Overview of the SSO flow
With the Symantec VIP integration kit, PingFederate includes the Symantec VIP service in the authentication flow.
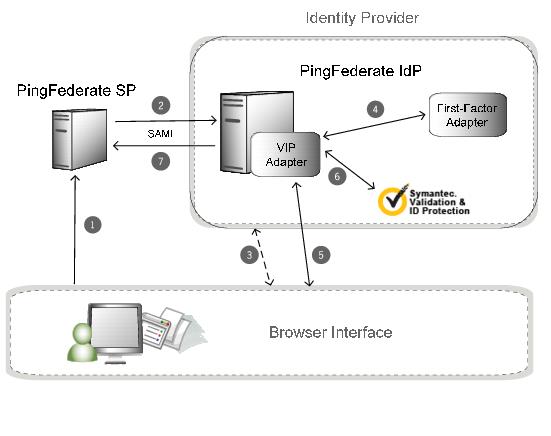
Description
-
The user initiates single sign-on (SSO) from an service provider (SP) application through a PingFederate SP server.
This SP-initiated scenario represents the optimal use case, one in which both the identity provider (IdP) and SP are using PingFederate. However, PingFederate accepts any valid Security Assertion Markup Language (SAML) authentication request from an SP.
In addition, you can enable IdP-initiated SSO. In this case, the user attempts SSO to an SP application from the IdP site, and the processing sequence would not include the following step.
-
The PingFederate SP server generates a SAML AuthnRequest to the PingFederate IdP server.
-
If not already signed on at the IdP (using a first-factor adapter such as Lightweight Directory Access Protocol (LDAP) or Integrated Windows authentication (IWA)), the user is challenged to authenticate.
-
The PingFederate IdP server obtains user-session information via the first-factor adapter.
-
The Symantec VIP IdP adapter requests a one-time passcode (OTP) from the user.
-
The Symantec VIP IdP adapter uses the username obtained by the first-factor adapter and the OTP to verify the user and the code via the Symantec VIP application programming interface (API).
-
If the validation succeeds, the PingFederate IdP server generates a SAML assertion with the username as the Subject and passes it to the PingFederate SP server.
-
(Not shown) The user is signed on to the SP target application.