Configuring Mobile Device Management (MDM)
This section describes the steps to configure PingID’s MDM integration, which verifies that devices connected through the PingID mobile app are managed by the organization’s MDM infrastructure.
MDM is the administration of mobile devices, such as smartphones, tablet computers, and laptops. It can also be applied to desktop computers. Organizations can control activities of their employees by implementing MDM products or services. MDM primarily deals with corporate data segregation, securing emails and corporate documents on mobile devices. MDM enforces corporate policies, and supports the integration and management of mobile devices including laptops and handhelds of various categories.
|
Flow
The basic flow comprises the following stages:
-
In the PingID admin portal, generate a token for MDM or manually enter or edit a token.
-
Configure the third-party MDM system for PingID integration:
-
Generate and configure an APNS certificate for iOS in the MDM system. For examples see:
-
Configure Android for Work in the MDM system so that the PingID app configuration can be pushed to managed phone sets. For examples, see:
-
In the organization’s MDM system, add PingID as a managed app and configure the token that was generated in the PingID admin portal. For examples, see:
-
-
After configuration, the MDM system distributes the token to its managed devices.
-
At pairing and authentication time, the PingID server compares the user’s token with current active tokens. PingID permits administrators to define more than one active token.
-
If there is no match between the user’s token with PingID’s current active tokens, the pairing or authentication flow is halted.
-
If the user’s token matches a current active token on the PingID server, the pairing or authentication flow will progress.
-
Ongoing maintenance
As part of periodic MDM maintenance activities, you can generate new tokens for the PingID app and revoke old tokens. For more information, see the following topics:
-
For PingID:
-
For the supported MDM systems:
Setting up MDM configuration in PingID for the first time
Set up the initial MDM configuration for PingID for the organization’s MDM to operate with PingID multi-factor authentication (MFA).
Steps
-
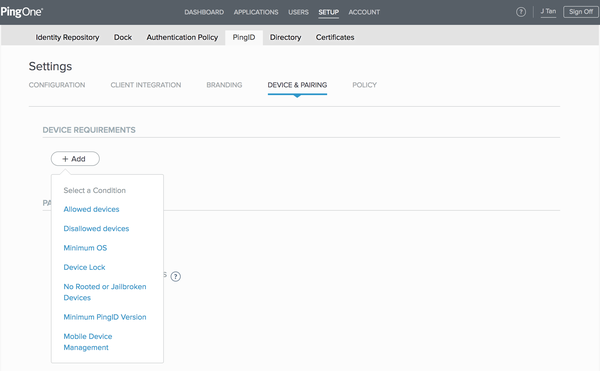
In the admin console, go to Setup → PingID → DEVICE & PAIRING.
-
In the DEVICE REQUIREMENTS section, click +Add.
-
From the Select a Condition list, select Mobile Device Management.
Result:
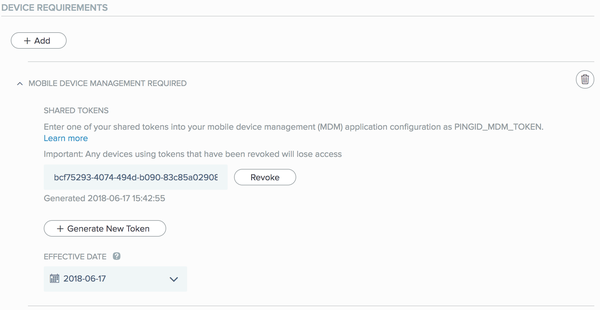
The Mobile Device Management section is displayed.
-
The generated SHARED TOKEN key is in UUID format.
-
The key value is editable. Administrators can use their own key value.
-
-
From the EFFECTIVE DATE list, select a future date.
This will allow time to distribute the token to all managed devices, before the MDM requirement takes effect. If the effective date is not a future date, all users will be blocked until the token is distributed by the MDM system to managed devices.
-
Click Save.
Next steps
Configure the organization’s MDM system. For more information, see Third-party MDM system configuration for PingID integration.
Adding a new MDM token
Add a new MDM token in PingID.
About this task
Multiple keys can coexist, for example, for allowing time for rotating keys and the time it takes to phase in new keys and retire old ones. PingID checks all listed keys to verify a match with the key submitted in the authentication request.
|
The MDM does not retain multiple values for the same token. Support for multiple keys is provided through PingID. |
Steps
-
Go to Setup → PingID → DEVICE & PAIRING.
-
In the DEVICE REQUIREMENTS section, click +Add.

