Configuring a RADIUS PCV and SSH access policy
Configure a policy for a user to access a protected application through a RADIUS PCV or SSH.
About this task
Edit the default policy and add one or more rules to the policy.
|
To apply PingID policy features that require IP address information, the client IP address must be provided. For more information, see Prerequisites: Pingfederate RADIUS server. |
Steps
-
In the admin portal, go to Setup → PingID → Policy, and click the RADIUS PCV and SSH tab.
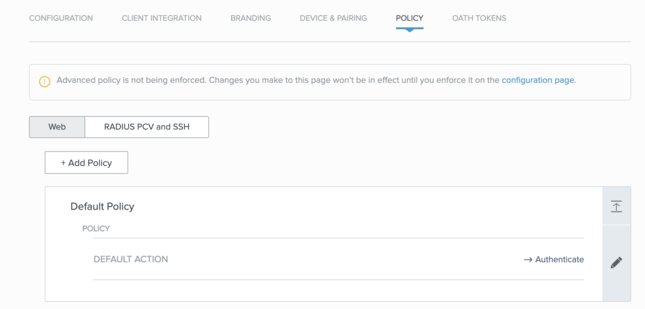
-
In the Allowed Methods section, select the authentication methods to allow for this policy.
Only the methods selected become available in the rule authentication Actions list.
You must select at least one authentication method. To include all authentication methods, including Deprecated authentication actions, select the All Methods check box. For a detailed description of available authentication methods at the policy and rule level, see Policy and rule authentication methods.
-
In the Rules section, from the list, select and configure one or more policy rules.
Choose from:
-
Configuring an accessing from company network rule (RADIUS PCV and SSH)
-
Configuring an accessing from countries rule (RADIUS PCV and SSH)
Result:
The chosen rule configuration section expands.
-
-
Complete the rule section configuration.
From the Action list, the default action selected determines which authentication action is performed if no other policy rule applies.
-
Click Save.
Configuring an accessing from company network rule (RADIUS PCV and SSH)
Determine which authentication action to prompt the user with when accessing the RADIUS PCV or SSH, if the users device is within the company network.
About this task
You can require a user’s authenticating device to be in the company offices when signing on from within the company network. In addition, you can choose to silently authenticate the user without requiring active user intervention in the authentication process for in-network access.
|
To apply the PingID policy features that require IP address information, the client’s IP address must be provided first. Find more information in Prerequisites: PingFederate RADIUS server. |
|
To ensure location-based policies are applied, you must also ensure location collection is enabled at the organization level (see Enabling or disabling location collection). |
Steps
-
From within the relevant policy, click Add Rule and from the Conditions list, select Accessing from company network.
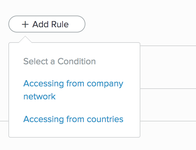
-
From the Action list:
Choose from:
-
Approve: Approves access without requiring PingID authentication.
-
Authenticate: Allows a user to authenticate using any of the authentication methods allowed at the policy level.
If more than one authentication method is available, the method initiated by default is the method most recently paired by the user that is authenticating.
-
Select a specific authentication method. The options listed are defined by those configured at policy level. For a description of each authentication type, see Rule authentication actions.
-
-
In the IP Addresses field, enter a list of external IP addresses or ranges that belong to the company network.
Enter the IP addresses or ranges using CIDR notation with each entry on its own line.
-
To require a user’s authenticating device to be in the company offices when signing on from within the company network, in the Authenticating Device In Company Offices field, click Enable and then define one or more company office locations.
If you are defining a company office in addition to an IP address, in the Allowed Authentication Method section, select the Swipe, Mobile App Biometrics, or One-time passcode check box to define an authentication method to apply this rule.
Result:
The Office Locations wizard opens, enabling you to define one or more office locations. If the authenticating device is located within one of the defined areas, it is considered to be inside a company office.
