Overview of the SSO flow
With the ThreatMetrix Integration Kit, PingFederate includes ThreatMetrix in the sign-on flow.
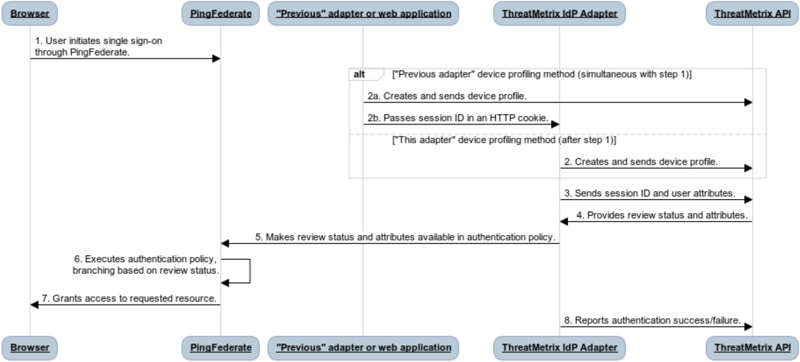
The following figure shows how ThreatMetrix is integrated into the sign-on process:
Description
-
A user initiates the sign-on process by requesting access to a protected resource.
-
Depending on the device profiling method, the ThreatMetrix IdP Adapter or a previous authentication adapter collects the device profile and sends it back to ThreatMetrix with a session ID.
If using the Captured by a Previous Adapter device profiling method, this step takes place at the same time as step 1.
-
The ThreatMetrix IdP Adapter sends the session ID and any optional user attributes to ThreatMetrix.
-
ThreatMetrix responds with the review status (
pass,review,challenge, orreject) as well as additional attributes and sign-on event data. -
The ThreatMetrix IdP Adapter makes the review status, attributes, and sign-on event data available in the PingFederate authentication policy.
-
PingFederate continues executing the authentication policy, which branches based on the review status provided by the adapter.
-
If the user authenticates successfully, PingFederate returns the resource that the user requested.
-
(Optional) If the review status was
reviewand authentication ultimately succeeded, the adapter notifies ThreatMetrix.This allows ThreatMetrix to train models and tune policies for future sign-on attempts.