(Legacy) Configuring security key authentication
Use the FIDO2 security key for web-based authentication only. The browser with which the user is accessing their resources must support WebAuthn, such as the latest version of Google Chrome or Mozilla Firefox.
About this task
|
Define the use of security keys for offline authentication when installing the PingID Integration for Windows Login. |
|
If the browser does not support WebAuthn, the user will be unable to authenticate with the security key and might be unable to authenticate if that is their only authenticating device. |
Steps
-
Sign on to the admin console.
-
Go to Setup → PingID → Configuration.
-
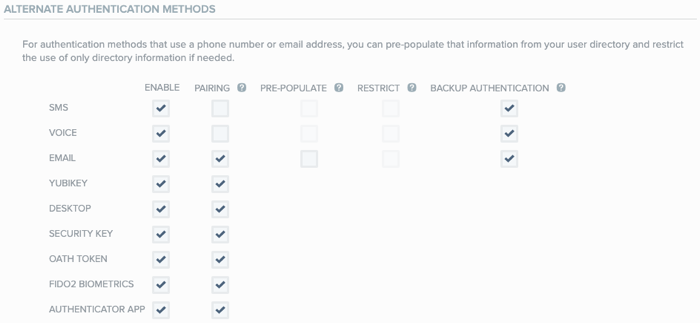
Go to the Alternate Authentication Methods section, and in the Security Key row, select the Enable check box.
Result:
The ability to pair and authenticate with a security key is enabled for all users in that organization, and additional security key configuration fields are shown.
-
In the Enable column, select the Security Key check box.
-
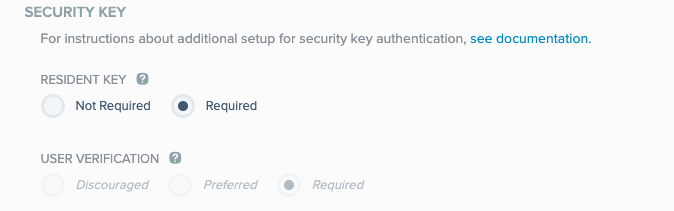
Optional: In the Security Key section, configure the following fields:
-
Resident Key. When set to Required, the private key is saved on the security key. To enforce passwordless authentication on all authentication attempts, set this field to Required.
-
User Verification. This option requires the user to perform a gesture using their security key, to validate their identity (for example, using their fingerprint, or entering a PIN code). Select either:
Choose from:
-
Required: only security keys that support user verification can be used to authenticate. When the Resident Key field is set to Required, this option is automatically set to Required.
-
Preferred (default): user verification is performed if the user’s security key supports it, and is skipped if not supported.
-
Discouraged: user verification is not performed, even when supported by the user’s security key. In cases where user verification is required by the security key itself, this setting does not override the device setting.
When user verification is changed from preferred to required, it will automatically unpair all security keys that have not undergone user verification during registration or authentication in the past. To identify security keys that have not been registered as security keys that support user verification, see the
fidoUserVerificationfield in the PingID User Detailed Status Report fields.To enable passwordless authentication with a security key, you also need to create a PingFederate policy for passwordless authentication with a security key.
-
-
To enforce the PingOne FIDO policy during authentication and registration, select theEnforce PingOne FIDO Policy check box.
-
This feature is only available for organizations that are using a PingID environment that is integrated with PingOne or created by PingOne.
-
Only the default PingOne FIDO policy is enforced. To edit the policy or change the default policy, see Managing FIDO policies.
-
-
Click Save.
Result
Users can pair and authenticate with their security keys.