Risk evaluations
Risk evaluations calculate the risk level associated with an event. The risk evaluation uses the risk policy and the predictors included in the risk policy to determine a final risk level of low, medium, or high. Learn more in Risk policies.
Adding risk evaluation to a user flow
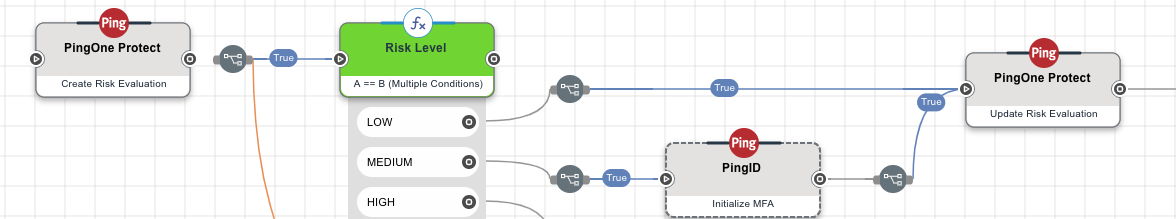
When you define a user journey, such as an authentication flow, you can include risk evaluations at relevant points in the flow. The risk evaluation is based on the risk policy that you specify for the evaluation. The following diagram shows a simplified sample flow using PingOne DaVinci that includes two steps related to risk evaluation.
-
Add a risk evaluation step at a point in the flow where you want the next action to be based on the calculated risk level. For example, you can design the flow to prompt the user to complete multi-factor authentication (MFA) for medium or high risk levels but automatically grant access for low risk level.
-
At the end of the flow, include a step to update the risk evaluation with the completion status of the flow (
SUCCESSorFAILED). In the sample DaVinci flow, completion status indicates whether the user was able to successfully authenticate or not. Learn more in Updating completion status for risk evaluations.
Analyzing risk evaluation results
Review and analyze the results from risk evaluations to see how your risk policy is performing. After reviewing the results, you might need to fine-tune your risk policy, depending on your organization’s needs and use cases. To make decisions on whether you need to adjust your risk policy, consider the following:
- Your business goals
-
Should your risk policy be more permissive or more restrictive? This decision depends on your organization’s needs, tolerance for fraud incidents, and overall revenue and user experience impacts.
- How your risk policy is configured
-
How are various predictors configured as part of your risk policy? How are the final risk levels assigned? Learn more about questions to consider when creating and fine-tuning a risk policy in Risk policies.
- The type of user flow
-
Is your risk policy used for an access, authentication, authorization, registration, or transaction flow? The type of user flow might affect the adjustments you make to a risk policy. You can also specify a flow subtype to provide additional detail about the context of the flow, such as if the user performed a password reset or signed on with their username and password. Learn more about flow types and subtypes in the PingOne Protect API documentation.
You can also create different risk policies for different use cases. Learn more in Risk policies.
- Additional identity mitigation tools
-
Should you use additional tools, such as MFA, identity verification, or knowledge-based authentication (KBA), in your user flow to prevent user identity fraud?
Learn more about how to:
-
Update the risk evaluation completion status to improve the accuracy of future risk evaluations.
-
View risk evaluations and determine if you need to fine-tune your risk policy.