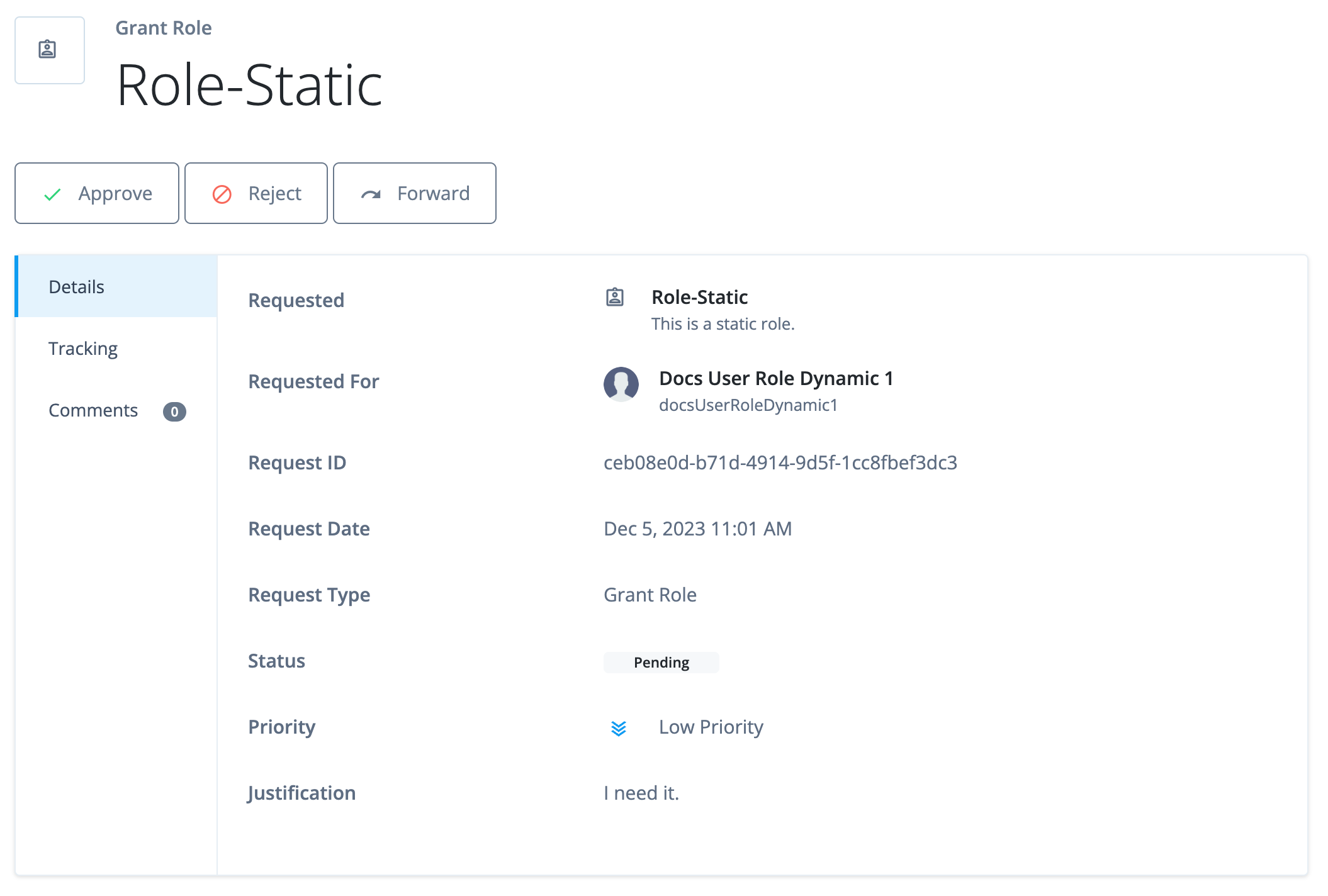
Approve item
-
Click the desired item to view the details.
-
(Optional) Add a comment to the request:
-
Click the Comments tab, then click Add Comment.
-
Enter a comment, and then click Add Comment to save it.
-
-
Click Approve.
-
Click Approve again to confirm the approval of the resource.
Identity Governance provisions the resource to the end user.
Reject item
-
Click the desired item to view the details.
-
(Optional) Add a comment to the request:
-
Click the Comments tab, then click Add Comment.
-
Enter a comment, and then click Add Comment.
-
-
Click Reject.
-
Enter a justification as to why the request is being rejected.
-
Click Reject.
Forward to another user or role
If the owner is unable to make a decision on their assigned access request due to insufficient information or other reasons, they can approve the request item request to one or more users assigned to a specific role.
To forward a request item to another user or role:
-
Click desired request to view the details.
-
Click Forward.
-
Select one of the following:
-
Another user: Forward the item to a single user.
-
Users with assigned role: Forward the item to users in a role.
Every user within the role can make a decision on the item. However, once a decision is reached, the assigned request item is considered complete.
-
-
Select the user or role to assign the item to.
-
Enter a comment as to why the item is being forwarded.
-
Click Forward.
Manage entitlements
In Identity Governance, an entitlement is a specific access right assigned to an account. An account is an identity profile in an onboarded application that maps to an identity in Advanced Identity Cloud within a target application and corresponds to a particular permission. It defines what a user can perform, such as viewing, modifying, or managing entitlements once they have access to the resource.
Identity Governance lets you act on entitlements, such as:
-
Discover and onboard entitlements
-
Grant entitlements including:
-
Using access requests
-
Using provisioning roles
-
Using direct assignment by administrators
-
-
Certify users who have been granted entitlements
-
Perform segregation of duties (SoD) checks to identity entitlement assignments that violate compliance policies.
-
Manage the entitlements lifecycles using Governance Workflows
Entitlements catalog
Identity Governance aggregates entitlements from onboarded target applications into a centralized repository called the entitlements catalog, providing a unified view of the entitlements.
The entitlement catalog gives you the ability:
Prepare the application for entitlements
Before your end users can work entitlements, tenant or governance administrators must prepare the application(s) for entitlements. Key tasks are:
|
For more details on provisioning applications, learn more in Provision an application. |
Load entitlements into Advanced Identity Cloud
When you onboard a target application into Advanced Identity Cloud, it also pulls in the application’s entitlements.
Each application’s account schema includes one or more attributes that define the account’s
privileges assigned to accounts within the target system. These attributes depend on other objects in the
application, known as non-account objects. Non-account objects represent entities linked to the user entity
in the target system. Examples of non-account objects are roles, groups, departments, permissions, and licenses.
For example, in a Salesforce application, the group object property is mapped to the GroupIds field
in the Advanced Identity Cloud user identity, which serve as the source for the account’s allowed entitlements.
Any changes to entitlements are later brought into the system through reconciliation, the process of comparing and synchronizing identity data between the IGA system and external target systems.
|
You must run entitlement reconciliations at regular intervals depending upon how frequently new entitlements are added to or deleted from the target application. |
Validate the entitlement configuration
After you have pulled in the entitlements into Advanced Identity Cloud, you see that most applications in the application catalog have predefined entitlement configurations. You must first validate the application configuration by:
-
Verifying that the account attribute has been correctly tagged as an entitlement based on your requirements.
-
Verify the account attribute is associated with the correct non-account object.
To validate the entitlement configuration and verify the account attribute:
-
In the Advanced Identity Cloud admin console, go to Applications > Browse App Catalog.
-
Select an application and click the Provisioning tab.
-
On the Details page, make sure you are viewing the
Userobject type. -
On the
Userobject page, click Properties. -
Select the account attribute containing the entitlements to be assigned to the account.
For most applications in the application catalog, the attribute is identified by a star.

-
Click > Edit to view or edit the property.
-
Verify that the application object type attribute has the correct non-account object specified and that the entitlement checkbox is selected. For example, the following image displays the
servicePlanIdsproperty:
There are some applications that require you to manually set the non-account object including:
-
Scripted REST
-
Scripted Groovy
-
Scripted Table
-
PowerShell
-
Multi-file CSV
-
SCIM
Learn more in Manually set non-account objects for an account object.
-
-
Click Data to preview the information, providing a real-time view of the target system data. You can scroll right to view the whole dataset.

Configure user-friendly display names
When you onboard entitlements into Advanced Identity Cloud, they can have highly cryptic or technical names that make its purpose difficult to ascertain. To ensure user-friendly names appear when displaying accounts or entitlements, configure the application object types accordingly.
-
In the Advanced Identity Cloud admin console, go to Applications > Browse App Catalog.
-
Select an application and click the Provisioning tab.
-
On the Details page, make sure you are viewing the
Userobject type. -
In the Display Name Attribute field, select a single-valued string attribute from the target application.
-
Click Save.
-
Repeat steps 1–5 for the other object types.
The following video shows an example:
Configuring the entitlement glossary
Administrators can enhance entitlements by adding meaningful business context, helping users understand their purpose and supporting Identity Governance in decision-making. This context is managed through the entitlement glossary, where administrators can add custom attributes in addition to the default ones.
Learn more in Managing the governance glossary.
Loading entitlements on-demand
Before running a reconciliation, make sure you have configured it to your requirements.
-
In the Advanced Identity Cloud admin console, go to Applications > Browse App Catalog.
-
Select an application and click the Provisioning tab.
-
On the Details page, make sure you are viewing the
Userobject type. -
Click Reconciliation > Reconcile.
-
Click Reconcile Now if you want to onboard the entitlements immediately.
The results of your reconciliation are displayed on the page. You can see the successful and unsuccessful matches.

View entitlements
When you load entitlements into Advanced Identity Cloud, they appear in the left navigation pane under the Governance > Entitlements tab.

There are three tabs that appear on the entitlements screen:
-
Details: Shows the entitlement owner, the end user who manages the entitlement as well as the entitlement glossary attributes.
-
Object Properties: Displays the entitlement data as it’s in the target application.
-
Users: Shows the Advanced Identity Cloud user and the corresponding user entity in the target application.

Manage governance glossary
In Identity Governance, you can use the governance glossary to attach custom attributes (metadata) to applications, entitlements, or roles to enhance certifications or access requests.
When using the governance glossary, you can create the following custom attributes:
Typical steps to make use of a governance glossary attribute
-
Create governance glossary attribute (application, entitlement, or role).
-
Populate the governance glossary attribute you create. For example, if you create an application glossary attribute, the attribute will appear on every target application in the Details tab.
-
Use the attribute you create to:
-
Filter on what you would like to certify when you create a template.
-
Allow the end user to filter on the attribute in applications, entitlements, or roles when they request access.
-
Example of when to use the governance glossary
| If you are already familiar with the use case(s) of governance glossary, start with Create a governance glossary attribute. |
There are many scenarios in which using identity glossary attributes can provide useful business logic to make decisions.
Oftentimes, organizations have specific attributes to track users' entitlements from applications.
An example could be that you want to attach a risk score to each entitlement pulled into Advanced Identity Cloud. This could be to determine the sensitivity of the entitlement (privilege) in the target application.
Steps:
-
From the Advanced Identity Cloud admin console, click Glossary.
-
Click Entitlement > + Entitlement Glossary Item.
-
Enter the following values:
-
Name -
riskScore -
Display Name -
Risk score -
Type -
NumberLearn more in create entitlement attribute.
-
-
Once you create the entitlement glossary attribute, it displays as metadata for each entitlement. To view this metadata in an entitlement, go to Entitlements > Select entitlement to view the attribute under the Details tab.
-
Assign a risk score of
80using the newly createdRisk scoreattribute. The higher the risk score for an entitlement, the more sensitive operations that entitlement allows.
Now that you have created an entitlement glossary attribute and enriched existing entitlements with
the Risk score attribute, you can leverage this new business-relevant data.
For example, you can create an entitlement assignment certification template that filters
the template to show entitlements to review that have a Risk score of 75 or higher. This allows you to
certify highly-sensitive entitlements.
This is just one scenario in which the identity glossary can be used. Create identity glossary attributes for applications, entitlements, or roles to suit your business cases.
Create a governance glossary attribute
To access the governance glossary, navigate to Glossary from the left navigation pane in the Advanced Identity Cloud admin console.
Create governance glossary attributes for:
Create an application glossary attribute
To create an application glossary attribute:
-
Select Application from the left pane in the table.
-
Select Application Glossary Item.
-
Enter details for the item:
Field Description Name
The backend name of the attribute.
Display Name
The name that displays on the Details tab of the target application.
Description
The rationale for the attribute.
Type
The data type of the attribute. The data type you select changes the way it displays in the application’s Details tab and the actions you can take.
Select one of the following:
-
String
-
Number
-
Boolean: A checkbox. Checking the box corresponds to
true. -
Date: A date field (
mm/dd/yyyy). -
User: Select from existing users.
-
Role: Select from existing roles.
-
Organization: Select from existing organizations.
-
-
Depending on the data type chosen, optional settings appear:
-
Multi-Valued: Lets you have more than one value when you populate the attribute, an array. For example, if you select the
Usertype in step 3, you can select multiple users instead of one. -
Enumerated Values: When you are populating the attribute on the application, create fixed values to choose from:
-
Select the icon.
-
Fill out the text and value for the item.
The text displays as the human-readable option to select. The value is the actual value saved to the backend.
-
If desired, add more values.
-
-
-
Click Show advanced settings and optionally select Searchable. This allows an end user to search using this attribute when requesting access to the application.
-
Click Save.
The application glossary attribute displays in the Details tab of every target application.
The following video shows an example:
Create an entitlement glossary attribute
To create an entitlement glossary attribute:
-
Select Entitlement from the left pane in the table.
-
Select Entitlement Glossary Item.
-
Enter details for the item:
Field Description Name
The backend name of the attribute.
Display Name
The name that displays on the Details tab of each entitlement.
Description
The rationale for the attribute.
Type
The data type of the attribute. The data type you select changes the way it displays each entitlement and the actions you can take.
Select one of the following:
-
String
-
Number
-
Boolean: A checkbox. Checking the box corresponds to
true. -
Date: A date field (
mm/dd/yyyy). -
User: Select from existing users.
-
Role: Select from existing roles.
-
Organization: Select from existing organizations.
-
-
Depending on the data type chosen, optional settings appear:
-
Multi-Valued: Lets you have more than one value when you populate the attribute, an array. For example, if you select the
Usertype in step 3, you can select multiple users instead of one. -
Enumerated Values: When you are populating the attribute on the entitlement, create fixed values to choose from:
-
Select the icon.
-
Fill out the text and value for the item.
The text displays as the human-readable option to select. The value is the actual value saved to the backend.
-
If desired, add more values.
-
-
-
Click Show advanced settings and optionally select Searchable. This allows an end user to search using this attribute when requesting access to the entitlement.
-
Click Save.
The entitlement glossary attribute displays in every onboarded entitlement. From the Advanced Identity Cloud admin console, go to Entitlements > Select entitlement > Details tab to view the newly created entitlement attribute.
The following video shows an example:
Create role glossary attribute
To create a role glossary attribute:
-
Select Role from the left pane in the table.
-
Select Role Glossary Item.
-
Enter details for the item:
Field Description Name
The backend name of the attribute.
Display Name
The name that displays on the Details tab of each role.
Description
The rationale for the attribute.
Type
The data type of the attribute. The data type you select changes the way it displays each role and the actions you can take.
Select one of the following:
-
String
-
Number
-
Boolean: A checkbox. Selecting the box corresponds to
true. -
Date: A date field (
mm/dd/yyyy). -
User: Select from existing users.
-
Role: Select from existing roles.
-
Organization: Select from existing organizations.
-
-
Depending on the data type chosen, optional settings appear:
-
Multi-Valued: Lets you have more than one value when you populate the attribute, an array. For example, if you select the
Usertype in step 3, you can select multiple users instead of one. -
Enumerated Values: When you are populating the attribute on the role, create fixed values to choose from:
-
Select the icon.
-
Fill out the text and value for the item.
The text displays as the human-readable option to select. The value is the actual value saved to the backend.
-
If desired, add more values.
-
-
-
Click Show advanced settings and select any of the following:
-
Click Show advanced settings and optionally select Searchable. This allows an end user to search using this attribute when requesting access to the entitlement.
-
Click Save.
The role glossary attribute displays in every role. From the Advanced Identity Cloud admin console, go to Manage > Identities > Select role > Details tab to view the newly created role attribute.
The following video shows an example:
Delete a governance glossary attribute
To delete a governance glossary attribute:
-
From the Advanced Identity Cloud admin console, click Glossary.
-
Select one of the following tabs:
-
Application
-
Entitlement
-
Role
-
-
Click ellipsis () next to the governance glossary attribute you want to delete.
-
Click Delete.
-
Click Delete again to confirm the deletion.
This action can’t be undone.
Identity Governance REST API reference
This section describes the endpoints and specific characteristics of Identity Governance REST APIs. You can find an overview of the Ping Identity REST API framework in Advanced Identity Cloud REST.
| Access Identity Governance REST APIs using access tokens. You can find information on obtaining a token in Authenticate to Advanced Identity Cloud REST API with access token. |
-
PingOne Identity Governance API reference: Identity Governance has many features, including access requests, the governance glossary (catalog), and entitlements. This page explores the Identity Governance REST API endpoints.
Identity Governance-related APIs
Identity Governance has many features, including access requests, the governance glossary (catalog), and entitlements.
The following sections comprehensively explore the Identity Governance REST API endpoints.
YAML file
The REST APIs contain many parameters and, in some instances, large request bodies. For your convenience, you can view the entire API using a YAML file based on the OpenAPI specification.
To download the YAML file, click here.
Learn more in the API reference documentation.
| Adjust the configurations of the file to match your specific details, such as your Advanced Identity Cloud tenant FQDN. |
Access token
You need to obtain an access token to authenticate to the Advanced Identity Cloud REST API. Learn more about obtaining an access token in Authenticate to Advanced Identity Cloud REST API with access token.
After you obtain an access token, you can access the Identity Governance API using
the specific HTTP methods: GET, POST, PUT, PATCH, and DELETE.
You can use client command-line tools, such as
cURL or API platforms, such as Postman to
transfer data to and from the IGA server.
For example, using cURL:
curl \
--request GET \
--header 'Authorization: Bearer <access token>' \
"https://<tenant-env-fqdn>/iga/governance/application?_pageSize=10&_queryFilter=true"Show example response
{
"result": [
{
"application": {
"authoritative": false,
"connectorId": "AzureAD",
"description": "AzureAD application",
...
"name": "AzureAD",
"templateName": "azure.ad",
"templateVersion": "2.0",
"objectTypes": [
{
"name": "__ACCOUNT__"
},
{
"name": "__GROUP__",
"accountAttribute": "memberOf"
}
]
},
...
}
],
"searchAfterKey": "string",
"resultCount": 0,
"totalCount": 0
}Endpoints
The following sections present the Identity Governance endpoints.
|
The output and examples presented in this section are based on a test dataset and are not real data. |
Application
| URI | HTTP method |
Description | ||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Query Identity Governance applications. This endpoint is subject to the end user’s scoped permissions. Parameters
Responses
Click for an example to get a list of applicationsMedia type: |
||||||||||||||||||||||||
|
GET |
Returns the schema of a given application’s object type. This endpoint helps identify the required payload structure for the request endpoint. It’s for the object key that holds the entitlement details. The UI also uses the endpoint to generate forms for creating and modifying entitlements. Parameters
Responses
Click for an example to get the object type schemaMedia type: |
Certification
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Query existing certification templates. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
POST |
Create a new certification template. ParametersNo parameters Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
POST |
Duplicate an existing certification template. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
PUT |
Updates a single certification template. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
DELETE |
Deletes a single certification template at the requested ID in the path.
Parameters
Responses
Click for an example responseMedia type: |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
POST |
Get the available schema on which to filter certification templates. Returns a collection of schema properties that are available to populate the certification templates target filter property, including properties of application, user, entitlement, role, and other objects. ParametersNo parameters Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
GET |
Query existing certification instances. Returns certificate campaigns based on query parameter. Parameters
Responses
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
GET |
Returns a certification campaign based on the provided campaign ID. Parameters
Responses
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
GET |
Returns the tasks assigned to different certifiers for a specific certification campaign. Parameters
Responses
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
POST |
Updates a certification’s deadline. Parameters
Request body exampleMedia type: Responses
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
POST |
Cancels a certification campaign at the requested ID in the path. This only cancels existing in-progress action items. It won’t revert any decisions that have been signed off and acted on. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
GET |
Query the review items (tasks) that are assigned to you. Returns the certification tasks currently assigned to the signed-on end user. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
GET |
Returns the certification line items that belong to this campaign, filtered by parameters. Certifier sign-off is indicated by status. The certifier’s decision is indicated by decision. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
POST |
Returns the certification line items that belong to the specified campaign, filtered by parameters. Parameters
Request body exampleMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
POST |
Take action on line items. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
POST |
Take action on a single line item. Parameters
Request body * requiredExample: Responses
Click for an example responseMedia type: |
Access request
In Identity Governance, end users can request access to resources. Resources are target applications, entitlements, or roles. You define which resources are requestable.
Learn more in access requests.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
POST |
Create or validate a new access request for a list of users. When you submit a new request for access, the system validates the request’s contents. If no issues are found, IGA creates a request for each pairing of user and catalog items included in the request. You can choose to only validate the request by using the Parameters
Request body exampleMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Create request for the given request type. Parameters
Request body * requiredPayload for creating the request. Properties must match the request type schema definition.
Media type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Retrieve the details of a single access request using a unique identifier, Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PUT |
Replace the content of a request. You can change only the properties
that are defined in the request schema and not in the Parameters
Request body * requiredThe payload for replacing request content. Properties must match the request type schema definition of this request.
Media type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PATCH |
Update the contents of a request. You can update only properties
that are defined in the request schema and not in the Parameters
Request body * requiredPayload for updating the request.
Media type: Responses
Click for an exampleMedia type: |
||||||||||||||||||||||||||||
|
POST |
Perform various actions on a specific request, such as Parameters
Request bodyExample: Responses
|
||||||||||||||||||||||||||||
|
GET |
Get requests for which the authenticated user has permissions to view. For additional search capabilities,
use the Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Get requests for which the authenticated user is assigned, either directly, through a role, or
through a delegate. You can use the Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
Access request form
Identity Governance enables administrators to create custom forms for users during request workflows.
| URI | HTTP method |
Description | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Search request forms. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||
|
POST |
Create a request form. ParametersNo parameters Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||
|
GET |
Get a request form by ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||
|
PUT |
Replace an existing request form by ID. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||
|
PATCH |
Update an existing request form by ID. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||
|
GET |
Search the request form assignments. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||
|
POST |
Assign and unassign a request form. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
Access request type
| URI | HTTP method |
Description | ||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Get a list of supported request types. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||
|
POST |
Create a new custom request type. ParametersNo parameters Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||
|
GET |
Get a request type by ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||
|
PUT |
Replace an existing request type. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||
|
PATCH |
Update an existing request type. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||
|
DELETE |
Delete a request type. Parameters
Responses
|
Account
Accounts are user profiles in applications. For example, when you provision an end user to an application, the system creates an account for them.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Retrieve all account objects across all applications that have been onboarded as part of any application. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
POST |
Retrieve all account objects across all applications that have been onboarded as part of any application. You can provide additional filter criteria to search by application, user, or glossary data. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
GET |
Retrieve by details of a single account object using its unique identifier. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
GET |
Retrieve the glossary-specific details of a single account object using its unique identifier. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
POST |
Create glossary entry for a single account object using its unique identifier. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
PUT |
Create or update a glossary entry for a single account object using its unique identifier. Parameters
Responses
Click for an example responseMedia type: |
Audit
Endpoints associated with IDM’s audit functionality.
|
To use the
This is a temporary requirement and will be removed in a future release. |
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Get audit reports. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||||||
|
GET |
Get the audit reports for a given user. Parameters
Responses
Click for an example responseendDate string (query) Last date to include in the report |
Catalog
The Catalog endpoint provides a list of requestable access items. The supported
types of requestable access are application, entitlement, and role.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Get a list of items from the Identity Governance access catalog. Each entry represents a single
type of requestable access that can be added to a request. The supported types
of requestable access are Parameters
Responses
Click for an example responseExample: |
||||||||||||||||||||||||||
|
POST |
Get a list of items from the Identity Governance access catalog using additional filter criteria.
Each entry represents a single type of requestable access that can be added to a request.
The supported types of requestable access are Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
GET |
Retrieve all configured properties eligible to be used for search or sort when searching against the catalog API. Each property includes additional metadata about the property, such as its datatype and whether it’s multivalued. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
GET |
Retrieve all configured properties eligible for search or sort for a single object when searching against the catalog API. For example, you can use the endpoint to search for all specific entitlement properties. Each property includes additional metadata about the property, such as whether it is multivalued or not and its datatype. Parameters
Responses
Click for an example responseMedia type: |
Config
Identity Governance has overarching configurations, such as requiring a justification when rejecting an access request.
| URI | HTTP method |
Description | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Reads and returns all Identity Governance configuration properties across all categories. Only access request-related properties are available. For example, access request features contain configuration on whether justification is required to reject a request or whether a user can approve their own access. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||
|
PUT |
Update all Identity Governance configuration properties across all categories. Only access request-related properties are available.
Parameters
Request bodyMedia type: Responses
Click for an example response |
||||||||||||||
|
GET |
Get Identity Governance configuration settings for a given category (for example, Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||
|
PUT |
Update Identity Governance configuration settings for a given category (for example, Parameters
Request bodyExample: Responses
Click for an example responseMedia type: |
Entitlement
All users can access the query entitlements endpoint, but the system filters the results they see based on their granted authorizations.
For example, administrators can see all entitlements. An application owner can see all entitlements that belong to their applications but not other applications' entitlements. An entitlement owner of three entitlements can see the entitlements that they own. A user who has been scoped permissions to view or act on a subset of entitlements can access that subset.
This endpoint also supports all standard pagination and query filtering abilities of other search APIs.
|
Every entitlement object in Identity Governance now includes an additional property at the |
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Search for all entitlements provided by the query parameters. Parameters
Responses
Click for an example to query entitlementsMedia type:
|
||||||||||||||||||||||||||||
|
POST |
Create a new entitlement. Users can submit a request using the
This endpoint creates the entitlement in the target system, creates the associated entry (if required), and ensures the entitlement is available in Identity Governance. Parameters
Request bodyExample: Responses
Click for an example to submit a Create entitlement requestMedia type:
|
||||||||||||||||||||||||||||
|
GET |
Return a single entitlement object by ID.
Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PUT |
Modify an existing entitlement. Users can submit a request using the
Parameters
Request bodyMedia type: Responses
Click for an example to submit a Modify entitlement requestMedia type:
Click for an example to modify an entitlement directlyMedia type: |
||||||||||||||||||||||||||||
|
GET |
Returns the entitlement grants for the given entitlement ID. Users who have the permissions can view the users who are currently granted a given entitlement. Administrators, application owners, and entitlement owners are granted this privilege implicitly. You can also scope additional end users to have this permission. Parameters
Responses
Click for an example to view grantsMedia type: |
||||||||||||||||||||||||||||
|
GET |
Get an entitlement’s glossary metadata by ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Create a glossary entry for a single entitlement using its unique identifier. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PUT |
Create or update a glossary entry for a single entitlement using its unique identifier. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
DELETE |
Delete a glossary entry for a single entitlement using its unique identifier. Parameters
Responses
Click for an example responseMedia type: |
Event
Events are rules defined to detect a change in the IGA system. Each rule has two core parts: a condition for the event and the action taken when that event occurs. For example, a rule might define that whenever someone creates a user in IGA, they should also generate a certification for that user.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Get and search for a list of event rules defined in IGA. Each entry represents a single event rule defined to detect a change in the system. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Create a single IGA event rule. A single event rule is defined to detect a change in the system. Parameters
Request bodyExample: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Get a single IGA event by ID. The response is a single event rule defined to detect a change in the system. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PUT |
Update a single IGA event by ID. This call requires that you provide the entire object and that it replaces the entire existing event definition. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PATCH |
Update a single IGA event by ID. This call allows the caller to update specific properties of the event only without providing the entire object. Parameters
Request bodyExample: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
DELETE |
Delete a single IGA event by ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Get the list of available event entities from which you can define a condition. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Get the available schema for defining a condition on a given object.
For example, Parameters
Responses
Click for an example responseMedia type: |
Job
You can trigger a governance job.
| URI | HTTP method |
Description | ||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
POST |
Trigger a governance job by ID. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
Provisioning
In the Advanced Identity Cloud admin console, you can add or remove, or provision, resources from end users. You can do the same through REST APIs.
| URI | HTTP method |
Description | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
POST |
Provision or de-provision applications for an end user. Parameters
Request body exampleMedia type: Responses
Click for an example responseMedia type: |
||||||||||||
|
POST |
Provision or de-provision roles for an end user. Parameters
Request body exampleMedia type: Responses
Click for an example responseMedia type: |
||||||||||||
|
POST |
Provision or de-provision entitlements for an end user. Parameters
Request body exampleMedia type: Responses
Click for an example responseMedia type: |
Roles
Roles define privileges for identities. Use the following endpoints to create, view, and manage governance roles.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Query governance roles based on multiple query parameters. Parameters
Responses
|
||||||||||||||||||||||||||||||
|
POST |
Create a new draft of a governance role. Request bodyMedia type: Responses
|
||||||||||||||||||||||||||||||
|
GET |
Get a specific governance role object by ID and status. Parameters
Responses
|
||||||||||||||||||||||||||||||
|
PUT |
Update a role’s contents. Provide the full contents to replace the existing contents. Parameters
Request bodyMedia type: Responses
|
||||||||||||||||||||||||||||||
|
PATCH |
Publish a governance role. Parameters
Request bodyMedia type: Responses
|
||||||||||||||||||||||||||||||
|
DELETE |
Delete an existing governance role. Parameters
Responses
|
||||||||||||||||||||||||||||||
|
GET |
Get role member information. Returns user details for members associated with a role by user features and added members. Parameters
Responses
|
||||||||||||||||||||||||||||||
|
GET |
Get entitlement information. Returns the entitlement details for entitlements associated with a role. Parameters
Responses
|
||||||||||||||||||||||||||||||
|
GET |
Get role member information. Returns user details for members associated with a role by user features and added members. Parameters
Responses
|
||||||||||||||||||||||||||||||
|
GET |
Get entitlement information. Returns the entitlement details for entitlements associated with a role. Parameters
Responses
|
||||||||||||||||||||||||||||||
|
GET |
Get the metadata for a governance role’s glossary entry. Returns the key-value pairs for all the metadata on a role’s glossary entry. Parameters
Responses
|
||||||||||||||||||||||||||||||
|
POST |
Create a glossary entry for a governance role. Parameters
Request body * requiredThe contents of the new glossary entry, key-value pairs. Media type: Responses
|
||||||||||||||||||||||||||||||
|
PUT |
Update the glossary data for a governance role. Parameters
Request body * requiredThe contents of the updated glossary entry, key-value pairs. Media type: Responses
|
||||||||||||||||||||||||||||||
|
DELETE |
Delete the metadata for a governance role’s glossary entry. Parameters
Responses
|
Scope
Scope determines which specific users can view or interact with particular target objects. Scoping rules have two core parts: a condition for the source object (who or what the scope applies to) and a condition for the target object that can be viewed or acted upon.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Get and search for a list of scoping rules defined in IGA. Each entry represents a single scoping rule defined to assign conditions that allow a subset of users visibility on a subset of target objects. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
POST |
Create a single scoping rule in IGA. Each scoping rule is defined to assign conditions that allow a subset of users visibility on a subset of target objects. IGA scoping rules consist of two core parts: a condition for the source object (who/what the scope applies to) and a condition for the target object that can be viewed or acted upon. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
GET |
Get a single scoping rule in IGA by ID. Each scoping rule is defined to assign conditions that allow a subset of users visibility on a subset of target objects. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
PUT |
Update a single IGA scope by ID. This call expects the entire object to be provided and replaces the entire existing scope definition. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
PATCH |
Update a single IGA scope by ID. This call allows the caller to update specific properties of the scope only without providing the entire object. Parameters
Request bodyExample: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
DELETE |
Delete a single IGA scope by ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
GET |
Get a list of available entities on which you can define a condition. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||
|
GET |
Get the available schema to define a condition on a given object. For example, 'user' returns the attributes available for defining a scope for users in IGA. Parameters
Responses
Click for an example responseMedia type: |
Segregation of Duty
Segregation of Duties (SoD) is an internal control process that ensures no single individual has privileges that could lead to a conflict of interest or fraud. Administrators can configure SoD using policies and policy rules that let them identify violations and run actions, such as create an exception, allow or remediate the violation, and others.
