Configuring FIDO2 authentication for PingID
PingID supports the FIDO2 authentication method. FIDO2 authentication allows users to authenticate using passkeys and other FIDO2-compatible authenticators.
About this task
Passkeys are FIDO credentials that are discoverable by browsers or housed within native applications or security keys for passwordless authentication. There are a wide range of devices that can be used as a passkey, including Windows Hello, iOS 14 and later, Android 7.0 and later, Apple Mac machines with fingerprint authentication capabilities, and FIDO2 security keys. PingID also supports non-discoverable credentials (FIDO2 devices that are not defined as passkeys).
To learn more about passwordless authentication using Passkeys, see Configuring passwordless authentication for passkeys.
|
PingID receives confirmation that a device has the relevant WebAuthn FIDO2 capabilities with the authenticating browser. If the capabilities are not sufficient, such as the browser is not supported, the OS does not support biometric authentication, or a compatible authentication method is not defined, the user will be unable to authenticate with the passkey device and might be unable to authenticate at all if that is their only authenticating device. |
To enable users to authenticate using FIDO2 authentication, the high-level flow is as follows:
Steps
-
In the Admin portal, enable FIDO2 authentication.
For more information, see Configuring passwordless authentication for passkeys or Configuring FIDO2 authentication method for MFA authentication.
-
Optional: Define a PingID policy.
For more information, see Authentication policy.
-
Have the user register their FIDO2 biometrics device and pair it with their PingID account to create a trust between the device and the user’s account, so they can use it authenticate during the sign-on process.
For more information, see the following sections in the PingID User Guide:
FIDO2 authentication requirements and limitations
The following list details the requirements and limitations when using FIDO2 with PingID.
FIDO2 passkey requirements and limitations are constantly evolving. For a list of the most up-to-date operating systems and browsers supported, see Device support.
General requirements:
To use FIDO authentication make sure that:
-
The PingID environment is integrated with PingOne. Learn more.
-
You enable FIDO2 authentication method in the admin portal. If you have an account that was previously using the security key or FIDO2 biometrics authentication methods, see also Updating a PingID account to use PingOne FIDO2 policy for Passkey support.
-
The user must perform registration and authentication with a WebAuthn supported browser (such as the latest versions of Google Chrome, Safari, or Microsoft Edge), that is running on a WebAuthn supported platform (such as Windows, MacOS, iOS, or Android).
-
PingID supports FIDO2 and U2F security keys.
U2F security keys can only generate a single credential per domain. A device can only be paired by one user per domain.
-
YubiKeys can be paired for either:
-
Security Key FIDO2 authentication
-
YubiKey OTP authentication
PingID YubiKeys that feature one-time passcode (OTP) support only, or for which you only want to use OTP authentication, should be paired as a YubiKey authentication method rather than as a security key. For more information, see Configuring YubiKey authentication (Yubico OTP) for PingID.
-
Passwordless authentication requirements:
-
When configuring a PingFederate policy for passwordless authentication with FIDO2 passkeys, you must use PingID Integration kit 2.7 or later, with PingFederate v9.3 or later.
-
To enable passwordless authentication, FIDO2 requires Discoverable Credentials. Make sure that in the relevant FIDO2 policy make sure that the Discoverable Credentials field is set to either Preferred or Required.
General limitations:
-
FIDO2 authentication is only supported for Web authentication, and Windows and Mac login machines.
-
WebAuthn timeout is defined for 2 minutes. The actual timeout value might vary depending on the browser used.
-
A user can pair more than one FIDO2 credential with their account, however, they cannot pair the same FIDO2 credentials with their account more than once.
-
Some browser versions might not support FIDO2 authentication when using incognito or private mode.
-
If an an iOS or Mac Touch ID device is paired with PingID, clearing history and website data from the device’s Safari settings will prevent a user from using PingID to authenticate. The user must unpair their device and then pair the device again to authenticate with PingID.
-
Security keys can be used for web-based authentication through WebAuthn supporting browsers only.
Second factor authentication limitations:
-
Android devices that are paired within a workspace can only be used to authenticate in the same workspace.
For troubleshooting, see the relevant section in the PingID User Guide.
Windows login and Mac login limitations:
Users authenticating as part of a Windows login, Windows login (passwordless), or Mac login authentication flow can only authenticate using a security key. PingID determines whether a passkey is a security key based on the Authenticator Attachment and the Transports attributes that are presented in the AuthenticatorAttestationResponse. Learn more about these authentication flows:
Configuring passwordless authentication for passkeys
FIDO2 passwordless authentication enables you to identify and authenticate a user based on the FIDO2 protocol without requiring the user to enter their username and password.
About this task
To configure FIDO2 passwordless authentication, you must configure a PingFederate policy for a passwordless authentication flow. FIDO2 must then be enabled in the administrative console.
The process of registering a FIDO2 passkey is the same for both a passwordless and a multi-factor authentication flow. The user is directed to the relevant flow, according to your organization’s configuration. Once registered, the same FIDO2 passkey can be used to authenticate with either flow.
|
This feature requires PingFederate 9.3 or later. For more information, see FIDO2 authentication requirements and limitations. |
Steps
-
In the PingFederate administrative console, create a policy for passwordless authentication.
For more information, see Configuring a PingFederate policy for passwordless authentication with FIDO2 passkeys.
-
Sign on to the PingID admin console and enable FIDO2 authentication.
-
Go to Setup → PingID → Configuration.
-
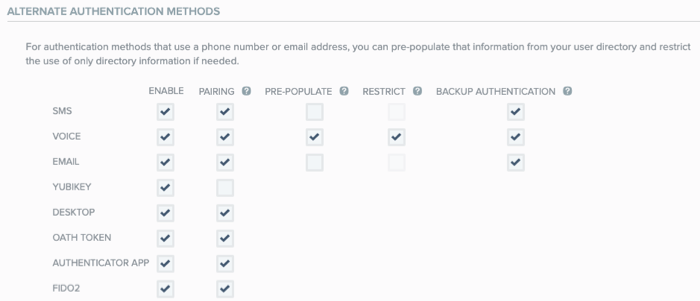
Go to the Alternate Authentication Methods section, and in the FIDO2 row, select the Enable check box.
-
Click Save.
-
-
To ensure your FIDO2 policy allows the use of Discoverable Credentials. Non-discoverable credentials cannot be used for passwordless authentication flows.
-
In the PingOne admin portal, go to Authentication → FIDO.
-
On the FIDO Policies page, in the relevant FIDO policy, in the Discoverable Credentials field, select either Preferred or Required. For information, see Adding a FIDO policy.
-
Result
The changes are saved, and users can pair a passkey and use it for passwordless authentication.
Configuring FIDO2 authentication method for MFA authentication
To allow users to pair and authenticate using passkeys for MFA (Multi-factor authentication), enable FIDO2 authentication in the admin portal.
About this task
Users must enter their username (and password, if required), and are then prompted to authenticate with their passkey.
|
To configure passwordless authentication for passkeys using the FIDO2 authentication method, see Configuring passwordless authentication for passkeys. |
Steps
-
Sign on to the admin portal.
-
Go to Setup → PingID → Configuration.
-
Go to the Alternate Authentication Methods section, and in the FIDO2 row, select the Enable check box.

-
Click Save.
Result
Users can pair and authenticate passkey devices. For examples, see Using Windows Hello for authentication, Using Apple Mac Touch ID for authentication, and Using Android biometrics for authentication in the PingID End User Guide.