Viewing policy events in the PingID report
Generate a PingID report to view a range of PingID events.
About this task
There are two types of policy events included in the PingID report:
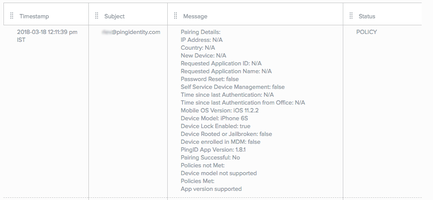
Pairing Detailsevent-
Provides details of a user’s pairing attempt, based on the Device & Pairing rules. For more information, see Device and pairing policy.
Authentication Detailsevent-
Provides details of a user’s authentication attempt, based on the defined policy rules together with the Device & Pairing rules. For more information, see Configuring a global authentication policy (default policy), Configuring a RADIUS PCV and SSH access policy, and Device and pairing policy. The entry also indicates the apps and groups to which a policy is applied, if applicable.
|
Steps
-
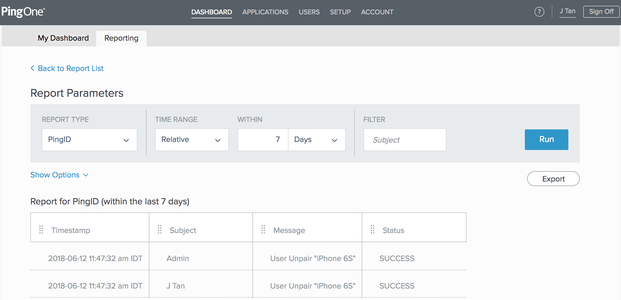
In the PingOne admin console, go to Dashboard → Reporting.
-
From the Report Type list, select PingID.
-
In the Within field, enter
7, and then select Days from the list. Click Run.You can filter the results by changing the Time Range or entering a string in the Filter field and then running the report again.
Result
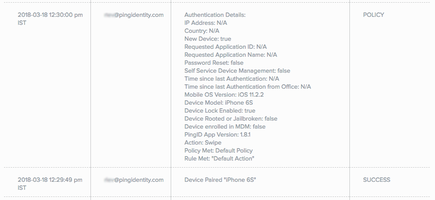
The PingID report displays, showing results for the past 7 days by default. Policy-related entries are identified by the following information:
- Timestamp
-
The time at which the policy event occurred.
- Subject
-
The user to whom the policy was applied.
- Message
-
A list of policy-related fields providing detailed information about policy-related events. The first line of the Message field indicates whether the event is a
Pairing Detailsevent or anAuthentication Detailsevent. - Status
-
The status
POLICYindicates that the event is a policy related event.
Each policy entry lists values for the relevant policy elements. The following table describes the elements that can be included in a policy event and their potential values. NOTE: The order of the elements in the table corresponds to the order of the elements in the displayed report.
| Policy element | Value |
|---|---|
Type of event |
|
IP Address |
The IP address of the accessing device. |
Previous Authentication IP |
The IP address of the IP address of the accessing device used in the previous sign on. |
Previous Authentication Time |
The time of the last successful authentication. |
IP Reputation Whitelist Met |
Indicates whether the IP address of the accessing device appears in the IP reputation rule white list ( |
Geovelocity Whitelist Met |
Indicates whether the IP address of the accessing device appears in the Geovelocity rule white list ( |
IP Risk Score |
The risk score category of the IP address of the accessing device ( |
Country |
The location from which the accessing device is communicating. |
Previous Country |
The location from which the accessing device communicated during the last sign on. |
Ground Speed |
The speed taken to travel between the current login location and the previous location, in the time that elapsed since the previous sign on ( |
Current VPN/Proxy login |
Whether the accessing device for the current sign on is using a proxy or VPN. Possible values are |
Previous VPN/Proxy login |
Indicates the accessing device for the previous sign on was using a proxy or VPN. Possible values are |
New Device |
Whether the accessing device is new. Possible values are |
Requested Application ID |
The ID of the app the user is trying to access. |
Requested Application Name |
The name of the app the user is trying to access. |
Password Reset |
Indicates whether the user tried to reset the SSO password. Possible values are |
Self Service Device Management |
Whether the user tried to access the Devices page. Possible values are |
Time since last Authentication |
The amount of time that has passed since the last authentication. |
Accessing Device UserAgent |
The user agent string of the browser on the accessing device. |
Accessing Device OS |
The name and version of the OS on the accessing device, for example, |
Accessing Device Browser |
The browser used on the accessing device, for example, |
Allowed Authentication Methods |
The allowed authentication methods in the applied policy. This information is displayed in the event that a user attempts to authenticate with a device that is not allowed by this policy. |
Time since last Authentication from Office |
The last time the user authenticated from the office, in minutes. If no office is defined, the value is |
Mobile OS Version |
The OS name and version of the authenticating device. For example, |
Device Model |
The make and model of the authenticating device. For example, |
Device Lock Enabled |
Whether device lock is enabled on the mobile device. Possible values are |
Device Rooted or Jailbroken |
Whether the mobile device rooted or jailbroken. Possible values are |
Device enrolled in MDM |
Whether the mobile device is enrolled in mobile device management (MDM). Possible values are |
PingID App version |
The version of the PingID app on the user device. For example, |
Action |
The action defined for this policy:
|
Policy/Policies not Met |
The name of the policy/policies that were not met during the pairing or authentication action. |
Policy/Policies Met |
The name of the policy or policies with which the action complied. |
Rule Met |
The rule within the policy that was executed. |
Group Affected |
The groups to which the policy was applied. |
Policy event examples
The following examples illustrate common policy event scenarios.
Authentication not requested because the user recently authenticated successfully
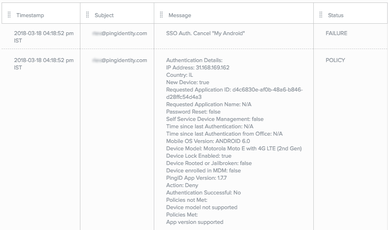
When performing an action that normally requires authentication, a user is not requested to authenticate (Action:Approve) because they already authenticated within the time stated in the policy (Rule Met: "Time since user’s last authentication: 2 minutes".
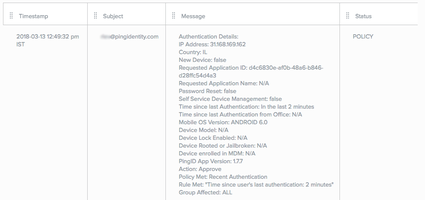
Authentication unsuccessful
The policy does not support the specific mobile device. Authentication is denied to a user attempting to sign on using a device that is no longer supported (Device Model: Moto E with 4G LTE (2nd Gen); Authentication Successful: No; Policies not Met: Device model not supported).