You can view the entire API using a YAML file based on the OpenAPI specification.
| Adjust the configurations of the file to match your specific details, such as your Advanced Identity Cloud tenant FQDN. |
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Search policies. The endpoint returns policies stored within the Identity Governance store, based on multiple query parameters. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Create a new policy object within Identity Governance. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Query policy objects using a targeted search filter. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Get policy by ID. The endpoint returns the policy with the provided ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PUT |
Update an existing policy object within Identity Governance. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
DELETE |
Delete an existing policy object within Identity Governance. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Run a scan on all given rules of a policy and create violations if desired. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Get policy rules associated with a policy ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Query policy rules based on multiple query parameters. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Create a new policy rule object within Identity Governance. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Query the policy rule objects using a targeted search filter. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Get policy rule by ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Duplicate a given policy rule. The rule will be set as Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PUT |
Update an existing policy rule object. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
DELETE |
Delete an existing policy rule. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Run a scan the given policy for violations and create violations if desired. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Run a scan on a given user rule and return potential violations. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Query policy scans with the Identity Governance store based on multiple query parameters. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Query policy scan objects using a targeted search filter. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Get policy scan by ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
DELETE |
Delete an existing policy scan object within Identity Governance. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Query the signed-in user’s violation objects. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
GET |
Query the violation objects. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Creates a violation with the given body. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Once a phase (or phases) have chosen to allow a violation, close and complete the
violations with the outcome of Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As a user who can take action on violations, cancel existing exceptions, reverting the violations to in-progress. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As a user who can take action on violations, add a comment to the violation objects. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As a user who can take action on violations, grant an exception to the violating access. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As a user who can take action on violations, edit the list of active actors on the violation tasks. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Query the violation objects using a targeted search filter. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Query the signed-in user’s violation object using a targeted search filter. Parameters
Request body! Responses
Click for an example responseMedia type: `application/json`å |
||||||||||||||||||||||||||||
|
GET |
Query the contents of a single violation object. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
PUT |
Updates a given violation with the given body. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
DELETE |
Deletes a violation with a given ID. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Once a phase (or phases) have chosen to allow a violation, close and complete the
violation with an outcome of Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As an actor on a violation, add a comment to a violation object. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Once a phase (or phases) have chosen to remediate a violation, complete the violation
with an outcome of Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
For violations with an outcome of Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Add a phase to a violation. A phase is a task that must be completed to move the violation forward,
which depends on the task configuration, such as expiration, assignee, notifications, and others.
For type= Parameters
Request bodyMedia type: Responses
|
||||||||||||||||||||||||||||
|
POST |
As an actor on a violation, allow the user to continue to violate the defined rule in perpetuity. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As an actor on a violation, cancel an existing exception, reverting the violation to Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Add a comment to a violation object. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As an actor on a violation, grant an exception to the violating access. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As an actor on a violation, edit the actors and permissions on a violation task. Parameters
Request body * stringMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As an actor on a violation, choose to remediate the access, kicking off the remediation workflow assigned to the violation. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As an actor on a manual provisioning task to handle the violation remediation, mark the action as completed. Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
As an actor on a manual provisioning task to handle the violation remediation, mark the action as canceled (not completed). Parameters
Request bodyMedia type: Responses
Click for an example responseMedia type: |
Task
Endpoints for fulfillment tasks.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Get the tasks for which the authenticated user has permissions to view. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||||||||||||||
|
POST |
Get the tasks for which the authenticated user has permissions to view. You can use the
Parameters
Request bodyResponses
Click for an example responseMedia type: |
User
Endpoint for a user’s grants and recommendations.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Get the user’s current privileges. The endpoint returns the Identity Governance-related authorization details for the authenticated users and includes the following information:
Parameters
Responses
Click for an example to get a user’s privilegesMedia type: |
||||||||||||||||||||||||||||||||||
|
GET |
Get the user’s current grants. Parameters
Responses
Click for an example to get a user’s privilegesMedia type: |
||||||||||||||||||||||||||||||||||
|
GET |
Get the access recommendations for a given user. Parameters
Responses
Click for an example responseMedia type: |
Workflow
|
To use the
This is a temporary requirement and will be removed in a future release. |
| URI | HTTP method |
Description | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Get the workflow definitions. Parameters
Responses
|
||||||||||||||||
|
Post |
Create or publish workflow definitions. Parameters
Request body * requiredMedia type: Responses
Click for an example responseMedia type: |
||||||||||||||||
|
GET |
Get the workflow definition. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||
|
DELETE |
Delete the workflow definition. If the status is published, it will try to delete the workflow model and process the definition in IDM. Parameters
Responses
Click for an example responseMedia type: |
||||||||||||||||
|
PUT |
Update or publish the workflow definition. Parameters
Request body * requiredResponses
Click for an example responseMedia type: |
Evolving APIs
| The APIs referenced in this section are evolving, which means they might change or become deprecated at any time. |
The current evolving APIs focus on entitlements. You can find more information in Manage entitlements.
| URI | HTTP method |
Description |
|---|---|---|
|
GET |
Get an entitlement by an ID. |
|
POST |
Search for a list of all entitlements that match the target filter. |
|
GET |
Gets the users assigned to a specific entitlement. |
Deprecated
These endpoints are deprecated and are no longer being updated. These endpoints might be removed in a future release.
| URI | HTTP method |
Description | ||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
GET |
Returns certification campaigns based on the provided query parameters. Parameters
Responses
|
||||||||||||||||||||||||||||
|
GET |
Returns certification campaigns based on the provided campaign ID. Parameters
Responses
|
||||||||||||||||||||||||||||
|
GET |
Returns the tasks assigned to different certifiers for the given certification campaign ID. Parameters
Responses
|
||||||||||||||||||||||||||||
|
GET |
Returns the glossary specific details of a single entitlement grant using the account and entitlement IDs. Parameters
Responses
|
||||||||||||||||||||||||||||
|
POST |
Create a glossary entry for a single entitlement grant using the account and entitlement IDs. Parameters
Request body exampleMedia type: Responses
|
||||||||||||||||||||||||||||
|
PUT |
Create or update a glossary entry for a single entitlement grant using the account and entitlement IDs. Parameters
Request body exampleMedia type: Responses
|
Supported browsers
The following browsers are supported in PingOne Advanced Identity Cloud:
| Browser | Version |
|---|---|
Google Chrome |
Latest stable version of full-desktop browser |
Firefox |
Latest stable version of full-desktop browser |
Safari |
Latest stable version of full-desktop browser |
Microsoft Edge |
Latest stable version of full-desktop browser |
|
Ping Identity does not provide support for these browsers:
Ping Identity optimizes its platform for modern browsers to ensure the best user experience, security, and performance. If you encounter issues while using the Ping Identity platform, ensure you use a supported, up-to-date browser for the optimal experience. |
|
While Advanced Identity Cloud works with all supported browsers, administrative activity works best using Google Chrome. |
Security and compliance
PingOne Advanced Identity Cloud provides full tenant isolation in a multi-tenant cloud service by using individual trust zones. Each customer’s environment is a dedicated trust zone that shares no code, data, or identities with other customers’ environments. This prevents any accidental or malicious commingling. All data is encrypted, at rest and in transmission, to prevent unauthorized access and data breaches.
Certifications and compliance
SOC 2 Type 2

Ping Identity is SOC 2 Type 2-certified. This confirms that Ping Identity’s information security practices, policies, procedures, and operations meet the SOC 2 standards for security, availability, and confidentiality. Our adherence to these standards is externally validated by an independent third party annually.
Our SOC 2 report is available to customers with a signed NDA on the Security Documentation page of the Ping Identity Support Portal. You must be signed on to access the report.
ISO 27001, 27017, and 27018

Ping Identity’s information security management system (ISMS) has been independently assessed and certified to the ISO 27001 standard. Ping Identity has included ISO 27017 and ISO 27018 into its certified ISMS and has also achieved independent certifications validating that the controls and implementation guidance relevant to those standards are in place and operational.
The scope of Ping Identity’s ISMS covers all major offices used in the development of Ping Identity products, all of our product offerings, both standalone on-premises products and our cloud services (PingOne, PingOne Advanced Services, and Advanced Identity Cloud), as well as all supporting infrastructure, systems, and internal processes.
Our ISO 27001 certificate is available in the Shellman Certificate Directory by searching for Ping Identity.
CSA STAR (Level 2)

Ping Identity’s cloud offerings are certified as meeting the criteria of the Cloud Security Alliance Cloud Controls Matrix (Version 4). Our CSA STAR (Level 2) Attestation demonstrates Ping Identity’s commitment to high standards and industry-accepted cloud security controls and transparency of our security posture.
Our attestation and the CSA Consensus Assessments Initiative Questionnaire are available on the CSA STAR (Level 2) Registry Page.
HIPAA and HITECH

The Health Insurance Portability and Accountability Act (HIPAA) is the US national standard for health information security and privacy that governs the use and disclosure of sensitive protected health information (PHI).
Advanced Identity Cloud complies with HIPAA security standards, as well as the breach notification requirements of the Health Information Technology for Economic and Clinical Health (HITECH) Act. Learn more about how Ping Identity supports HIPAA compliance.
Trusted Information Security Assessments Exchange

The Trusted Information Security Assessment Exchange (TISAX) is an assessment and exchange mechanism for the information security of enterprises governed by ENX on behalf of the German VDA. The exchange allows recognition of assessment results among the participants. TISAX can be accessed by active participants through https://enx.com/tisax. TISAX and TISAX results are not intended for general public use.
ForgeRock Inc. and ForgeRock Ltd. (Ping Identity) are active TISAX participants with assessment results available through the ENX portal - Tisax assessment results, under scope ID: SZZMC3 and assessment ID: AZ5YYL-1.
Security white paper
Learn more about our security practices in our security white paper.
Identity Cloud product lifecycle and releases
PingOne Advanced Identity Cloud releases new features, updates functionality and fixes bugs on a continual cadence. Ping Identity aims to deliver features and functionality that will be the most useful, complete and intuitive for customers. In order to deliver on this goal we have several stages to our release lifecycle.
Early access
Participating in Early Access programs allow customers to provide feedback and collaborate with Ping Identity in designing future capabilities in the product.
Select customers are invited to provide feedback on new features. Customers are encouraged to give feedback and have an active say in product direction; product management and customer success will work with you to gather feedback. Features may be unstable, changed in backward-incompatible ways, and are not guaranteed to be released. We will use all reasonable efforts to communicate breaking changes to customers participating in the program.
Beta
Beta features give customers advanced insights into up-and-coming product capabilities with extra time to prepare to adopt the feature and provide design feedback to the product team. Generally speaking, functionality is stable and meets security and quality expectations but please note that a beta feature is not officially supported for production use.
Upcoming features
Customers receive notifications of new and upcoming features at least a week in advance of a release. The notifications provide customers with high-level information on changes or new functionality.
Limited availability
Features are available for production use and are fully functional and supported; however, they are available only to a select set of customers.
General availability
Features are available for production use and are fully functional and supported. They are available to all customers.
Migration dependent features
Features are not backward compatible and require a tenant migration before they can be used. Learn more in Migration dependent features.
Bug fixes and low impact changes
On an ongoing basis, Ping Identity makes bug fixes and low impact changes as necessary to Advanced Identity Cloud. These types of fixes are deployed as necessary. You can monitor these in the Regular channel changelog and Rapid channel changelog. You can also subscribe to the RSS feeds mentioned at the start of the two changelog pages.
Deprecation and end of life
To maintain both security and quality in Advanced Identity Cloud, we periodically have to modify or remove functionality.
Learn more in Deprecation Notices.
Deprecated features
A feature or behavior (or API endpoint) flagged for deprecation means it is no longer actively enhanced and is minimally maintained. Tenants using the feature at the time of deprecation will continue to have access to the feature until it reaches end of life, at which point customers will no longer have access to the feature. We know deprecation disruptions are inconvenient, and as such, we attempt to limit the frequency of deprecations and to pair them with alternative options and migration recommendations where available.
Deprecation notification
Deprecation information is posted to the Advanced Identity Cloud documentation. Deprecation notices typically include a date the feature or behavior reaches end of life. Our policy is to flag a feature for deprecation with at least 12 months advance notice prior to end of life whenever possible to allow a 12 month migration window.
Periodically, and in case of emergency (critical vulnerabilities or changes required by applicable law or third-party certification standards), we may accelerate this time frame. In such cases, we will provide as much prior notice as is reasonable under the circumstances.
Tenant administrator mandatory 2-step verification FAQ
How is 2-step verification changing?
Ping Identity is making 2-step verification mandatory for all PingOne Advanced Identity Cloud tenant administrators.
The option to skip registration for 2-step verification is deprecated and will be removed a year after the deprecation notification date (Friday, February 3, 2023), following the Advanced Identity Cloud deprecation and end of life policy.
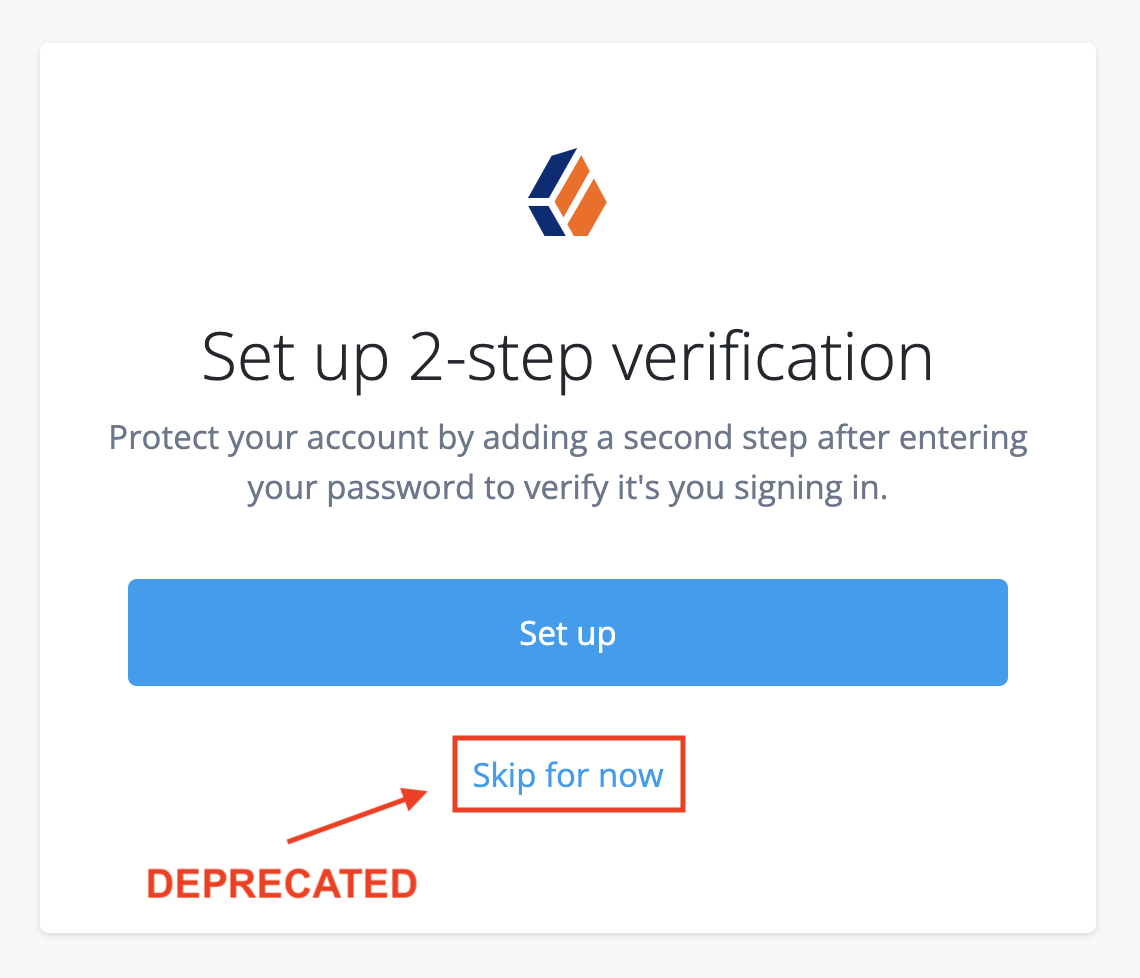
After the option to skip registration is removed, any tenant administrator that has not already set up 2-step verification will be forced to do so the next time they sign in. Advanced Identity Cloud guides the tenant administrator through the device registration process, with no assistance needed from Ping Identity support.
Will the change to mandatory 2-step verification affect me?
Yes, this change affects all customers. You have until the deprecation end-of-life date (Tuesday, April 2, 2024) to update your tenants to make 2-step verification mandatory for all tenant administrators.
How do I prepare my tenants to support 2-step verification?
If you have any automation that relies on the skip option to authenticate to Advanced Identity Cloud APIs, it must be updated to use a service account to get an access token.
| After 2-step verification is enforced, any automation that depends on the skip option will fail authentication. |
How do I enable mandatory 2-step verification for my tenants?
-
Make sure you have updated any automation that authenticates to Advanced Identity Cloud APIs to use a service account. Learn more in How do I prepare my tenants to support 2-step verification?.
-
Open a support case with Ping Identity support:
-
Click Create a case.
-
Follow the steps in the case submission wizard by selecting your account and contract and answering questions about your tenant environments.
-
On the Please answer the following questions to help us understand the issue you’re facing page, enter the following details, and then click Next:
Field Value What product family is experiencing the issue?
Select PingOne Advanced Identity Cloud
What specific product is experiencing the issue?
Select Configuration
What version of the product are you using?
Select NA
What Hostname(s) or Tenant ID(s) does this apply to?
Enter a comma-separated list of FQDNs for the relevant tenant environments.
-
On the Tell us about the issue page, enter the following details, and then click Next:
Field Value Provide a descriptive title for your issue
Enter
Enforce 2-step verification for tenant administratorsDescribe the issue below
Enter
Enforce 2-step verification for tenant administrators -
Click Submit.
-
Ping Identity support turns on the enforcement of 2-step verification for your tenant administrators and then asks you to verify that everything is working as expected.
Application management migration FAQ
Application management allows you to manage the security and access of common and custom relying-party applications and SAML 2.0 applications directly from PingOne Advanced Identity Cloud. This functionality is most commonly used to manage data and system access for employees within an organization, commonly referred to as workforce identity and access management.
How is application management changing?
Ping Identity has improved application management by introducing a single UI interface to the Advanced Identity Cloud admin console that manages all aspects of an application relevant to Advanced Identity Cloud. This replaces the previous arrangement, which required a combination of actions across the Advanced Identity Cloud admin console, AM native admin console, and IDM admin console. In addition, Ping Identity has introduced an application catalog to speed up application configuration for common use cases.
How is the improved application management UI being introduced?
The improved application management UI is only available in tenants created on or after January 12, 2023.
What documentation should I use?
-
For tenants created on or after January 12, 2023, learn more in Application management.
-
For tenants created before January 12, 2023, learn more in Application management (legacy).
Group identity migration FAQ
What has changed?
Ping Identity has introduced a group identity to PingOne Advanced Identity Cloud to simplify the management of permissions and authorizations for collections of users.
How is the group identity being introduced?
Tenants created on or after November 29, 2022 have the group identity enabled by default. Tenants created before that date can follow an upgrade path to enable it; learn more in Enable groups.
Does this affect any other features?
Yes. If you have not upgraded your tenant, event hooks are not available for group identities.
What documentation should I use?
Learn more in Group management.
Deprecation notices
For information about the PingOne Advanced Identity Cloud product lifecycle and deprecation, learn more in Deprecation and end of life.
PingOne Verify service and PingOne Marketplace nodes
- Notification date
-
November 20, 2025
The PingOne Verify service is deprecated. Use the PingOne Worker service instead.
The following Marketplace nodes are deprecated:
Depending on your use case, use the following nodes instead:
- End-of-life date
-
November 30, 2026
IDC.CLI OAuth 2.0 client
- Notification date
-
June 24, 2025
Ping Identity is no longer provisioning the
IDC.CLIOAuth 2.0 client in new tenants and has deprecated it in existing tenants.If you have any automation or scripts that rely on using the
IDC.CLIOAuth 2.0 client in existing tenants, you must update them to use a service account before the end-of-life date when the client will be removed. - End-of-life date
-
June 26, 2026
Access to ESV REST API endpoints using resource version 1.0
- Notification date
-
June 24, 2025
Ping Identity has deprecated the use of resource version
1.0to access ESV REST API endpoints in Advanced Identity Cloud.In the short term, you can continue to use the
1.0resource version to access to ESV REST API endpoints, but this won’t be possible after the end-of-life date.If you have any automation or scripts that rely on using the
1.0resource version for ESV REST API endpoints, you must update them to use resource version2.0before the end-of-life date. - End-of-life date
-
June 26, 2026
Access to ESV REST API endpoints using fr:idm:* scope
- Notification date
-
June 24, 2025
Ping Identity has deprecated use of the
fr:idm:*scope to access ESV REST API endpoints in Advanced Identity Cloud.In the short term, you can continue to use the scope to access ESV REST API endpoints, but this won’t be possible after the end-of-life date.
If you have any automation or scripts that rely on using the scope for ESV REST API endpoints, you must update them to use the
fr:idc:esv:*scope or an appropriate child scope (fr:idc:esv:read,fr:idc:esv:update, orfr:idc:esv:restart) before the end-of-life date. - End-of-life date
-
June 26, 2026
Autonomous Access
- Notification date
-
November 18, 2024
Ping Identity has deprecated Autonomous Access. The product will reach end of life on October 31, 2025. During the deprecation period, Ping Identity will not provide new patches, updates, or new features for Autonomous Access.
To support our Autonomous Access customers, we’re providing migration assistance to PingOne Protect. This advanced threat detection solution leverages machine learning to analyze authentication signals and detect abnormal online behavior. PingOne Protect is a well-established product trusted by hundreds of customers worldwide.
The Autonomous Access documentation has moved to the documentation archive at https://docs.pingidentity.com/archive/.
- End-of-life date
-
October 31, 2025
Duo authentication node
- Notification date
-
March 5, 2024
ForgeRock has deprecated the Duo authentication node because Duo has deprecated Traditional Duo Prompt that is used by the Duo node.
ForgeRock created Duo Universal Prompt node in anticipation of this depreciation. You should use Duo Universal Prompt node instead of Duo node (Deprecated).
- End-of-life date
-
September 30, 2024
Introspect endpoint GET requests and URL query string parameters
- Notification date
-
July 19, 2023
ForgeRock has deprecated the following behaviors of the OAuth 2.0
introspectendpoint in Advanced Identity Cloud:-
Accept GET requests
-
Accept data in POST requests from URL query string parameters
You can continue to use these behaviors, but they will be removed on July 19, 2024. Instead, when using the OAuth 2.0
introspectendpoint, you should use POST requests and pass data in the POST request body. -
- End-of-life date
-
July 19, 2024
Health check endpoints
- Notification date
-
June 13, 2023
ForgeRock has deprecated the following Advanced Identity Cloud health check endpoints:
-
/am/isAlive.jsp -
/am/json/health/live -
/am/json/health/ready -
/openidm/info/ping
You can continue to use the endpoints, but they will be removed on June 13, 2024. You should update any external monitoring to use the Advanced Identity Cloud
/monitoring/healthendpoint instead. Learn more in Monitor using health check endpoint. -
- End-of-life date
-
June 13, 2024
Skip option for 2-step verification registration for Advanced Identity Cloud tenant administrators
- Notification date
-
February 3, 2023
ForgeRock has deprecated the option to let Advanced Identity Cloud tenant administrators skip 2-step verification. You can continue to use the skip option in your tenants, but this functionality will be removed from Advanced Identity Cloud on April 2, 2024. Learn more in Tenant administrator mandatory 2-step verification FAQ.
- End-of-life date
-
April 2, 2024
ForgeRock Identity Cloud Email Server Service
- Notification date
-
April 12, 2021
Built-in Email Server Service
ForgeRock no longer supports the default email provider settings for use in production. The default email provider settings will only be available for testing purposes. Current customers can continue to use the default email provider settings for production purposes, but this functionality will reach end of life on April 12, 2022. Customers should move to using their own email provider.
- End-of-life date
-
April 12, 2022
Groovy OIDC Custom Claims Script
- Notification date
-
April 20, 2021
ForgeRock will continue to support the Groovy version of the OIDC custom claims script until it is end of lifed on April 20th 2022. Current customers can continue to use the Groovy version of the OIDC custom claims script for production purposes, but this functionality will reach end of life on April 20, 2022.
- End-of-life date
-
April 20, 2022
Release process
Ping Identity continuously provides general availability (GA) releases to PingOne Advanced Identity Cloud to introduce new features, fix known issues, and address security issues.
GA releases are delivered through two channels:
-
Rapid channel releases contain the newest GA release features and fixes and are deployed to sandbox[1] environments.
-
Regular channel releases contain established GA release features and fixes and are deployed to development, UAT[2], staging, and production environments.
Optionally, you can defer releases from the regular channel to your production environment to let you test and validate regular channel releases.
Release versions
Ping Identity assigns each release a unique version number, which helps track what’s included and when it’s released.
Instead of separate version numbering for the rapid and regular channels, both increment the same sequence. Version numbers are cumulative. A higher number includes all earlier updates.
Each version number follows a major.minor format.
For example, in version 15158.2:
-
15158is the major version. It increments with each new general availability (GA) release. -
2is the minor version. It increments with each update to that GA release.
The version number is displayed in your tenant environments and in each published changelog entry to let you track which features are in your tenant environments.
Rapid channel
If you have a sandbox[1] environment, a continuous stream of the newest features and fixes are deployed there as soon as they are ready for GA release. This lets you test and evaluate GA releases to make sure they are compatible with your Advanced Identity Cloud implementation. It also lets Ping Identity qualify and establish GA releases through cumulative usage and soak testing, typically over a two-week period. When a GA release has been established, it is allocated to the regular channel and deployed into your development, UAT[2], staging, and production environments.
For early access to documentation about features in the rapid channel, learn more in Rapid channel features.
Track rapid channel releases
You can track rapid channel releases in these ways:
-
Read the web pages: Rapid channel changelog and Rapid channel changelog archive.
-
Subscribe to the RSS feed:
-
If you haven’t done so already, install an RSS reader application. For example, if you use Chrome as your web browser, install an extension such as RSS Feed Reader.
-
Configure your RSS reader to consume the Rapid channel changelog RSS feed.
-
-
Subscribe to email notifications:
-
Scroll down to Documentation Digests.
-
Check the Advanced Identity Cloud Rapid Channel Changelog checkbox.
Regular channel
Only established GA releases are deployed to your development, UAT[2], staging, and production environments. Typically, two weeks' worth of GA releases in the rapid channel are rolled up into one release to the regular channel 2–4 weeks later[16].
Track regular channel releases
You can track regular channel releases in these ways:
-
Read the web pages: Regular channel changelog and Regular channel changelog archive.
-
Subscribe to the RSS feed:
-
If you haven’t done so already, install an RSS reader application. For example, if you use Chrome as your web browser, install an extension such as RSS Feed Reader.
-
Configure your RSS reader to consume the Regular channel changelog RSS feed.
-
-
Subscribe to email notifications:
-
Scroll down to Documentation Digests.
-
Check the Advanced Identity Cloud Regular Channel Changelog checkbox.
Release deferral
|
Release deferral is an opt-in feature. Contact your Ping Identity representative if you are interested. |
Ping Identity lets you defer regular channel releases to your production tenant environments for up to seven days. This allows you to test and validate new regular channel releases in your lower environments (development, UAT[2], and staging) using your most up-to-date configuration.
Each scheduled major release is eligible for deferral. The deferral period has the following characteristics:
-
It begins when the major release is deployed to your lower environments.
-
It ends 7 days later, or sooner if you choose.
-
It isn’t extended for minor version updates (for example,
15158.1to15158.2). These incremental updates are part of the same scheduled major release and don’t restart the deferral period.
Deployment options
During this 7-day deferral period, you have several options for managing the production release:
-
Default option: At the end of the 7-day deferral period, the regular channel release is automatically deployed to your production environment.
-
Self-service option:
-
Trigger the deployment of the new regular channel release to your production environment at any time by running a promotion from your staging environment to your production environment.
The deployment of the new regular channel release to your production environment is triggered by the first promotion to that environment during the seven-day deferral period. This means that you must pause promotions to your production environment until you have validated the new release in your lower environments.
-
-
Support-assisted options:
-
Upgrade without a promotion: Upgrade your production environment without promoting any changes from staging. To do this, create a support case in the Ping Identity Support Portal to request an upgrade.
-
Promote without an upgrade: Promote configuration changes to production but wait to apply the release upgrade. To do this, create a support case in the Ping Identity Support Portal to request the configuration promotion. This option is only available if the configuration changes you’re promoting are compatible with the release version currently in your production environment.
Learn more about configuration promotion and version compatibility
If your changes were made after your staging environment was upgraded, they might depend on the new release and can’t be promoted without also upgrading production.
Scenario 1: Compatible changesYou made configuration changes before your staging environment was upgraded to the new release.
The changes can be promoted to production without the release upgrade because they’re compatible with the older version.
Scenario 2: Incompatible changesYou made configuration changes after your staging environment was upgraded.
The changes can’t be promoted to production without the release upgrade because they could depend on features only available in the new version.
-
Additional considerations
-
If you’ve recently promoted an upgrade to production on a deferred release, you can roll back both the upgrade and the promotion by creating a support case in the Ping Identity Support Portal.
-
In the rare event that Ping Identity applies a hotfix to the major release while you’re testing it in the lower environments, only the minor version changes, so the 7-day deferral period in your production environment isn’t extended. This ensures that Ping Identity can apply security updates quickly and effectively, without impacting the cadence of scheduled regular channel releases.
-
You can use the release information from your production environment to track the 7-day deferral period.
Release notes
Advanced Identity Cloud provides the following changelogs as part of its release process:
| Sandbox and UAT environments are add-on capabilities. |
Scheduled release freezes
Rapid channel release freezes (all dates inclusive):
-
Tuesday, November 25, 2025 - Friday, November 28, 2025
-
Monday, December 22, 2025 - Friday, January 2, 2026
Regular channel release freezes (all dates inclusive):
-
Friday, November 21, 2025 - Tuesday, December 2, 2025
-
Monday, December 15, 2025 - Monday, January 5, 2026
During a release freeze, Ping Identity only performs emergency maintenance.
Regular channel changelog
Subscribe to get automatic updates. Learn more in Track regular channel releases.
For release notes published before May 2025, refer to the Regular channel changelog archive.
February 2026
11 Feb 2026
Version 20340.8
Fixes
-
OPENAM-25702: The PingOne Protect Evaluation node again supports a Node State Attribute For Username setting. PingOne Protect risk evaluation calls can depend on the username.
