IdP implementation
This section describes using the OAM Integration Kit as an identity provider (IdP).
The OAM IdP Adapter uses the Access Server SDK to decrypt the OAM session cookie and pass attributes to the PingFederate server. You can then add attribute values to the Attribute Contract in the PingFederate administrative console and transfer them to a partner application in a SAML assertion. (For more information, see: Creating an Attribute Contract in the PingFederate Administrator’s Manual.)
The following figure illustrates the request flow and how the OAM IdP Adapter is used to facilitate generating a SAML WS-Federation assertion from the ObSSOCookie:
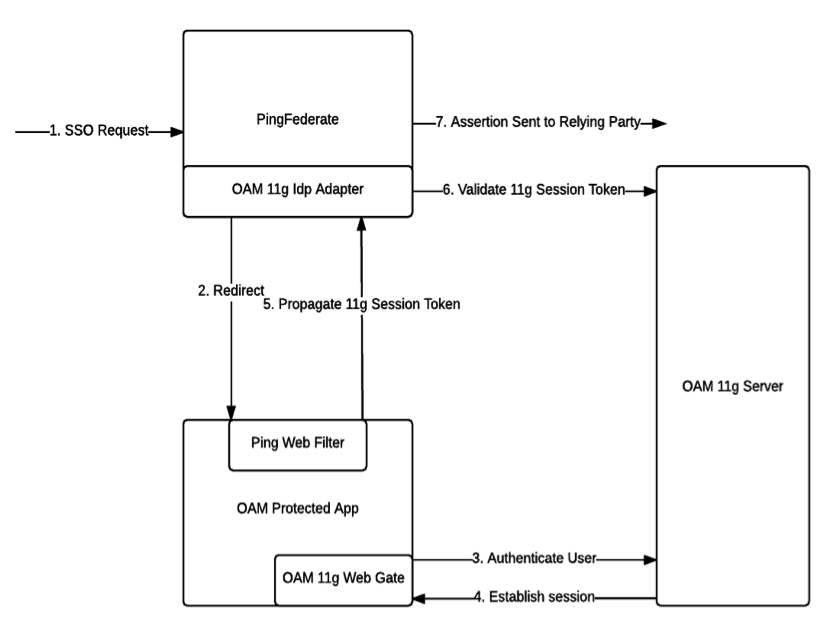
Processing Steps
-
User initiates single sign on through PingFederate.
-
The OAM IdP Adapter redirects the user to an OAM Protected Resource.
-
OAM Webgate authenticates the user.
-
After successful authentication an OAM 11g session is established and a host level cookie is created for the Webgate.
-
User is allowed access to the OAM protected resource at which point the Ping Web Filter intercepts this request and sends the host level OAM Session token to PingFederate.
-
OAM IdP Adapter validates the session token using Access Server APIs.
-
The user information is passed to PingFederate, which can create an assertion and send it to the required relying party (aka service provider).