(Legacy) Configuring the FIDO2 security key for PingID
Configure FIDO2 security key for PingID authentication. FIDO2 and U2F-compatible security keys enable relying parties to offer a strong cryptographic authentication option for end user security.
You can use a security key hardware authenticator to cover many use cases, including those of sensitive environments or users working in environment with limited device or phone access, such as hospitals, financial institutions, or federal buildings.
FIDO2 security keys are fully backward compatible with U2F, enabling PingID to support both FIDO2 and U2F security keys.
When security key authentication is enabled, the user registers the security key and pairs it with their PingID account. This creates a trust between the security key and the user’s account, so they can use the security key to authenticate during the sign-on process.
|
Use security keys for web-based authentication through WebAuthn supporting browsers only. |
Passwordless security key
You can configure a PingFederate policy to allow users to authenticate with their security key as a first factor authentication, eliminating the need to enter a users name or password, and providing a frictionless and secure sign on experience.
To configure passwordless authentication using a security key:
-
(Legacy) Configuring security key authentication with Resident Key set to Required.
-
Configure a PingFederate policy for passwordless authentication with a security key (see (Legacy) Configuring a PingFederate policy for passwordless authentication with a security key).
For information about security key requirements and limitations, see (Legacy) Security key authentication requirements and limitations.The process of registering a security key is the same for both passwordless and secondary authentication flows. The user is directed to the relevant flow, according to your organization’s configuration. Once registered, the same security key can be used to authenticate via either flow (see Setting up your security key in the PingID User Guide).
Manual authentication with a FIDO2 security key
PingID integration with Windows login supports the use of FIDO2 security keys for manual authentication, such as if a user does not have an internet or network connection when signing on.
-
FIDO2 security key for manual authentication is supported by PingID Integration for Windows login 2.3 or later.
-
U2F security key for manual authentication is only supported by PingID Integration for Windows login 2.3 - 2.7.x.
Users must pair a security key and authenticate successfully at least once online, to use it when offline. For more information, see the PingID End User Guide.
(Legacy) Security key authentication requirements and limitations
When using security keys with PingID, the following requirements and limitations apply:
|
For PingID environments that are integrated with PingOne: From April 15th 2024, the FIDO2 Biometrics and Security Key authentication methods are deprecated and replaced by the more advanced FIDO2 authentication method. Learn more: Updating a PingID account to use PingOne FIDO2 policy for Passkey support. |
-
Security keys are supported for Web authentication only.
-
PingID supports FIDO2 and U2F security keys.
U2F security keys can only generate a single credential per domain. A device can only be paired by one user per domain.
-
Security keys can be used for web-based authentication through WebAuthn supporting browsers only.
If a browser supports the use of a security key, the browser also supports WebAuthn.
-
When authenticating with a mobile device, use of FIDO2 and U2F security keys with PingID:
-
Is supported on Android 7 and later
-
Is supported on iOS 13.3 and later
-
-
Registration and authentication must be performed with a WebAuthn supported browser, such as the latest versions of Google Chrome or Microsoft Edge.
-
The use of FIDO2 security keys for manual (offline) authentication:
-
Requires PingID Integration for Windows login 2.3 or later.
-
-
WebAuthn timeout is defined for 2 minutes. The actual timeout value might vary depending on the browser used.
-
PingID does not support security keys that require a signed attestation using ECDAA in packed attestation format.
-
A user can pair more than one security key with their account.
-
The same security key can be used by more than one user if each user is pairing the security key to a different account.
-
A user cannot pair the same security key with their account more than once.
-
YubiKeys can be paired for either:
-
Security Key FIDO2 authentication
-
YubiKey OTP authentication
PingID YubiKeys that feature one-time passcode (OTP) support only, or for which you only want to use OTP authentication, should be paired as a YubiKey authentication method rather than as a security key. For more information, see Configuring YubiKey authentication (Yubico OTP) for PingID.
-
-
The following limitations should be considered when configuring security key authentication with PingID:
-
Some browsers do not support the use of a FIDO2 security key when User Verificationis set to Required.
-
Some browsers do not allow authentication with a security key when the security key is paired as a resident key.
-
Some browsers do not support security key registration whenResident Key is set to Required.
-
-
Windows login supports the use of FIDO2 security keys.
If user verification has been set to Required for security keys in the admin portal, this will not affect offline authentication, and users will be able to use their security key for offline authentication without user verification.
Passwordless security key
To use a security key for passwordless authentication:
-
The security key must support the use of a resident key, and be paired as a resident key.
-
When creating a PingFederate policy for passwordless authentication with a security key you must use PingID Integration kit 2.10 or later, with PingFederate v9.3 or later.
Some browsers do not support the security key passwordless authentication flow. Passwordless authentication with a security key has been successfully tested on:
-
Windows 10 machines running the latest version of Windows Edge, FireFox, Opera, and Chrome.
-
Apple Mac 10.15 (Catalina) machines running the latest versions of Windows Edge, Opera, and Chrome.
