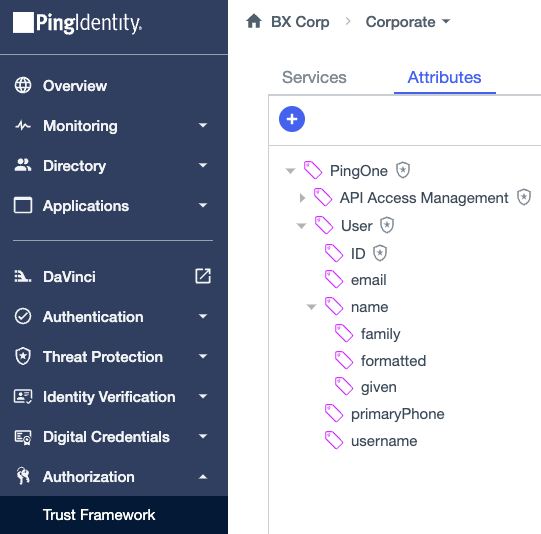
Built-in attributes
The Trust Framework provides built-in attributes that enable you to use PingOne service and user profile data right out of the box.
Built-in attributes are nested under the PingOne parent attribute on the Attributes tab. PingOne Authorize owns the PingOne parent attribute and its children.
The Shield ( ) icon indicates that these attributes are system owned and editing restrictions apply. You can’t move, update, or delete these attributes. You can’t nest your own attributes under the PingOne and user ID attributes. This ensures that built-in attributes are configured correctly and always available.
) icon indicates that these attributes are system owned and editing restrictions apply. You can’t move, update, or delete these attributes. You can’t nest your own attributes under the PingOne and user ID attributes. This ensures that built-in attributes are configured correctly and always available.
User attributes
Built-in User attributes model user identity information for use in other attributes and directly in policies. You can nest your own attributes under the User attribute.
|
The following built-in user attributes resolve from the userContext.userId property of the decision request. These attributes are derived from properties of the PingOne user object. Learn more about the user object in Users data model in the PingOne Platform API Reference.
| Attribute | Data type | Description |
|---|---|---|
User |
JSON |
The This attribute retrieves the PingOne user object through the Learn more about the PingOne User resolver in Resolvers. |
ID |
String |
The Learn more about the PingOne User ID resolver in Resolvers. |
String |
The This attribute uses a JSONPath processor to extract the user’s email address from the |
|
name |
JSON |
The This attribute uses a JSONPath processor to extract the user’s name information from the |
family |
String |
The This attribute uses a JSONPath processor to extract the user’s last name (for example, |
formatted |
String |
The This attribute uses a JSONPath processor to extract the user’s formatted name (for example, |
given |
String |
The This attribute uses a JSONPath processor to extract the user’s first name (for example, |
primaryPhone |
String |
The This attribute uses a JSONPath processor to extract the user’s phone number from the |
username |
String |
The This attribute uses a JSONPath processor to extract the username from the |
Built-in user attributes comprise a subset of the standard and core PingOne user attributes available in Directory > User Attributes. You can generate attributes in PingOne Authorize for standard, core, and custom PingOne user attributes that aren’t already built in, and use them in conditions, processors, and rules.
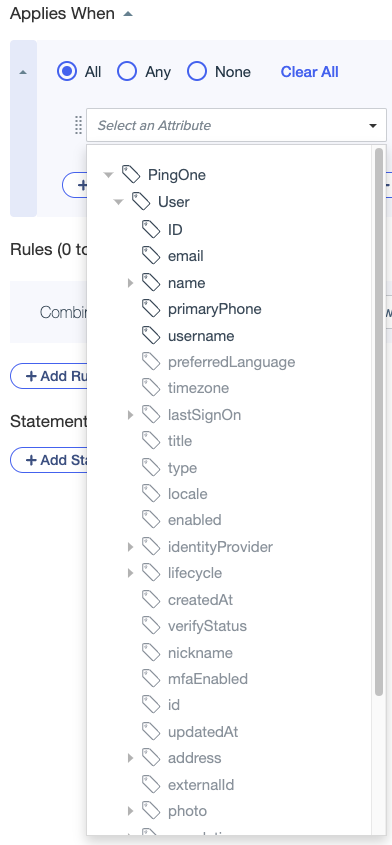
Changes made to PingOne user attributes, such as deleting an attribute or changing a custom attribute’s description, don’t affect the corresponding built-in or generated user attributes in PingOne Authorize, as long as they’re in use. Deleting a PingOne user attribute deletes the corresponding attribute in PingOne Authorize if the attribute has no dependencies.