-
OPENIDM-21776: The Advanced Identity Cloud identity management service now uses synchronous HTTP client requests to connect to external identity management, REST, and token introspection services. This change prevents connection closure exceptions from terminating reconciliation.
03 Feb 2026
Version 20340.5
Fixes
-
FRAAS-13233: AM script validation now ignores ESV placeholders in commented-out code.
-
IAM-9803: The link to the access management native console from the Advanced Identity Cloud admin console now always correctly links to the Alpha or Bravo realm.
-
OPENAM-25707: Fixed PingOneProtectInitializeCallback processing to prevent unwarranted HTTP 4xx and 5xx errors.
January 2026
27 Jan 2026
Version 20133.10
Fixes
-
OPENDJ-11576[17]: Empty user attribute values are no longer considered when evaluating password policies.
21 Jan 2026
Version 20133.8
Key features
- AD Decision node to authenticate against Active Directory identity stores (AME-14959)
-
The new AD Decision node verifies that the provided username and password exist in the specified Active Directory data store. The node also checks whether the user account is locked, disabled, or has expired.
- Cache management service (AME-32248, AME-32285)
-
A new scripted cache management service lets you create and use caches in Scripted Decision nodes. This can improve performance for slow tasks, such as fetching access tokens for third party services that can be reused between journeys. The service has its own metrics.
Learn more in Cache script values.
- SAML 2.0 SP account mapper (OPENAM-23986)
-
A new SAML 2.0 SP account mapper script type enables dynamic modification of SAML assertion data before it’s used to identify local users.
Learn more in SP account mapper.
- Support for SAML 2.0 IdP-initiated flows in integrated mode (AME-29258)
-
You can now configure the hosted SP to redirect to a journey when a response is received from the IdP.
Use the new configuration option to check that the IdP entity ID in the incoming SAML assertion matches the IdP entity ID configured for the node.
A new method has also been added to the
samlApplicationscript binding that returns the assertion as a JSON map.Learn more in Redirect to a journey on the hosted SP.
- RADIUS authentication nodes (AME-32871)[17]
-
The new RADIUS Decision node and RADIUS Challenge Collector node provide RADIUS authentication functionality from within a journey, where Advanced Identity Cloud is acting as the RADIUS client.
- Set Logout Details node (OPENAM-24505)[17]
-
The new Set Logout Details node lets you add details to the JSON response when a journey ends with the user logging out.
- Identity Governance reports (ANALYTICS-1307)[18][17]
-
Advanced Identity Cloud now provides pre-built reports for the Identity Governance service. These reports help you understand and manage your identity governance data. Learn more in Identity Governance Reports.
Enhancements
-
AME-31153: Consent request data can now be pushed via backchannel.
-
AME-31429: A new field on the remote consent agent lets you include properties from the resource owner’s session as part of the consent request.
-
AME-31846: Next-generation Config Provider Node scripts can now access the following additional scripted node bindings:
-
callbacks -
callbacksBuilder -
jwtAssertion -
jwtValidator -
resumedFromSuspend -
requestCookies -
samlApplication -
oauthApplication
-
-
AME-32064: The SAML2 Authentication node includes a new configuration option,Validate IdP Entity ID. When enabled, the node validates that the IdP entity ID from the SAML assertion is the same as the IdP entity ID configured on the node.
-
AME-32970: You can now access the application context for all OAuth 2.0 / OIDC flows through the
oauthApplicationbinding by settingEnable Application Contextin the OAuth 2.0 provider or at the client level. Previously, you could only use this binding when using an application journey. -
IAM-8244: Adds support for bidirectional mappings in synchronization configuration.
-
IAM-8497: Added a brand administrator role to the Advanced Identity Cloud admin console. Brand administrators only have access to change hosted pages themes.
-
IAM-9484: Added ability to provide translation overrides for the Waiting Message field in the Polling Wait node and the Email Suspend Message field in the Email Suspend node. This lets you provide translations when the
PollingWaitCallbackor theSuspendedTextOutputCallbackcallbacks are added using scripts. -
OPENAM-23711: Adds a Detect Connection Time Out option to the Social Provider Handler node. When enabled, connection timeouts from social identity providers result in the journey following the Timeout outcome.
-
OPENAM-24059: Adds support for the
android-keyWebAuthn attestation format. -
OPENAM-24130: The PingOne Protect Evaluation node now lets you set the flow subtype that’s sent to PingOne Protect.
-
OPENAM-24137: You can now configure the PingOne Verify Evaluation node to obtain biographic matching data from the node state.
-
OPENAM-24350: Cryptographic keys can now be derived in next-generation scripts using the PBKDF2 algorithm.
-
OPENAM-24548: The PingOne Protect Initialize node now lets you obtain PingID Device Trust Agent attributes when going through a PingOne Protect flow.
-
OPENAM-24552: The PingOne Protect Evaluation node now lets you send a target application name in addition to the existing target application ID, in the PingOne Protect evaluation request
-
OPENAM-24554: The PingOne Protect Evaluation node now lets you use targeted PingOne policies.
-
OPENAM-24560: Removed the User Type and User Name fields from the PingOne Protect Evaluation node. The user type is always
EXTERNALand the user name is not applicable to external user types. Only theUser IDis sent in the PingOne Protect evaluation request. -
OPENAM-24587: You can now configure Google Secret Manager key IDs (KIDs) as ESVs.
-
OPENAM-25327: Next-generation OAuth 2.0 scripts can now access the
redirectUrisproperty on theclientPropertiesbinding. -
OPENAM-25417: You can now configure the SameSite attribute for cookies in the Set Persistent Cookie node and the Persistent Cookie Decision node.
-
OPENAM-25418: The attestation
fmttype is now included in the transient state data of the WebAuthn nodes. -
OPENAM-24309: The PingOne Verify Evaluation node now supports biographic matching using multiple user attributes.
Fixes
-
AME-32307: Fixed an issue where end users weren’t able to continue a PingOne Verify journey that requested a QR code if they didn’t have a separate device to scan the code.
-
AME-32513: Added the
suspendaction to Custom nodes. -
AME-32979: The Core Token Service (CTS) now stores
AUTHENTICATION_WHITELISTtokens with millisecond-level precision for the expiry timestamp. This minimizes contention in indexes. -
IAM-8766: Fixed an issue with mustRun journeys and query parameters such as
forceAuth=true, where end users were authenticated then immediately unauthenticated. -
IAM-9430: A warning is now displayed in the Advanced Identity Cloud admin console when a promotion would cause a deferred release tenant to be upgraded at the same time.
-
OPENAM-20582: Lets you configure a list of accepted JWT issuers for OAuth 2.0 clients. These are now accepted in addition to the OAuth 2.0 client ID for private key JWT authentication.
-
OPENAM-23929: Fixed a performance issue related to schema caching.
-
OPENAM-24297: Fixed an issue where the PingOne Verify Evaluation node incorrectly returned a failure outcome when the PingOne environment timed out during the identity verification process. This could happen if an end user didn’t engage with the QR code or selfie capture. The update correctly detects the
TRANSACTION_TIMED_OUTstatus in PingOne responses and returns the timeout outcome, letting journeys handle timeouts distinctly from failures.
December 2025
09 Dec 2025
Version N/A
Key features
- x.509 certificate authentication for Microsoft 365 WS-Trust SSO applications (IAM-9212)
-
Microsoft 365 SSO applications that use the WS-Trust protocol can use x.509 authentication. Trusted certificates are accessible to all your Microsoft 365 applications. WS-Trust is included with the WS-Federation[20] add-on.
Learn more in Manage Microsoft 365 application trusted certificates.
This feature requires Advanced Identity Cloud version 19722.7 or later.
03 Dec 2025
Version 19722.7
Key features
- Entitlement composition certification (IGA-3827[17][18])
-
Entitlement composition certification provides a review mechanism that allows certifiers to evaluate, review, and modify the definition of entitlements within the certification process. This capability enables reviewers to submit requests to change the entitlement definition, even independently of the certification decision, with options for drafting and deferring modification requests until sign off.
Learn more in Create an entitlement composition certification template.
- Accounts page (IGA-3960[17][18])
-
The accounts page gives application owners and application administrators a single place to manage all user accounts without granting them full application configuration permissions.
Learn more in Accounts.
Enhancements
-
IAM-9395: Table columns are now resized uniformly across the Advanced Identity Cloud admin console.
-
IAM-9429: If your production environment is configured for deferred release, you can use the new
/environment/promotion/promoteendpoint to check if running a promotion will trigger a release upgrade. -
IAM-9516: The tenant administrator profile page now prompts for re-authentication when adding or removing an MFA device.
-
OPENIDM-19400: New Prometheus metric for the availability of connector servers, for example:
idm_icf_connector_server_availability{name="system-id",type="connector-server-type",} 1.0. -
OPENIDM-20341: Identity management scripts now natively support Base64 encoding using the
btoa(encode) andatob(decode) global script bindings. -
OPENIDM-20790: The
openidm/sync/mappingsendpoint now supports paging using either offsets or cookies. -
OPENIDM-20933: Improved task scanner exception handling. If the task scanner encounters a task that results in an exception, it now aborts only that task and continues processing the remaining tasks. Previously, the scanner would abort the entire process when any task caused an exception.
-
OPENIDM-20937: New provisioner metric
idm_icf_pending. Includes all the same tags asidm_icf*. -
OPENIDM-21170: Metrics for router filters now use
router_filterfor the metric name and include anametag to identify the specific filter. -
OPENIDM-21171: Metrics for managed identity script hooks now use
managed-script-hookfor the metric name,objectto tag the identity object, andscript-hookto tag the script hook. -
OPENIDM-21172: Metrics for custom endpoints now use the new
custom_endpointmetric name and include anametag based on the custom endpoint configuration name after the hyphen. For example, a custom endpoint configurationendpoint-onboardCustomer.jsonwill generate metrics with a name tag/label of "onboardCustomer". The policy service makes use of an internal scripted endpoint based on the filepolicy.js, and its metric name ispolicy-js. -
OPENIDM-21233: The
openidm/health/readyendpoint has been enhanced to include the number of waiting requests. A new set of metrics have been added to provide a historical accounting of IDM health.
Fixes
-
FRAAS-28885[17]: ESV secret
useInPlaceholdersattribute is now taken into account by promotion integrity checks. -
IAM-9466: Annotation comments added to sub-nodes are now saved correctly.
-
IAM-9496: The tooltip in journey comments now correctly displays the creator’s name without overflow.
-
IAM-9527: The hosted account pages logo now correctly uses the height specified in the theme.
-
OPENICF-3277: The SaaS REST connector no longer throws a
NullPointerExceptionwhen attributes are missing in the request payload. -
OPENIDM-20525: The
cnandtelephoneNumberschema foralpha_userandbravo_userare nowscope: publicandsearchable: true. This schema change applies to tenants created on or after December 3, 2025. Existing tenants are unchanged. -
OPENIDM-20863: Default values for multivalue mappings are now copied by value to prevent unintended mutations during runtime.
-
OPENIDM-21421: Updating the configuration of an inactive provisioner no longer throws an
IllegalStateException. -
OPENIDM-21454: Every failed record from a live sync is now stored in the dead-letter queue with a unique entry ID.
Changed functionality
- Default API version for unversioned requests to
openidm/*endpoints (OPENIDM-21191) -
Previously, REST API requests made to
openidm/*endpoints without anAccept-API-Versionheader defaulted to the latest available API version for the resource. These unversioned requests now default to API version1.0for most resources. However, theconsent,scheduler/job,scheduler/trigger, andschemaendpoints default to API version2.0.
November 2025
20 Nov 2025
Version N/A
Key Features
- WS-Trust for Microsoft 365 SSO applications (IAM-8263)
-
Microsoft 365 SSO applications can now use the WS-Trust protocol for legacy rich applications and hybrid joined devices. WS-Trust is included with the WS-Federation[20] add-on.
Learn more in Register an SSO application > Microsoft 365.
This feature requires Advanced Identity Cloud version 19521.3 or later.
11 Nov 2025
Version 19521.3
Enhancements
-
FRAAS-28370: Fixed an issue where requests to the
/monitoring/prometheus/amand/monitoring/prometheus/idmendpoints occasionally didn’t return timely responses. -
IAM-1709: Exposed
useInPlaceholdersandencodingattributes when creating ESV secrets in the admin console. -
IAM-9312: Table columns are now resized uniformly across the following Advanced Identity Cloud admin console pages:
-
Tenant settings
-
Scripts
-
Security
-
Terms & Conditions
-
-
IAM-9323: Added Metadata tab to user resource page to display properties such as
createDateandloginCount.
October 2025
28 Oct 2025
Version 19379.7
Key features
- Audit logging of modifications to environments (FRAAS-17087)
-
You can now use the
/monitoringendpoints and log streaming to track configuration changes made to your environments. The new environment-access log source captures environment changes as audit events.This enhancement improves visibility and observability for environment updates, helping teams monitor configuration activity, identify unexpected changes, and support troubleshooting or alerting workflows.
21 Oct 2025
Version 19190.10
Key features
- Create custom authentication nodes (IAM-5759)
-
Advanced Identity Cloud lets you create your own nodes to reuse common functionality in authentication journeys. Define properties and run custom server-side scripts in these nodes to dynamically set values and decide the outcome of journeys.
Learn more in Custom nodes.
- Next-generation OAuth 2.0 access token modification scripts (AME-31083)
-
You can now create next-generation access token modification scripts that can use next-generation common bindings, such as
httpClient,openidm, andutils. - Ability to configure journeys as transactional only (AME-31843)
-
A transactional authentication journey only runs when Advanced Identity Cloud starts a transaction, which happens when Advanced Identity Cloud does one of the following:
-
Initializes backchannel authentication using either the
/authenticate/backchannel/initializeendpoint or the Backchannel Initialize node. -
Runs a SAML 2.0 app journey for a remote SP.
-
Runs an OAuth 2.0 app journey when Advanced Identity Cloud is acting as an authorization server.
-
Enforces a transactional authorization policy.
You can only configure transactional authentication journeys using the REST API. Set the
transactionalOnlyproperty totruein the journey configuration. -
- Mapping custom key IDs to secrets (AME-31380)
-
You can now map custom
kidheader values for JWTs signed with the signing key to a specific ESV secret. - Nodes to support backchannel authentication journeys (AME-31636 and AME-31635)
-
The new Backchannel Initialize node and Backchannel Status node let you implement backchannel authentication from within a journey.
- Journey binding for scripted nodes (OPENAM-23127)
-
The new
journeybinding for scripted nodes lets you obtain details of the current journey, including inner or child journeys.
Enhancements
-
AME-30984 and AME-30609: Enhanced authentication audit logging to include the SAML Identity Provider (IdP) and Service Provider (SP) entity IDs during SAML flows. This information lets you report on the SAML applications users are accessing, supporting analytics and dashboarding efforts.
-
AME-30985: In SAML v2.0 single sign-on (SSO) flows, the JSON web token (JWT) created in the browser’s session storage no longer expires.
-
AME-31082 and SDKS-3681: Added support for device token refreshing to the Push Notification Service endpoint, enabling the reception of new tokens from mobile devices.
-
AME-31351 and AME-31471: Improvements to the Device Code flow mean that end users are now prompted to reauthenticate even when there’s an existing session for must-run and app journeys.
-
AME-31398: The PingOne Protect Evaluation node has been enhanced to support custom attributes. To specify custom attributes to be used in PingOne Protect for custom predictors, set the
Node State Attribute For Custom Attributesin the node configuration. The node retrieves a map of custom attributes from the node state to be used in the evaluation request to PingOne Protect. -
AME-31656 and AME-31468: The PingOne Protect Evaluation node has been enhanced to support dynamic risk policy IDs and target app IDs. To set the risk policy set ID dynamically, enable
Use Node State Attribute For Risk Policy Set IDin the node configuration. To set the target app ID dynamically, enableUse Node State Attribute For Target App IDin the node configuration. This instructs the node to obtain these IDs from the node state. -
AME-31487: Improvements to SAML v2.0 standalone mode include replacing legacy JSPs with URL endpoints.
You can still invoke the JSPs because they’re mapped to URLs for backward compatibility, but any customizations to these JSPs will be lost.
The following URLs supersede SAML v2.0 JSPs:
URLs
Old URL New URL /saml2/jsp/exportmetadata.jsp/ExportSamlMetadata/saml2/jsp/idpSingleLogoutInit.jsp/IDPSloInit/saml2/jsp/idpSingleLogoutRedirect.jsp/IDPSloRedirect/saml2/jsp/idpSingleLogoutPOST.jsp/IDPSloPOST/saml2/jsp/idpMNIRedirect.jsp/IDPMniRedirect/saml2/jsp/idpMNIRequestInit.jsp/IDPMniInit/saml2/jsp/idpSSOFederate.jsp/idpSSOFederate/saml2/jsp/spAssertionConsumer.jsp/Consumer/saml2/jsp/saml2AuthAssertionConsumer.jsp/AuthConsumer/saml2/jsp/spSingleLogoutInit.jsp/SPSloInit/saml2/jsp/spSingleLogoutRedirect.jsp/SPSloRedirect/saml2/jsp/spSingleLogoutPOST.jsp/SPSloPOST/saml2/jsp/spMNIRedirect.jsp/SPMniRedirect/saml2/jsp/spMNIPOST.jsp/SPMniPOST/saml2/jsp/spMNIRequestInit.jsp/SPMniInit/saml2/jsp/spSSOInit.jsp/spssoinit/saml2/jsp/idpSSOInit.jsp/idpssoinit/saml2/jsp/idpSSOFederate.jsp/idpSSOFederate/saml2/jsp/SA_IDP.jsp/idpsaehandler/saml2/jsp/SA_SP.jsp/spsaehandler -
OPENAM-23051 and AME-31918: A new ESV,
esv.oauth2.request.object.restrictions.enforcedlets you enforce stricter adherence to the PAR and JAR specifications.Setting the value of this ESV to
trueenforces the following: The authorization server ignores authorize parameters outside therequest_uri. When sending a JWT-Secured Authorization Request (JAR), therequest_urimust be anhttpsURI. -
IAM-8236: The ability to edit journeys from the AM native admin console has been removed. Use the Advanced Identity Cloud admin console to edit journeys.
-
IAM-9000, IAM-9001: Add annotations and sticky notes to journeys to assist learning and collaboration.
-
IAM-9237: Allow ESVs to be embedded in URL fields for federation IdPs. This lets you set up federation IdPs with fewer ESVs because you can define a single ESV containing a UUID shared by multiple URL fields.
-
IAM-9246: Table columns are now resized uniformly across all table views.
-
OPENAM-20776: A new OIDC client configuration option,
Private Key JWT Audience, lets you configure and override the audience (aud) claim of a Private Key JWT. -
OPENAM-21783: Improved token management for OAuth 2.0 client applications.
-
OPENAM-23669: Full scopes (scopes ending in
*) can now be used by service accounts in all cases where more specific scopes (for example,:read) are used. -
OPENAM-23710: The
httpClientbinding is now available to legacy SAML 2.0 IdP adapter scripts. -
OPENAM-23850: Enhanced the PingOne Verify Evaluation node with an
Allow same device verificationoption that lets end users continue verification on their current device. -
OPENAM-23867: The LDAP Decision node no longer logs credential failures as errors. It now logs them at the
infolevel. -
OPENAM-24062: Added support for the
ECDSAalgorithm to theutils.crypto.subtlenext-generation binding. This algorithm is supported for key generation, signing, and verification.
Fixes
-
AME-31351 and AME-31471: Improvements to the Device Code flow mean that end users are now prompted to reauthenticate even when there’s an existing session for must-run and app journeys.
-
AME-31481: Validation around policy creation has been improved. If you’re using the legacy "Policy" environment condition (or a custom environment condition), you’ll need to add that to the list of allowed environment conditions for your policy set to create or update policies that use that condition type.
-
IAM-9153: Password validation now works correctly when pasting a value that matches the existing value.
-
OPENAM-20749: A new ESV,
esv-enable-oauth2-sync-refresh-token-issuercauses a stateful OAuth 2.0 introspect response to overwrite theissclaim of the introspectable token. To enable this behavior, set this ESV tofalse. -
OPENAM-23770: Canceling a WebAuthn flow now results in a
Client Erroroutcome, rather than an internal failure. -
OPENAM-24159: Fixed an issue that prevented multiple Identity Assertion nodes from being used in a single journey.
September 2025
30 Sept 2025
Version 19054.9
Enhancements
-
OPENAM-24486: Improved performance when creating large numbers of OAuth 2.0 clients simultaneously.
Fixes
-
OPENDJ-11486: Fixed an exception caused when identity management queries for users with a filter containing wildcards and specific object classes.
Related releases
|
This section contains information about releases of other Ping Identity products that are often deployed as part of an Advanced Identity Cloud implementation. To take advantage of these updates, you must manually upgrade your RCS implementation. |
-
RCS 1.5.20.32 is now available to download. Learn more in ICF release notes.
22 Sept 2025
Version N/A
Key Features
- Log event exporter (FRAAS-19963)
-
Advanced Identity Cloud now lets you export log event data to an external monitoring tool, such as an OpenTelemetry-compatible SIEM or Splunk. This helps you monitor events and troubleshoot issues in near real time.
Learn more in Export log events to an external monitoring tool.
This feature requires Advanced Identity Cloud version 18842.8 or later.
17 Sept 2025
Version 18842.8
Enhancements
-
ANALYTICS-582[21][22]: Custom objects can now be used as data sources for reporting. The system uses an object’s configured title for the data source name, makes its properties available as attributes, and represents all object relationships.
-
ANALYTICS-1165[21]: Added the capability to change a report name.
-
ANALYTICS-1195[21]: Added the ability to import and export report templates using reports API endpoints.
-
FRAAS-25919: You can now use the API to configure custom domains for the Advanced Identity Cloud admin console.
-
IAM-8922: The Advanced Identity Cloud admin console now accepts ESV placeholders for the following federation fields:
-
Application ID
-
Application Secret
-
Well-Known Endpoint
-
Authorization Endpoint
-
User Info Endpoint
-
Token Endpoint
-
Issuer
-
-
IAM-8982[18]: Add event function for setting the query filter/select options of a select field.
-
IAM-9066: Added Tenant Auditor option to Advanced Identity Cloud admin console federation groups claim.
-
IAM-9099, IAM-9146, IAM-9167: Many table views now support column resizing and customization.
Fixes
-
IAM-5488: Terms and Conditions now respects target attribute in anchor tags.
-
IAM-6588: The Advanced Identity Cloud admin console now correctly displays journey status for journeys disabled and enabled using ESVs.
-
IAM-8887: Prevent browsers auto-filling passwords in user registration journeys.
-
IAM-8940: Managed identity number property now accepts float values.
-
IAM-8956: Deselecting the Personal Information option now disables the section containing the user avatar in hosted account pages.
-
IAM-9169: Fixed styling for responsive table layouts with sticky action column in Identities table views.
-
OPENIDM-21372: Advanced Identity Cloud now prevents access to the identity repository endpoint,
/openidm/repo. This prevents uncontrolled and potentially incompatible schema changes.
Additional information
The new PingOne integration guide helps you configure Advanced Identity Cloud to use PingOne products such as PingOne Protect and PingOne Verify. The guide covers the following topics:
-
Best practices for naming and arranging PingOne environments.
-
Best practices for configuring PingOne workers and Advanced Identity Cloud worker services when integrating with PingOne products.
-
How to configure, test, and optimize PingOne Protect.
12 Sept 2025
Version 18712.10
Enhancements
-
OPENAM-24476[23]: Added
java.util.zip.Deflater,java.util.zip.Inflater,java.util.zip.DeflaterOutputStream, andjava.util.zip.InflaterInputStreamto the allowlist for Scripted Decision nodes.
03 Sept 2025
Version 18712.7
Enhancements
-
FRAAS-24857: CNAME verification is no longer required when creating a custom domain.
-
FRAAS-25547: The sender address for emails sent to Advanced Identity Cloud tenant administrators is now
saas@pingidentity.com. -
FRAAS-26063: You can now override the
samlErrorPageUrl. To do so, configure an ESV variable namedesv-global-saml-error-page-urland set its value to your SAML error page URL. If you don’t set this variable, Advanced Identity Cloud uses the default value of/saml2/jsp/saml2error.jsp.
Fixes
-
FRAAS-25734: Exception stacktraces in access management and identity management logs are now truncated to approximately 300-400 lines.
-
FRAAS-25821[24]: Fixed an issue that prevented IP rules in Proxy Connect from being disabled.
August 2025
19 Aug 2025
Version 18368.10
Enhancements
-
OPENAM-24384: Added
javax.crypto.SecretKeyFactory,javax.crypto.spec.PBEKeySpec, andcom.sun.crypto.provider.PBKDF2KeyImplclasses to the allowlist for theOAUTH2_ACCESS_TOKEN_MODIFICATIONscripting context.
Fixes
-
OPENAM-24393[23]: Fixed an issue where the InnerTreeEvaluator node failed for authentication journeys initially accessed using REST without an
authId.
12 Aug 2025
Version 18368.8
Key features
- Policy binding for next-generation scripting (AME-26150)
-
The next-generation
policybinding lets you access the policy engine API and evaluate policies from within scripts. Thepolicybinding works in a similar way to the Request policy decisions for a specific resource API call. - Set Error Details node (AME-30968)
-
The Set Error Details node adds details to the JSON response when a journey ends in an error.
- Monitor log entries in the admin console (FRAAS-25665)
-
Advanced Identity Cloud now provides a console for monitoring log entries in development and sandbox[1] environments. You can view, filter, and search log entries for specific log sources within a timeframe to quickly identify issues, track events, and ensure system security.
Learn more in Monitor log entries in the admin console.
- Custom WS-Fed applications (IAM-8261)
-
You can now create custom WS-Fed[20] applications for single sign-on (SSO).
- Try In SDK button (IAM-8618)
-
A Try In SDK button has been added to the Details page for Native / SPA applications. This lets developers quickly test SDKs with dynamic configuration code snippets.
Enhancements
-
AME-31372[17]: An Agent journey is now available by default in both Alpha and Bravo realms. The
Agentjourney makes it easier to integrate with Ping Identity agents and gateways. It validates the agent credentials with an Agent Data Store Decision node. -
AME-30050: You can now enable a next-generation script in the AM native admin console native console to run after a Dynamic Client Registration request is processed.
-
AME-30716: Removed
Failed to create SSO Tokenfrom logs at warning level. To observe these warnings, increase the log level to debug. -
AME-30801: The Inner Tree Evaluator node now has an optional Error Outcome that lets you capture exception details if an exception occurs during the evaluation of the child journey.
-
FRAAS-25818: The built-in SMTP server in new tenants now has a limit of 10 emails per minute and a fixed email sender address with the format
noreply@<tenant-fqdn>. -
IAM-7581: Text wrapping in table views has been improved for readability.
-
IAM-8573: IDM now includes an endpoint to retrieve individual themes from the
/themerealmconfiguration using either anIDor a_queryFilterby name. This improves performance and ensures reliable theme loading, even on slow networks. -
IAM-8610: When you create an SSO application for Microsoft 365, the application now generates a signing certificate, which you can download or rotate as needed.
-
IAM-8633: You can now add, remove, and rearrange table columns for managed identities and application provisioning tables.
-
IAM-8925[1]: In Identity Governance, you can now configure actions that trigger automatically when a form first loads or when a user changes the value of a specific field.
-
OPENAM-22467: Customers can now provide any value in the
typheader in JWTs. -
Greater control over journey session duration and authenticated session timeouts:
-
OPENAM-23265: The Set Session Properties node now lets you customize the Maximum Session Time and Maximum Idle Time of the session granted at the end of the journey.
-
OPENAM-23290: The new Update Journey Timeout node lets you update the timeout of the journey.
-
OPENAM-23291: The Email Suspend node now lets you configure the Suspend Duration in minutes. This duration overrides existing global or realm settings.
-
OPENAM-23515: You can now set the suspend duration in next-generation scripted decision nodes when suspending the journey.
-
-
OPENAM-23438: Following WebAuthn registration and authentication, new information is added to the transient state.
-
OPENAM-20709: On successful authentication, the WebAuthn Authentication node now adds the UUID of the device (
webauthnDeviceUuid) and the name of the device (webauthnDeviceName) to the shared state. This lets you track the use of biometric authentication and the device used to authenticate.
Fixes
-
AME-30969: If the OIDC Claims Plugin Type in the OAuth 2.0 provider is set to
SCRIPTEDbut no script is selected, theuserinfoendpoint now returns thesubclaim, in compliance with the OIDC specification. Previously, theuserinfoendpoint returned an empty JSON object. If you still require this behavior, set theesv-scripting-legacynulloidcclaimsscriptbehaviourESV totrue. -
IAM-4397: Fixed an issue in the hosted journey pages where the prompt text for the Choice Collector node wasn’t fully visible and the default option wasn’t visible at all.
-
IAM-8632: Fixed an issue where validation errors were incorrectly displayed for pre-populated fields.
-
IAM-8789: Managed identity modals now correctly handle both single-value and array-based enum types.
-
IAM-8871: The hosted account pages no longer freeze and throw an error when editing details if there are empty custom enum array values.
-
IAM-8902: The application username field in SAML 2.0 NameID flows is now correctly set to
uidinstead ofusername. -
IAM-8933: Fixed an issue in the Advanced Identity Cloud admin console when creating or modifying identity objects with a required boolean property. You can now set the value of the required boolean property to
false. -
IAM-9062: Hosted pages themes no longer continuously refresh when trying to set up or confirm two-factor authentication (2FA).
-
OPENAM-20749: For server-side OAuth 2.0 tokens, the /oauth2/introspect response can now overwrite the
issclaim of the introspectable token. To enable this behavior, set theesv-enable-oauth2-sync-refresh-token-issuerESV tofalse. -
OPENAM-22928: When agents authenticate to Advanced Identity Cloud, the session created no longer expires.
-
OPENAM-23303[17]: Fixed an issue where access management scripts were failing to load because they contained strings that resembled configuration placeholders. The code that parses these scripts now correctly ignores configuration placeholders and any strings that resemble them.
If you have access management scripts that reference ESVs, ensure that they use the correct syntax for ESVs. For example, for a script that references an ESV named esv-my-variable, use the syntaxsystemEnv.getProperty("esv.my.variable"). -
OPENAM-23334: You can now use the
mergeSharedandmergeTransientmethods to add nested objects toObjectAttributes. -
OPENAM-23519: Improved error handling during WebAuthn registration when the Android lock screen isn’t enabled.
-
OPENAM-24159: Fixed an issue with Identity Assertion nodes failing if there are more than one in a journey.
Removed
- Modules and chains (AME-30762)
-
The legacy PingAM authentication mechanism using modules and chains is enabled by default in Advanced Identity Cloud but has never been supported. Modules and chains remain enabled but have been removed from the Advanced Identity Cloud admin console.
Modules and chains will be removed entirely in the near future. If you’re using them for authentication, you must migrate to nodes and journeys as soon as possible.
Advanced Identity Cloud provides default journeys that replace the corresponding default modules and chains. Any default authentication processes that relied on modules and chains are unaffected by their removal.
July 2025
08 Jul 2025
Version 18076.3
Enhancements
-
AME-31379: Setting the new ESV
esv-oauth2-provider-request-object-processing-enforcedtotruenow lets admins enforce which validation rules are applied when processing OAuth 2.0 request objects. -
FRAAS-25437: Tenant administrators with the
tenant-auditorrole can now use federated access to authenticate to Advanced Identity Cloud. -
IAM-3441: Added pagination to all list views.
