Overview of Cisco ASA for PingID MFA
This topic details the configuration required in your Cisco ASA VPN for integrating PingID multi-factor authentication (MFA).
How Multi-Factor VPN Authentication Works
The following image represents a general flow. Actual configuration varies according to company infrastructure considerations and policies.
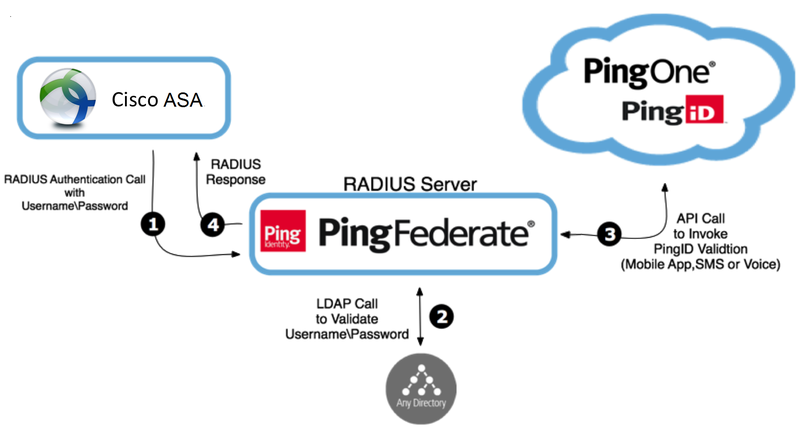
Processing steps
-
When a user opens either their IPSec or SSL VPN sign-on window and enters a username and password, their details are sent to the RADIUS Server on PingFederate through the VPN.
-
PingFederate authenticates the user’s credentials against the LDAP Server as first-factor authentication.
-
After LDAP authentication approval, the RADIUS server initiates second-factor authentication with PingID. If authentication is denied, the user’s VPN window displays an error message.