Changes made to built-in user attributes in PingOne Authorize don’t affect the corresponding PingOne user attributes. For example, changing the name of the built-in email attribute to emailAddress in PingOne Authorize doesn’t change the name of the associated PingOne email user attribute. The PingOne Authorize emailAddress attribute will continue to work as usual to resolve the user’s email address.
API Access Management attributes
API Access Management attributes model API services and operations, HTTP requests and responses, and access tokens. PingOne Authorize generates these attributes when you enable custom policies for an API service.
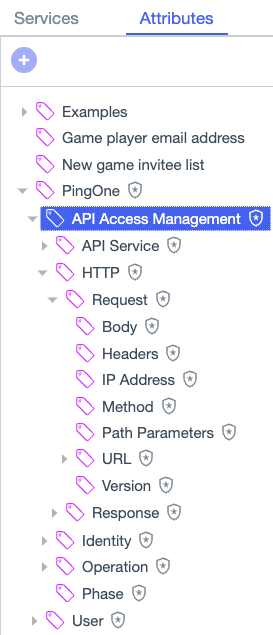
Creating attributes from built-in attributes
You can derive your own attributes from built-in API Access Management attributes, as described in the following examples.
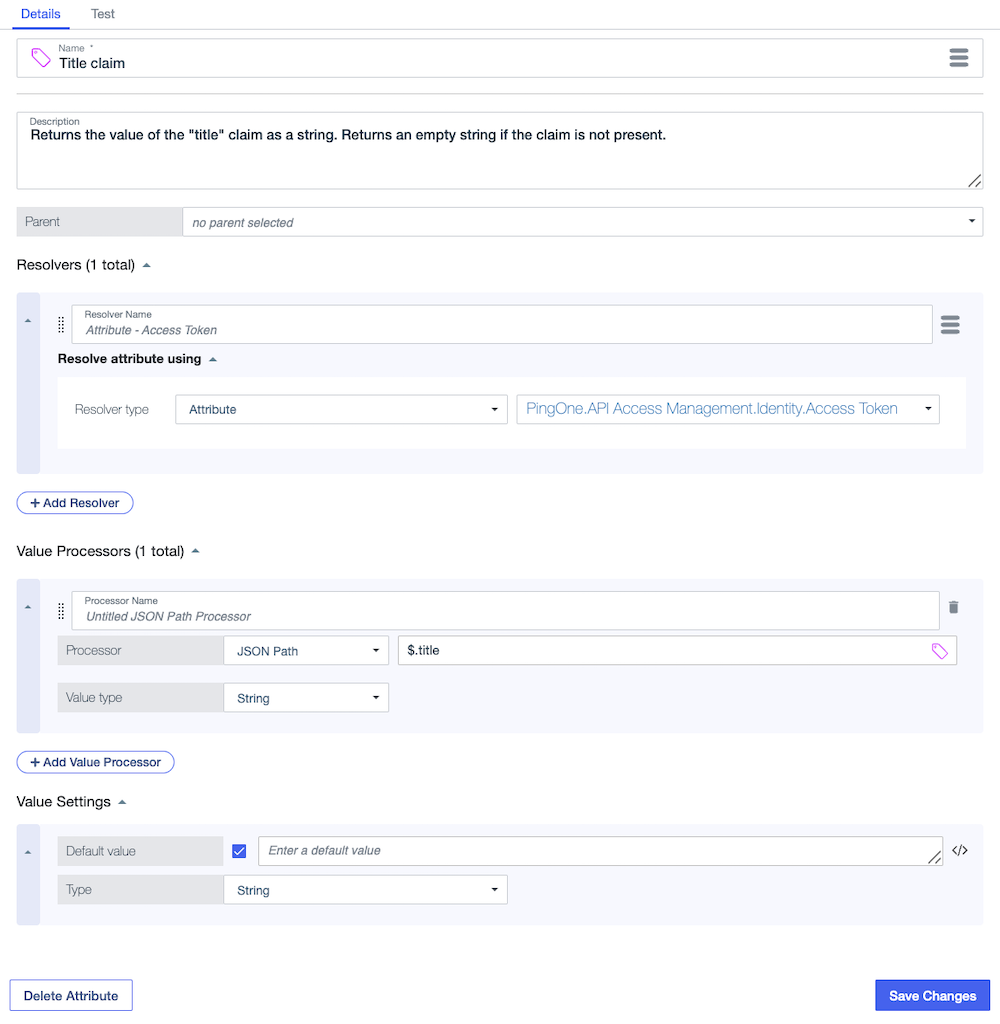
Custom access token claim attribute
In the following attribute, a value processor is used to resolve a custom title claim from the built-in PingOne.API Access Management.Identity.Access Token attribute. To ensure that a token without the custom claim is resolved successfully, the attribute has an empty string as its default value. In this example, the claim’s JSON data type is String. Access token claims can have other data types, including Number and Collection.
