Implementing IdP functionality
The NetWeaver IdP Adapter uses the SAP SSO extension library to decrypt the session ticket and pass the attributes to the PingFederate server, which maps the values into an assertion and sends the assertion to the SP’s federation gateway. For more information about configuration setup and attribute mapping, see Configuring an IdP adapter instance and User attributes in the PingFederate documentation.
The following figure illustrates the request flow and how the NetWeaver IdP Adapter is used in generating a SAML assertion:
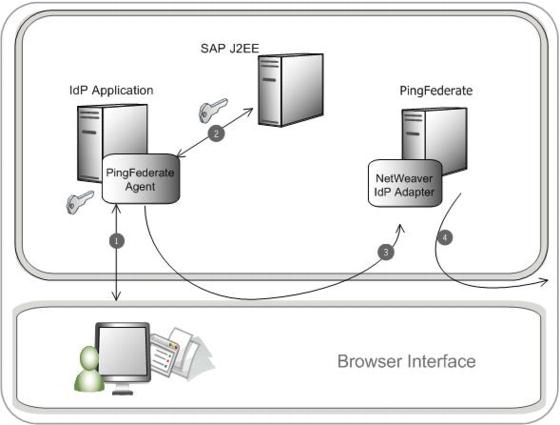
Processing Steps
-
The user’s browser accesses the IdP application.
-
The SAP J2EE Server authenticates the user and creates a session ticket.
-
The user clicks a link that initiates a Single Sign-on (SSO) transaction to the partner application. The request is redirected to the PingFederate IdP Server.
-
The NetWeaver IdP Adapter retrieves the session ticket from the session cookie, decrypts the session ticket, and then transfers the attributes to the PingFederate IdP Server.
-
The PingFederate IdP server generates a SAML assertion and redirects the request, with the assertion, back through the user’s browser to the SP site.