-
Testing has also been performed successfully on Apple Mac 11 (Big Sur), and Mac 12.4 (Monterey).
(Legacy) Configuring security key authentication
Use the FIDO2 security key for web-based authentication only. The browser with which the user is accessing their resources must support WebAuthn, such as the latest version of Google Chrome or Mozilla Firefox.
About this task
|
Define the use of security keys for offline authentication when installing the PingID Integration for Windows Login. |
|
If the browser does not support WebAuthn, the user will be unable to authenticate with the security key and might be unable to authenticate if that is their only authenticating device. |
Steps
-
Sign on to the admin console.
-
Go to Setup → PingID → Configuration.
-
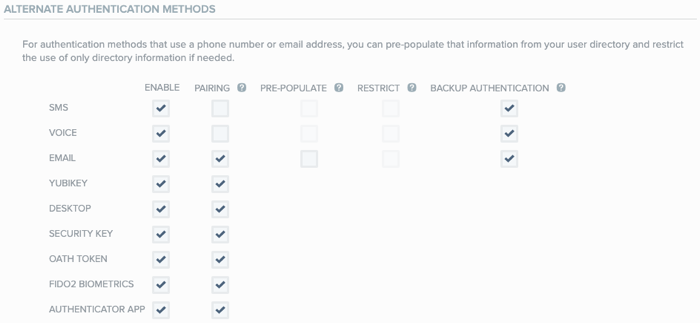
Go to the Alternate Authentication Methods section, and in the Security Key row, select the Enable check box.
Result:
The ability to pair and authenticate with a security key is enabled for all users in that organization, and additional security key configuration fields are shown.
-
In the Enable column, select the Security Key check box.
-
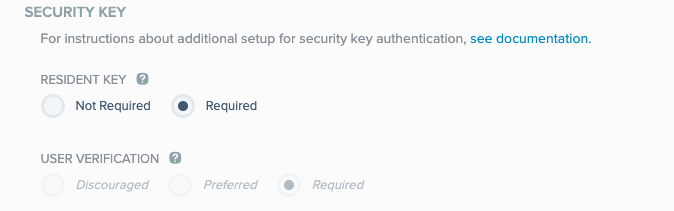
Optional: In the Security Key section, configure the following fields:
-
Resident Key. When set to Required, the private key is saved on the security key. To enforce passwordless authentication on all authentication attempts, set this field to Required.
-
User Verification. This option requires the user to perform a gesture using their security key, to validate their identity (for example, using their fingerprint, or entering a PIN code). Select either:
Choose from:
-
Required: only security keys that support user verification can be used to authenticate. When the Resident Key field is set to Required, this option is automatically set to Required.
-
Preferred (default): user verification is performed if the user’s security key supports it, and is skipped if not supported.
-
Discouraged: user verification is not performed, even when supported by the user’s security key. In cases where user verification is required by the security key itself, this setting does not override the device setting.
When user verification is changed from preferred to required, it will automatically unpair all security keys that have not undergone user verification during registration or authentication in the past. To identify security keys that have not been registered as security keys that support user verification, see the
fidoUserVerificationfield in the PingID User Detailed Status Report fields.To enable passwordless authentication with a security key, you also need to create a PingFederate policy for passwordless authentication with a security key.
-
-
To enforce the PingOne FIDO policy during authentication and registration, select theEnforce PingOne FIDO Policy check box.
-
This feature is only available for organizations that are using a PingID environment that is integrated with PingOne or created by PingOne.
-
Only the default PingOne FIDO policy is enforced. To edit the policy or change the default policy, see Managing FIDO policies.
-
-
Click Save.
Result
Users can pair and authenticate with their security keys.
(Legacy) Security key use cases
The following table outlines common use cases and their expected behaviors when using security key authentication.
|
The results can vary from those described in the table if policy rules are applied. For more information, see PingID authentication policy. |
| Paired devices | Browser | Results | Reason |
|---|---|---|---|
Security key only |
WebAuthn compliant |
The user is prompted to authenticate using their security key. |
Security key is the only allowed authentication method and the browser supports WebAuthn, so the user can authenticate using their security key. |
|
WebAuthn compliant |
The user is prompted to authenticate using their security key. If Prompt to Select is enabled, security key appears in the list of authentication options. |
The browser supports security key, which is the user’s primary device. |
Security key only |
WebAuthn compliant |
|
The user did not tap the security key within the required time, or the relevant browser window was not selected when they tapped the security key button. The user should click Retry and authenticate again. |
Security key only |
Not WebAuthn compliant |
|
The browser does not support the user’s current authentication method. The user should try a different browser that is WebAuthn compliant, such as the latest version of Chrome. |
|
Not WebAuthn compliant |
The user is prompted to authenticate using the next paired device, in this case email or SMS. If Prompt to Select is enabled, security key does not appear in the list of authentication options. |
The browser is not WebAuthn compliant and does not support the use of a security key. Secondary authentication method is presented to the user. |