Configuring PingID MFA for Microsoft Azure AD Conditional Access
Integrating PingID multi-factor authentication (MFA) requires setting up the configuration in the admin portal and in Azure AD.
About this task
Setting up PingID MFA for Microsoft Azure AD Conditional Access involves the following steps:
-
In the admin portal, set up the integration, including attribute mapping.
-
In Azure AD:
-
Create a PingID MFA custom control.
-
Create a PingID MFA conditional access policy.
-
-
Optionally apply a PingID MFA policy to the Azure AD integration.
Default attribute mapping is based on the attributes that Azure sends to PingOne during the authorization request to trigger PingID MFA and includes the following attributes.
| PingID PingIDattribute | Azure AD attribute |
|---|---|
|
|
|
|
|
|
Steps
-
In the Admin portal, go to Setup → PingID → Client Integration.
-
In the Integrate with Microsoft Azure AD section, click Setup Integration.
Result:
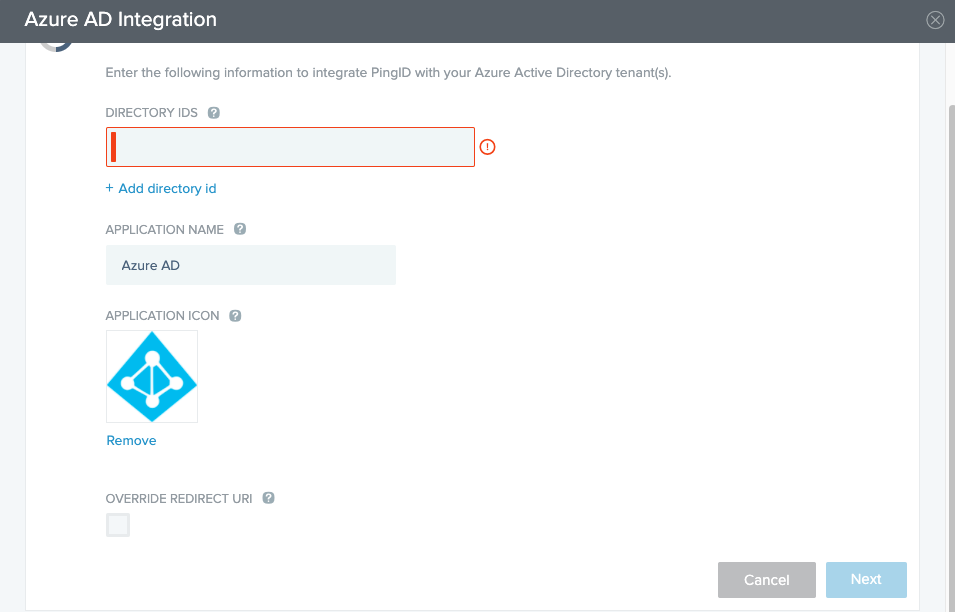
The Azure AD Integration window opens.
-
To find the relevant Directory ID, in the Azure portal:
-
In the FAVORITES menu in the left side bar, go to Azure Active Directory.
-
In the Manage section, click Properties.
-
Copy the value from the Directory ID field.
-
-
In the Admin portal:
-
Paste the directory ID value into the Directory IDS field.
-
Optional: To add additional directory IDs, click Add directory ID and paste the relevant Directory ID, as it appears in the relevant Azure AD account.
The directory ID must be a valid UUID string.
-
In the Application Name field, enter the name you want to use to represent authorization requests from Azure AD.
This is the name that users will see displayed if using the PingID mobile app during authorization. This name is also used to identify the Azure AD application in the PingID policy applications list.
-
To change the application icon, choose one of the following:
-
Select a new icon: Click the application icon and go to the icon you want to use.
-
Use the default icon: Click Remove.
The PingID mobile app displays the selected icon during authorization.
-
-
If your environment uses a redirect URI that is different than the default Azure AD redirect URI, use the Override Redirect URI field to specify the correct URI.
