Adding risk results to your authentication policy
By modifying your authentication policy to include risk results, you can dynamically change authentication requirements for higher-risk users.
About this task
These steps are designed to help you add to an existing authentication policy. You can find general information about configuring authentication policies in Policies in the PingFederate documentation.
Steps
-
Sign on to the PingFederate administrative console.
-
Go to Authentication > Policies and either open an existing authentication policy, or create a new one.
Learn more in Defining authentication policies in the PingFederate documentation.
-
In the Policy section, in the Select list, select an iovation IdP Adapter instance.
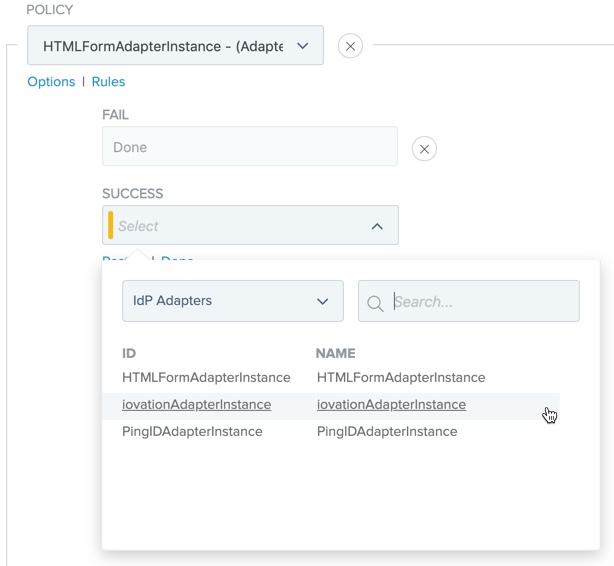
-
Map the user ID into the iovation IdP Adapter instance:
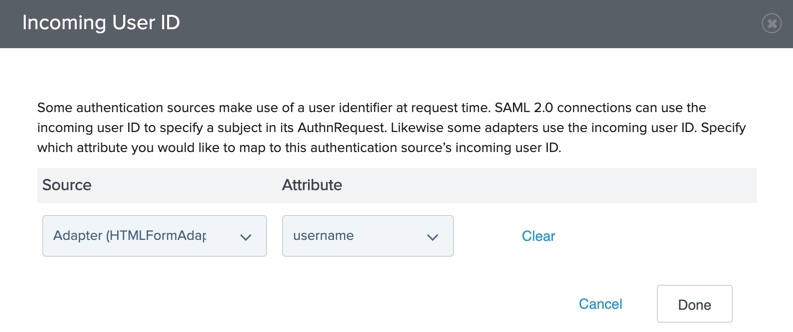
-
Under the iovation IdP Adapter instance, click Options.
-
On the Options modal, in the Source list, select a previous authentication source that collects the user ID.
-
In the Attribute list, select the user ID. Click Done.
-
-
Define policy paths based on risk results:
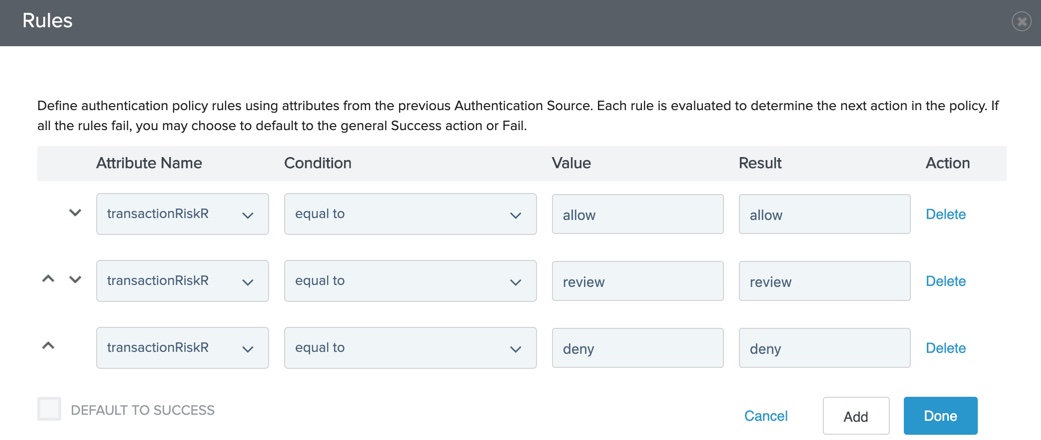
-
Under the iovation IdP Adapter instance, click Rules.
-
On the Rules modal, in the Attribute Name list, select transactionRiskResult.
-
In the Condition list, select equal to.
-
In the Value field, enter
allow,review, ordeny. -
In the Result field, enter a name.
This appears as a new policy path that branches from the authentication source.
-
To add more authentication paths, click Add and repeat steps a - d.
-
Clear the Default to success checkbox.
-
Click Done.
-
-
Configure each of the authentication paths, including Fail, Success, and the paths that you defined in the Rules modal.
In case the iovation API is unreachable or returns an error, you can allow users to continue to sign on by satisfying stricter authentication requirements.
You can do this in your authentication policy by setting the Fail outcome of the iovation IdP Adapter instance to point to a second authentication factor, as shown in the following example.
Alternately, you can do this in your iovation IdP Adapter instance by setting the Failure Mode as shown in Configuring an adapter instance.
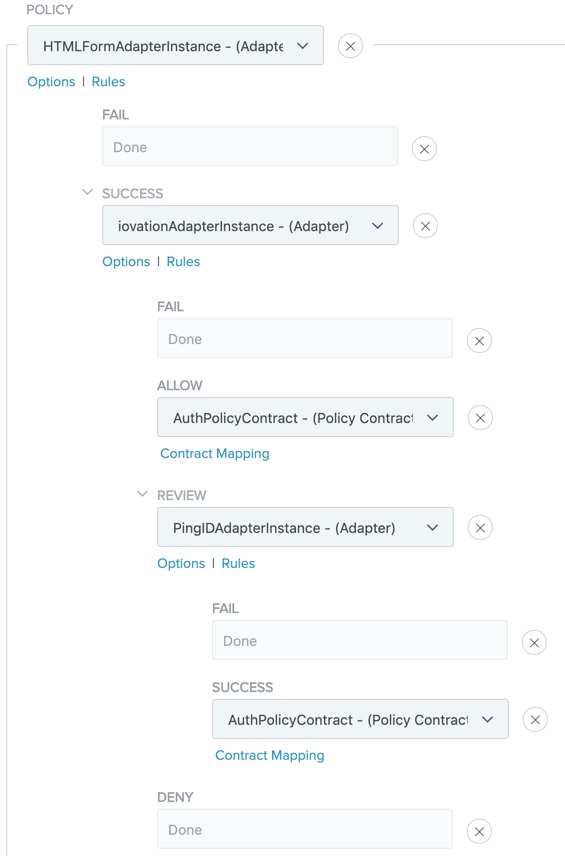
-
Click Done.
-
On the Policies page, click Save.