Redirect URIs
A redirect URI is the address to which PingOne forwards the OIDC response after authentication. For flexibility in configuring the redirect URI, you can use patterns and loopback IP redirects.
Wildcards in redirect URIs
You can choose to allow a wildcard in the redirect URI. Rather than entering an exact URI, you can use a wildcard to include multiple paths using one entry. You can use only one wildcard in the path and query portions of the URI, that is, the portion of the URI after the authority. Only one wildcard is allowed per URI. The * operator is the only supported wildcard. Learn more in Editing an application.
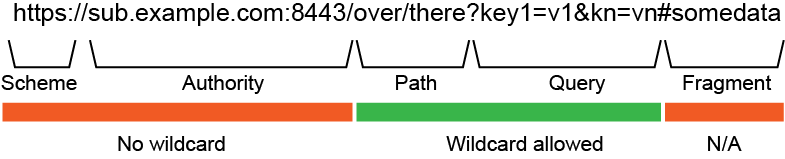
|
Fragment is not applicable because redirect URIs can’t contain fragments, following the OAuth 2.0 Authorization Framework specification. |
Example
An application is configured with a Redirect URI entry of:
https://www.example.com/th*/callback
| redirect_urivalue in the authorization request | Result |
|---|---|
|
PingOne accepts the provided |
|
PingOne accepts the provided |
|
PingOne rejects the provided |
|
For security reasons, we recommend that you use a hardcoded URL (exact match), but the wildcard option can give you flexibility if you need it. |
Loopback IP redirect URIs
PingOne supports any valid port for loopback IP redirect URIs. Native applications that can open a port on the loopback network interface without needing special permissions can use the loopback interface to receive the OAuth redirect.
To use a loopback URI, specify the Authority URL as a loopback IP address or localhost, and the port that the client is listening on. The Scheme must be HTTP or HTTPS. For more information, see Loopback Interface Redirection in the OAuth 2.0 for Native Apps RFC.
Example 1
An application is configured with a Redirect URI entry of:
http://127.0.0.1/cb
| redirect_urivalue in the authorization request | Result |
|---|---|
|
PingOne accepts the provided |
|
PingOne accepts the provided |
|
PingOne accepts the provided |
|
PingOne rejects the provided |
Example 2
An application is configured with a Redirect URI entry of:
http://127.0.0.1:8080/cb
| redirect_urivalue in the authorization request | Result |
|---|---|
|
PingOne accepts the provided |
|
PingOne rejects the provided |
|
PingOne rejects the provided |