SP single sign-on integration using account linking
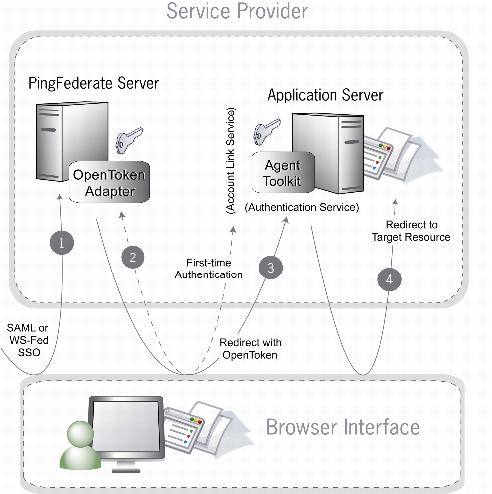
If an SP’s SSO implementation employs account linking, the flow of events is somewhat different since a user must authenticate to the SP application the first time SSO is initiated (for more information, see Key concepts in the PingFederate documentation). In this case, PingFederate and the OpenToken Adapter support an integration mechanism to redirect the user to an Account Link Service to which a user can authenticate initially. Upon successful authentication, the user’s browser is redirected back to PingFederate with an OpenToken, which PingFederate uses to create an account link for the user. For subsequent SSO requests, PingFederate uses the account link established in the first SSO request to identify the user. It then creates an OpenToken and sends it to the Authentication Service associated with the application.
-
PingFederate receives an assertion under either the SAML 2.0, OpenID Connect, or WS-Federation protocol.
-
If this is the first time the user has initiated SSO to this SP, PingFederate redirects the browser to the Application Server’s Account Link Service, where the user must authenticate. Upon successful authentication, an OpenToken is returned to PingFederate, and an account link is established for this user within PingFederate. This account link is used on subsequent SSO transactions.
-
PingFederate retrieves the local user ID from its account link data store. Through the OpenToken Adapter, PingFederate generates an OpenToken based on the assertion and account link. PingFederate then redirects the user’s browser to the web application’s SSO Authentication Service, passing the OpenToken in the redirect.
-
The Authentication Service extracts the contents of the OpenToken, establishes a session for the user, and redirects the user’s browser to the Target Resource (the resumePath URL sent as a query parameter).
Linking accounts
In an Account Linking event, the user’s browser is redirected to the configured Account Linking service in the SP OpenToken Adapter instance. The application should capture the resumePath upon a GET request to this URL with something similar to the following:
IDictionary userInfo = new Dictionary<String, String>();
// Add userId for the logged on user as the token subject
userInfo.Add(Agent.TOKEN_SUBJECT, <userId>);
String returnUrl = "https://<{pingfed} DNS>:9031" + Request["resume"];
. . . .
try {
UrlHelper urlHelper = new UrlHelper(returnUrl);
//For sample code that instantiates and configures an Agent instance, see the
//"Integrating the OpenToken Agent into your application" topic in the documentation
agent.WriteToken(userInfo,Response,urlHelper,false);
returnUrl = urlHelper.ToString();
}
catch(TokenException e) {
// Handle exception
}
Response.Redirect(returnUrl);