Creating an SSO connection in PingOne
To allow PingOne to handle single sign-on (SSO) to Code42, add a Security Assertion Markup Language (SAML) application profile.
Steps
-
In PingOne, go to Applications > Applications and click .
-
On the Add Application pane, enter a unique Application Name.
-
In the Application Type section, click SAML Application, then click Configure.
-
On the SAML Configuration page, enter your SAML details:
-
Click Manually Enter.
-
Enter the following connection details using your own Code42 console address.
You can find your Code42 console address in the address bar of your browser when you sign on to Code42.

Connection details
Setting Value ACS URLs
https://Code42-console-address/api/SsoAuthLoginResponseEntity ID
https://Code42-console-address -
Click Save, then click the Pencil icon and enter the following configuration details.
Connection details continued
Setting Value Assertion Validity Duration
180or your preferred duration.Target Application URL
https://Code42-console-address/consoleUse the default settings for the rest of the configuration.
-
Click Save.
-
-
On the Attribute Mappings tab, map the PingOne
Email Addressattribute tomail: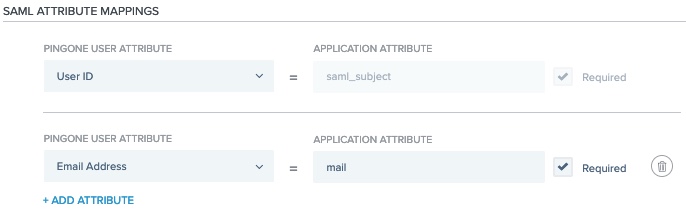
-
Click the Pencil icon, then click Add.
-
In the Attributes field, enter mail.
-
In the PingOne Mappings list, select Email Address.
If the
Email Addressattribute is unavailable, go to Directory > User Attributes, select the Show disabled attributes checkbox, and click the toggle next to email. Return to the Attribute Mapping tab for your application. -
Select the Required checkbox, then click Save.
-
-
To enable the application, in its details pane, click the toggle.
-
On the Configuration tab, click Download Metadata to save the
saml2-metadata-idp-***.xmlfile.