Configuring a limit push notifications rule
Use this rule to reduce the likelihood of a user acknowledging a malicious push notification as part of an MFA fatigue attack by limiting the number of push notifications the user can deny or ignore within a 24-hour period.
About this task
Specify an action from the list of allowed methods that are available, or choose to deny the user access. Then specify the time period for which the rule actions should be applied.
You can define an array of up to three push notification limits (subrules), and specify up to three actions that are triggered sequentially as the user reaches each limit. A rule defines the number of push notifications (ignored or denied) that must occur consecutively within a 24-hour period in order to trigger the rule action.
Each time the user authenticates successfully, the counter is reset.
For example, when applying the rule for 20 minutes:
-
After 5 push notifications, the user must authenticate with a security key for a period of 20 mins.
-
After 10 push notifications, the user must authenticate using biometrics, or number matching for a period of 20 mins.
-
After 15 push notifications, the user is denied access for a period of 20 mins.
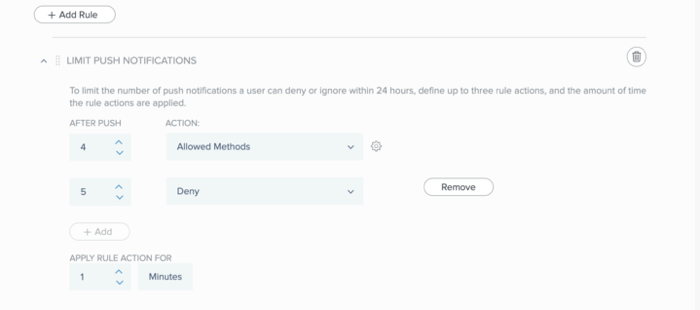
|
Steps
-
From within the relevant policy, click Add Rule and from the list, select Limit push notifications.
Result:
The Limit Push Notifications rule wizard open
-
To define a push notification limit:
-
In the After Push field, select the number of push notifications after which the action is triggered, and then in the Action field, select the action that is triggered when the limit is reached. Choose from the following actions:
-
Deny: Deny access after the number of push notifications is reached.
-
Allowed Methods: Click Allowed Methods to reveal a list of authentication methods allowed by this policy, and then select the check box of each authentication method that you want to allow for this rule. See Rule authentication actions for description per authentication type.
-
-
To add another push notification limit, click Add and repeat substep a.
-
-
In the Apply Rule Action For field, set a duration for the rule actions to be applied after they’re triggered.
-
Click Save.
-
In the Policy list, click and drag the new policy and place it in the order in which you want it to be considered. Click Save Order.
Next steps
To ensure the policy is applied to your organization, go to PingID → Configuration and ensure Enforce Policy is set to Enabled.