Updating an existing MFA policy to use FIDO2
If your MFA policy includes FIDO biometrics or security key authentication methods, you’ll be asked to update your FIDO policy to the enhanced FIDO2 policy.
Before you begin
Note the following:
-
FIDO2 authentication is supported in PingOne MFA and PingOne DaVinci.
-
In a future version, PingFederate Integration Kit for PingOne MFA will also support the FIDO2 authentication method. Until support is added, if you are using the PingFederate Integration Kit, do not update your MFA policy to use the FIDO2 authentication method.
-
When updating your MFA policies to support the FIDO2 authentication method, you must also update:
-
All scripts that include the deprecated FIDO Biometrics and Security Key authentication methods.
-
All PingOne DaVinci flows that include the PingOne MFA Connector, and use the deprecated FIDO Biometrics and Security Key authentication methods.
-
|
If you have integrated an existing PingID account with your PingOne environment, after updating FIDO devices to use the FIDO2 authentication method it is not possible to unlink the PingID account. Deleting the PingOne environment will also delete the PingID account. |
About this task
As of June 20, 2023, FIDO biometrics and Security Key authentication methods are being phased out.
The FIDO2 authentication method replaces the deprecated FIDO biometrics and security key authentication methods and offers an expanded range of configurations and support for a wide range of FIDO authentication devices, including cloud-synced FIDO devices.
If your MFA policy references a FIDO policy with the deprecated authentication methods, you’ll see a notice in the MFA page asking you to update the policy.
If you see this notice, follow these instructions to update your policy.
|
Steps
-
Go to Authentication > MFA.
If you are required to update your policy, first ensure that your FIDO2 policy is defined correctly for your organization. For information about configuring a FIDO2 policy, see Adding a FIDO policy.
-
At the top of the MFA Policies page, click Update.
Result:
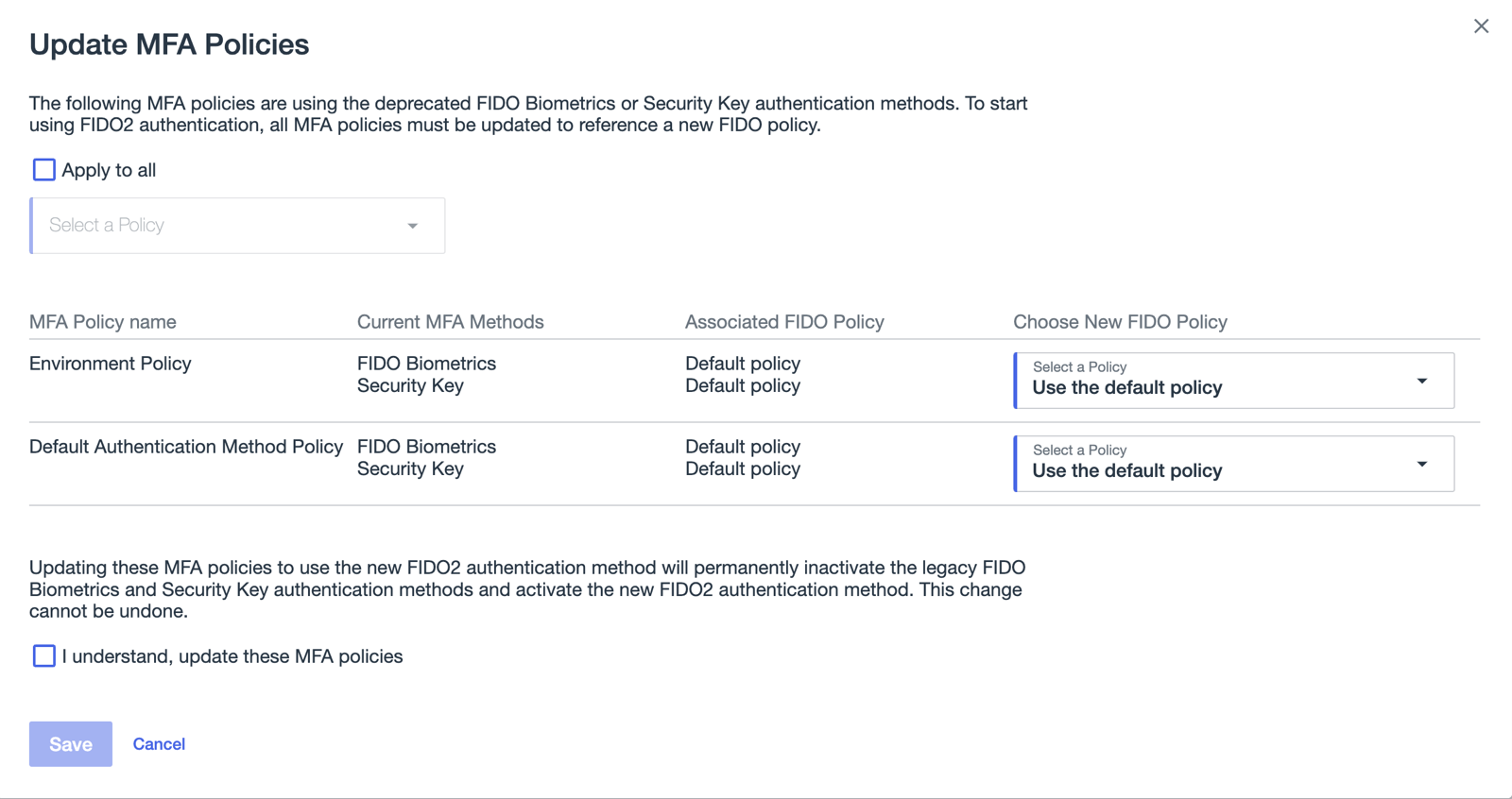
The Update MFA Policies window opens, listing all of the MFA policies that currently include a deprecated FIDO policy.
-
Update the affected MFA policies.
Choose from:
-
To update all affected MFA policies with the same enhanced FIDO policy, select the Apply to all check box, and then select the relevant enhanced FIDO policy from the list. The selected FIDO policy is applied to all MFA policies listed.
-
To update each MFA policy individually, for each MFA policy listed in the table, in the relevant row, select the enhanced FIDO policy from the Choose New FIDO Policy list.
To specify the default FIDO policy, select Use the default policy.
-
-
To complete the upgrade, clickI understand and then click Save.
Result:
The FIDO2 biometrics and security key authentication methods are deactivated for the MFA policies listed, and FIDO2 authentication is activated.
Next steps
After updating your MFA policies, all scripts that rely on the deprecated FIDO Biometrics and Security Key methods, and all PingOne DaVinci flows that include the PingOne MFA Connector using one of these methods, should also be updated.