-
Click Next.
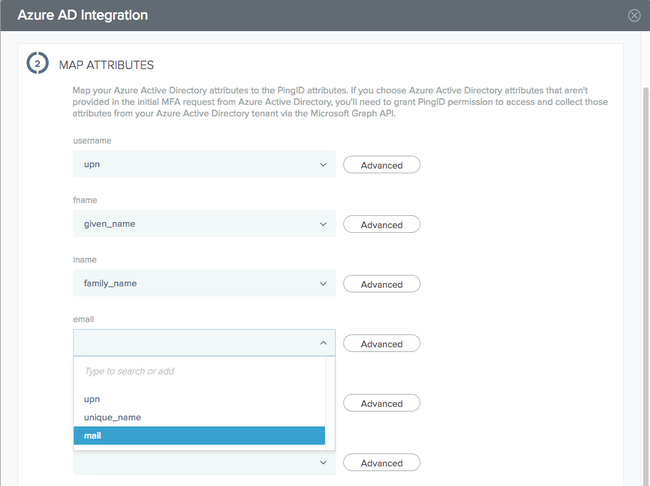
The Map Attributes tab opens, displaying the default attribute mapping.
-
-
Optional: To map Azure AD attributes that are not provided in the initial MFA request to the relevant PingID attributes:
-
In the relevant attribute field, select the Azure AD attribute from the drop-down list, or type the attribute into the field.
By default, the username for PingID is taken from the upn attribute in Azure. However, if you are also using Azure as the identity provider (IdP) for PingOne for Enterprise, make sure that you select from the list the attribute that you mapped to MFA_SUBJECT. Otherwise, you may end up with a situation where a single user is listed as two different users: one whose username comes from the upn attribute and one whose username comes from the attribute mapped to MFA_SUBJECT.
-
To perform attribute transformations on a specific attribute, in the relevant row, click Advanced and configure the fields as required.
For more information, see Creating advanced attribute mappings.
-
Click Next.
-
If you included Azure AD attributes that are not provided in the initial MFA request from Azure AD, you’ll receive a prompt requesting that you grant PingID permission to access and collect those attributes from your Azure AD tenant.
If you are not prompted to grant permissions, skip this step.
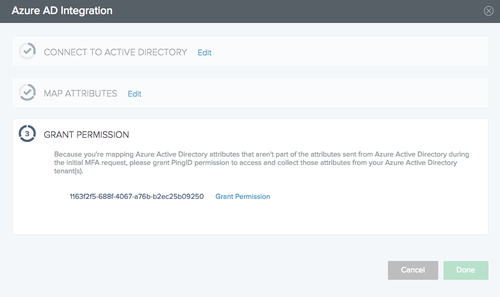
In the Grant Permission window, for each Azure AD tenant:
-
To open the Azure login window, in the Grant Permission section, click Grant Permission.
-
To grant the relevant access to PingID, sign on to your Azure AD Tenant and click Accept.
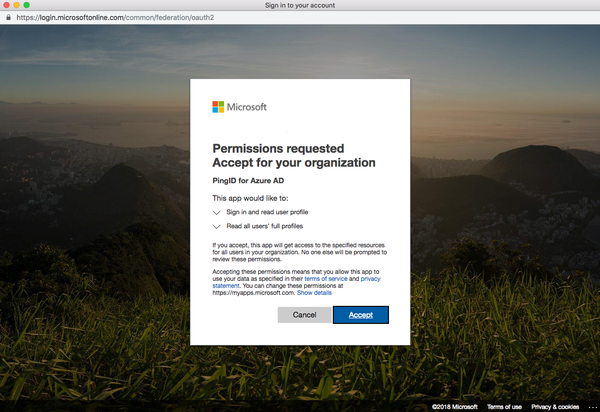
You are redirected back to the Azure AD Integration window.
