Configuring an adapter instance
To get started with the integration, deploy the PingOne Risk Integration Kit files to your PingFederate directory.
Steps
-
In the PingFederate administrative console, go to Authentication > Integration > IdP Adapters. Click Create New Instance.
-
On the Type tab, set the basic adapter instance attributes:
-
In the Instance Name field, enter a name for the adapter instance.
-
In the Instance ID field, enter a unique identifier for the adapter instance.
-
In the Type list, select PingOne Risk IdP Adapter. Click Next.
-
-
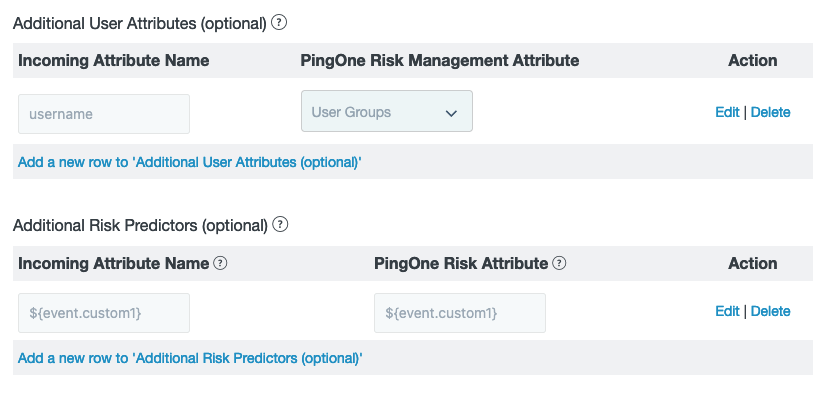
On the IdP Adapter tab, in the Additional User Attributes section, configure additional information to send to PingOne Risk.
-
Click Add a new row to 'Additional User Attributes'.
-
In the Incoming Attribute Name field, enter the name of an attribute from any authentication source that appears earlier in your PingFederate authentication policy than the PingOne Risk IdP Adapter.
-
In the PingOne Risk Attribute list, select the PingOne attribute that you want to populate.
-
In the Action column, click Update.
-
To add more attributes, repeat Steps a-d.
-
-
Optional: On the IdP Adapter tab, map any custom risk predictors.
Learn more in Using custom risk predictors.
-
Click Add a new row to 'Additional Risk Predictors (optional)'.
-
In the Incoming Attribute Name field, enter the name of an attribute from any authentication source that appears earlier in your PingFederate authentication policy than the PingOne Risk IdP Adapter.
-
In the PingOne Risk Attribute list, select the PingOne attribute that will be assessed in the risk policy, for example
$\{event.isManaged}. -
In the Action column, click Update.
-
To add more attributes, repeat steps a - d.
-
-
Optional: On the IdP Adapter tab, in the PingOne Risk API Response Mappings section, map attributes from PingOne Risk Evaluation API response to the attribute contract.
These attributes become available in your PingFederate authentication policy.
-
Click Add a new row to 'PingOne Risk API Response Mappings'.
-
In the Local Attribute field, enter a name of your choosing for an attribute.
-
In the PingOne Risk API Attribute Mapping field, enter the JSON Pointer syntax for the source PingOne attribute as shown in JSON pointer syntax reference.
For example, the JSON pointer
/details/ipAddressReputation/levelwill return the IP address repuation level, such asLOW. -
In the Action column, click Update.
-
To add more attributes, repeat steps a-d.
-
-
On the IdP Adapter tab, configure the adapter instance by referring to PingOne Risk IdP adapter settings reference. Click Next.
-
On the Actions tab, test your connection to PingOne Risk. Resolve any issues that are reported, and then click Next.
-
On the Extended Contract tab, add any attributes that you included in the PingOne Risk API Response Mappings section of the IdP Adapter tab. Click Next.
-
On the Adapter Attributes tab, set pseudonym and masking options as shown in Set pseudonym and masking options in the PingFederate documentation. Click Next.
-
On the Adapter Contract Mapping tab, configure the contract fulfillment details for the adapter as shown in Define the IdP adapter contract in the PingFederate documentation. Click Next.
-
On the Summary tab, check and save your configuration. Click Save.