-
IAM-7265: You can now right-click a node in the journey editor to access a context menu.
-
IAM-7266: Added an action bar to the journey editor that lets you deselect or delete currently selected nodes.
-
IAM-7580: Pages now span the full width of the screen, improving navigation and usability.
-
IAM-8260: Advanced Identity Cloud now supports multiple WS-Fed[20] applications.
-
IAM-8640: The Release Notes link in Tenant Settings now opens the release notes for the tenant’s specific version.
-
IAM-8714[18]: You can now configure columns in the Identity Governance access review page.
-
OPENIDM-21206: Usernames and application names must now be unique, as enforced by the datastore.
Fixes
-
IAM-7413: The reCAPTCHA Enterprise node is now fully supported.
-
IAM-8489: Fixed an issue with the display of application logos in the hosted account pages.
-
IAM-8770: Fixed an issue with the calendar icon position in date fields.
-
IAM-8773: Fixed an issue where key actions such as realm login were blocked in older tenants with an unmodified original theme.
The impact of the fix for IAM-8773 is that unmodified original themes in older tenants have been purposefully updated to add any missing theme properties that are present on the latest themes. This has been done to make them compatible with recent efficiency improvements to themes in the hosted account pages, but without changing their appearance.
The missing properties will appear in your promotion reports, but this is expected and does not require you to take any action.
Related releases
|
This section contains information about releases of other Ping Identity products that are often deployed as part of an Advanced Identity Cloud implementation. To take advantage of these updates, you must manually upgrade your RCS and PingGateway implementations. |
-
The RCS 1.5.20.30 release is now available to download. Learn more in ICF release notes.
-
The PingGateway 2025.6.1 release is now available to download. Learn more in PingGateway 2025.6.1.
03 Jul 2025
Version 17889.11
Fixes
-
IAM-8314[23]: Fixed an issue where setting ESVs in connector or provisioner configuration stops the Advanced Identity Cloud admin console from being able to update connectors or run a liveSync operation.
June 2025
24 Jun 2025
Version 17889.7
Key features
- Tenant auditors (IAM-8086)
-
Advanced Identity Cloud now lets you invite tenant auditors to access the Advanced Identity Cloud admin console. Tenant auditors can view settings, configuration, and data but cannot modify them.
Learn more in Tenant administrator groups.
Enhancements
-
FRAAS-25155: Increased log batching size to avoid truncation of large JSON log entries.
-
ANALYTICS-868: The Tenant Admin Activity report has been changed to the Tenant Admin Initiated Entity Type Changes report. The new report provides more detailed and business-friendly insights into changes made by tenant administrators:
-
Field names added, deleted, or modified.
-
Before and after values of changed attributes (if applicable).
-
Business-friendly entity name and entity type changes to custom attributes and custom objects.
Learn more in Tenant admin initiated entity type changes report.
-
-
IAM-8405: You can now duplicate out-of-the-box reports.
-
IAM-8591: Dynamic sorting for report results. You can now sort report results directly in the Advanced Identity Cloud admin console after running a report.
Fixes
-
FRAAS-25142: Fixed a memory issue in the ESV service.
-
FRAAS-25434: Fix issue causing source to sometimes be defined as
unknownin/monitoring/logs/*endpoints. -
FRAAS-25226: Allow a higher threshold for large JSON log entries before splitting them into smaller plaintext log entries.
Deprecations
-
FRAAS-23329: Access to ESV REST API endpoints using the fr:idm:* scope is now deprecated.
-
FRAAS-23330: Access to ESV REST API endpoints using resource version 1.0 is now deprecated.
-
FRAAS-25269: The IDC.CLI OAuth 2.0 client is now deprecated in existing tenants and no longer provisioned in new tenants.
Learn more in Deprecation notices.
10 Jun 2025
Version 17713.5
Key features
- Akamai Account Protector node (TNTP-227)[17]
-
Use the Akamai Account Protector node to inject the Akamai risk score into your authentication journey. When the Akamai Account Protector feature is enabled for your application, the Akamai Edge service provides the risk score in an HTTP header, which is consumed by the Akamai Account Protector node.
Learn more in Akamai Account Protector node.
Enhancements
-
FRAAS-25205: Consolidated
End User UI,Login UI,Administrator Registration UI, andAdministrator UIstatus page components into a singleAdministrator UIcomponent as they were all reporting the same service. -
IAM-2453[17]: Hosted pages themes now show the loading spinner until they are fully loaded.
-
IAM-4769[17]: Hosted journey pages now fall back to the default theme if a journey is configured with a deleted theme.
-
IAM-6781[17]: Password policy hints now show all policy conditions when creating a new user identity in the Advanced Identity Cloud admin console.
-
IAM-7615[17]: The Certificate Collector node now validates the value set in the HTTP Header Name for Client Certificate field based on the value selected in the Certificate Choice Method field.
-
IAM-8358[17][18]: Hosted account pages now display a New User button in the Users list view for delegated administrators.
-
OPENIDM-15771: You can now set locales in identity management scripts with the
_localeparameter. -
OPENIDM-17680: Advanced Identity Cloud now supports enumerations in string and number attributes of its identity schema. To make an attribute an enumeration, add
"enum" : [ "one", "two", "three" ]to the attribute. Advanced Identity Cloud requires create and update privileges to use one of the enumerated values. -
OPENIDM-19918: You can now choose whether synchronization detects identity array changes using ordered or unordered comparisons. Set the
comparisonconfiguration property in the schema. Unordered JSON array comparison ignores the order of elements and can negate the need for certain custom scripts within mappings. Relationship and virtual property array fields default to unordered comparisons. All other fields default to ordered comparisons. -
OPENIDM-20023: RCS communication with Advanced Identity Cloud can now use stricter authorization. Learn more in Secure RCS access and Migration dependent features.
Fixes
-
FRAAS-25256: Fixed an issue that was causing missing data in analytics dashboards.
-
IAM-1479[17]: Email field validation in the Advanced Identity Cloud admin console now runs only when typing stops or the field is unfocused.
-
IAM-7858[17]: Hosted account pages now use the access management
maxIdleExpirationTimevalue to prompt the You will be signed out soon modal. -
IAM-8382[17]: Fixed an issue in the bookmark app where the URL field validation stopped the Create Application button working the first time it was clicked.
-
IAM-8383[17]: Fixed an issue in the bookmark app where the URL field accepted ESV secrets.
-
IAM-8398[17]: Field labels positioned above a field now remain left aligned when autofill is triggered.
-
IAM-8441[17]: Fixed a display issue in the Advanced Identity Cloud admin console where connector servers and connector server clusters with long names went off the edge of the screen.
-
OPENAM-21783: Improved token management for OAuth 2.0 clients that override the Use Client-Side Access & Refresh Tokens setting. The OAuth 2.0
applicationsendpoint now correctly shows all tokens issued to these clients. Additionally, administrators can now successfully revoke any of the tokens issued to these clients. -
OPENDJ-11486[17]: Fixed an exception caused by identity management user queries with a filter containing wildcards and specific object classes.
May 2025
27 May 2025
Version 17584.6
Enhancements
-
ANALYTICS-1004[22]: Support for custom attributes and relationships in the organization entity for advanced reports.
-
OPENAM-23218: Legacy SAML 2.0 IDP attribute mapper scripts now have access to the
httpClientbinding. -
OPENAM-23710: Legacy SAML 2.0 IDP adapter scripts now have access to the
httpClientbinding.
16 May 2025
Version N/A
Key features
- Integrate with Microsoft 365 (FRAAS-21607)
-
Ping Identity introduces Microsoft 365 integration, a new add-on capability for Advanced Identity Cloud. The new Microsoft 365 application lets you set up SSO using the WS-Federation identity protocol.
Learn more in Register an SSO application.
13 May 2025
Version 17436.7
Enhancements
-
IAM-987: Added support for enums (drop-down lists) to hosted account pages.
-
IAM-1116: Added support for enums (drop-down lists) to the Advanced Identity Cloud admin console.
-
IAM-2103: Added support for enums (drop-down lists) to hosted journey pages.
-
IAM-6822: Added the ability to manage cookie domains in the Advanced Identity Cloud admin console.
-
IAM-7412: Updated the password policy feature in the Advanced Identity Cloud admin console. Added the ability to specify a minimum substring length between 3 - 64 to use when validating passwords against user attribute values. The default is still 5 characters, but can now be reduced to as few as 3 characters to catch shorter string matches.
-
IAM-7794[18]: Added support for using custom identity objects in the form builder.
-
IAM-7919: Improved color contrast ratio of the Delete Account button text when focused.
-
IAM-7934: Improved color contrast ratio of date fields when focused.
-
IAM-7957: Improved color contrast ratio of the Deselect button text when focused.
-
IAM-7966: Improved color contrast ratio of In Progress text.
-
IAM-8016[18]: Allow form authors to specify a user filter when dynamic enums are selected.
-
IAM-8085: Updated the Add a Parameter reports modal to use entity attributes for input.
Fixes
-
FRAAS-15518: Fixed issue that prevented localization of Session timed out message in certain locales.
-
FRAAS-24449: Enhanced the reliability of metrics collection under high-load conditions.
-
FRAAS-24990: Fixed an issue where requests to the
/monitoring/logsand/monitoring/logs/tailendpoints timed out after 15 seconds rather than the expected 60 seconds. -
IAM-5834: Fixed a double-encoding issue in the SAML app that affected IdP-initiated sign on.
-
IAM-6796: Jobs are now prevented from being scheduled with frequencies that cause invalid date errors.
-
IAM-7855: Fixed a typo in the help text returned when there are no results to display.
-
IAM-8237: Corrected floating labels in the date picker in the hosted journey pages.
-
IAM-8361: The Save button in the Edit Bookmark application is now inactive while checking if the ESV exists.
-
IAM-8364: Fixed issues in SAML end-to-end scenarios.
-
IAM-8378: Fixed an issue that stripped HTML elements from email templates.
-
IAM-8403: Fixed border focus location and floating label issues in Tag fields.
-
IAM-8434: Fixed an issue that prevented duplication of new themes that contain special characters.
Rapid channel changelog
Subscribe to get automatic updates. Learn more in Track rapid channel releases.
For release notes published before May 2025, refer to the Rapid channel changelog archive.
February 2026
12 Feb 2026
Version 20612.0
Enhancements
-
ANALYTICS-1383[22]: The new historical change report feature provides a complete audit trail of changes to your managed identities. It tracks all modifications to user profiles, roles, accounts, and applications. You can easily generate reports to see what changed, who made the change, and when it happened, which gives you clear insights for compliance and security monitoring.
09 Feb 2026
Versions 20575.0, 20577.0
No customer-facing features, enhancements, or fixes released.[19]
06 Feb 2026
Versions 20552.0, 20554.0
Enhancements
-
OPENIDM-21472: When provisioning applications and using queued synchronization, changes to a user account now propagate to all associated accounts.
Fixes
-
OPENAM-25702: The PingOne Protect Evaluation node again supports a Node State Attribute For Username setting. PingOne Protect risk evaluation calls can depend on the username.
-
OPENIDM-21493: You can now cancel a clustered reconciliation even when a route associated with the source or target system is unavailable.
-
OPENIDM-21776: The Advanced Identity Cloud identity management service now uses synchronous HTTP client requests to connect to external identity management, REST, and token introspection services. This change prevents connection closure exceptions from terminating reconciliation.
Changed functionality
-
OPENIDM-21718: The
maxQueueSizefor queued synchronization now defaults to1000and can’t be configured to a value higher than1000or lower than100. The previous default was20000.The
pageSizestill defaults to100, but now can’t be configured to a value higher than100or lower than10. If the configuredpageSizeis greater thanmaxQueueSize / 10, Advanced Identity Cloud usesmaxQueueSize / 10for the page size.If you have any configuration outside of these bounds, Advanced Identity Cloud automatically adjusts the values to the nearest bound.
January 2026
28 Jan 2026
Version 20408.0
Fixes
-
OPENAM-25707: Fixed PingOneProtectInitializeCallback processing to prevent unwarranted HTTP 4xx and 5xx errors.
27 Jan 2026
Version 20406.0
Enhancements
-
IAM-4464: Next-generation configuration provider scripts created through the journey editor now contain the default config for the selected node type.
-
IAM-9709: Updated the journey editor to make fewer network calls when saving a journey that contains page nodes.
Fixes
-
IAM-4345: Vertical tabs were missing a hover state.
-
IAM-8033: Journey name field did not have a length check in place.
-
IAM-8226: When importing a journey, if you skip the the download backup option but then return to it using the Previous link, it now completes the backup before offering the download.
-
IAM-9590: The message shown in the hosted pages for an unauthorized access attempt is now correctly centered on a single page.
-
IAM-9687: When you enter a valid ESV placeholder in the URL field of a bookmark application, the field is now immediately disabled and shows a delete icon to remove the placeholder.
-
IAM-9803: The link to the access management native console from the Advanced Identity Cloud admin console now always correctly links to the Alpha or Bravo realm.
14 Jan 2026
Version 20285.0
Fixes
-
OPENAM-25646: For backward compatibility, we’ve restored the following deprecated fields sent to PingOne Protect by the PingOne Protect Initialize node (in the
PingOneProtectInitializeCallback):-
consoleLogEnabled -
deviceAttributesIgnored -
customHost -
lazyMetadata -
deviceKeyRsyncIntervals -
disableHub
These fields are deprecated and no longer supported in PingOne. This fix restores the fields but you should update your clients and scripts to remove the unsupported fields as soon as possible. -
December 2025
17 Dec 2025
Version 20090.0
Key features
- AD Decision node to authenticate against Active Directory identity stores (AME-14959)
-
The AD Decision node verifies that the provided username and password exist in the specified Active Directory data store. The node also checks whether the user account is locked, disabled, or has expired.
- Cache management service (AME-32248, AME-32285)
-
A new scripted cache management service lets you create and use caches in Scripted Decision nodes. This can improve performance for slow tasks, such as fetching access tokens for third party services that can be reused between journeys. The service has its own metrics.
Find more information in Cache script values.
- SAML 2.0 SP account mapper (OPENAM-23986)
-
A new SAML 2.0 SP account mapper script type enables dynamic modification of SAML assertion data before it’s used to identify local users.
Find more information in SP account mapper.
- Support for SAML 2.0 IdP-initiated flows in integrated mode (AME-29258)
-
You can now configure the hosted SP to redirect to a journey when a response is received from the IdP.
Use the new configuration option to check that the IdP entity ID in the incoming SAML assertion matches the IdP entity ID configured for the node.
A new method has also been added to the
samlApplicationscript binding that returns the assertion as a JSON map.Find more information in Redirect to a journey on the hosted SP.
Enhancements
-
AME-31153: Consent request data can now be pushed via backchannel.
-
AME-31429: A new field on the remote consent agent lets you include properties from the resource owner’s session as part of the consent request.
-
AME-31846: Next-generation Config Provider Node scripts can now access the following additional scripted node bindings:
-
callbacks -
callbacksBuilder -
jwtAssertion -
jwtValidator -
resumedFromSuspend -
requestCookies -
samlApplication -
oauthApplication
-
-
AME-32064: The SAML2 Authentication node includes a new configuration option,
validateIdpEntityId. When set totrue, the node validates that the IdP entity ID from the SAML assertion is the same as the IdP entity ID configured on the node. -
AME-32970: You can now access the application context for _all OAuth 2.0 / OIDC flows through the
oauthApplicationbinding by settingEnable Application Contextin the OAuth 2.0 provider or at the client level. Previously, you could only use this binding when using an application journey. -
IAM-8244: Adds support for bidirectional mappings in synchronization configuration.
-
IAM-8497: Added a brand administrator role to the Advanced Identity Cloud admin console. Brand administrators only have access to change hosted pages themes.
-
IAM-9484: Added ability to provide translation overrides for the Waiting Message field in the Polling Wait node and the Email Suspend Message field in the Email Suspend node. This lets you provide translations when the
PollingWaitCallbackor theSuspendedTextOutputCallbackcallbacks are added using scripts. -
OPENAM-23711: Adds a
Detect connection timeoutoption to the Social Provider Handler node. When enabled, connection timeouts from social identity providers result in the journey following the Timeout outcome. -
OPENAM-24059: Adds support for the
android-keyWebAuthn attestation format. -
OPENAM-24130: The PingOne Protect Evaluation node now lets you set the flow subtype that’s sent to PingOne Protect.
-
OPENAM-24137: You can now configure the PingOne Verify Evaluation node to obtain biographic matching data from the node state.
-
OPENAM-24350: Cryptographic keys can now be derived in next-generation scripts using the PBKDF2 algorithm.
-
OPENAM-24548: The PingOne ProtectInitialize node now lets you obtain PingID Device Trust Agent attributes when going through a PingOne Protect flow.
-
OPENAM-24552: The PingOne Protect Evaluation node now lets you send a target application name in addition to the existing target application ID, in the PingOne Protect evaluation request.
-
OPENAM-24554: The PingOne Protect Evaluation node now lets you use targeted PingOne policies.
-
OPENAM-24560: Removed the User Type and User Name fields from the PingOne Protect Evaluation node. The user type is always
EXTERNALand the user name is not applicable to external user types. Only theUser IDis sent in the PingOne Protect evaluation request. -
OPENAM-24587: You can now configure Google Secret Manager key IDs (KIDs) as ESVs.
-
OPENAM-25327: Next-generation OAuth 2.0 scripts can now access the
redirectUrisproperty on theclientPropertiesbinding. -
OPENAM-25417: You can now configure the
SameSiteoption for cookies in the Set Persistent Cookie node and the Persistent Cookie Decision node. -
OPENAM-25418: The attestation
fmttype is now included in the transient state data of the WebAuthn nodes.
Fixes
-
AME-32307: Fixed an issue where end users weren’t able to continue a PingOne Verify journey that requested a QR code if they didn’t have a separate device to scan the code.
-
AME-32513: Added the
suspendaction to Custom nodes. -
IAM-8766: Fixed an issue with mustRun journeys and query parameters such as
forceAuth=true, where end users were authenticated then immediately unauthenticated. -
IAM-9430: A warning is now displayed in the Advanced Identity Cloud admin console when a promotion would cause a deferred release tenant to be upgraded at the same time.
-
OPENAM-20582: Lets you configure a list of accepted JWT issuers for OAuth 2.0 clients. These are now accepted in addition to the OAuth 2.0 client ID for private key JWT authentication.
-
OPENAM-23929: Fixed a performance issue related to schema caching.
-
OPENAM-24297: Fixed an issue where the PingOne Verify Evaluation node incorrectly returned a failure outcome when the PingOne environment timed out during the identity verification process. This could happen, for example, if an end user didn’t engage with the QR code or selfie capture. The update correctly detects the
TRANSACTION_TIMED_OUTstatus in PingOne responses and returns the timeout outcome, letting journeys handle timeouts distinctly from failures. -
OPENAM-24309: The PingOne Verify Evaluation node now supports a list of values in an attribute sent for biographic matching.
15 Dec 2025
Versions 20039.0, 20042.0
No customer-facing features, enhancements, or fixes released.[19]
10 Dec 2025
Version 19974.0
Enhancements
-
FRAAS-28686: For log streaming, the
am-everythingandidm-everythingsources now include sub-source information in thesourceandextracted_sourcefields.For example,
am-everythingreturns logs containing the corresponding match inam-access,am-activity,am-authentication,am-config,am-core. This ensures that logs consolidated underam-everythingare correctly identified and parsed by log analysis tools such as Splunk, retaining their original context.
November 2025
17 Nov 2025
Version 19722.0
Enhancements
-
IAM-9395: Table columns are now resized uniformly across the Advanced Identity Cloud admin console.
-
IAM-9516: The tenant administrator profile page now prompts for re-authentication when adding or removing an MFA device.
-
OPENIDM-19400: New Prometheus metric for the availability of connector servers, for example:
idm_icf_connector_server_availability{name="system-id",type="connector-server-type",} 1.0. -
OPENIDM-20341: Identity management scripts now natively support Base64 encoding using the
btoa(encode) andatob(decode) global script bindings. -
OPENIDM-20790: The
openidm/sync/mappingsendpoint now supports paging using either offsets or cookies. -
OPENIDM-20933: Improved task scanner exception handling. If the task scanner encounters a task that results in an exception, it now aborts only that task and continues processing the remaining tasks. Previously, the scanner would abort the entire process when any task caused an exception.
-
OPENIDM-20937: New provisioner metric
idm_icf_pending. Includes all the same tags asidm_icf*. -
OPENIDM-21170: Metrics for router filters now use
router_filterfor the metric name and include anametag to identify the specific filter. -
OPENIDM-21171: Metrics for managed identity script hooks now use
managed-script-hookfor the metric name,objectto tag the identity object, andscript-hookto tag the script hook. -
OPENIDM-21172: Metrics for custom endpoints now use the new
custom_endpointmetric name and include anametag based on the custom endpoint configuration name after the hyphen. For example, a custom endpoint configurationendpoint-onboardCustomer.jsonwill generate metrics with a name tag/label of "onboardCustomer". The policy service makes use of an internal scripted endpoint based on the filepolicy.js, and its metric name ispolicy-js. -
OPENIDM-21233: The
openidm/health/readyendpoint has been enhanced to include the number of waiting requests. A new set of metrics have been added to provide a historical accounting of IDM health.
Fixes
-
IAM-9466: Annotation comments added to sub-nodes are now saved correctly.
-
IAM-9496: The tooltip in journey comments now correctly displays the creator’s name without overflow.
-
IAM-9527: The theme logo now correctly uses the height specified in the theme.
-
OPENICF-3277: The SaaS REST connector no longer throws a
NullPointerExceptionwhen attributes are missing in the request payload. -
OPENIDM-20525: The
cnandtelephoneNumberschema foralpha_userandbravo_userare nowscope: publicandsearchable: true. This schema change applies to sandbox tenants created on or after November 17, 2025. Existing sandbox tenants are unchanged. -
OPENIDM-20863: Default values for multivalue mappings are now copied by value to prevent unintended mutations during runtime.
-
OPENIDM-21421: Updating the configuration of an inactive provisioner no longer throws an
IllegalStateException. -
OPENIDM-21454: Every failed record from a live sync is now stored in the dead-letter queue with a unique entry ID.
Changed functionality
- Default API version for unversioned requests (OPENIDM-21191)
-
Previously, REST API requests without an
Accept-API-Versionheader used the latest available API version for the resource. These unversioned requests now default to API version1.0for most endpoints. However, theconsent,scheduler/job,scheduler/trigger, andschemaendpoints default to API version2.0.
October 2025
27 Oct 2025
Version 19521.0
Enhancements
-
IAM-1709: Exposed
useInPlaceholdersandencodingattributes when creating ESV secrets in the admin console. -
IAM-9312: Table columns are now resized uniformly across the following Advanced Identity Cloud admin console pages:
-
Tenant settings
-
Scripts
-
Security
-
Terms & Conditions
-
-
IAM-9323: Added Metadata tab to user resource page to display properties such as
createDateandloginCount.
15 Oct 2025
Versions 19379.0, 19387.0
No customer-facing features, enhancements, or fixes released.[19]
September 2025
26 Sept 2025
Version 19173.0
Key features
- Create custom authentication nodes (IAM-5759)
-
Advanced Identity Cloud lets you create your own nodes to reuse common functionality in authentication journeys. Define properties and run custom server-side scripts in these nodes to dynamically set values and decide the outcome of journeys.
Learn more in Custom nodes.
Enhancements
-
IAM-9000, IAM-9001: Added annotations and sticky notes to journeys to assist learning and collaboration.
-
IAM-9237: Allow ESVs to be embedded in URL fields for federation IdPs. This lets you set up federation IdPs with fewer ESVs because you can define a single ESV containing a UUID shared by multiple URL fields.
-
IAM-9246: Table columns are now resized uniformly across all table views.
25 Sept 2025
Version 19095.0
Key features
- Mapping custom key IDs to secrets (AME-31380)
-
You can now map custom
kidheader values for JWTs signed with the signing key to a specific ESV secret. - Nodes to support backchannel authentication journeys (AME-31636 and AME-31635)
-
The new Backchannel Initialize node and Backchannel Status node let you implement backchannel authentication from within a journey.
- Next-generation OAuth 2.0 access token modification scripts (AME-31083)
-
You can now create next-generation access token modification scripts that can use next-generation common bindings, such as
httpClient,openidm, andutils. - Ability to configure journeys as transactional only ([._2025-10-14]#AME-31843)
-
A transactional authentication journey only runs when Advanced Identity Cloud starts a transaction, which happens when Advanced Identity Cloud does one of the following:
-
Initializes backchannel authentication using either the
/authenticate/backchannel/initializeendpoint or the Backchannel Initialize node. -
Runs a SAML 2.0 app journey for a remote SP.
-
Runs an OAuth 2.0 app journey when Advanced Identity Cloud is acting as an authorization server.
-
Enforces a transactional authorization policy.
You can only configure transactional authentication journeys using the REST API. Set the
transactionalOnlyproperty totruein the journey configuration. -
- Journey binding for scripted nodes (OPENAM-23127)
-
The new
journeybinding for scripted nodes lets you obtain details of the current journey, including inner or child journeys.
Enhancements
-
AME-30984 and AME-30609: Enhanced authentication audit logging to include the SAML Identity Provider (IdP) and Service Provider (SP) entity IDs during SAML flows. This information lets you report on the SAML applications users are accessing, supporting analytics and dashboarding efforts.
-
AME-30985: In SAML v2.0 single sign-on (SSO) flows, the JSON web token (JWT) created in the browser’s session storage no longer expires.
The time allowed to complete the SSO flow is now determined by the configurable maximum duration of the journey session instead of the JWT expiration.
Previously, the JWT expired when the cache was cleared.
-
AME-31082 and SDKS-3681: Added support for device token refreshing to the Push Notification Service endpoint, enabling the reception of new tokens from mobile devices.
-
AME-31379: You can now enforce the OAuth 2.0 request object processing rules that apply, regardless of the request type. Create an ESV named
esv.oauth2.provider.request.object.processing.enforcedand set its value totrue. This setting forces Advanced Identity Cloud to use the specification set in the Request Object Processing Specification field of the OAuth 2.0 provider configuration for JWT requests. -
AME-31656 and AME-31468: The PingOne Protect Evaluation node has been enhanced to support dynamic risk policy IDs and target app IDs. To set the risk policy set ID dynamically, enable
Use Node State Attribute For Risk Policy Set IDin the node configuration. To set the target app ID dynamically, enableUse Node State Attribute For Target App IDin the node configuration. This instructs the node to obtain these IDs from the node state. -
AME-31398: The PingOne Protect Evaluation node has been enhanced to support custom attributes. To specify custom attributes to be used in PingOne Protect for custom predictors, set the
Node State Attribute For Custom Attributesin the node configuration. The node retrieves a map of custom attributes from the node state to be used in the evaluation request to PingOne Protect. -
AME-31487: Improvements to SAML v2.0 standalone mode include replacing legacy JSPs with URL endpoints.
You can still invoke the JSPs because they’re mapped to URLs for backward compatibility, but any customizations to these JSPs will be lost.
The following URLs supersede SAML v2.0 JSPs:
URLs
Old URL New URL /saml2/jsp/exportmetadata.jsp/ExportSamlMetadata/saml2/jsp/idpSingleLogoutInit.jsp/IDPSloInit/saml2/jsp/idpSingleLogoutRedirect.jsp/IDPSloRedirect/saml2/jsp/idpSingleLogoutPOST.jsp/IDPSloPOST/saml2/jsp/idpMNIRedirect.jsp/IDPMniRedirect/saml2/jsp/idpMNIRequestInit.jsp/IDPMniInit/saml2/jsp/idpSSOFederate.jsp/idpSSOFederate/saml2/jsp/spAssertionConsumer.jsp/Consumer/saml2/jsp/saml2AuthAssertionConsumer.jsp/AuthConsumer/saml2/jsp/spSingleLogoutInit.jsp/SPSloInit/saml2/jsp/spSingleLogoutRedirect.jsp/SPSloRedirect/saml2/jsp/spSingleLogoutPOST.jsp/SPSloPOST/saml2/jsp/spMNIRedirect.jsp/SPMniRedirect/saml2/jsp/spMNIPOST.jsp/SPMniPOST/saml2/jsp/spMNIRequestInit.jsp/SPMniInit/saml2/jsp/spSSOInit.jsp/spssoinit/saml2/jsp/idpSSOInit.jsp/idpssoinit/saml2/jsp/idpSSOFederate.jsp/idpSSOFederate/saml2/jsp/SA_IDP.jsp/idpsaehandler/saml2/jsp/SA_SP.jsp/spsaehandler -
IAM-8236: The ability to edit journeys from the AM native admin console has been removed. Use the Advanced Identity Cloud admin console to edit journeys.
-
OPENAM-20776: A new OIDC client configuration option,
Private Key JWT Audience, lets you configure and override the audience (aud) claim of a Private Key JWT. -
OPENAM-21783: Improved token management for OAuth 2.0 client applications.
This change resolves issues related to managing tokens issued to OAuth 2.0 clients that override the
Use Client-Side Access & Refresh Tokenssetting. Specifically: The /users/user/oauth2/applications endpoint now correctly returns all tokens issued to clients. Administrators can now successfully revoke any tokens issued to a client, as required. -
OPENAM-23051 and AME-31918: A new ESV,
esv.oauth2.request.object.restrictions.enforcedlets you enforce stricter adherence to the PAR and JAR specifications.Setting the value of this ESV to
trueenforces the following: The authorization server ignores authorize parameters outside therequest_uri. When sending a JWT-Secured Authorization Request (JAR), therequest_urimust be anhttpsURI. -
OPENAM-23669: _Full scopes (scopes ending in
*) can now be used by service accounts in all cases where more specific scopes (for example,:read) are used. -
OPENAM-23710: The
httpClientbinding is now available to legacy SAML 2.0 IdP adapter scripts. -
OPENAM-23850: Enhanced the PingOne Verify Evaluation node with an
Allow same device verificationoption that lets end users continue verification on their current device. -
OPENAM-23867: The LDAP Decision node no longer logs credential failures as errors. It now logs them at the
infolevel. -
OPENAM-24062: Added support for the
ECDSAalgorithm to theutils.crypto.subtlenext-generation binding. This algorithm is supported for key generation, signing, and verification.
Fixes
-
AME-31351 and AME-31471: Improvements to the Device Code flow mean that end users are now prompted to reauthenticate even when there’s an existing session for must-run and app journeys.
-
AME-31481: Validation around policy creation has been improved. If you’re using the legacy "Policy" environment condition (or a custom environment condition), you’ll need to add that to the list of allowed environment conditions for your policy set to create or update policies that use that condition type.
-
OPENAM-20749: A new ESV,
esv-enable-oauth2-sync-refresh-token-issuercauses a stateful OAuth 2.0 introspect response to overwrite theissclaim of the introspectable token. To enable this behavior, set this ESV tofalse.For compatibility reasons, the existing behavior in Advanced Identity Cloud is not changed by default.
-
OPENAM-23770: Canceling a WebAuthn flow now results in a
Client Erroroutcome, rather than an internal failure. -
OPENAM-24159: Fixed an issue that prevented multiple Identity Assertion nodes from being used in a single journey.
19 Sept 2025
Versions 19095.0, 19101.0
No customer-facing features, enhancements, or fixes released.[19]
16 Sept 2025
Version 19054.0
03 Sept 2025
Versions 18859.0, 18878.0
No customer-facing features, enhancements, or fixes released.[19]
01 Sept 2025
Version 18842.0
Key features
- Reports API endpoints to import and export report templates# (ANALYTICS-1195[25])
-
Added the ability to import and export report templates using reports API endpoints.