-
From the Select a Condition list, select Mobile Device Management.
-
Click the Expand icon for MOBILE DEVICE MANAGEMENT REQUIRED.
-
Click Generate New Token to create a new PingID key for MDM.
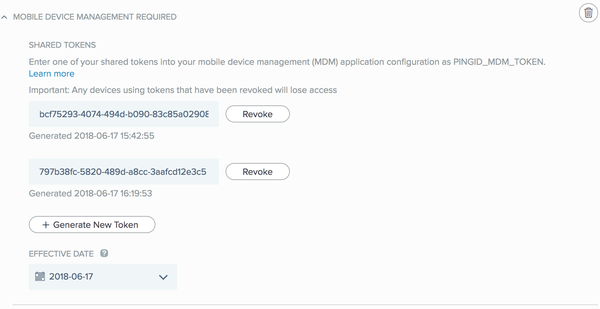
The generated date following each token indicates the date and time of its creation.
-
Click Save.
-
Copy the value of the new SHARED TOKEN key.
-
Update the token key in the MDM system:
-
Sign on to the MDM system, and go to the app configuration settings page.
-
Update the
PINGID_MDM_TOKENtoken key. -
Delete the existing key value. In its place, paste the value of the new SHARED TOKEN key that you copied from the PingID admin portal.
See the following examples for the supported MDM systems:
-
Revoking an MDM token
Organizational security policies might require periodic revocation of retired or obsolete tokens to prevent use of old tokens for authentication.
Steps
-
Go to Setup → PingID → DEVICE & PAIRING.
-
Click the Expand icon for DEVICE REQUIREMENTS.
-
Click the Expand icon for MOBILE DEVICE MANAGEMENT REQUIRED to expand the section.
-
Scroll the list of tokens to identify and locate the old token to be revoked.
The generated date following each token indicates the date and time of its creation.

-
Click Revoke to remove the associated key.
A minimum of one token must be retained. When there is only one token, clicking Revoke will offer the option to replace the existing token with a new generated token.
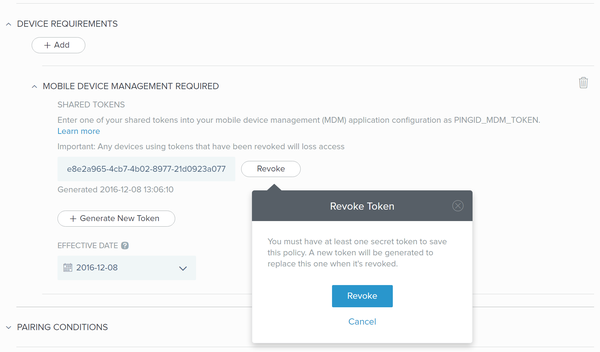
If a new token was generated as the result of revoking the single listed token, all devices will be prevented from authenticating until the new token value is both updated in the MDM, and distributed to all devices. Consider setting the EFFECTIVE DATE to a future date to permit time for distribution of the new token to all devices.
-
Click Save.
Rotating MDM tokens
Organizational security policies might require periodic rotation of MDM tokens to prevent use of old tokens for authentication.
About this task
Rotation is implemented by adding a new token, distributing it to all managed devices, and then removing (revoking) the old token.
|
More than one token should coexist to permit token rotation without blocking users from authentication. |
Steps
-
In the admin console, go to Setup → PingID → Device & Pairing.

Identify and locate the old token to be revoked.
|
The generated date following each token indicates the date and time of its creation. |
