Creating a SCIM connection
You can set up provisioning to or from a System for Cross-domain Identity Management (SCIM) identity store. You can also use the PingOne API to set up inbound SCIM for user provisioning. Learn more in SCIM in the PingOne API documentation.
Steps
-
In the PingOne admin console, go to Integrations > Provisioning.
-
Click and then click New Connection.
-
On the Identity Store line, click Select.
-
On the SCIM Outbound tile, click Select. Click Next.
-
Enter a name and description for this provisioning connection.
Result:
The connection name appears in the provisioning list after you save the connection.
-
Click Next.
-
In the Configure Authentication section, enter the values for the following fields:
Field Value SCIM Base URL
The fully qualified URL to use for the SCIM resources, such as
https://scim-example.com/v2/.Users Resource
The endpoint for the SCIM
Userresource.SCIM Version
The SCIM version to use for the connection.
Groups Resource
The endpoint for the SCIM
GroupsAuthentication Method
The SCIM authentication method to use for the connection.
You can choose to use no authentication (None). For all other methods, additional entry fields are displayed, depending on the selected authentication method.
If possible, you should use the OAuth 2 Bearer Token or OAuth 2 Client Credentials authentication methods.
Basic Authentication provides limited security:
-
The identity store configuration has the provided Basic Auth credentials.
-
The authentication scope is exactly that of the Basic Auth user, rather than a subset of the user data.
-
Basic Authentication
-
Basic Auth User: Enter the Basic Auth user for the identity store.
-
Basic Auth Password: Enter the Basic Auth user password for the identity store.
-
Auth Type Header: Select Basic, Bearer, OAuth Client Credentials, or Custom (to supply your own header configuration).
-
-
OAuth 2 Bearer Token
-
OAuth Access Token: Enter the OAuth access token value supplied by the authorization server for the identity store.
-
Auth Type Header: Select Basic, Bearer, OAuth Client Credentials, or Custom (to supply your own header configuration).
-
-
OAuth 2 Client Credentials
-
OAuth Token Request: Enter the endpoint URL used to obtain an access token, such as
https://scim-example.com/as/token.oauth2. -
OAuth Client ID: Enter the client ID registered with the OAuth server for the provisioning identity store.
-
OAuth Client Secret: Enter the client secret value associated with the OAuth client ID.
-
Auth Type Header: Select Basic, Bearer, OAuth Client Credentials, or Custom (to supply your own header configuration).
-
If you select Custom, the Custom Header entry field displays. Enter the custom header configuration.
Custom headers added here will be added only as authorization headers in the request.
-
-
Click Test connection to verify that PingOne can establish a connection to the SCIM resource.
Result:
If there are any issues with the connection, a Test Connection Failed modal opens. Click Continue to resume the setup with an invalid connection.
You can’t use the connection for provisioning until you’ve established a valid connection to SCIM. To retry, click Cancel in the Test Connection Failed modal and repeat step 7.
Troubleshooting:
Learn more about troubleshooting your connection in Troubleshooting Test Connections Failure.
-
In the Configure Preferences and Actions sections, enter the following:
Field Description User filter expression
Determines how the connection uses the specified User Identifier to match existing users in the target identity store to the users being provisioned from the source identity store. Learn more in SCIM filter expressions.
User Identifier
The identifier for the user filter expression.
Custom Attribute Schema URNs (optional)
A comma-delimited list of schema URNs to define a location for custom attributes. Use this option if the SCIM provider does not follow the standard naming convention for schema extensions in which custom attributes are defined. That is, URNs of the form
urn:ietf:params:scim:schemas:extension:<Organization Name>:2.0:User.Group Membership Handling
Determines whether to update or replace target groups with PingOne memberships. Select Merge or Overwrite.
Merging or overwriting memberships only applies to SCIM, Slack, and GitHub EMU provisioning connections.
There is a limitation when syncing groups and group memberships to AWS Identity Centre and Atlassian Cloud. Learn more in SCIM provisioning known limitations.
Allow Users to be Created
Determines whether to create a user in the target identity store when the user is created in the source identity store.
Allow Users to be Updated
Determines whether to update user attributes in the target identity store when the user is updated in the source identity store.
Allow Users to be Disabled
Determines whether to disable a user in the target identity store when the user is disabled in the source identity store.
Allow Users to be Deprovisioned
Determines whether to deprovision a user in the target identity store when the user is deprovisioned in the source identity store.