- Custom objects as data sources for reporting (ANALYTICS-582[25][22])
-
Custom objects can now be used as data sources for reporting. The system uses an object’s configured title for the data source name, makes its properties available as attributes, and represents all object relationships.
Enhancements
-
ANALYTICS-1165[25]: Added the capability to change a report name.
-
IAM-7547: Access policy modal now validates IPv4 or IPv6 format for IP addresses.
-
IAM-8922: The Advanced Identity Cloud admin console now accepts ESV placeholders for the following federation fields:
-
Application ID
-
Application Secret
-
Well-Known Endpoint
-
Authorization Endpoint
-
User Info Endpoint
-
Token Endpoint
-
Issuer
-
-
IAM-8982[18]: Add event function for setting the query filter/select options of a select field.
-
IAM-9066: Added Tenant Auditor option to Advanced Identity Cloud admin console federation groups claim.
-
IAM-9099, IAM-9146, IAM-9167: Many table views now support column resizing and customization.
Fixes
-
IAM-5488: Terms and Conditions now respects target attribute in anchor tags.
-
IAM-6588: The Advanced Identity Cloud admin console now correctly displays journey status for journeys disabled and enabled using ESVs.
-
IAM-8887: Prevent browsers auto-filling passwords in user registration journeys.
-
IAM-8940: Managed identity number property now accepts float values.
-
IAM-8956: Deselecting the Personal Information option now disables the section containing the user avatar in hosted account pages.
-
IAM-9169: Fixed styling for responsive table layouts with sticky action column in Identities table views.
August 2025
29 Aug 2025
Version 18823.0
Enhancements
-
FRAAS-25919: You can now use the API to configure custom domains for the Advanced Identity Cloud admin console.
-
OPENIDM-21372: Advanced Identity Cloud now prevents access to the identity repository endpoint,
/openidm/repo. This prevents uncontrolled and potentially incompatible schema changes.
Fixes
-
AME-32756: Fixed an issue with policy evaluation returning results from a stale policy index cache.
-
FRAAS-26287: Advanced Identity Cloud now correctly authenticates the sender address for emails sent to Advanced Identity Cloud tenant administrators,
saas@pingidentity.com. -
OPENDJ-11634: Advanced Identity Cloud now prevents searches with many results and no applicable index from overloading the system.
26 Aug 2025
Version N/A
Key features
- Log event exporter (FRAAS-19963)
-
Advanced Identity Cloud now lets you export log event data to an external monitoring tool, such as an OpenTelemetry-compatible SIEM or Splunk. This helps you monitor events and troubleshoot issues in near real time.
Learn more in Stream logs to an external monitoring tool.
15 Aug 2025
Versions 18678.0, 18684.0
07 Aug 2025
Versions 18559.0, 18570.0
Fixes
-
FRAAS-25821[24]: Fixed an issue that prevented IP rules in the Proxy Connect add-on from being disabled.
-
OPENAM-24159: Fixed an issue with Identity Assertion nodes failing if there are more than one in a journey.
06 Aug 2025
Version 18550.0
Enhancements
-
FRAAS-24857: CNAME verification is no longer required when creating a custom domain.
-
FRAAS-26063: You can now override the
samlErrorPageUrl. To do so, configure an ESV variable namedesv-global-saml-error-page-urland set its value to your SAML error page URL. If you don’t set this variable, Advanced Identity Cloud uses the default value of/saml2/jsp/saml2error.jsp.
July 2025
28 Jul 2025
Versions 18435.0, 18444.0
No customer-facing features, enhancements, or fixes released.[19]
21 Jul 2025
Version 18347.0, 18351.0
No customer-facing features, enhancements, or fixes released.[19]
18 Jul 2025
Version 18331.0
Key features
- Try In SDK button (IAM-8618)
-
A Try In SDK button has been added to the Details page for Native / SPA applications. This lets developers quickly test SDKs with dynamic configuration code snippets.
- Custom WS-Fed applications (IAM-8261)
-
You can now create custom WS-Fed[20] applications for single sign-on (SSO).
Enhancements
-
FRAAS-25818: The built-in SMTP server in new tenants now has a limit of 10 emails per minute and a fixed email sender address with the format
noreply@<tenant-fqdn>. -
IAM-7581: Text wrapping in table views has been improved for readability.
-
IAM-8573: IDM now includes an endpoint to retrieve individual themes from the
/themerealmconfiguration using either anIDor a_queryFilterby name. This improves performance and ensures reliable theme loading, even on slow networks. -
IAM-8610: When you create an SSO application for Microsoft 365, the application now generates a signing certificate, which you can download or rotate as needed.
-
IAM-8633: You can now add, remove, and rearrange table columns for managed identities and application provisioning tables.
-
IAM-8925[1]: In Identity Governance, you can now configure actions that trigger automatically when a form first loads or when a user changes the value of a specific field.
-
IGA-3674[1]: A Wait node is now available for IGA workflows. This node pauses the workflow until a specified date and time, for example, if you need to seek approvals.
-
IGA-3700[1]: Improved UI for suspended requests in table and request view.
-
IGA-3742[1]: The form editor now includes icons in the list of fields in the left panel.
Fixes
-
IAM-8789: Managed identity modals now correctly handle both single-value and array-based enum types.
-
IAM-4397: Fixed an issue in the hosted journey pages where the prompt text for the Choice Collector node wasn’t fully visible and the default option wasn’t visible at all.
-
IAM-8632: Fixed an issue where validation errors were incorrectly displayed for pre-populated fields.
-
IAM-8871: The hosted account pages no longer freeze and throw an error when editing details if there are empty custom enum array values.
-
IAM-8902: The application username field in SAML 2.0 NameID flows is now correctly set to
uidinstead ofusername.
16 Jul 2025
Version 18295.0
Key features
- Monitor log entries in the admin console (FRAAS-25665)
-
Advanced Identity Cloud now provides a console for monitoring log entries in development and sandbox[1] environments. You can view, filter, and search log entries for specific log sources within a timeframe to quickly identify issues, track events, and ensure system security.
01 Jul 2025
Version 18170.0
Key features
- Policy binding for next-generation scripting (AME-26150)
-
The next-generation
policybinding lets you access the policy engine API and evaluate policies from within scripts. Thepolicybinding works in a similar way to the Request policy decisions for a specific resource API call. - Set Error Details node (AME-30968)
-
The Set Error Details node adds details to the JSON response when a journey ends in an error.
Enhancements
-
AME-31372: An Agent journey is now available by default in both Alpha and Bravo realms. The
Agentjourney makes it easier to integrate with Ping Identity agents and gateways. It validates the agent credentials with an Agent Data Store Decision node. -
AME-30050: You can now enable a next-generation script in the AM native admin console native console to run after a Dynamic Client Registration request is processed.
-
AME-30716: Removed
Failed to create SSO Tokenfrom logs at warning level. To observe these warnings, increase the log level to debug. -
AME-30801: The Inner Tree Evaluator node now has an optional Error Outcome that lets you capture exception details if an exception occurs during the evaluation of the child journey.
-
OPENAM-22467: Customers can now provide any value in the
typheader in JWTs. -
Greater control over journey session duration and authenticated session timeouts:
-
OPENAM-23265: The Set Session Properties node now lets you customize the Maximum Session Time and Maximum Idle Time of the session granted at the end of the journey.
-
OPENAM-23290: The new Update Journey Timeout node lets you update the timeout of the journey.
-
OPENAM-23291: The Email Suspend node now lets you configure the Suspend Duration in minutes. This duration overrides existing global or realm settings.
-
OPENAM-23515: You can now set the suspend duration in next-generation scripted decision nodes when suspending the journey.
-
-
OPENAM-23438: Following Webauthn Registration and Authentication, new information is added to the transient state.
-
OPENAM-20709: On successful authentication, the WebAuthn Authentication node now adds the UUID of the device (
webauthnDeviceUuid) and the name of the device (webauthnDeviceName) to the shared state. This lets you track the use of biometric authentication and the device used to authenticate.
Fixes
-
AME-30969: If the OIDC Claims Plugin Type in the OAuth 2.0 provider is set to
SCRIPTEDbut no script is selected, theuserinfoendpoint now returns thesubclaim, in compliance with the OIDC specification. Previously, theuserinfoendpoint returned an empty JSON object. If you still require this behavior, set theesv-scripting-legacynulloidcclaimsscriptbehaviourESV totrue. -
OPENAM-20749: For server-side OAuth 2.0 tokens, the /oauth2/introspect response can now overwrite the
issclaim of the introspectable token. To enable this behavior, set theesv-enable-oauth2-sync-refresh-token-issuerESV tofalse. -
OPENAM-22928: When agents authenticate to Advanced Identity Cloud, the session created no longer expires.
-
OPENAM-23334: You can now use the
mergeSharedandmergeTransientmethods to add nested objects toObjectAttributes. -
OPENAM-23519: Improved error handling during WebAuthn registration when the Android lock screen isn’t enabled.
Removed
- Modules and chains (AME-30762)
-
The legacy PingAM authentication mechanism using modules and chains is enabled by default in Advanced Identity Cloud but has never been supported. Modules and chains remain enabled but have been removed from the Advanced Identity Cloud admin console.
Modules and chains will be removed entirely in the near future. If you’re using them for authentication, you must migrate to nodes and trees as soon as possible.
Advanced Identity Cloud provides default journeys that replace the corresponding default modules and chains. Any default authentication processes that relied on modules and chains are unaffected by their removal.
June 2025
30 June 2025
23 Jun 2025
Version 18045.0
18 Jun 2025
Version 17994.0
Enhancements
-
FRAAS-25437: Tenant administrators with the
tenant-auditorrole can now use federated access to authenticate to Advanced Identity Cloud. -
IAM-3441: Added pagination to all list views.
-
IAM-7265: You can now right-click a node in the journey editor to access a context menu.
-
IAM-7266: Added an action bar to the journey editor that lets you deselect or delete currently selected nodes.
-
IAM-7580: Pages now span the full width of the screen, improving navigation and usability.
-
IAM-8260: Advanced Identity Cloud now supports multiple WS-Fed applications[20].
-
IAM-8640: The Release Notes link in Tenant Settings now opens the release notes for the tenant’s specific version.
-
IAM-8714[18]: You can now configure columns in the Identity Governance access review page.
-
IAM-6820: The Email Suspend node now provides a drop-down list of available email templates.
-
OPENIDM-21206[26]: Usernames and application names must now be unique, as enforced by the datastore.
Fixes
-
IAM-7413: The reCAPTCHA Enterprise node is now fully supported.
-
IAM-8489: Fixed an issue with the display of application logos in the hosted account pages.
-
IAM-8770: Fixed an issue with the calendar icon position in date fields.
-
IAM-8773: Fixed an issue where key actions such as realm login were blocked in older tenants with an unmodified original theme.
10 Jun 2025
Version 17889.0
Enhancements
-
ANALYTICS-868: The Tenant Admin Activity report has been changed to the Tenant Admin Initiated Managed Objects Changes report. The new report provides more detailed and business-friendly insights into changes made by tenant administrators:
-
Field names added, deleted, or modified.
-
Before and after values of changed attributes (if applicable).
-
Business-friendly entity name and entity type changes to custom attributes and custom objects.
-
Fixes
-
OPENAM-21783: Improved token management for OAuth 2.0 clients that override the Use Client-Side Access & Refresh Tokens setting. The OAuth 2.0 applications endpoint now correctly shows all tokens issued to these clients. Additionally, administrators can now successfully revoke any of the tokens issued to these clients.
06 Jun 2025
Version 17853.0
Enhancements
-
IAM-8405: You can now duplicate out-of-the-box reports.
-
IAM-8591: Dynamic sorting for report results. You can now sort report results directly in the Advanced Identity Cloud admin console after running a report.
-
Sorting is available only when the result set contains fewer than 10,000 rows.
-
Columns with complex data types (for example, JSON) can’t be sorted.
-
Downloaded reports reflect the original data order, not the sorted view from the Advanced Identity Cloud admin console.
-
06 Jun 2025
Version 17836.0
Fixes
-
FRAAS-25269: The IDC.CLI OAuth 2.0 client is now deprecated in existing tenants and no longer provisioned in new tenants. Use a service account instead.
03 Jun 2025
Versions 17804.0, 17821.0
No customer-facing features, enhancements, or fixes released.[19]
May 2025
30 May 2025
Version 17779.0
Key features
- Tenant auditors (IAM-8086)
-
Advanced Identity Cloud now lets you invite tenant auditors to access the Advanced Identity Cloud admin console. Tenant auditors can view settings, configuration, and data but cannot modify them.
- Tenant auditor role (FRAAS-24460)
-
Advanced Identity Cloud now supports a tenant auditor role with read-only access to ancillary APIs.
For new tenants, Advanced Identity Cloud doesn’t support non-global realm user access and OAuth2 client access to the ESV API. Access is deprecated for existing tenants.
23 May 2025
Versions 17709.0, 17713.0
Enhancements
-
FRAAS-25205: Consolidated
End User UI,Login UI,Administrator Registration UI, andAdministrator UIstatus page components into a singleAdministrator UIcomponent as they were all reporting the same service. -
OPENIDM-15771: You can now set locales in identity management scripts with the
_localeparameter. -
OPENIDM-17680: Advanced Identity Cloud now supports enumerations in string and number attributes of its identity schema. To make an attribute an enumeration, add
"enum" : [ "one", "two", "three" ]to the attribute. Advanced Identity Cloud requires create and update privileges to use one of the enumerated values. -
OPENIDM-19918: You can now choose whether synchronization detects identity array changes using _ordered or unordered comparisons. Set the
comparisonconfiguration property in the schema. Unordered JSON array comparison ignores the order of elements and can negate the need for certain custom scripts within mappings. Relationship and virtual property array fields default to unordered comparisons. All other fields default to ordered comparisons. -
OPENIDM-20023: RCS communication with Advanced Identity Cloud can now use stricter authorization. Learn more in Secure RCS access and Migration dependent features.
21 May 2025
Version 17680.0
Fixes
-
FRAAS-25256: Fixed an issue that was causing missing data in analytics dashboards.
-
OPENIDM-20995: Fixed an issue that prevented error reports during certain operations on groups or users. For example trying to remove a non-existing attribute or null value now correctly results in an exception message to the client if these operations are not supported by the target system.
13 May 2025
Versions 17581.0, 17584.0
No customer-facing features, enhancements, or fixes released.[19]
08 May 2025
Versions 17546.0, 17549.0
Enhancements
-
ANALYTICS-1004[22]: Support for custom attributes and relationships in the organization entity for advanced reports.
06 May 2025
Versions 17513.0, 17514.0
No customer-facing features, enhancements, or fixes released.[19]
Rapid channel features
This page links to early access documentation for features available in the rapid channel and not in the regular channel. As these features become available in the regular channel, we update the links to refer to the main body of the PingOne Advanced Identity Cloud documentation.
| These topics are draft documentation and subject to change. |
Rapid channel changelog archive
2025
28 Apr 2025
Versions 17434.0, 17436.0
No customer-facing features, enhancements, or fixes released.[19]
23 Apr 2025
Version 17384.0
Enhancements
-
IAM-987: Added support for enums (drop-down lists) to hosted account pages.
-
IAM-1116: Added support for enums (drop-down lists) to the Advanced Identity Cloud admin console.
-
IAM-2103: Added support for enums (drop-down lists) to hosted journey pages.
-
IAM-6822: Added the ability to manage cookie domains in the Advanced Identity Cloud admin console.
-
IAM-7412: Updated the password policy feature in the Advanced Identity Cloud admin console. Added the ability to specify a minimum substring length between 3 - 64 to use when validating passwords against user attribute values. The default is still 5 characters, but can now be reduced to as few as 3 characters to catch shorter string matches.
-
IAM-7794[18]: Added support for using custom identity objects in the form builder.
-
IAM-7919: Improved color contrast ratio of the Delete Account button text when focused.
-
IAM-7934: Improved color contrast ratio of date fields when focused.
-
IAM-7957: Improved color contrast ratio of the Deselect button text when focused.
-
IAM-7966: Improved color contrast ratio of In Progress text.
-
IAM-8016[18]: Allow form authors to specify a user filter when dynamic enums are selected.
-
IAM-8085: Updated the Add a Parameter reports modal to use entity attributes for input.
Fixes
-
FRAAS-15518: Fixed issue that prevented localization of Session timed out message in certain locales.
-
IAM-5834: Fixed a double-encoding issue in the SAML app that affected IdP-initiated sign on.
-
IAM-6796: Jobs are now prevented from being scheduled with frequencies that cause invalid date errors.
-
IAM-7855: Fixed a typo in the help text returned when there are no results to display.
-
IAM-8237: Corrected floating labels in the date picker in the hosted journey pages.
-
IAM-8361: The Save button in the Edit Bookmark application is now inactive while checking if the ESV exists.
-
IAM-8364: Fixed issues in SAML end-to-end scenarios.
-
IAM-8378: Fixed an issue that stripped HTML elements from email templates.
-
IAM-8403: Fixed border focus location and floating label issues in Tag fields.
-
IAM-8434: Fixed an issue that prevented duplication of new themes that contain special characters.
16 Apr 2025
Versions 17283.0, 17299.0
No customer-facing features, enhancements, or fixes released.[19]
08 Apr 2025
Versions 17178.0, 17186.0
Enhancements
-
OPENDJ-11175: The password validation mechanism has been enhanced to include checks for attribute values shorter than the
min-substring-length(the default is 5).For example, if the password contains
Bobfor a user named Bob, the password is rejected, even ifmin-substring-lengthis set to 5.
02 Apr 2025
Version 17111.0
28 Mar 2025
Versions 17072.0, 17079.0
Enhancements
-
ANALYTICS-846: You can now select the attribute type and value for report entity attributes.
-
ANALYTICS-983[22]: You can now use regular expression operators in Advanced Reporting.
21 Mar 2025
Key Features
- Custom attributes for user entity in Advanced Reports (ANALYTICS-863)[22][27]
-
When a tenant administrator modifies the
usersidentity object from the native console and adds a new custom attribute, the attribute is immediately available on the Create Report page. Administrators can use the custom attribute for their reports and filters.Learn more in Custom attributes for user objects.
20 Mar 2025
Versions 17002.0, 17015.0
No customer-facing features, enhancements, or fixes released.[19]
19 Mar 2025
Versions 16981.0, 16989.0
No customer-facing features, enhancements, or fixes released.[19]
17 Mar 2025
Version 16940.0
Key Features
- Tenant auditors (IAM-8086)
-
Advanced Identity Cloud now lets you invite tenant auditors to access the Advanced Identity Cloud admin console. Tenant auditors can view settings, configuration, and data but cannot modify them.
Enhancements
-
IAM-6996: Added the ability to create a specific OAuth 2.0 client when creating a connector server, rather than relying on the default RCSClient.
-
IAM-7109: You can now use an ESV to set the From Address in the email provider configuration.
-
IAM-7827/ANALYTICS-835[22]: In the analytics report editor in Advanced Reporting, you can now reorder columns by dragging and dropping them.
-
IAM-7841/ANALYTICS-840[22]: The reports page in Advanced Reporting is now a list view with pagination and search.
-
IAM-8321: In the journey editor, the node titles now wrap within the left nodes panel.
13 Mar 2025
Version 16885.0, 16887.0
No customer-facing features, enhancements, or fixes released.[19]
27 Feb 2025
Version 16747.0
Key Features
- Flow Control node (AME-30017)
-
You can now randomly direct users down different journey paths. Learn more in Flow Control node.
- OIDC application journeys (AME-28650)
-
You can now configure OAuth 2.0 / OIDC client applications to redirect authentication requests to a specified journey. Learn more in Client application journeys.
Enhancements
-
AME-27705: Extend the
utilsbinding for all next-generation scripts to support low-level cryptographic operations. These operations include encryption, decryption, hashing, signing, verification, and key generation.Find more information in Access utility functions.
-
AME-28780: Added an IDM policy condition that can assert conditions against an IDM resource type such as user identities.
-
AME-28954: Modified the import metadata endpoint to support updating signing and encryption certificates for existing SAML service providers (SPs) without requiring the deletion or recreation of SP configurations.
-
AME-29307: You can now use DER-encoded certificates for OAuth 2.0 client authentication.
-
AME-29810: The realm default authentication service can no longer be a journey with
mustRunenabled. Also,mustRuncan no longer be enabled on journeys that are set as the realm default authentication service. -
AME-29835: Configuration Provider Node scripts can now use the next-generation scripting engine, which gives them access to common bindings such as
openidmandhttpClient. -
AME-30076: New
getApplicationId()method provides a consistent way to retrieve the application ID from both SAML and OAuth 2.0 applications.
Fixes
-
AME-29504: The
scriptNameandloggerbindings in library scripts referenced the same default script name and ID. Their previous behavior has now been restored by inheriting values from the referencing script. -
AME-29965: The Configuration Provider node now works with the Inner Tree Evaluator for nested inner journeys.
-
AME-30377: The following two warning level log messages have been reduced to debug level because they’re rarely useful and appear frequently, drowning out more useful log entries:
-
No users have been identified. -
Ignoring the new universal id as that is empty and the current universal id is already set.
-
-
OPENAM-22120: Back-channel logout tokens now include the
expclaim. -
OPENAM-23077: The
access_tokenendpoint now responds with the correct error code when thecode_verifierisn’t supplied (for example,invalid_grant).
20 Feb 2025
Version 16676.0
Key features
- Advanced sync (IAM-8090)
-
Many of the mapping synchronization features available in the IDM admin console are now exposed in the Advanced Sync tab when viewing an application. You can create additional mappings between applications or between applications and identity profiles.
Enhancements
-
IAM-7967[18]: Added an image description for the approvals Low Priority icon.
-
IAM-7977: Improved the font color contrast ratio of the email address displayed in Advanced Identity Cloud admin console user profiles.
-
IAM-8053: The Advanced Identity Cloud end-user UI can now use
defaultTextvalue as a fallback value when the actual value of a field returns empty. -
OPENIDM-20139: Applications can now use
postActionscripts for theONBOARDaction.
Fixes
-
IAM-7719[18]: Users are now redirected back to the compliance Policy Rules tab after creating or editing a policy rule.
04 Feb 2025
Version 16508.0
Enhancements
-
IAM-4692: Managed identity boolean fields now use a checkbox instead of a toggle.
-
IAM-6581: SAML 2.0 application journeys can now be configured in the Advanced Identity Cloud admin console.
-
IAM-7248[18]: In IGA sources, the
displayNameandlogocan now be obtained from the CDN. -
IAM-7874[18]: The Governance > Requests > Settings tab now lets you activate or deactivate Governance LCM.
31 Jan 2025
Versions 16460.0, 16466.0
No customer-facing features, enhancements, or fixes released.[19]
29 Jan 2025
Versions 16437.0, 16441.0
No customer-facing features, enhancements, or fixes released.[19]
24 Jan 2025
Versions 16410.0, 16412.0
Enhancements
-
FRAAS-23002: Improvements to OATH support for MFA authenticators
-
Update the default OATH shared secret length from 32 to 40 for existing and new tenants so that tenant administrators can use Google Authenticator with MFA when signing on using their Advanced Identity Cloud native accounts.
-
Make the OATH shared secret length configurable (using a support request) to support other MFA authenticators.
-
23 Jan 2025
Versions 16386.0, 16388.0
No customer-facing features, enhancements, or fixes released.[19]
22 Jan 2025
Versions 16368.0, 16376.0
No customer-facing features, enhancements, or fixes released.[19]
20 Jan 2025
Versions 16345.0, 16348.0
15 Jan 2025
Versions 16294.0, 16297.0
Enhancements
-
FRAAS-23375: You can now obtain the HTTP client location from the
X-Client-City&X-Client-City-Lat-LongHTTP headers in Advanced Identity Cloud scripts and journeys.X-Client-Citycontains the name of the city from which the request originated, for example,Mountain Viewfor Mountain View, California. There is no canonical list of valid values for this variable. The city names can contain US-ASCII letters, numbers, spaces, and the following characters:"!#$%&'*+-.^_`|~".X-Client-City-Lat-Longcontains the latitude and longitude of the city from which the request originated, for example,37.386051,-122.083851for a request from Mountain View.
14 Jan 2025
Versions 16276.0, 16278.0
No customer-facing features, enhancements, or fixes released.[19]
10 Jan 2025
Versions 16216.0, 16229.0
Enhancements
-
IAM-6833: Made existing synchronization tokens editable for incremental reconciliations.
-
IAM-7223[18]: Added the ability to set user, role, organization, application, or entitlement objects to provide predefined values for select and multiselect fields in request forms.
03 Jan 2025
Version 15989.0
Enhancements
-
ANALYTICS-459[28]: Report query data is now retained for 30 days for customers using OOTB reports and 90 days for customers with Advanced Reporting[29].
-
ANALYTICS-495[28]: Replace
emailwithusernamein User Last Login report. -
ANALYTICS-817[28][22]: Report authors can now query on "Password Last Changed Time" for user entity.
-
ANALYTICS-818[28][22]: Report authors can now query on "Password Expiration Time" for user entity.
Fixes
-
ANALYTICS-474[28]: The User Journey Stats report now provides aggregates by outcome in the report result when more than one outcome is selected.
-
ANALYTICS-837[28]: The User Count by Status report now provides aggregates by status in the report result when more than one outcome is selected
-
ANALYTICS-585[28][22]: Remove Report Admin and Report Owner group selection when creating a new report.
2024
17 Dec 2024
Version 16028.0
Enhancements
-
OPENDJ-9287: The password validation mechanism has been enhanced to include checks for portions of attribute values within passwords. This improvement ensures that even partial matches between portions of passwords and portions of attribute values are identified and restricted, thereby enhancing security.
For example, if the password is
abcdefand the attribute value isabcdef123, the password is rejected. Similarly, if the password isabcdefAZERTYand the attribute value isabcdef123, the password is rejected.
16 Dec 2024
Version 15989.0
This release reintroduces many features, enhancements, and fixes previously present in reverted versions.
Key features
- PingOne Authorize node (TNTP-183)
-
Use this node to send a decision request to a specified decision endpoint in your PingOne Authorize environment.
- PingOne node improvements (SDKS-3468)
-
- PingOne Create, Identify, and Delete Nodes
-
The following PingOne nodes are now available:
- PingOne Identity Match node
-
Use the PingOne Identity Match node to identify if a user exists both in the user repository and in PingOne, using defined attributes.
- PingOne Create User node
-
Create new users in the PingOne platform using the PingOne Create User node. Create users based on an existing user’s properties or choose to create the user anonymously. For example, when used in conjunction with PingOne Verify.
- PingOne Delete User node
-
Delete users from the PingOne platform with the PingOne Delete User node.
- PingOne Verify nodes
-
Use the following PingOne Verify nodes in conjunction with the PingOne Identity Match node, PingOne Create User node, and PingOne Delete User node to create a seamless verification process in your journey:
- PingOne Verify Evaluation node
-
Leverage PingOne Verify to initiate or continue a verification transaction with the PingOne Verify Evaluation Node.
- PingOne Verify Completion Decision node
-
Determine the completion status of the most recent identity verification transaction for an end user.
Use before the PingOne Verify Evaluation node to determine the status of the verification process or after the PingOne Verify Evaluation node using a script to evaluate the transaction.
For example, you can evaluate if the transaction was completed using a passport and route your journey accordingly.
Use these nodes in place of the PingOne Verify Marketplace nodes. - reCAPTCHA Enterprise node (SDKS-3322)
-
The reCAPTCHA Enterprise node node adds Google reCAPTCHA Enterprise support to your journeys.
- SAML application journeys (AME-27850)
-
Added support for SAML application journeys with a new setting on the remote SP. Configure a specific authentication journey that always runs for users authenticating with your SAML 2.0 app, regardless of existing sessions or configured authentication context.
Learn more in Configure a SAML 2.0 application journey.
- Set Failure Details node (AME-27871)
-
Use the Set Failure Details node to configure a localized error message on journey failure. You can also configure extra details in the response body of the failure request.
- Set Success Details node (OPENAM-12335)
-
Use the Set Success Details node to add additional details to the success response of a journey.
- UI support for managing certificates (IAM-5813)
-
You can now use the Advanced Identity Cloud admin console to generate CSRs and upload SSL certificates in your tenant environments.
Learn more in Manage server certificates using the admin console.
Enhancements
-
AME-26050: You can now create Next-generation Policy Condition scripts that have access to all common bindings, such as
openidmandhttpClient. Additionally, some existing bindings have been wrapped to improve usability in scripts. -
AME-28228: OAuth 2.0 audit logs now include the OAuth 2.0 client ID and any journey associated with the client.
-
AME-29009: When using the new FIDO Metadata Service, if you link to the FIDO metadata using a URL, Advanced Identity Cloud periodically downloads and updates the latest FIDO metadata based on the
nextUpdatedate specified in the downloaded data. -
AME-29093: Added configuration for integration with WebAuthn Metadata Services (such as the FIDO Metadata Service). This includes a realm-level WebAuthn Metadata service and a new FIDO Certification Level configuration attribute in the WebAuthn Registration Node.
-
FRAAS-22321: You can now obtain the HTTP client location from the
X-Client-RegionHTTP header within your scripts and journeys. TheX-Client-Regionheader contains the country (or region) associated with the client’s IP address in the form of a Unicode CLDR region code, such asUSorFR. For most countries, these codes correspond directly to ISO-3166-2 codes. -
FRAAS-23073: The SAML scripting adapter now lets scripts access
org.forgerock.http.protocol.*. -
IAM-3323: You can now use XPath transformation functions with additional Workday application template attributes.
-
IAM-4540: You can now change the border color of a selected input field in journey and end-user pages.
-
IAM-6397: The Advanced Identity Cloud admin console now lets you page through the list of OAuth 2.0 client profiles.
-
OPENAM-23109: During a WebAuthn registration flow, if Store data in transient state is enabled, the Authenticator Attestation Global Unique Identifier (AAGUID) is now added to the node state under the
webauthnDatakey.
Fixes
-
AME-28016: When an invalid redirect URI is provided to the
/parendpoint, the URI mismatch error is nowredirect_uri_mismatchinstead ofinvalid_request. -
AME-28017: Advanced Identity Cloud now accepts the requested OAuth 2.0 endpoint as a valid JWT audience claim, as per RFC 7519 and RFC 9126.
-
AME-29170: On LDAP Decision node login failure, stack traces are now logged at
debuglevel. -
AME-29965: The Configuration Provider node now works with the Inner Tree Evaluator node for nested inner journeys.
-
IAM-1782: Long gateway and agent IDs no longer overflow in the Advanced Identity Cloud admin console.
-
IAM-7523[18]: A user receiving a forwarded fulfillment task now has permission to approve or reject the task.
-
IAM-7537[18]: Governance functionality is now only shown for the
alpharealm. -
IAM-7689[18]: The Advanced Identity Cloud admin console now displays the Assigned To value in the task list for a user assigned to a role who receives a forwarded fulfillment task.
-
OPENAM-18252: Journeys acting on multiple identities now successfully update
universalIdin the journey context during the authentication flow. -
OPENAM-20314: Added the ability to indicate whether an OIDC provider doesn’t return a unique value for the
subclaim. -
OPENAM-22966: Social IDPs now support NONE as a client authentication method. This option should be used if the provider doesn’t require client authentication at the token endpoint.
03 Dec 2024
02 Dec 2024
Version 15824.0
| This version has been reverted and all associated changes withdrawn. |
This release reintroduces many features, enhancements, and fixes previously present in reverted versions.
Key features
- PingOne Authorize node
-
Use this node to send a decision request to a specified decision endpoint in your PingOne Authorize environment.
