Using the IdP sample application
When accessed first, the identity provider (IdP) sample application simulates the IdP-initiated SSO and SLO scenario in which users authenticate to an IdP locally to access a remote service provider (SP) application. As an example scenario, users could be accessing a company portal that provides links to partner web resources such as HR or 401(k) information.
Steps
-
Start PingFederate.
-
In a web browser, open the sample application:
https://<pf_host>:<pf_port>/IdpSample
If you deployed the application elsewhere, modify the host name accordingly. Learn more in Advanced installation and configuration.
-
On the IdP Application home page, click Local Login.
-
On the Local Login page, sign on with the following credentials:
Username:
joePassword
test -
Click Login.
When you authenticate locally to the IdP sample application, no communication occurs between the application and PingFederate; the user authenticates using the local user store. No SSO use cases are invoked until PingFederate is called on the home page via the Single Sign-On button.
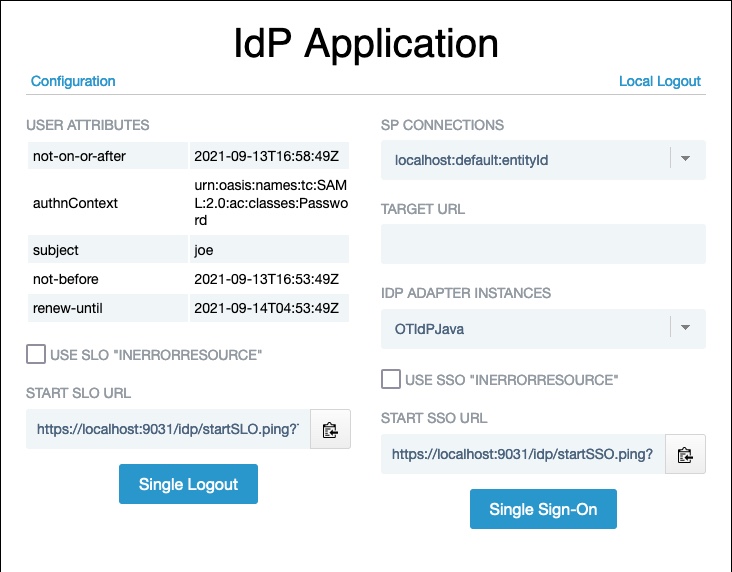
-
If you customized your configuration by creating different SP connections or deploying the IdP application on a separate server, update the application configuration as shown in IdP sample application configuration reference.
-
After logging on to the IdP sample application, the IdP Application home page reappears. In addition to SSO/SLO information and controls, this page now shows attributes sent to the SP in the SAML assertion.
The steps below describe how to test the basic SSO/SLO functionality of this page:
-
Click Single Sign-On to begin IdP-initiated SSO to the SP sample application. A user session on the SP is created, and you are signed on to the SP sample application. You can find more information in Using the SP sample application.
-
To demonstrate IdP-initiated SLO, return to this identity provider page by changing the browser location back to https://<pf_host>:<pf_port>/IdpSample. Then click Single Logout to initiate an SLO request to the SP. When the user session on the remote SP is destroyed, the local session is destroyed as well (clicking Single Sign-on here or on the SP application page redirects to the IdP logon page).
If you initiate SSO from the SP, the Single Logout button is operational and ends both sessions. If you click Local Logout on this screen, the SP session is still in force. You can access the SP application directly in the browser and see the attributes passed in from the original SAML assertion.
-