Configuring an IP reputation rule (web policy)
Use this rule to determine which authentication action to prompt the user with, based on the risk score of the IP address of the user’s accessing device.
About this task
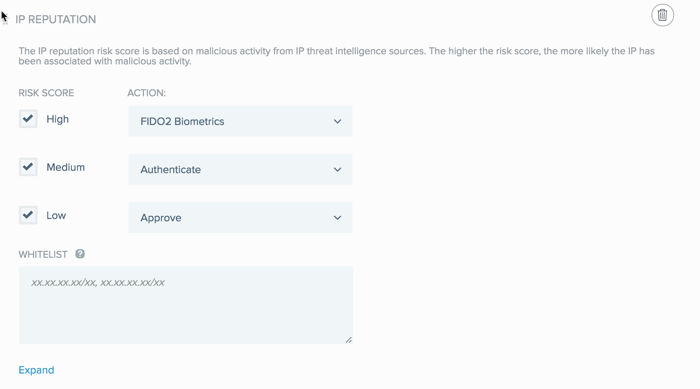
PingID collects and analyzes IP address data from the user’s accessing device and enables you to apply different authentication actions to IP addresses according to their risk scores. IP addresses are grouped into the following levels of risk:
-
High: The IP address is considered high risk and might have recently been involved in numerous malicious activities, such as DDos attacks or spam activity.
-
Medium: The IP address is considered medium risk and might have been involved in malicious activities, such as DDos attacks or spam activity.
-
Low: The IP address is considered low risk.
You can define a different authentication for each risk group. Define more restrictive authentication for IP addresses in a higher risk group You can also define a whitelist of IP addresses that you want this rule to ignore.
|
The IP reputation rule is not applied if there is insufficient data to determine the IP address' risk score. |
Steps
-
From within the relevant policy, click Add Rule and from the list, select IP Reputation.
Result:
The IP Reputation rule wizard opens.
-
Select the check box of each Risk Score group to which you want to apply a rule action, and from the Action list, select the action that you want to apply to that risk score group.
Choose from:
-
Deny: Deny access for authentication requests originating from IP addresses in the selected risk score category. This option is selected for the High risk category, by default.
-
Approve: Approve access without requiring PingID authentication for authentication requests originating from IP addresses in the selected risk score category.
-
Authenticate: Allow the user to authenticate using any of the authentication methods allowed at the policy level.
-
Allowed Methods: Click Allowed Methods to reveal a list of authentication methods allowed by this policy, and then select the check box of each authentication method that you want to allow for this rule. See Rule authentication actions for description per authentication type.
-
-
In the Whitelist field, specify one or more IP address ranges that you want the rule to ignore.
Enter each IP address range in the format
XX.XX.XX.XX/XXand separate each IP address range with a comma. -
Click Save.
-
In the Policy list, click and drag the new policy and place it in the order in which you want it to be considered. Click Save Order.
Next steps
To ensure the policy is applied to your organization, go to PingID → Configuration and ensure Enforce Policy is set to Enabled.