- PingOne Create, Identify, and Delete Nodes
-
The following PingOne nodes are now available:
- PingOne Identity Match node
-
Use the PingOne Identity Match node to identify if a user exists both in the user repository and in PingOne, using defined attributes.
- PingOne Create User node
-
Create new users in the PingOne platform using the PingOne Create User node. Create users based off of an existing user’s properties or choose to create the user anonymously. For example, when used in conjunction with PingOne Verify.
- PingOne Delete User node
-
Delete users from the PingOne platform with the PingOne Delete User node.
- PingOne Verify Nodes
-
Use the following PingOne Verify nodes in conjunction with the PingOne Identity Match node, PingOne Create User node, and PingOne Delete User node to create a seamless verification process in your journey:
- PingOne Verify Evaluation node
-
Leverage PingOne Verify to initiate or continue a verification transaction with the PingOne Verify Evaluation Node.
- PingOne Verify Completion Decision node
-
Determine the completion status of the most recent identity verification transaction for an end user.
Use before the PingOne Verify Evaluation node to determine the status of the verification process or after the PingOne Verify Evaluation node using a script to evaluate the transaction.
For example, you can evaluate if the transaction was completed using a passport and route your journey accordingly.
Use these nodes in place of the PingOne Verify Marketplace nodes. - reCAPTCHA Enterprise node
-
The reCAPTCHA Enterprise node node adds Google reCAPTCHA Enterprise support to your journeys.
- SAML application journeys (AME-27850)
-
Added support for SAML application journeys with a new setting on the remote SP. Configure a specific authentication journey that always runs for users authenticating with your SAML 2.0 app, regardless of existing sessions or configured authentication context.
Learn more in Configure a SAML 2.0 application journey.
- Set Failure Details node (AME-27871)
-
Use the Set Failure Details node to configure a localized error message on journey failure. You can also configure extra details in the response body of the failure request.
- Set Success Details node (OPENAM-12335)
-
Use the Set Success Details node to add additional details to the success response of a journey.
Enhancements
-
AME-26050: You can now create Next-generation Policy Condition scripts that have access to all common bindings, such as
openidmandhttpClient. Additionally, some existing bindings have been wrapped to improve usability in scripts. -
AME-28228: OAuth 2.0 audit logs now include the OAuth 2.0 client ID and any journey associated with the client.
-
AME-29009: When using the new FIDO Metadata Service, if you link to the FIDO metadata using a URL, Advanced Identity Cloud periodically downloads and updates the latest FIDO metadata based on the
nextUpdatedate specified in the downloaded data. -
AME-29093: Added configuration for integration with WebAuthn Metadata Services (such as the FIDO Metadata Service). This includes a realm-level WebAuthn Metadata service and a new FIDO Certification Level configuration attribute in the WebAuthn Registration Node.
-
AME-29769: The Social Provider Handler node has a new configuration option, Store Tokens, that allows access and refresh tokens to be stored in the transient state.
-
FRAAS-22321: You can now obtain the HTTP client location from the
X-Client-RegionHTTP header within your scripts and journeys. TheX-Client-Regionheader contains the country (or region) associated with the client’s IP address in the form of a Unicode CLDR region code, such asUSorFR. For most countries, these codes correspond directly to ISO-3166-2 codes. -
IAM-3323: You can now use XPath transformation functions with additional Workday application template attributes.
-
IAM-4540: You can now change the border color of a selected input field in journey and end-user pages.
-
OPENAM-23109: During a WebAuthn registration flow, if Store data in transient state is enabled, the Authenticator Attestation Global Unique Identifier (AAGUID) is now added to the node state under the
webauthnDatakey.
Fixes
-
AME-28016: When an invalid redirect URI is provided to the
/parendpoint, the URI mismatch error is nowredirect_uri_mismatchinstead ofinvalid_request. -
AME-28017: Advanced Identity Cloud now accepts the requested OAuth 2.0 endpoint as a valid JWT audience claim, as per RFC 7519 and RFC 9126.
-
AME-28906: The stack trace of an authentication exception generated on login failure is now logged only when
debuglevel logging is enabled. -
AME-29170: On LDAP Decision node login failure, stack traces are now logged at
debuglevel. -
IAM-7523[18]: A user receiving a forwarded fulfillment task now has permission to approve or reject the task.
-
IAM-7537[18]: Governance functionality is now only shown for the
alpharealm. -
OPENAM-18252: Journeys acting on multiple identities now successfully update
universalIdin the journey context during the authentication flow. -
OPENAM-20314: Added the ability to indicate whether an OIDC provider doesn’t return a unique value for the
subclaim. -
OPENAM-22966: Social IDPs now support
NONEas a client authentication method. Use this option if the provider doesn’t require client authentication at the token endpoint.
26 Nov 2024
25 Nov 2024
Version 15770.0
| This version has been reverted and all associated changes withdrawn. |
Enhancements
-
FRAAS-22321: You can now obtain the HTTP client location from the
X-Client-RegionHTTP header within your scripts and journeys. TheX-Client-Regionheader contains the country (or region) associated with the client’s IP address in the form of a Unicode CLDR region code, such asUSorFR. For most countries, these codes correspond directly to ISO-3166-2 codes.
21 Nov 2024
Version 15726.0 (supplementary)
| This version has been reverted and all associated changes withdrawn. |
Key features
- PingOne Create, Identify, and Delete Nodes [30]
-
The following PingOne nodes are now available:
- PingOne Identity Match node
-
Use the PingOne Identity Match node to identify if a user exists both in the user repository as well as in PingOne, using defined attributes.
- PingOne Create User node
-
Create new users in the PingOne platform using the PingOne Create User node. Create users based off of an existing user’s properties or choose to create the user anonymously. For example, when used in conjunction with PingOne Verify.
- PingOne Delete User node
-
Delete users from the PingOne platform with the PingOne Delete User node.
- PingOne Verify Nodes [30]
-
Use the following PingOne Verify nodes in conjunction with the PingOne Identity Match node, PingOne Create User node, and PingOne Delete User node to create a seamless verification process in your journey:
- PingOne Verify Evaluation node
-
Leverage PingOne Verify to initiate or continue a verification transaction with the PingOne Verify Evaluation Node.
- PingOne Verify Completion Decision node
-
Determine the completion status of the most recent identity verification transaction for an end user.
Use before the PingOne Verify Evaluation node to determine the status of the verification process, or after the PingOne Verify Evaluation node using a script to evaluate the transaction.
For example, you can evaluate if the transaction was completed using a passport and route your journey accordingly.
Use these nodes in place of the PingOne Verify Marketplace nodes. - reCAPTCHA Enterprise node [30]
-
The reCAPTCHA Enterprise node node adds Google reCAPTCHA Enterprise support to your journeys.
20 Nov 2024
Version 15726.0
| This version has been reverted and all associated changes withdrawn. |
Key features
- Set Success Details node (OPENAM-12335)
-
Use the Set Success Details node to add additional details to the success response of a journey.
- Set Failure Details node (AME-27871)
-
Use the Set Failure Details node to configure a localized error message on journey failure. You can also configure extra details in the response body of the failure request.
Enhancements
-
AME-29769: The Social Provider Handler node has a new configuration option, Store Tokens, that allows access and refresh tokens to be stored in the transient state.
-
AME-29009: When using the new FIDO Metadata Service, if you link to the FIDO metadata using a URL, Advanced Identity Cloud periodically downloads and updates the latest FIDO metadata based upon the
nextUpdatedate specified in the downloaded data. -
AME-29093: Added configuration for integration with WebAuthn Metadata Services (such as the FIDO Metadata Service). This includes a realm-level WebAuthn Metadata service and a new FIDO Certification Level configuration attribute in the WebAuthn Registration Node.
-
AME-26050: You can now create Next-generation Policy Condition scripts that have access to all common bindings, such as
openidmandhttpClient. Additionally, some existing bindings have been wrapped to improve usability in scripts. -
OPENAM-23109: During a WebAuthn registration flow, if Store data in transient state is enabled, the Authenticator Attestation Global Unique Identifier (AAGUID) is now added to the node state under the
webauthnDatakey.
Fixes
-
AME-28016: When an invalid redirect URI is provided to the
/parendpoint, the URI mismatch error is nowredirect_uri_mismatchinstead ofinvalid_request. -
AME-28017: Advanced Identity Cloud now accepts the requested OAuth 2.0 endpoint as a valid JWT audience claim, as per RFC 7519 and RFC 9126.
-
AME-28906: The stack trace of an authentication exception generated on login failure is now logged only when
debuglevel logging is enabled. -
AME-29170: On LDAP Decision node login failure, stack traces are now logged at
debuglevel. -
OPENAM-18252: Journeys acting on multiple identities now successfully update
universalIdin the journey context during the authentication flow. -
OPENAM-22966: Social IDPs now support
NONEas a client authentication method. Use this option if the provider doesn’t require client authentication at the token endpoint. -
OPENAM-20314: Added the ability to indicate whether an OIDC provider doesn’t return a unique value for the
subclaim.
19 Nov 2024
Versions 15711.0, 15715.0
No customer-facing features, enhancements, or fixes released.[19]
18 Nov 2024
Versions 15703.0, 15708.0
No customer-facing features, enhancements, or fixes released.[19]
15 Nov 2024
Versions 15687.0, 15696.0, 15699.0
No customer-facing features, enhancements, or fixes released.[19]
06 Nov 2024
Version 15572.0
Key features
- Configure journey to always run[31] (AME-27848)
-
Added a new setting for journeys to always run regardless of existing user sessions.
Learn more in Configure an authentication journey to always run.
- SAML application journeys (AME-27850)
-
Added support for SAML application journeys with a new setting on the remote SP. Configure a specific authentication journey that always runs for users authenticating with your SAML 2.0 app, regardless of existing sessions or configured authentication context.
Learn more in Configure a SAML 2.0 application journey.
- SAML application script binding[31] (AME-28012)
-
Added a new
samlApplicationbinding for querying the SAML 2.0 authentication request properties and IdP and SP configuration attributes.Learn more in Query SAML application and authentication request.
- Suspend and resume journeys (OPENAM-21806)
-
Next-generation decision node scripts can now use the new
action.suspend()method to suspend the current authentication session and send a message to the user. Implement custom logic with the resume URI, for example, to send an email or SMS using the HTTP client service.Learn more in Suspend and resume journeys.
Enhancements
-
AME-27074: Added a new
configProviderScriptaction to each authentication node endpoint to generate a configuration provider template script, for example:authentication/authenticationtrees/nodes/MessageNode?_action=configProviderScript. -
AME-28258: Added a new "webAuthnExtensions" input to the WebAuthn Registration and Authentication nodes. This can be set via a Scripted Decision node. It is expected to contain a map of extension name to input. Output is currently not available.
-
AME-28384: The outcome of a Scripted Decision node can now also be a
CharSequencetype. -
AME-28777: The refresh token grace period now applies to both client-side refresh tokens and server-side refresh tokens.
-
AME-29157: Authentication nodes with limited possible outcomes are now available to the Configuration Provider node, including:
The Identity Assertion node, Push Wait node, and Enable Device Management node nodes with fixed outcomes are also now available to the Configuration Provider node.
-
OPENAM-22601: You can now use the next-generation script binding,
utils, to generate secure random numbers. -
OPENAM-22811: NodeState has two new methods:
mergeShared(Map<String, Object>)andmergeTransient(Map<String, Object>). Use them to merge keys into the shared/transient state, including "objectAttributes" keys.
Fixes
-
AME-25491: The Configuration Provider node script now correctly reads node state after an inner tree callback.
-
AME-28786: Removed several unused UI properties from default social identity provider profiles.
-
AME-29027: WebAuthN attestations containing a self-signed root CA are now rejected instead of silently removed.
-
OPENAM-22465: Fixed error to return
invalid_resource_uriwhen request_uri client doesn’t match request parameter client in PAR authorise request. -
OPENAM-22675: In next-generation scripting, you can now set a default name correctly when creating a NameCallback.
-
OPENAM-22688: Fixed Page node localization to default to correct locale when the incoming
accepted-languageheader doesn’t match the node’s language configuration.
29 Oct 2024
Versions 15466.0, 15472.0
17 Oct 2024
Versions 15335.0, 15337.0
No customer-facing features, enhancements, or fixes released.[19]
15 Oct 2024
Versions 15310.0, 15312.0
No customer-facing features, enhancements, or fixes released.[19]
14 Oct 2024
Version 15300.0
Enhancements
-
IAM-7187: Integration of SAP app template with IDM scripts.
-
IAM-7243[18]: Added text field to utilities category in IGA access request forms.
20 Sept 2024
Versions 15044.0, 15052.0
Key features
- Support for LINE as a social identity provider (AME-28672)
-
You can now configure a social provider authentication with LINE Login when signing in from a browser. There is a separate configuration for authenticating from a mobile app.
Learn more in Social authentication.
- Identity Governance request and approval forms[18] (IAM-6358)
-
Identity Governance now lets you create request and approval forms to make it easier for end users to request access to applications.
Learn more in Identity Governance forms.
16 Sept 2024
Version 14975.0
Key features
- Additional cloud connectors
-
The following connectors are now bundled with Advanced Identity Cloud:
-
AWS IAM Identity Center Connector v1.5.20.23 (OPENIDM-20038)
-
Box Connector v1.5.20.23 (OPENIDM-20367)
Learn more in the ICF documentation.
-
13 Sept 2024
Version 14962.0
Key features
- Advanced Reporting[29] (ANALYTICS-763)
-
Advanced Identity Cloud now offers Advanced Reporting to let you create custom reports on activity in your tenant environments. You can query a number of metrics to create useful reports for your company.
Learn more in Advanced Reporting.
09 Sept 2024
Versions 14868.0, 14888.0
Key features
- Scripted SAML 2.0 NameID values(AME-25921)
-
The NameID mapper script lets you customize SAML 2.0 NameID values per application.
- Set State node (AME-26443)
-
The Set State node lets you add attributes to the journey state.
- Http Client service (AME-27936)
-
The new Http Client service lets you create named instances that you can reference from a next-generation script to make mTLS connections to external services.
Learn more in Access HTTP services.
- Enable Device Management node (SDKS-2919)
-
The new Enable Device Management node lets end users manage devices from their account.
Enhancements
-
FRAAS-21728: Updated the cookie domain API to add default values for GET requests where cookie domain values haven’t been overridden by a PUT request. The default values are derived from the existing tenant cookie domain configuration, so are backward compatible.
-
AME-26594: Added secrets API binding to all next-generation script contexts.
-
AME-27129: Added option to exclude client certificate from SAML hosted SP metadata.
-
AME-27792: Added
AM-TREE-LOGIN-COMPLETEDaudit log event that outputs aresultofFAILED. when a journey ends with an error. -
AME-27839: Added the ability to specify connection and response timeouts for Http Client service instances.
-
AME-28008: You can now disable certificate revocation checks, or all certificate checks entirely, on your Http Client service instances.
Fixes
-
OPENAM-15410: Fixed an issue that prevented customization of claims if
profileandopenidscopes are requested. -
OPENAM-20609: Fixed inconsistent error message when generating access token using refresh token after changing username.
-
OPENAM-21974: Adds an OAuth 2.0 client configuration for the new version of the LinkedIn provider.
-
OPENAM-22298: Log unretrieved SP and IdP descriptors in SAML2 Authentication node.
29 Aug 2024
Version 14741.0
Key features
- DocuSign application template (IAM-6194)
-
The DocuSign application lets you manage DocuSign service accounts and synchronize DocuSign accounts and Advanced Identity Cloud identities.
Enhancements
-
IAM-6493: The PingOne application template now supports specifying an LDAP gateway.
-
IAM-6868: Added screen reader label to end-user access approval button.
-
IAM-6870: Added screen reader label to end-user access request button.
-
IAM-6880: Added a toggle in the hosted pages journey settings to disable the error heading fallback that displays if there is no heading in the page content. (FORGEROCK-1582)
21 Aug 2024
Version 14626.0
Key features
- BeyondTrust application template (IAM-6492)
-
The BeyondTrust application lets you manage and synchronize data from Advanced Identity Cloud to BeyondTrust.
02 Aug 2024
Versions 14410.0, 14417.0
19 Jul 2024
Version 14225.0
Key features
- Adobe Admin Console application template (IAM-6195)
-
The Advanced Identity Cloud Adobe Admin Console application lets you manage users, groups, and user group memberships between Adobe Admin Console and Advanced Identity Cloud.
02 Jul 2024
Version 14013.0
Fixes
-
FRAAS-20970: The
/monitoring/logsendpoint now returns anX-Ratelimit-Limitheader with a fixed value of 60. Previously, the value was misleading due to the way it was calculated when scaling an environment’s resources. TheX-Ratelimit-Remainingheader continues to report the number of requests that may be sent before receiving a rate limited response.
27 Jun 2024
Versions 13964.0, 13966.0
Key features
- Additional cloud connectors
-
The following connectors are now bundled with Advanced Identity Cloud:
-
Adobe Admin Console connector (OPENIDM-19843)
-
DocuSign connector (OPENIDM-20190)
For more information, refer to the ICF documentation.
-
Fixes
-
OPENIDM-20142: Resolved a communication failure between Advanced Identity Cloud and RCS instances that could result in a prolonged failure to activate remote connectors.
Changed functionality
-
OPENIDM-20178: You can’t use scope private fields in query filters. For more information, refer to link:Security Advisory #202402.
24 Jun 2024
Versions 13937.0
Key features
- Product name change for Identity Cloud (FRAAS-20178)
-
To align ForgeRock products with Ping family names, ForgeRock Identity Cloud has been renamed to PingOne Advanced Identity Cloud. Name and logo changes have been updated throughout the user interfaces, and documentation updates will occur when the UI changes are released to the regular channel.
Enhancements
-
IAM-4785: Synchronize only the modified properties on a target source during reconciliation of applications.
-
IAM-5237[18]: Add ability for B2B business partners to certify access for their users using organizational-based certification.
-
IAM-5487: Correlation rules moved to the top of the reconciliation settings page.
-
IAM-5629[18]: Add ability to create scoping rules in Identity Governance.
-
IAM-6231: Scripted Decision Node now updates the list of scripts when a script is added or edited.
-
IAM-6544[18]: Add reviewer column to administrator list view of compliance violations.
Fixes
-
IAM-6135: ESV values containing accents get corrupted by encoding process.
-
IAM-6562: Label duplicated for OAuth 2.0 access token and ID token endpoints.
-
IAM-6669[18]: Badge count of violations in end-user navigation doesn’t update when an action is performed.
18 Jun 2024
Versions 13896.0, 13900.0
Key features
- PingOne Protect nodes[32] (TNTP-180)
-
The new PingOne Protect nodes replace the deprecated PingOne Protect Marketplace nodes.
Fixes
-
FRAAS-20604: Removed superfluous AM metrics related to token store internals:
-
am_cts_connection_count -
am_cts_connection_seconds -
am_cts_connection_seconds_total -
am_cts_connection_state -
am_cts_reaper_cache_size -
am_cts_reaper_deletion -
am_cts_reaper_deletion_count -
am_cts_reaper_deletion_total
-
-
FRAAS-20786: Fix promotion issue where an attempt was made to delete an already deleted application.
12 Jun 2024
Version 13848.0
Key features
- New utility binding available for scripting (AME-25519)
-
You can now use a new utility binding in your scripts to access several common utility classes. For example, the utility binding includes classes for generating random UUIDs and for base64 encoding and decoding.
Enhancements
-
AME-26199: Added the ability to set additional claims, including non-registered claims, during JWT assertion and generation, as per the specification.
-
AME-26820: Provided library scripts with access to all common script bindings.
-
AME-26993: Enhanced secret mapping for agents. Updating a secret label identifier value now causes any corresponding secret mapping for the previous identifier to also be updated, provided no other agent shares that secret mapping. If another agent shares the secret mapping, Advanced Identity Cloud creates a new secret mapping for the updated identifier and copies its aliases from the previously shared secret mapping.
-
AME-27346: Renamed Secret ID Identifier to Secret Label Identifier in the SAML remote entity provider configuration.
-
AME-27478: Renamed Client ID Token Public Encryption Key property to ID Token Encryption Public Key in the OAuth 2.0 client configuration.
-
AME-27775: Added scripting thread pool metrics per script context.
-
OPENAM-16564: Enabled next-generation scripts to access the cookies in incoming requests.
-
OPENAM-21800: Added page node functionality to next-generation scripts.
-
OPENAM-21933: Enabled auto-encoding of the
httpClientform body in next-generation scripts.
Fixes
-
FRAAS-19461: Fixed an issue where large audit logs could be missing from IGA events and processing.
-
OPENAM-21748: Restored the missing
getwrapper function forHiddenValueCallbackin next-generation scripting. -
OPENAM-21864: Fixed an issue that prevented setting the tracking cookie to resume a journey after returning from a redirect flow.
-
OPENAM-21897: Corrected inconsistent results from the policy
evaluateTreeendpoint. -
OPENAM-21951: Enabled setting of the
selectedIndexproperty in aChoiceCallbackin next-generation scripts. -
OPENAM-22181: Corrected an issue with UMA
approveandapproveAllrequests failing.
05 Jun 2024
Version 13760.0
Enhancements
-
FRAAS-20048: Configuration promotions can now be rolled back using the API. An environment can be rolled back successively to revert as many previous promotion changes as needed.
This feature can’t be used in sandbox environments; a promotion or a rollback can only be run between development, UAT[2], staging, and production environments.
22 May 2024
Versions 13570.0
Key features
- Oracle E-Business Suite app template (IAM-6342)
-
The Oracle E-Business Suite (EBS) application lets you manage and synchronize accounts between EBS and Advanced Identity Cloud.
Enhancements
-
IAM-6376: In the applications rules tab, you can now configure custom logic to perform specific actions, such as sending an email, when an account is successfully created or updated.
-
IAM-6380: In the applications rules tab, you can now use the provisioning failure rule to configure custom logic to perform specific actions when provisioning fails.
20 May 2024
Version 13528.0
03 May 2024
Key features
- Webex application template (IAM-5234[34])
-
The Advanced Identity Cloud Webex application lets you manage and synchronize data between Webex Control Hub and Advanced Identity Cloud.
- Epic EMP application template (IAM-2407)
-
The Epic EMP application lets you manage and synchronize data between Epic EMP and Advanced Identity Cloud.
Enhancements
-
IAM-2653: Configure object properties with user-friendly display names.
-
IAM-3857: Application list view displays enabled/disabled status of enterprise apps.
-
IAM-5913[18]: Create custom access request workflows.
17 Apr 2024
Version 13218.0
Key features
- Event-based certification[18] (IAM-5148)
-
Identity Governance now allows tenant administrators to configure certifications that are triggered by specific governance events, a process referred to as event-based certification. This method offers faster certification resolution compared to scheduled—and often lengthy—campaigns spanning weeks or months and involving numerous applications, intricate rules, and hundreds of reviewers.
The event-based certifications feature kicks off an identity certification for the following events:
-
User create. Advanced Identity Cloud detects when a user account has been created.
-
User modify. Advanced Identity Cloud detects when an existing user account has been modified or updated.
-
Attribute change. Advanced Identity Cloud detects changes in the attributes of an existing user account.
-
User delete/deactivate. Advanced Identity Cloud detects if a user account has been deleted or deactivated.
For more information, refer to Certify access by event.
-
- Grant entitlements to users and roles[18] (IAM-5146)
-
Identity Governance now allows tenant administrators to carry out more fine-grained entitlement grants for their user accounts. Tenant administrators can now:
-
Create a role and grant entitlements to the role.
-
Revoke entitlements in a role.
-
Grant entitlements to a user account.
-
Revoke entitlements from a user account.
For more information, refer to Manage entitlements.
-
- Identity Assertion node (AME-26821)
-
The new Identity Assertion node provides a secure communication channel for authentication journeys to communicate directly with PingGateway.
- PingOne application template (IAM-5232)
-
The PingOne application lets you manage and synchronize data between PingOne and Advanced Identity Cloud.
- Authenticate gateway and agent profiles with a shared secret (IAM-5833)
-
The Advanced Identity Cloud admin console for gateways and agents now lets you authenticate with a shared secret instead of a password. Use this to set the label for the shared secret.
- Authenticate OAuth 2.0 applications with a shared secret (IAM-6028)
-
The Advanced Identity Cloud admin console for OAuth 2.0 applications now lets you authenticate with a shared secret instead of a password. Use this to set the label for the shared secret.
Enhancements
-
OPENAM-21031: The performance of Google KMS has been improved by the introduction of caching.
-
AME-27126: A SAML SP can now authenticate to IDPs using mutual TLS (mTLS) when making an artifact resolution request.
-
IAM-3199: HTML styling in the Message node journey editor allows you to left justify text.
Fixes
-
FRAAS-19334: Failure to look up service account names following changes applied through the ESV API.
-
IAM-5079[18]: End-user roles page sometimes shows role grants as conditional even when the grants are direct.
-
IAM-5363[18]: Show the total number of approvals and access reviews in the inbox.
-
IAM-5858[18]: Missing support for access request global configuration options.
-
IAM-6138[18]: The governance events filter builder incorrectly validates
beforeandafterproperties in the user created state. -
IAM-6176[18]: The end-user access request rejection is missing a justification message.
-
IAM-6203[18]: The governance events filter doesn’t use
aftertemporal values for user created flows. -
IAM-6209: The Advanced Identity Cloud admin console navigation panel text appears when the panel is collapsed.
-
OPENAM-21473: If you set the collection method of a Certificate Collector node to
REQUEST,HEADER, orEITHER, and the certificate is not provided in the request or in the header, the node now returns a status ofNot collected.This node is currently not supported in Advanced Identity Cloud. -
SDKS-2935: The Device Binding node now gracefully handles the case of a user being set to
inactive.
11 Apr 2024
Version 13149.0
Enhancements
-
AME-26085: SAML 2.0
NameIDmapping can be configured per SP -
AME-27133: "Secret ID" has been renamed to "Secret Label" for secret mappings
-
The following services now support configuration using the Secrets API:
-
AME-16536: The OAuth 2.0 provider hash salt secret
-
AME-25885: The persistent cookie core authentication attribute
-
AME-26110: The client-side session signing key
-
AME-26134: The social provider service
-
AME-26441: The new CAPTCHA node (replaces the legacy CAPTCHA node)
-
AME-26442: The OIDC Token Validator node now lets you store the client secret in any type of secret store
-
AME-26633: The OAuth 2.0 client
clientJwtPublicKey -
AME-26637: The OAuth 2.0 client
idTokenPublicEncryptionKey -
AME-26639: OAuth 2.0 client mTLS self-signed certificates
-
AME-26668: The post authentication process (PAP) replay password
-
AME-26670: The web agents replay password key
-
AME-26998: The OAuth 2.0 client secret
-
-
The following services now support rotation of secrets using secret versions:
-
AME-25988: The persistent cookie encryption secret
-
AME-26999: OAuth 2.0 client secrets
-
AME-27000: OAuth 2.0 client
clientJwtPublicKey -
AME-27001: OAuth 2.0 client mTLS self-signed certificates
-
09 Apr 2024
Version 13122.0
Key features
- PingOne Verify service node (TNTP-118)
-
The PingOne Verify service node lets you configure and use PingOne Verify nodes (PingOne Verify Authentication node and PingOne Verify Proofing node) in your authentication journeys.
26 Mar 2024
Versions 12899.0
Key features
- Social Provider Handler node[35] (OPENAM-20924)
-
The new Social Provider Handler node adds an outcome to better handle interruptions in a social authentication journey after requesting profile information.
- Event-based certification[18] (IGA-2357)
-
Identity Governance now allows tenant administrators to configure certifications that are triggered by specific governance events, a process referred to as event-based certification. This method offers faster certification resolution compared to scheduled—and often lengthy—campaigns spanning weeks or months and involving numerous applications, intricate rules, and hundreds of reviewers.
The event-based certifications feature kicks off an identity certification for the following events:
-
User create. Advanced Identity Cloud detects when a user account has been created.
-
User modify. Advanced Identity Cloud detects when an existing user account has been modified or updated.
-
Attribute change. Advanced Identity Cloud detects changes in the attributes of an existing user account.
-
User delete/deactivate. Advanced Identity Cloud detects if a user account has been deleted or deactivated.
For more information, refer to Certify access by event.
-
- Grant entitlements to users and roles[18] (IAM-5146)
-
Identity Governance now allows tenant administrators to carry out more fine-grained entitlement grants for their user accounts. Tenant administrators can now:
-
Create a role and grant entitlements to the role.
-
Revoke entitlements in a role.
-
Grant entitlements to a user account.
-
Revoke entitlements from a user account.
For more information, refer to Manage entitlements.
-
Enhancements
-
AME-26130[35]: Updated the PUSH Notification service to store access keys as a secret
-
AME-25906[35]: Updated Identity Gateway agents to store credentials as a secret
-
IAM-4585: Request and approvals page now shows the current and past approvers, their decisions, and the dates
-
IAM-4968: Expose additional top-level parameters in the advanced section of mapping pages
-
IAM-5769: Add grouping logic to journey node items
-
IAM-5674: Target application can use ONBOARD action for FOUND situation
-
IAM-5814: Allow fixed application usernames to be chosen for custom SAML apps
-
OPENAM-21575[35]: Added
org.forgerock.json.jose.jwe.JweHeaderto the allowlist for Scripted Decision nodes
Fixes
-
AME-25915[35]: Assertion consumer processing fails if NameID format not present in the assertion response
-
IAM-3927[18]: Identity Governance now enforces mandatory comments (if configured) for revoke and allow exceptions
-
IAM-4309: Access reviews no longer display the internal
lastSyncuser attribute -
IAM-4762: Authoritative apps are now requestable
-
IAM-4986: Platform UI can now determine whether to use a pagedResultsCookie or offset for paging results
-
IAM-5076: "Abstain from action" option no longer displays when a campaign has expired
-
IAM-5362: Marking a property as an authoritative app entitlement no longer causes target app config to be generated
-
IAM-5413: Account deprovisioning now works in AD/LDAP after deleting a user identity
-
IAM-5794: Border color of sign-in input fields in hosted pages can now be overridden in themes
-
IAM-5875: Journey editor no longer orphans deleted nodes
21 Mar 2024
Versions 12899.0, 12863.0, 12855.0
Key features
- Additional cloud connectors
-
The following connectors are now bundled with Advanced Identity Cloud:
-
Dropbox connector (OPENIDM-19838)
-
PingOne connector (OPENIDM-19736)
-
Webex connector (OPENIDM-19920)
For more information, refer to the ICF documentation.
-
Enhancements
-
OPENIDM-19921: The following connectors included with Advanced Identity Cloud were upgraded to 1.5.20.21:
-
Google Apps connector
-
Microsoft Graph API connector
-
AWS connector
For details, refer to 1.5.20.21 Connector changes.
-
18 Mar 2024
Versions 12873.0, 12784.0
Enhancements
-
FRAAS-19341: ESV support for AES keys through the
base64aesencoding typeFor more information, refer to Encoding format.
15 Mar 2024
Versions 12754.0
Key features
- PingOne Service (TNTP-148)
-
Set up the PingOne Service in your Advanced Identity Cloud tenant so you can add Ping Identity nodes to your authentication journeys.
- PingOne nodes (TNTP-119)
-
- PingOne node
-
The PingOne node establishes trust between PingOne and Advanced Identity Cloud by leveraging a federated connection. Learn more in PingOne node.
- PingOne DaVinci API node
-
The PingOne DaVinci API node lets an Advanced Identity Cloud journey trigger a PingOne DaVinci flow through the API integration method. Learn more in PingOne DaVinci API node.
- PingOne Protect nodes (TNTP-127)
-
Ping Identity’s PingOne Protect is a centralized identity threat protection service, for securing your digital assets against online fraud attempts.
