Kerberos authentication
If you are using Microsoft Active Directory as your Lightweight Directory Access Protocol (LDAP) user store, you can use Kerberos for authentication. PingOne will authenticate users against the Active Directory user store using the Kerberos authentication protocol.
|
Because Microsoft Active Directory is the only directory that supports Kerberos for authentication, when you add the gateway connection, select Microsoft Active Directory for Directory type. Learn more in Adding an LDAP gateway. |
Known limitations
When an Active Directory user is a member of a large number of groups, they might receive a 413 Request Entity Too Large response during Kerberos authentication. As a user is added to more groups, the size of the Kerberos ticket increases and can exceed the limitations of the PingOne infrastructure.
To resolve this:
-
Remove the user from extraneous groups.
-
Fallback to sign on with username and password when Kerberos fails.
End user authentication flow
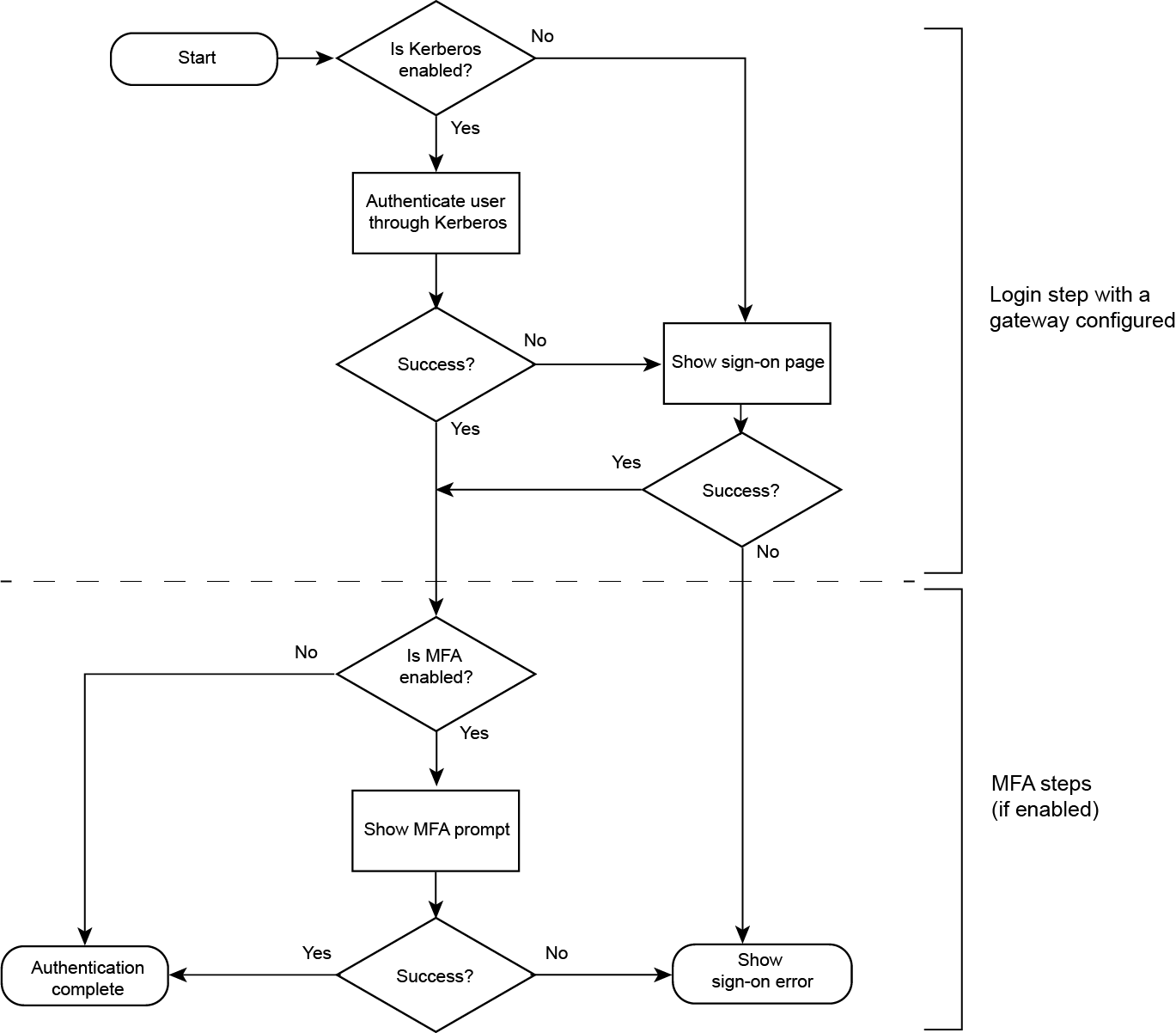
With Kerberos authentication properly configured, the end user authentication flow behaves as follows:
-
First, PingOne tries to authenticate the end user through Kerberos. This is a seamless experience and requires no user interaction.
If Kerberos authentication succeeds, the login step is complete.
-
If the authentication policy has an multi-factor authentication (MFA) step, the end user proceeds to MFA. When the end user completes all steps, PingOne redirects the browser to the target application.
-
If Kerberos authentication fails, PingOne tries to authenticate the end user by showing the sign-on page with user name and password fields.
If the end user provides the correct credentials, the login step is complete.
-
If the authentication policy has an MFA step, the end user will proceed to MFA. When the end user completes all steps, PingOne redirects the browser to the target application.
-
If the end user fails to provide the correct credentials, PingOne returns a sign-on error to the browser.
The following illustration shows the authentication flow.