Authentication method management
The PingOne MFA IdP Adapter supports a variety of methods for managing authentication methods for PingOne users.
|
The PingOne MFA IdP Adapter can add and remove authentication methods and set a default method, but it cannot update a method’s nickname. If you want to synchronize authentication methods and other user attributes, use the PingOne Connector provided in the PingOne Integration Kit. |
Automatic authentication method provisioning
The PingOne MFA IdP Adapter supports automatic pairing for SMS, voice, and email authentication methods, which use one-time passcodes (OTPs). The adapter creates the user and associated authentication methods from attributes in the PingFederate authentication policy.
You can find details in Enabling user and authentication method provisioning.
Prompting users to set up their first authentication method
The PingOne MFA IdP Adapter allows you to prompt users to set up their first multi-factor authentication (MFA) method.
You can find details in Enabling the MFA setup prompt.
Allowing users to manage authentication methods
When the Allow Users To Manage Additional Authentication Methods checkbox is selected in the PingOne MFA IdP Adapter configuration, users can add or remove a new authentication method when they sign on.
|
This option is only available to users who authenticate with an existing authentication method. |
Users can pair any PingOne authentication method, including:
-
Authenticator apps, such as Google Authenticator
-
SMS message
-
Voice call
-
Email
-
Mobile app built with the PingOne SDK
-
FIDO2 biometrics
-
Security key
They can also remove any of these authentication methods.
Alternately, users can manage their authentication methods directly through the PingOne MFA self-service URL. Learn more in Self service and Managing authentication methods in the PingOne documentation.
Default authentication methods
On the authentication method selection page, users can set a default authentication method.
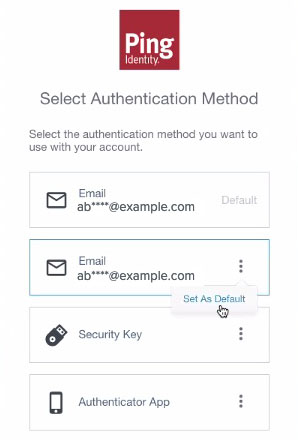
When a default method is set, the PingOne MFA IdP Adapter skips the selection screen. Users can select a different authentication method if they don’t want to continue with the default.
This capability is available when the User-selected default option is turned on in PingOne. Learn more details and limitations in the Set a default authentication method section of Managing authentication methods in the PingOne documentation.
Device integrity checks
When you create a native OIDC application as described in Creating a web or native OIDC application in PingOne, you can turn on a device integrity check. The device integrity check identifies jailbroken iOS devices and rooted Android devices. When it’s enabled, users can’t pair or authenticate with compromised devices.
When a user authenticates, PingOne reports whether the device passed the integrity check.
When a device fails, one of the following happens:
-
If you’re using the PingFederate authentication API, your application receives an
MFA_FAILEDstatus with the codeDEVICE_INTEGRITY_FAILED. -
If you’re using the PingFederate web interface, the PingOne MFA IdP Adapter shows an error page to the user.
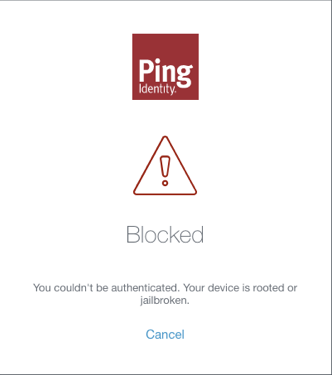
You don’t need to change anything in the PingOne MFA IdP Adapter configuration to support device integrity checks. Just enable them in your PingOne native OIDC application settings. To do so:
-
In your native OIDC application, go to the Mobile tab and click the Pencil icon.
-
In the Settings section, go to Device Integrity Check and click On.