Connecting an LDAP Gateway service
Connect PingOne Authorize to a PingOne gateway to access user information stored in an external, on-premise LDAP directory.
Before you begin
You must configure an LDAP gateway connection to allow PingOne to communicate with the LDAP directory that contains the user information that you want to access.
About this task
PingOne gateways provide access to user identities and data stored in an external directory. After you configure an LDAP gateway connection in PingOne, add an LDAP Gateway service connection in PingOne Authorize to access user profile and group information stored in the on-premise LDAP directory.
|
Only LDAP gateway connections are supported. You cannot connect to other gateway types, such as RADIUS Gateway. |
PingOne Authorize converts user information retrieved from an LDAP Gateway service to JSON. The following is an example response from an LDAP Gateway service connection:
{
"entries": [
{
"_dn": ["cn=Philip J. Wilson,ou=people,dc=example,dc=com"],
"objectClass": ["inetOrgPerson","organizationalPerson","person","top"],
"cn": ["Philip J. Wilson"],
"sn": ["Wilson"],
"description": ["Human"],
"displayName": ["Wilson"],
"employeeType": ["Loan Officer"],
"givenName": ["Philip"],
"mail": ["wilson@example.com"],
"ou": ["Commercial Banking"],
"uid": ["wilson"],
"userPassword": ["xx"],
"entryDN": ["cn=philip j. wilson,ou=people,dc=example,dc=com"],
"entryUUID": ["3d7d9bfa-4d85-4414-94bc-ed9cfbe717b9"],
"subschemaSubentry": ["cn=schema"],
"creatorsName": ["cn=Internal Root User"],
"createTimestamp": ["20230516132411.457Z"],
"modifiersName": ["cn=Internal Root User"],
"modifyTimestamp": ["20230516132411.457Z"]
}
]
}You can use JSON Path processors in attributes to extract the information that you require from the service response for use in authorization policies.
When you add an LDAP Gateway service, configure the following LDAP Gateway settings, then configure general settings to finish the service connection:
Steps
-
Go to Authorization > Trust Framework and add a service.
-
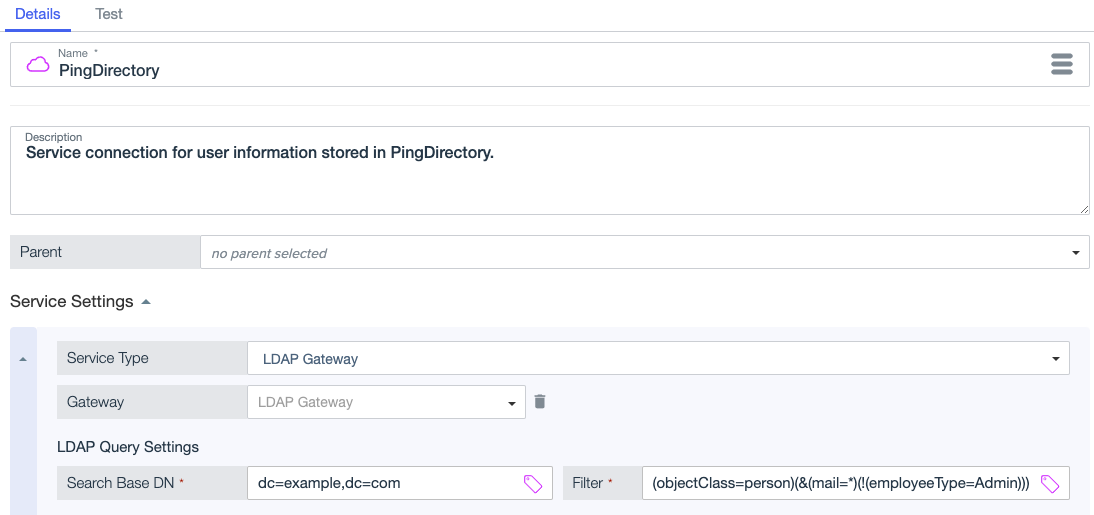
For the Service Type, select LDAP Gateway.