-
-
If you selected an attribute mapping for the
memberOfgroup attribute in the Admin portal, when prompted to synchronize groups, select the Synchronize Groups box to copy your Azure AD group names into PingID and click Next.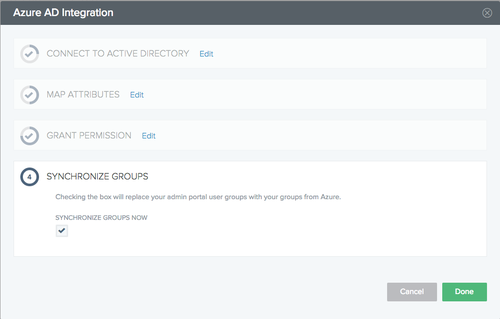
Result:
After groups are synchronized and the integration is complete, Azure groups appear in the PingID policy groups list, and the User Groups list at Users → User Groups, enabling you to apply the PingID policy to your Azure groups.
-
-
To save the integration, click Done.
The custom control JSON object that is generated includes a summary of the attribute mapping. This custom control JSON must be provided to your Azure AD account.
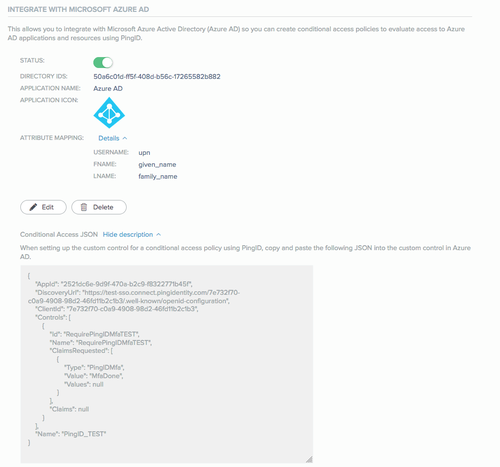
-
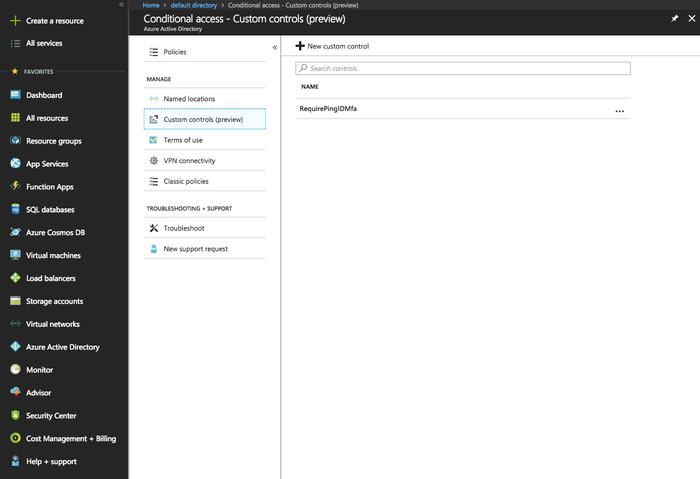
In the Azure AD portal, create a new PingID MFA custom control:
-
On the left side bar, click Azure Active Directory.
-
In the Security section, go to Conditional access → Custom controls.
-
Click New custom control.
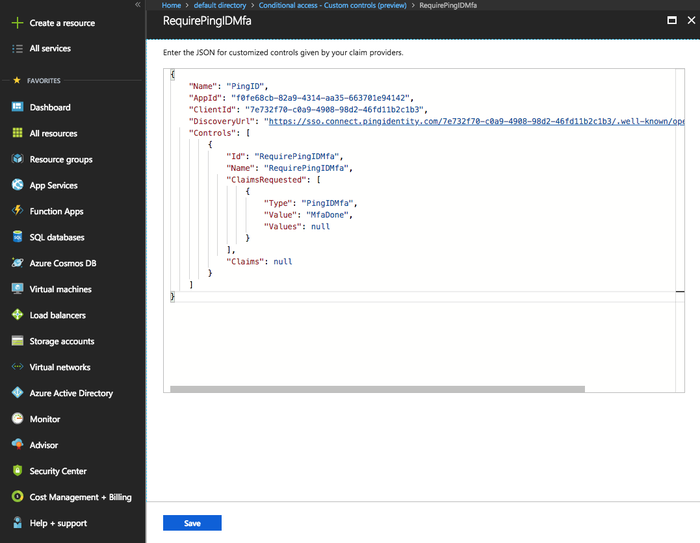
-
Delete the default JSON text, and then paste the custom control JSON that you copied from the PingOne admin portal into the Azure AD custom control field.
