Creating an authentication profile
To configure Palo Alto Global Protect to work with PingID multi-factor authentication (MFA), you must create an authentication profile.
Steps
-
Go to Device → Authentication Profile, and then click Add.
Result:
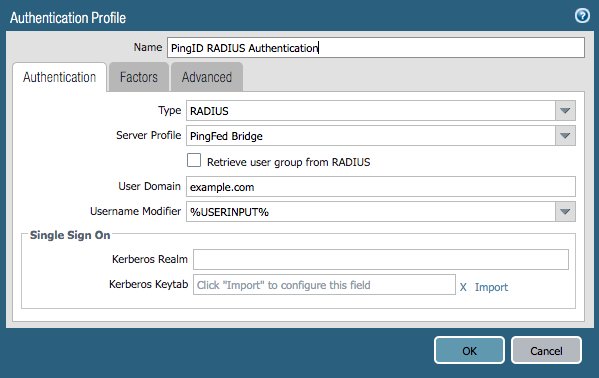
The Authentication tab of the Authentication Profile window is displayed.
-
In the Name field, enter a name for the profile.
-
From the Type list, select RADIUS.
-
From the Server Profile list, select the RADIUS profile that you previously created.
-
In the User Domain field, enter your own domain name.
-
From the Username Modifier list, leave the default selection of %USERINPUT%.
-
Click Advanced.
Result:
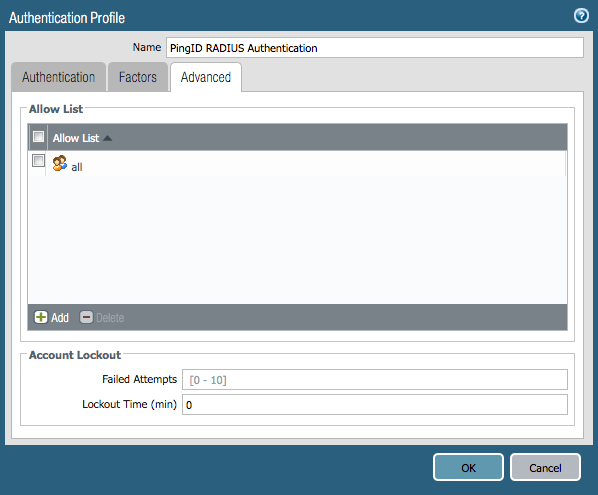
The Advanced tab of the Authentication Profile window is displayed.
-
In the Allow List section, select the group to which this authentication profile will apply. Click OK.