Learn more in PingOne Protect > How it Works.
13 Mar 2024
Version 12714.0
Key features
- HTTP Client node (TNTP-136)
-
The HTTP Client node lets you make HTTP(S) requests to APIs and services external to Advanced Identity Cloud from within a journey.
Use the HTTP Client node to simplify the integration with a broad range of external services by making direct HTTP(S) requests.
For more information, refer to HTTP Client node.
02 Mar 2024
Version 12580.0
Enhancements
-
The following services now support setting secrets using the secrets API rather than setting secrets in the service configuration:
-
AME-25709: AuthId signing key
-
AME-25907: Java agents
-
AME-25908: Web agents
-
AME-26014: Rotatable secrets for agents
-
AME-26301: SAML remote entities
-
AME-26241: OATH, Push, Web AuthN devices and the device binding, device ID, and Device profile services
-
-
The following nodes now support setting their secrets using the secrets API rather than setting secrets in the node configuration:
-
AME-26117: OTP SMS Sender and OTP SMTP Sender nodes
-
AME-16535: Set Persistent Cookie node
-
-
AME-26041: Enhanced handling of agents secret mappings – if you update or delete a secret label identifier, any corresponding secret mapping for the previous identifier is updated or deleted, provided no other agent shares that secret mapping
-
AME-25434: New Request Header node lets you inject values into shared state based on request header values
-
AME-26039: Added LDAP Affinity Level configuration option to the LDAP Decision node, to enable affinity-based load balancing for BIND requests
-
OPENAM-21768: Added
org.forgerock.opendj.ldap.Rdnandorg.forgerock.opendj.ldap.Dnclasses to the allowlist for all script contexts
Fixes
-
AME-24760: Inner nodes of a PageNode don’t independently audit node-login-complete events
-
AME-26158: Exception thrown when generating a Signed JWT with no encryption within a next-gen script called by a Scripted Journey node
-
OPENAM-17315: Scripts used to call 'response.getEntity()' in the past should now use 'response.getEntity().getString()' instead
-
OPENAM-21856: Introspecting stateless token with IG/Web agents causes
OAuth2ChfException
29 Feb 2024
Version 12560.0
Enhancements
-
IAM-4257: Azure AD app template updates
-
IAM-4342: MSGraphAPI connector includes a new optional
licenseCacheExpiryTimeconfiguration property -
IAM-4892: Salesforce app template updates
-
IAM-4900: UI has been updated to show the Advanced Identity Cloud build number
-
IAM-5033: Added new "Remember my username" checkbox to authentication trees
-
IAM-5287: Updated username, password, and KBA heading size on the profile page to improve accessibility
-
IAM-5334: Expose "Guarded String" as an object type property for Scripted Groovy, ScriptedREST, ScriptedSQL, CSV, Database table, and SCIM connectors
-
IAM-5459: KBA answer field now contains question context
-
IAM-5461: Custom errors sent as
TextOutputCallback.ERRORare now rendered as primary login errors, improving screen reader accessibility feature -
IAM-5503: Rename Orchestrations to Workflows
-
IAM-5563: Google Apps app template updates
-
IAM-5603: Create device details modal for managed user identities
-
IAM-5606: Add "POWERED BY" metadata to marketplace nodes
-
IAM-5748: Make "PingOne" a special case on the federation providers page
Fixes
-
IAM-5598: Styled terms and conditions included in a journey causes authenticate calls to fail
-
IAM-5611: Can’t revoke custom apps from roles or edit them from the role view
-
IAM-5641: Custom endpoints search returns endpoints created by other areas of the UI
-
IAM-5692: Console errors when opening the Add user modal for Bravo realm
-
IAM-5767: SAML SSO is not used when an application is saved from another tab after SSO setup
-
IAM-5873: Hosted page may fail to match user locale
28 Feb 2024
Version 12547.0
Enhancements
-
OPENIDM-19405: Allow email addresses to contain non-ASCII characters for supported SMTP providers
24 Jan 2024
Fixes
-
OPENIDM-18743[36]: Attempts to use connectors fail with null pointer exceptions when
operationOptionsis defined in the provisioner configuration
23 Jan 2024
Key features
- iProov Authentication node (TNTP-131)
-
The iProov authentication node integrates Advanced Identity Cloud authentication journeys with the Genuine Presence Assurance and Liveness Assurance products from iProov.
22 Jan 2024 (supplementary)
Key features
- Fingerprint Profiler and Fingerprint Response nodes (TNTP-130)
-
The Fingerprint nodes nodes let you integrate your Advanced Identity Cloud environment with the Fingerprint platform to help reduce fraud and improve customer experience.
Enhancements
-
AME-25906: Add the ability to configure the password for authenticating to an Identity Gateway agent as an ESV secret
-
AME-26130: Add the ability to configure the SNS access key secret for the push notification service to use an ESV secret
-
OPENAM-21575: Add
org.forgerock.json.jose.jwe.JweHeaderto the class allowlist for Scripted Decision node
Fixes
-
AME-25915: SAML flow fails if a
NameIDFormatelement is not present in an assertion response -
FRAAS-18464: Sandbox debug logging level set to
WARNinstead ofDEBUG -
IAM-5656: Fix alignment of text, buttons, and links in Message nodes
-
IAM-5660: Hosted pages not displaying list of themes
-
OPENAM-20924: Social Provider Handler node does not let end user switch to a different IdP
22 Jan 2024
Enhancements
-
AME-26117: Updated nodes relating to one-time passwords to use secret labels for passwords. Refer to OTP Email Sender node and OTP SMS Sender node.
19 Jan 2024
Key features
- RSA SecurID node (FRAAS-18037)
-
The RSA SecurID lets you use the RSA Cloud Authentication Service (RSA ID Plus) or RSA Authentication Manager from within an authentication journey on your Advanced Identity Cloud environment.
- Advanced Identity Cloud use case catalog
-
Introducing the release of the Advanced Identity Cloud use case catalog, a collection of guides that focus on tenant administrator use cases and third-party integrations.
18 Jan 2024
Key features
- Create and manage custom relationship properties (OPENIDM-19106, OPENIDM-19109)
-
You can now create and manage custom relationship properties using the Advanced Identity Cloud admin console.
- Schema API improvements (OPENIDM-19107)
-
You can now directly modify managed object schemas over REST using the schema API. This capability includes configuring custom relationship properties.
- Password timestamps (OPENIDM-19262)
-
Enabling this new feature lets you view or query when a user password was last changed and when it is set to expire.
Enhancements
-
OPENIDM-19674: The relationship-defined virtual property (RDVP) schema editor allows you to edit the
flattenPropertiesproperty. The managed object schema editor allows you to edit thenotifyRelationshipsproperty.
Fixes
-
OPENIDM-18957: The scheduler now attempts to release any triggers it attempted to acquire during a timeout due to an unresponsive repository
-
OPENIDM-19141: Workflow engine queries now properly honor
tablePrefixandtablePrefixIsSchemaconfiguration options -
OPENIDM-19279: Resource collection is required to create a relationship
-
OPENIDM-19565: The default
apiVersionconfiguration has been updated with additional resource paths
2023
19 Dec 2023
Key features
- Schedule jobs directly in the Advanced Identity Cloud admin console (IAM-3489)
-
You can now schedule the following jobs directly in the Advanced Identity Cloud admin console without using the IDM native admin console:
-
Scripts: Execute a script at a regular interval.
-
Task scanner: Execute a scan of identities using a complex query filter at a regular interval. The scan can then execute a script on the identities returned by the query filter.
-
- New Identity Governance capabilities[18] (IAM-4617, IGA-1664)
-
The Workflow UI lets you define custom workflow definitions for all access request types.
Create a role membership certification template, a new certification type for access reviews, lets you review and certify roles and the users who have access to roles. Primary reviewers are role owners, a single user, or users assigned to a role.
Enhancements
-
FRAAS-7382: Add ability to include JavaScript snippets in login and end-user UIs
-
IAM-4514[18]: Allow reviewers to add user, entitlement, and role columns to an access review
-
IAM-4739: Add read schema option to SCIM application template to discover custom schemas/attributes
-
IAM-5201: Focus on first input field or button automatically upon page load
-
IAM-5268: Add source-missing situation rule to authoritative applications
Fixes
-
FRAAS-16659: ESV mapping updates aren’t captured in promotions report
-
IAM-4810: Custom endpoint UI missing context option
-
IAM-5072: Inbound mapping tab shows in target applications
-
IAM-5171: Azure Active Directory application template doesn’t return a user’s role membership
-
IAM-5187: LDAP v2.1 application template doesn’t clear
dc=example,dc=combase DN -
IAM-5238: LDAP application template is missing the group object classes property
-
IAM-5422[18]: Entitlement owner doesn’t show in the entitlement list
12 Dec 2023
Enhancements
-
AME-22326[37]: The
httpClientavailable in scripts now automatically adds the currenttransactionIdas an HTTP header. This lets you correlate caller and receiver logs to make requests to other ForgeRock products and services. -
AME-25392[37]: Add
org.forgerock.openam.scripting.api.PrefixedScriptPropertyResolver, used for accessing ESVs from scripts, to the allowlist forSAML2_SP_ADAPTERandSAML2_IDP_ADAPTERscript types -
AME-25433[37]: Add
com.sun.crypto.provider.PBKDF2KeyImpl,javax.crypto.SecretKeyFactory, andjavax.crypto.spec.PBEKeySpecto the allowlists for Scripted Decision nodes and Configuration Provider nodes -
AME-25608[37]: Add auditing for opening and closing connections for the LDAP decision node, ID Repo service, and Policy Configuration service
-
AME-25630[37]: Add
java.security.spec.InvalidKeySpecExceptionto the allowlist for the Scripted Decision and Configuration Provider nodes -
OPENAM-16897[37]: The OAuth 2.0 Device grant flow can now return either JSON or HTML
Fixes
-
COMMONS-1397[37]: Audit event log entries not logged due to thread contention
-
FRAAS-17686[38]: Add
org.forgerock.json.jose.jwe.JweHeaderto the allowlists for theAUTHENTICATION_TREE_DECISION_NODEandCONFIG_PROVIDER_NODEscript types -
IAM-4401[37]: Disabling
Clear-Site-Dataheader breaks realm login -
OPENAM-17331[37]: Disabled SNS endpoints can now be re-enabled
-
OPENAM-17816[37]: OAuth 2.0 requests without a
Content-Typeheader fail with a 500 error -
OPENAM-19282[37]: Recovery Code Display node only works immediately after a registration node
-
OPENAM-19889[37]: Policy evaluation fails when subject is agent access token JWT
-
OPENAM-20026[37]: Social IDP with trailing whitespace in the name can’t be deleted using the UI
-
OPENAM-20329[37]: Issuer missing from OAuth 2.0 JARM response
-
OPENAM-21053[37]: Missing
userIdfrom access audit log whenorg.forgerock.security.oauth2.enforce.sub.claim.uniqueness=falsein JWT client authentication flow -
OPENAM-21421[37]: Scripting logger name isn’t based on logging hierarchy convention
-
OPENAM-21476[37]: Persistent cookie is not created when using Configuration Provider node
-
OPENAM-21484[37]: Introspection of a stateful refresh token for claims field for known OAuth2 fields is now a string and not nested in a list
30 Nov 2023
Fixes
-
IAM-5275[37]: Advanced Identity Cloud admin console doesn’t add query parameters to the logout URL
Notices
ForgeRock deprecated the option to let Advanced Identity Cloud tenant administrators skip 2-step verification on Friday, February 3, 2023.
The end-of-life date for this deprecation is Friday, March 1, 2024, when the skip option functionality will be removed from Advanced Identity Cloud. You have until this date to update your tenants to make 2-step verification mandatory for all tenant administrators. For more information, refer to Tenant administrator mandatory 2-step verification FAQ.
28 Nov 2023
Key features
- Duo Universal Prompt node (FRAAS-15675)
-
The Duo Universal Prompt node lets you provide two-factor authentication using Duo’s Universal Prompt authentication interface. You can integrate Universal Prompt with your web applications using the Duo Web v4 SDK.
For details, refer to Duo Universal Prompt node.
27 Nov 2023
Enhancements
-
FRAAS-17939[39]: Some connectors included with Advanced Identity Cloud were upgraded to the following versions:
1.5.20.19For details, refer to 1.5.20.19 Connector changes.
-
Microsoft Graph API connector
-
SCIM connector
1.5.20.18For details, refer to 1.5.20.18 Connector changes.
-
Google Apps connector
-
Microsoft Graph API connector
-
Salesforce connector
-
SCIM connector
-
Workday connector
-
-
OPENIDM-19037: Update property value substitution to reflect boolean value in the UI
17 Nov 2023
13 Nov 2023
Fixes
-
FRAAS-17883: Tenant administrators cannot save edits to their personal information
-
IAM-5226: Tenant administrator security questions should not be shown when editing personal information
-
IAM-5240: No error message displays when a tenant administrator fails to save edits to their personal information
31 Oct 2023
Key features
- next-generation scripting enhancements (AME-25928)
-
The next-generation scripting engine for journey decision node scripts lets you:
-
Reduce the need to allowlist Java classes with a stable set of enhanced bindings.
-
Simplify scripts with fewer imports and more intuitive return types that require less code.
-
Debug efficiently with clear log messages and a simple logging interface based on SLF4J.
-
Make requests to other APIs from within scripts with a more intuitive HTTP client.
-
Modularize your scripts by reusing common code snippets, including external libraries such as CommonJS, with library scripts.
-
Access identity management information seamlessly through the
openidmbinding.
The next-generation engine can’t use legacy scripts.
If your Scripted Decision node uses legacy scripts, you must convert them to use updated bindings to take advantage of the benefits of the next-generation scripting engine.
Where possible, you should migrate legacy scripts to take advantage of next-generation stability.
For more information, refer to Next-generation scripts.
-
Enhancements
-
FRAAS-3841: Activate and deactivate journeys in the Advanced Identity Cloud admin console. Refer to Deactivate journeys.
-
IAM-4191: Allow tenant session cookie name to be configured. Refer to Session cookie name.
-
IAM-4735: Add support for schema discovery in application templates
-
IAM-4806: Show outbound tenant IP addresses in Advanced Identity Cloud admin console. Refer to Access global settings.
-
IAM-4853: Add AS400 application template. Refer to the AS400 section in Provision an application.
Fixes
-
FRAAS-16785: Incorrect positioning of reCAPTCHA v2 elements
-
IAM-2936: Journeys hang indefinitely when using a State Metadata node within a Page node
-
IAM-4521: Screen readers announce field labels twice
-
IAM-4956: Advanced Identity Cloud admin console doesn’t use the current realm when logging out
-
IAM-5113: Unable to remove an NAO assignment from a user in Advanced Identity Cloud admin console
19 Oct 2023
Key features
- Gateway Communication node (FRAAS-17380)
-
Lets Advanced Identity Cloud authentication journeys communicate directly with the PingGateway (PingGateway).
This secure communication channel extends the Advanced Identity Cloud capabilities with PingGateway features, such as validating a Kerberos ticket and performing other certificate handshakes.
For details, refer to Gateway Communication overview.
16 Oct 2023
Key features
- New Autonomous Access capabilities[40] (DATASCI-1269)
-
Autonomous Access User access behavior and tenant access behavior let end users understand their "normal" login behavior for the past six months by graphically displaying key access metrics on a UI. Users can filter the UI to show certain login metrics, like time of day, city, country, day of week, device used for login, operating system, and browser type. Users can also compare an individual user’s login behavior to that of the access attempts for all other users.
Enhancements
-
IAM-4211: Display disaster recovery region in the Advanced Identity Cloud admin console
-
IAM-4369: Remove AM applications from application list view
-
IAM-5045: Display pop-up warning when an end user is about to be logged out of an Advanced Identity Cloud hosted page
Fixes
-
IAM-4812: Correctly save array ESVs containing newline characters
-
IAM-4863: Display ESV buttons properly when the user gives them focus
-
IAM-4877: Display ESV selection button properly while user is modifying a script associated with a Scripted Decision node
-
IAM-4698: Fix accessibility issues with messages in page nodes
13 Oct 2023
Enhancements
-
FRAAS-17373[41]: The following connectors included with Advanced Identity Cloud were upgraded from 1.5.20.15 to 1.5.20.17:
-
Adobe Marketing Cloud connector
-
Google Apps connector
-
Microsoft Graph API connector
-
Salesforce connector
-
SCIM connector
Some highlights include:
-
OPENICF-900: SCIM connector: Add support for dynamically generated SCIM schemas
-
OPENICF-2453: SCIM connector: Persist optional refresh token upon successful access token renewal
For a complete list of enhancements and fixes, refer to Connector changes.
-
Fixes
-
ANALYTICS-311: The
USER-LAST-LOGINreport doesn’t show results if the last journey failed -
FRAAS-17413: Improve IDM service reliability during upgrades and routine maintenance
-
OPENICF-1723: Salesforce connector: Clarify usage of
proxyUriconfiguration property -
OPENICF-2297: SCIM connector: Roles attribute should be a list of
Strings, not a list ofObjects -
OPENICF-2482: SCIM connector: Dynamic schema doesn’t default to static schema on all exceptions
-
OPENICF-2483: SCIM connector: Creating a user with special attributes fails with dynamically generated schema
-
OPENICF-2484: SCIM connector: PUT with
schemasattribute fails for providers that support PATCH -
OPENICF-2448: SCIM connector: HTTP client fails to handle OAuth 2.0 errors
12 Oct 2023
Key features
- OneSpan Get User Authenticator node (FRAAS-17378)
-
Retrieves the authenticators assigned to a user and helps enable user’s authentication and security levels.
For details, refer to OneSpan Get User Authenticator node.
- OneSpan Identity Verification node (FRAAS-17378)
-
Sends request to OneSpan to analyze the image and determine whether the document is genuine or fraudulent.
For details, refer to OneSpan Identity Verification node.
03 Oct 2023
Fixes
-
FRAAS-17283: Tenant status pages not automatically updated during downtime
-
IAM-4235: Passthrough authentication using AD connector fails if set up in UI and user DN includes a space
-
IAM-4903: API calls to IGA endpoints not working with custom domain
-
IAM-4915: User details modal for IGA access review shows manager details as JSON object
-
OPENIDM-19192: Personal information is still editable by end users when User Editable is set to
false
25 Sep 2023
Enhancements
-
IAM-4515[42]: Include autocomplete attribute with login form fields
-
IAM-4525[42]: Update profile picture modal with accessibility improvements for screen readers
-
IAM-4576[42]: Increase time on screen for loading spinner so that screen readers can announce it
-
IAM-4616[42]: Include contextual information with the show/hide buttons for improved accessibility
Fixes
-
FRAAS-17278: Health status reports for
AM,IDM, andplatform-adminservices incorrectly reported as available in some situations -
IAM-4460[42]: Screen readers read show/hide buttons for security questions as show/hide password
-
IAM-4523[42]: Screen readers read avatar alt text when tabbing to action menu
-
IAM-4524[42]: Two buttons with different labels open the same dialog
20 Sep 2023
Key features
- New Identity Governance capabilities[18] (IGA-1691)
-
Access requests let end users request access to resources and let managers request that access be removed from their delegates. The list of resources an end user can request access to is referred to as the access catalog.
Manage access request workflows is a new feature that lets you optionally define flows to include business logic, decisions, and approvals. For example, decide what happens when an approver rejects an access request for an application. Workflows currently only supports access request-related features.
New options in the hosted account pages let end users submit access requests, submit requests to remove access, and review assigned request items:
-
The My Requests option lets you view and create access requests to resources (applications, roles, entitlements) for yourself or on behalf of others.
-
The My Directory > Direct Reports option lets managers submit access removal requests.
-
The Inbox > Approvals option lists request items (requests an end user submits) for an approver (designated owner) to act on.
-
Enhancements
-
IAM-3648: ESV placeholders can now be entered from a drop-down list
-
IAM-3651: ESV placeholders can now be entered from key-value input fields
-
IAM-4236: Improve layout of the applications reconciliation tab
-
IAM-4367: Separate the connection status of OAuth 2.0 client applications into a dedicated list
-
IAM-4662: ESV placeholders can now be entered from tag input fields
-
IAM-4717: Added date, datetime, and time fields to the login UI
-
IAM-4789: Grant roles now show temporal constraints
-
OPENAM-20847: Sanitized HTML can now be added into messages for the Email Suspend node
Fixes
-
IAM-4418: Fix accessibility issues with multi-select input fields
-
IAM-4489: Align checkbox color with other form elements
-
IAM-4491: Correctly label sidebar buttons when expanded or collapsed
-
IAM-4492: Make navigation bars in end-user UI accessible for screen readers
-
IAM-4798: The
aria-labelis now correctly displayed for all component types on sidebar buttons -
IAM-4843: The user column in the certification task list now shows a user’s full name instead of only the first name
-
IAM-4528: Outbound reconciliation mapping preview shows generated password value
15 Sep 2023
Key features
- Query Parameter node (AME-24069)
-
Allows you to insert query parameter values from a journey URL into configurable node state properties. This lets you customize journeys based on the query parameter values.
For details, refer to Query Parameter node.
Enhancements
-
OPENAM-21073: Request headers are now accessible in OAuth 2.0/OIDC scripts for
OIDC_CLAIMS,OAUTH2_ACCESS_TOKEN_MODIFICATION, andOAUTH2_MAY_ACTscript contexts using therequestPropertiesbinding -
OPENAM-21355: Jakarta AWS region (ap-southeast-3) enabled for the PingAM push notification service
Fixes
-
IAM-4639: String/password field button is highlighted in the UI
-
IAM-4829: Eye icon displays over the password field highlight box in the UI
-
OPENAM-18599: Allow customization of the error message that displays to end users when their account is locked or inactive using
.withErrorMessage()in a Scripted Decision node -
OPENAM-18685: Use the OAuth2 Provider service in the AM native admin console to specify if tokens issued should contain the
subnameclaim -
OPENAM-19261: Errors are incorrectly logged when triggered by introspection of tokens using OAuth 2.0 client credentials grant
-
OPENAM-20451: The WebAuthn Registration node now displays an end user’s
userNamewhen registering a device when the identity’s name isn’t human-readable -
OPENAM-21158: Add support for trusted platform module (TPM) attestation using elliptic curve cryptography (ECC) unique parameter validation starting with Windows 11 version 22H2
-
OPENAM-21304: The
request_urisfield does not populate when OAuth 2.0 clients register using dynamic client registration -
OPENAM-21390: Fix caching error to correctly provide data to
nodeStatewhen a journey switches server instances
11 Sep 2023
Enhancements
-
IAM-3650: Add a drop-down menu to checkbox inputs for selecting ESV placeholders
-
IAM-3826: Add the ability to specify a source and transformation script when mapping application properties. For details, refer to app-management:provision-an-application.adoc#apply-a-transformation-script-to-a-mapping.
-
IAM-4567: Add a warning when running reconciliations and selecting the
persistAssociationsoption. For details, refer to View a report about the last reconciliation.
Fixes
-
IAM-4366: Provide browser-specific logic to handle alternative CSS for accessibility
-
IAM-4409: Require at least three characters before running identity searches when there are more than 1000 identities of that type
-
IAM-4478: Only allow certain combinations of properties in a mapping transformation script
-
IAM-4493: Fix the heading hierarchy in the UI
-
IAM-4568: Do not enable the option to change a user association in the UI
-
IAM-4703: Fix display of password fields in some themes
-
IAM-4710: Fix rounded border of password fields in hosted pages
22 Aug 2023
Key features
- Salesforce Community User application template (IAM-4340)
-
Provision, reconcile, and synchronize Salesforce, Salesforce Portal, and Salesforce Community accounts.
For details, refer to Salesforce application template or Salesforce Community User application template
- Add preference-based provisioning to Privacy and Consent settings (IAM-4243)
-
End users in target applications can share their data with other applications. After the end user configures a preference to share data with other applications, data from the target application is synchronized with Advanced Identity Cloud.
For details, refer to End-user data sharing
18 Aug 2023
Key features
- OneSpan Auth VDP User Register node (FRAAS-15426)
-
Registers users to authenticate using the virtual one-time password (VOTP). For details, refer to OneSpan Auth VDP User Register node.
- OneSpan Auth Assign Authenticator node (FRAAS-15426)
-
Assigns VIR10 authenticator to the user when there’s a VIR10 authenticator available in the tenant and the user isn’t assigned a VIR10 authenticator. For details, refer to OneSpan Auth Assign Authenticator node.
- OneSpan Auth Generate VOTP node (FRAAS-15426)
-
Generates and delivers a virtual one-time password (VOTP) through the delivery method configured in the node if there’s a VIR10 authenticator assigned to the user. For details, refer to OneSpan Auth Generate VOTP node.
09 Aug 2023
Fixes
-
OPENAM-18004[43]: Audit logging does not specify transaction IDs correctly for internal requests to certain APIs
-
OPENAM-18709[43]: Calls to the
nodeState.get()method in Scripted Decision nodes do not return values in shared state when a variable is stored in both shared state and secure state -
OPENAM-20230[43]: Calls to classes in the allowlist fail occasionally with access prohibited messages
-
OPENAM-20682[43]: Unable to encrypt
id_tokenerror when there are multiple JWKs with the same key ID but different encryption algorithms -
OPENAM-20691[43]: Session quota reached when oldest session is not destroyed due to race condition
-
OPENAM-20783[43]: Logging is incorrect when the authorization code grant flow is used successfully
-
OPENAM-20920[43]: Null pointer exceptions when a SAML 2.0 binding is null and the SSO endpoint list contains non-SAML 2.0 entries
-
OPENAM-20953[43]: Policy evaluation with a subject type
JwtClaimreturns HTTP response code 500 -
OPENAM-20980[43]: The OIDC social provider is unable to use an issuer’s comparison check regex
-
OPENAM-21001[43]: Custom scripted SAML 2.0 IDP account mappers are determined incorrectly
-
OPENAM-21004[43]: Invalid session ID error when session management is disabled in an OIDC provider
-
OPENAM-21046[43]: The Create Object and Patch Object nodes do not log exception stack traces when they can’t retrieve the object schema
-
OPENAM-21164[43]: XML string formatted incorrectly when using a custom adapter to get the assertion from a SAML 2.0 response
31 Jul 2023
Enhancements
-
IAM-3502: Add the ability to set and reset a sync token for identity management account object type. For details, refer to Reset the last reconciliation job.
-
IAM-3678: Update error messages and labels in login and signup pages
-
IAM-3962: Improve design of push number challenge page for Push Wait node
-
IAM-4248: Add three additional non-account objects to ServiceNow page
-
IAM-4326: Improve onLink script to handle mapped properties of type array and object
-
IAM-4334: Update SuccessFactors application templates to support Advanced Identity Cloud built-in SuccessFactors connector
Fixes
-
IAM-3877: UI loader spins indefinitely when realm is deactivated
-
IAM-4093: Replace Google Fonts in the login UI to meet GDPR compliancy requirements
-
IAM-4176: Advanced setting query filter does not show all available properties
-
IAM-4240: Accessibility issues in Page node when NVDA readers are used
-
IAM-4261: Accessing end-user UI with query parameter "code" displays empty page
-
IAM-4371: Unable to create applications due to
userpasswordproperty set -
IAM-4384: Platform UI does not resume journeys with custom redirect logic
-
IAM-4427: Platform UI does not show assignments for tenants running deprecated application management
-
IAM-4475: Platform UI does not load after tenant administrator signs into an upper tenant during promotion
17 Jul 2023
Fixes
-
OPENIDM-18292[44]: Add support for the
_fieldsrequest parameter to the syncgetTargetPreviewendpoint -
OPENIDM-18898[44]: Add support for the
_countOnlyparameter in identity management scripts -
OPENIDM-18980[44]: Add a new metric to measure the duration of a LiveSync event
-
OPENIDM-19098[44]: Enable ES6 support for identity management scripts
22 Jun 2023
Enhancements
-
DATASCI-1331[45]: Distributed attack heuristics
-
DATASCI-1677[45]: Support the right to access or be forgotten (GDPR compliance)
-
IAM-2026: Support versioning of the application and connector templates
-
IAM-3408: Let provisioners use a range of connector versions
-
IAM-4074: Add a loading animation to the pie chart component
-
IAM-4242: Add "Conflicting changes" category to reconciliation summary
Fixes
-
FRAAS-9230: Sanitize
aria-hiddenfields -
FRAAS-16041: Users can choose Basic Auth for Identity Cloud logging endpoints
-
IAM-2972: Route users to the correct realm after granting Salesforce permissions
-
IAM-3719: Modals not showing display access review comments and activity
-
IAM-4116: Don’t let access review users add reviewers with greater privileges than they themselves have
-
IAM-4134: User pop-up is visible in "Entitlement" tab
-
IAM-4200: Last certified date, decision, and actor displaying incorrectly in Governance account details
14 Jun 2023
Key features
- New Identity Governance capabilities[18] (IGA-1592)
-
Entitlements are specific permissions given to an account in an onboarded target application. Each entitlement correlates to a permission. Pull in entitlements from all onboarded target applications into Advanced Identity Cloud for use in certifications.
Entitlement assignment certification, a new certification type for access reviews, lets you review and certify entitlements and the users who have access to entitlements on some or all applications. Primary reviewers are entitlement owners, a single user, or users assigned to a role.
The governance glossary lets you attach business-friendly attributes to applications, entitlements, and roles to add more specificity to the data you review in access certifications.
New options in the hosted account pages let you view your access, your direct reports, and the access your direct reports have:
-
The My Access option lets you view your access in Advanced Identity Cloud and onboarded target applications. This includes accounts from onboarded target applications, roles you are assigned in Advanced Identity Cloud, and entitlements or privileges you have in onboarded target applications.
-
The Direct Reports option lets you get access information for individuals you manage. This includes their profile information, accounts from onboarded target applications, roles they are assigned in Advanced Identity Cloud, and entitlements or privileges they have in onboarded target applications.
-
- Microsoft Graph API email client (OPENIDM-17899)
-
Configure the email client to use the MS Graph API Client for sending email.
For more information, refer to Microsoft Graph API email client.
Enhancements
-
IAM-2826: Filter the "Assignments" tab for identities so that it does not show overrides, entitlements, or resources
-
IAM-3677: Remove increment/decrement arrows from numeric input fields
-
IAM-3982: Let users filter risk activity using distributed attack as a risk reason
-
IAM-3983: Show distributed attack as a risk reason in the risk dashboard
-
IAM-4136: Use the tab key to move focus and remove tags in multi-select components
Fixes
-
FRAAS-14262: Include changes to group privileges in the configuration promotions report
-
IAM-2713: Prohibit editing of managed application objects
-
IAM-3594: Correctly redirect control to the End User UI after authenticating with itsme
-
IAM-3939: Let end users switch to a different authentication journey
-
IAM-4013: When using a custom domain,
originalLoginRealmis set incorrectly -
OPENIDM-17481: Managed object schema can now describe a field as a nullable array and specify a default value for this field if not provided in a create request
-
OPENIDM-17771: Processing of a large number of scheduled jobs no longer causes all scheduled tasks to continuously misfire
-
OPENIDM-18192: Updating a relationship-defined virtual property (RDVP) on a managed object by signal receipt no longer causes other RDVP state within that object to be lost
-
OPENIDM-18360: Use the full object state when validating requests made by a delegated administrator to modify a relationship
-
OPENIDM-18613: Provide the ability to remove the
userPasswordattribute -
OPENIDM-18644: Correctly determine whether it’s possible to configure clustered reconciliation
-
OPENIDM-18895: Fixes support for multi-version concurrency control on managed object patches and updates
08 Jun 2023
Key features
- Lexis-Nexis ThreatMetrix Authentication nodes (FRAAS-15325)
-
Integrate Lexis-Nexis ThreatMetrix decision tools and enable device intelligence and risk assessment in Advanced Identity Cloud.