-
For Gateway, select the LDAP gateway connection that you set up in PingOne.
-
For the Search Base DN, enter the distinguished name for the directory information tree location where you want PingOne Authorize to start looking for user information.
Example:
The search base in the following is the domain component example.com:
dc=example,dc=com
-
To limit the scope of the results returned from the LDAP directory, enter a Filter.
Example:
This filter returns users that have email addresses, but are not administrators:
(objectClass=person)(&(mail=*)(!(employeeType=Admin)))
-
Finish general settings for the service.
Next steps
After you configure the gateway connection, you can add attributes that extract information from the service response for use in authorization policies.
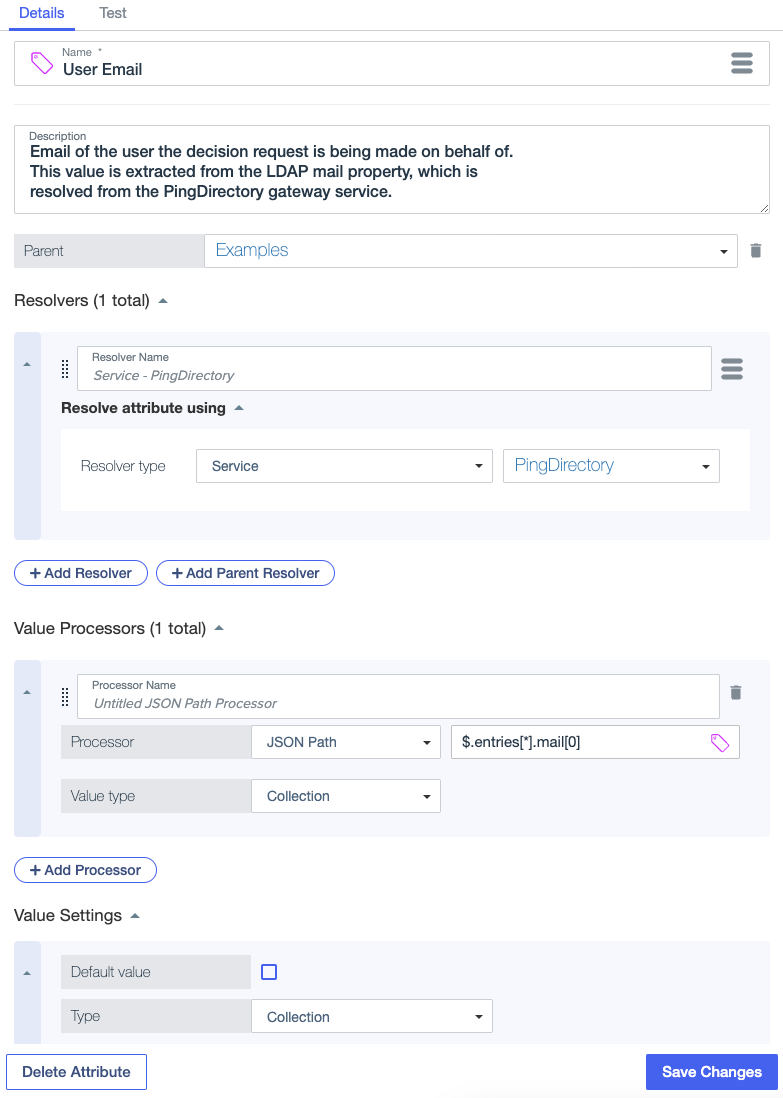
Example: Retrieve user profile information
The following attribute extracts user email addresses from the PingDirectory service. The JSON Path expression $.entries[*].mail[0] returns an array of mail strings, such as ["wilson@example.com"].
