Adding Jamf security posture results to your authentication policy
By modifying your PingFederate authentication policy to include the isManaged or isMDMCapable results from Jamf Pro, you can dynamically control access to resources based on the device’s security posture.
About this task
These steps are designed to help you add to an existing authentication policy. For general information about configuring authentication policies, see PingFederate authentication API in the PingFederate documentation.
Steps
-
In the PingFederate administrative console, go to the Policies tab.
Choose from:
-
For PingFederate 10.1 or later: go to Authentication > Policies > Policies.
-
For PingFederate 10.0 or earlier: go to Identity Provider > Authentication Policies > Policies.
-
-
Select the IdP Authentication Policies check box.
-
Open an existing authentication policy, or click Add Policy. See Defining authentication policies in the PingFederate documentation.
-
In the Policy area, from the Select list, select a Jamf IdP Adapter instance.
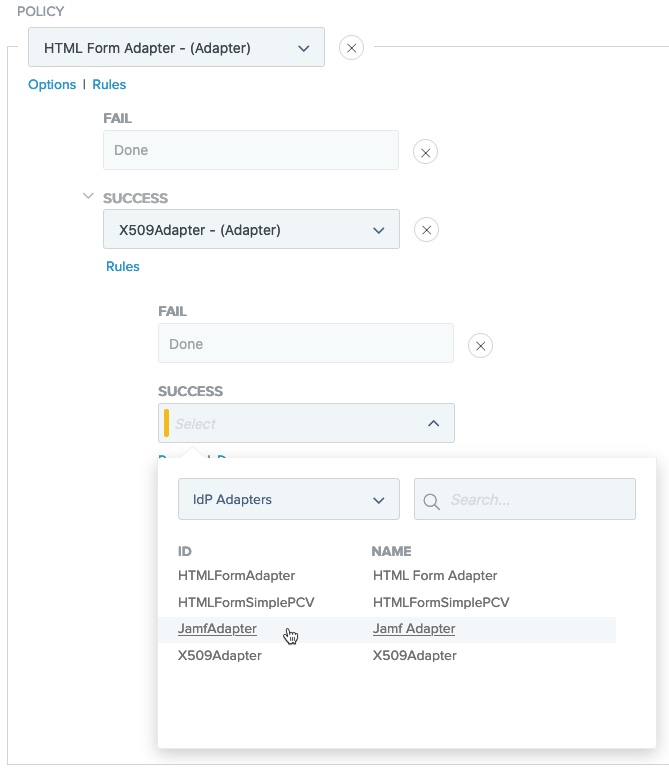
-
Map the attribute that contains the device identifier (shown here as SerialNumber) from your X.509 Certificate IdP Adapter instance into the Jamf IdP Adapter instance.
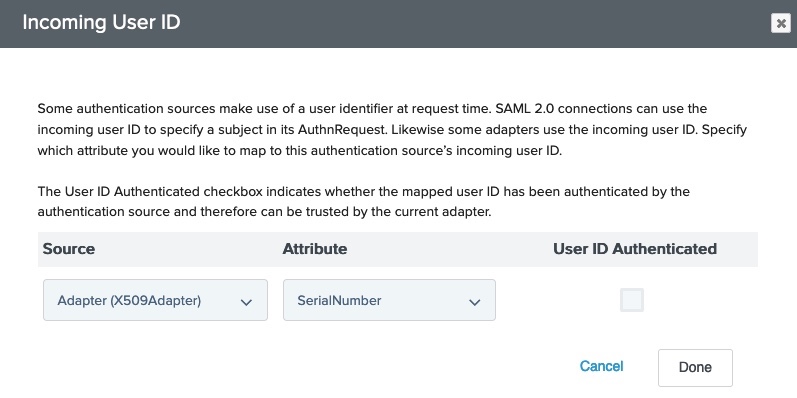
-
Under the Jamf IdP Adapter instance, click Options.
-
On the Options dialog, from the Source list, select your X.509 Certificate IdP Adapter instance.
-
From the Attribute list, select attribute that matches the Device Identifier that you selected in your adapter configuration. Click Done.
