Overview of the SSO flow
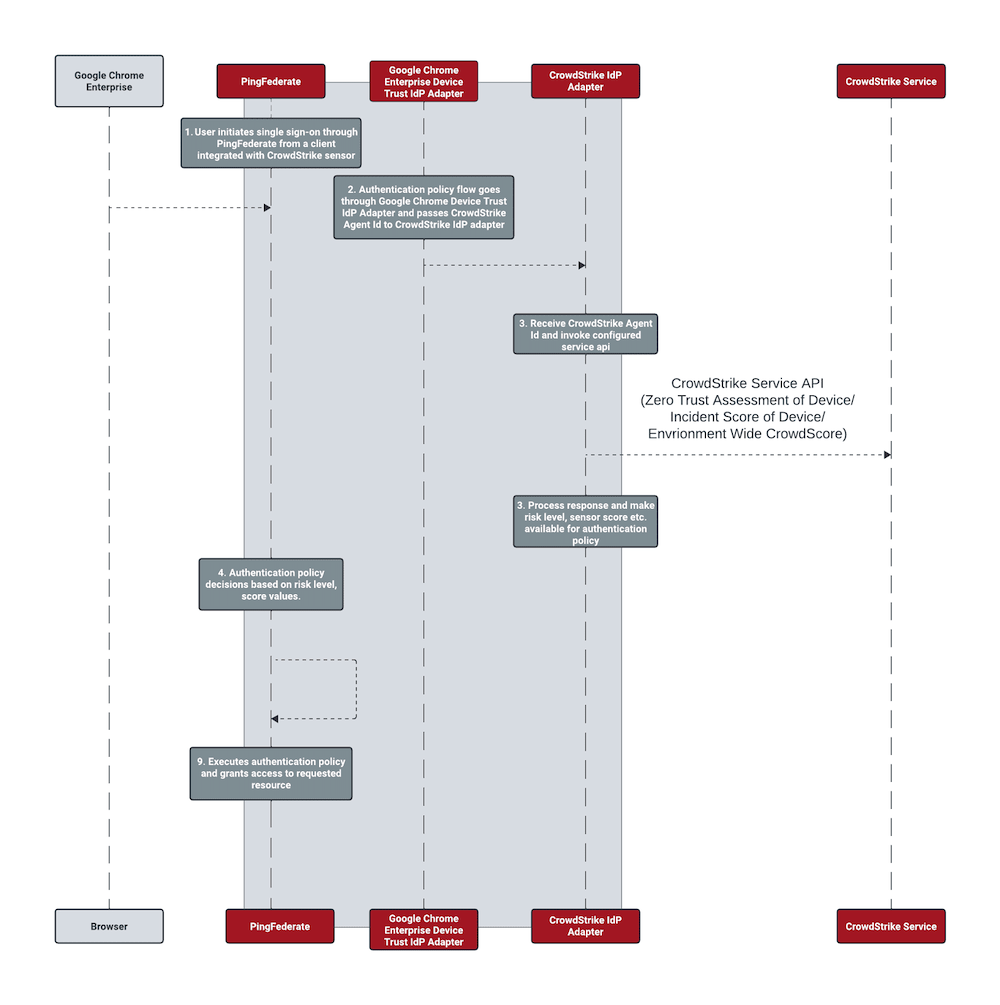
The following figure illustrates an example SSO process flow.
-
A user initiates the sign-on process by requesting access to a protected resource.
-
The Google Chrome Enterprise Device Trust IdP Adapter determines if the incoming request is from the Google Chrome Enterprise browser. If so, the authentication request goes through the adapter flow, which fulfills core contract attributes, such as the CrowdStrike Agent ID.
-
The CrowdStrike Agent ID is made available to the CrowdStrike IdP Adapter.
-
The adapter invokes the configured CrowdStrike Service API for the agent ID that it received.
-
If the CrowdStrike incident returns with a score, the risk level value is fulfilled based on the threshold level scores configured in the adapter. Learn more in CrowdStrike IdP Adapter settings reference.
-
The authentication policy can use the risk level value in subsequent decision making.