LDAP gateways
PingOne can use an LDAP gateway to authenticate and authorize user identities that are stored in an external directory.
Use an LDAP gateway to:
-
Authenticate users in PingOne when their credentials are stored in an external directory.
-
Set up provisioning to or from an AD or PingDirectory user store through a new or existing gateway configuration. Learn more in Creating an LDAP gateway provisioning connection.
-
Migrate identities to the PingOne directory when users initially sign on through the LDAP gateway client. Learn more in Creating an authentication policy that uses the gateway.
-
Make authorization decisions using identity data stored in an external directory. Learn more in Connecting an LDAP Gateway service.
When a user signs on to PingOne, if PingOne finds the user in the PingOne directory, then the sign-on flow continues.
If PingOne doesn’t find the user in the PingOne directory, and a gateway is configured, then PingOne checks the external user directory. If PingOne finds an identity matching the username and password, it authenticates the user and can create the identity in the PingOne directory. Each user that’s authenticated using a gateway can have their identities added to the PingOne directory.
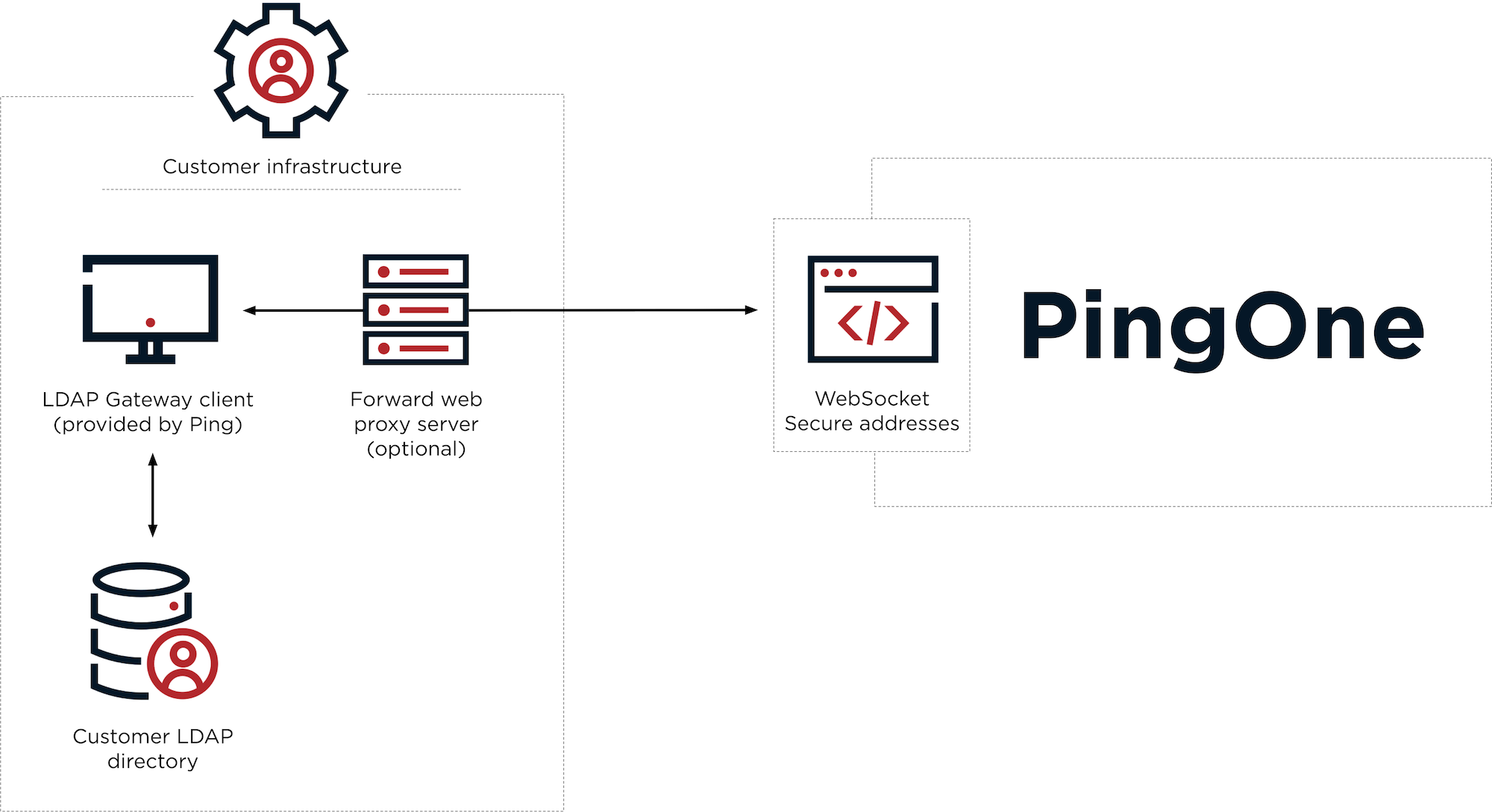
The following diagram shows a high-level overview of how LDAP gateways work in PingOne. Beginning with the LDAP gateway client application 3.2.0, you can optionally configure a forward web proxy server to handle WebSocket traffic between the gateway client and PingOne.
Supported directories
PingOne LDAP gateways support the following directories:
-
PingDirectory
-
Microsoft AD with or without Kerberos authentication
Learn more in Kerberos authentication.
-
Oracle Directory Server Enterprise Edition
-
Oracle Unified Directory
-
CA Directory
-
IBM (Tivoli) Security Directory Server
-
Any LDAP v3-compliant directory server