-
-
Define policy paths based on the security posture attribute
isCompliant.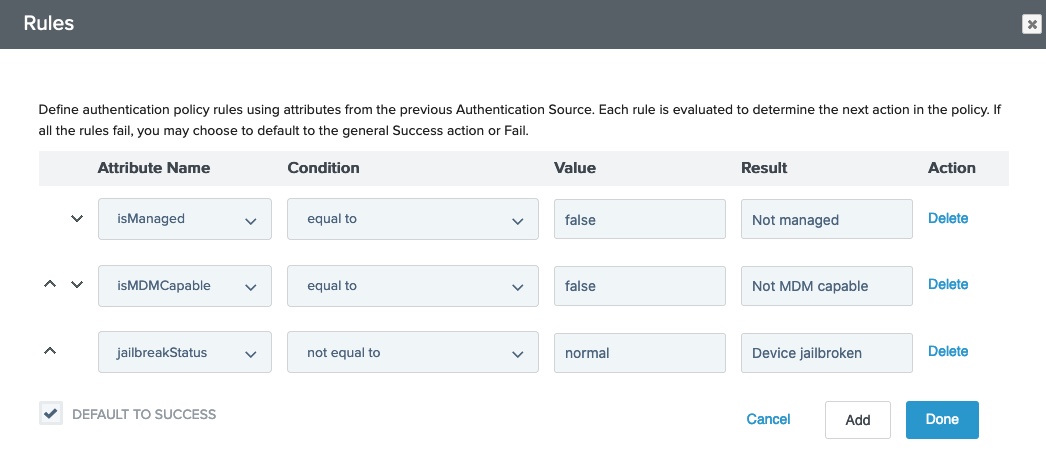
-
Under the Jamf IdP Adapter instance, click Rules.
-
On the Rules dialog, in the Attribute Name list, select isCompliant.
-
In the Condition list, select equal to.
-
In the Value field, enter
trueorfalse. -
In the Result field, enter a name. This appears as a new policy path that branches from the authentication source.
-
Optional: Repeat steps a-e for
isMDMCapableor any attributes that you mapped in the Jamf API Attribute Mappings table in the adapter configuration. -
Optional: Clear the Default to success check box to ensure the authentication flow follows one of the paths that you defined.
-
Click Done.
-
-
Configure each of the authentication paths.
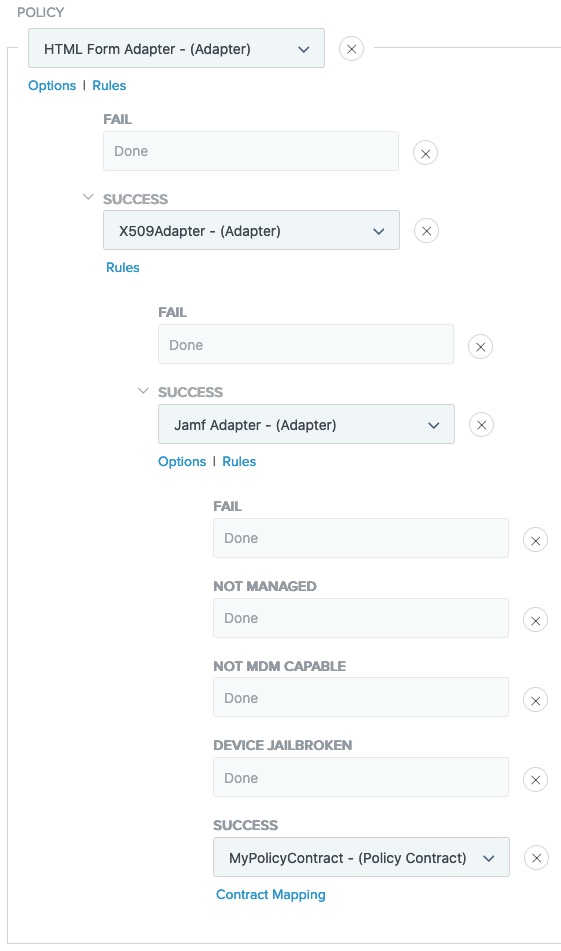
-
Click Done.
-
In the Policies window, click Save.