Overview of the SSO flow
The following figure demonstrates an example single sign-on (SSO) process flow.
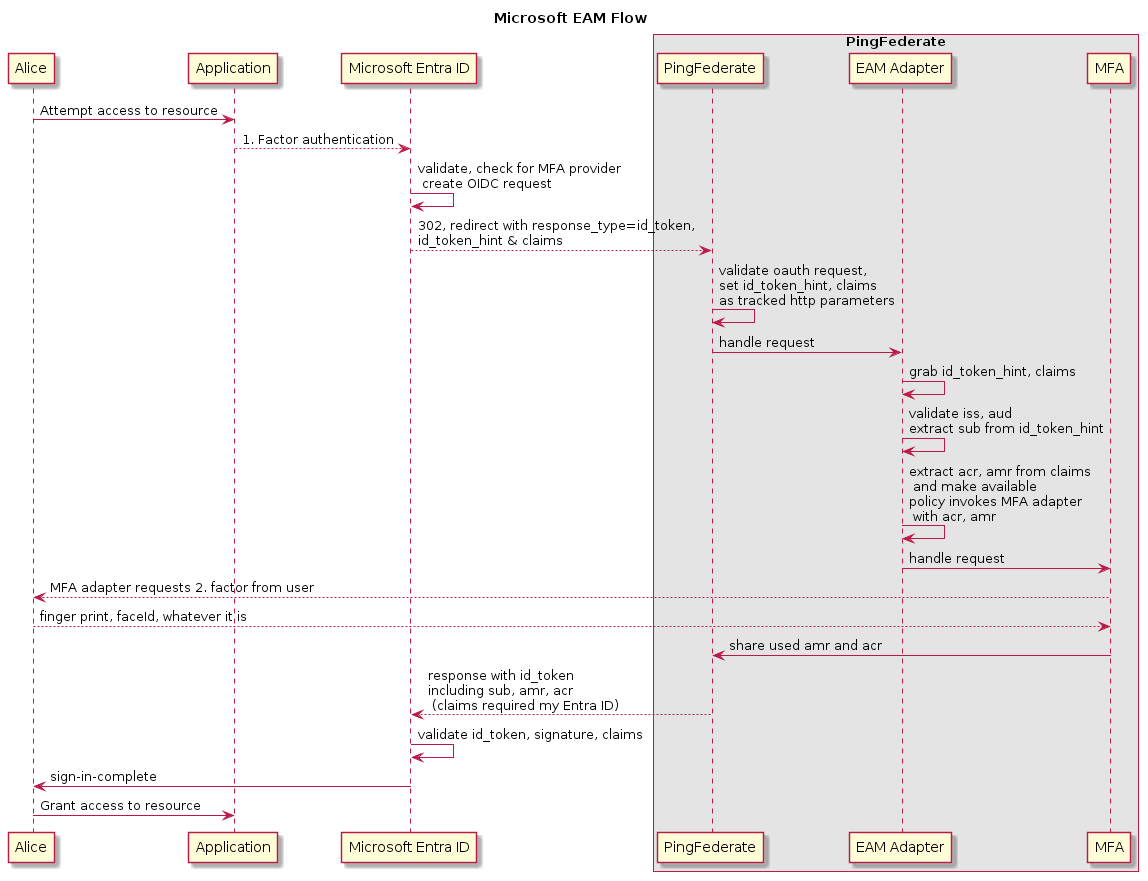
In summary:
-
A user initiates the sign-on process by requesting access to an application that’s protected by Microsoft Entra ID.
-
The user authenticates with Microsoft Entra ID using a primary authentication method.
-
Microsoft Entra ID makes an OpenID Connect (OIDC) request to PingFederate for secondary authentication.
-
PingFederate validates the OIDC request, then sets the id_token_hint and claims provided by Microsoft Entra ID as tracked parameters.
-
The Microsoft EAM IdP Adapter picks up the id_token_hint and claims; validates the id_token_hint; then sets the
sub,acr, andamrvalues for downstream adapters like PingID. -
The downstream adapter requests a second authentication factor from the user.
-
The user authenticates with the downstream adapter using a secondary authentication method.
-
The downstream adapter shares the used
amrandacrvalues with PingFederate. -
PingFederate sends a response to Microsoft Entra ID with the id_token, including the
sub,acr, andamrclaims required by Microsoft Entra ID. -
Microsoft Entra ID validates the id_token, signature, and claims.
-
Microsoft Entra ID grants the user access to the protected application.