Configuring Browser SSO
Use the following details for the Browser SSO part of your single sign-on (SSO) connection to Slack.
About this task
|
For all other settings, you can use the default or customize the configuration for your needs. For help, see Configuring IdP Browser SSO in the PingFederate documentation. |
For more context on subject format requirements, see SAML NameID Format urn:oasis:names:tc:SAML:2.0:nameid-format:persistent in the Ping Identity Knowledge Center.
Steps
-
On the Browser SSO tab, click Configure Browser SSO.
-
On the Browser SSO > SAML Profiles tab, select only IDP-Initiated SSO and SP-Initiated SSO. Click Next.
-
On the Assertion Lifetime tab, click Next.
-
On the Assertion Creation tab, configure the assertion.
The following steps only cover the critical settings for the Slack connection. For a complete guide, see Managing authentication source mappings in the PingFederate documentation.
-
Click Configure Assertion Creation.
-
On the Attribute Contract tab, set the following name format.
Attribute Contract Subject Name Format SAML_SUBJECT
urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified -
In the Extended the Contract section, add the following attributes, and then click Next.
Extend the Contract Mappings Extend the Contract Attribute name Format SAML_NAME_FORMAT
urn:oasis:names:tc:SAML:2.0:attrname-format:unspecifiedUser.Email
urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified -
On the Authentication Source Mapping tab, select or create your authentication source.
For help, see Managing authentication source mappings in the PingFederate documentation.
-
On your authentication source Mapping Methodtab, select Retrieve additional attributes from a data store.
-
On your authentication source Attribute Sources & User Lookuptab, select or create your LDAP datastore.
-
On your authentication source Attribute Sources & User Lookuptab, select or create your LDAP datastore. On the LDAP Directory Search tab, use the following configuration.
For more information, see Specifying directory properties and attributes in the PingFederate documentation.
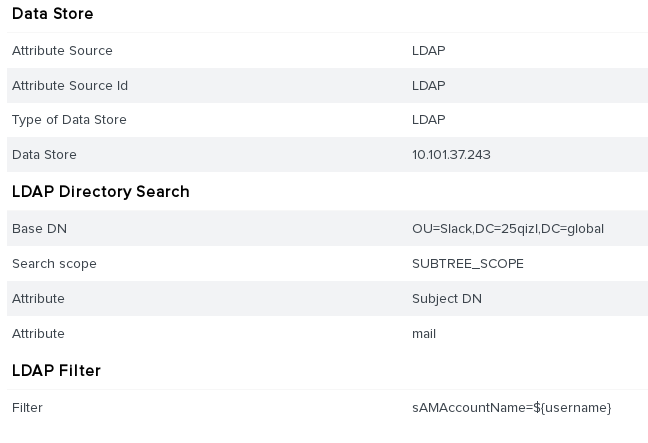
-
On the Browser SSO > Assertion Creation > IdP Adapter Mapping > Attribute Contract Fulfillment tab, map the attributes as follows. Click Next.
This allows the connection to provide Slack with the required
urn:oasis:names:tc:SAML:2.0:nameid-format:persistentname format, which PingFederate does not provide as a default option.Attribute Contract Source Value SAML_NAME_FORMAT
text
urn:oasis:names:tc:SAML:2.0:nameid-format:persistentSAML_SUBJECT
Adapter
usernameUser.Email
LDAP
mail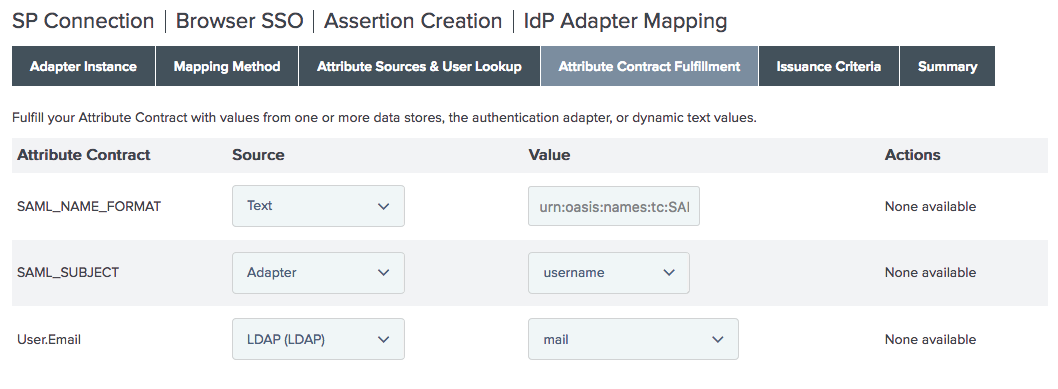
-
-
On the Browser SSO > Protocol Settings > Signature Policy tab, clear the Require authn requests… and Always sign assertion check boxes. Click Next.
-
On the Encryption Policy tab, select None. Click Next.
-
On the Browser SSO > Protocol Settings tab, click Next.
-
On the Summary tab, click Done.
-
On the SP Connection > Browser SSO tab, click Next.