Remove Action
The action to take when removing a user from the target identity store.
Deprovision on Rule Deletion
Determines whether to deprovision users if the associated provisioning rule is deleted.
-
Click Save.
-
To enable the connection, click the toggle at the top of the details panel to the right (blue).
You can disable the connection by clicking the toggle to the left (gray).
Result
The SCIM provisioning profile is complete and added to the list of provisioning profiles on the Provisioning page.
Next steps
Sync group members out of PingOne into a software as a service (SaaS) application. Learn more in Configuring outbound group provisioning.
SCIM provisioning features
Provision users from the PingOne identity store to a System for Cross-domain Identity Management (SCIM)-compliant identity store.
The provisioner offers the following features:
-
Supports the SCIM 1.1 and 2.0 specifications
-
User provisioning, including
create,update,disable, anddelete -
Supports SCIM core and enterprise attributes
-
Basic authentication, OAuth 2 bearer token, and OAuth 2 client credentials authentication
-
Supports SCIM overrides, such as filter expression, authorization header type, and users API path
-
Ability to provision disabled user accounts
-
Configurable deprovisioning actions
-
Configurable group provisioning
SCIM filter expressions
Use SCIM filter expressions to define how the provisioner matches existing users in the target application to users in the identity store. The expression overrides the default filter expression that is set by the User Identifier field.
The user filter expression contains the attribute name, the operation, and the attribute value. The attribute value is represented by "%s" in the expression.
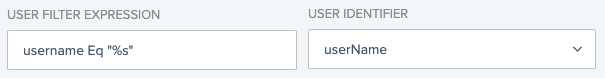
The “%s” variable stores the value of the user identifier. The value that you select in the User Identifier list, such as userName or workEmail, is used in the User Filter Expression and replaces the contents of the "%s" variable.
Example filter expressions:
-
userName Eq "%s" -
email Co "%s"
For more information, see the Filtering section in the SCIM 2.0 specification RFC 7644.
SCIM provisioning known limitations
The following are known issues or limitations with System for Cross-domain Identity Management (SCIM) user provisioning.
Service provider (SP) connections
-
The
Unique User Identifiercannot be changed in an SP connection configuration.To change to a different
Unique User Identifier, delete the existing connection and then create a connection with the newUnique User Identifier. -
All SP connections with the same target must use the same
Unique User Identifier.If multiple SP connections are created for the same target, every subsequent connection will use the
Unique User Identifierconfigured in the first connection that was created.
Attributes
-
The connector has a limit of one value per type (for example, home, work, and other) for multi-value attributes (for example, email, phone, and address).
-
If the application does not specify type or primary information on multi-value attributes, unexpected behavior can occur.
During an update, existing attributes on the application cannot be removed, and the desired value cannot be correctly set as primary.
-
The provisioner cannot clear a user attribute after it is set.
-
PingOne does not support multi-value attributes, so the first attribute value will be used.
-
If the target application supports two email attributes and one attribute is empty, the provisioner populates both attributes with the email address and sets both as primary.
This can produce unexpected effects in some target applications.
Other
-
SCIM-compliant SPs might implement or interpret the SCIM standards differently, which can result in behavior that is not consistent with the intended use of the SCIM provisioner.
-
When syncing groups and group memberships to AWS Identity Centre, you can encounter a
400 invalidfilter when a group’s name has a special character in a different language. -
When syncing groups and group memberships to Atlassian Cloud, renaming a group is not supported. Updating the Group Name causes a UI mismatch on the group’s Sync Status(Healthy - for overwrite / Sync Failure - for merge). Adding and removing members continues to work.
-
When provisioning users and groups to AWS Identity Center, you might encounter an error such as
The resource could not be modified. [prov_exception_msg] [SCIM004,].The SCIM Provisioner responds with the messageRequest is unparsable, syntactically incorrect, or violates schema.For AWS, every user must have a First name, Last name, Username, and Display name value specified. If any of these values are missing from a user, that user is not provisioned.
Learn more about special characters that you must not use in attributes synchronized with SCIM in Limitations and ListUsers in the AWS documentation. The
<>;:%SCIM filter expression is in the correct format as defined by AWS. -
When provisioning users and groups to Atlassian Cloud, the SCIM filter is
userName eq "%s". If given an invalid SCIM filter, you might encounter an error such asThe resource could not be modified. [prov_exception_msg] [SCIM004].The SCIM Provisioner responds with the messageResource [USER] invalid filter.