IdP process overview
The following figure illustrates the request flow and how the WAM IdP Adapter is leveraged in generating a SAML/WS-Federation assertion using a WAM session cookie.
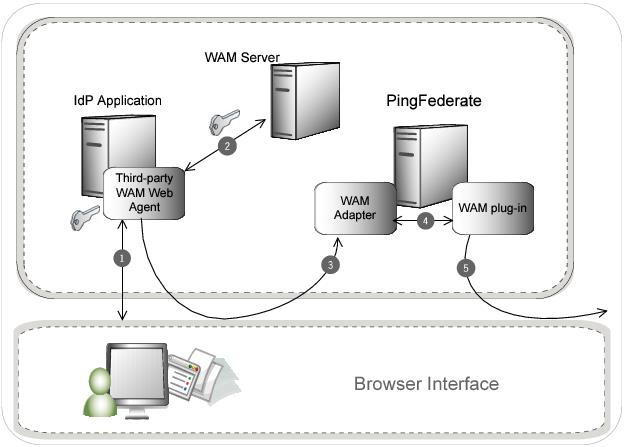
Processing Steps
-
The user’s browser attempts to access the IdP application. The third-party WAM Web Agent intercepts the request and asks for the user’s identity. The user enters the requested credentials and submits the login page.
-
The WAM Server validates the user’s credentials and creates a WAM session cookie. The user now has access to the application.
-
The user clicks a link that initiates an SSO transaction to the partner application. The request is redirected to the PingFederate IdP Server. The WAM session cookie generated in step 2 is included in the request.
-
The PingFederate WAM IdP Adapter uses the WAM plug-in to decrypt the WAM session cookie and then transfers the attributes to the PingFederate IdP Server. You can create an attribute contract to map the WAM session cookie and response attributes. For more information, see Defining an attribute contract in the PingFederate documentation.
-
The PingFederate IdP server generates a SAML/WS-Federation assertion and redirects the request, with the assertion, back through the user’s browser to the SP site.