For details, refer to ThreatMetrix Authentication nodes.
05 Jun 2023
Key features
- Filter log results
-
Use the
_queryFilterparameter to filter log results on any field or combination of fields in a payload. For details, refer to Filter log results.
30 May 2023
Key features
- Scripted SAML 2.0 SP adapter
-
Customize the SAML 2.0 SP adapter using a script.
For details, refer to SP adapter.
- OIDC ID Token Validator node
-
The new OIDC ID Token Validator node lets Advanced Identity Cloud rely on an OIDC provider’s ID token to authenticate an end user. The node evaluates whether the ID token is valid according to the OIDC specification.
For details, refer to OIDC ID Token Validator node.
Fixes
-
AME-21638: Customize an SP adapter by using a script
-
AME-24026: Allow specifying inputs required by the provider scripts in the Configuration Provider node
-
AME-24073: Expose the
prompt_values_supportedparameter of the provider configuration at the OIDC well-known endpoint -
AME-24175: Provide additional classes in the allowlist that scripts used in the Scripted Decision node
-
OPENAM-12030: Authentication node instances are deleted when journeys containing them are deleted
-
OPENAM-13293: New OIDC ID Token Validator node evaluates whether the ID token is valid according to the OIDC specification
-
OPENAM-13329: Display journeys with spaces in their name in the Authentication Configuration drop-down menu
-
OPENAM-13766: Route user session based on whether policy evaluation is requested or not
-
OPENAM-17179: Correctly delete a script if its referring journey is deleted
-
OPENAM-17566: Display account name instead of UUID in the ForgeRock Authenticator when using MFA
-
OPENAM-18488: Support certificate-based attestation in certificate chains terminating at an intermediate CA
-
OPENAM-18692: Set the minimum value for the Default Max Age property to 0
-
OPENAM-19745: Add support for EdDSA signing algorithm to WebAuthn Registration node
-
OPENAM-20082: Show correct error message to locked out users
-
OPENAM-20104: Fix the fragment response mode for the OAuth 2.0 authorize endpoint
-
OPENAM-20187: Fix the "waiting for response" page so that it fails authentication as configured in the authentication journey
-
OPENAM-20230: Prevent class allowlist from failing for classes already on the allowlist
-
OPENAM-20318: Allow a restricted set of HTML tags to be rendered in page node headers and descriptions
-
OPENAM-20360: Fix default URL encoding to ensure ampersand characters are not double encoded in a SAML assertion
-
OPENAM-20386: Fix authentication node state reconciliation in some complex journeys
-
OPENAM-20396: Preserve ordering of ACR to chain mapping configuration of OIDC provider after a restart
-
OPENAM-20451: Fix WebAuthn registration node to return a human-readable username
-
OPENAM-20457: Route Device Location Match node to "Unknown Device" outcome when the previously stored location of the device is not provided
-
OPENAM-20479: Enhance OIDC authentication to handle unsecured JWS requests
-
OPENAM-20541: Add additional inner classes to scripting allowlist to support RSA key pair generation
18 May 2023
Key features
- Administrator federation enhancements
-
Groups support: The new groups feature allows you to add and remove administrators depending on group membership in your identity provider. Using administration groups lets you automate the granting and removing of access for administrators that are being on-boarded, switching roles, or leaving your organization.
OIDC Federation: OIDC is now supported as a federation identity provider, along with Microsoft ADFS and Microsoft Azure.
For more information, refer to Configure federated access for tenant administrators.
17 May 2023
Fixes
-
FRAAS-13293: Provide more accurate and granular information in promotion reports
-
FRAAS-14063: Remove orphaned unused scripts during promotion
-
FRAAS-15022: Improve promotion reports
-
FRAAS-15188: Ensure environments can be recreated after deletion
-
IAM-2561: Allow adding applications to a user or role from the Identities > Manage page
-
IAM-3550: When attempting to validate Office 365 applications, a blank screen appears
-
IAM-3580: Improve service accounts UI including error handling
-
IAM-3666: Add alternative text to QR code image
-
IAM-3676: Add keyboard controls to UI to select multiple values in multivalued lists
-
IAM-4030: Improve handling of identity provider and groups claims
-
IAM-4031: Generic OIDC configuration returns HTTP 400 Bad Request
-
IAM-4032: Federation enforcement is missing from the UI
-
IAM-4058: Admin UI routing for locked tenants is no longer working correctly
05 May 2023
Fixes
| Issue ID[47] | Summary |
|---|---|
IAM-3043 |
CAPTCHA node not behaving properly when false |
26 Apr 2023
Key features
- PowerShell connector
-
Use the PowerShell Connector Toolkit to register a connector that can provision any Microsoft system.
For details, refer to PowerShell.
- SAP SuccessFactors Account or SAP SuccessFactors HR connector
-
Use the SAP SuccessFactors connectors to synchronize SAP SuccessFactors users with Advanced Identity Cloud users.
For details, refer to SAP SuccessFactors Account or SAP SuccessFactors HR.
- Bookmark application
-
You can now register a bookmark application - for example, OneNote, Evernote, Google Bookmarks, or raindrop.io - to direct users to specific URLs. A bookmark application displays shortcut links on dashboards. When you click one of the links, the browser opens a new tab.
For details, refer to Bookmark.
Resolved issues
| Issue ID | Summary |
|---|---|
IAM-2911 |
Add support for bookmark apps in application management |
IAM-3472 |
Update promotions UI to set tenant color dynamically based on the tenant name |
IAM-3630 |
Add SuccessFactors template and connector configuration |
IAM-3666 |
Add alt text to QR code |
IAM-3667 |
Add visual indication of keyboard focus on input fields |
IAM-3681 |
Improve accessibility of the |
IAM-3778 |
Allow login UI to work when browser session storage is unavailable |
IAM-3792 |
Prevent login UI rendering extra whitespace character in front of text on suspended nodes |
IAM-3806 |
Remove beta indicator from the trends chart in admin UI dashboard |
IAM-3840 |
Change color of radio button changed in Choice Collector node |
IAM-3879 |
Ensure global variable |
IAM-3910 |
New PowerShell configuration properties |
OPENAM-18895 |
Fix API request timeout errors for slow connections |
OPENIDM-18917 |
Display last name instead of user ID on user profile when no first name is provided |
OPENAM-20815 |
Add missing footer to Page node when session expired |
24 Apr 2023
Key features
- Microsoft Intune node
-
Integrates Microsoft Intune to control features and settings on Android, Android Enterprise, iOS/iPadOS, macOS, and Windows 10/11 devices in your organization.
For details, refer to Microsoft Intune node.
- Secret Double Octopus (SDO) nodes
-
PingOne Advanced Identity Cloud integrates with Secret Double Octopus (SDO) to provide high-assurance, passwordless authentication systems that address the diverse authentication needs of a real-world, working enterprise.
For details, refer to Secret Double Octopus (SDO) nodes.
06 Apr 2023
Key features
- Support for all Google Fonts for hosted pages
-
Meet your organization’s brand guidelines by using any Google Font in your hosted pages.
Resolved issues
| Issue ID | Summary |
|---|---|
IAM-1686 |
Allow any Google Font to be used on hosted pages |
IAM-3164 |
Prevent table columns from stacking vertically on smaller viewports |
IAM-3313[18] |
Additional Options section missing from Identity Certification campaign template |
30 Mar 2023
Key features
- IP allowlisting
-
Enterprises often need to ensure that requests entering their network come from trusted sources. PingOne Advanced Identity Cloud now offers outbound static IP addressess for sandbox environments.
Outbound static IP addresses let you implement network security policies by setting up allowlists of IPs originating from Advanced Identity Cloud. This adds an extra layer of security to outbound calls to your APIs or SMTP servers.
For more information, refer to Outbound static IP addresses.
20 Mar 2023
Resolved issues
| Issue ID | Summary |
|---|---|
OPENIDM-18476 |
The IDM admin UI now defaults identity object number fields to |
OPENIDM-18216 |
IDM admin UI should query recon association data instead of audit data |
OPENIDM-18870 |
Inability to delete an inline reconciliation or schedule script |
OPENIDM-18868 |
Inability to save a schedule when you add or remove a passed variable |
OPENIDM-18865 |
Script changes cannot be saved unless you click outside the Inline Script box |
FRAAS-14097 |
Promotion report should identify journeys by their name |
FRAAS-13522 |
Promotion report does not include changes to custom email provider |
FRAAS-14353 |
Configuration placeholder replacement assumes a string value |
16 Mar 2023
Key features
- PingOne® Identity Governance (add-on capability)
-
PingOne Identity Governance is a new add-on capability of PingOne Advanced Identity Cloud. Identity Governance allows you to centrally administer and manage user access to applications and data across your organization to support regulatory compliance.
With Identity Governance you can:
-
Work with onboarded target applications when reviewing user data. This allows you to review user data for onboarded applications.
-
Define and launch reviews of data using certification campaigns.
-
Review and manage user access to applications. This includes managers reviewing the access their direct reports have.
For more information, refer to What is PingOne Identity Governance?.
To purchase an Identity Governance subscription, contact your ForgeRock representative.
-
10 Mar 2023
Key features
- Support for Scripted Groovy connector applications
-
Application management now lets you register, provision, and manage Scripted Groovy connector applications.
For details, refer to Scripted Groovy connector.
Resolved issues
| Issue ID[48] | Summary |
|---|---|
IAM-662 |
Fixed agent logout in platform UI |
IAM-3160 |
Added ability to configure the scripted Groovy connector |
IAM-3180 |
Hide the SSO tab when an application is authoritative |
IAM-3193 |
Updated SCIM app template to only show the refresh token property for OAuth authentication |
IAM-3303 |
Enable clicking a row to edit entries on the service accounts page |
IAM-3304 |
Added breadcrumbs to the service accounts page |
IAM-3305 |
Added a search field to the service accounts page |
IAM-3462 |
Corrected AD template property from |
IAM-3478 |
Addressed accessibility concerns when displaying password policy validation |
IAM-3642 |
Fixed an issue with unselected applications being imported when promoting, and improved the user experience for selecting and deselecting applications in the promotions UI |
IAM-3669 |
Fixed drop-down lists to show the value of the selected option in the form |
IAM-3694 |
Added ability to customize the success color in hosted pages |
08 Mar 2023
Key features
- Administrator federation
-
Administrator federation allows administrators to use single sign-on (SSO) to log in to an Advanced Identity Cloud tenant.
By using federation to authenticate your administrators to Advanced Identity Cloud, you can quickly and easily deprovision an administrator by removing their access from your centralized identity provider.
For details, refer to Configure federated access for tenant administrators.
06 Mar 2023
Resolved issues
| Issue ID | Summary |
|---|---|
IAM-2921 |
In the Dashboard, the total number of applications that display in the Applications box now includes those applications registered using the new app catalog in tenants created on or after January 12, 2023. |
IAM-3760 |
Apple social authentication works with other authentication methods |
03 Mar 2023
Key features
- SCIM built-in connector
-
You can now use the SCIM built-in connector to manage user and group accounts on any SCIM-compliant resource provider.
- Promotions API documentation
-
The promotions API documentation is now publicly available at https://apidocs.id.forgerock.io/#tag/Promotion.
Resolved issues
| Issue ID | Summary |
|---|---|
FRAAS-8225 |
The promotions API documentation is now publicly available at https://apidocs.id.forgerock.io/#tag/Promotion |
FRAAS-8709 |
Include the log sources in the logged events |
FRAAS-12402 |
Add /platform/oauthReturn route to support authentication for Salesforce and Google Apps |
FRAAS-12413 |
OIDC login from a custom domain results in blank page |
OPENICF-400 |
The LDAP connector now correctly reads the AD Account tokenGroups attribute |
OPENICF-1858 |
Add group owners management support to the Microsoft Graph API connector |
OPENICF-2039 |
Add archived, languages, isEnrolledIn2Sv, and isEnforcedIn2Sv fields to the Google Apps connector |
OPENICF-2067 |
Adjust license assignments as part of the user creation and update operations in the Google Apps connector |
OPENICF-2068 |
The Microsoft Graph API connector now lets you assign and revoke directory roles to an Azure AD user account and query the target instance for roles |
OPENICF-2088 |
The Microsoft Graph API connector now lets you assign and revoke custom roles to an Azure AD user account and query the target instance for roles |
OPENICF-2102 |
Assign and revoke PermissionSets and Groups to Salesforce user accounts in the Salesforce connector |
OPENICF-2110 |
Expose groups and roles through user object in the ServiceNow connector |
OPENICF-2111 |
View, update, and remove a group’s roles through the role object in the ServiceNow connector |
OPENICF-2129 |
The LDAP connector now includes a parameter to use isMemberOf by ldapGroups |
OPENICF-2192 |
In the Google Apps connector, don’t throw an NPE when updating a user with a change to license assignments if _NAME_ is not specified |
OPENIDM-17876 |
Query filter editor no longer removes double quotes from all properties that aren’t of type string |
OPENIDM-17936 |
Saving changes to the authzRoles field on users no longer overrides the field type |
OPENIDM-18001 |
Country codes in locales are no longer ignored when sending emails |
OPENIDM-18077 |
Added new default policy, cannot-contain-others-case-insensitive |
OPENIDM-18153 |
Custom script exception messages are no longer incorrectly truncated in REST responses |
OPENIDM-18238 |
Improved resiliency of clustered reconciliations |
OPENIDM-18243 |
Validate that connector names are alphanumeric |
OPENIDM-18260 |
New sync mapping fields, defaultSourceFields and defaultTargetFields, let you specify which fields to use for read and query requests |
OPENIDM-18261 |
Endpoints within /system now support specifying additional fields when using wildcards |
OPENIDM-18275 |
The groups' name field is now searchable |
OPENIDM-18319 |
An up-to-date target object state is now provided in sync script bindings and sync audit mechanisms |
OPENIDM-18336 |
The default assignment object schema now contains a "condition" field |
OPENIDM-18498 |
Queued sync not triggered if target is a CREST proxy endpoint |
OPENIDM-18501 |
Tenant administrator password policy no longer restricts passwords to a maximum length |
OPENIDM-18629 |
Reconciliation job identifiers now use a more precise timestamp |
OPENIDM-18650 |
Add new SCIM connector; applications now support creating connections to SCIM services |
01 Mar 2023
| Issue ID | Summary |
|---|---|
IAM-3089[49] |
Unable to exit a social provider and select a different social provider in a journey |
22 Feb 2023
Resolved issues
| Issue ID | Summary |
|---|---|
FRAAS-14069 |
Add |
FRAAS-14030 |
Add inner classes from |
FRAAS-13974 |
Add class |
FRAAS-13597 |
Remove unexpected changes from promotion reports |
14 Feb 2023
Key features
- Support for REST connector applications
-
Application management now lets you register, provision, and manage REST connector applications.
For details, refer to Scripted REST connector.
Resolved issues
| Issue ID | Summary |
|---|---|
IAM-2879 |
Allow properties in forms to be reordered |
IAM-3094 |
Add support for enumerated values in array attributes |
IAM-3156 |
Update the descriptive text in the "Add Property" modal to be more accurate |
IAM-3261 |
Adjust Autonomous Access risk filter to better handle scoring edge cases |
IAM-3262 |
Adjust menu width on the Autonomous Access Risk Administration page |
IAM-3461 |
Fix display of OAuth 2.0 applications with a UUID for a name |
IAM-3492 |
Fix objects ending in |
09 Feb 2023
Key features
- OneSpan authentication journey nodes
-
The new OneSpan authentication journey nodes integrate OneSpan Intelligent Adaptive Authentication (IAA) scoring for identity proofing, continuous authentication, and fraud protection.
For details about OneSpan authentication integration set up, refer to OneSpan.
- Jumio identity verification
-
The new Jumio identity verification integrates with Jumio’s NetVerify service to easily and securely verify identity by using facial recognition to authenticate against government issued IDs.
For details about Jumio identity verification, refer to Jumio identity verification.
- Logout for all server-side sessions for a user or set of users
-
Administrators can now invalidate (log out) all server-side sessions for a user by sending a POST request to the
json/sessionsendpoint with thelogoutByUseraction, specifying the username in the request payload. - Composite advice with an AuthLevelCondition in journeys
-
Composite advice gives AM hints about which authentication services to use when logging in a user. Journeys now take into account the AuthLevelCondition composite advice.
For example, you can now use AuthLevelCondition composite advice so that AM uses a journey that provides an authentication level of 10 or higher.
Resolved issues
| Issue ID | Summary |
|---|---|
AME-22942 |
Log out all server-side sessions for a user or set of users so that they have to reauthenticate |
FRAAS-13454 |
Integrate Jumio identity verification journey nodes |
FRAAS-13555 |
Integrate OneSpan authentication nodes |
FRAAS-13809 |
Autonomous log filters fail in connected environments |
OPENAM-11319 |
Add description key to the JSON response from OAuth2UserApplications#getResourceResponse |
OPENAM-16374 |
Add support for composite advices with a AuthLevelCondition to journeys |
OPENAM-18270 |
Don’t raise errors when calls to the access_token endpoint specify the scope parameter in OAuth2 authorization_code exchange |
OPENAM-18488 |
Handle the CA certificate correctly for Windows Hello attestations |
31 Jan 2023
Resolved issues
| Issue ID[50] | Summary |
|---|---|
FRAAS-13011 |
Security improvements |
IAM-2025 |
Add Uncategorized to the journey category filter |
IAM-3107 |
Remove bitwise filter on Active Directory page |
IAM-3108 |
Update Maintain LDAP Group Membership option to not be selected by default |
IAM-3109 |
Update cn property to be optional in Active Directory target mode |
IAM-3110 |
Update ldapGroups property to be available by default in Active Directory target mode |
IAM-3111 |
Fix password hash algorithm |
IAM-3139 |
Fix Revoke button in users and roles to revoke users, and not be clickable when there are no users to revoke |
IAM-3142 |
Fix Active Directory user filter anomaly when deleting a row |
IAM-3146 |
Update user-specific attributes to be editable by administrators |
IAM-3257 |
Fix escaping of ESV placeholders in the advanced email editor |
27 Jan 2023
Resolved issues
| Issue ID | Summary |
|---|---|
FRAAS-13464 |
Adjust sandbox environment migration to not use development environment migration steps |
FRAAS-13478 |
Remove unrelated AM root realm changes from promotion reports |
FRAAS-13620 |
Improve performance of promotion report generation by removing unrelated data |
IAM-2305[50] |
Add support for localized logos in end-user UI |
IAM-3091[50] |
Fix localized headers rendering as [object Object] |
25 Jan 2023
Key features
- Improved access control for hosted pages
-
You can now block access separately for hosted end user account and journey pages:
-
Advanced Identity Cloud displays account pages after authentication for user profile and delegated administration details.
-
Advanced Identity Cloud displays journey pages during authentication for login, registration, password reset, and more.
By default, Hosted pages are active and accessible for accounts and journeys.
To disable access through the Advanced Identity Cloud admin console, go to Tenant Settings > Global Settings > End User UI and select the pages to disable.
-
Resolved issues
| Issue ID | Summary |
|---|---|
IAM-2735 |
SAML application improvements, including adding ability to update metadata without recreating application and adding ability to download IdP certificate from application |
IAM-3044 |
Applications list overflows when screen size is reduced |
IAM-3084 |
Only allow unique values when adding application owners |
IAM-3141 |
Add the ability to promote dynamic configuration attached to application |
IAM-3151 |
Remove redirect to global settings during administrator login |
IAM-3183 |
Let users filter the trends dashboard by date without resetting the journeys dashboard |
IAM-3339 |
After refreshing the realm settings page, set the current tab using the identifier specified in the URL fragment |
FRAAS-7542 |
Control access to hosted account and journey pages |
FRAAS-11599 |
Don’t allow changes to scripts in staging and production environments |
13 Jan 2023
Key features
- Service accounts
-
You can now use service accounts to request access tokens for most Advanced Identity Cloud REST API endpoints without relying on a particular identity in your system:
-
Call Identity Cloud APIs programmatically without needing a human identity.
-
Access AM or IDM APIs in the same way using a signed JWT.
-
Set scopes on each service account to assign only necessary permissions to access tokens.
-
Use for automation and CI/CD tooling.
For details, refer to Service accounts.
-
Resolved issues
| Issue ID | Summary |
|---|---|
FRAAS-8477 |
Service accounts |
IAM-1939 |
Fix hCaptcha support in Platform UI |
IAM-2224 |
Replace bullets with checkmarks when validating password policy |
IAM-2847 |
Increase the size of the terms and conditions modal window |
IAM-2912 |
Enable promotions UI to ignore encrypted secrets |
IAM-3011 |
Update risk configuration UI to show only user-modifiable configuration |
IAM-3012 |
Add new |
IAM-3015 |
Update risk configuration evaluation UI so that updates use the new APIs |
IAM-3016 |
Fix the |
IAM-3041 |
Prevent proceeding from the Active Directory modal window without entering base DNs |
IAM-3076 |
Fix Salesforce provisioning connection |
IAM-3079 |
Fix single sign-on (SSO) setup when app name has a space |
IAM-3088 |
Enable suppression of the login failure message from the failure node |
IAM-3122 |
Fix font weight of the title text on provisioning tab |
IAM-3145 |
Fix Active Directory assignment on array attributes to be a merge and not replace |
IAM-3177 |
Add paging back to application list view if workforce feature is not enabled |
IAM-3335 |
Fixed display of localized favicon |
04 Jan 2023
Resolved issues
| Issue ID | Summary |
|---|---|
FRAAS-13242 |
Improve invalid page size error message |
OPENAM-19485[51] |
Access multi-tenant social providers without requiring multiple secondary configurations |
OPENIDM-17392 |
Prevent script typos that cause services to fail from being introduced into the system |
OPENIDM-17953 |
Support email addresses that contain non-ASCII UTF-8 characters |
2022
20 Dec 2022
Key features
- BioCatch authentication nodes
-
The new BioCatch authentication nodes integrate BioCatch scoring for identity proofing, continuous authentication, and fraud protection.
For details, refer to Marketplace journey nodes.
09 Dec 2022
Key features
- Event hooks
-
Event hooks let you trigger scripts during various stages of the lifecycle of users, roles, assignments, and organizations.
You can trigger scripts when one of these identity objects is created, updated, retrieved, deleted, validated, or stored in the repository. You can also trigger a script when a change to an identity object triggers an implicit synchronization operation.
Post-action scripts let you manipulate identity objects after they are created, updated, or deleted.
For details, refer to Event hooks.
07 Dec 2022
Resolved issues
| Issue ID | Summary |
|---|---|
FRAAS-12494 |
Unlock the environment and stop checking progress after successfully promoting an environment |
FRAAS-12988 |
Prevent placeholder support being enabled unless a specific migration flag value is set |
OPENIDM-17556 |
Ensure RDVPs are not erased for all types of managed objects for all types of PUT operations |
06 Dec 2022
Key features
- Workforce application and connector management
-
In new tenants created on or after January 12, 2023, you can use the improved applications page to integrate Advanced Identity Cloud with external data stores or identity providers. The applications page acts as a one-stop location where you can:
-
Register and provision popular federation-capable applications quickly and easily by choosing from a library of templates, such as Salesforce and Workday.
-
Register and provision your organization’s custom applications.
-
Manage data, properties, rules, SSO, provisioning, users, and groups for an application.
-
View the connection status of each application.
-
Activate and deactivate an application.
For details, refer to Application management improvements (new tenants only).
-
- Daon IdentityX authentication nodes
-
The new Daon authentication nodes let you integrate with the Daon IdentityX platform for MFA with mobile authentication or out-of-band authentication using a separate, secure channel.
For details, refer to Marketplace journey nodes.
Resolved issues
| Issue ID | Summary |
|---|---|
FRAAS-11574 |
Integrate Daon authentication journey nodes |
IAM-2658 |
Application management improvements |
DATASCI-1548 |
Update the filter text on the Autonomous Access dashboard from "All Risk Scores" to "Risk Score" |
DATASCI-1550 |
Update text on the Autonomous Access dashboard’s Copy on User Detail page |
29 Nov 2022
Key features
- Onfido authentication nodes
-
The new Onfido authentication nodes let you use Onfido’s solution for collecting and sending document identification and, optionally, biometrics to the Onfido backend for verification.
For details, refer to Marketplace journey nodes.
23 Nov 2022
Resolved issues
| Issue ID | Summary |
|---|---|
IAM-2354 |
Add system notification capability to UI |
IAM-2355 |
Self-service promotions migration UI |
IAM-2465 |
Password policy to force password expiry not working |
IAM-2706 |
Embedding images in the theme editor only displays alternative text |
IAM-2739 |
Email suspend message displayed without line breaks |
IAM-2939 |
Add translation configuration key for "Passwords do not match" message |
IAM-2973 |
Self-service promotions migration UI flow should enable promotions UI features |
08 Nov 2022
Key features
- Group management
-
You can now create and manage groups that are shared across AM and IDM within your Advanced Identity Cloud instance. New tenants have group management enabled by default, and existing tenants can follow an upgrade path to enable it.
For more information, refer to Group management.
02 Nov 2022
Key features
- ID Cloud Analytics Dashboard enhancements
-
You can now take advantage of the following enhancements to the analytics dashboard:
-
The journey chart now lets users drill down at specific points on a trend line to view individual journey outcomes for that date/hour. Journeys are sorted by a ranking of percentage failures, but can also be sorted based on number ranking.
-
Two new widgets — Top Five Journeys by Outcome and Top Five Journeys by Usage — that rank trending journeys based on outcomes and usages are now available.
For more information, refer to Advanced Identity Cloud analytics dashboard.
-
25 Oct 2022
Key features
- Self-service promotions
-
Self-service promotions let you promote configuration between environments without raising a support ticket. You can perform self-service promotions from development to staging tenant environments, and from staging to production tenant environments. You cannot promote sandbox environments.
For more information, refer to Introduction to self-service promotions.
- Configuration placeholders visible in all APIs
-
Configuration placeholders let you set ESVs in your configuration.
For more information, refer to Manage configuration placeholders using the API.
19 Oct 2022
Key features
- Duo authentication node
-
The new Duo authentication node lets you use Duo’s solution for adaptive authentication, bring your own device security, cloud security, endpoint security, mobile security, and two-factor authentication.
- Twilio authentication node
-
The new Twilio authentication node allows you to use Twilio for two-factor authentication during account setup, sign-on, and other scenarios. The node lets you integrate Twilio’s APIs to build solutions for SMS and WhatsApp messaging, voice, video, and email. The node uses Twilio’s latest Lookup API, which uses real-time risk signals to detect fraud and trigger step-up authentication when needed.
For details, refer to Marketplace journey nodes.
Resolved issues
| Issue ID | Summary |
|---|---|
ANALYTICS-52 |
Correct the value in the All Journeys field |
DATASCI-1437 |
Correct prefilled username fields in Filters window |
DATASCI-1474 |
Don’t show explainability if not specified in response after applying Unusual Day of Week filter |
DATASCI-1497 |
Let users see previously selected risk reasons after closing the Filter window |
DATASCI-1504 |
Prevent the truncation of text on the right side of pages |
FRAAS-11570 |
Add Duo authentication node |
FRAAS-11571 |
Add Twilio authentication node |
FRAAS-11825 |
Add translation configuration key for no search results message |
FRAAS-12301 |
Add Marketplace nodes to journey editor menu |
FRAAS-12413 |
Remove blank page shown when user returns to login page following successful login to custom domain |
IAM-1935 |
Expose ESV variable type in the UI |
IAM-2038 |
Prevent theme styles rendering in the hosted pages editor |
IAM-2066 |
Show the entire answer to a long security question after clicking the visibility icon |
IAM-2259 |
Do not let users save email templates that contain JavaScript |
IAM-2312 |
Render SVG images correctly |
IAM-2411 |
ForgeRock favicon displays briefly before the customer’s favicon |
IAM-2502 |
Remove flashing red text from security questions window |
IAM-2633 |
Support localization for radio display fields in Choice Collector node |
IAM-2696 |
Remove legend from Risk Score window |
IAM-2869 |
Update UI regex validation for ESV list type |
22 Sep 2022
Resolved issues
| Issue ID | Summary |
|---|---|
AME-22684 |
Include grace period configuration in the OAuth2 provider settings |
OPENAM-18112 |
Provide better error message when an LDAP authentication node encounters a TLS connection issue |
OPENAM-19196 |
Do not wait for cache timeout before OAuth2 clients reflect changes to Javascript origins |
OPENIDM-16420 |
Update the default email validation policy to conform with RFC 5322 |
OPENIDM-17533 |
Allow configuration changes to the repo.ds.json file to take effect without restarting IDM |
OPENIDM-17720 |
Fix null pointer exception when the repo.ds.json file is misconfigured |
OPENIDM-17836 |
Fix for startup error message caused by ObjectMapping constructor exception |
OPENIDM-17911 |
Fix email validation errors in the IDM admin UI (native console) |
20 Sep 2022
Resolved issues
| Issue ID | Summary |
|---|---|
DATASCI-1165 |
Remove Automated User Agent from the list of risk reasons filters |
DATASCI-1358 |
Let users filter dashboards by date, risk scores and features |
DATASCI-1365 |
Update the Risk Activity page when applying a filter without requiring users to refresh the page |
DATASCI-1394 |
Show the times that events occurred correctly without requiring users to refresh the display |
DATASCI-1395 |
Let users see their last five risky authentication attempts |
DATASCI-1397 |
Remove risk administration options from end users' navigation menus |
DATASCI-1406 |
When filtering activities using a date range, include the activities that occur on the end date |
IAM-1678 |
Allow login journey attributes that are not required to have empty values |
IAM-1682 |
When editing email templates, cut text correctly |
IAM-1932 |
When placeholders are used, display read-only strings in the Platform UI |
IAM-2028 |
Remove excess space from journey editor fields that do not require floating labels |
IAM-2064 |
Replace fields for specifying numeric thresholds with a risk score definition slider in Autonomous Access Decision nodes |
IAM-2080 |
Let users create customized footers on Page nodes |
IAM-2141 |
Add option to customize Page node background color |
IAM-2142 |
Add option to customize Page node button width |
IAM-2143 |
Add option to customize label text for Page node fields |
IAM-2227 |
Remove spurious "No configuration exists for id external.email" pop-up warning |
IAM-2249 |
Add option to display Message node as a link |
IAM-2250 |
After importing journeys, let user delete all imported journeys with a single delete action |
IAM-2251 |
Provide a value when the object.password variable is specified in an email template |
IAM-2258 |
Remove tenant information from the realm menu |
IAM-2285 |
Make H2, H3, and H4 HTML headings bigger when there’s no higher-level predecessor heading |
IAM-2290 |
Show the correct number of events per country on the Activity Risk dashboard |
IAM-2294 |
Show previous authentication attempts when doing anomaly lookups |
IAM-2320 |
Change the default navigation background color of Account pages without changing the dashboard color |
IAM-2329 |
Change the color of the Autonomous Access event log indicator to red |
IAM-2351 |
Correct pagination on the Autonomous Access Risk page |
IAM-2373 |
Make dashboard analytics pipeline logs in Autonomous Access work as expected |
IAM-2468 |
Wrap long security questions |
IAM-2521 |
Don’t reuse authId during password validation |
OPENAM-18933 |
Do not override the Success URL node’s value |
SDKS-1720 |
Point developers to the ForgeRock SDKs when they create an OAuth2.0 client in the Platform UI |
SDKS-1721 |
Point developers to the ForgeRock SDKs when they configure CORS in the Platform UI |