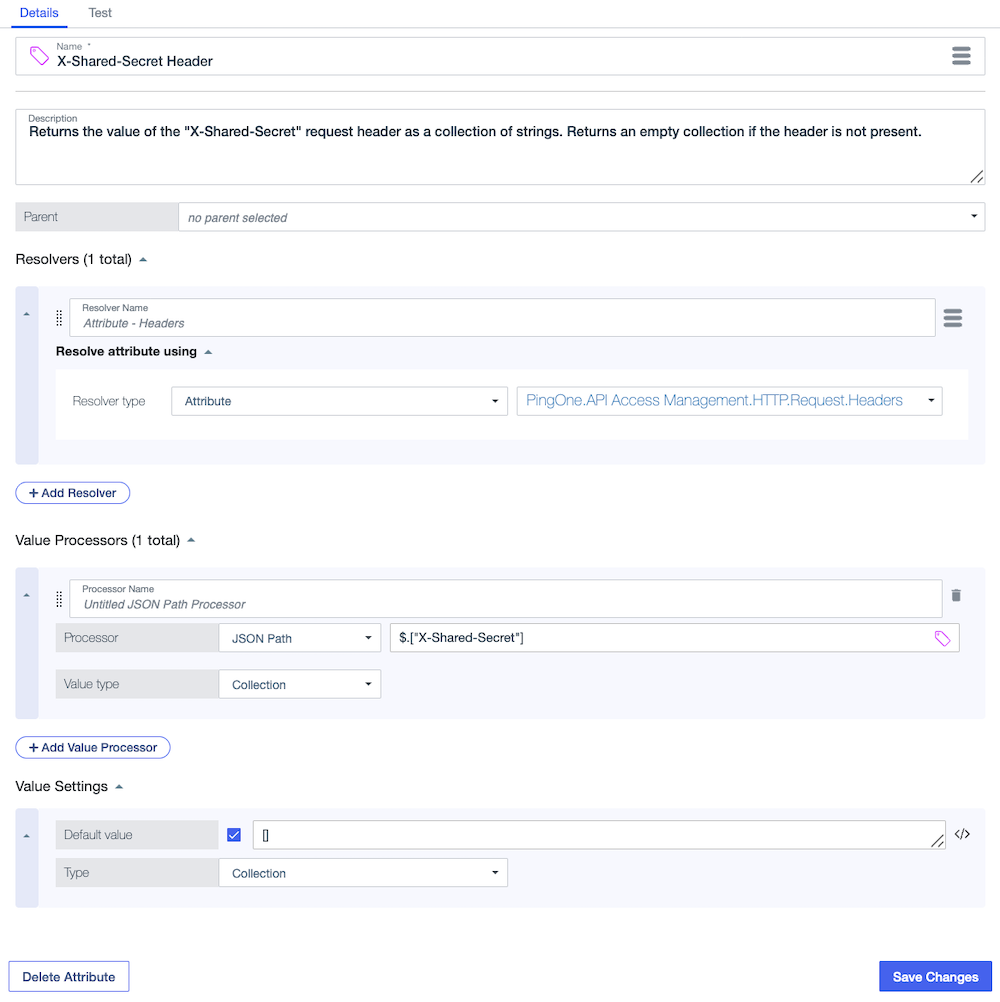
HTTP request header attribute
To allow policy authors to use a custom header in policies, you can define an attribute that extracts a custom header value from an HTTP request or response. In the following attribute, a value processor is used to resolve the X-Shared-Secret value from the built-in PingOne.API Access Management.HTTP.Request.Headers attribute as a collection. To ensure that a header without the custom value is resolved successfully, the attribute has an empty collection as its default value.