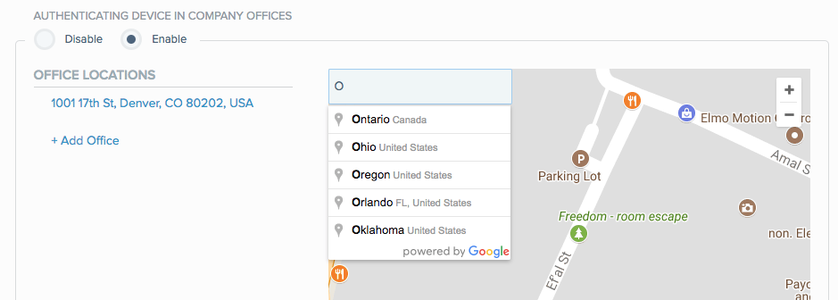
-
To define additional office locations:
-
Click Add office or enter an address in the search box.
Result:
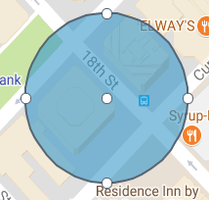
A blue circle appears on the map, defining the office area.
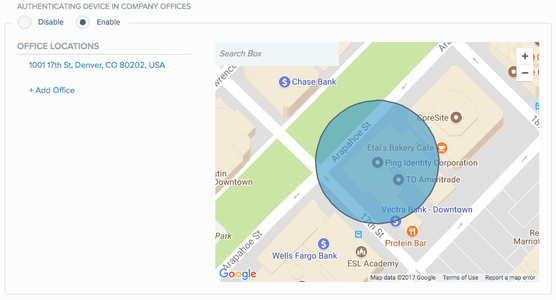
-
Click center of the circle to edit the coordinates.
-
To reposition the circle, click and drag the white dot at the circle’s center to the desired location.
-
To resize the circle, click and drag any white dot on the circle’s rim.
-
To add another office location, click a location outside the circle. A new circle is added.
-
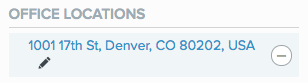
To edit an office location, click the Pencil icon (
 ) and edit the name.
) and edit the name.By default, the location is named after its street address.
-
To delete an office address, click the Minus icon (
 ).
).If you edit or delete offices in the Office Locations list, changes are applied to all rules that specify office locations.
-
-
-
In the Policy list, click and drag the new rule and place it in the order in which you want it to be considered. Click Save Order.
-
Click Save.
Next steps
To ensure the policy is applied to your organization, go to PingID → Configuration and ensure Enforce Policy is set to Enabled.
Configuring an accessing from countries rule (RADIUS PCV and SSH)
According to the country, determine which authentication action to prompt the user with on the machine that uses RADIUS PCV or SSH for access.
About this task
|
The country location is determined by the IP address of the accessing device and not by the IP address of the authentication device. |
Steps
-
From within the relevant policy, click Add Rule and from the Conditions list, select Accessing from countries.

-
From the Action list:
Choose from:
-
Authenticate: Allows a user to authenticate using any of the authentication methods allowed at the policy level.
If more than one authentication method is available, the method initiated by default is the method most recently paired by the user that is authenticating.
-
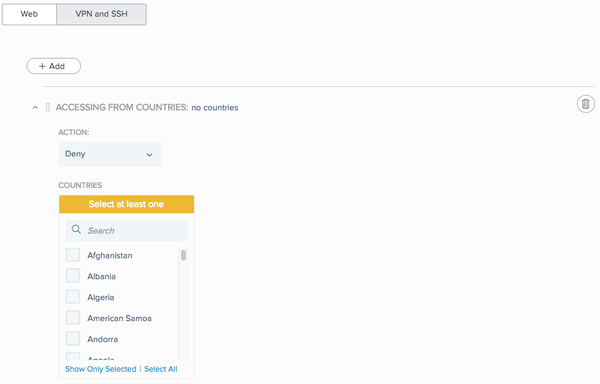
Deny: Denies access.
-
Select a specific authentication method. The options listed are defined by those configured at policy level. For a description of each authentication type, see Rule authentication actions.
-
-
From the Countries list, select the check box of each country to which you want the policy to apply.
Option Description Search bar
Use to search for a specific country, enter the country name or part of the name. Only countries whose name contains that string are displayed.
Show Only Selected
Use to show only the countries you have selected.
Select All
Use to select all countries.
-
If you have more than one rule listed, from the Rules list, click and drag the new rule and place it in the order you want it to be considered. Click Save Order.
-
Click Save.
Next steps
To ensure the policy is applied to your organization, go to PingID → Configuration and ensure Enforce Policy is set to Enabled.