SP single sign-on (using account linking)
If an SP’s SSO implementation uses account linking, the flow of events is slightly different because a user must authenticate to the SP application the first time SSO is initiated. Learn more in Key concepts in the PingFederate documentation.
In this case, PingFederate and the OpenToken Adapter support an integration mechanism to redirect the user to an Account Link Service to which a user can initially authenticate. After the user authenticates successfully, the account link service must redirect the user back to PingFederate with an OpenToken that PingFederate uses to create an account link for the user.
For subsequent SSO requests, PingFederate uses the account link established in the first SSO request to identify the user. It then creates an OpenToken and sends it to the authentication service associated with the application.
The following diagram shows the SP SSO flow using account linking:
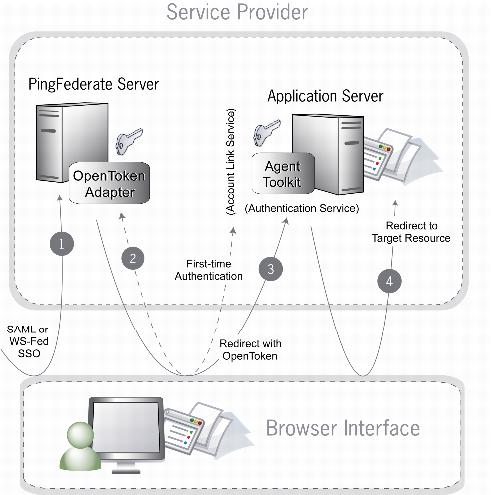
Sequence
-
PingFederate receives an assertion under the SAML 2.0 or WS-Federation protocol.
-
If this is the first time the user has initiated SSO to this SP, PingFederate redirects the browser to the application server’s account link service, where the user must authenticate. After the user authenticates successfully, an
OpenTokenis returned to PingFederate, and an account link is established for this user within PingFederate. This account link is used on subsequent SSO transactions. -
PingFederate retrieves the local user ID from its account link data store. PingFederate’s OpenToken Adapter generates an
OpenTokenbased on the assertion and account link. PingFederate then redirects the user’s browser to the web application’s SSO authentication service, passing theOpenTokenin the redirect. -
The authentication service extracts the contents of the
OpenToken, establishes a session for the user, and redirects the user’s browser to the target resource (the resumePath URL is sent as a query parameter).