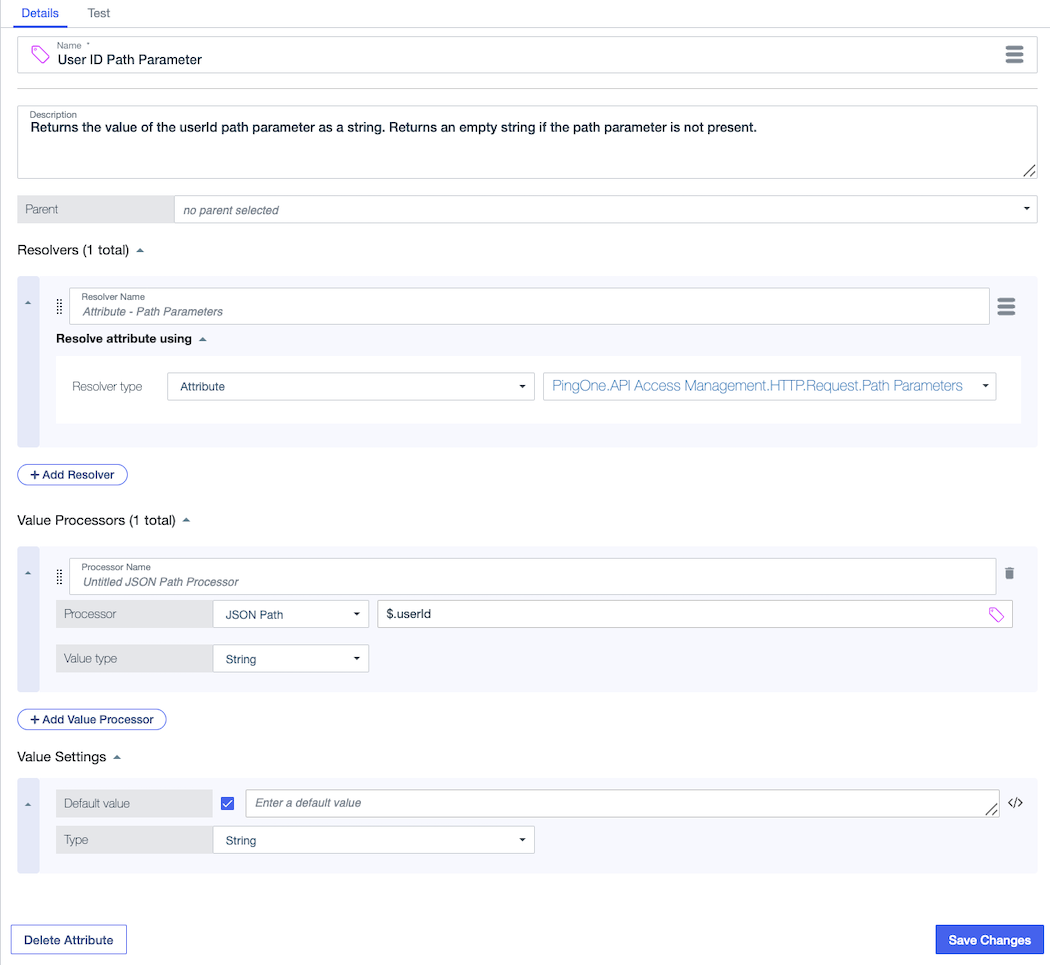
API operation path parameters
If an API operation path includes a parameter, you can define an attribute that allows policy authors to use the parameter in custom policies. For example, the following attribute extracts the user ID from a decision request that matches an API operation defined with the path /records/user/{userId}. Learn more about using this attribute in a policy in Adding custom policies for API services and operations.
Access token-related attributes
When you deploy an API service, PingOne Authorize generates a set of attributes based on various access token claims. You can use these attributes in custom policies for claims-based access control. You can also generate additional attributes for access token claims that aren’t already represented by built-in attributes.
PingOne Authorize uses the Authentication Age, Authentication Policy, and Authentication Time attributes in basic access control rules for step-up authentication.
| Attribute | Data type | Description |
|---|---|---|
Authentication Age |
Number |
The This attribute uses the |
Authentication Policy |
String |
The If the access token contains an |
Authentication Time |
Zoned Date Time |
The If the access token contains an |
Client ID |
String |
The If the access token contains a |
Scopes |
Collection |
The If the access token contains a |
Subject |
String |
The Some token issuers populate the If the access token contains a |