Enabling PingID as an MFA provider in AD FS
The process of enabling PingID as a multi-factor authentication (MFA) provider in Microsoft Active Directory Federation Services (AD FS) varies slightly between AD FS 4.0 and 3.0. The process for each is described in the following sections.
Enabling PingID as an MFA provider in AD FS 4.0
After installing the PingID MFA Adapter, enable it as the MFA provider for AD FS 4.0.
Steps
-
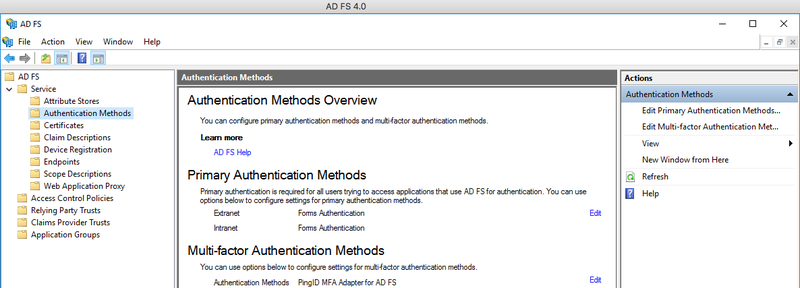
In Windows, open Server Manager and go to Tools → AD FS Management → AD FS → Service → Authentication Methods.
-
From the Actions menu, select Authentication Methods, and then click Edit Multi-factor Authentication Methods.
Result:
The Edit Authentication Policy window opens.
-
In the Multi-factortab, select PingID MFA Adapter for AD FS, then click OK.
Result
PingID MFA is applied to the AD FS login process, according to the policy and general configurations of AD FS.
Enabling PingID as an MFA provider in AD FS 3.0
After installing the PingID MFA Adapter, enable it as the MFA provider for AD FS 3.0.
About this task
Steps
-
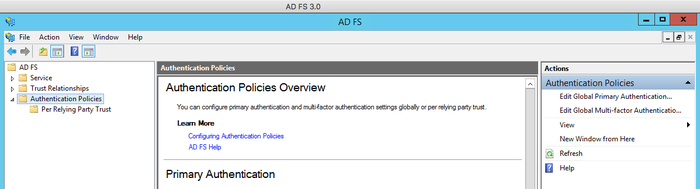
In Windows, open Server Manager and go to Tools → AD FS Management → AD FS → Authentication Policies.
-
From the Actions menu, select Authentication Policies, and then click Edit Global Multi-factor Authentication Methods.
-
On the Multi-factor tab, select PingID MFA Adapter for AD FS, and then click Apply.
Result
PingID MFA is applied to the AD FS login process, according to the policy and general configurations of AD FS.
Configuring advanced settings
Configure optional advanced settings for PingID MFA Adapter for AD FS.
About this task
Steps
-
In the Microsoft Management Console, go to File → Add/Remove Snap-in.
-
If the PingID MFA Adapter for AD FS folder is not shown under the Console Root folder, in the Available snap-ins section, select PingID MFA Adapter for AD FS and click Add and then click OK.
-
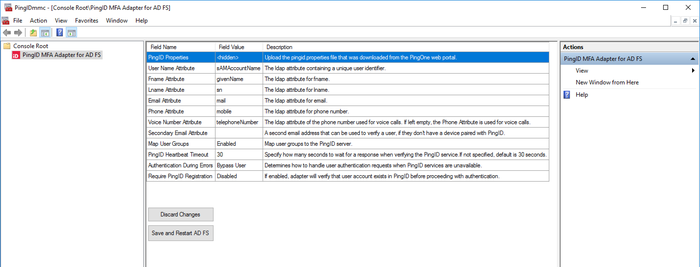
To display a list of advanced parameters, in the Console Root folder, click PingID MFA Adapter for AD FS.
-
Double-click the attributes you want to change and enter the relevant value.
Attribute Description PingID PropertiesGo to the
pingid.propertiesfile, and click Open. If you have not yet configured the PingID service, see Configure the PingID service for instructions.User Name AttributeThe name of the user name attribute that will be mapped to the PingID user name value , such as
sAMAccountName. The value of this attribute must be unique for each user identity.Fname AttributeThe LDAP attribute containing the user first name.
Lname AttributeThe LDAP attribute containing the user last name.
Email AttributeThe LDAP attribute containing the user email address. This email address is used during registration if users need to receive a link on their mobile device to download the PingID application.
Phone AttributeThe LDAP attribute of the phone number used for SMS messages, as well as voice calls if the Voice Number attribute is left empty.
This attribute must use the Google Library format, which dictates that all phone numbers must include ‘+’, as well as the international country code.
Voice Number AttributeThe LDAP attribute of the phone number used for voice calls. If left empty, the Phone Attribute is used for voice calls.
This attribute must use the Google Library format, which dictates that all phone numbers must include ‘+’, as well as the international country code.
Secondary Email AttributeA second email address that can be used to verify a user if they don’t have a device paired with PingID.
Map User Groups AttributeDetermine whether to map user groups to enable the PingID server to evaluate group-based policy during authentication. Select either:
-
Enable: User group information is sent to the PingID server. PingID group-based polices are evaluated during authentication.
-
Disable: User group information is not to the PingID server. PingID group-based polices are not evaluated during authentication.
For information on configuring a group-based policy, see PingID policy settings.
The LDAP attribute for group membership (e.g.
memberOf).PingID Heartbeat TimeoutTime to wait for a response when verifying the PingID and PingOne services. If a value is not specified, the default is 30 seconds.
Authentication During ErrorsDetermines how to handle user authentication requests when PingID services are unavailable. Allowed values are:
-
Bypass User: Accept the user’s first factor authentication, and bypass the PingID MFA flow when the PingID MFA service is unavailable.
-
Block User: Reject and block the user’s login attempt when the PingID MFA service is unavailable.
Require PingID RegistrationIf enabled, requires that users are registered with PingID and verify their registration prior to authentication.
Proxy URLIf you want PingID to use a specific proxy, provide the URL here. The proxy URL format must be
http://<server name or IP>:<port>. Https is not supported.Alternate DomainIf the users belong to a domain that is not reflected in the login information provided, you can use this field to specify the relevant domain.
-
-
After you have configured all relevant attributes, click Save and Restart AD FS.
Modifying advanced settings requires you to restart the AD FS service. This might affect users that are using this instance of AD FS.
Result
Windows applies the configuration changes after restarting the AD FS service.
Next steps
To apply a PingID authentication policy to your AD FS integration, see Configuring an app or group-specific authentication policy). The AD FS app should appear in the PingID Policy app list.