Running, analyzing, and adjusting your risk policy
To make informed decisions about how to fine-tune risk predictors and policies, you’ll have to accumulate a certain amount of data on authentication attempts and how the risk evaluation impacts them.
About this task
You should use the default risk policy for the initial period before you start customizing the policy or defining multiple risk policies.
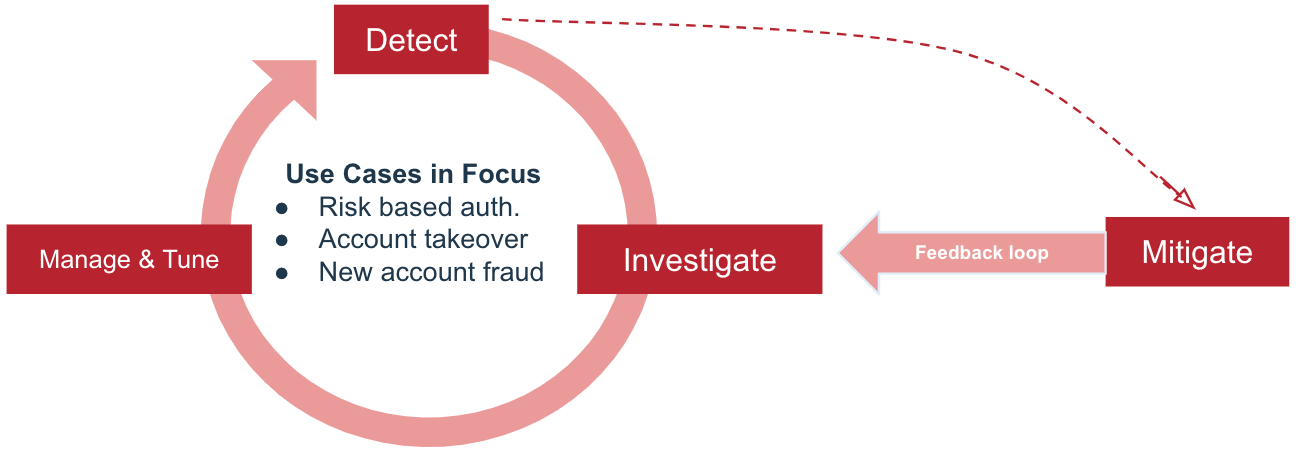
Fine-tuning your policy is an iterative process and should follow this approach:
Steps
-
Train the risk models with production data for 1-3 weeks for workforce usage or 2-4 weeks for customer usage. This should be done with the default risk policy.
-
Use the Protect dashboards to analyze the results. Identify false positive results, meaning situations that are identified as High risk even though they are legitimate users. Check what is causing these false positives.
-
Adjust the scores for the different risk predictors in the risk policy to see if you can reduce the incidence of false positives.