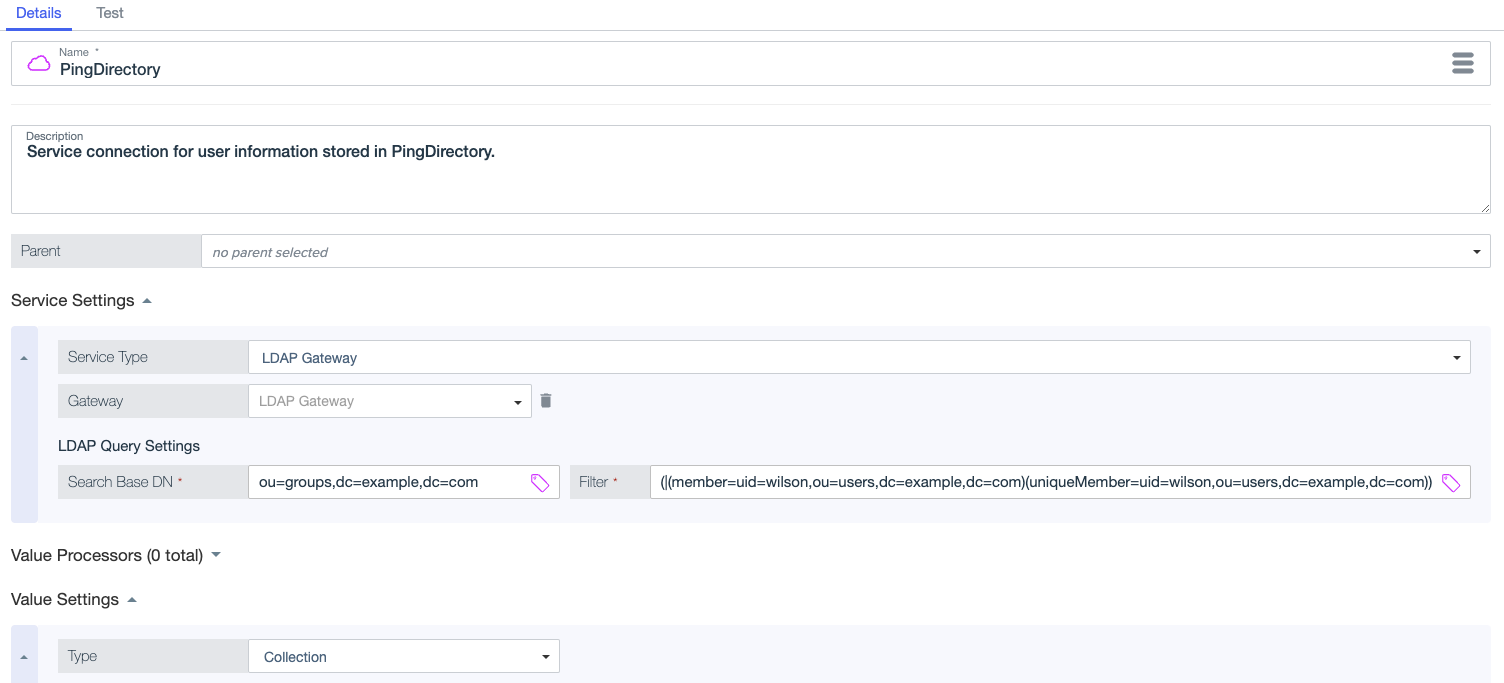
Example: Retrieve user groups
To retrieve a user’s group memberships:
-
Set the Search Base DN in the PingDirectory service to
ou=groups,dc=example,dc=com. -
Enter a Filter to retrieve a list of groups for a particular user, such as Philip Wilson.
This filter returns a list of the static groups to which Philip Wilson belongs.
(|(member=uid=wilson,ou=users,dc=example,dc=com)(uniqueMember=uid=wilson,ou=users,dc=example,dc=com))
To retrieve all of the users that are a member of a group, such as loan officers, enter the following settings for the PingDirectory service:
-
Search Base DN:
ou=people,dc=example,dc=com -
Filter:
(isMemberOf=cn=loanAdmin,ou=groups,dc=example,dc=com)
To retrieve a particular user if they are a member of a group, such as loan officers, enter the following settings for the PingDirectory service:
-
Search Base DN:
uid=wilson,ou=people,dc=example,dc=com -
Filter:
(isMemberOf=cn=loanAdmin,ou=groups,dc=example,dc=com)