-
Click Create.
Result:
The new custom control appears in the custom controls list.
-
-
In the Azure AD portal, create a new PingID MFA conditional access policy.
To avoid blocking administrator access to the Azure AD portal, do not apply the PingID policy to all users and applications until you have successfully tested the integration between Azure AD and PingID.
-
Go to Azure Active Directory → Conditional access.
-
Click New policy.
-
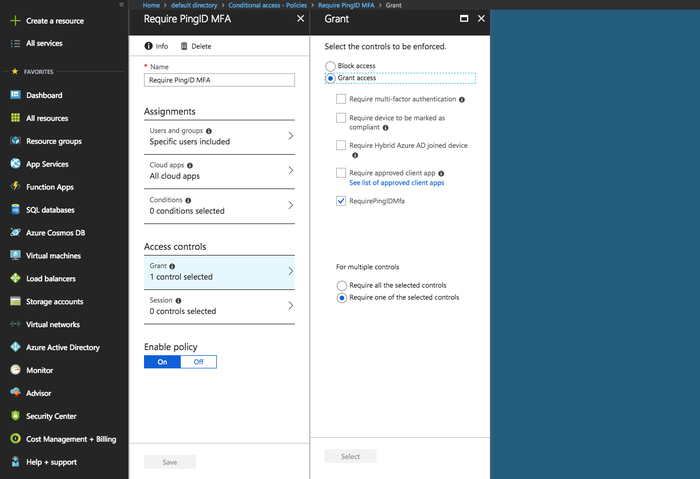
Enter a meaningful name for the policy (for example, Require PingID MFA).
-
To specify which users and groups the policy applies to, in the Assignments section, click Users and groups. On the Include tab, select the users and groups that you want to include in the policy. Click Select.
-
To specify which cloud apps you want the policy to apply to, in the Assignments section, click Cloud apps. On the Include tab, click Select apps, and select the relevant apps. Click Select.
-
Go to Access controls → Grant, click Grant access, and select the check box next to the custom control that you created earlier. Click Select.
-
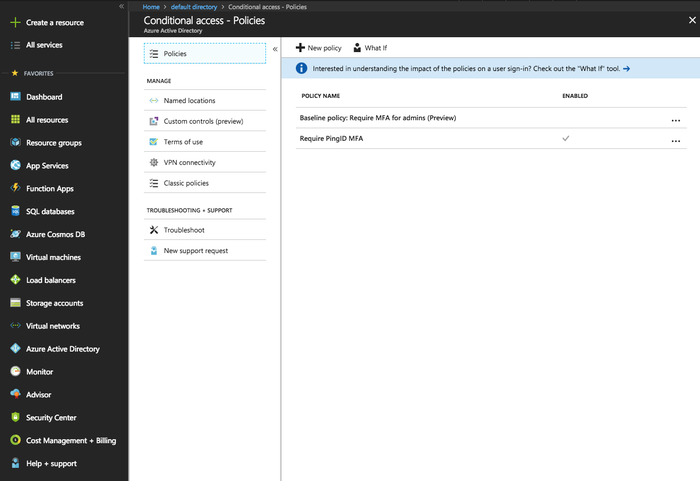
Click Create.
-
Result
The conditional access policy is created and is shown in the Azure Policies list.
Next steps
For information about applying a PingID MFA policy to your Azure AD integration, see Configuring an app or group-specific authentication policy. The Azure AD app will appear in the PingID policy app list.